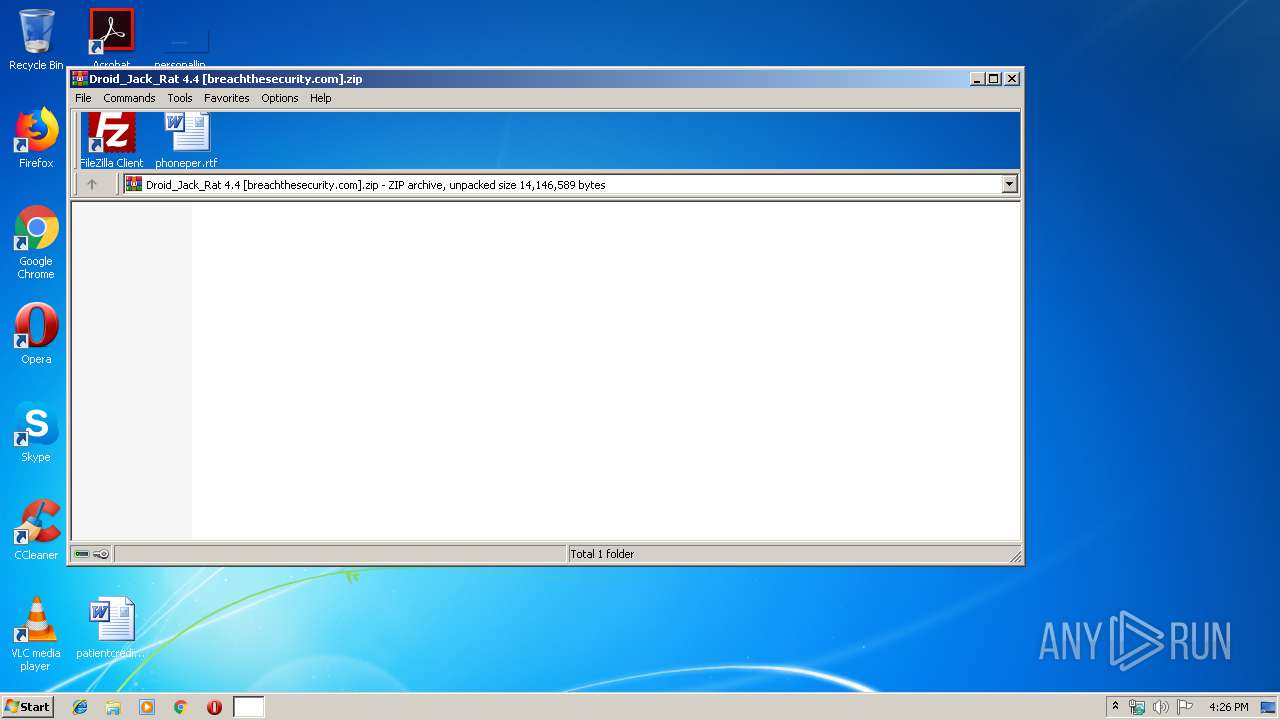
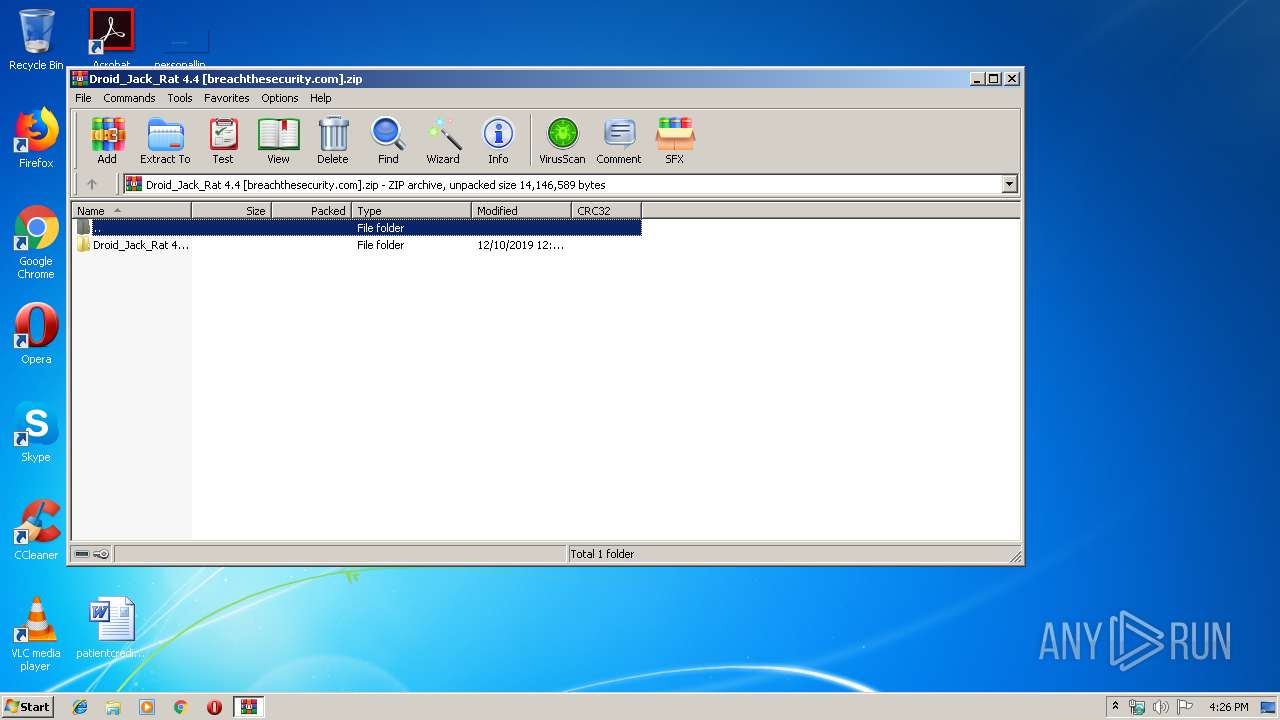
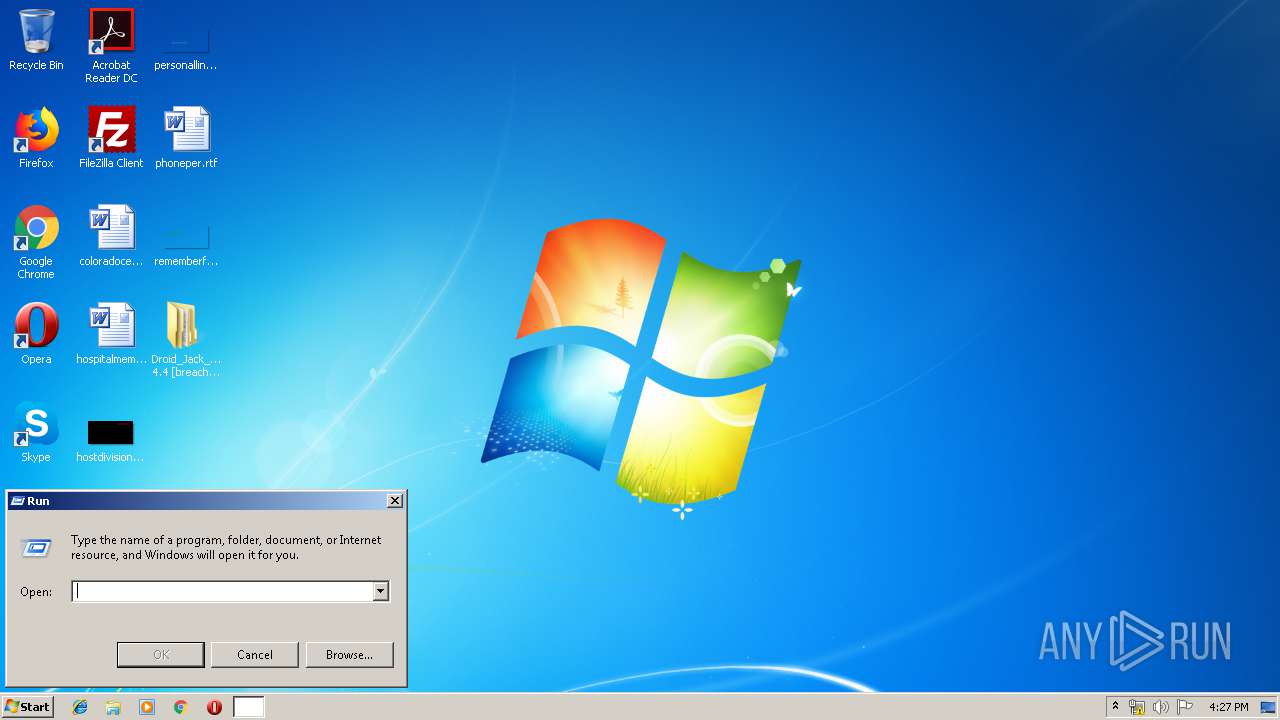
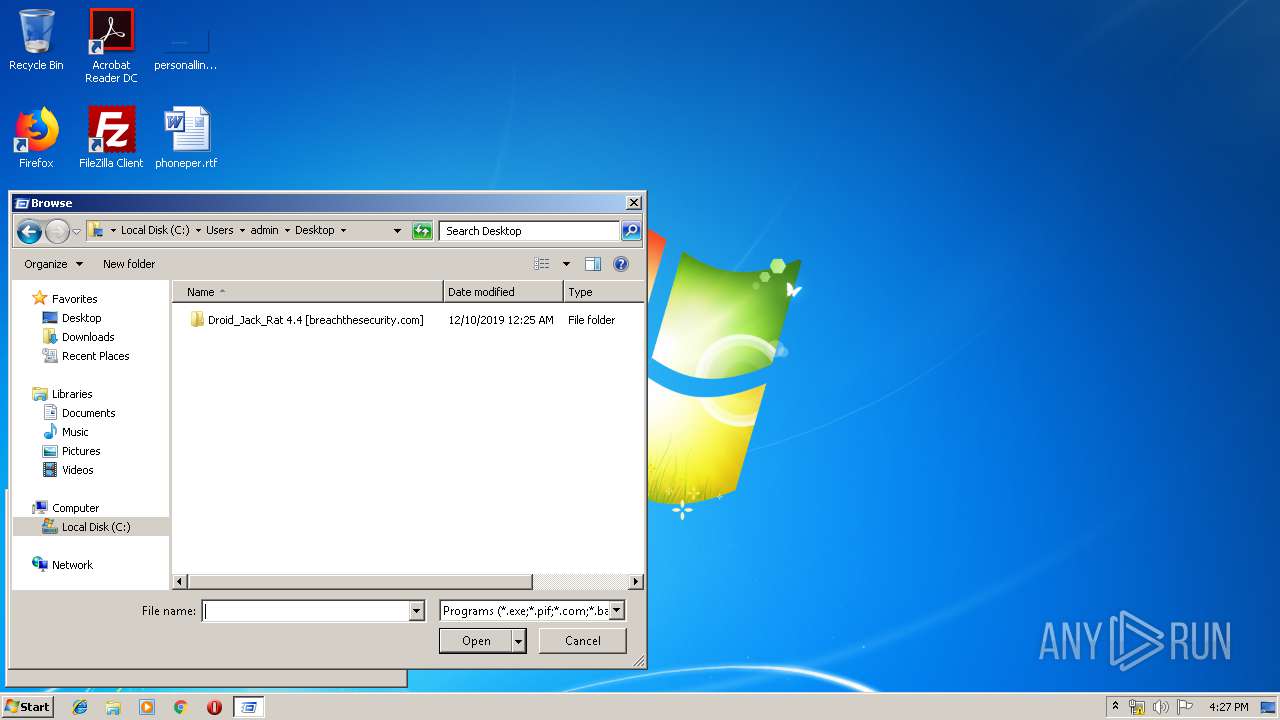
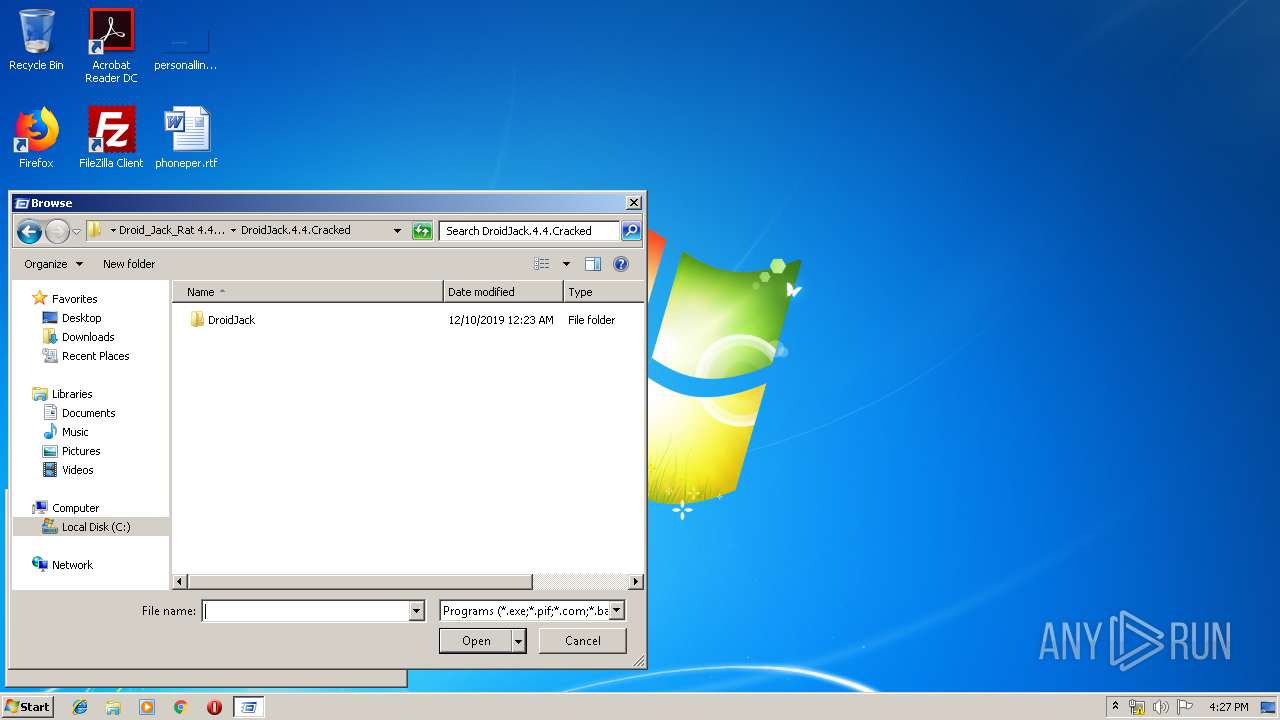
| File name: | Droid_Jack_Rat 4.4 [breachthesecurity.com].zip |
| Full analysis: | https://app.any.run/tasks/a55cb67f-39b9-4e4d-89e2-cc8f6096a81b |
| Verdict: | No threats detected |
| Analysis date: | December 09, 2019, 16:25:47 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 9008AE2EDFB3FA5BADBFE8AB034503F0 |
| SHA1: | 67E0F7A8040973676249F7E2F2AC06A42A1FC31A |
| SHA256: | ACD8FBE3A856A9CB6DF2781F4EF3864E0503A7C87FF80B3425423FBC47ABFAAB |
| SSDEEP: | 196608:eeh4W3dHjgq++lrv0YgquwqHxJ0bRronk9Jv3y7sPbARZeG09WB8OiV+dOf:vhpdJ+THxJGokjyCAGkBVLdO |
MALICIOUS
Loads dropped or rewritten executable
- javaw.exe (PID: 3700)
SUSPICIOUS
Executes JAVA applets
- javaw.exe (PID: 3700)
Creates files in the user directory
- javaw.exe (PID: 3700)
Executable content was dropped or overwritten
- javaw.exe (PID: 3700)
INFO
Manual execution by user
- javaw.exe (PID: 3700)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0808 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2019:12:10 00:25:05 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | 2 |
| ZipUncompressedSize: | - |
| ZipFileName: | Droid_Jack_Rat 4.4 [breachthesecurity.com]/ |
Total processes
40
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 956 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Droid_Jack_Rat 4.4 [breachthesecurity.com].zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3320 | java -jar Apktool/apktool.jar d Apktool/SandroRat.apk -o Apktool/SandroRat | C:\Program Files\Java\jre1.8.0_92\bin\java.exe | — | javaw.exe | |||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 1 Version: 8.0.920.14 Modules
| |||||||||||||||
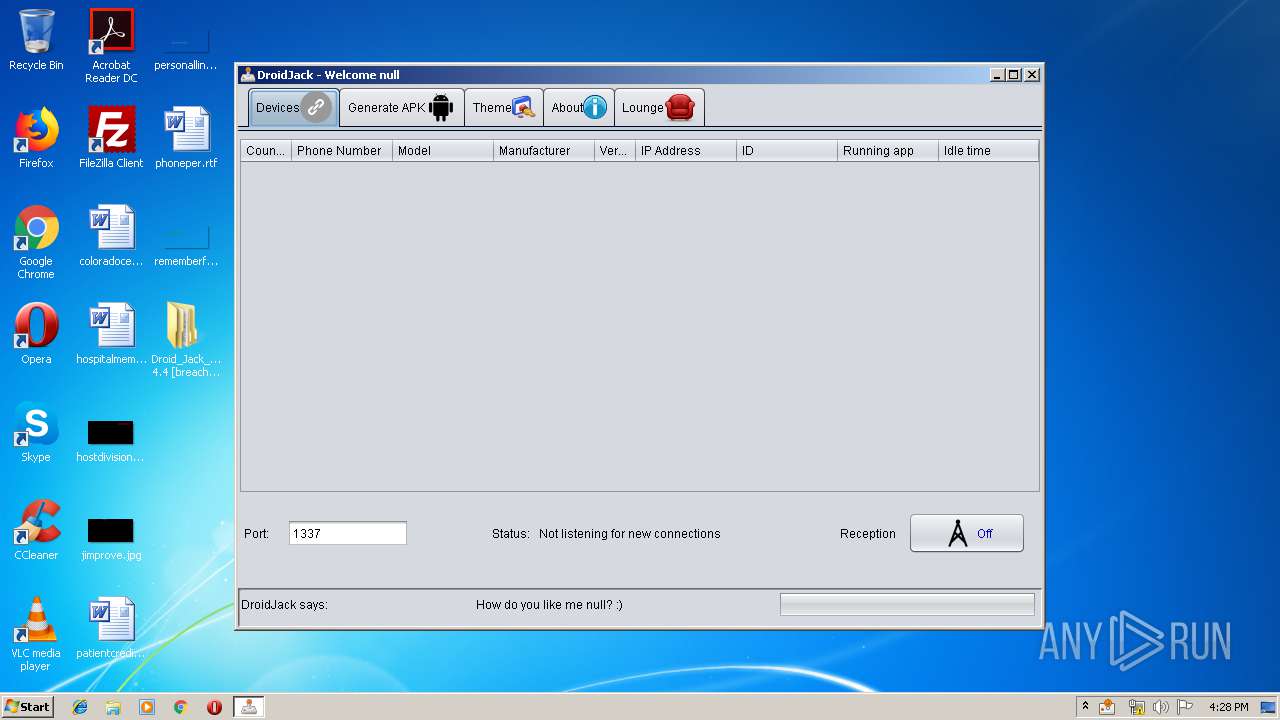
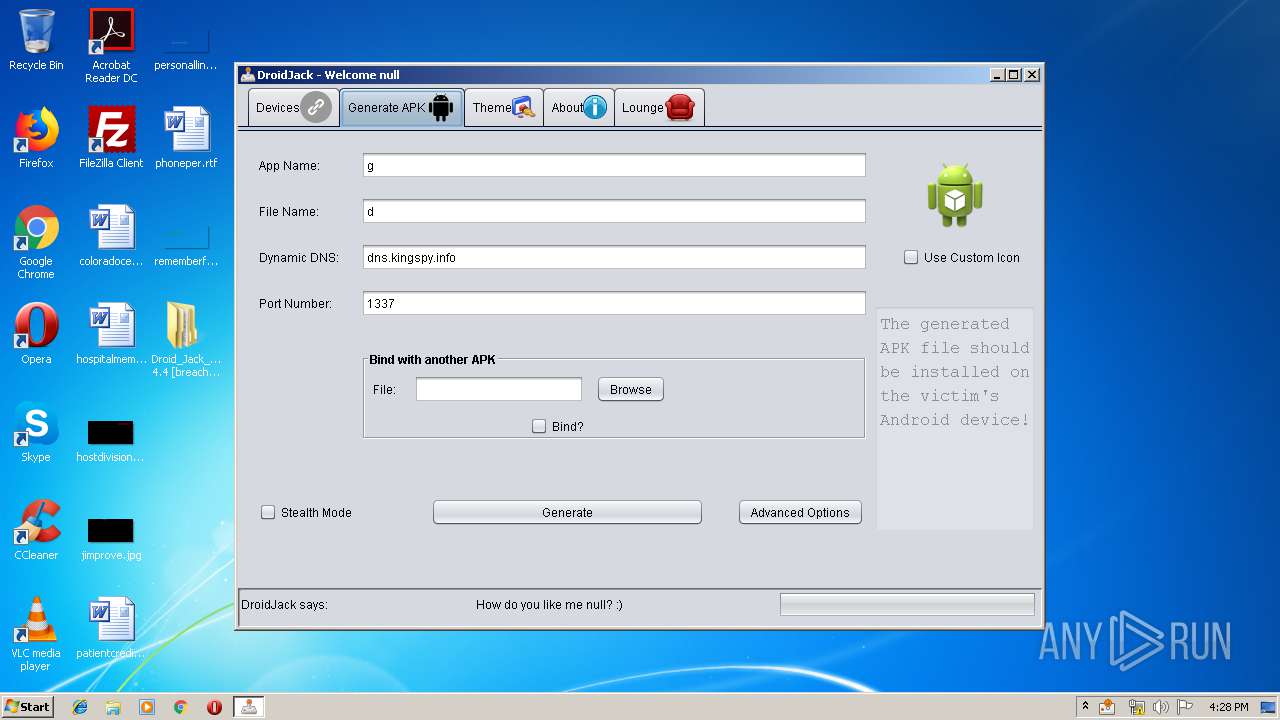
| 3700 | "C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe" -jar "C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\Droidjack.jar" | C:\Program Files\Java\jre1.8.0_92\bin\javaw.exe | explorer.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Exit code: 0 Version: 8.0.920.14 Modules
| |||||||||||||||
Total events
477
Read events
455
Write events
22
Delete events
0
Modification events
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\12B\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Droid_Jack_Rat 4.4 [breachthesecurity.com].zip | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (956) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
Executable files
6
Suspicious files
15
Text files
4
Unknown types
12
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 956 | WinRAR.exe | C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\Apktool\.DS_Store | ds_store | |
MD5:010C44C7918725F07BC33DDA1FE1938B | SHA256:8C7D7C53AF7189A9235E4A43ED2694F874C20CE061CE23B1F271436E8404A64D | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\Apktool\signapk.jar | java | |
MD5:AEC6985FE2314E4D032BA6D192AC4163 | SHA256:B17534E89A5B58D5E343BA54A49DA579CF9213988F4BEEAE24FE4582A0C226BB | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\Apktool\SandroRat.apk | compressed | |
MD5:15F7199148DD83CC0F76FBD7EDCD6EE5 | SHA256:30AA2EEEB8401E4A312A7E99462432769A7C569114180AAEDBFCBEF18B6DB268 | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\DroidJack_lib\commons-io-2.4.jar | compressed | |
MD5:7F97854DC04C119D461FED14F5D8BB96 | SHA256:CC6A41DC3EAACC9E440A6BD0D2890B20D36B4EE408FE2D67122F328BB6E01581 | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\DroidJack_lib\commons-lang3-3.3.2.jar | compressed | |
MD5:18BB67AFA15354843EBFB7640CBB9C5F | SHA256:46D24EA8D0771655AEC5FDF203CA4BFAB4CC1A4587B8A15901D385F80263DD36 | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\Apktool\efm.jar | text | |
MD5:A91F7CBBD06F657BD7608B70CF7FB864 | SHA256:91D79633B19D62B0EA71341B1692F49B2B59F9535E30A181D66FC4E83B0A2660 | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\DroidJack_lib\json.jar | compressed | |
MD5:092F12BCF4E448262CEBDA81C032950B | SHA256:38C21B9C3D6D24919CD15D027D20AFAB0A019AC9205F7ED9083B32BDD42A2353 | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\DroidJack_lib\fluent-hc-4.2.5.jar | compressed | |
MD5:5A387F6BEC45CB94C7F2667C15CBF00F | SHA256:E13070F38957FC1C063895105AB64C810A3FD8B4B6AB5D45CE2D508C8D5FA192 | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\DroidJack_lib\commons-logging-1.1.1.jar | compressed | |
MD5:ED448347FC0104034AA14C8189BF37DE | SHA256:CE6F913CAD1F0DB3AAD70186D65C5BC7FFCC9A99E3FE8E0B137312819F7C362F | |||
| 956 | WinRAR.exe | C:\Users\admin\Desktop\Droid_Jack_Rat 4.4 [breachthesecurity.com]\DroidJack.4.4.Cracked\DroidJack\DroidJack_lib\httpmime-4.2.5.jar | compressed | |
MD5:8DF1654C39F4116C9F1FCD04F8505BC2 | SHA256:2EF409C599C532CA1E692013582695231BDB9F3956D4EC9BA3AC71300728B382 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
1
TCP/UDP connections
1
DNS requests
1
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3700 | javaw.exe | GET | 200 | 162.251.80.24:80 | http://www.droidjack.net/Terms.html | US | html | 3.37 Kb | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3700 | javaw.exe | 162.251.80.24:80 | www.droidjack.net | PDR | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.droidjack.net |
| malicious |