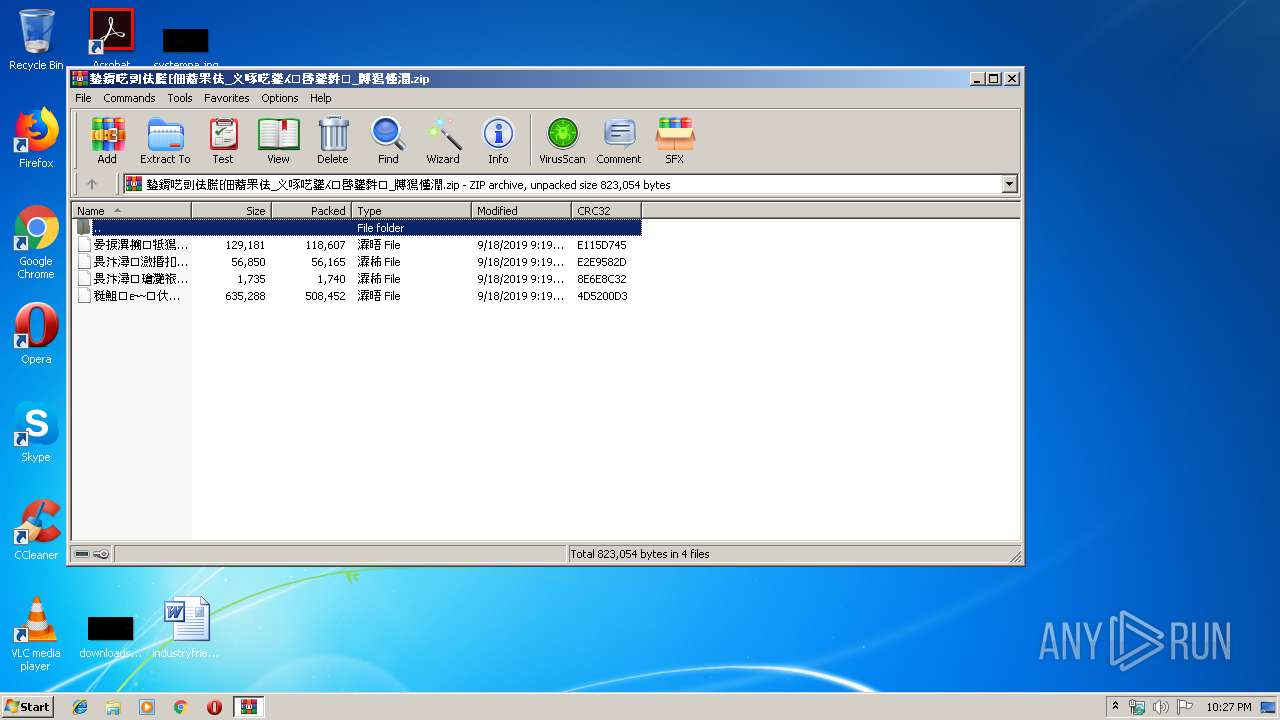
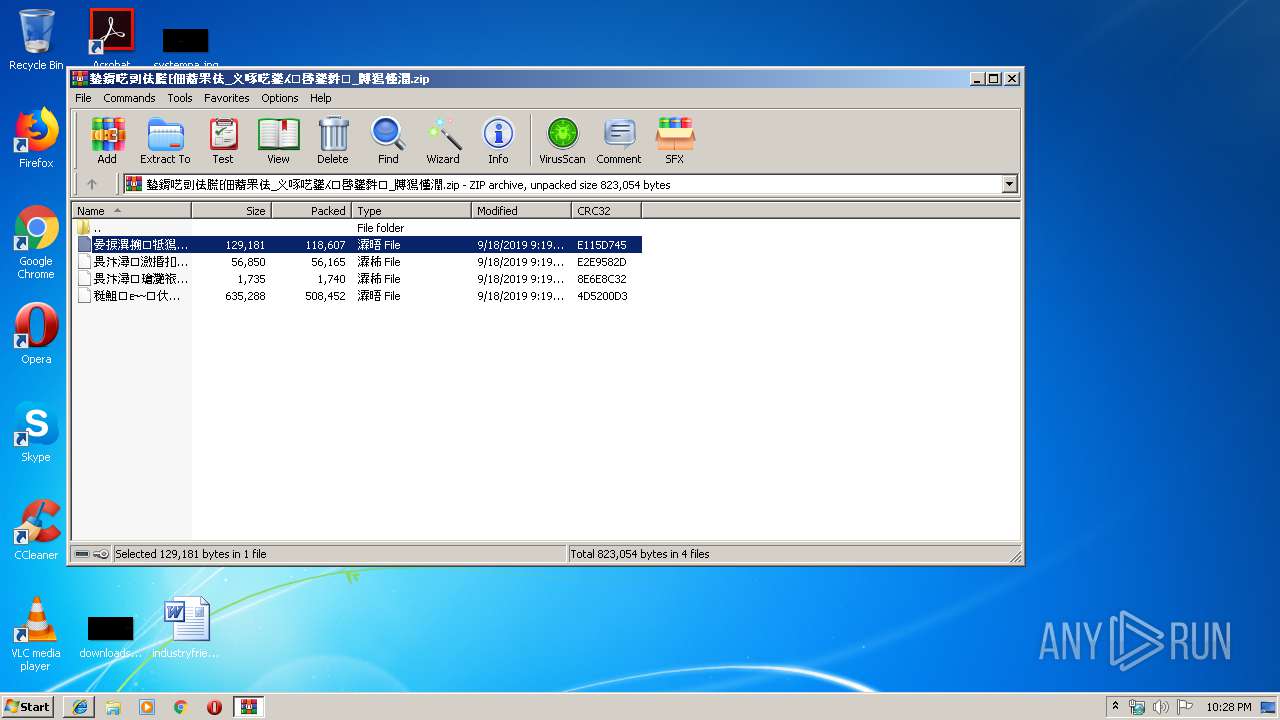
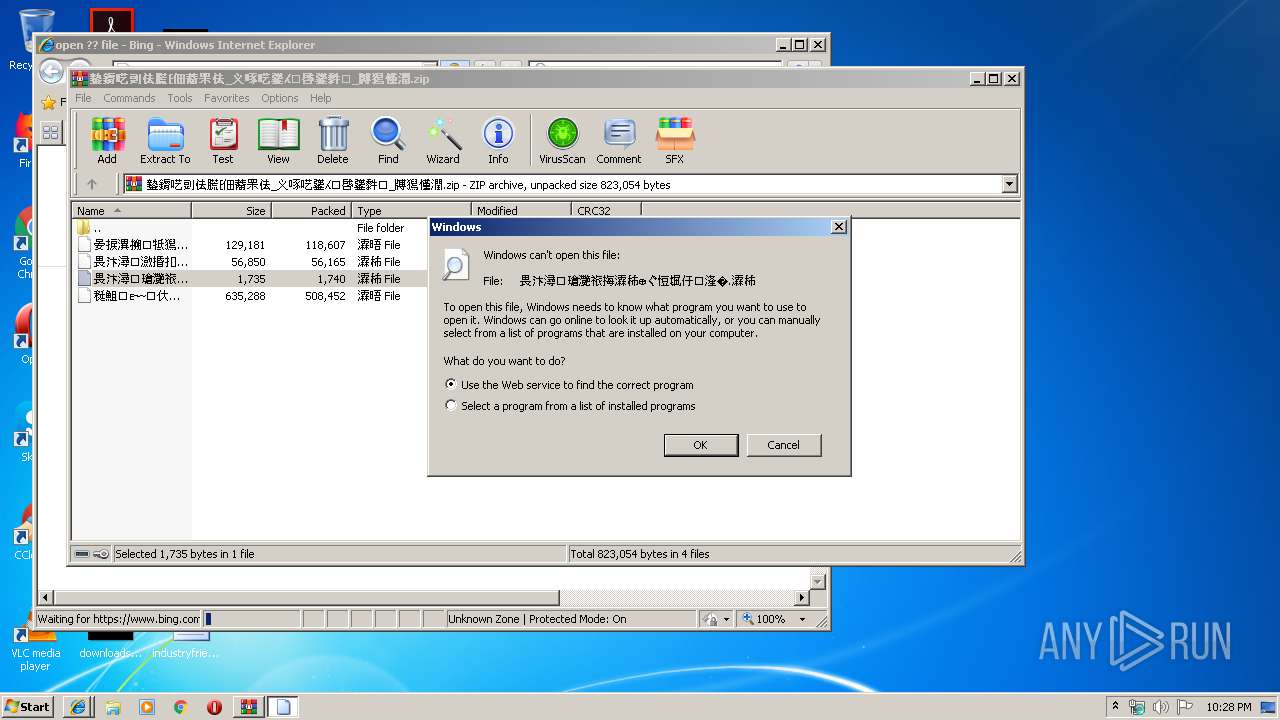
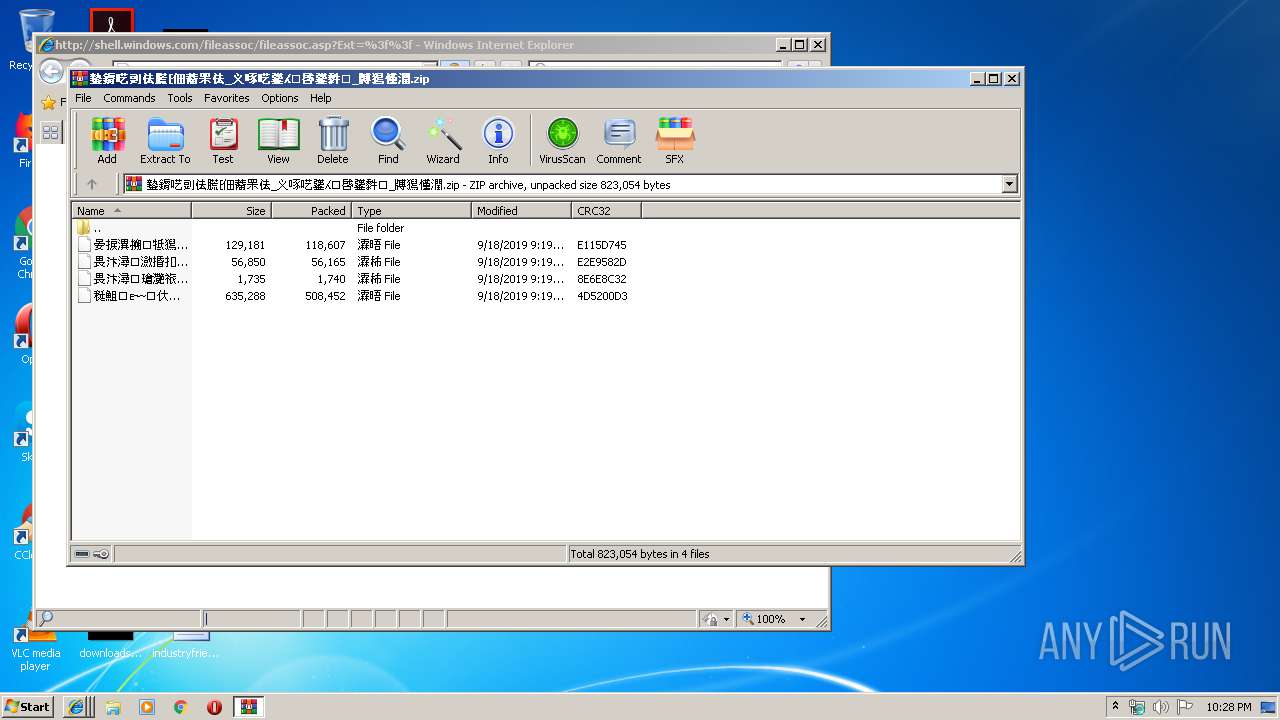
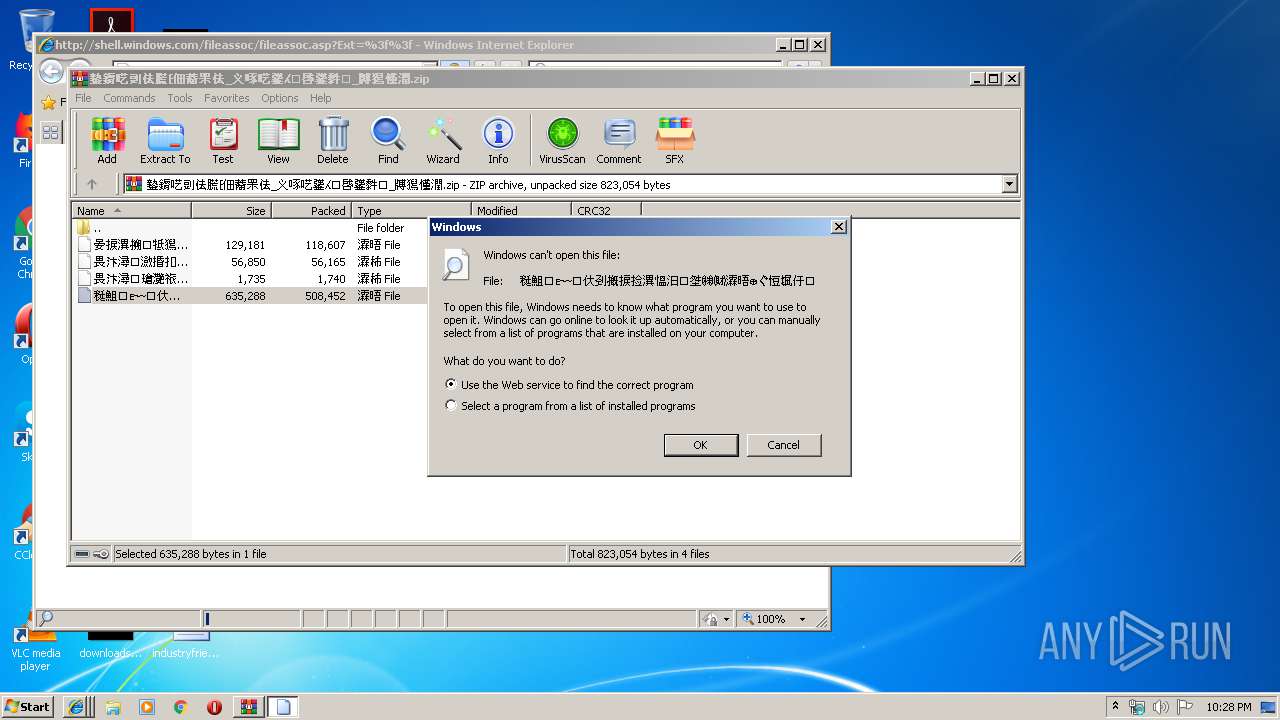
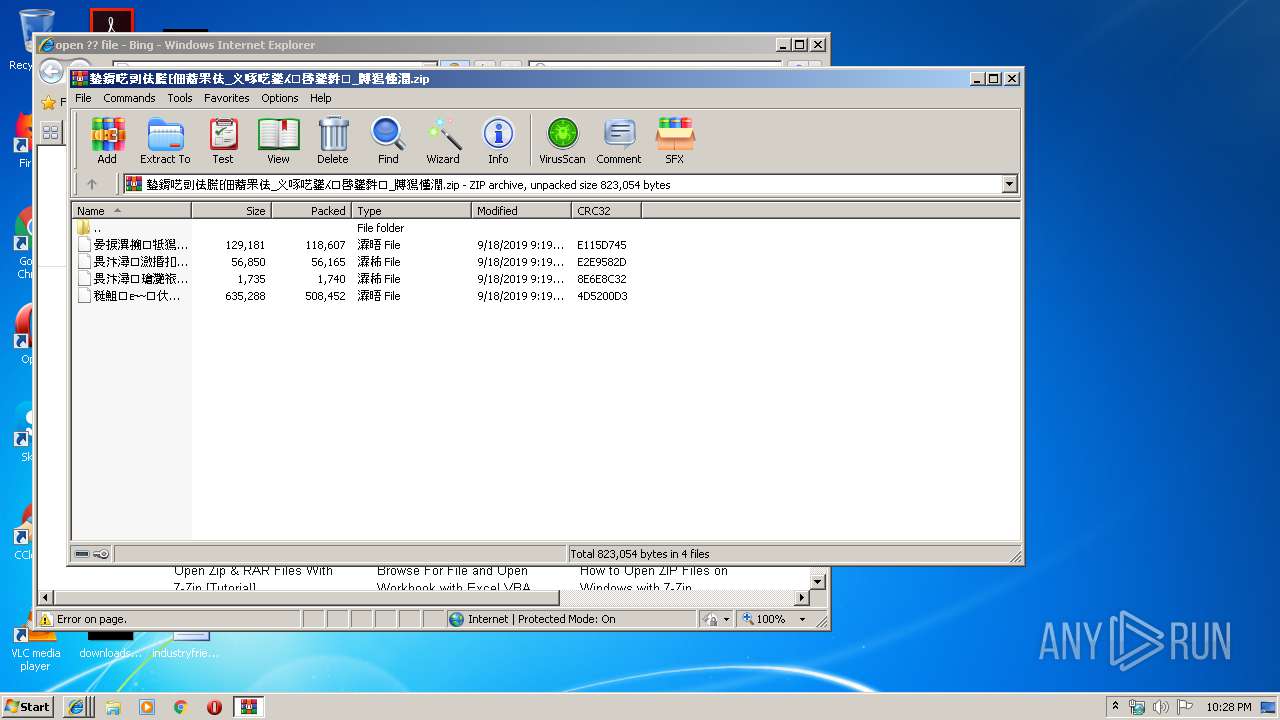
| File name: | 䥍䥎呓剅佉䐠⁅佃䕍䍒佉_义啄呓䥒⁁⁙啔䥒䵓⁏_牔獡慬潤.zip |
| Full analysis: | https://app.any.run/tasks/be0b5660-8034-416b-8b03-794996ed9dd4 |
| Verdict: | Malicious activity |
| Analysis date: | September 18, 2019, 21:27:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 6058E36939D8FEE8FAB67373609D41B9 |
| SHA1: | 229444FAA54F4DE8FF135EB4A1C19BD9D3A3B8BA |
| SHA256: | ACF76FBFCBF0A5405037C710A7E0205D2C5EBBA94CDD378513FF46ED399BCC82 |
| SSDEEP: | 12288:A9zwHtTSH+gRI3NlNF3CQsVGaNOpcQBk8b+UPpslm9Xw7+S6nykhGzABcAoc:A9zItTSH+53NlTjmEpcQBPJPpsl8wCS0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
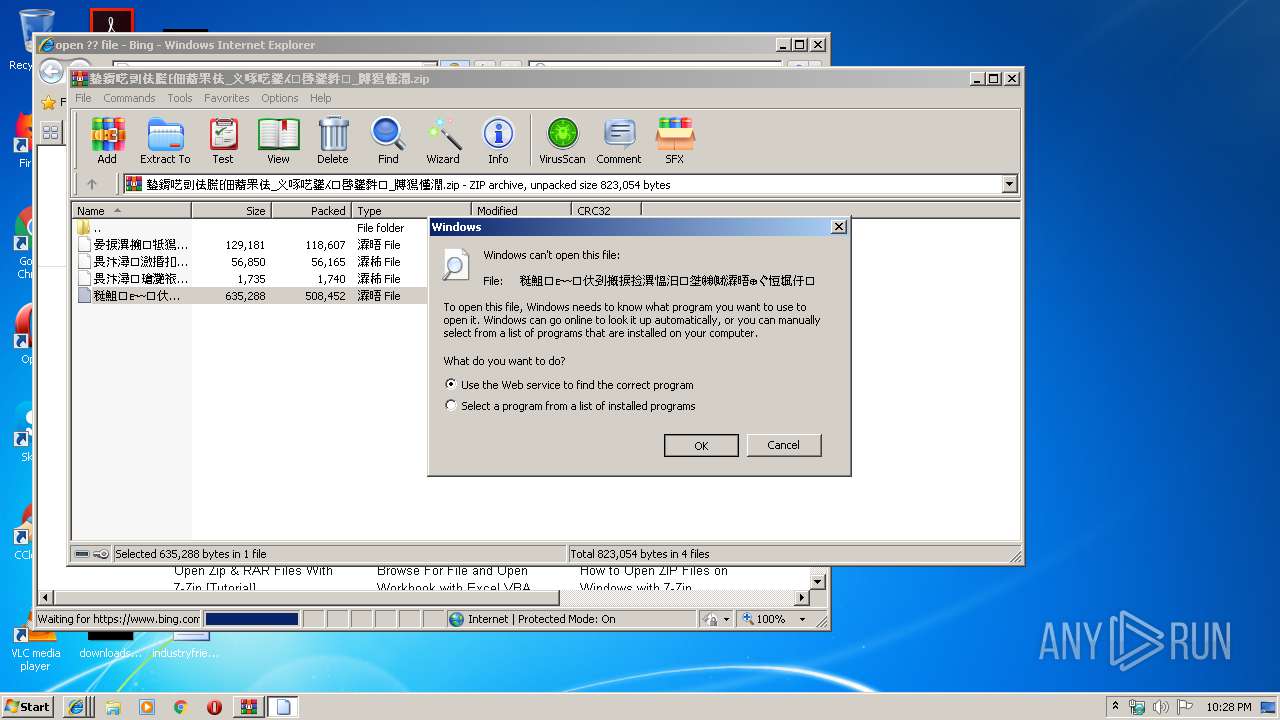
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 2864)
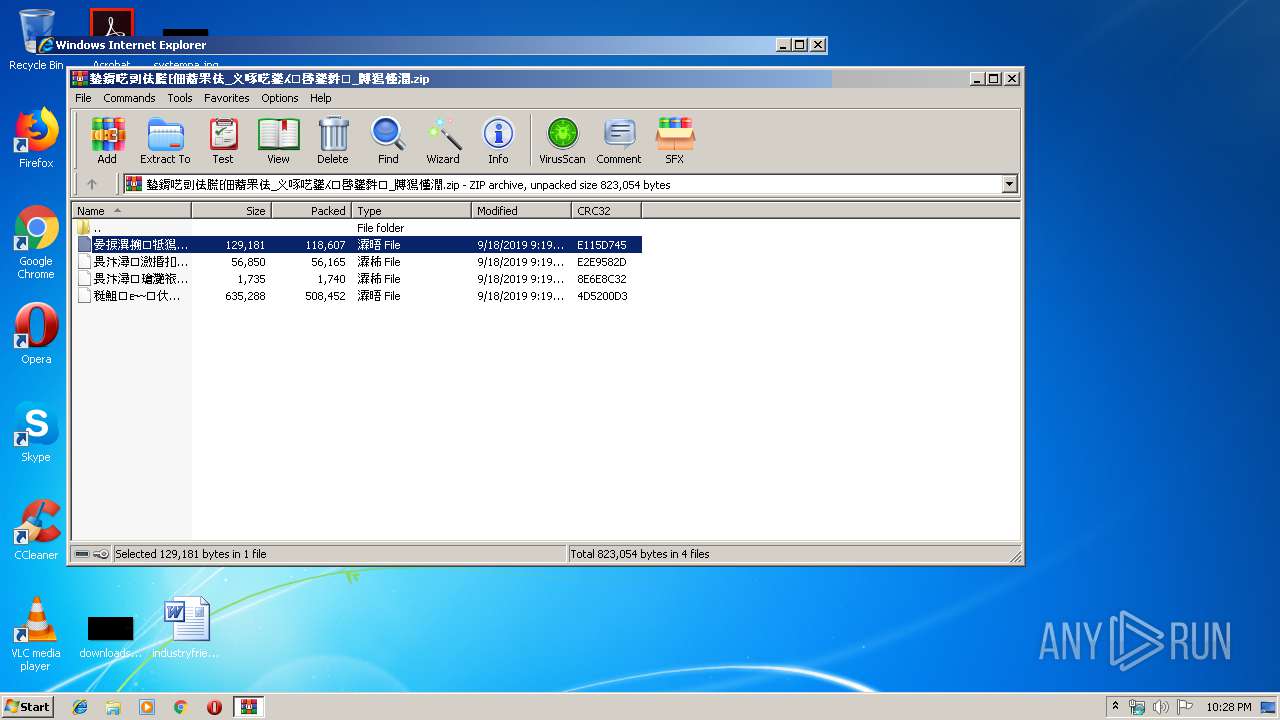
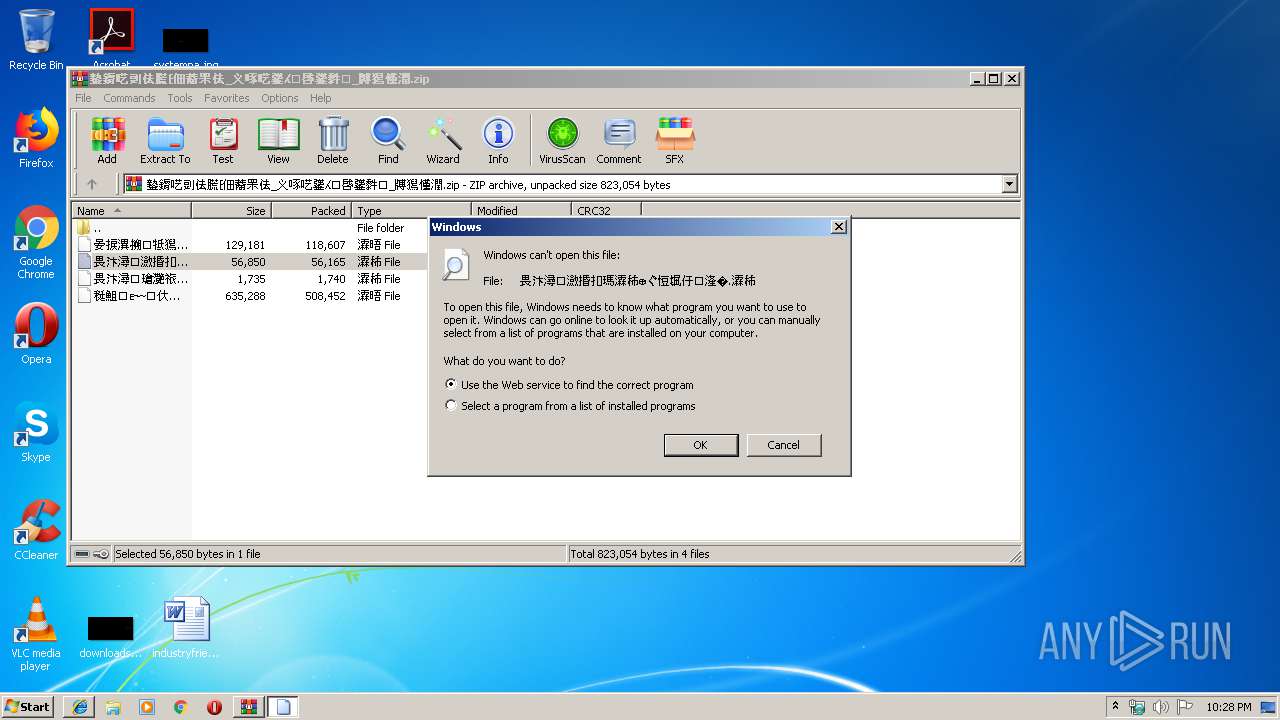
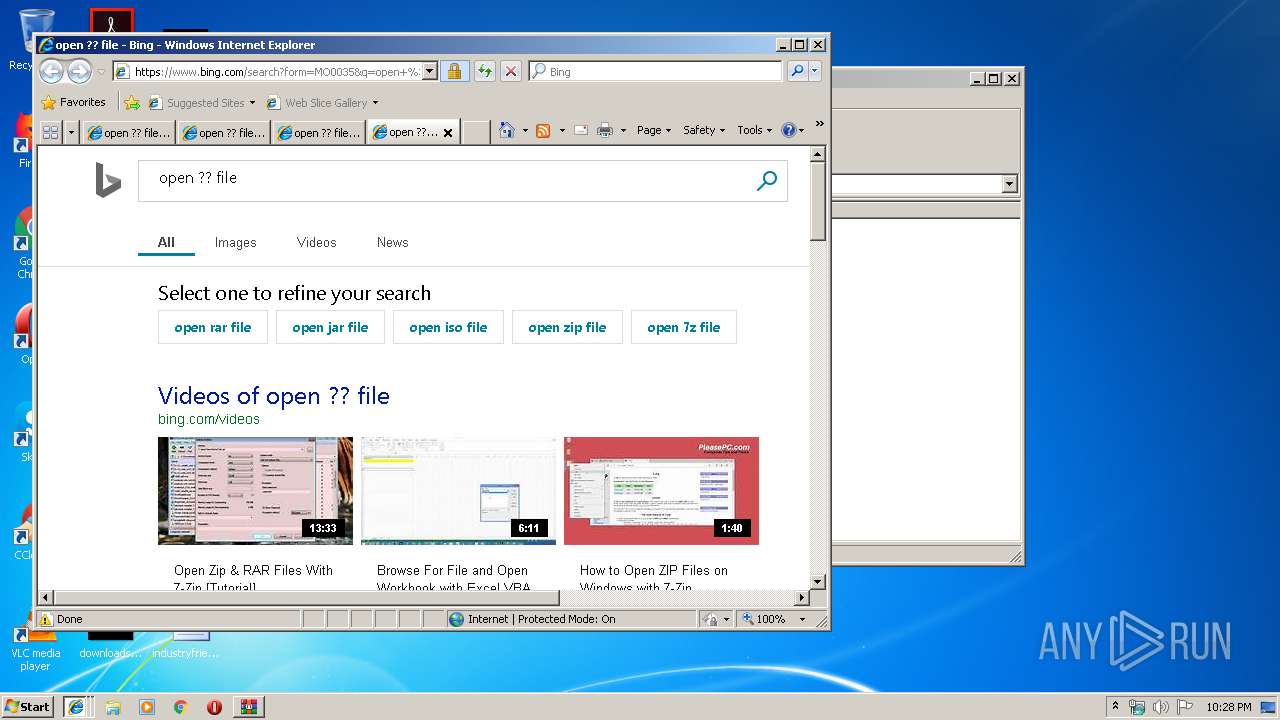
Starts Internet Explorer
- rundll32.exe (PID: 2736)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 3588)
- iexplore.exe (PID: 2136)
Creates files in the user directory
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 3588)
- iexplore.exe (PID: 2136)
Reads internet explorer settings
- iexplore.exe (PID: 2824)
- iexplore.exe (PID: 3588)
- iexplore.exe (PID: 2136)
Changes internet zones settings
- iexplore.exe (PID: 3792)
Reads settings of System Certificates
- iexplore.exe (PID: 3792)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3792)
Application launched itself
- iexplore.exe (PID: 3792)
Changes settings of System certificates
- iexplore.exe (PID: 3792)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
Total processes
40
Monitored processes
9
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2136 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3792 CREDAT:71937 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
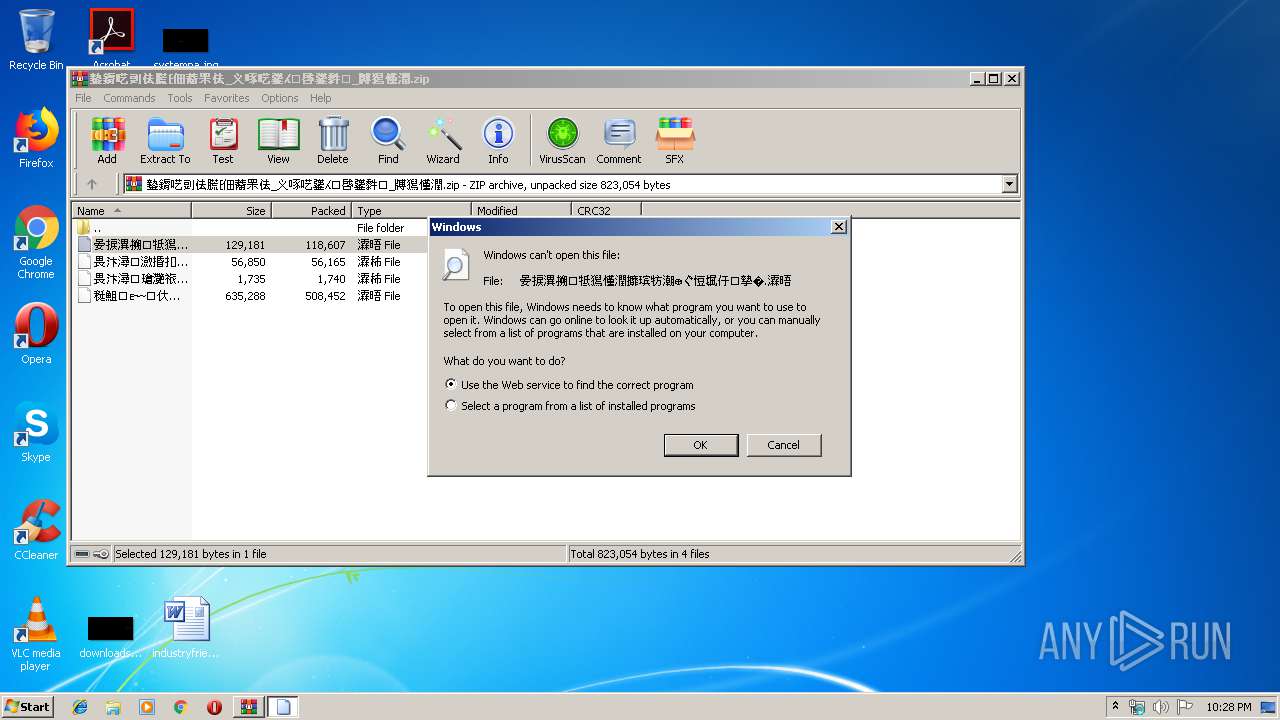
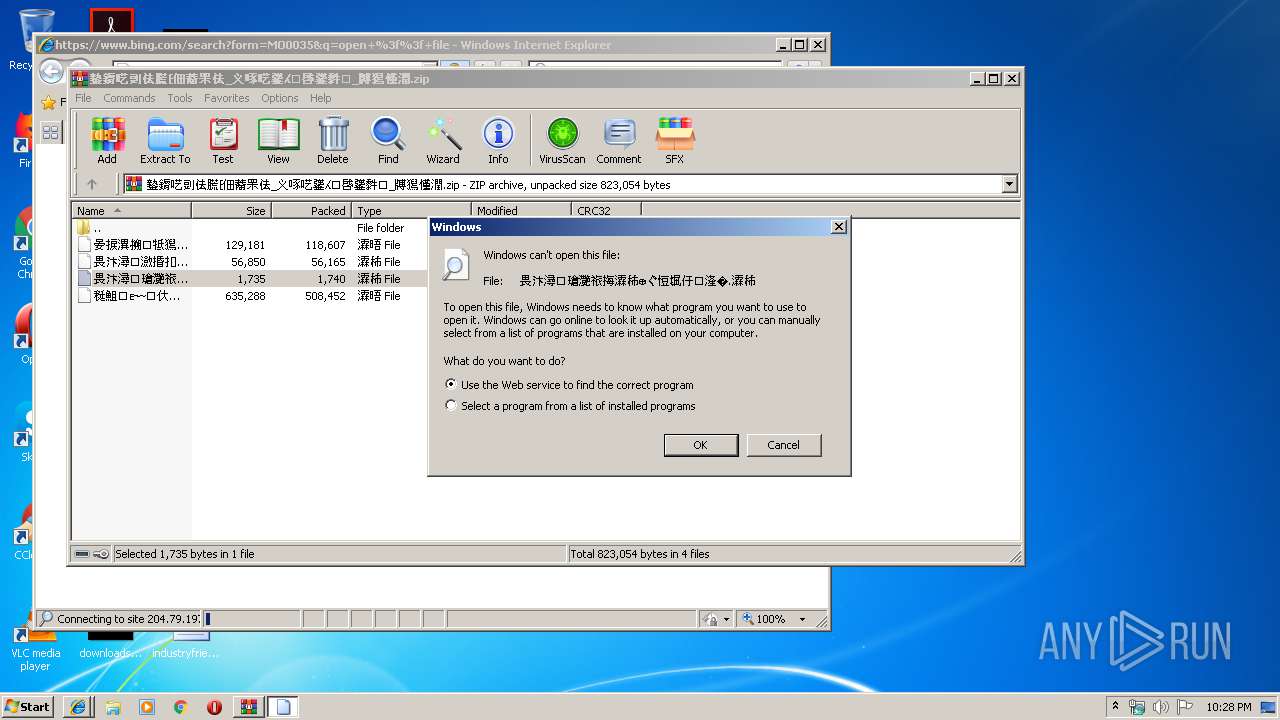
| 2736 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa2864.8437\晏捩潩搠牴獡慬潤攠瑸牥潮ⴲ〲㤱〭㘲㐵⸵摰�.瀮晤 | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2824 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3792 CREDAT:6404 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
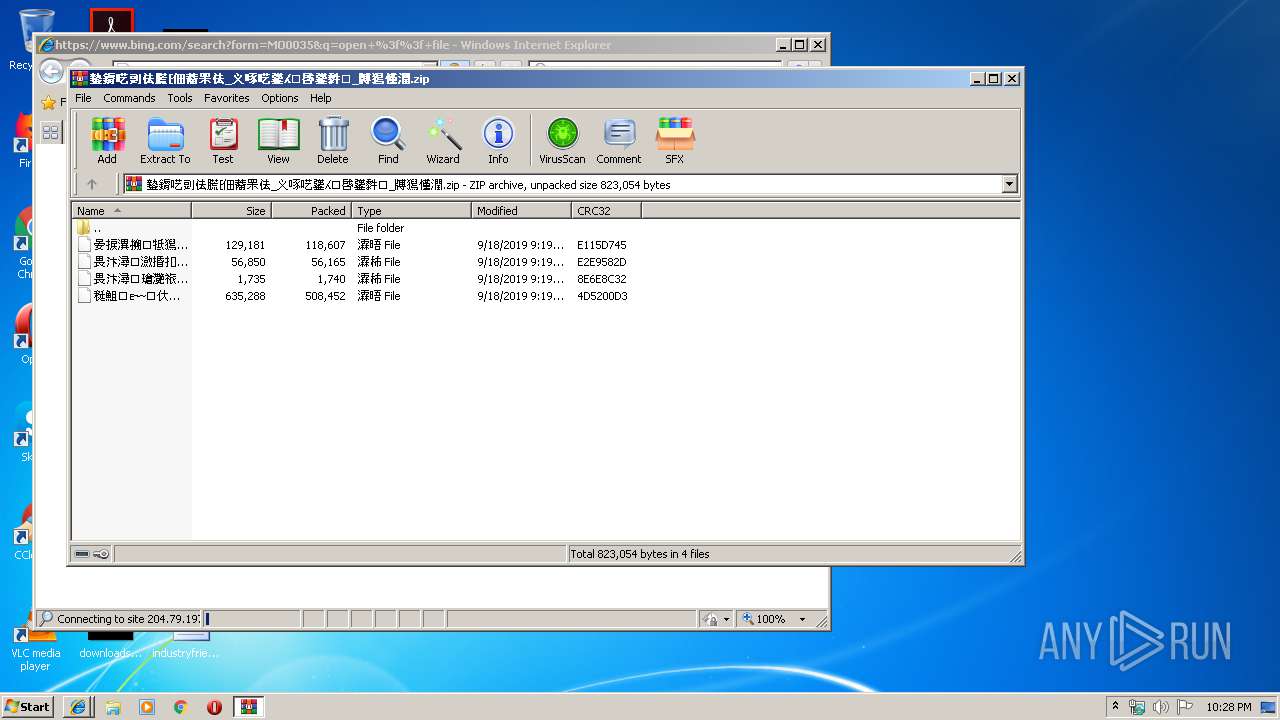
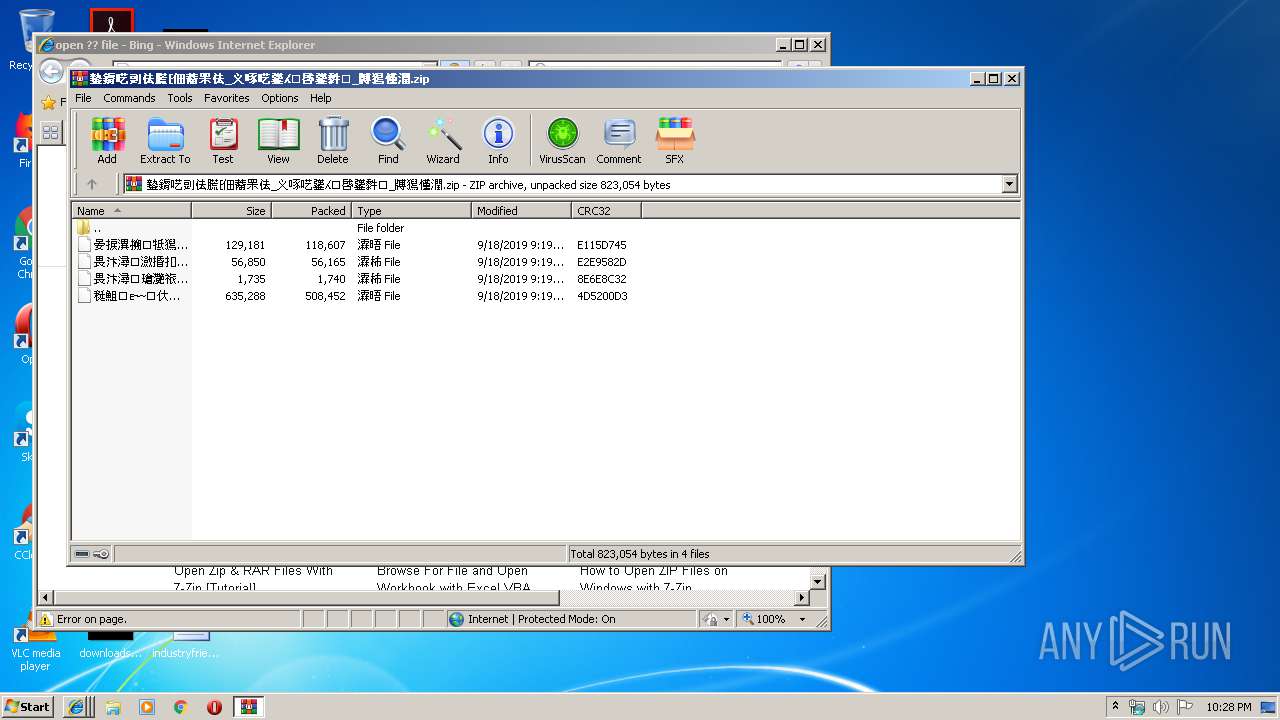
| 2864 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\䥍䥎呓剅佉䐠⁅佃䕍䍒佉_义啄呓䥒⁁⁙啔䥒䵓⁏_牔獡慬潤.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3184 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa2864.10437\䅍䱉ㄭⴹ〰㐲刭摡捩捡潩慍汩ㄭ㘶㈱㈶瀮晤ⴲ〲㤱〭㘲㐵⸵摰�.瀮晤 | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3588 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3792 CREDAT:6407 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3688 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa2864.9386\畏汴潯瀲捪扣瑪瀮杮ⴲ〲㤱〭㘲㐵⸵湰�.瀮杮 | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3792 | "C:\Program Files\Internet Explorer\iexplore.exe" -nohome | C:\Program Files\Internet Explorer\iexplore.exe | rundll32.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3908 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIa2864.9958\畏汴潯瑲灧祣挴瀮杮ⴲ〲㤱〭㘲㐵⸵湰�.瀮杮 | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 306
Read events
1 186
Write events
117
Delete events
3
Modification events
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\䥍䥎呓剅佉䐠⁅佃䕍䍒佉_义啄呓䥒⁁⁙啔䥒䵓⁏_牔獡慬潤.zip | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2864) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3792) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
Executable files
0
Suspicious files
4
Text files
41
Unknown types
7
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3792 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\LH043OAM\favicon[1].ico | — | |
MD5:— | SHA256:— | |||
| 3792 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bing[2].txt | — | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\RS2LHYB8\search[1].txt | — | |
MD5:— | SHA256:— | |||
| 2864 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIa2864.8437\晏捩潩搠牴獡慬潤攠瑸牥潮ⴲ〲㤱〭㘲㐵⸵摰�.瀮晤 | ||
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\History\Low\History.IE5\index.dat | dat | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\RS2LHYB8\search[1].htm | html | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\admin@bing[1].txt | text | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\MSIMGSIZ.DAT | dbf | |
MD5:— | SHA256:— | |||
| 2136 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\index.dat | dat | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
21
DNS requests
6
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
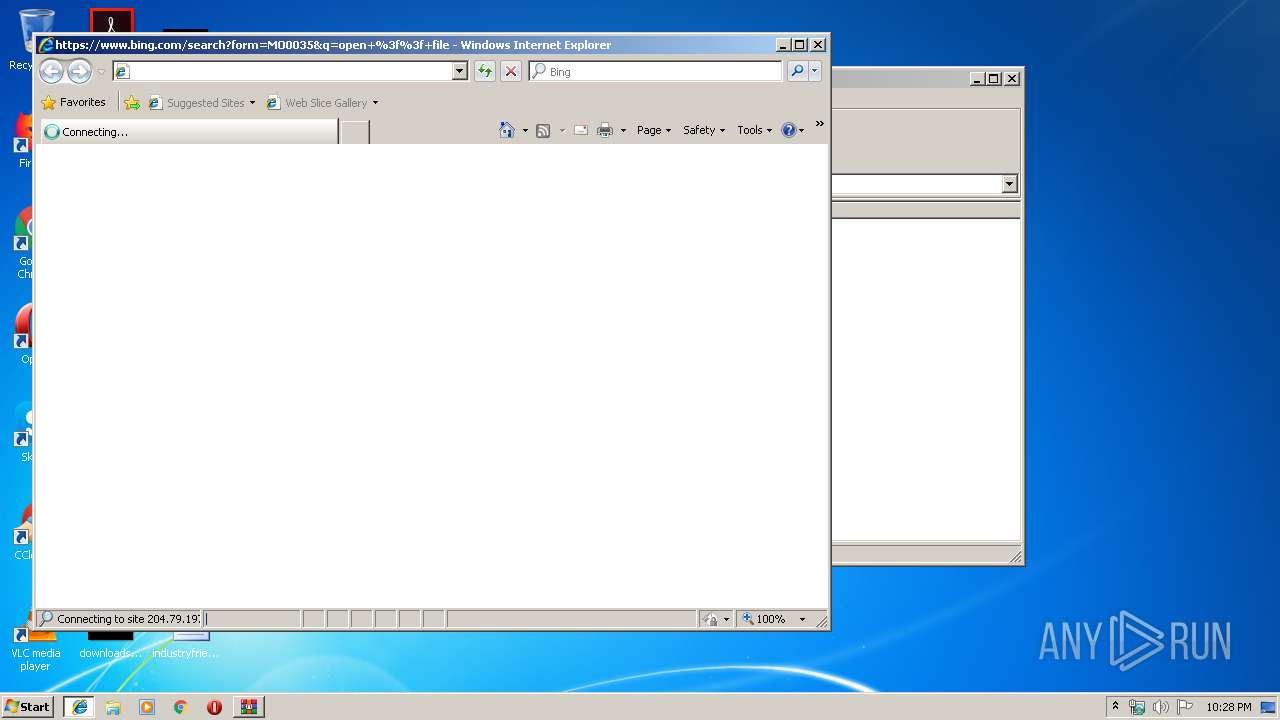
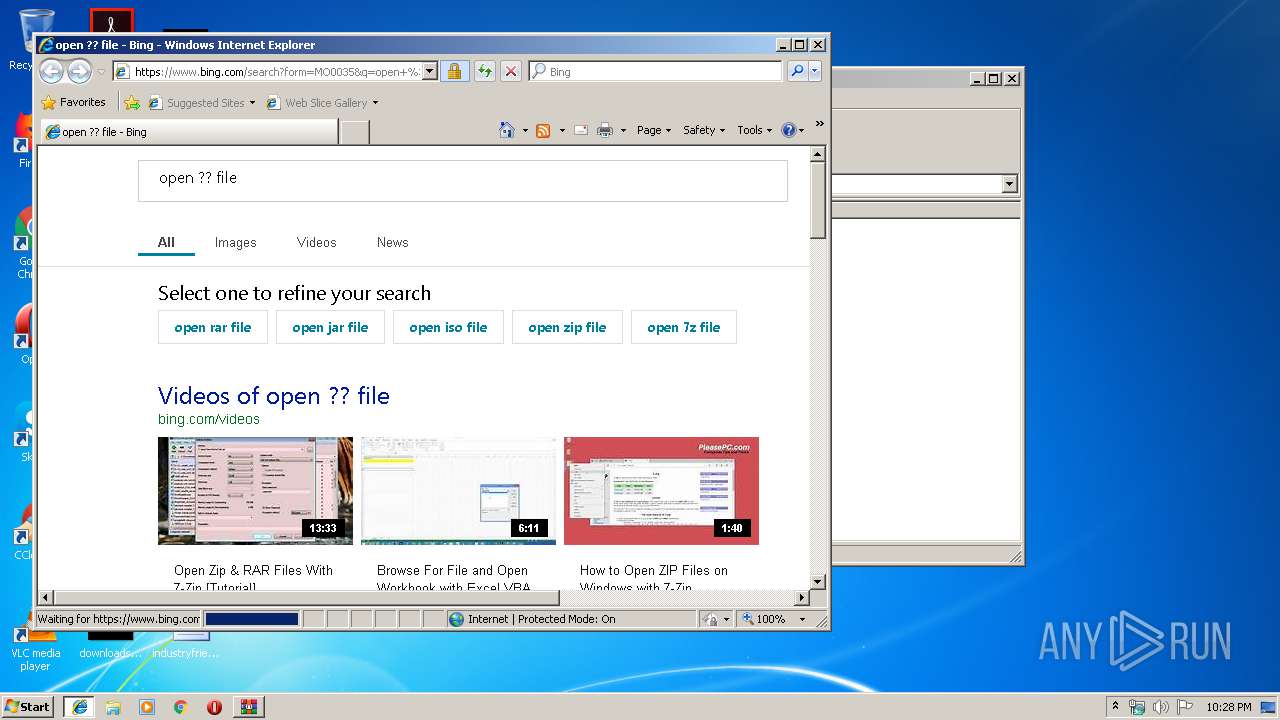
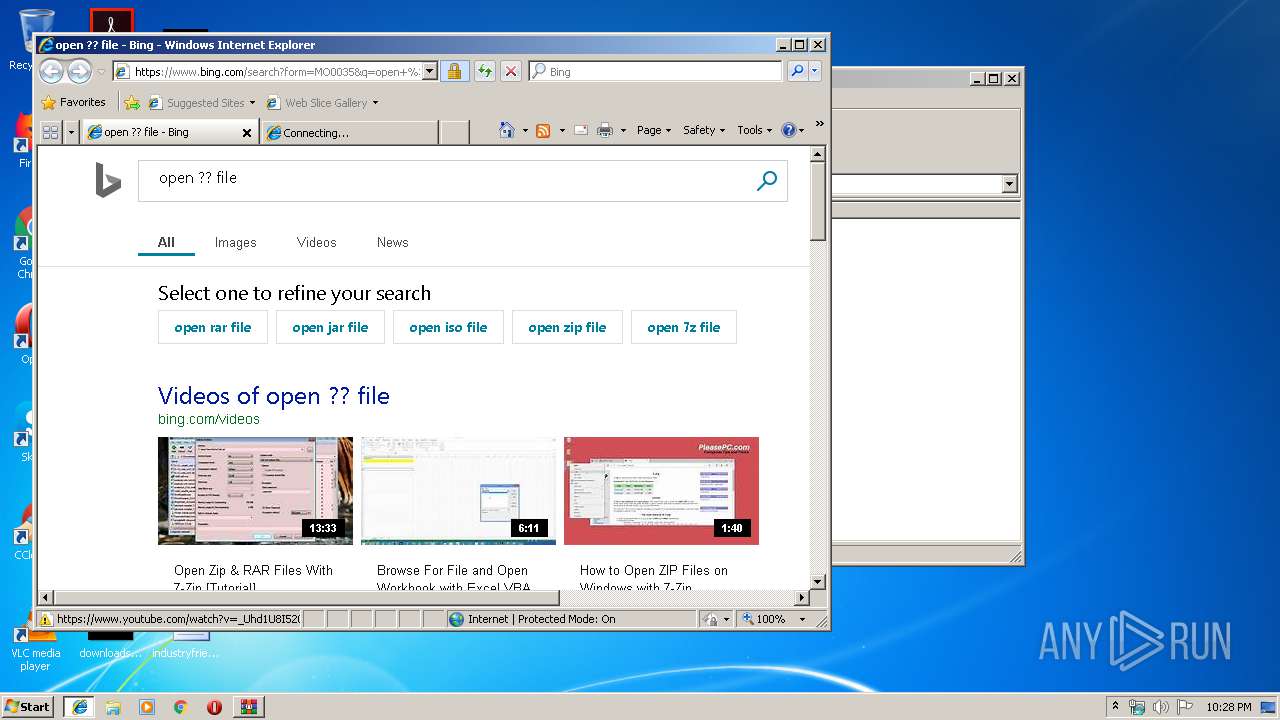
2136 | iexplore.exe | GET | 301 | 2.16.186.27:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=%3f%3f | unknown | — | — | whitelisted |
2824 | iexplore.exe | GET | 302 | 2.19.38.59:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=?? | unknown | — | — | whitelisted |
3588 | iexplore.exe | GET | 302 | 2.19.38.59:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=?? | unknown | — | — | whitelisted |
2824 | iexplore.exe | GET | 301 | 2.16.186.27:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=%3f%3f | unknown | — | — | whitelisted |
2136 | iexplore.exe | GET | 301 | 2.16.186.27:80 | http://shell.windows.com/fileassoc/fileassoc.asp?Ext=%3f%3f | unknown | — | — | whitelisted |
2136 | iexplore.exe | GET | 302 | 2.19.38.59:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=?? | unknown | — | — | whitelisted |
3792 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
2136 | iexplore.exe | GET | 302 | 2.19.38.59:80 | http://go.microsoft.com/fwlink/?LinkId=57426&Ext=?? | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2136 | iexplore.exe | 2.16.186.27:80 | shell.windows.com | Akamai International B.V. | — | whitelisted |
2136 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3792 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
2136 | iexplore.exe | 2.19.38.59:80 | go.microsoft.com | Akamai International B.V. | — | whitelisted |
2824 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
3792 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
2136 | iexplore.exe | 40.90.137.120:443 | login.live.com | Microsoft Corporation | US | unknown |
2824 | iexplore.exe | 2.16.186.27:80 | shell.windows.com | Akamai International B.V. | — | whitelisted |
2824 | iexplore.exe | 2.19.38.59:80 | go.microsoft.com | Akamai International B.V. | — | whitelisted |
3588 | iexplore.exe | 2.16.186.27:80 | shell.windows.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.bing.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
shell.windows.com |
| whitelisted |
login.live.com |
| whitelisted |