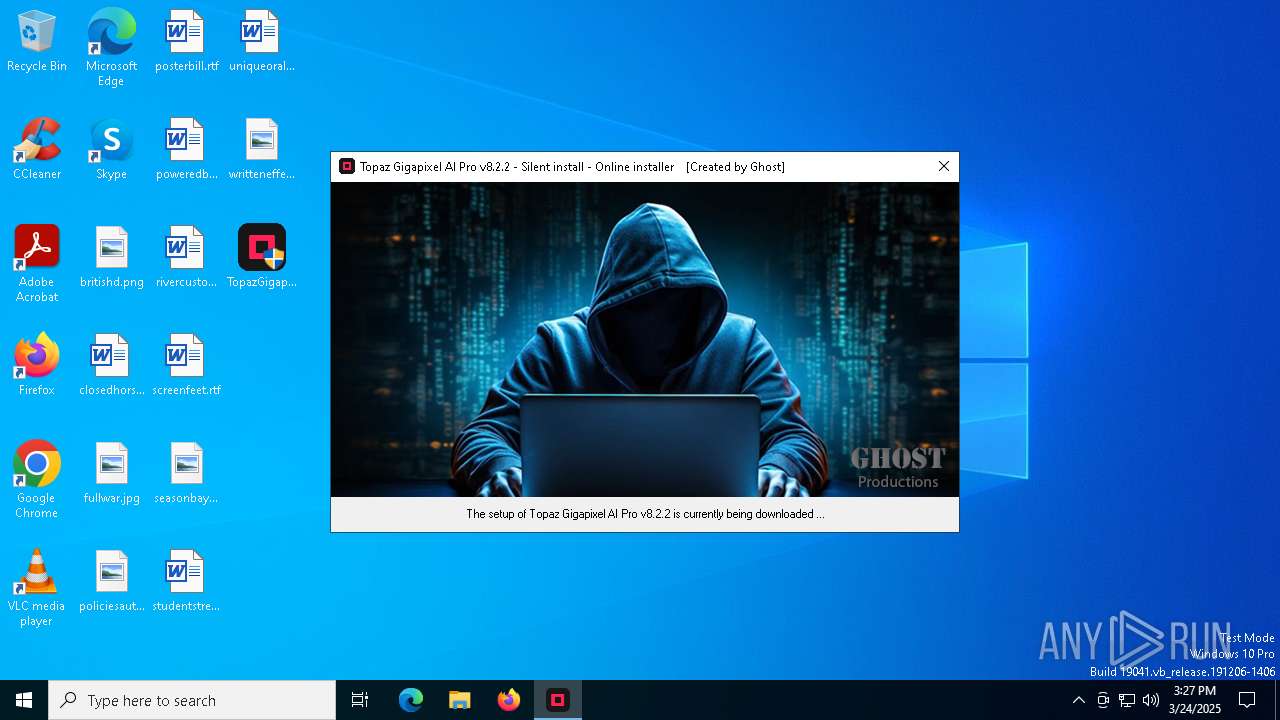
| File name: | TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe |
| Full analysis: | https://app.any.run/tasks/936e7c7f-bbae-42e4-80e0-63b6fb9db8e3 |
| Verdict: | Malicious activity |
| Analysis date: | March 24, 2025, 15:26:51 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, UPX compressed, 3 sections |
| MD5: | B8B574302546C7438DB7789159AE3DF6 |
| SHA1: | C1EA27BF5072BAE210F32AD208D8B818DDBFE240 |
| SHA256: | AD1BF9CB469E21CCD8B6B1A9395DA13A99B1107060C83E78CFEACD481E36FE67 |
| SSDEEP: | 24576:IPP9zj8VMACXt+gR2xRc5AAMGibKza52WbN4pB0P7dP8wd/iQVt12vWzfqKEhdHy:IPP9zj8qACXQgCy6AMGibKza52WbN4pK |
MALICIOUS
Script downloads file (POWERSHELL)
- powershell.exe (PID: 6744)
SUSPICIOUS
Executing commands from ".cmd" file
- TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe (PID: 7688)
Starts CMD.EXE for commands execution
- TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe (PID: 7688)
- cmd.exe (PID: 7736)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 7736)
Downloads file from URI via Powershell
- powershell.exe (PID: 7800)
- powershell.exe (PID: 1324)
There is functionality for taking screenshot (YARA)
- TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe (PID: 7688)
Application launched itself
- cmd.exe (PID: 7736)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 6248)
- cmd.exe (PID: 1052)
Probably download files using WebClient
- cmd.exe (PID: 7736)
INFO
The sample compiled with english language support
- TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe (PID: 7688)
Reads mouse settings
- TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe (PID: 7688)
Checks supported languages
- TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe (PID: 7688)
Reads the computer name
- TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe (PID: 7688)
Create files in a temporary directory
- TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe (PID: 7688)
UPX packer has been detected
- TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe (PID: 7688)
The process uses AutoIt
- TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe (PID: 7688)
Disables trace logs
- powershell.exe (PID: 7800)
Checks proxy server information
- powershell.exe (PID: 7800)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 6744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (43.5) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (42.7) |
| .exe | | | Win32 Executable (generic) (7.2) |
| .exe | | | Generic Win/DOS Executable (3.2) |
| .exe | | | DOS Executable Generic (3.2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2025:02:26 16:10:40+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 380928 |
