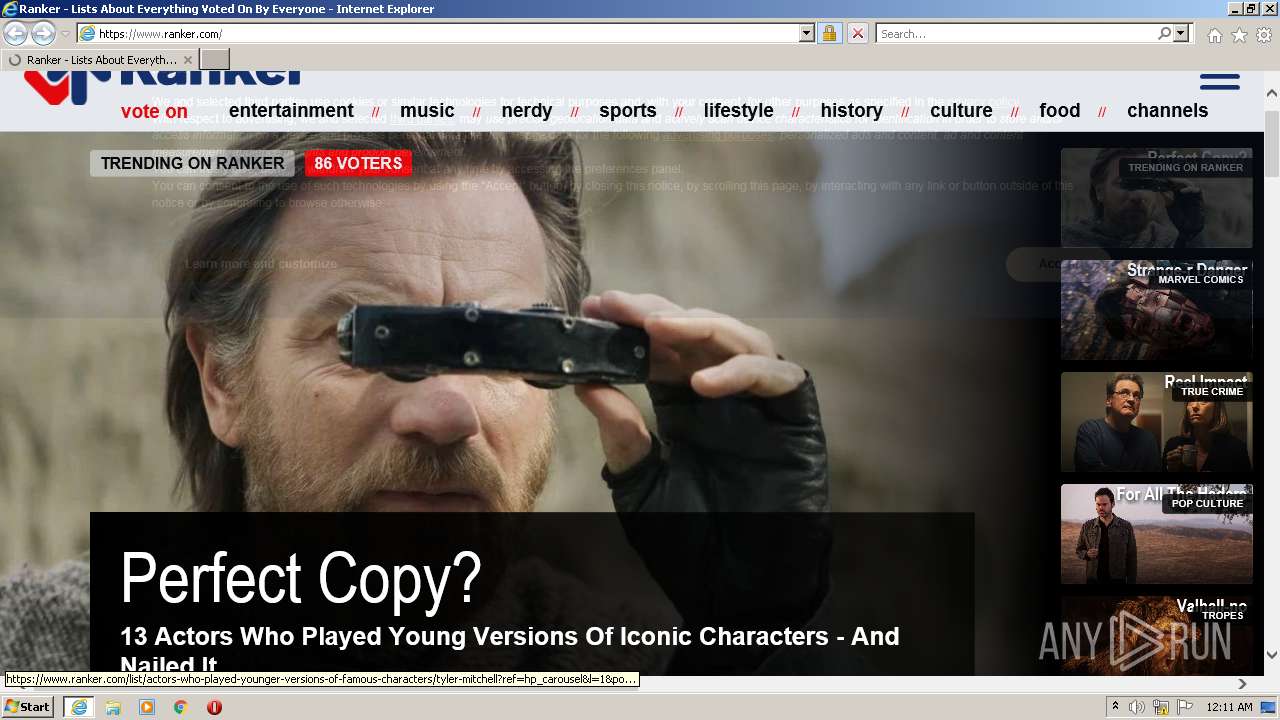
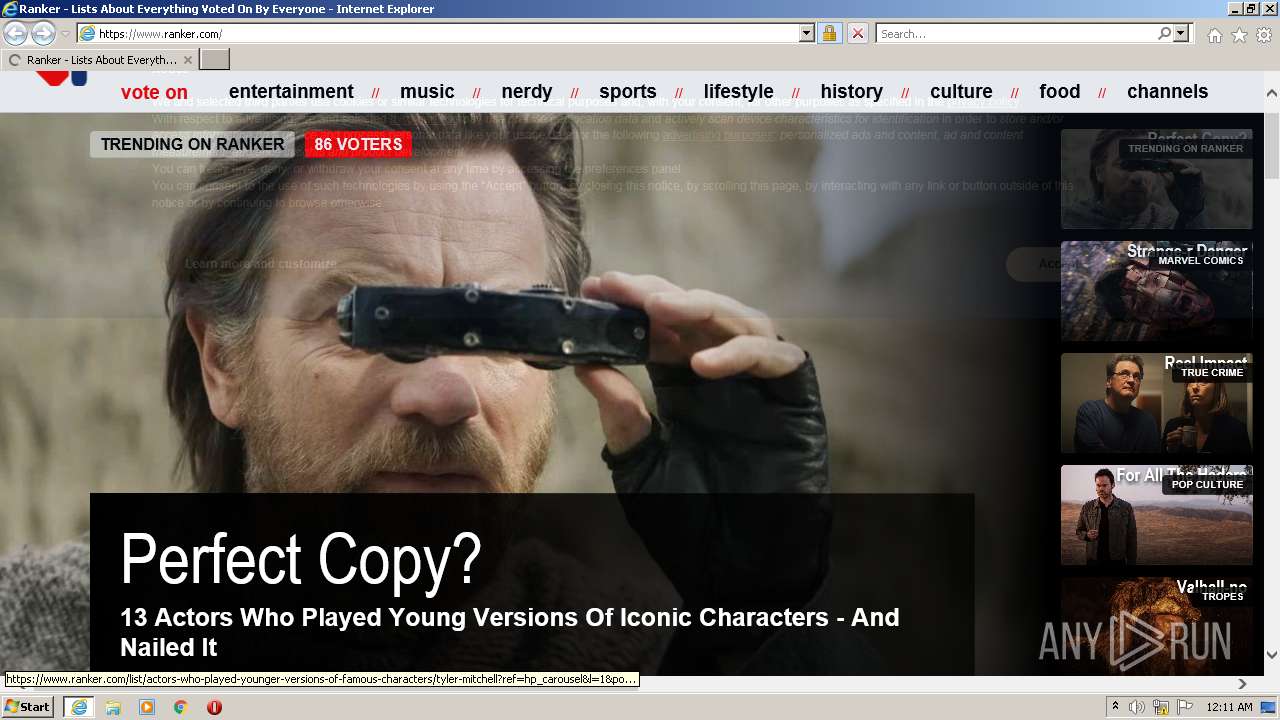
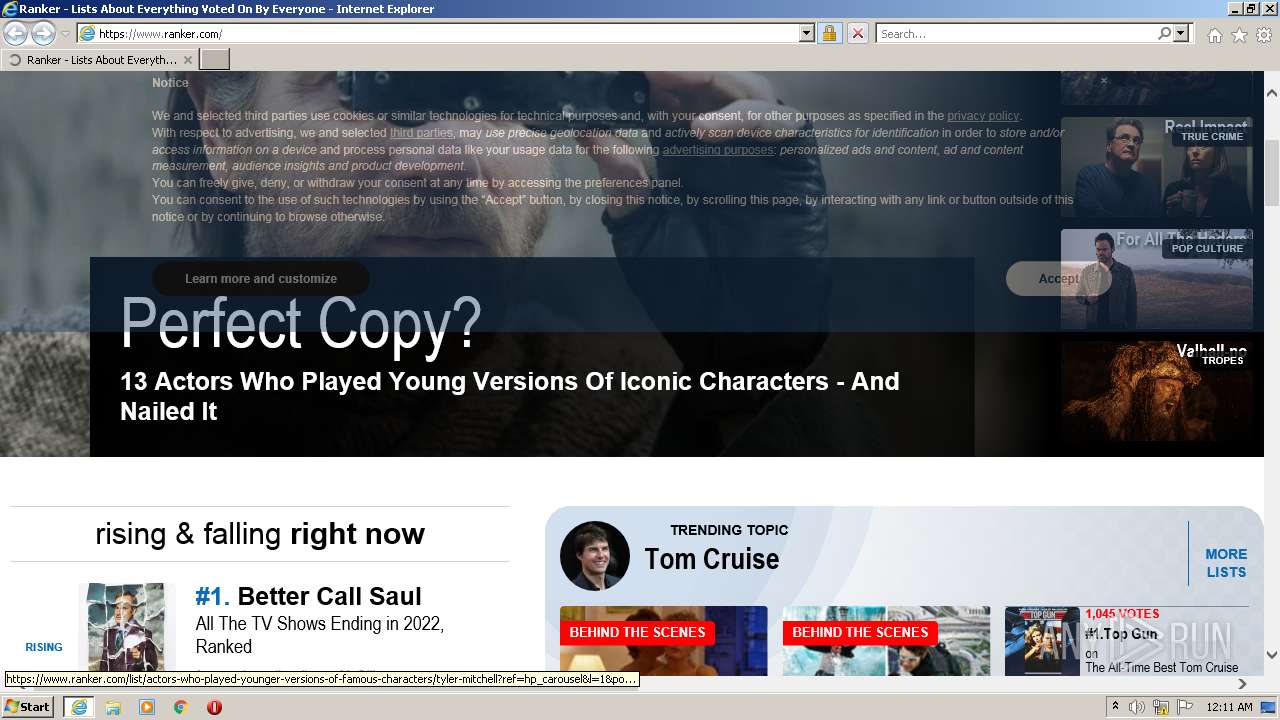
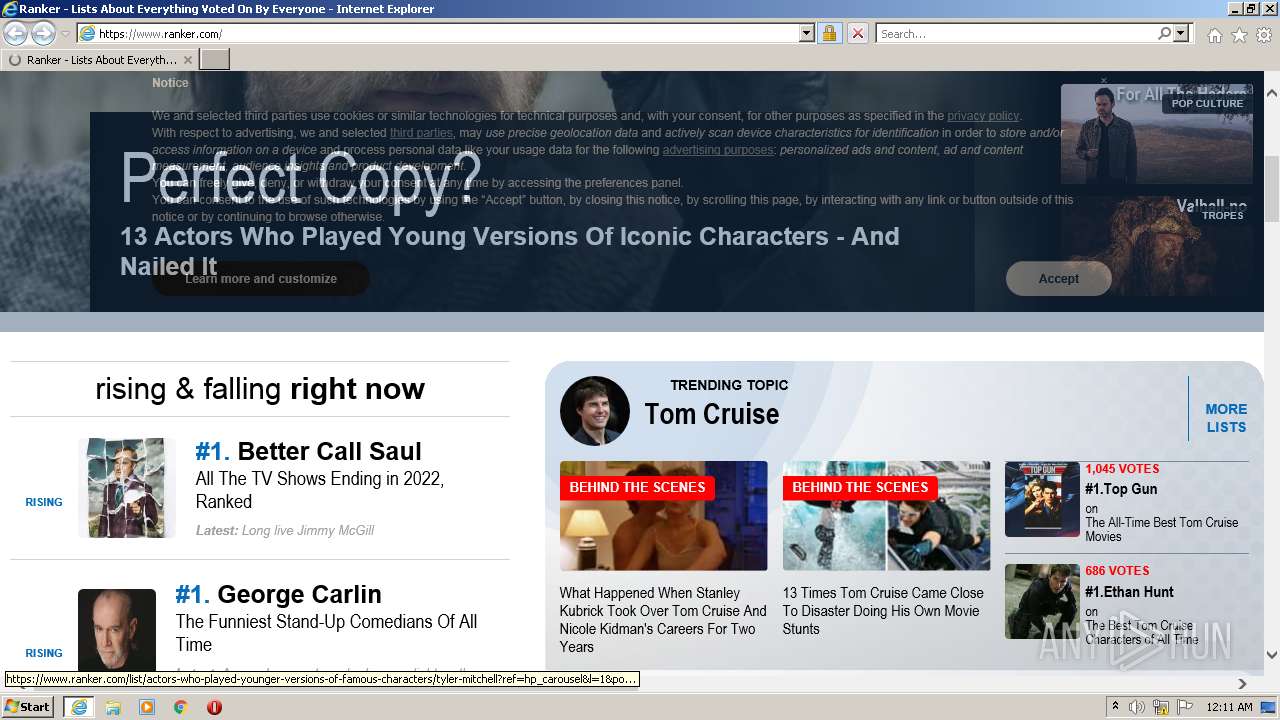
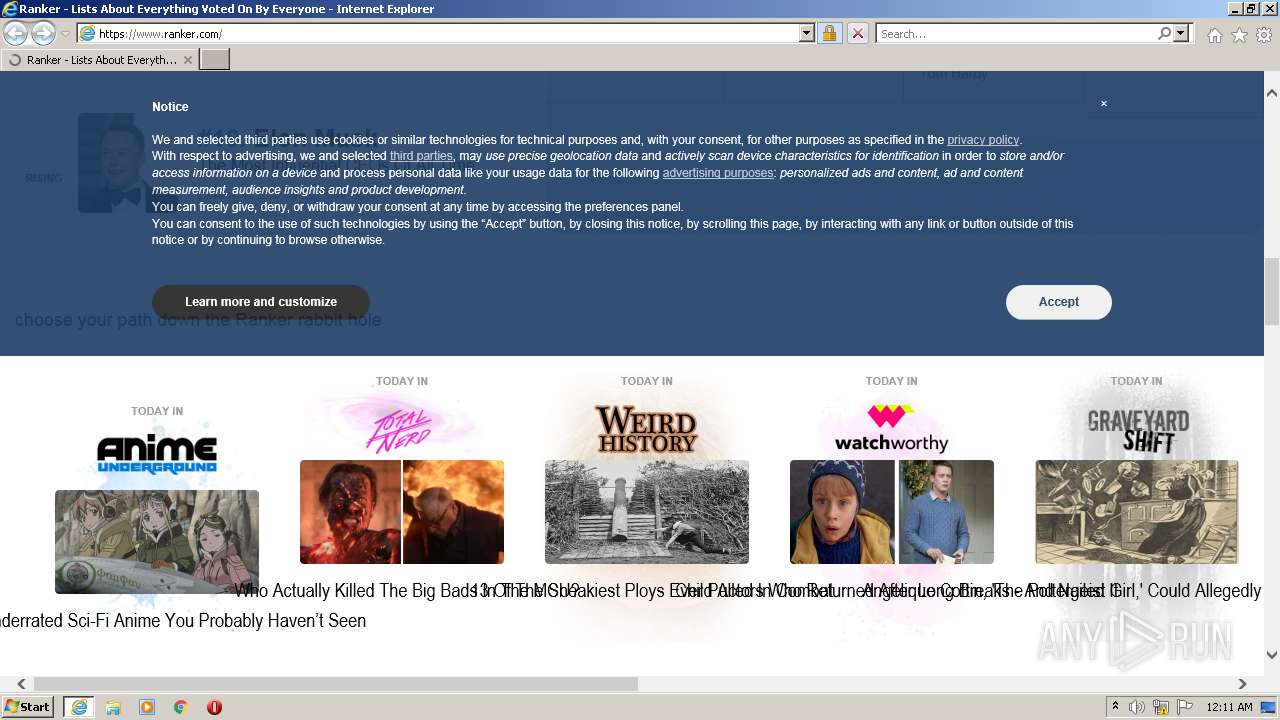
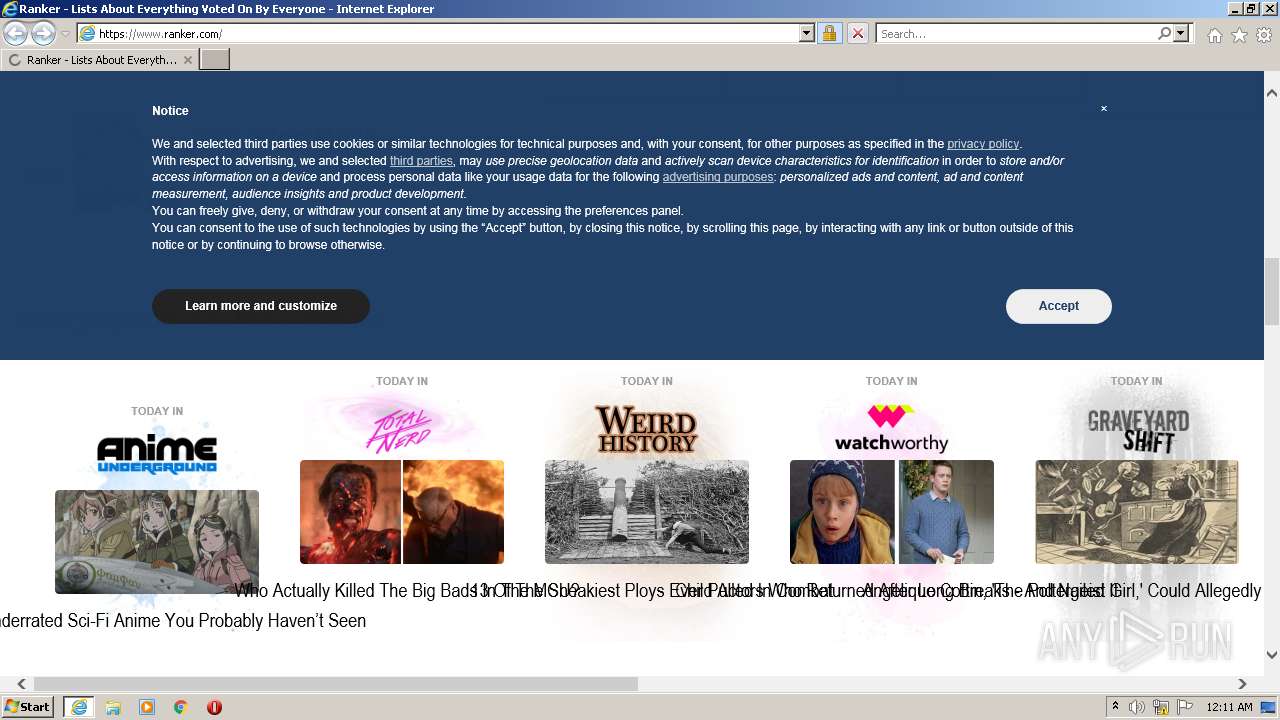
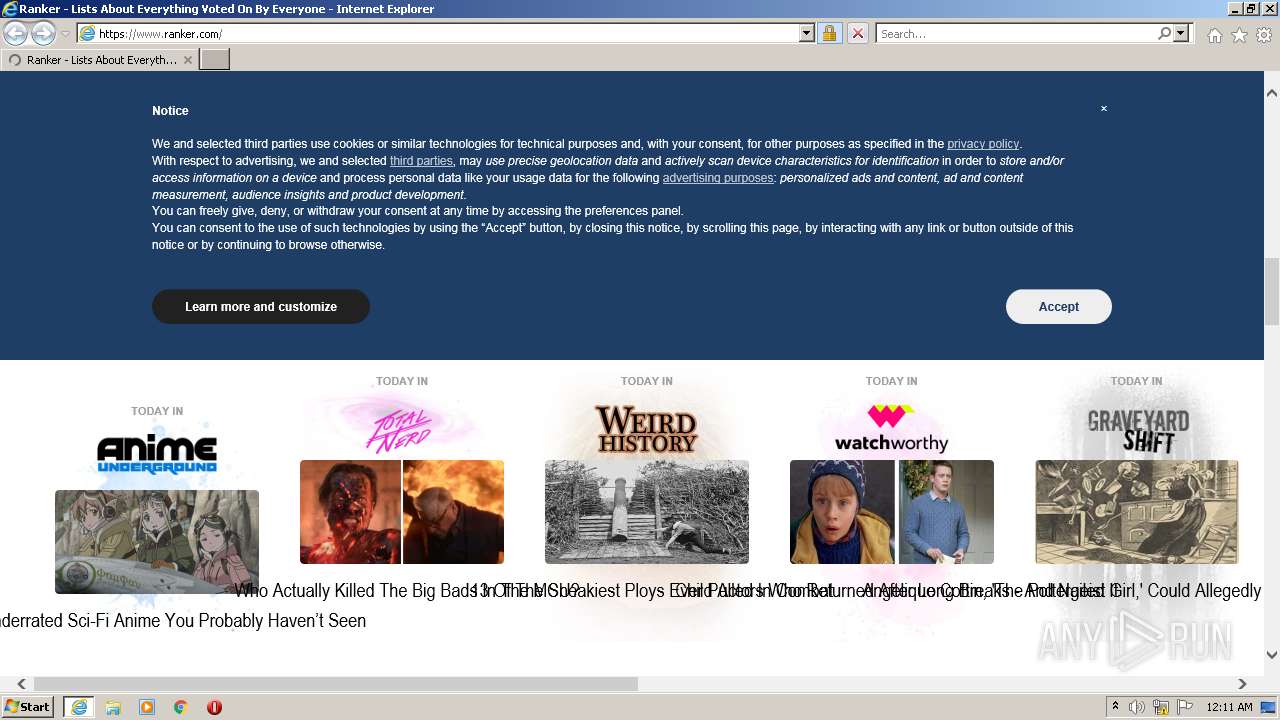
| URL: | https://m.ranker.com/ |
| Full analysis: | https://app.any.run/tasks/7e71d363-e05d-4552-b5b6-b2696922f084 |
| Verdict: | Malicious activity |
| Analysis date: | May 20, 2022, 23:11:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 34576CE070079391EFA348278288A7CE |
| SHA1: | CA8E40685DEB664555DE6453CAE9B82DEA2FCA5B |
| SHA256: | AD0218B9C73B68BAB15208C71DE5B0620878C8BF56F9AF003507104C3F002EC1 |
| SSDEEP: | 3:N8vZ3:2vZ3 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 2124)
INFO
Checks supported languages
- iexplore.exe (PID: 2124)
- iexplore.exe (PID: 1976)
Changes internet zones settings
- iexplore.exe (PID: 1976)
Reads the computer name
- iexplore.exe (PID: 1976)
