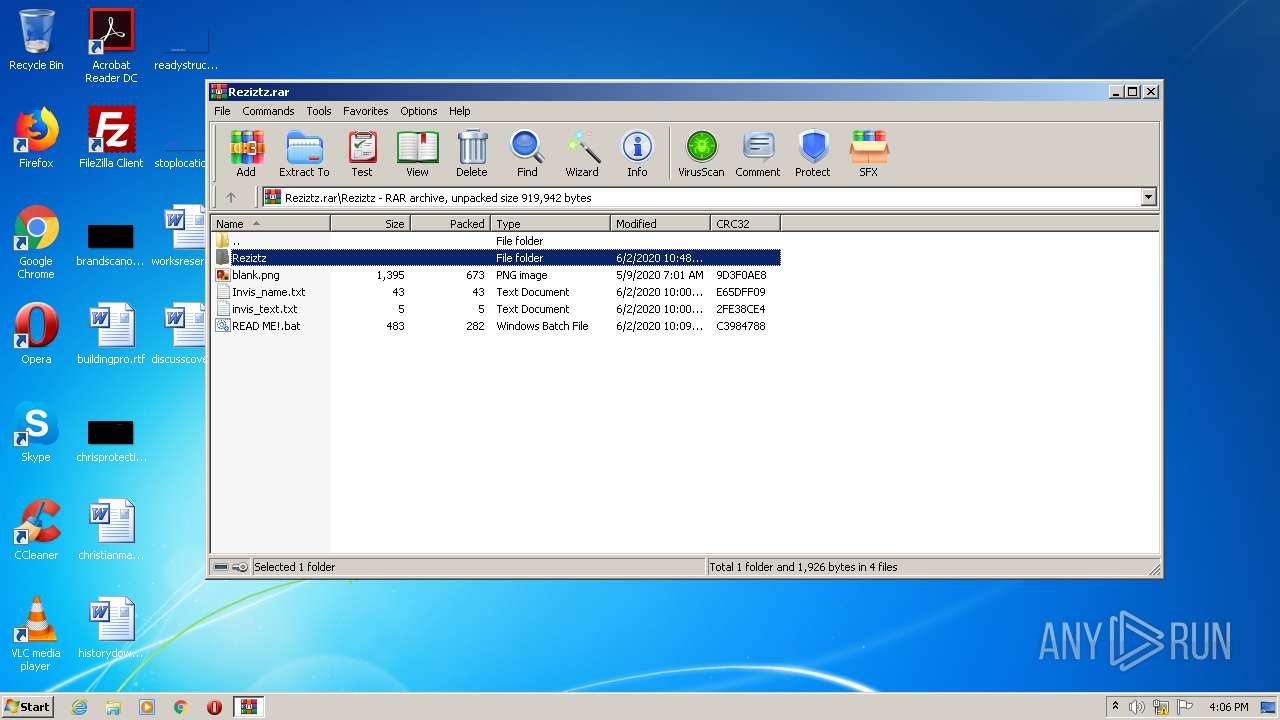
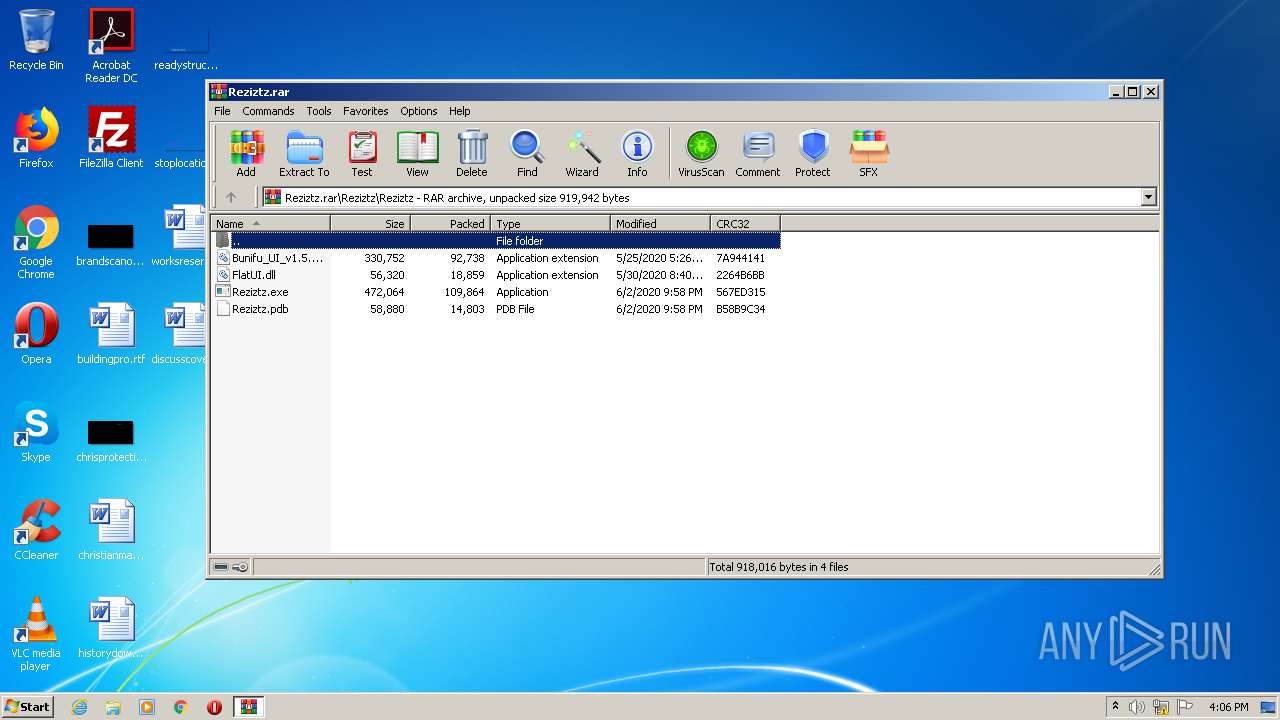
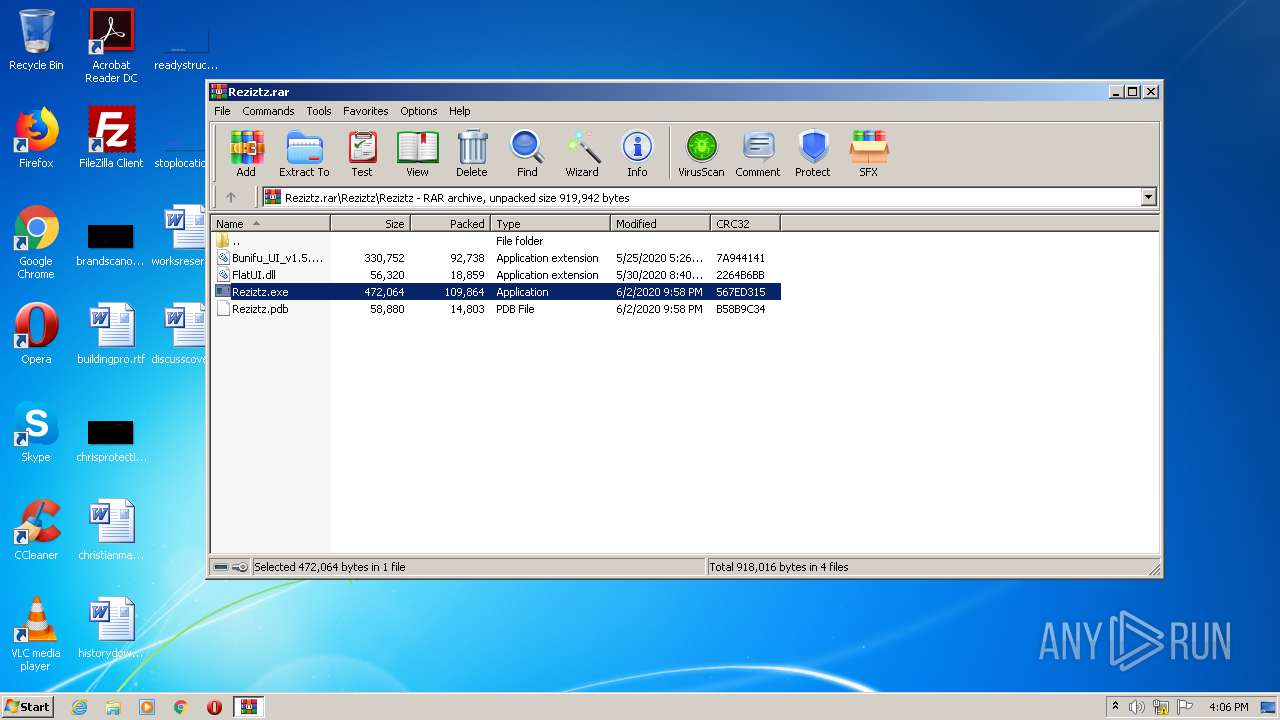
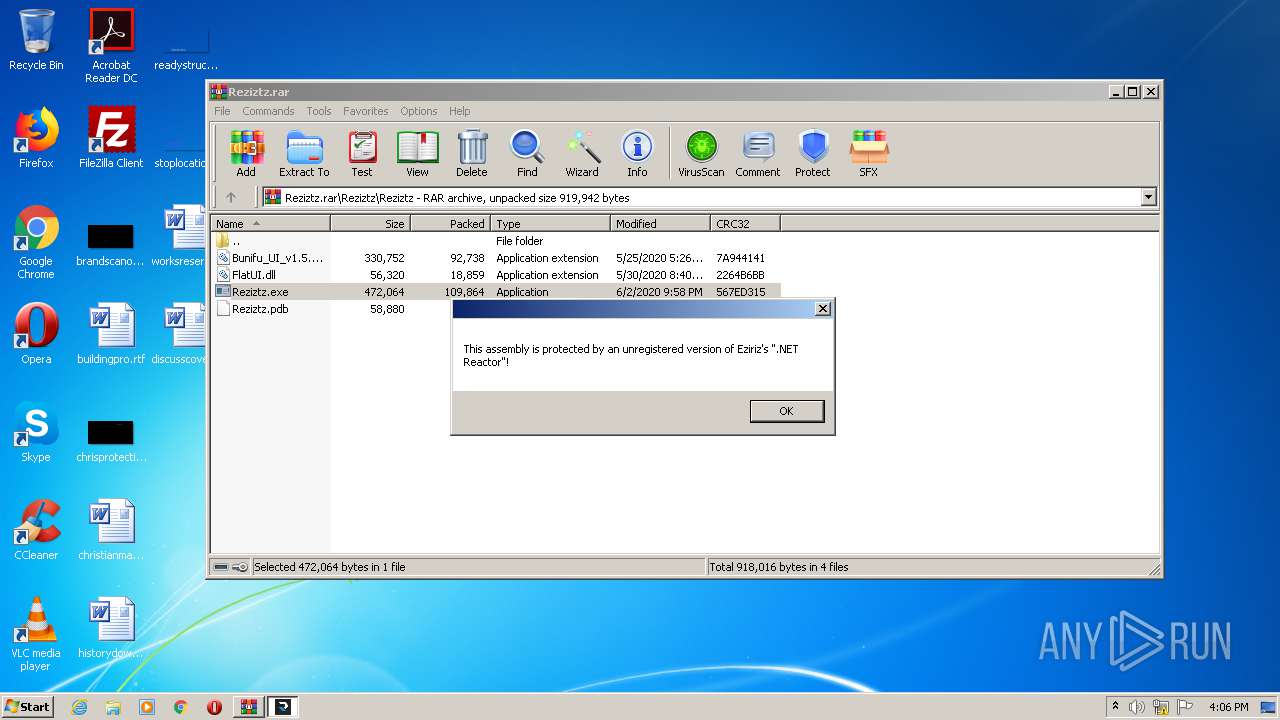
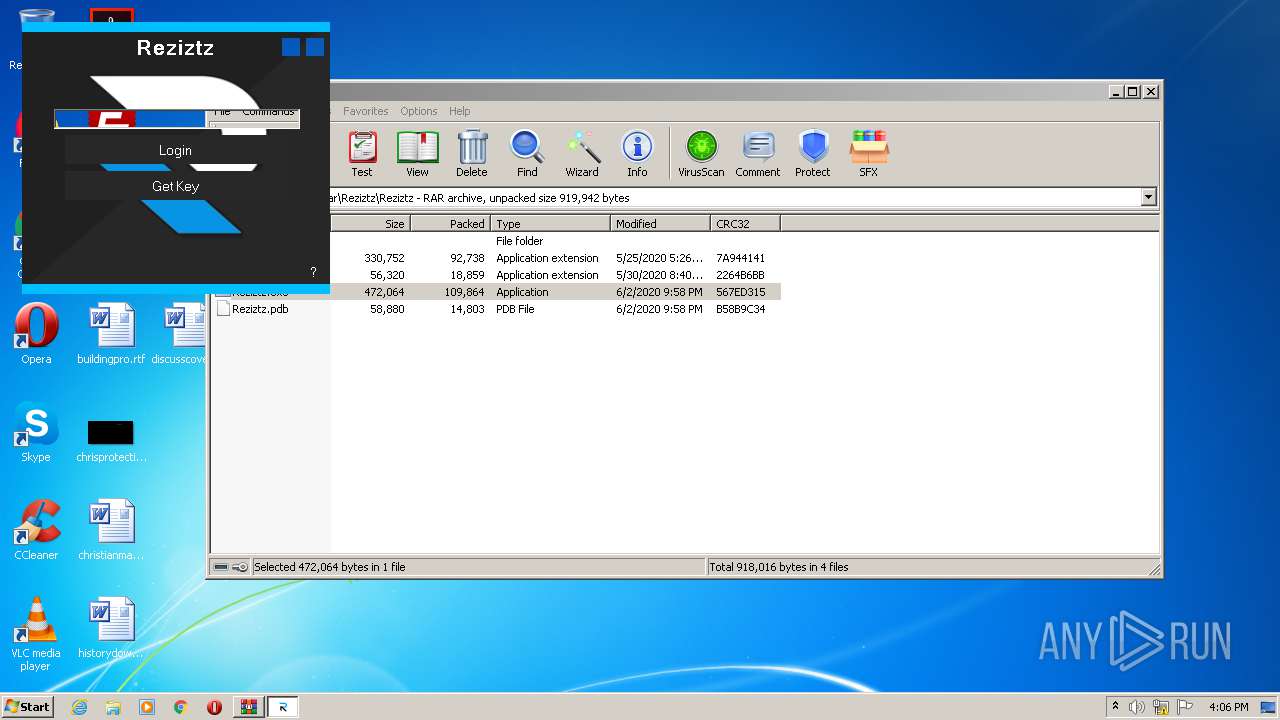
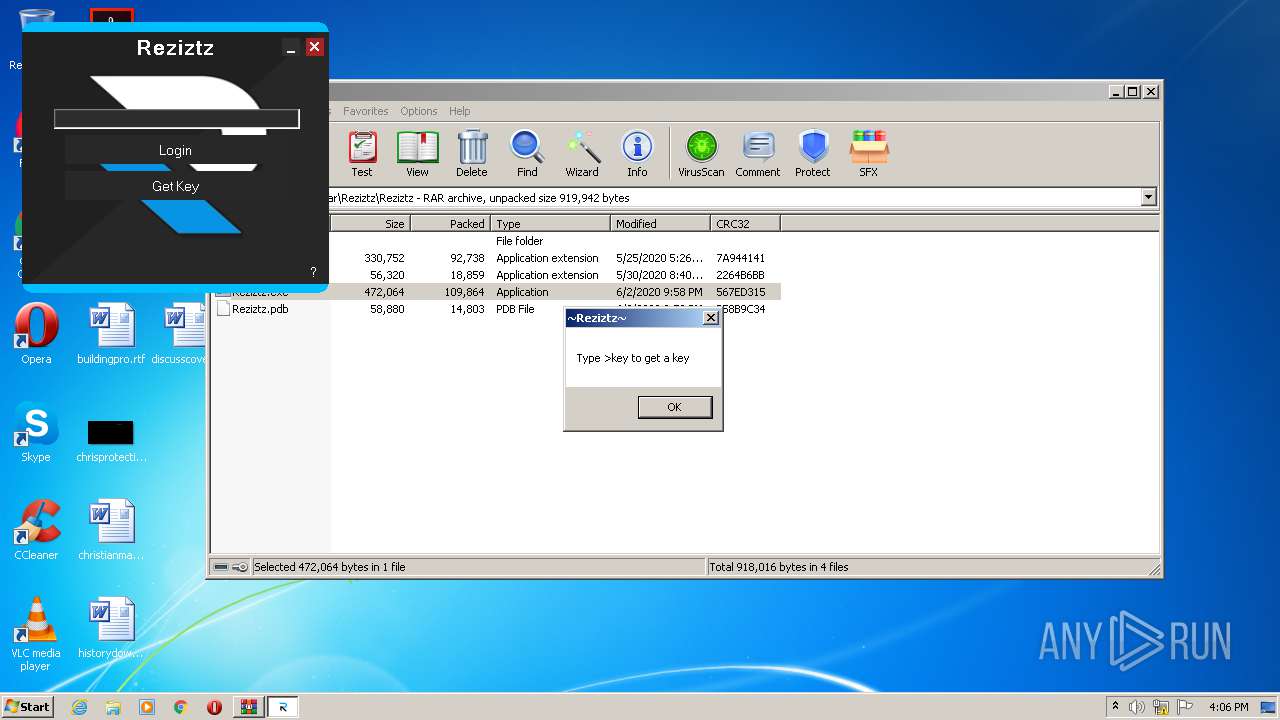
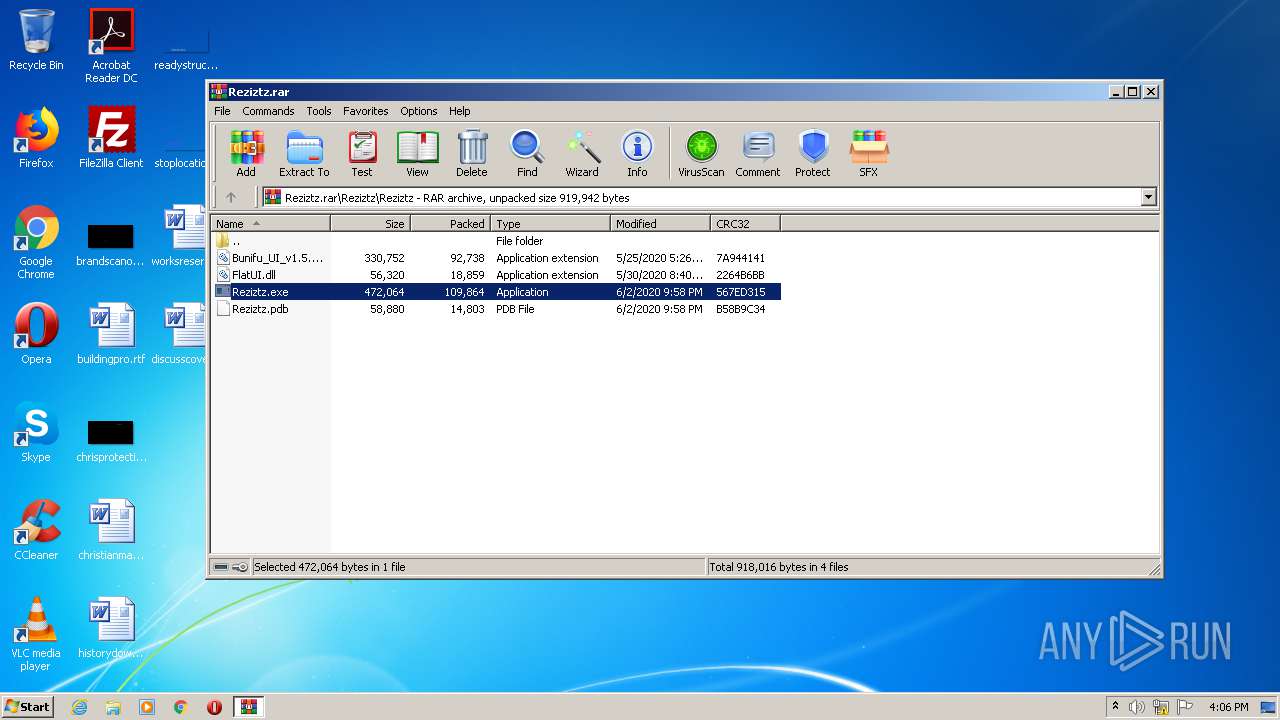
| File name: | Reziztz.rar |
| Full analysis: | https://app.any.run/tasks/42f5846b-bb13-42ec-a768-c307f14f2fb9 |
| Verdict: | Malicious activity |
| Analysis date: | August 08, 2020, 15:05:45 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | 2637DEEF589971B4612EC3C51DEE60C4 |
| SHA1: | 760A4B7B169376A7430AC4E5931D193C52285DC2 |
| SHA256: | ACC5C4FB8952C367C6E04435818E09E563943CE1A9EB4CA57609B14ED100210E |
| SSDEEP: | 6144:mMBLRv0bk2Y0CsHtvgiiIryt2/8NkAoX/JtKZ:bLRvILYfs2H7N1s/Jc |
MALICIOUS
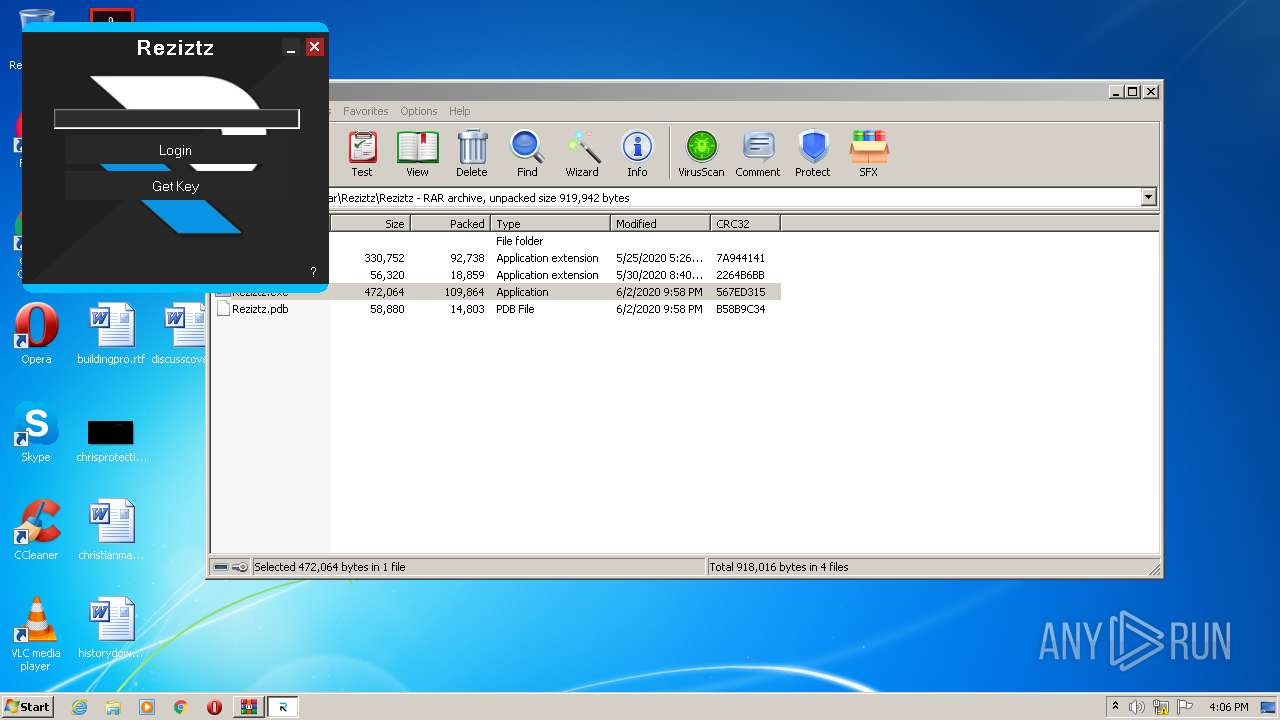