| InitializedDataSize: | 417792 |
| UninitializedDataSize: | 970752 |
| EntryPoint: | 0x14a720 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 8.2.2.0 |
| ProductVersionNumber: | 8.2.2.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Unknown |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Unicode |
| FileVersion: | 8.2.2.0 |
| Comments: | Always the latest version |
| FileDescription: | Topaz Gigapixel AI Pro v8.2.2 |
| ProductVersion: | 8.2.2.0 |
| CompanyName: | Ghost Productions |
| LegalCopyright: | Ghost |
Total processes
141
Monitored processes
12
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1052 | C:\WINDOWS\system32\cmd.exe /c findstr /r /c:"TopazGigapixelAI-8.2.2*.msi" "C:\Users\admin\AppData\Local\Temp\Ghost\html.txt" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1324 | powershell -Command "Invoke-WebRequest -Uri 'https://community.topazlabs.com/t/gigapixel-8-2-2/87852' -OutFile 'C:\Users\admin\AppData\Local\Temp\Ghost\html.txt' -UseBasicParsing" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4784 | findstr /r /c:"Gigapixel 8.2.2" "C:\Users\admin\AppData\Local\Temp\Ghost\html.txt" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5416 | findstr /r /c:"TopazGigapixelAI-8.2.2*.msi" "C:\Users\admin\AppData\Local\Temp\Ghost\html.txt" | C:\Windows\SysWOW64\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6248 | C:\WINDOWS\system32\cmd.exe /c findstr /r /c:"Gigapixel 8.2.2" "C:\Users\admin\AppData\Local\Temp\Ghost\html.txt" | C:\Windows\SysWOW64\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
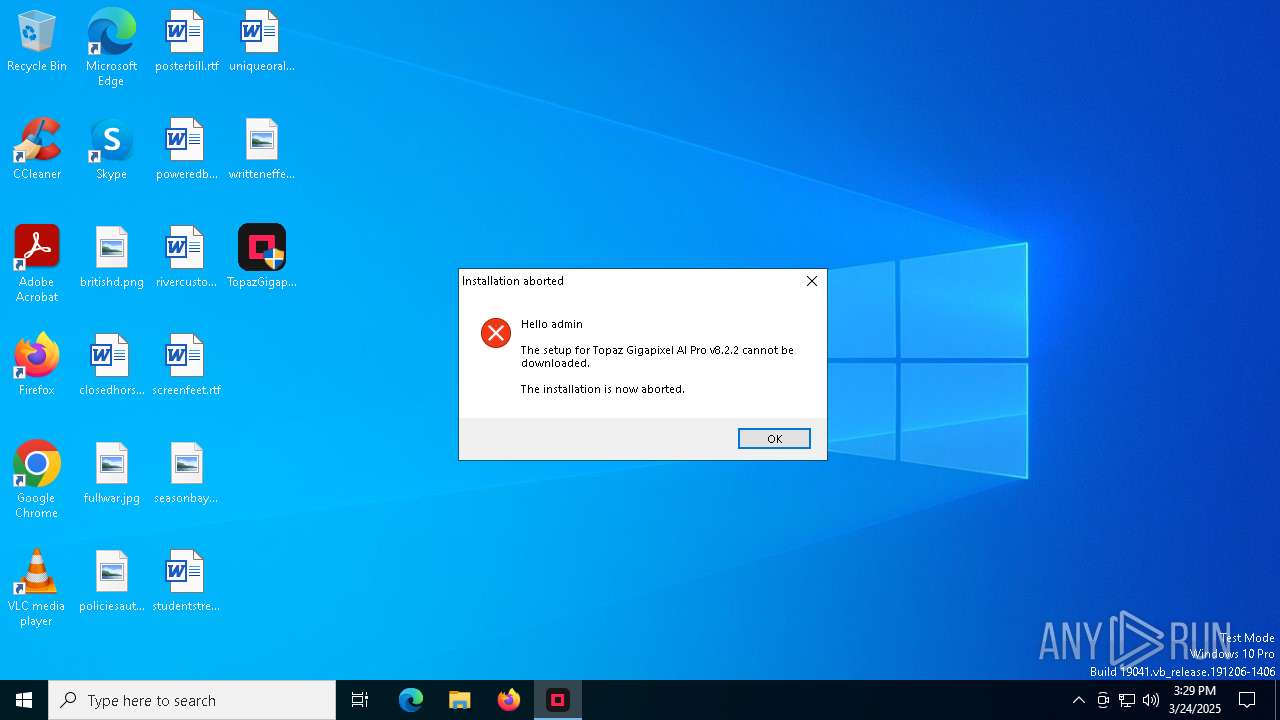
| 6744 | powershell -Command "$webClient = New-Object System.Net.WebClient; $webClient.DownloadFile('https://downloads.topazlabs.com/deploy/TopazGigapixelAI/8.2.2/TopazGigapixelAI-8.2.2.msi', 'C:\Users\admin\AppData\Local\Temp\Ghost\Setup.msi')" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7444 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7580 | "C:\Users\admin\Desktop\TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe" | C:\Users\admin\Desktop\TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe | — | explorer.exe | |||||||||||
User: admin Company: Ghost Productions Integrity Level: MEDIUM Description: Topaz Gigapixel AI Pro v8.2.2 Exit code: 3221226540 Version: 8.2.2.0 Modules
| |||||||||||||||
| 7688 | "C:\Users\admin\Desktop\TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe" | C:\Users\admin\Desktop\TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe | explorer.exe | ||||||||||||
User: admin Company: Ghost Productions Integrity Level: HIGH Description: Topaz Gigapixel AI Pro v8.2.2 Exit code: 0 Version: 8.2.2.0 Modules
| |||||||||||||||
| 7736 | C:\WINDOWS\system32\cmd.exe /c "C:\Users\admin\AppData\Local\Temp\Ghost\Ghost.cmd" | C:\Windows\SysWOW64\cmd.exe | — | TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
18 138
Read events
18 124
Write events
14
Delete events
0
Modification events
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: | |||
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: | |||
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASAPI32 |
| Operation: | write | Name: | FileDirectory |
Value: %windir%\tracing | |||
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableAutoFileTracing |
Value: 0 | |||
| (PID) Process: | (7800) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Tracing\powershell_RASMANCS |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
Executable files
0
Suspicious files
6
Text files
10
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7688 | TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe | C:\Users\admin\AppData\Local\Temp\autE1E7.tmp | binary | |
MD5:1B525660EF5F8B63642A15EC89E5940B | SHA256:0398CA5BE0B3473DECF85EA29E45AF83C5EE0D01D58C8AD87E54A51F6AA9B2EA | |||
| 1324 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_wz5kylow.rqt.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7688 | TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe | C:\Users\admin\AppData\Local\Temp\~DFB163197A649F267D.TMP | binary | |
MD5:B53513A93B784E8F8ED62ED23904FC93 | SHA256:820943C5F290136B7BEF26B8807E65854C12B3463D2025691989879B0DE037C3 | |||
| 1324 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_ecu3k0x3.clo.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7800 | powershell.exe | C:\Users\admin\AppData\Local\Temp\Ghost\html.txt | html | |
MD5:50C436D85B8EAE4428631F228EFECD80 | SHA256:63A5DE8FF2798C2215959B110B2090554533B5B10451E0F538E1D60DE8E17A6E | |||
| 7800 | powershell.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\PowerShell\StartupProfileData-NonInteractive | binary | |
MD5:3466B9F556F04E21C02078BD49704793 | SHA256:03B8FEB15D5EB05F728D653B7CFF4066422840D39D408AAF1FB584C0D5F80805 | |||
| 7736 | cmd.exe | C:\Users\admin\AppData\Local\Temp\Ghost\nummer.txt | text | |
MD5:F4EB5C50EB1655643DCA5DFA5881C428 | SHA256:A518D826D74B7BB54F4B670E486E56E3601ED6305E69C67B5D4BDB73B89517D3 | |||
| 7800 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_w2xqhbwe.rhe.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7800 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_nxg4qfjd.sf0.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7688 | TopazGigapixelAIProv8.2.2ONLINEbyGhost.exe | C:\Users\admin\AppData\Local\Temp\Ghost\Banner.jpg | binary | |
MD5:AA2A2EBD443366E37324B87E399A78AE | SHA256:9B4C3645E0AC4D30BE53802511EC952976D2E21847E67485C211B1E6A63F5169 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