- iexplore.exe (PID: 2124)
Application launched itself
- iexplore.exe (PID: 1976)
Reads settings of System Certificates
- iexplore.exe (PID: 2124)
- iexplore.exe (PID: 1976)
Checks Windows Trust Settings
- iexplore.exe (PID: 2124)
- iexplore.exe (PID: 1976)
Creates files in the user directory
- iexplore.exe (PID: 2124)
Reads internet explorer settings
- iexplore.exe (PID: 2124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
36
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1976 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://m.ranker.com/" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2124 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1976 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
14 618
Read events
14 484
Write events
134
Delete events
0
Modification events
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960798 | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960798 | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1976) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
24
Text files
132
Unknown types
20
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2124 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\715Z9KQN.txt | text | |
MD5:— | SHA256:— | |||
| 2124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | der | |
MD5:— | SHA256:— | |||
| 2124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\db83d5eec292fd5ac226[1].css | text | |
MD5:— | SHA256:— | |||
| 2124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\52EWC05Y.htm | html | |
MD5:— | SHA256:— | |||
| 2124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:— | SHA256:— | |||
| 2124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\7b5bf61d9aec8225f02b[1].css | text | |
MD5:— | SHA256:— | |||
| 2124 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 2124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\dfcfa5d4eb2a25a3bd30[1].css | text | |
MD5:— | SHA256:— | |||
