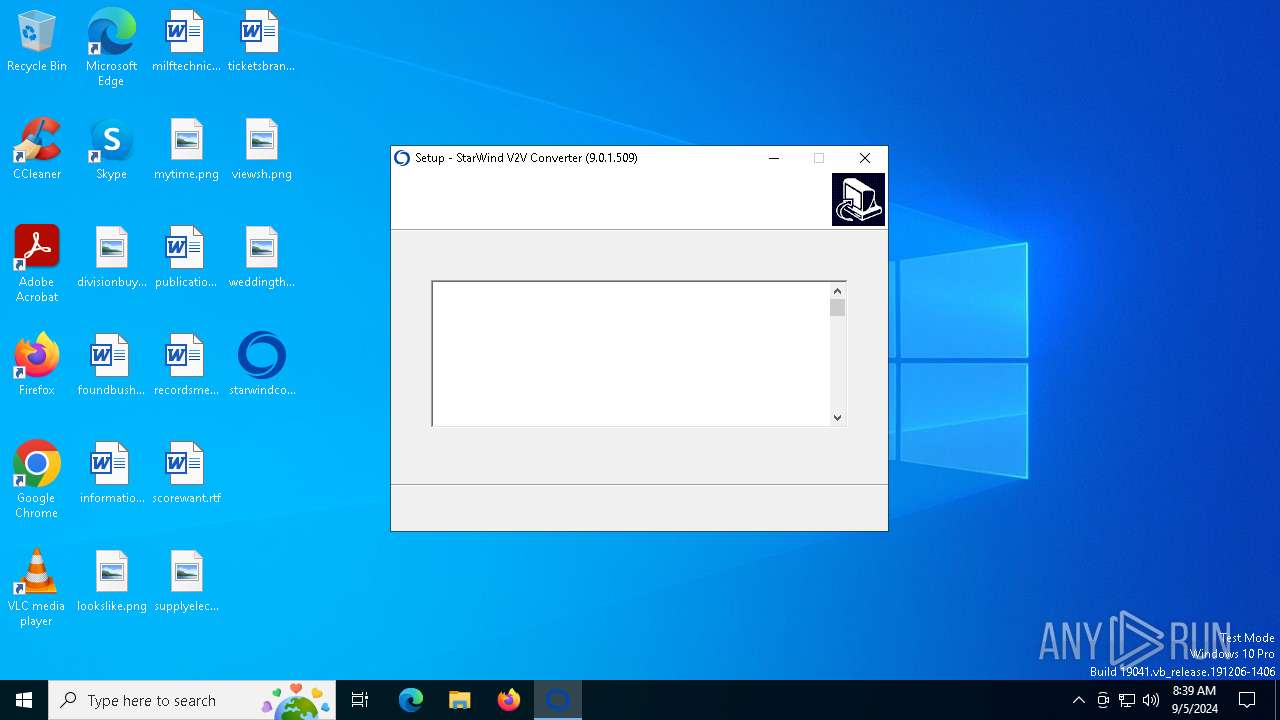
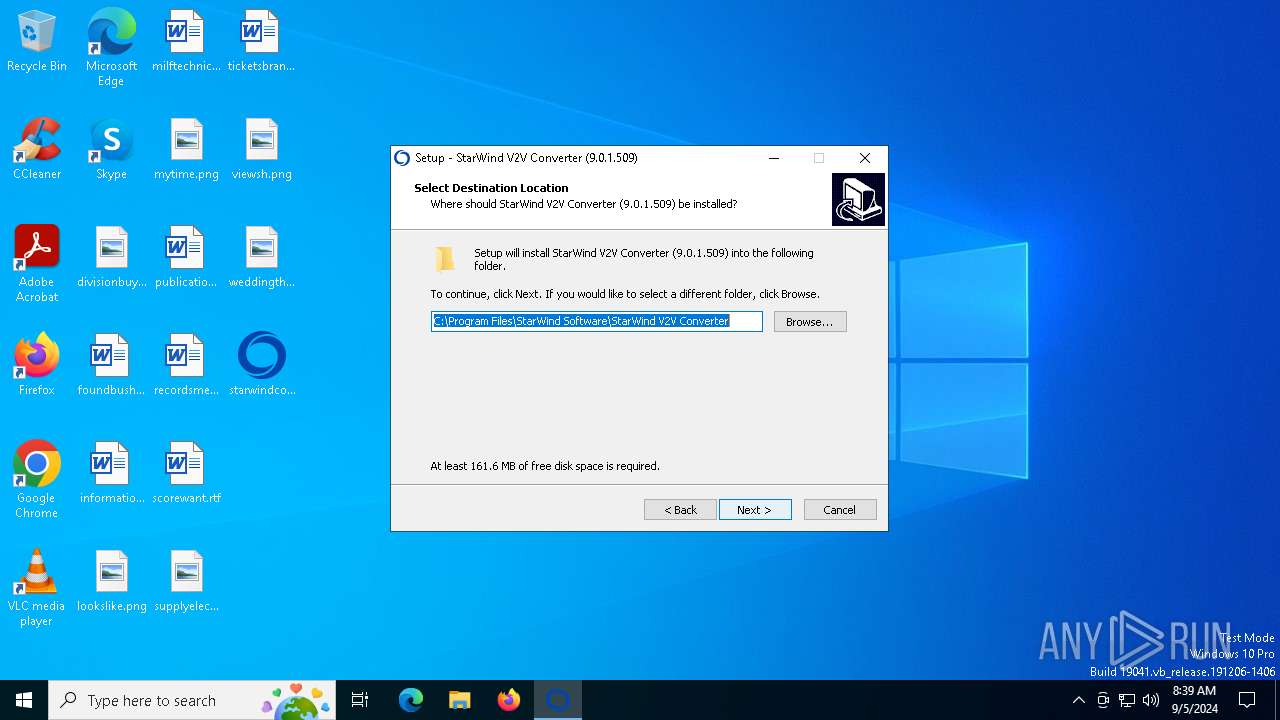
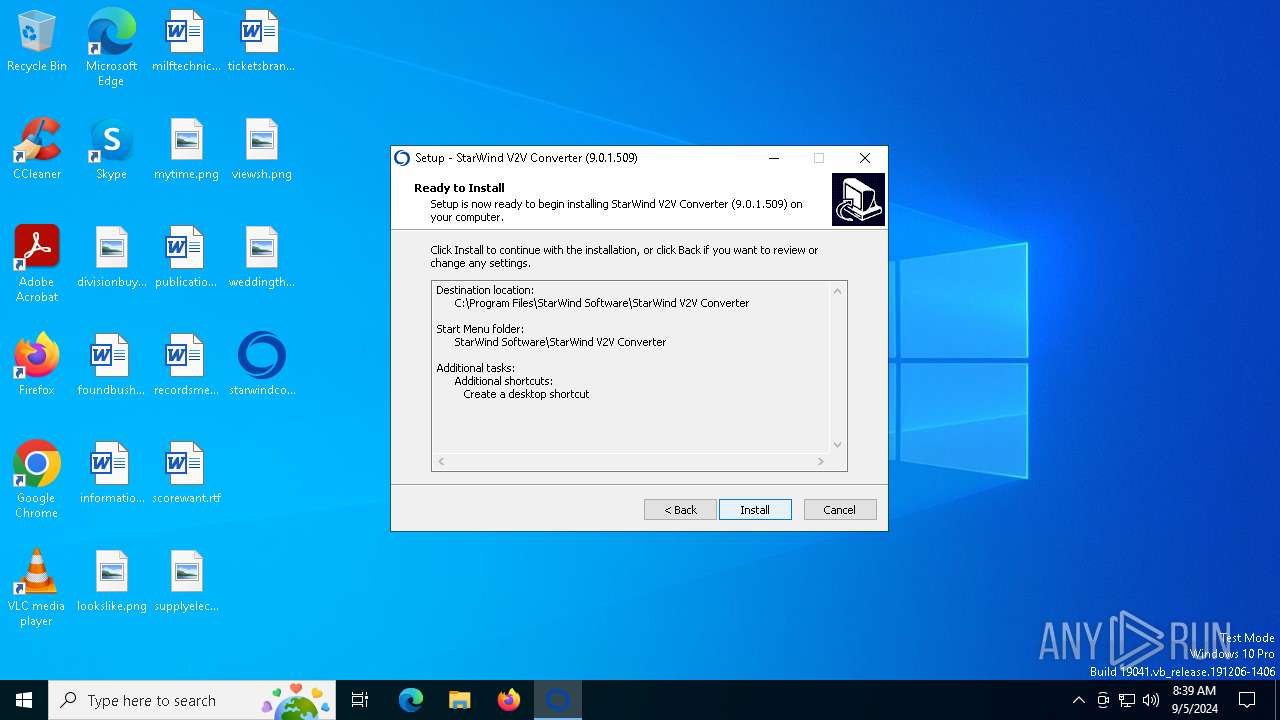
| File name: | starwindconverter.exe |
| Full analysis: | https://app.any.run/tasks/359cb65a-327a-46c0-a5a3-2c84f9fe2973 |
| Verdict: | Malicious activity |
| Analysis date: | September 05, 2024, 08:38:43 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 06DF1D80075680439507FACB6888DB5E |
| SHA1: | CB0AF930B0D2F29D5F0F7757D8C265CB75D36958 |
| SHA256: | AD01DC3DCF725BEE263C04729AB1F4D6EA668CC5AAF7B0547416BE1B9F84A72E |
| SSDEEP: | 393216:MjOBzuVCSkmmw3oI1l7TxtLyhMOuqy6iDaLG5XOqpW4rC:MjfSavDxXOAjsN |
MALICIOUS
Changes the autorun value in the registry
- vc_redist.x64.130.exe (PID: 2368)
SUSPICIOUS
Executable content was dropped or overwritten
- starwindconverter.exe (PID: 4876)
- cmd.exe (PID: 5656)
- vc_redist.x64.130.exe (PID: 2384)
- vc_redist.x64.140.exe (PID: 5292)
Reads security settings of Internet Explorer
- starwindconverter.tmp (PID: 6628)
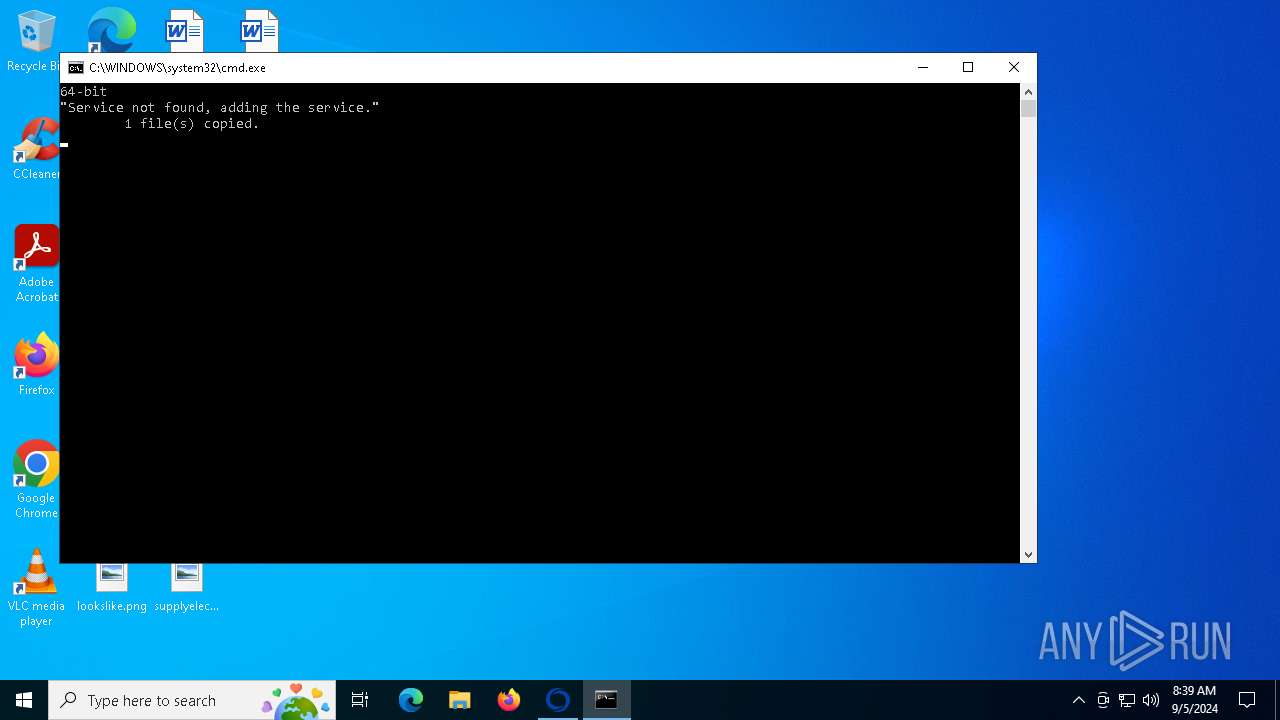
Starts SC.EXE for service management
- cmd.exe (PID: 5656)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 5656)
Drops a system driver (possible attempt to evade defenses)
- cmd.exe (PID: 5656)
Creates files in the driver directory
- cmd.exe (PID: 5656)
Uses WMIC.EXE to obtain operating system information
- cmd.exe (PID: 5656)
Application launched itself
- vc_redist.x64.130.exe (PID: 2368)
- vc_redist.x64.140.exe (PID: 1780)
Process drops legitimate windows executable
- vc_redist.x64.130.exe (PID: 2384)
- vc_redist.x64.140.exe (PID: 5292)
Searches for installed software
- vc_redist.x64.130.exe (PID: 2368)
- dllhost.exe (PID: 4060)
- vc_redist.x64.140.exe (PID: 5292)