36
TCP/UDP connections
59
DNS requests
17
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 20.109.210.53:443 | https://slscr.update.microsoft.com/SLS/%7B522D76A4-93E1-47F8-B8CE-07C937AD1A1E%7D/x64/10.0.19045.4046/0?CH=686&L=en-US&P=&PT=0x30&WUA=10.0.19041.3996&MK=DELL&MD=DELL | unknown | — | — | unknown |
8176 | SIHClient.exe | GET | 200 | 23.48.23.139:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
8176 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
8176 | SIHClient.exe | GET | 200 | 23.48.23.139:80 | http://crl.microsoft.com/pki/crl/products/MicTimStaPCA_2010-07-01.crl | unknown | — | — | whitelisted |
8176 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
8176 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Signing%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.3.187.198:443 | https://fe3cr.delivery.mp.microsoft.com/clientwebservice/ping | unknown | — | — | unknown |
— | — | POST | — | 20.190.160.22:443 | https://login.live.com/RST2.srf | unknown | — | — | whitelisted |
— | — | GET | 200 | 20.223.35.26:443 | https://arc.msn.com/v3/Delivery/Placement?pubid=da63df93-3dbc-42ae-a505-b34988683ac7&pid=280815&adm=2&w=1&h=1&wpx=1&hpx=1&fmt=json&cltp=app&dim=le&rafb=0&nct=1&pm=1&cfmt=text,image,poly&sft=jpeg,png,gif&topt=1&poptin=0&localid=w:AC7699B0-48EA-FD22-C8DC-06A02098A0F0&ctry=US&time=20250324T152702Z&lc=en-US&pl=en-US&idtp=mid&uid=9115d6d1-9f4e-4053-9297-2a8c833b3912&aid=00000000-0000-0000-0000-000000000000&ua=WindowsShellClient%2F9.0.40929.0%20%28Windows%29&asid=2c155c384e354efeba2fad0882286025&ctmode=MultiSession&arch=x64&betaedgever=0.0.0.0&canedgever=0.0.0.0&cdm=1&cdmver=10.0.19041.3636&currsel=137271744000000000&devedgever=0.0.0.0&devfam=Windows.Desktop&devform=Unknown&devosver=10.0.19045.4046&disphorzres=1280&dispsize=15.3&dispvertres=720&fosver=16299&isu=0&lo=3967646&metered=false&nettype=ethernet&npid=sc-280815&oemName=DELL&oemid=DELL&ossku=Professional&prevosver=15063&smBiosDm=DELL&stabedgever=122.0.2365.59&tl=2&tsu=1358176&waasBldFlt=1&waasCfgExp=1&waasCfgSet=1&waasRetail=1&waasRing=&svoffered=2 | unknown | binary | 2.95 Kb | whitelisted |
— | — | POST | 200 | 20.190.160.3:443 | https://login.live.com/RST2.srf | unknown | xml | 1.35 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
664 | backgroundTaskHost.exe | 20.223.35.26:443 | arc.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 20.190.160.3:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
arc.msn.com |
| whitelisted |
google.com |
| whitelisted |
community.topazlabs.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |
— | — | Not Suspicious Traffic | ET INFO Windows Powershell User-Agent Usage |