| 2124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\elon-musk-photo-u14[1].jpg | image | |
MD5:— | SHA256:— | |||
| 2124 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\the-kids-in-the-hall-photo-u5[1].jpg | image | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
21
TCP/UDP connections
67
DNS requests
30
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2124 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEAXk3DuUOKs7hZfLpqGYUOM%3D | US | der | 727 b | whitelisted |
2124 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRDC9IOTxN6GmyRjyTl2n4yTUczyAQUjYxexFStiuF36Zv5mwXhuAGNYeECEAD1mg4vY3OWNHCY%2FWzBCII%3D | US | der | 471 b | whitelisted |
2124 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAfy81yHqHeveu%2FpR5k1Jb0%3D | US | der | 471 b | whitelisted |
2124 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
2124 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEFZnHQTqT5lMbxCBR1nSdZQ%3D | US | der | 471 b | whitelisted |
2124 | iexplore.exe | GET | 200 | 142.250.186.131:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
2124 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBSr83eyJy3njhjVpn5bEpfc6MXawQQUOuEJhtTPGcKWdnRJdtzgNcZjY5oCEQDzZE5rbgBQI34JRr174fUd | US | der | 315 b | whitelisted |
2124 | iexplore.exe | GET | 200 | 104.18.32.68:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTPlNxcMEqnlIVyH5VuZ4lawhZX3QQU9oUKOxGG4QR9DqoLLNLuzGR7e64CECaskpnzeBKasxyXxNJbmBs%3D | US | der | 279 b | whitelisted |
1976 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | der | 1.47 Kb | whitelisted |
2124 | iexplore.exe | GET | 200 | 172.64.155.188:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEDlyRDr5IrdR19NsEN0xNZU%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2124 | iexplore.exe | 184.51.85.186:443 | cdn.iubenda.com | Akamai Technologies, Inc. | US | unknown |
2124 | iexplore.exe | 23.50.131.221:443 | m.ranker.com | TELECOM ITALIA SPARKLE S.p.A. | NL | unknown |
2124 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
2124 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2124 | iexplore.exe | 23.50.131.201:443 | www.ranker.com | TELECOM ITALIA SPARKLE S.p.A. | NL | suspicious |
2124 | iexplore.exe | 23.50.131.200:443 | static.ranker.com | TELECOM ITALIA SPARKLE S.p.A. | NL | suspicious |
2124 | iexplore.exe | 23.50.131.204:443 | imgix.ranker.com | TELECOM ITALIA SPARKLE S.p.A. | NL | unknown |
2124 | iexplore.exe | 142.250.186.131:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2124 | iexplore.exe | 142.250.186.136:443 | www.googletagmanager.com | Google Inc. | US | suspicious |
2124 | iexplore.exe | 108.138.2.10:80 | o.ss2.us | BellSouth.net Inc. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
m.ranker.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.ranker.com |
| malicious |
static.ranker.com |
| suspicious |
imgix.ranker.com |
| whitelisted |
cdn.p-n.io |
| shared |
www.googletagmanager.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
cdn.keywee.co |
| whitelisted |