- vc_redist.x64.130.exe (PID: 2384)
Executes as Windows Service
- VSSVC.exe (PID: 7108)
INFO
Checks supported languages
- starwindconverter.tmp (PID: 6628)
- starwindconverter.exe (PID: 4876)
- vc_redist.x64.130.exe (PID: 2368)
- vc_redist.x64.130.exe (PID: 2384)
- vc_redist.x64.140.exe (PID: 1780)
- vc_redist.x64.140.exe (PID: 5292)
Create files in a temporary directory
- starwindconverter.exe (PID: 4876)
- vc_redist.x64.130.exe (PID: 2384)
- vc_redist.x64.140.exe (PID: 5292)
Process checks computer location settings
- starwindconverter.tmp (PID: 6628)
Reads the computer name
- starwindconverter.tmp (PID: 6628)
- vc_redist.x64.130.exe (PID: 2384)
- vc_redist.x64.140.exe (PID: 5292)
- vc_redist.x64.140.exe (PID: 1780)
- vc_redist.x64.130.exe (PID: 2368)
Reads security settings of Internet Explorer
- WMIC.exe (PID: 6200)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Inno Setup installer (91.2) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (3.7) |
| .exe | | | Win16/32 Executable Delphi generic (1.7) |
| .exe | | | Generic Win/DOS Executable (1.6) |
| .exe | | | DOS Executable Generic (1.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 1992:06:19 22:22:17+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, Bytes reversed lo, 32-bit, Bytes reversed hi |
| PEType: | PE32 |
| LinkerVersion: | 2.25 |
| CodeSize: | 41472 |
| InitializedDataSize: | 296448 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xaa98 |
| OSVersion: | 1 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 9.0.1.509 |
| ProductVersionNumber: | 9.0.1.509 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Neutral |
| CharacterSet: | Unicode |
| Comments: | This installation was built with Inno Setup. |
| CompanyName: | StarWind Software |
| FileDescription: | StarWind V2V Converter |
| FileVersion: | 9.0.1.509 |
| LegalCopyright: | StarWind Software Inc. All rights reserved. |
| ProductName: | StarWind V2V Converter |
| ProductVersion: | 9.0 build 509 |
Total processes
135
Monitored processes
18
Malicious processes
4
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1020 | sc start vstor2-mntapi20-shared | C:\Windows\System32\sc.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Service Control Manager Configuration Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1780 | "C:\Program Files\StarWind Software\StarWind V2V Converter\vc\vc_redist.x64.140.exe" /quiet | C:\Program Files\StarWind Software\StarWind V2V Converter\vc\vc_redist.x64.140.exe | — | starwindconverter.tmp | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2015 Redistributable (x64) - 14.0.23026 Exit code: 1638 Version: 14.0.23026.0 Modules
| |||||||||||||||
| 2080 | findstr 64 | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2368 | "C:\Program Files\StarWind Software\StarWind V2V Converter\vc\vc_redist.x64.130.exe" /quiet | C:\Program Files\StarWind Software\StarWind V2V Converter\vc\vc_redist.x64.130.exe | starwindconverter.tmp | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2013 Redistributable (x64) - 12.0.30501 Exit code: 0 Version: 12.0.30501.0 Modules
| |||||||||||||||
| 2384 | "C:\Program Files\StarWind Software\StarWind V2V Converter\vc\vc_redist.x64.130.exe" /quiet -burn.unelevated BurnPipe.{429A3722-7D83-438F-8B38-7928192124E7} {C6CE9B65-6B27-40B0-9382-BEFEE0489958} 2368 | C:\Program Files\StarWind Software\StarWind V2V Converter\vc\vc_redist.x64.130.exe | vc_redist.x64.130.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Visual C++ 2013 Redistributable (x64) - 12.0.30501 Exit code: 0 Version: 12.0.30501.0 Modules
| |||||||||||||||
| 3304 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | dllhost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4060 | C:\WINDOWS\system32\DllHost.exe /Processid:{F32D97DF-E3E5-4CB9-9E3E-0EB5B4E49801} | C:\Windows\System32\dllhost.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: COM Surrogate Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4876 | "C:\Users\admin\Desktop\starwindconverter.exe" | C:\Users\admin\Desktop\starwindconverter.exe | explorer.exe | ||||||||||||
User: admin Company: StarWind Software Integrity Level: MEDIUM Description: StarWind V2V Converter Exit code: 0 Version: 9.0.1.509 Modules
| |||||||||||||||
| 5184 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
2 333
Read events
2 139
Write events
171
Delete events
23
Modification events
| (PID) Process: | (4060) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 48000000000000000B3282266FFFDA01DC0F0000441B0000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2368) vc_redist.x64.130.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 40000000000000000B3282266FFFDA0140090000D4180000D5070000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4060) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000007DD5BD266FFFDA01DC0F0000441B0000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4060) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 4800000000000000613AC0266FFFDA01DC0F0000441B0000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4060) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000D08BC2266FFFDA01DC0F0000441B0000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4060) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000006255C7266FFFDA01DC0F0000441B0000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4060) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (4060) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 480000000000000039E32D276FFFDA01DC0F0000441B0000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4060) dllhost.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000000B4730276FFFDA01DC0F0000D8070000E8030000010000000000000000000000C94C79C85671B84F8A8F242787E92A6B00000000000000000000000000000000 | |||
| (PID) Process: | (7108) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 480000000000000082FA34276FFFDA01C41B0000E41B0000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
5
Suspicious files
3
Text files
38
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4060 | dllhost.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 4876 | starwindconverter.exe | C:\Users\admin\AppData\Local\Temp\is-IA97D.tmp\starwindconverter.tmp | executable | |
MD5:4005538D0689C8182A32DCF5AE91008E | SHA256:3F6B4C708994788167BA110B0E2E88398D904511F6CE1720B6DB5F10286397BB | |||
| 5656 | cmd.exe | C:\Windows\System32\drivers\vstor2-mntapi20-shared.sys | executable | |
MD5:701F6FB77B31ED04321108C264D04DE0 | SHA256:ADE2410D00A9667B4003BB9ECFE7F64621151246F44CD3A55BF322BEE950181C | |||
| 2384 | vc_redist.x64.130.exe | C:\Users\admin\AppData\Local\Temp\{050d4fc8-5d48-4b8f-8972-47c82c46020f}\.ba1\logo.png | image | |
MD5:D6BD210F227442B3362493D046CEA233 | SHA256:335A256D4779EC5DCF283D007FB56FD8211BBCAF47DCD70FE60DED6A112744EF | |||
| 2384 | vc_redist.x64.130.exe | C:\Users\admin\AppData\Local\Temp\{050d4fc8-5d48-4b8f-8972-47c82c46020f}\.ba1\thm.wxl | xml | |
MD5:FBFCBC4DACC566A3C426F43CE10907B6 | SHA256:70400F181D00E1769774FF36BCD8B1AB5FBC431418067D31B876D18CC04EF4CE | |||
| 2384 | vc_redist.x64.130.exe | C:\Users\admin\AppData\Local\Temp\{050d4fc8-5d48-4b8f-8972-47c82c46020f}\.ba1\wixstdba.dll | executable | |
MD5:A52E5220EFB60813B31A82D101A97DCB | SHA256:E7C8E7EDD9112137895820E789BAAAECA41626B01FB99FEDE82968DDB66D02CF | |||
| 5292 | vc_redist.x64.140.exe | C:\Users\admin\AppData\Local\Temp\{e46eca4f-393b-40df-9f49-076faf788d83}\.ba1\wixstdba.dll | executable | |
MD5:4D20A950A3571D11236482754B4A8E76 | SHA256:A9295AD4E909F979E2B6CB2B2495C3D35C8517E689CD64A918C690E17B49078B | |||
| 2384 | vc_redist.x64.130.exe | C:\Users\admin\AppData\Local\Temp\{050d4fc8-5d48-4b8f-8972-47c82c46020f}\.ba1\BootstrapperApplicationData.xml | xml | |
MD5:0BD4FA44198EB101D1F070BB99A12C0B | SHA256:54BF9F4BC4ADCBBA99AEF3C048522C23822D3DDAB51891DCBA3B6F59192A2B28 | |||
| 4060 | dllhost.exe | C:\System Volume Information\SPP\snapshot-2 | binary | |
MD5:6A02491F7EFA9D62FCA2CF93A9970E2A | SHA256:BADD1DC4CF02168E6D531717D775D238BC52C742A06E08CEF47FB4EE489F3E93 | |||
| 5292 | vc_redist.x64.140.exe | C:\Users\admin\AppData\Local\Temp\{e46eca4f-393b-40df-9f49-076faf788d83}\.ba1\1029\license.rtf | text | |
MD5:FD8353F3BC88A47B8880B59A5DAD3F03 | SHA256:2428E8BA8FC9648422333B6B4B92FB476741FC1022DE7CB59D030EC35CC21AC7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
17
DNS requests
5
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6052 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 192.168.100.255:138 | — | — | — | whitelisted |
6052 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |