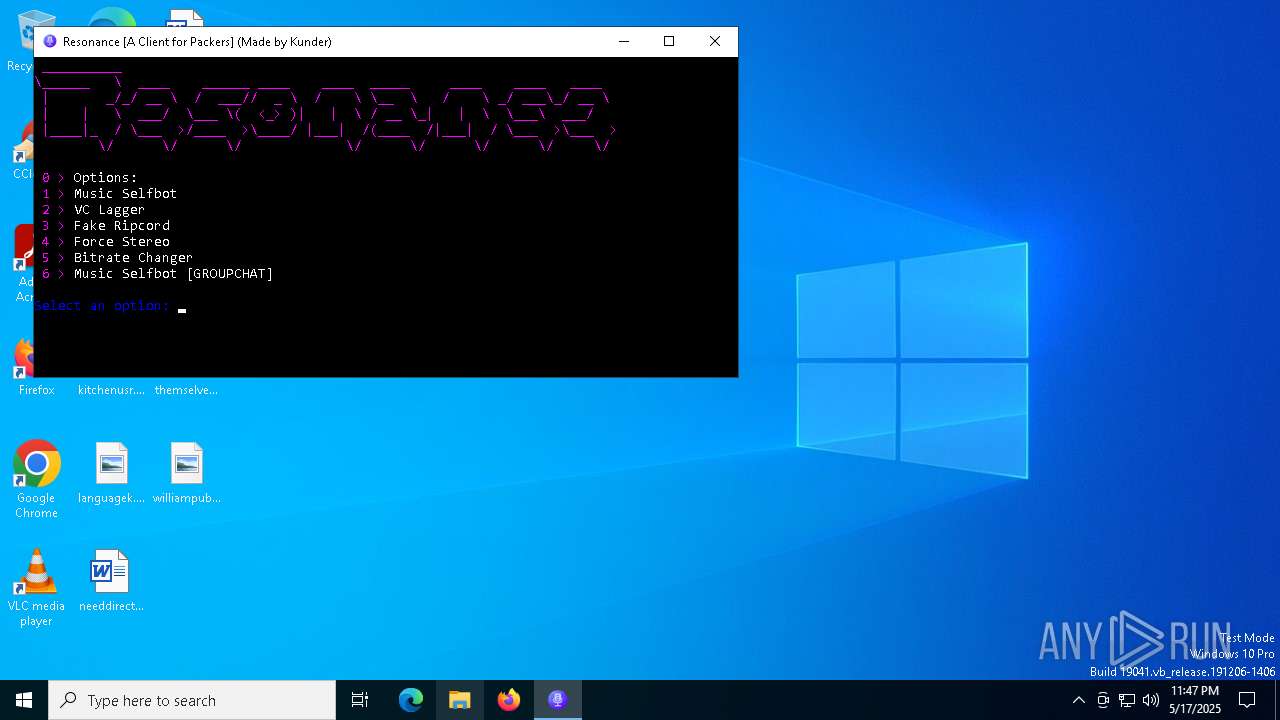
| File name: | Resonance Client.exe |
| Full analysis: | https://app.any.run/tasks/97752aa5-f747-4ddc-989f-b20099d326dc |
| Verdict: | Malicious activity |
| Analysis date: | May 17, 2025, 23:47:25 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32+ executable (console) x86-64, for MS Windows, 7 sections |
| MD5: | A328147B62804AC1F01A974980D7280F |
| SHA1: | 05093037C6F307FAB1E6B05F9F4A70A99E871A09 |
| SHA256: | ACDB076164BBA9EB27ED0DCB5182C093C6D5232CFDFC270749B9C16EABEC512B |
| SSDEEP: | 98304:daoEfy0Hc2pjRu8M+YzMM0SxYVbkrPWjxA9zv1nxeq57NoRGvHbwBGRDhy7lFiRB:hhX1NgKLGZgA |
MALICIOUS
No malicious indicators.SUSPICIOUS
Process drops legitimate windows executable
- Resonance Client.exe (PID: 7216)
Executable content was dropped or overwritten
- Resonance Client.exe (PID: 7216)
Application launched itself
- Resonance Client.exe (PID: 7216)
The process drops C-runtime libraries
- Resonance Client.exe (PID: 7216)
Loads Python modules
- Resonance Client.exe (PID: 7308)
Process drops python dynamic module
- Resonance Client.exe (PID: 7216)
Starts CMD.EXE for commands execution
- Resonance Client.exe (PID: 7308)
INFO
The sample compiled with english language support
- Resonance Client.exe (PID: 7216)
Checks supported languages
- Resonance Client.exe (PID: 7216)
- Resonance Client.exe (PID: 7308)
- mode.com (PID: 7480)
Create files in a temporary directory
- Resonance Client.exe (PID: 7216)
Reads the computer name
- Resonance Client.exe (PID: 7216)
- Resonance Client.exe (PID: 7308)
Checks operating system version
- Resonance Client.exe (PID: 7308)
Starts MODE.COM to configure console settings
- mode.com (PID: 7480)
Reads the machine GUID from the registry
- Resonance Client.exe (PID: 7308)
PyInstaller has been detected (YARA)
- Resonance Client.exe (PID: 7216)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (87.3) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (6.3) |
| .exe | | | DOS Executable Generic (6.3) |
EXIF
EXE
| MachineType: | AMD AMD64 |
|---|---|
| TimeStamp: | 2023:03:17 23:23:25+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware |
| PEType: | PE32+ |
| LinkerVersion: | 14.33 |
| CodeSize: | 165888 |
| InitializedDataSize: | 148480 |
| UninitializedDataSize: | - |
| EntryPoint: | 0xa360 |
| OSVersion: | 5.2 |
| ImageVersion: | - |
| SubsystemVersion: | 5.2 |
| Subsystem: | Windows command line |
Total processes
134
Monitored processes
9
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 7216 | "C:\Users\admin\AppData\Local\Temp\Resonance Client.exe" | C:\Users\admin\AppData\Local\Temp\Resonance Client.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 7224 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | Resonance Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7308 | "C:\Users\admin\AppData\Local\Temp\Resonance Client.exe" | C:\Users\admin\AppData\Local\Temp\Resonance Client.exe | Resonance Client.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 1 Modules
| |||||||||||||||
| 7328 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7360 | "C:\WINDOWS\System32\SLUI.exe" RuleId=3482d82e-ca2c-4e1f-8864-da0267b484b2;Action=AutoActivate;AppId=55c92734-d682-4d71-983e-d6ec3f16059f;SkuId=4de7cb65-cdf1-4de9-8ae8-e3cce27b9f2c;NotificationInterval=1440;Trigger=TimerEvent | C:\Windows\System32\slui.exe | SppExtComObj.Exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7408 | C:\WINDOWS\system32\cmd.exe /c "ver" | C:\Windows\System32\cmd.exe | — | Resonance Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7428 | C:\WINDOWS\system32\cmd.exe /c title Resonance [A Client for Packers] (Made by Kunder) | C:\Windows\System32\cmd.exe | — | Resonance Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7452 | C:\WINDOWS\system32\cmd.exe /c mode 88,20 | C:\Windows\System32\cmd.exe | — | Resonance Client.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7480 | mode 88,20 | C:\Windows\System32\mode.com | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: DOS Device MODE Utility Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
3 688
Read events
3 688
Write events
0
Delete events
0
Modification events
Executable files
28
Suspicious files
1
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7216 | Resonance Client.exe | C:\Users\admin\AppData\Local\Temp\_MEI72162\VCRUNTIME140.dll | executable | |
MD5:F34EB034AA4A9735218686590CBA2E8B | SHA256:9D2B40F0395CC5D1B4D5EA17B84970C29971D448C37104676DB577586D4AD1B1 | |||
| 7216 | Resonance Client.exe | C:\Users\admin\AppData\Local\Temp\_MEI72162\MSVCP140.dll | executable | |
MD5:0929E46B1020B372956F204F85E48ED6 | SHA256:CB3C74D6FCC091F4EB7C67EE5EB5F76C1C973DEA8B1C6B851FCCA62C2A9D8AA8 | |||
| 7216 | Resonance Client.exe | C:\Users\admin\AppData\Local\Temp\_MEI72162\VCRUNTIME140_1.dll | executable | |
MD5:135359D350F72AD4BF716B764D39E749 | SHA256:34048ABAA070ECC13B318CEA31425F4CA3EDD133D350318AC65259E6058C8B32 | |||
| 7216 | Resonance Client.exe | C:\Users\admin\AppData\Local\Temp\_MEI72162\_brotli.cp310-win_amd64.pyd | executable | |
MD5:6D44FD95C62C6415999EBC01AF40574B | SHA256:58BACB135729A70102356C2D110651F1735BF40A602858941E13BDEABFACAB4A | |||
| 7216 | Resonance Client.exe | C:\Users\admin\AppData\Local\Temp\_MEI72162\_hashlib.pyd | executable | |
MD5:7A74284813386818ADA7BF55C8D8ACF9 | SHA256:21A1819013DE423BB3B9B682D0B3506C6EF57EE88C61EDF4BA12D8D5F589C9C2 | |||
| 7216 | Resonance Client.exe | C:\Users\admin\AppData\Local\Temp\_MEI72162\_bz2.pyd | executable | |
MD5:56203038756826A0A683D5750EE04093 | SHA256:31C2F21ADF27CA77FA746C0FDA9C7D7734587AB123B95F2310725AAF4BF4FF3C | |||
| 7216 | Resonance Client.exe | C:\Users\admin\AppData\Local\Temp\_MEI72162\_decimal.pyd | executable | |
MD5:709613D7D7BC30ABDAEE015C331664B6 | SHA256:8600CAE4F34CC64C406198E19539D0D4F5A574FC60B32B8AA8F32FD64C981DA5 | |||
| 7216 | Resonance Client.exe | C:\Users\admin\AppData\Local\Temp\_MEI72162\_lzma.pyd | executable | |
MD5:14EA9D8BA0C2379FB1A9F6F3E9BBD63B | SHA256:C414A5A418C41A7A8316687047ED816CAD576741BD09A268928E381A03E1EB39 | |||
| 7216 | Resonance Client.exe | C:\Users\admin\AppData\Local\Temp\_MEI72162\_asyncio.pyd | executable | |
MD5:686262283BA69CCE7F3EABA7CDEB0372 | SHA256:02EC5CD22543C0CA298C598B7E13949A4E8247CEC288D0BCA0A1269059B548EF | |||
| 7216 | Resonance Client.exe | C:\Users\admin\AppData\Local\Temp\_MEI72162\libssl-1_1.dll | executable | |
MD5:86F2D9CC8CC54BBB005B15CABF715E5D | SHA256:D98DD943517963FD0E790FDE00965822AA4E4A48E8A479AFAD74ABF14A300771 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
22
DNS requests
15
Threats
4
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7872 | SIHClient.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
— | — | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3216 | svchost.exe | 172.211.123.249:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.160.131:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
6544 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
discord.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Misc activity | ET INFO Observed Discord Domain in DNS Lookup (discord .com) |
7308 | Resonance Client.exe | Misc activity | ET INFO Observed Discord Domain (discord .com in TLS SNI) |
2196 | svchost.exe | Misc activity | ET INFO Discord Chat Service Domain in DNS Lookup (discord .com) |
7308 | Resonance Client.exe | Misc activity | ET INFO Observed Discord Service Domain (discord .com) in TLS SNI |