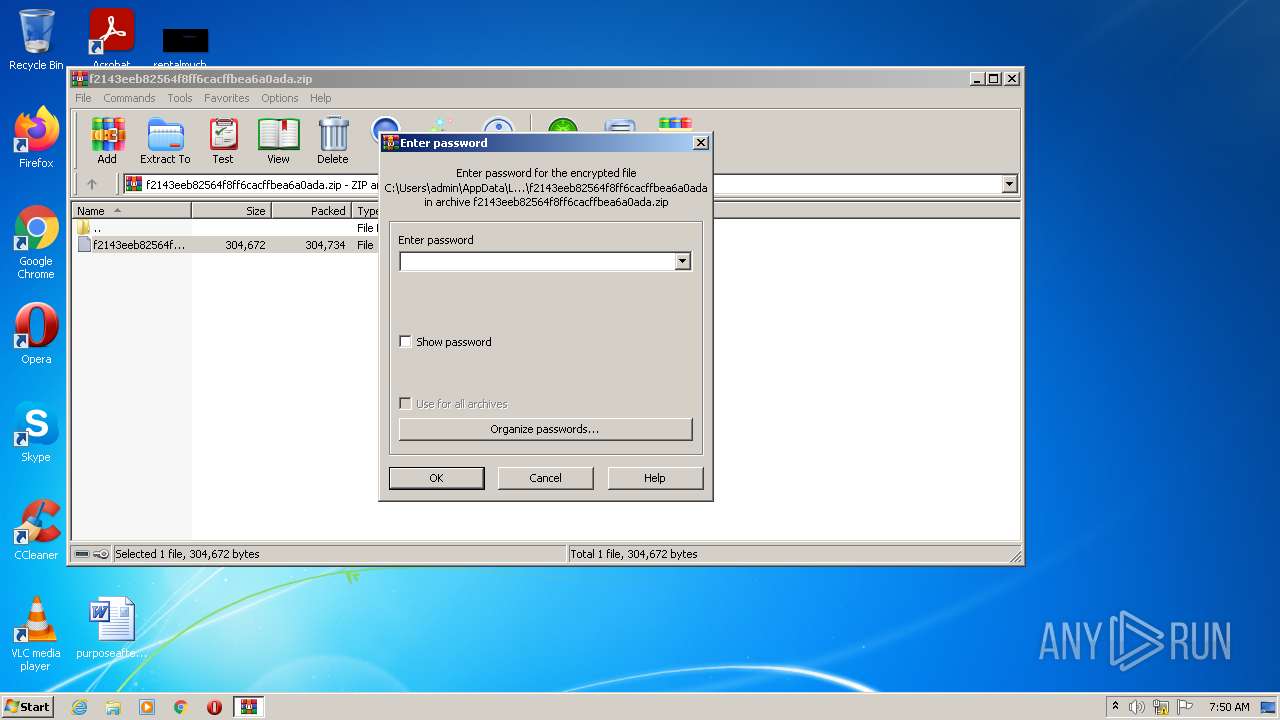
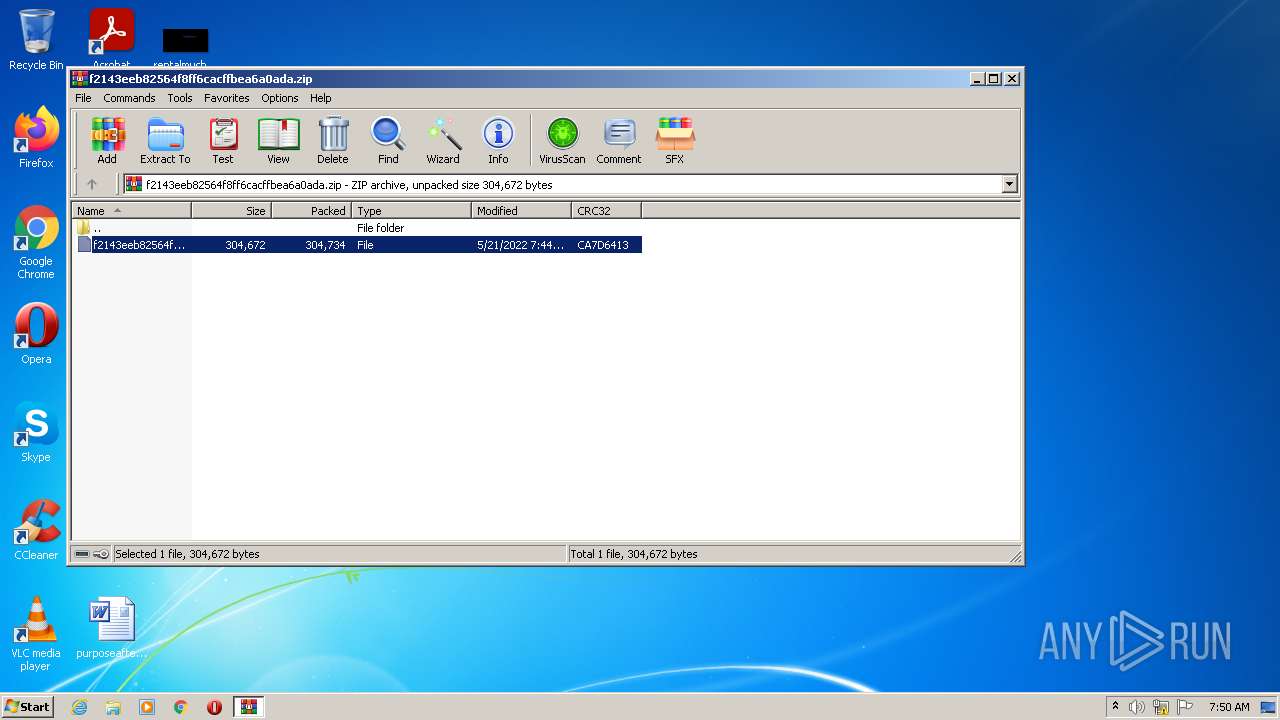
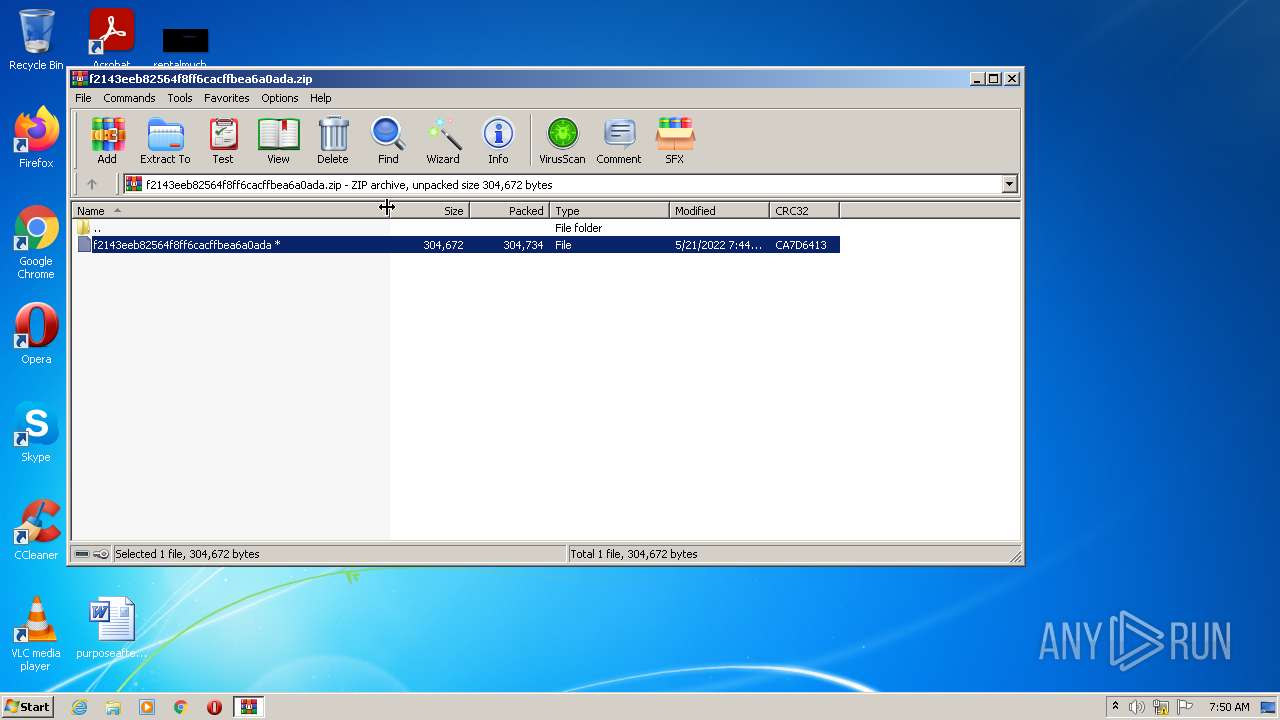
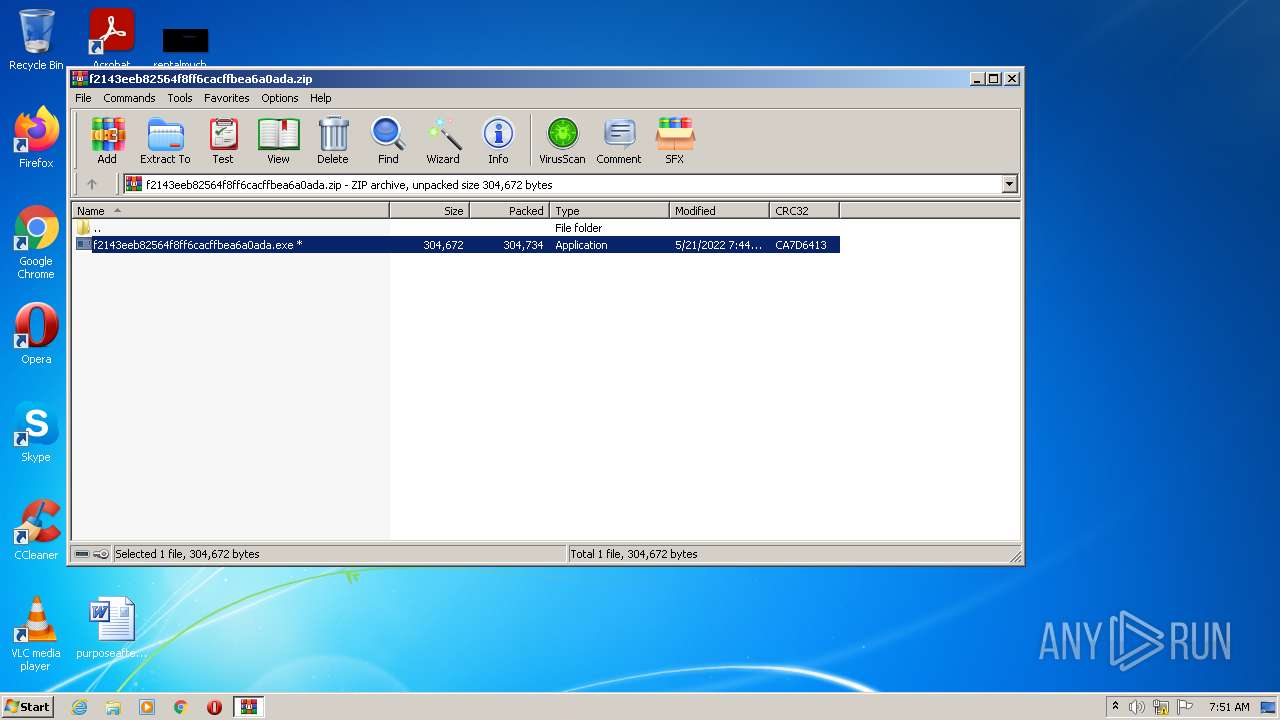
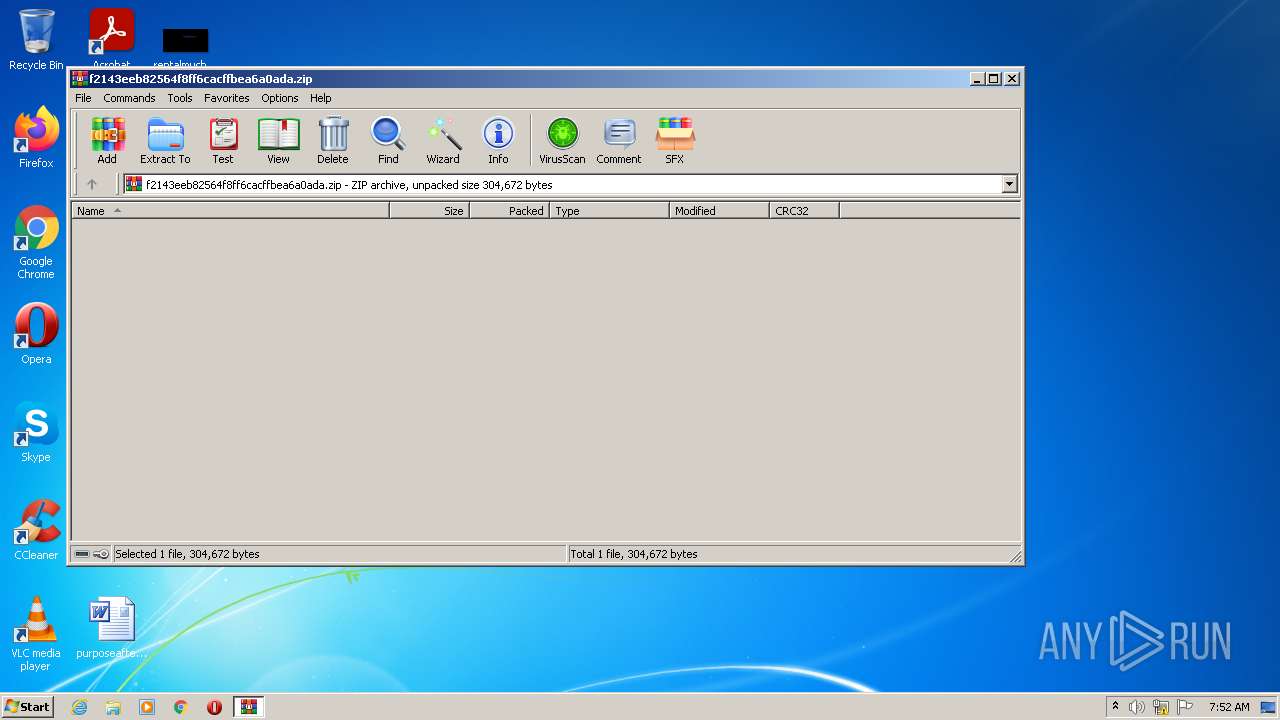
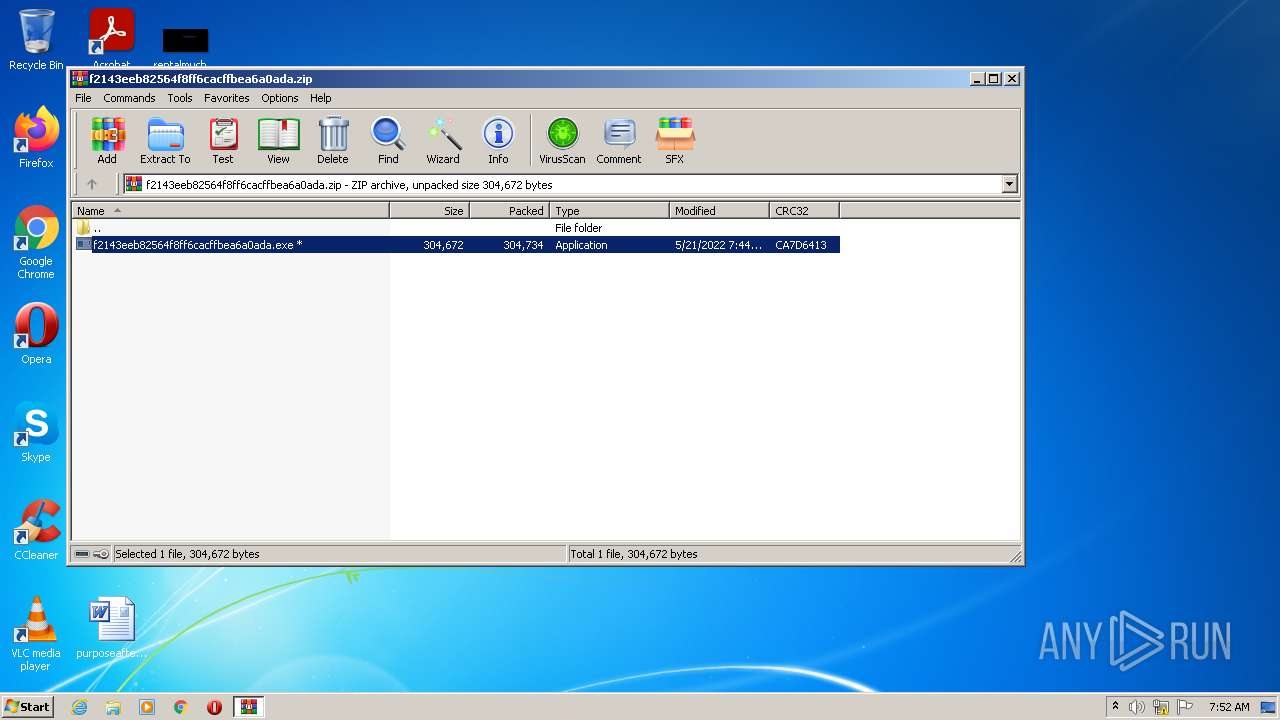
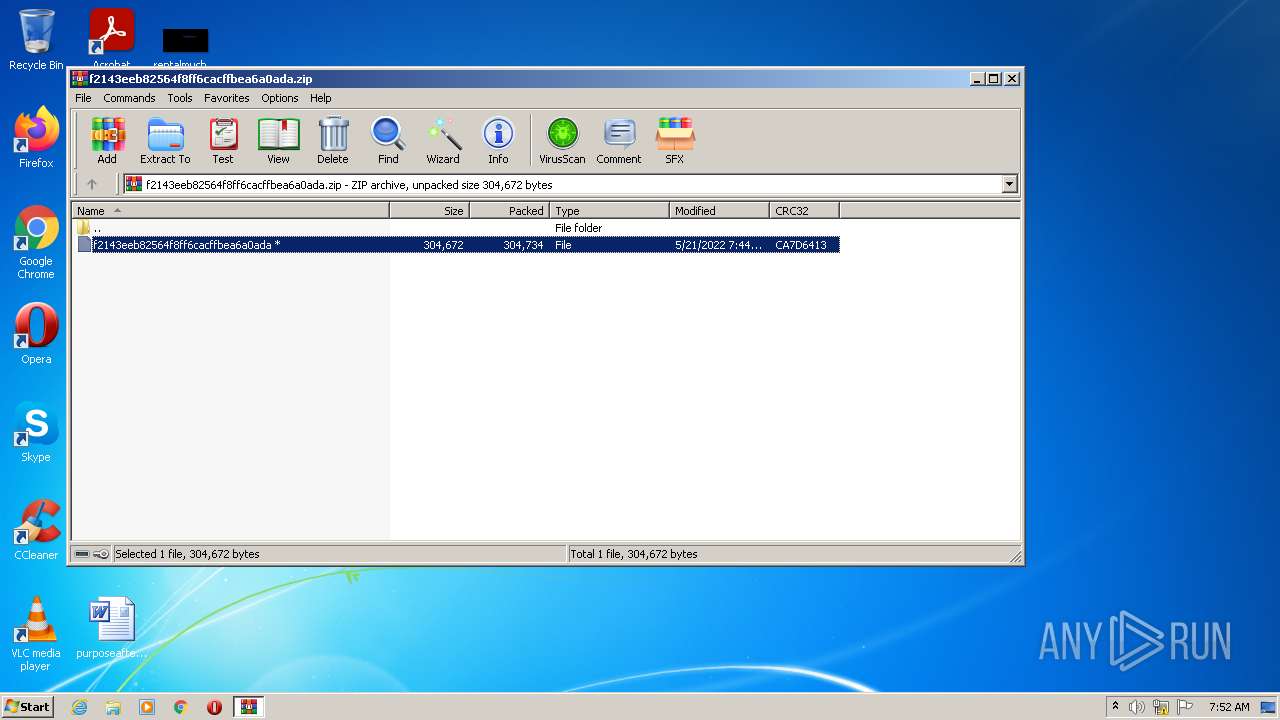
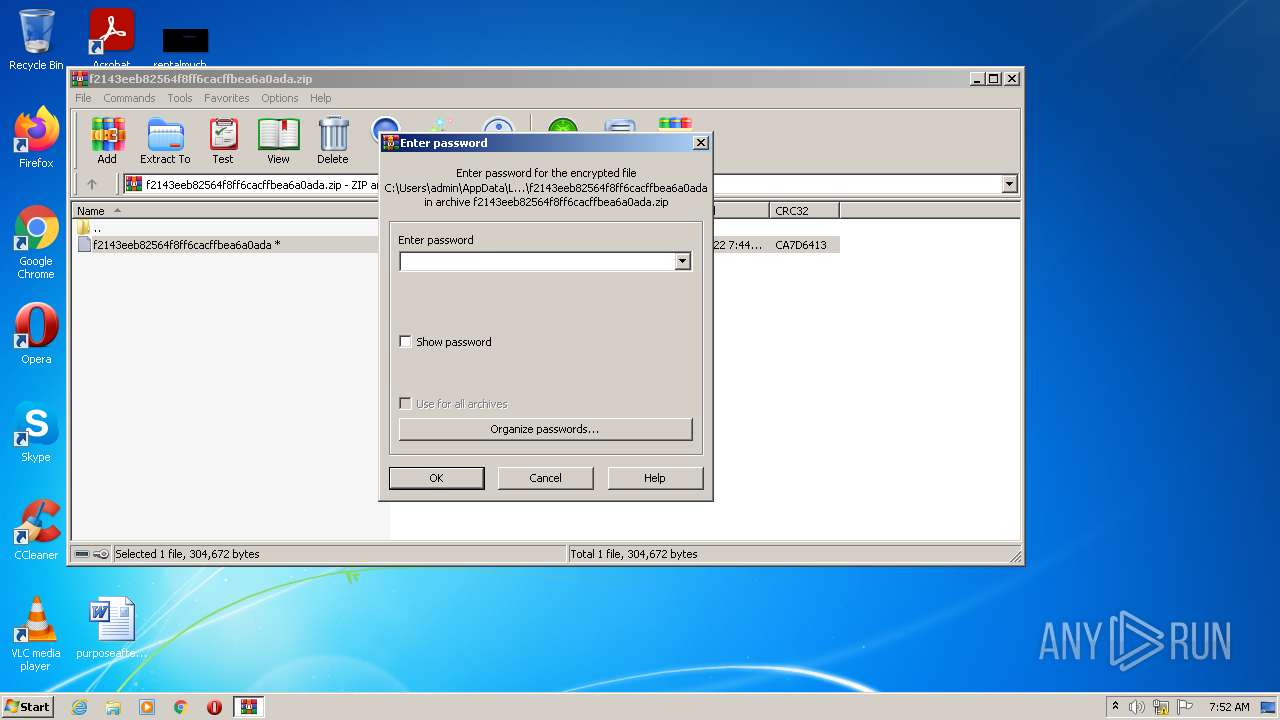
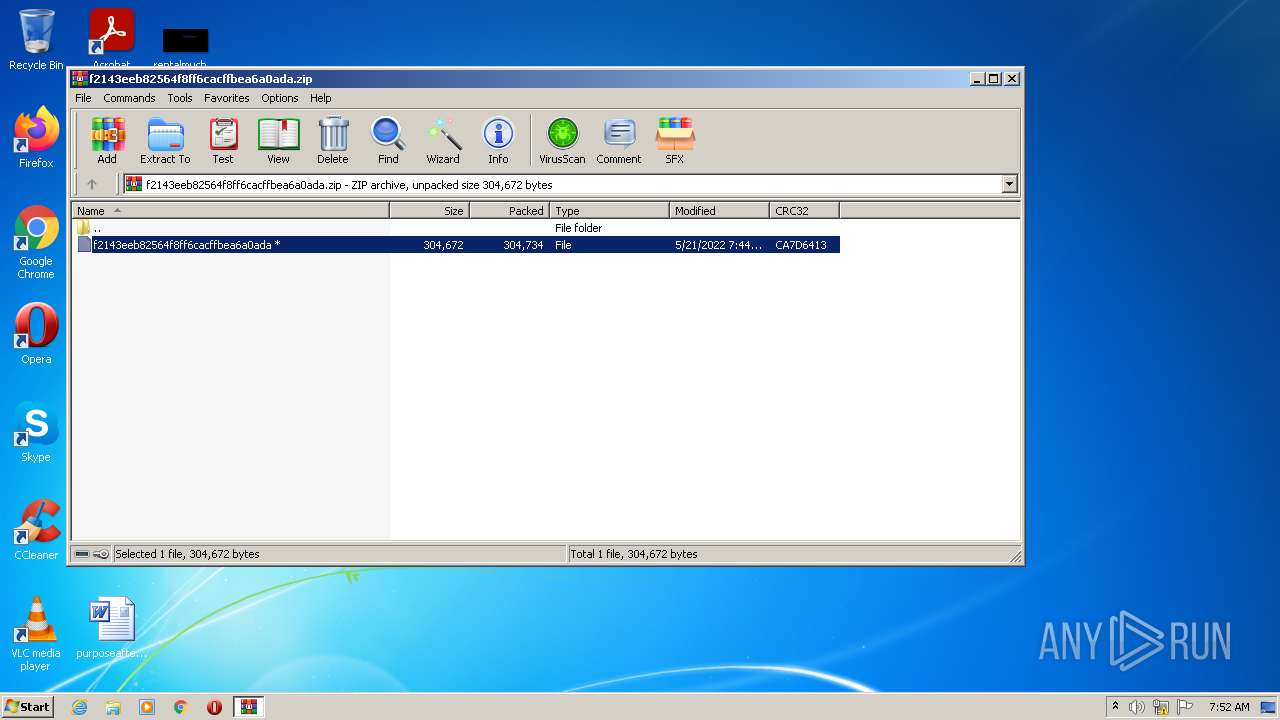
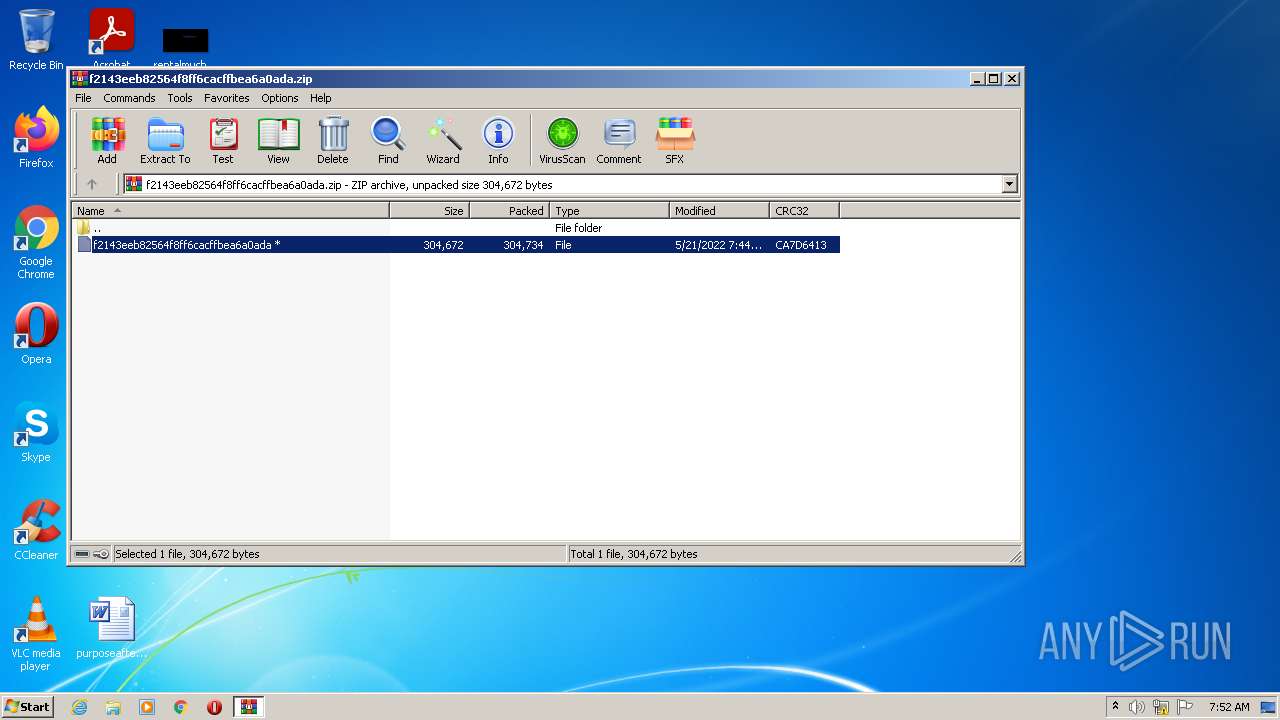
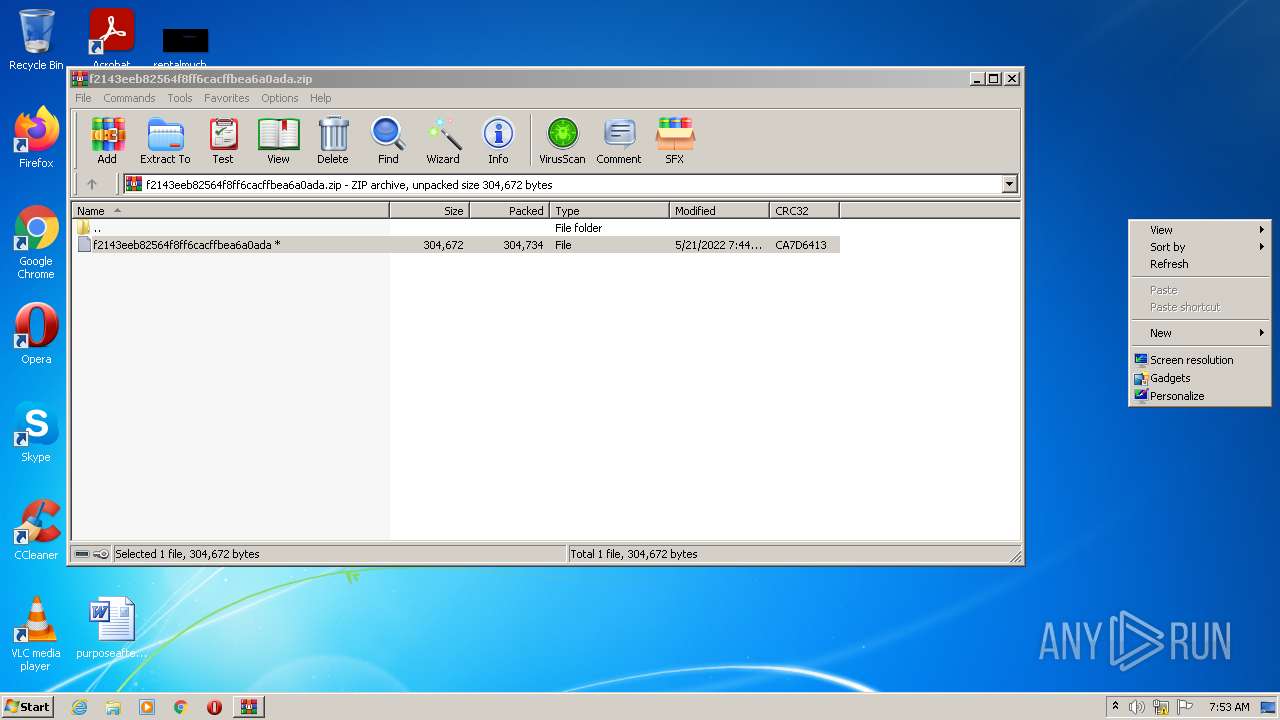
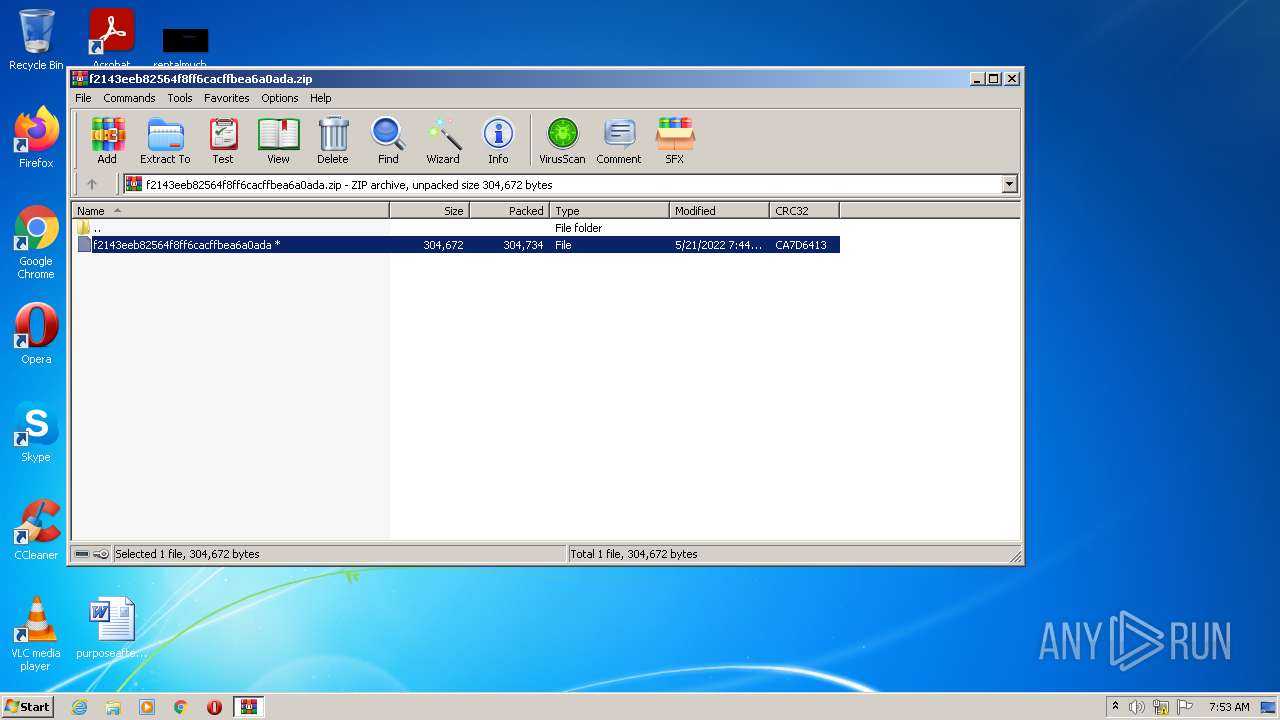
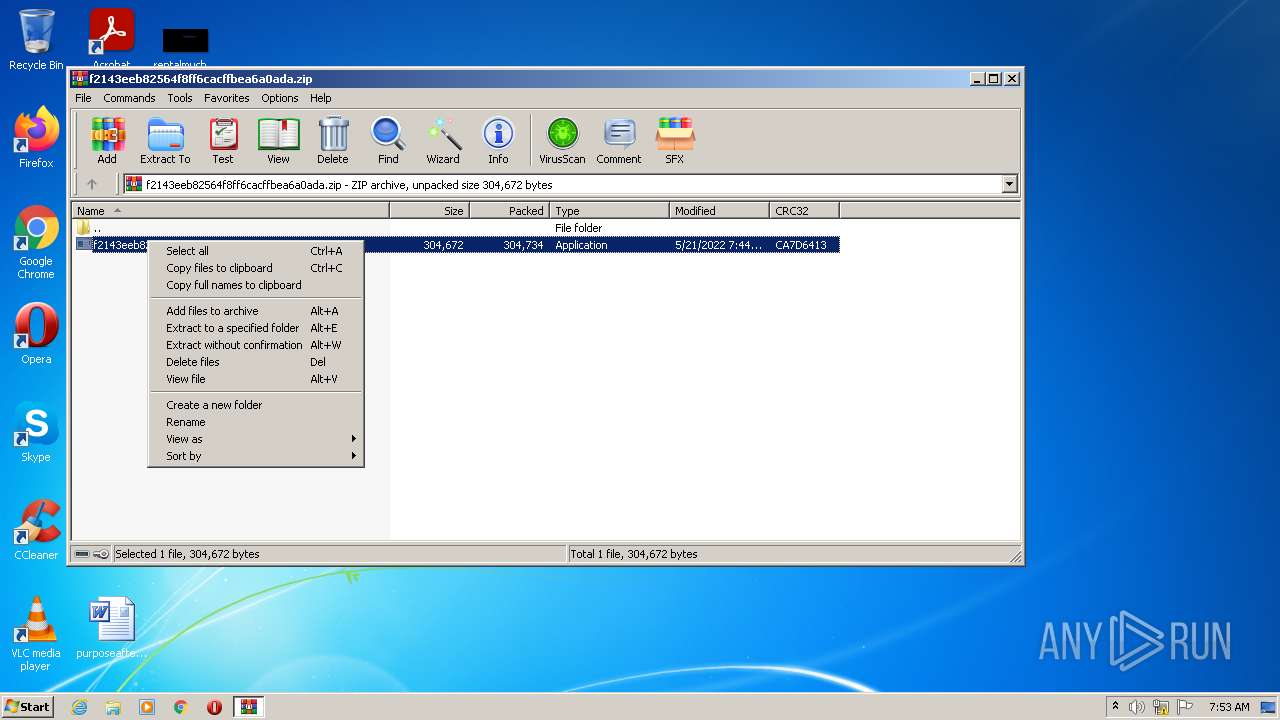
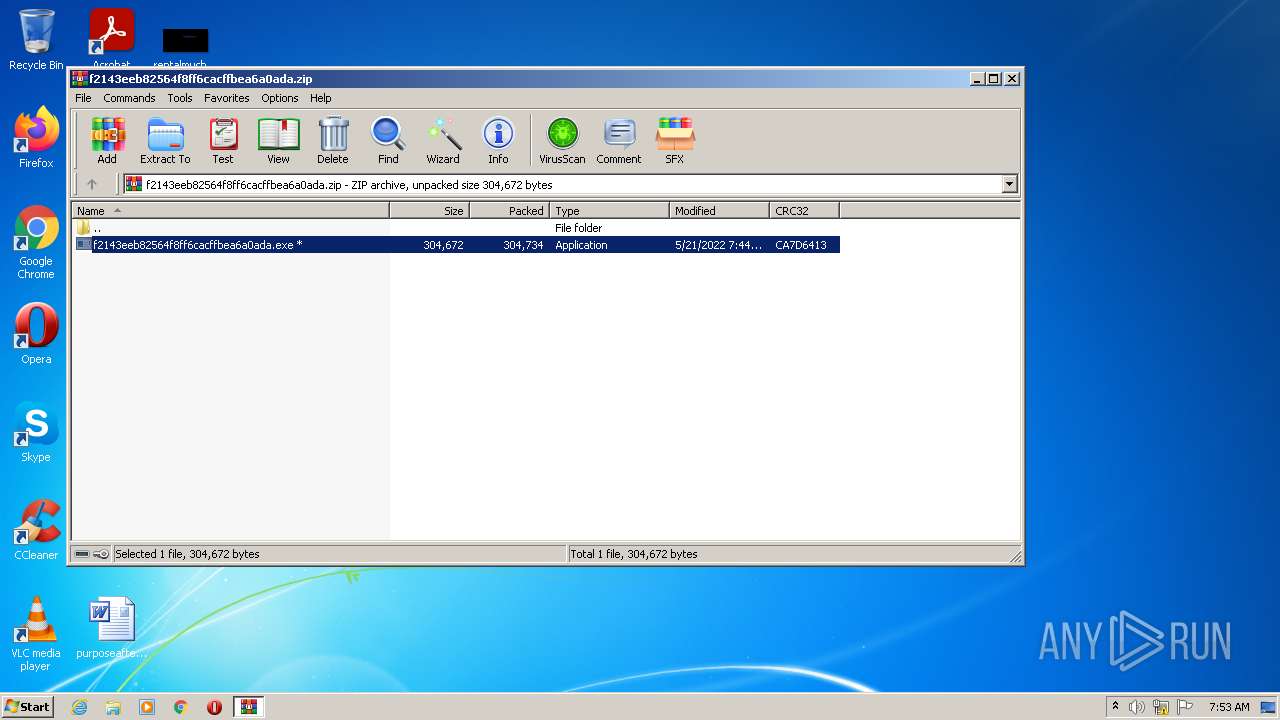
| File name: | f2143eeb82564f8ff6cacffbea6a0ada.zip |
| Full analysis: | https://app.any.run/tasks/b378f9c0-1f17-4810-9111-c402d9bf67d2 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2022, 06:50:23 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | B25DAC140DAFD052C24A98F95CCDEA35 |
| SHA1: | 5DADD05703FFBCA1862EFFAEDBEC73F2C2BCC105 |
| SHA256: | ACBCD4A0C6349F8F9956E6E1010E18F5E980E4AFA5114479C0742085284F4D52 |
| SSDEEP: | 6144:BeUXMk2vcPxXyPhVBVuuDpxtaMwoRm/RtZdhfSQpqyy2HivY1eHG+nVwod6q:B3M7cPMPbBVuudxtarGm5aQpM2CEswoR |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executes application which crashes
- WinRAR.exe (PID: 2952)
Reads the computer name
- WinRAR.exe (PID: 2952)
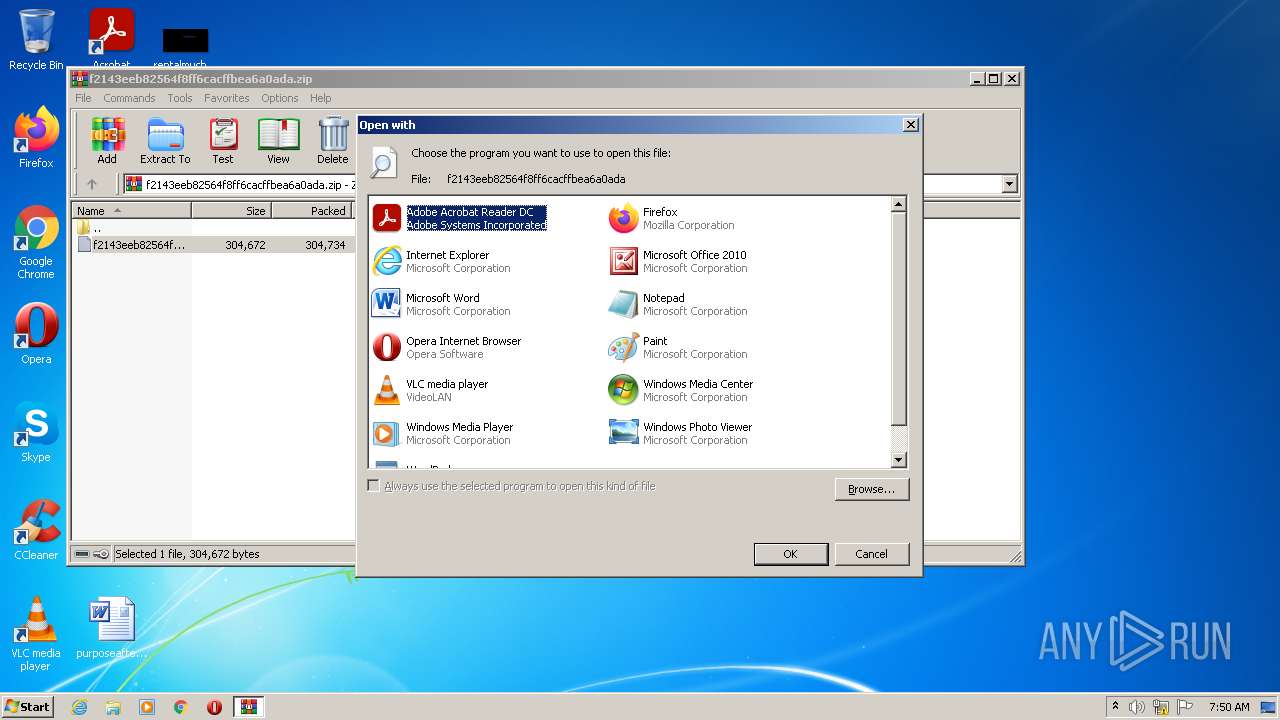
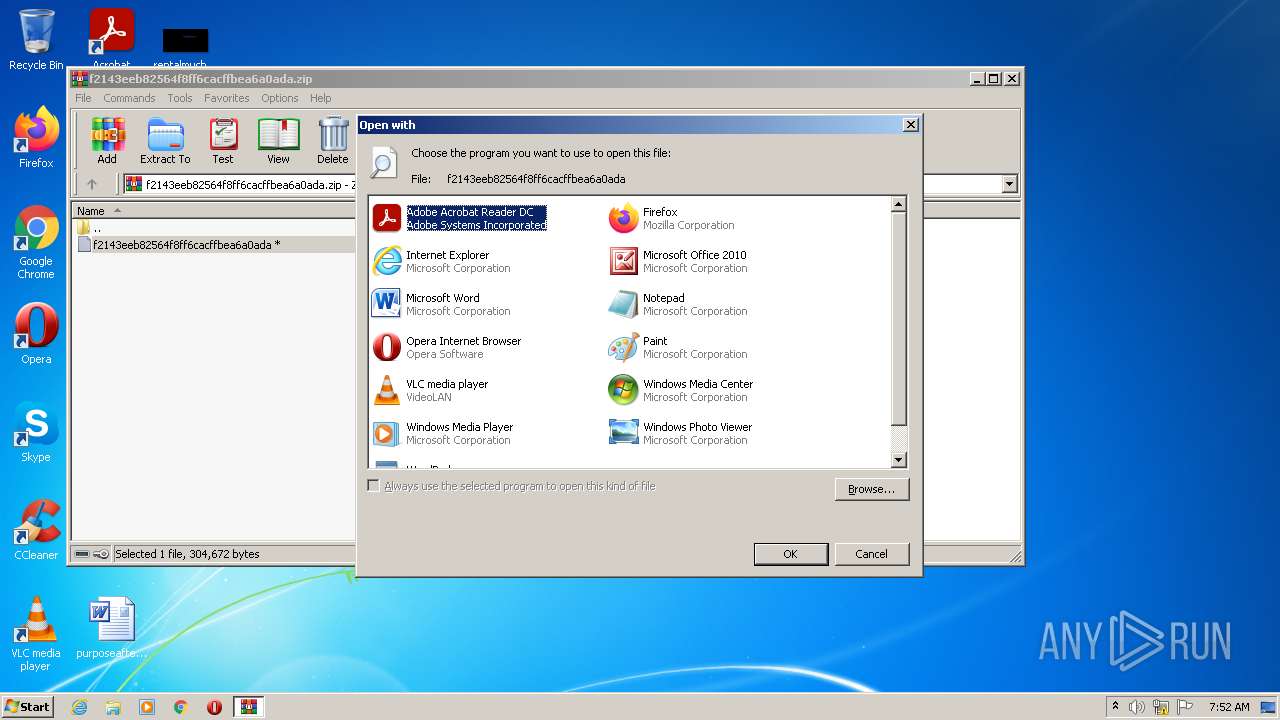
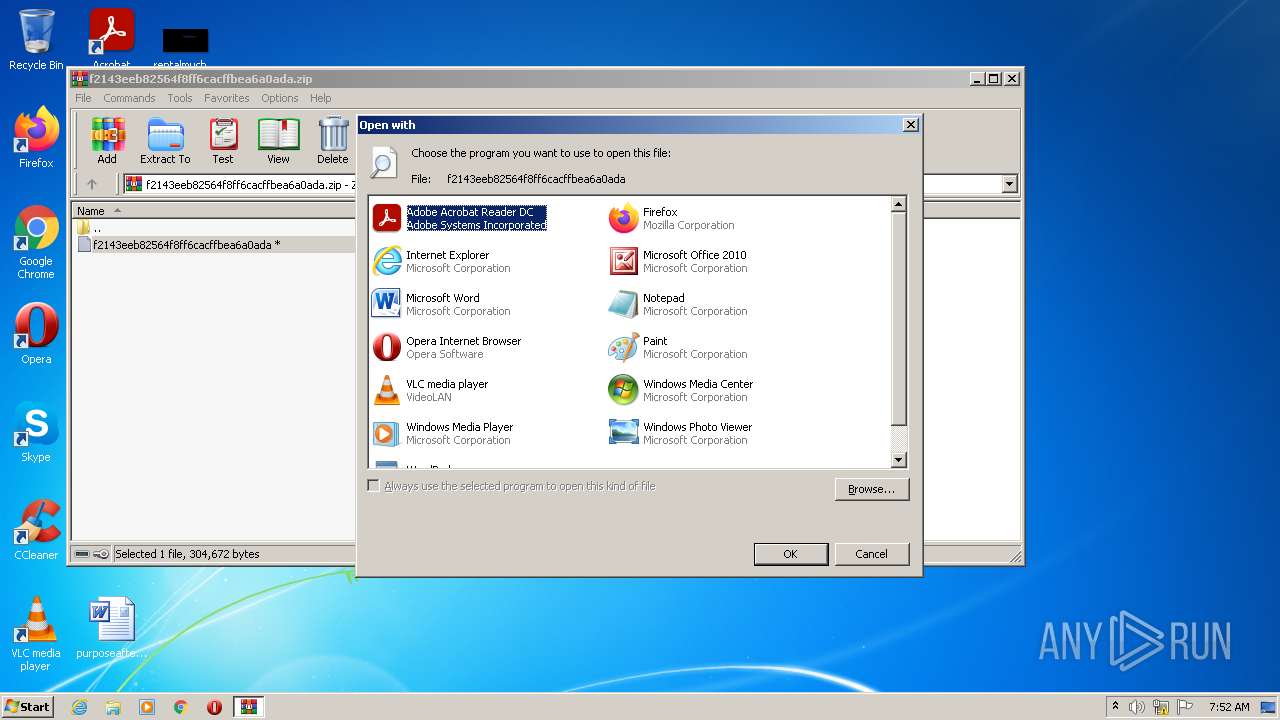
Uses RUNDLL32.EXE to load library
- WinRAR.exe (PID: 2952)
Starts Microsoft Office Application
- rundll32.exe (PID: 1372)
- rundll32.exe (PID: 2320)
Reads default file associations for system extensions
- rundll32.exe (PID: 2320)
Reads the date of Windows installation
- rundll32.exe (PID: 2320)
- rundll32.exe (PID: 1372)
Checks supported languages
- WinRAR.exe (PID: 2952)
INFO
Manual execution by user
- explorer.exe (PID: 4080)
Checks supported languages
- ntvdm.exe (PID: 2552)
- explorer.exe (PID: 4080)
- WINWORD.EXE (PID: 2748)
- EXCEL.EXE (PID: 2504)
- ntvdm.exe (PID: 3456)
- rundll32.exe (PID: 2320)
- rundll32.exe (PID: 2692)
- ntvdm.exe (PID: 2504)
- rundll32.exe (PID: 1372)
Reads the computer name
- explorer.exe (PID: 4080)
- rundll32.exe (PID: 1372)
- WINWORD.EXE (PID: 2748)
- EXCEL.EXE (PID: 2504)
- rundll32.exe (PID: 2320)
- rundll32.exe (PID: 2692)
Changes default file association
- rundll32.exe (PID: 2320)
Creates files in the user directory
- WINWORD.EXE (PID: 2748)
Reads Microsoft Office registry keys
- WINWORD.EXE (PID: 2748)
- EXCEL.EXE (PID: 2504)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipFileName: | f2143eeb82564f8ff6cacffbea6a0ada |
|---|---|
| ZipUncompressedSize: | 304672 |
| ZipCompressedSize: | 304734 |
| ZipCRC: | 0xca7d6413 |
| ZipModifyDate: | 2022:05:21 08:44:16 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0009 |
| ZipRequiredVersion: | 20 |
Total processes
50
Monitored processes
10
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
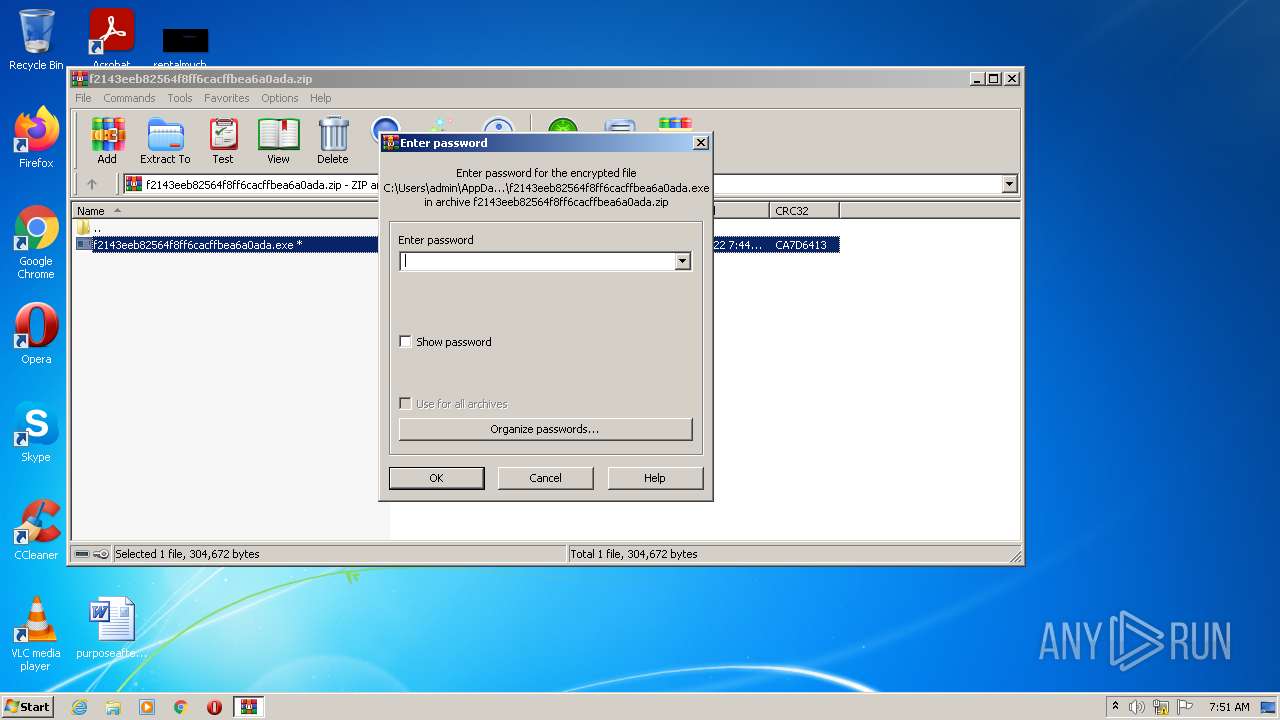
| 1372 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb2952.8922\f2143eeb82564f8ff6cacffbea6a0ada | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2320 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb2952.10856\f2143eeb82564f8ff6cacffbea6a0ada | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2504 | "C:\Windows\system32\ntvdm.exe" -i2 | C:\Windows\system32\ntvdm.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
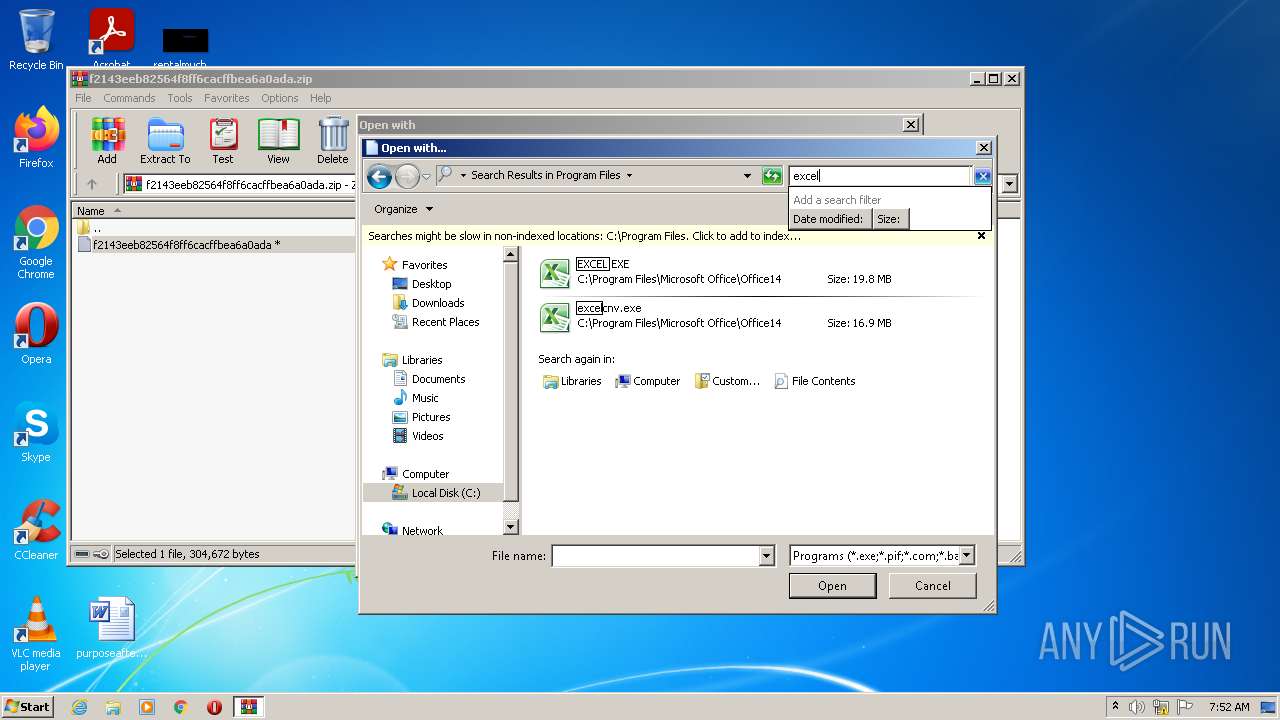
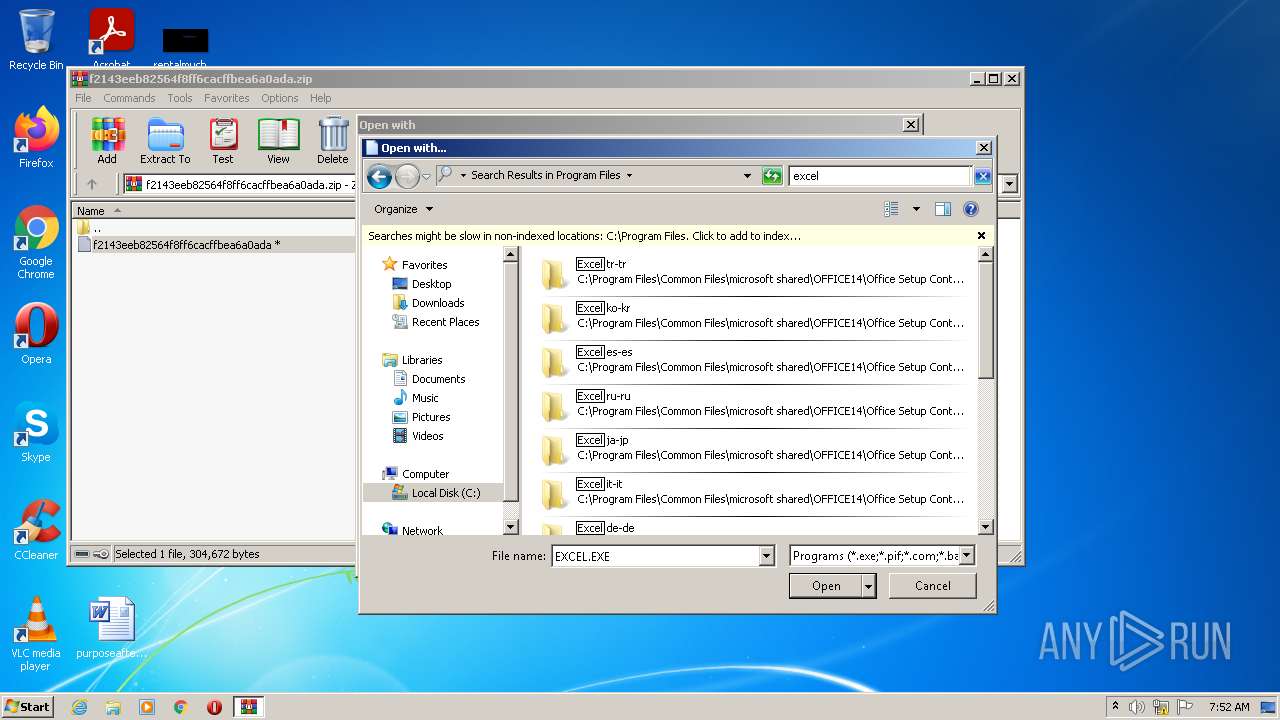
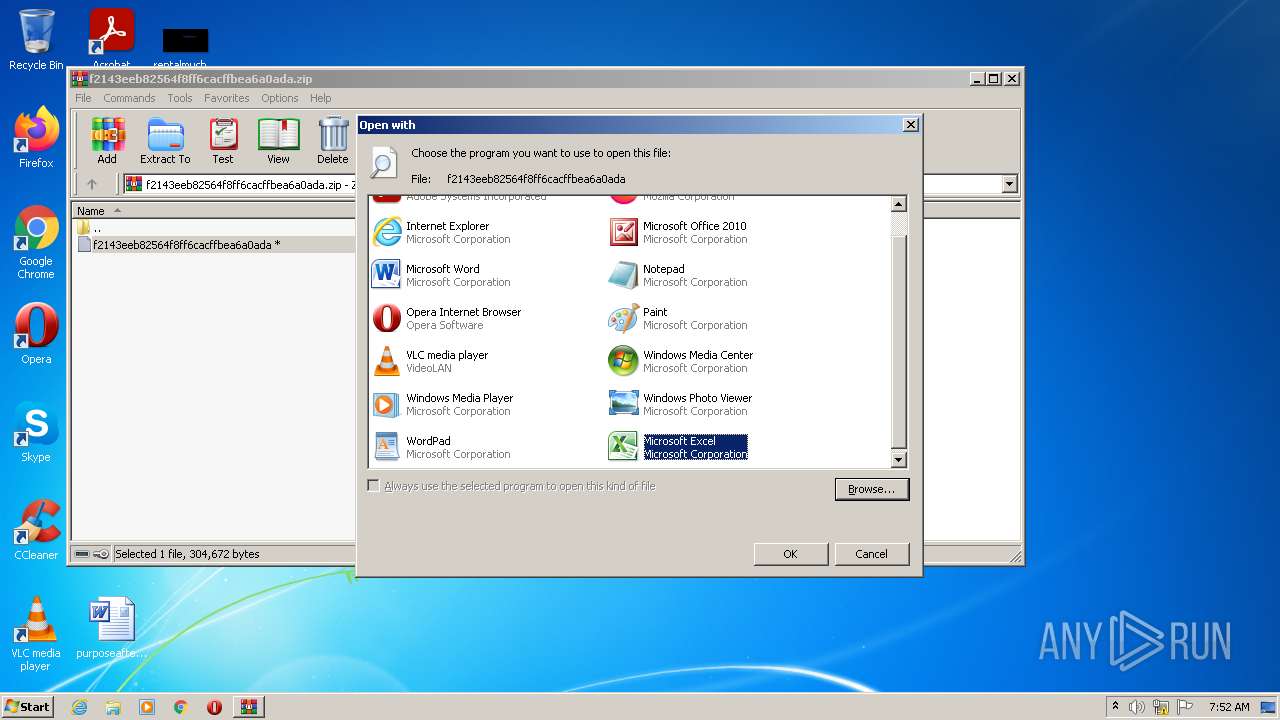
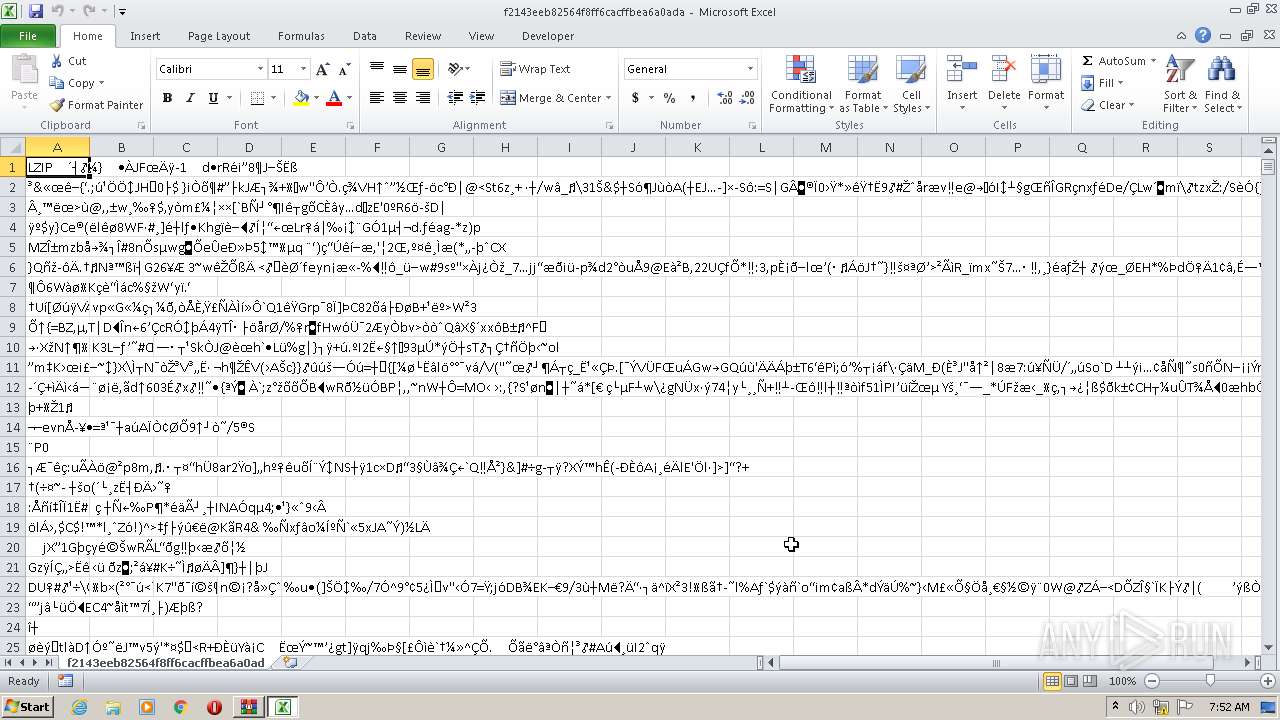
| 2504 | "C:\Program Files\Microsoft Office\Office14\EXCEL.EXE" "C:\Users\admin\AppData\Local\Temp\Rar$DIb2952.10856\f2143eeb82564f8ff6cacffbea6a0ada" | C:\Program Files\Microsoft Office\Office14\EXCEL.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Excel Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 2552 | "C:\Windows\system32\ntvdm.exe" -i1 | C:\Windows\system32\ntvdm.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2692 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\Rar$DIb2952.49639\f2143eeb82564f8ff6cacffbea6a0ada | C:\Windows\system32\rundll32.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2748 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Rar$DIb2952.8922\f2143eeb82564f8ff6cacffbea6a0ada" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
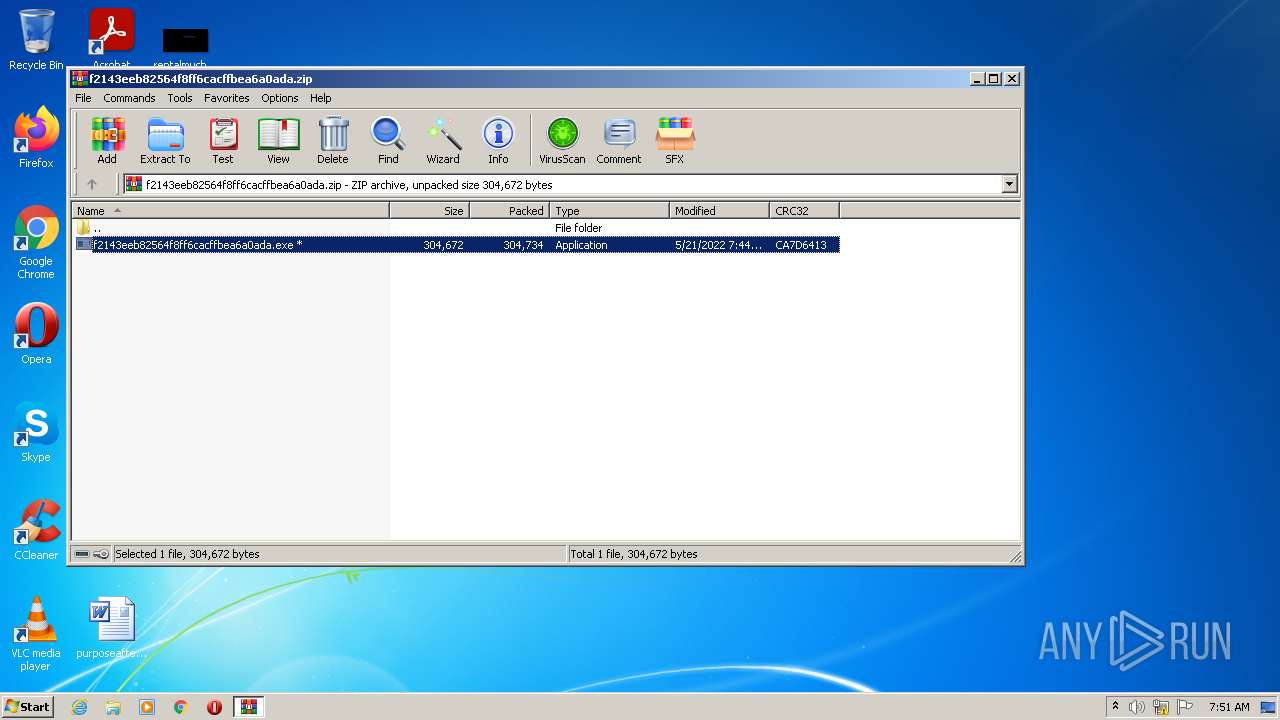
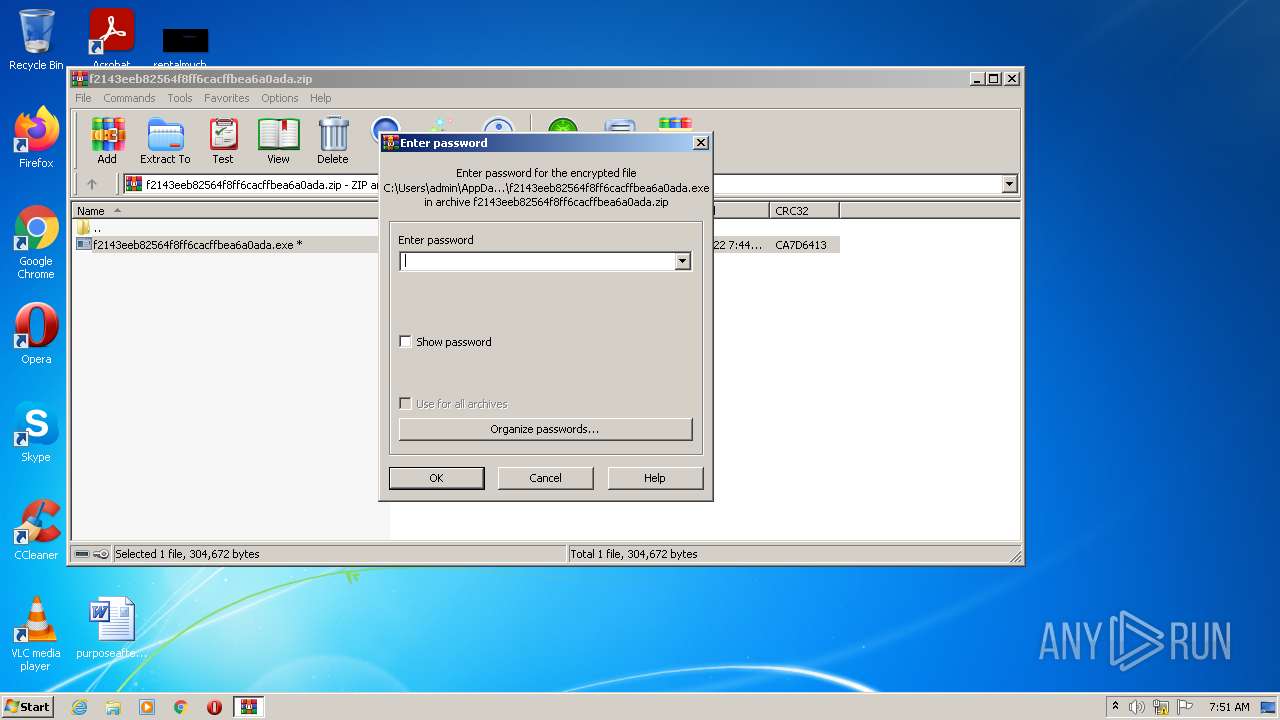
| 2952 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\f2143eeb82564f8ff6cacffbea6a0ada.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3456 | "C:\Windows\system32\ntvdm.exe" -i3 | C:\Windows\system32\ntvdm.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: NTVDM.EXE Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4080 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
13 718
Read events
13 110
Write events
458
Delete events
150
Modification events
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\f2143eeb82564f8ff6cacffbea6a0ada.zip | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2952) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
16
Text files
6
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR8F1E.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\f2143eeb82564f8ff6cacffbea6a0ada.zip | compressed | |
MD5:— | SHA256:— | |||
| 2504 | EXCEL.EXE | C:\Users\admin\AppData\Local\Temp\CVR9FB.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb2952.8922\f2143eeb82564f8ff6cacffbea6a0ada | compressed | |
MD5:— | SHA256:— | |||
| 2748 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRD0000.doc | binary | |
MD5:— | SHA256:— | |||
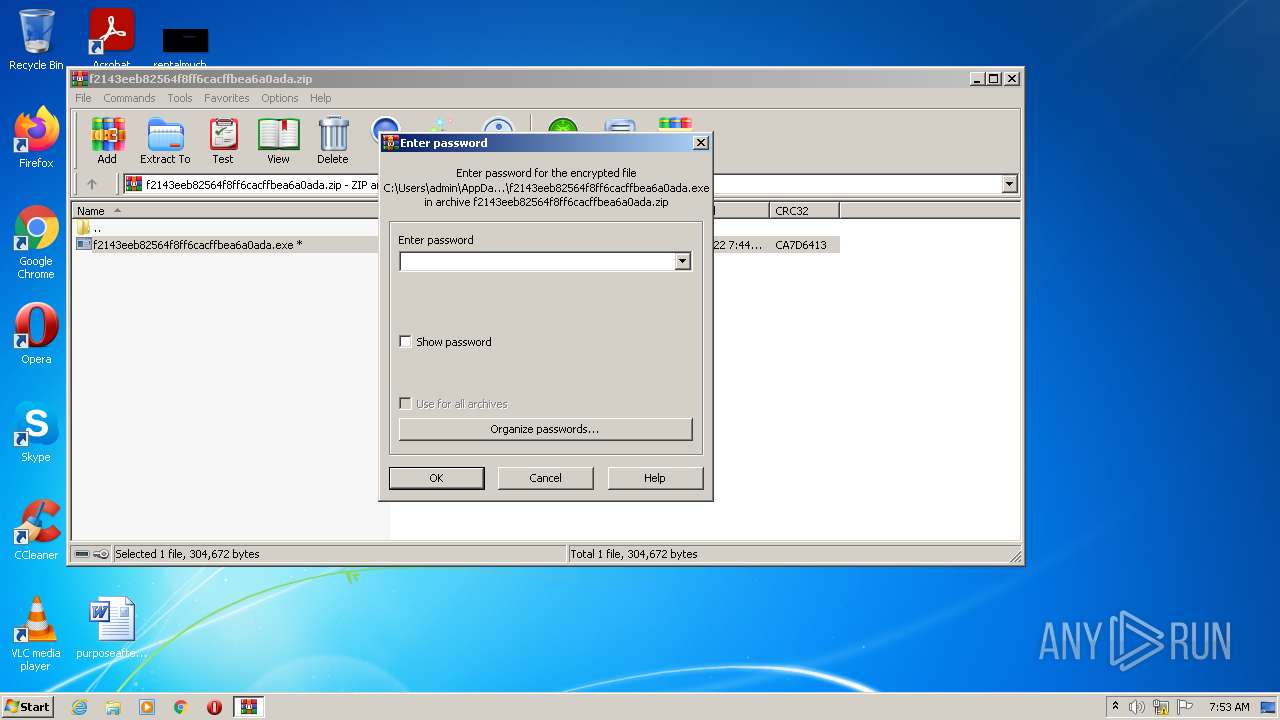
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2952.5034\f2143eeb82564f8ff6cacffbea6a0ada.exe | compressed | |
MD5:— | SHA256:— | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rzi_2952.8772 | compressed | |
MD5:— | SHA256:— | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\__rzi_2952.1931 | compressed | |
MD5:— | SHA256:— | |||
| 2748 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2952 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb2952.2128\f2143eeb82564f8ff6cacffbea6a0ada.exe | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report