Application was dropped or rewritten from another process
- Reziztz.exe (PID: 2480)
- Reziztz.exe (PID: 3952)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1700)
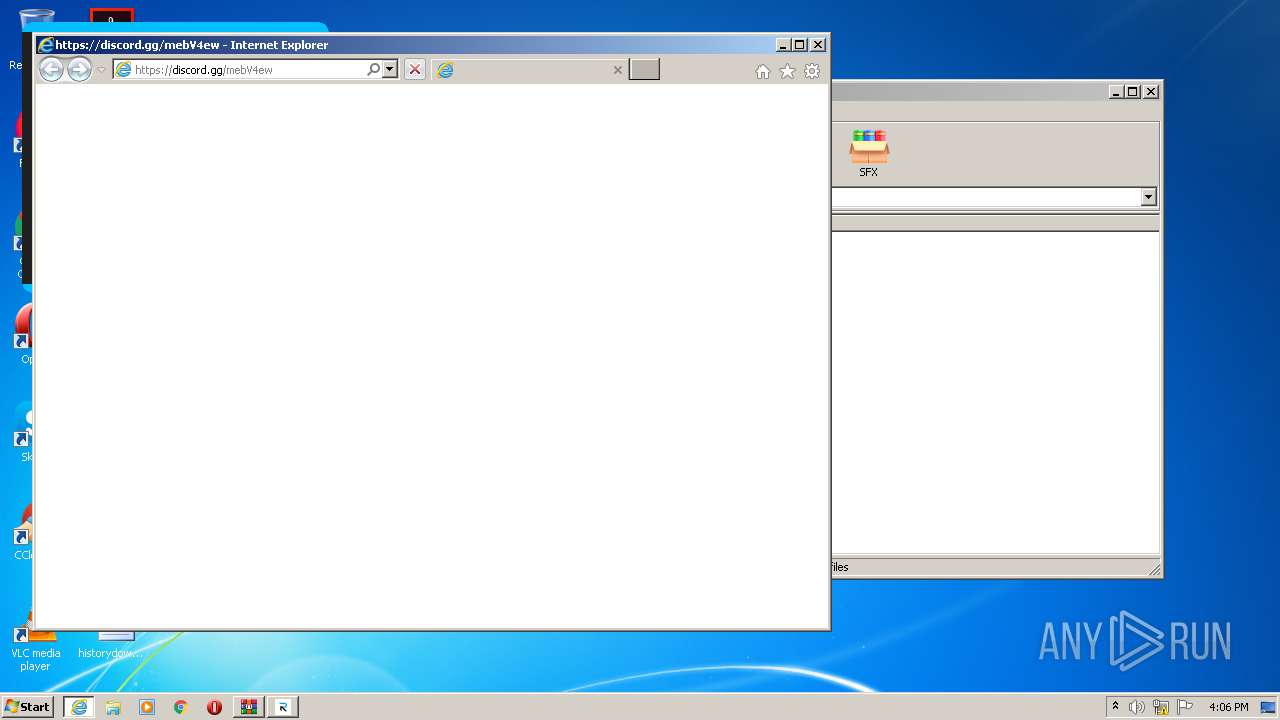
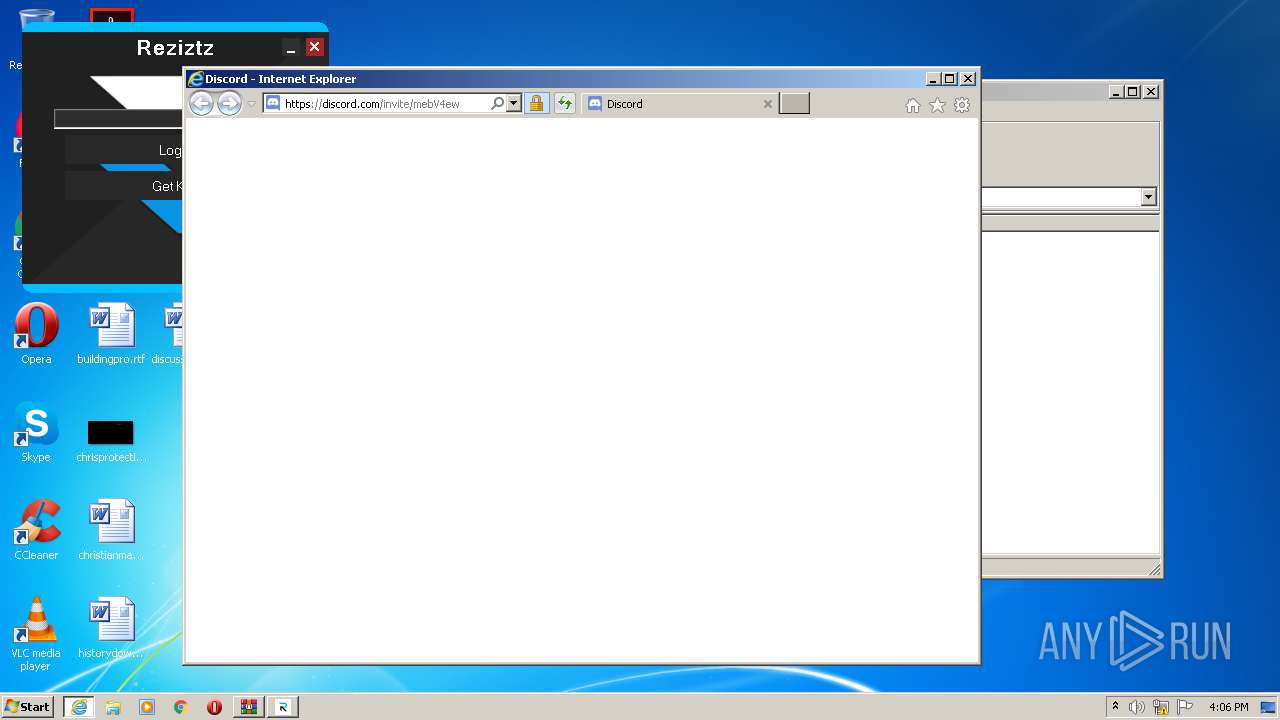
Starts Internet Explorer
- Reziztz.exe (PID: 3952)
INFO
Dropped object may contain Bitcoin addresses
- WinRAR.exe (PID: 1700)
- iexplore.exe (PID: 3352)
Reads Internet Cache Settings
- iexplore.exe (PID: 3088)
- iexplore.exe (PID: 3352)
Application launched itself
- iexplore.exe (PID: 3088)
Changes internet zones settings
- iexplore.exe (PID: 3088)
Reads settings of System Certificates
- iexplore.exe (PID: 3352)
Changes settings of System certificates
- iexplore.exe (PID: 3352)
Adds / modifies Windows certificates
- iexplore.exe (PID: 3352)
Creates files in the user directory
- iexplore.exe (PID: 3352)
