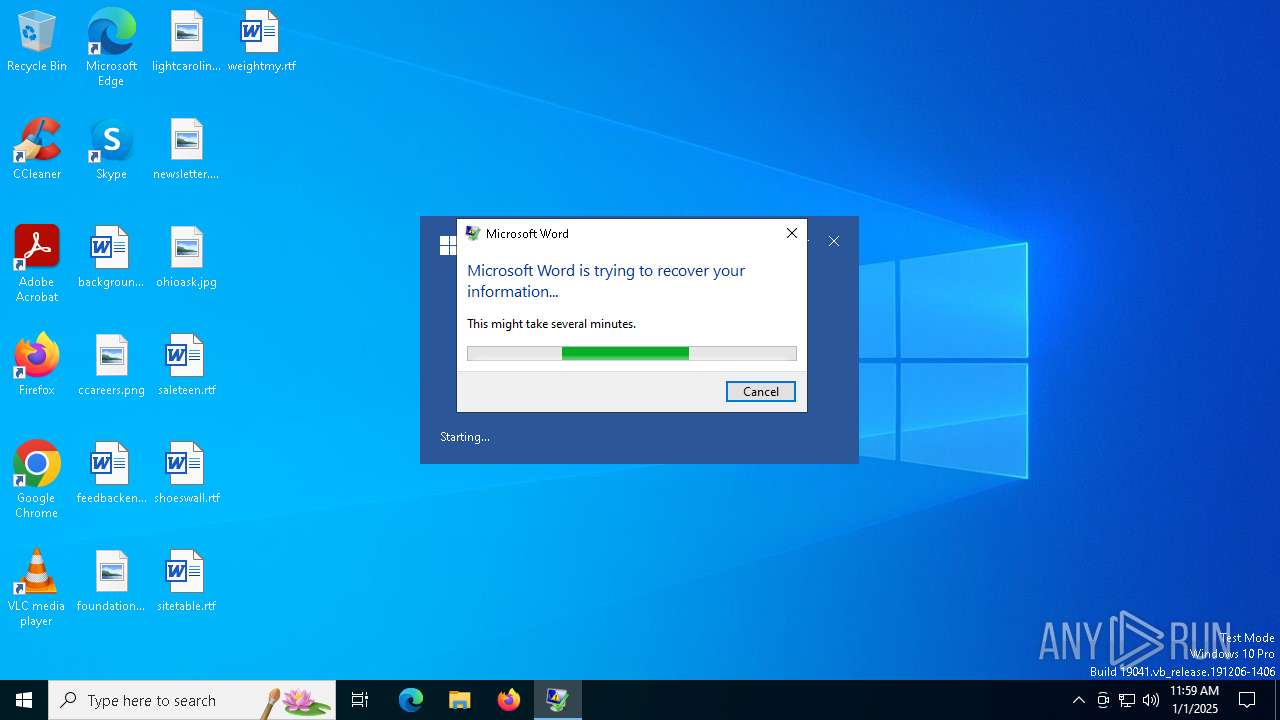
| File name: | POC-CVE-2023-21716.rtf |
| Full analysis: | https://app.any.run/tasks/96ed450b-b642-48fd-918c-f0ade868332e |
| Verdict: | Malicious activity |
| Analysis date: | January 01, 2025, 11:59:19 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | text/rtf |
| File info: | Rich Text Format data, version 1 |
| MD5: | D1E8C1498D56E7DA0E8FC0671B5AB2B5 |
| SHA1: | 8276FACC6EF40DF6385DD3DD49E41848228C7735 |
| SHA256: | ACF196F673746A742CC77AB864E0A81C2AC85200BC33EE27543E7D4C257ECDEA |
| SSDEEP: | 3072:2S3COPNhY0WulaBX+g3iXHfEPsOMf0ReLwtKnMht197h5IbS9MP2BwxPSmqO5G5/:r/Z1Od5IbS9MP2BGfBrDBPZvzjZU1 |
MALICIOUS
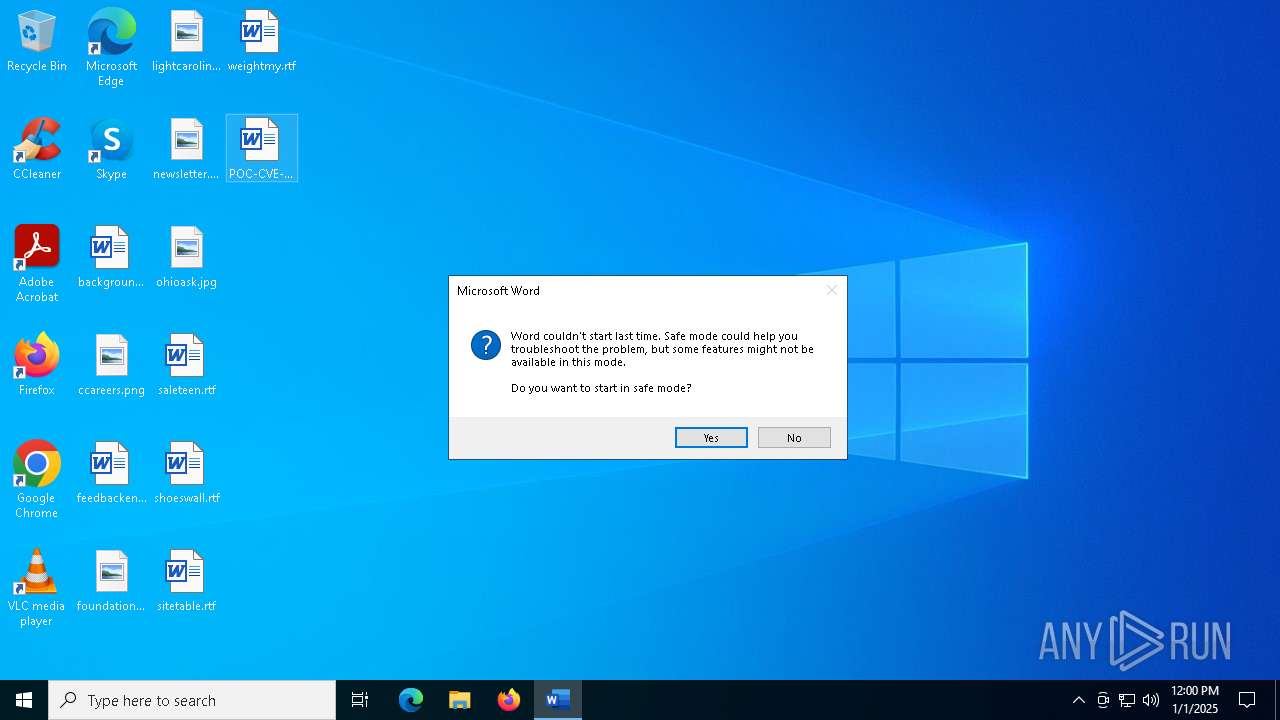
Unusual execution from MS Office
- WINWORD.EXE (PID: 6348)
SUSPICIOUS
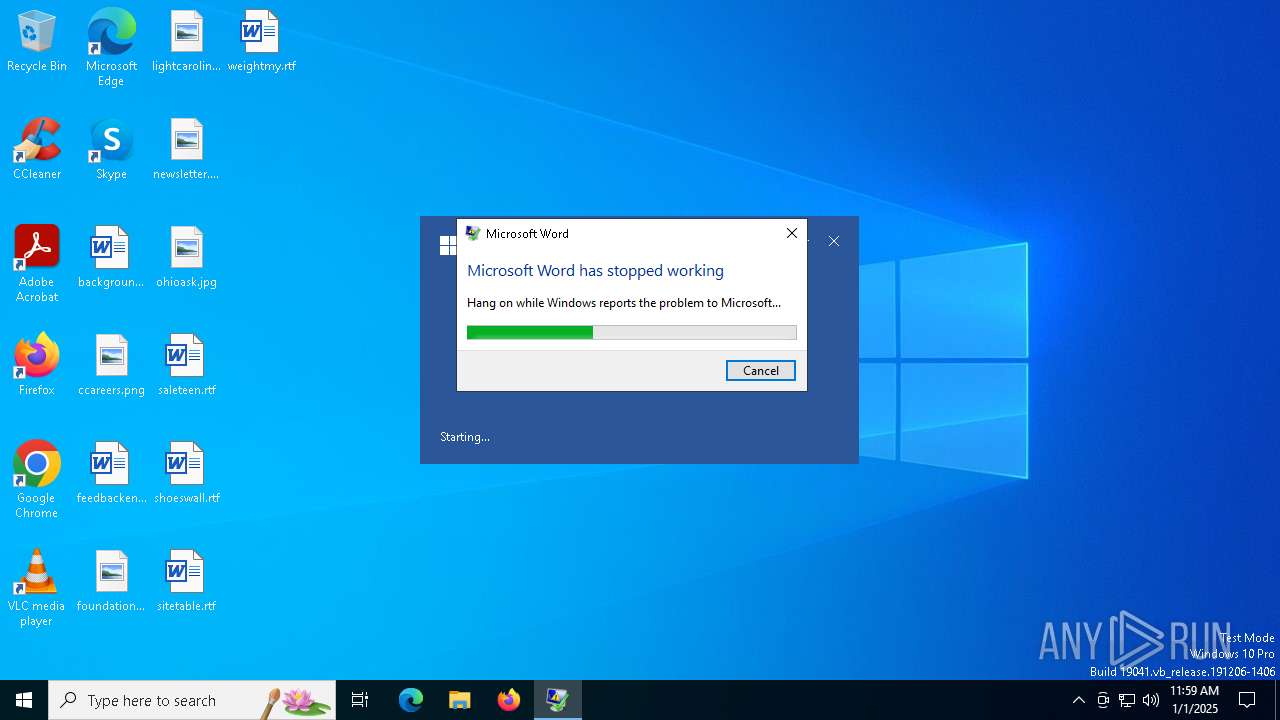
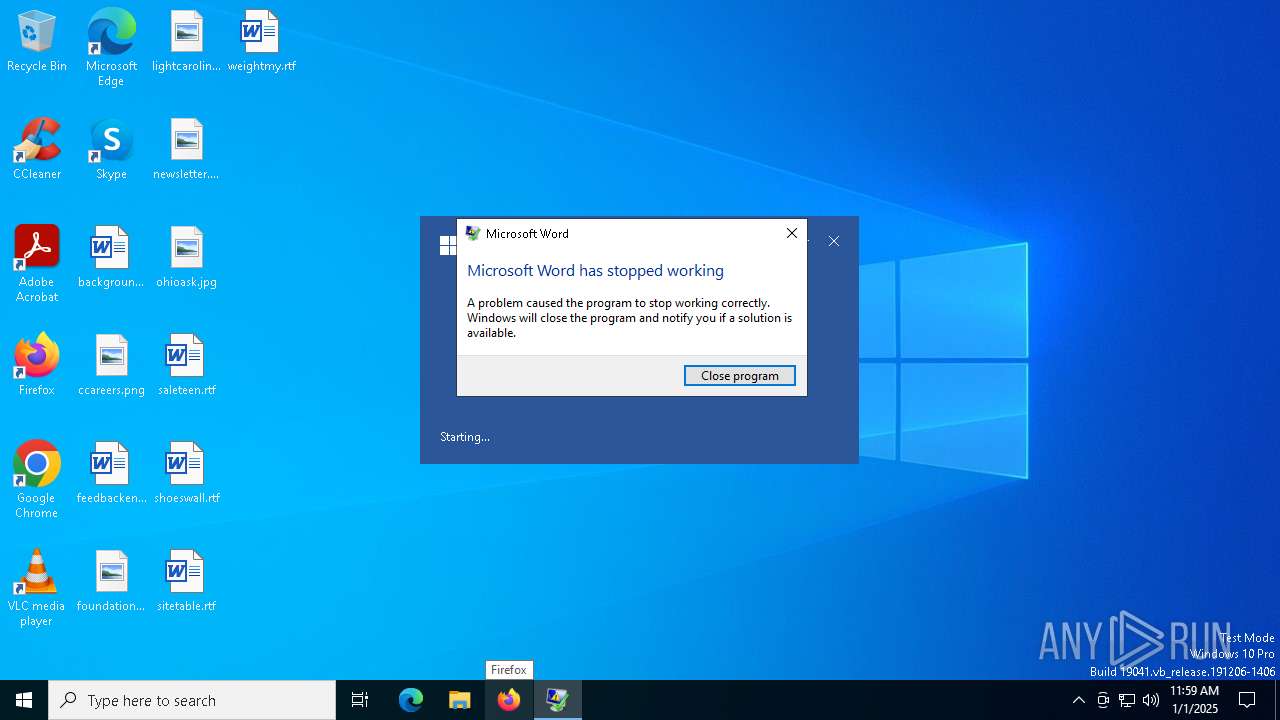
Executes application which crashes
- WINWORD.EXE (PID: 6348)
INFO
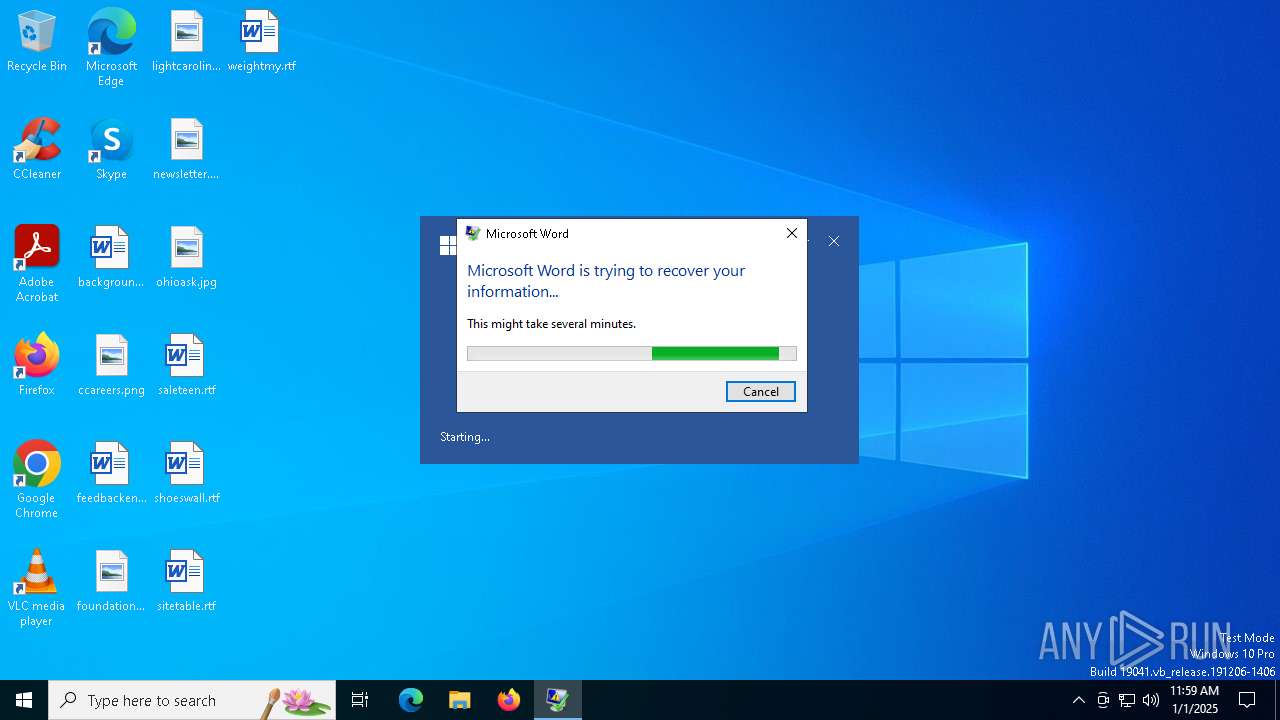
The process uses the downloaded file
- WINWORD.EXE (PID: 6348)
Checks proxy server information
- WerFault.exe (PID: 7032)
Checks supported languages
- SearchApp.exe (PID: 5064)
Creates files or folders in the user directory
- WerFault.exe (PID: 7032)
Reads Microsoft Office registry keys
- WerFault.exe (PID: 7032)
Reads the software policy settings
- WerFault.exe (PID: 7032)
- SearchApp.exe (PID: 5064)
Reads the machine GUID from the registry
- SearchApp.exe (PID: 5064)
Manual execution by a user
- WINWORD.EXE (PID: 6220)
Process checks computer location settings
- SearchApp.exe (PID: 5064)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rtf | | | Rich Text Format (100) |
|---|
Total processes
134
Monitored processes
4
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 5064 | "C:\WINDOWS\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe" -ServerName:CortanaUI.AppX8z9r6jm96hw4bsbneegw0kyxx296wr9t.mca | C:\Windows\SystemApps\Microsoft.Windows.Search_cw5n1h2txyewy\SearchApp.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Search application Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6220 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n "C:\Users\admin\Desktop\POC-CVE-2023-21716.rtf" /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 6348 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\AppData\Local\Temp\POC-CVE-2023-21716.rtf /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 255 Version: 16.0.16026.20146 Modules
| |||||||||||||||
| 7032 | C:\WINDOWS\system32\WerFault.exe -u -p 6348 -s 3444 | C:\Windows\System32\WerFault.exe | WINWORD.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
11 124
Read events
10 842
Write events
270
Delete events
12
Modification events
| (PID) Process: | (6348) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (6348) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\6348 |
| Operation: | write | Name: | 0 |
Value: 0B0E10F3A5AB37CA44734E9C15B406366943B5230046C290C5D8C988D7ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511CC31D2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (6348) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (6348) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (6348) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (6348) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (6348) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (6348) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (6348) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (6348) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
0
Suspicious files
69
Text files
18
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7032 | WerFault.exe | C:\Users\admin\AppData\Local\CrashDumps\WINWORD.EXE.6348.dmp | — | |
MD5:— | SHA256:— | |||
| 7032 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\ReportArchive\AppCrash_WINWORD.EXE_7d193f321d3dfd097d07787288fc64eb44a20f_0c83796a_6d9177f2-2521-49be-ac13-0da91139b7ec\Report.wer | — | |
MD5:— | SHA256:— | |||
| 6348 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\089d66ba04a8cec4bdc5267f42f39cf84278bb67.tbres | binary | |
MD5:5C21630AB2C67A0399BDAB0C9339B5D0 | SHA256:5062F00045899520D39CAE9EDC8C80D5153C9BDD368BDFD39D7F381C2B442CEA | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\AC\Microsoft\Internet Explorer\DOMStore\ZWUI0EBX\www.bing[1].xml | text | |
MD5:99C5928166DE24E6D012178D4B92AC15 | SHA256:DAC3357E969F6EED7EAAB9396661EB7BD5E74B70539A739E9F740D3CCB727822 | |||
| 7032 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER6F57.tmp.dmp | dmp | |
MD5:9884BB9570174D28B2AC76F9FD48009E | SHA256:602D22D0BF9C88B260A6AB28F95A18D4CE0A92B16F78CA26184AF36DA8D55C96 | |||
| 6348 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:7EFA0FCC97E37FB9305F59A277F1DB11 | SHA256:CAA1EAE0658A7206FC4C7C566B27939739CF00540758DFC08E321E7CEC257E70 | |||
| 7032 | WerFault.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\37C951188967C8EB88D99893D9D191FE | der | |
MD5:FA84E4BCC92AA5DB735AB50711040CDE | SHA256:6D7205E794FDE4219A62D9692ECDDF612663A5CF20399E79BE87B851FCA4CA33 | |||
| 5064 | SearchApp.exe | C:\Users\admin\AppData\Local\Packages\Microsoft.Windows.Search_cw5n1h2txyewy\LocalState\ConstraintIndex\Apps_{002807ef-fdd3-40aa-8947-30813f3e75c0}\0.0.filtertrie.intermediate.txt | text | |
MD5:313FB75B427790D01342FE144D9C3C06 | SHA256:50DBBA1A26C02E1C1B831C474708E68C9B11E3FCF6B254AE908A2C3007D88100 | |||
| 7032 | WerFault.exe | C:\ProgramData\Microsoft\Windows\WER\Temp\WER72F2.tmp.WERInternalMetadata.xml | xml | |
MD5:83268E5D1A33B567E8ECBEE86D55D645 | SHA256:04BD774EBA9B718F24B5BA0477916E14AB143E97E8F02222A817E75546DD9561 | |||
| 6348 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\825A1125-C003-4674-8809-DE19D19A0875 | xml | |
MD5:C53748513B59A55008FBA8667D953E8F | SHA256:BAE4A018AF9E0F2C6E0ACF9FD73C4870A5BADDF9CAD0A638E9E60F9DE4F918F9 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
44
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | GET | 200 | 2.16.164.113:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 2.16.164.113:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7032 | WerFault.exe | GET | 200 | 2.16.164.16:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
7032 | WerFault.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5888 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
5064 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5064 | SearchApp.exe | 2.23.209.182:443 | www.bing.com | Akamai International B.V. | GB | whitelisted |
5064 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4712 | MoUsoCoreWorker.exe | 2.16.164.113:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
— | — | 2.16.164.113:80 | crl.microsoft.com | Akamai International B.V. | NL | whitelisted |
4712 | MoUsoCoreWorker.exe | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 88.221.169.152:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
6348 | WINWORD.EXE | 52.109.76.240:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6348 | WINWORD.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
ecs.office.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
watson.events.data.microsoft.com |
| whitelisted |