Reads internet explorer settings
- iexplore.exe (PID: 3352)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
49
Monitored processes
5
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1700 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Reziztz.rar" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 2480 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1700.1446\Reziztz\Reziztz\Reziztz.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1700.1446\Reziztz\Reziztz\Reziztz.exe | — | WinRAR.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: Reziztz Exit code: 3221226540 Version: 1.0.0.0 Modules
| |||||||||||||||
| 3088 | "C:\Program Files\Internet Explorer\iexplore.exe" https://discord.gg/mebV4ew | C:\Program Files\Internet Explorer\iexplore.exe | Reziztz.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3352 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3088 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3952 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa1700.1446\Reziztz\Reziztz\Reziztz.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa1700.1446\Reziztz\Reziztz\Reziztz.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: Reziztz Exit code: 0 Version: 1.0.0.0 Modules
| |||||||||||||||
Total events
982
Read events
877
Write events
105
Delete events
0
Modification events
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\137\52C64B7E |
| Operation: | write | Name: | @C:\Windows\system32\NetworkExplorer.dll,-1 |
Value: Network | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Reziztz.rar | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (1700) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
Executable files
3
Suspicious files
22
Text files
15
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3352 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab823.tmp | — | |
MD5:— | SHA256:— | |||
| 3352 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar824.tmp | — | |
MD5:— | SHA256:— | |||
| 1700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1700.1446\Reziztz\READ ME!.bat | text | |
MD5:— | SHA256:— | |||
| 1700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1700.1446\Reziztz\invis_text.txt | text | |
MD5:— | SHA256:— | |||
| 1700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1700.1446\Reziztz\Reziztz\Reziztz.exe | executable | |
MD5:— | SHA256:— | |||
| 1700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1700.1446\Reziztz\blank.png | image | |
MD5:— | SHA256:— | |||
| 3352 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6AF4EE75E3A4ABA658C0087EB9A0BB5B_920AF9260C528FAB1F15CA0957850F9F | binary | |
MD5:— | SHA256:— | |||
| 3352 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\6AF4EE75E3A4ABA658C0087EB9A0BB5B_A71343B9E0448D72FD8C4A424ADA33C2 | binary | |
MD5:— | SHA256:— | |||
| 1700 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa1700.1446\Reziztz\Reziztz\Bunifu_UI_v1.5.3.dll | executable | |
MD5:E0EF2817EE5A7C8CD1EB837195768BD2 | SHA256:76E1D3EC95FDEF74ABAF90392DD6F4AA5E344922ABF11E572707287D467F2930 | |||
| 3352 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\6AF4EE75E3A4ABA658C0087EB9A0BB5B_A71343B9E0448D72FD8C4A424ADA33C2 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
13
DNS requests
8
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3352 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 314 b | whitelisted |
3352 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEBblhnjgcJQ5S9%2FbTvymO98%3D | US | der | 471 b | whitelisted |
3352 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEDsJGKKiFxWJllawuNqPxXw%3D | US | der | 279 b | whitelisted |
3352 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrJdiQ%2Ficg9B19asFe73bPYs%2BreAQUdXGnGUgZvJ2d6kFH35TESHeZ03kCEFslzmkHxCZVZtM5DJmpVK0%3D | US | der | 314 b | whitelisted |
3352 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEQCML6NXQdejdBJDG5j4aa9U | US | der | 279 b | whitelisted |
3352 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEDsJGKKiFxWJllawuNqPxXw%3D | US | der | 279 b | whitelisted |
3352 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca4.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTOpjOEf6LG1z52jqAxwDlTxoaOCgQUQAlhZ%2FC8g3FP3hIILG%2FU1Ct2PZYCEQCML6NXQdejdBJDG5j4aa9U | US | der | 279 b | whitelisted |
3352 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEBblhnjgcJQ5S9%2FbTvymO98%3D | US | der | 471 b | whitelisted |
3088 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3352 | iexplore.exe | 151.139.128.14:80 | ocsp.comodoca.com | Highwinds Network Group, Inc. | US | suspicious |
— | — | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3352 | iexplore.exe | 162.159.135.232:443 | discord.com | Cloudflare Inc | — | malicious |
3352 | iexplore.exe | 162.159.133.234:443 | discord.gg | Cloudflare Inc | — | shared |
DNS requests
Domain | IP | Reputation |
|---|---|---|
discord.gg |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
ocsp.comodoca4.com |
| whitelisted |
discord.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |