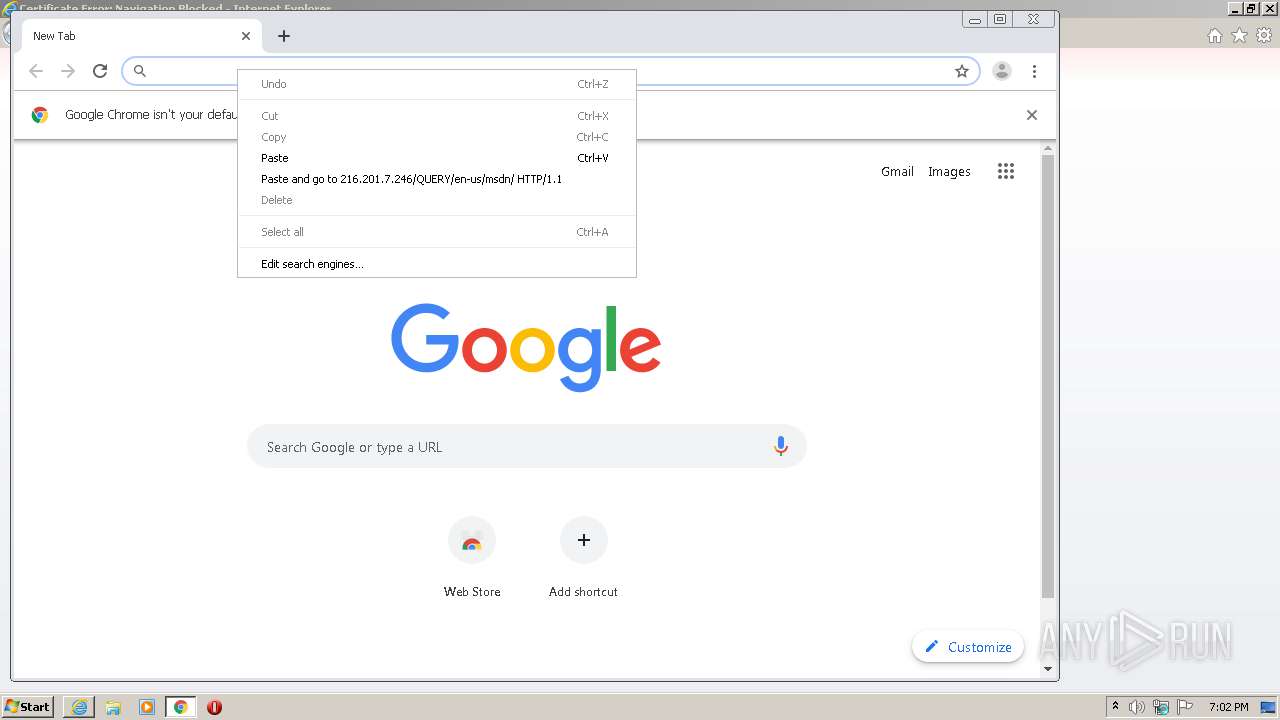
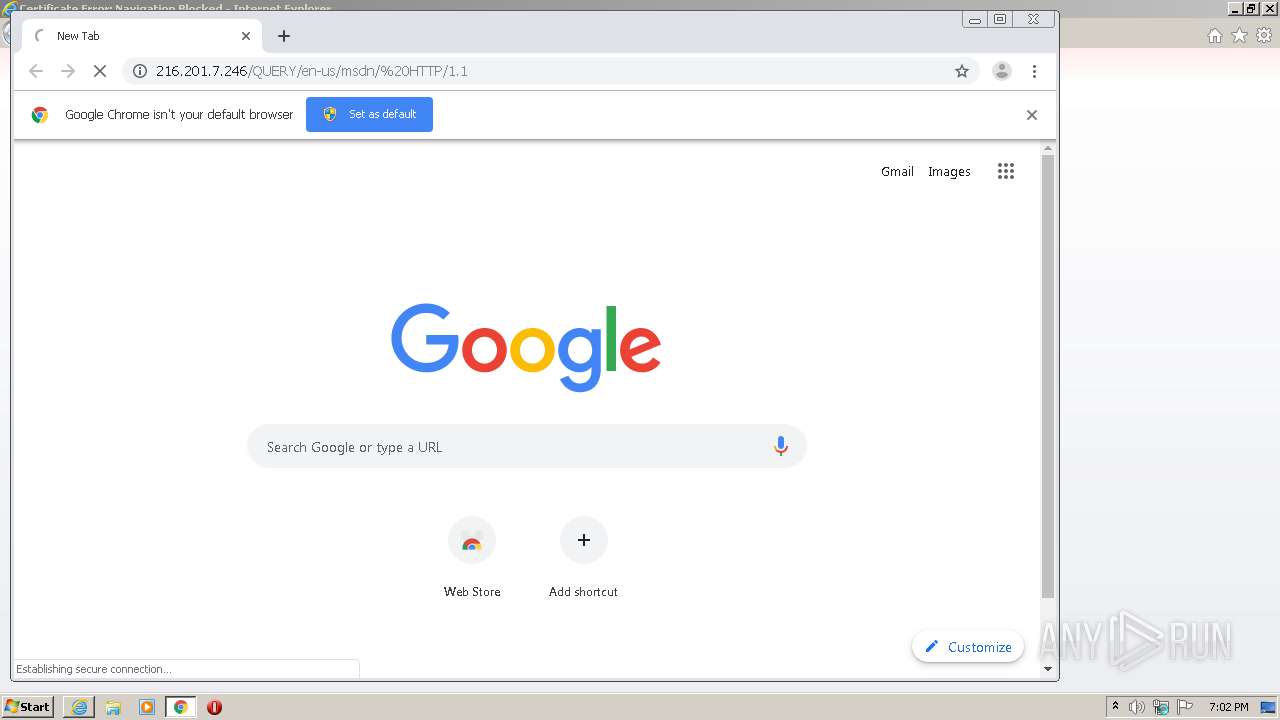
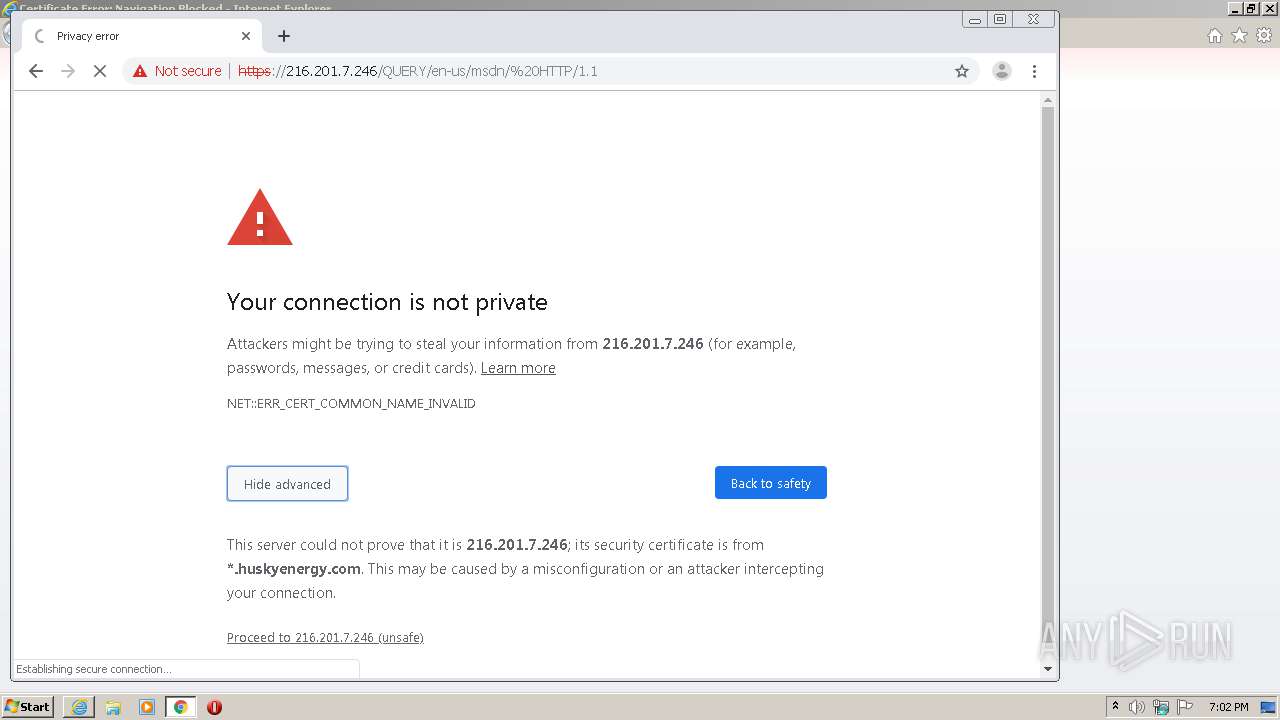
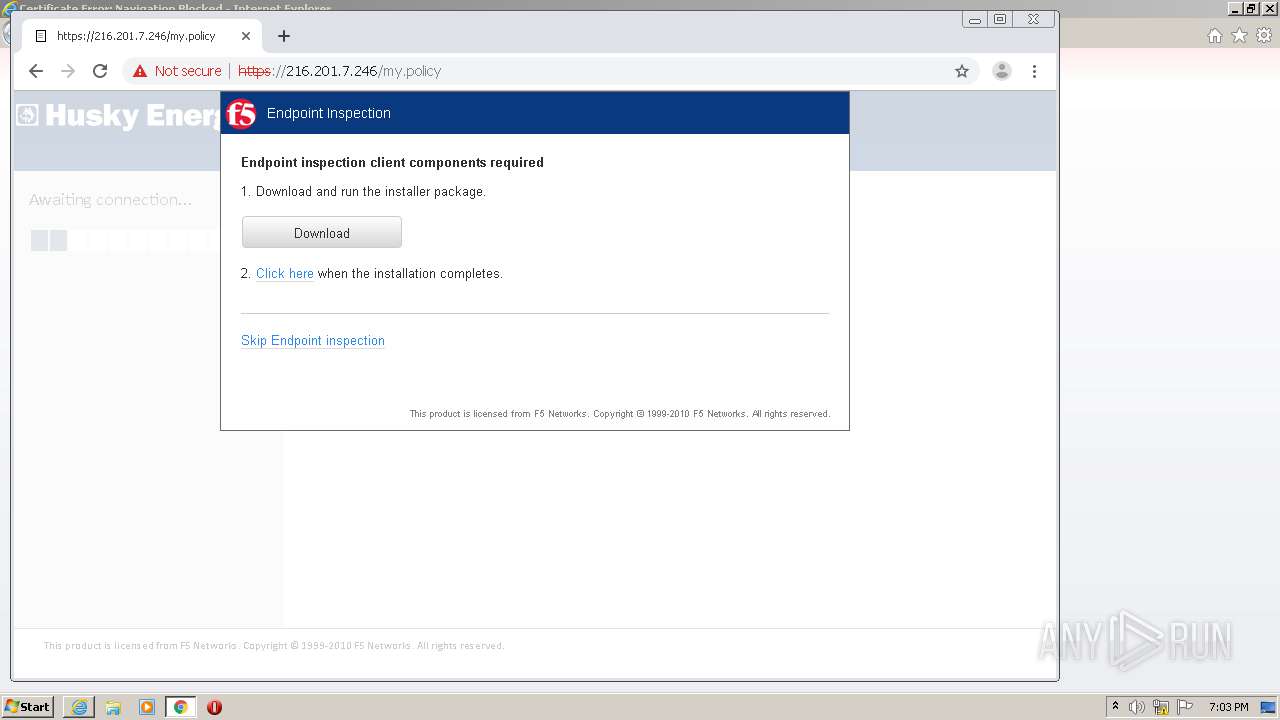
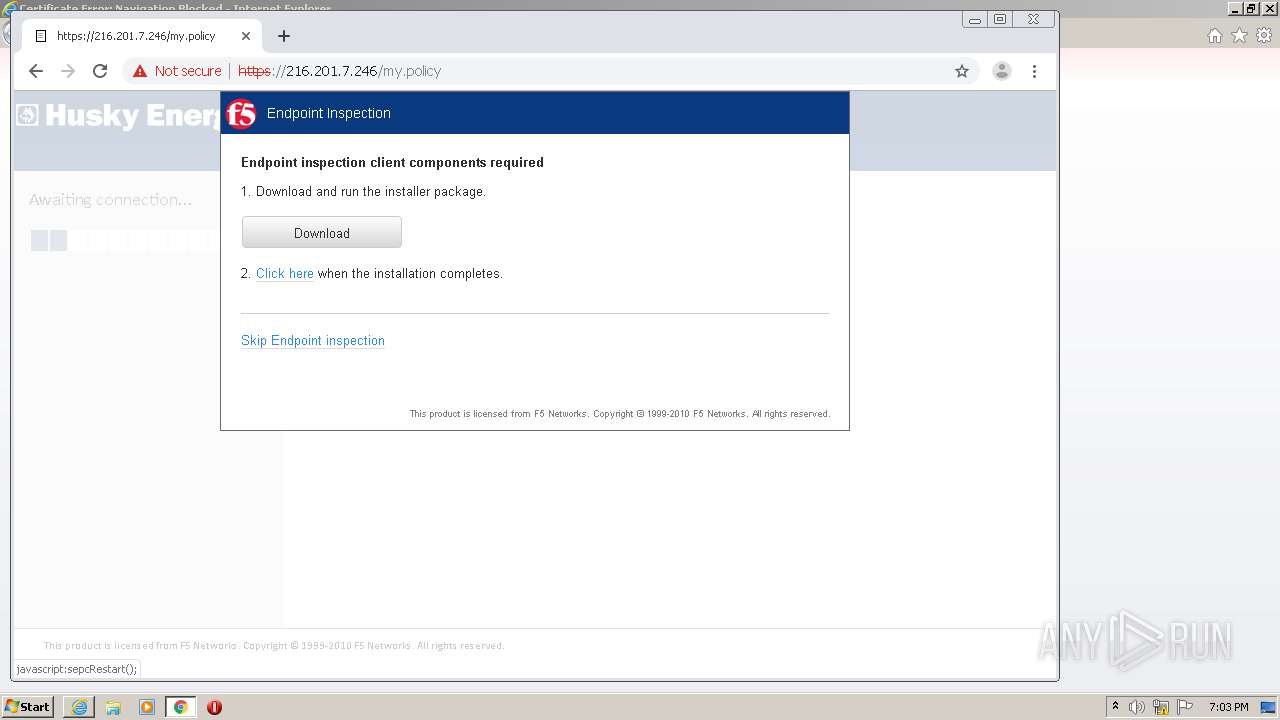
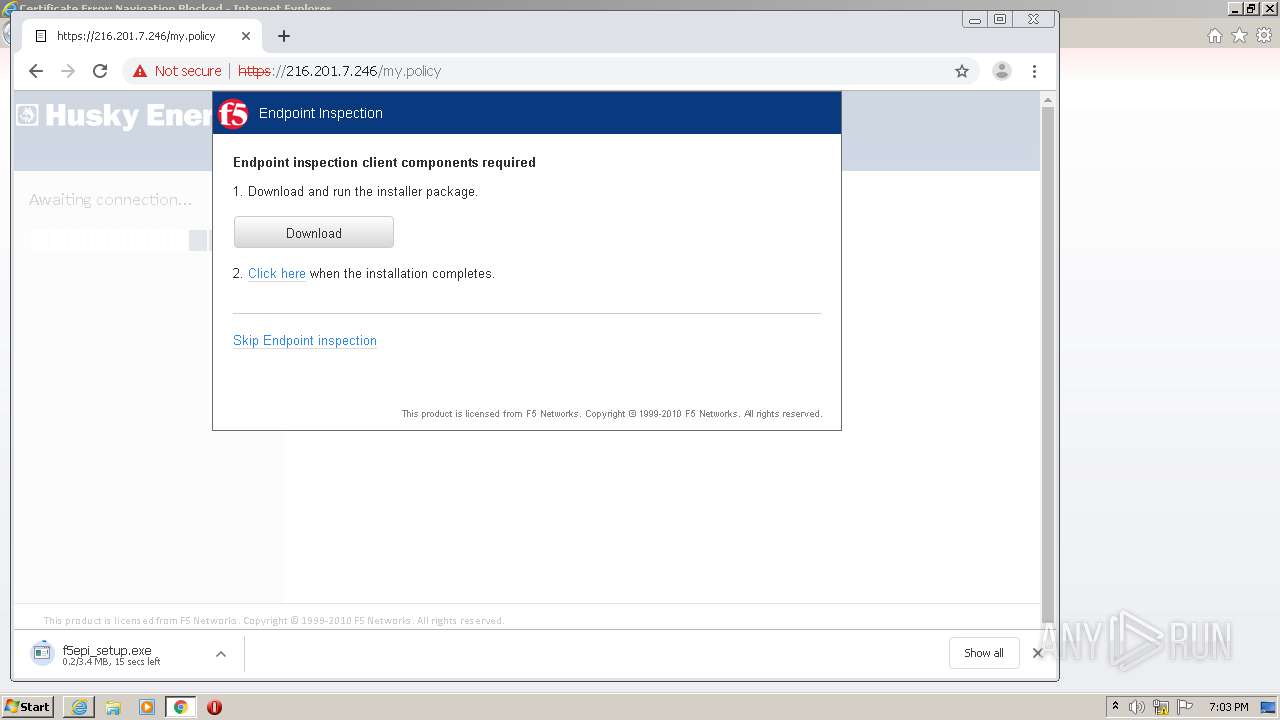
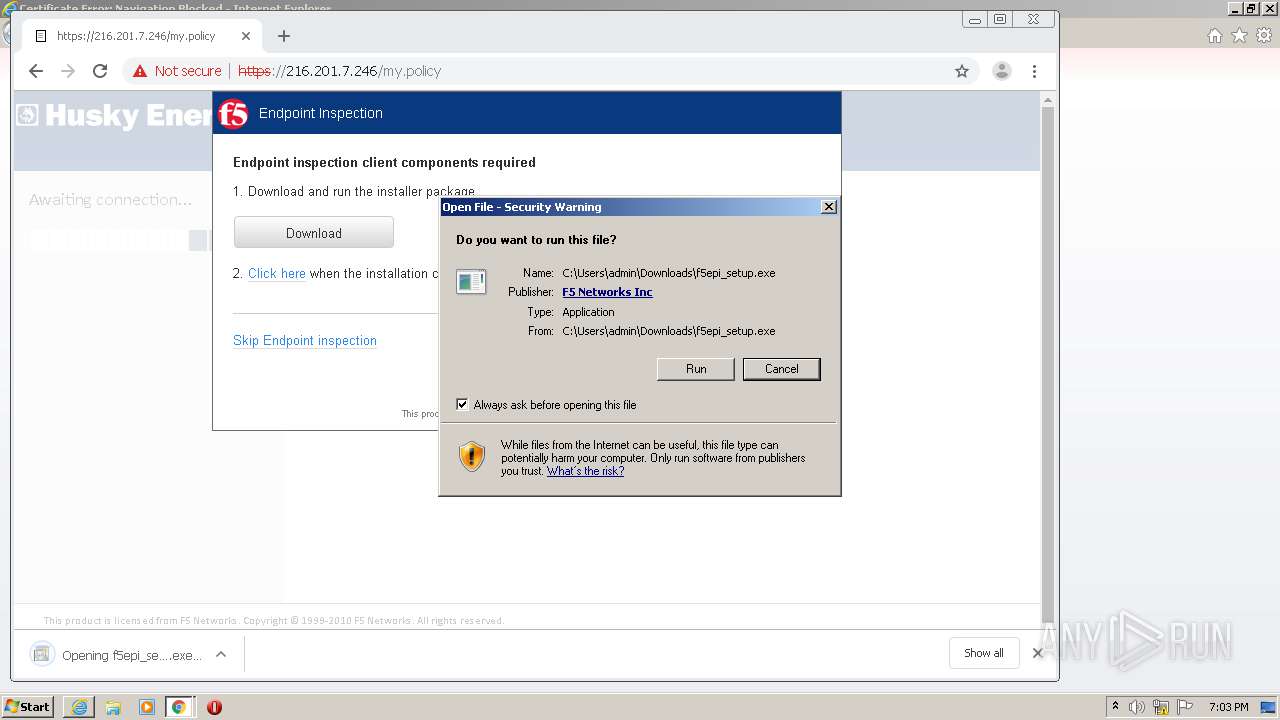
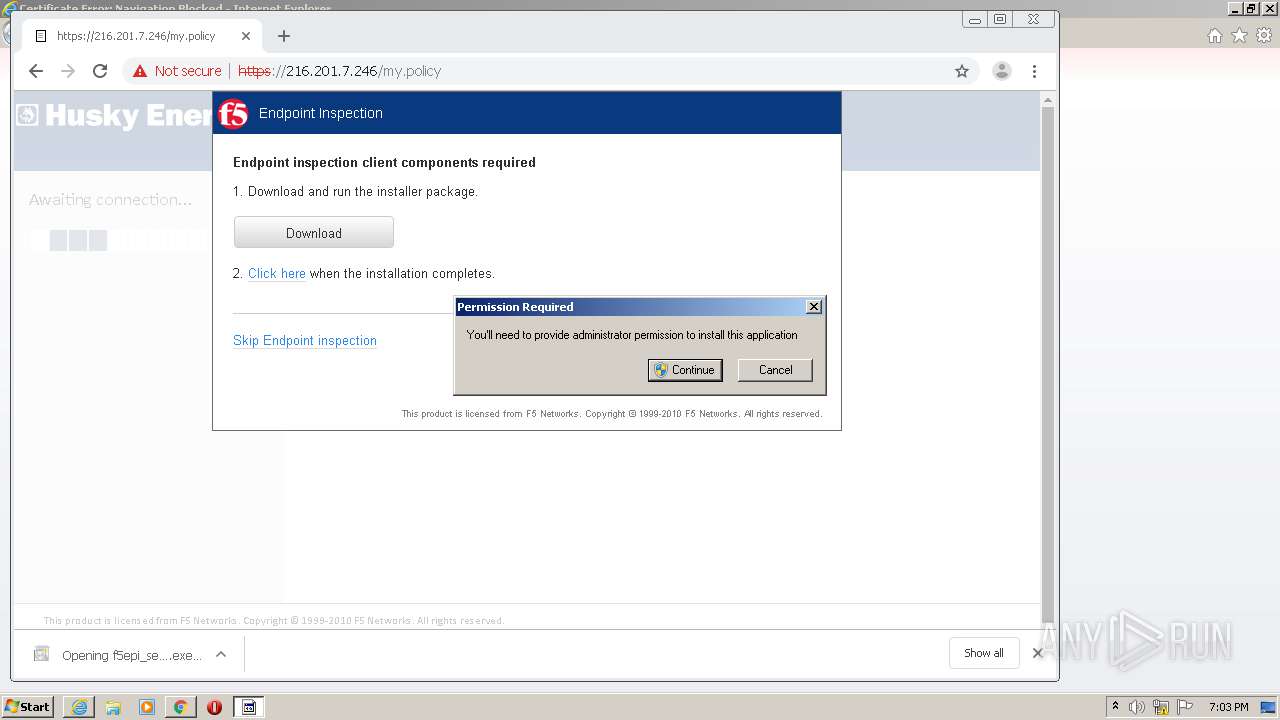
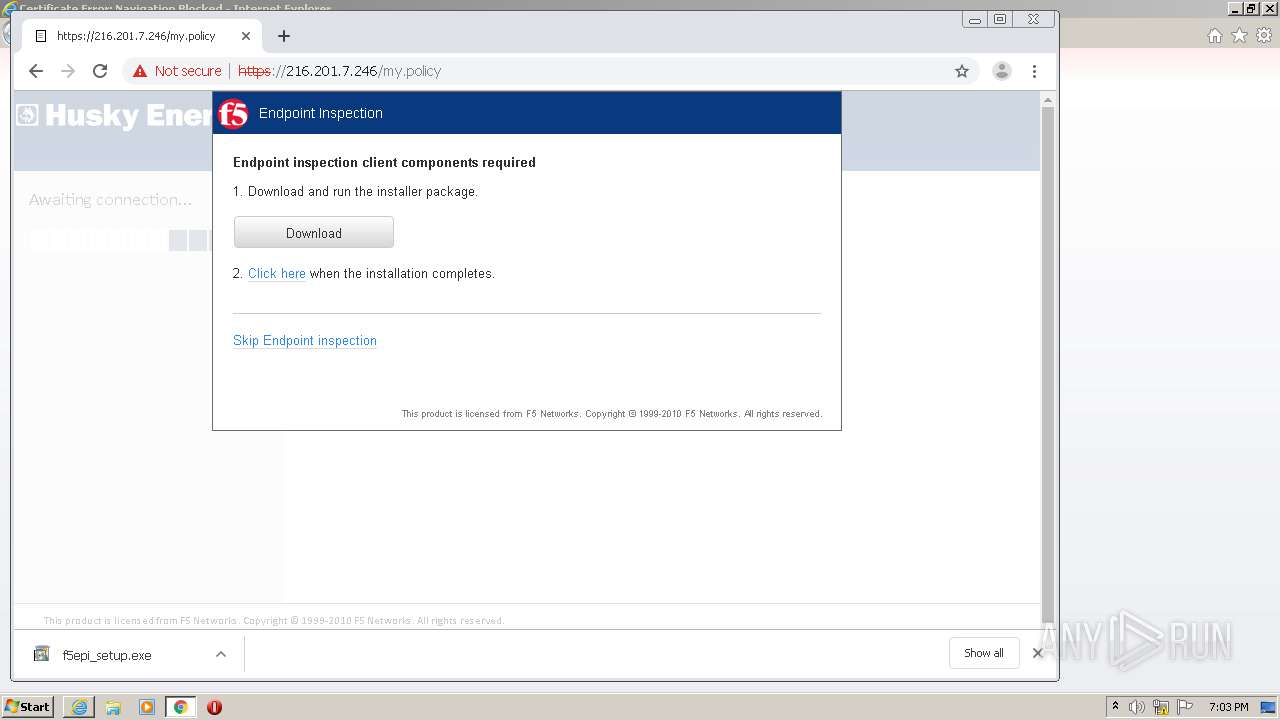
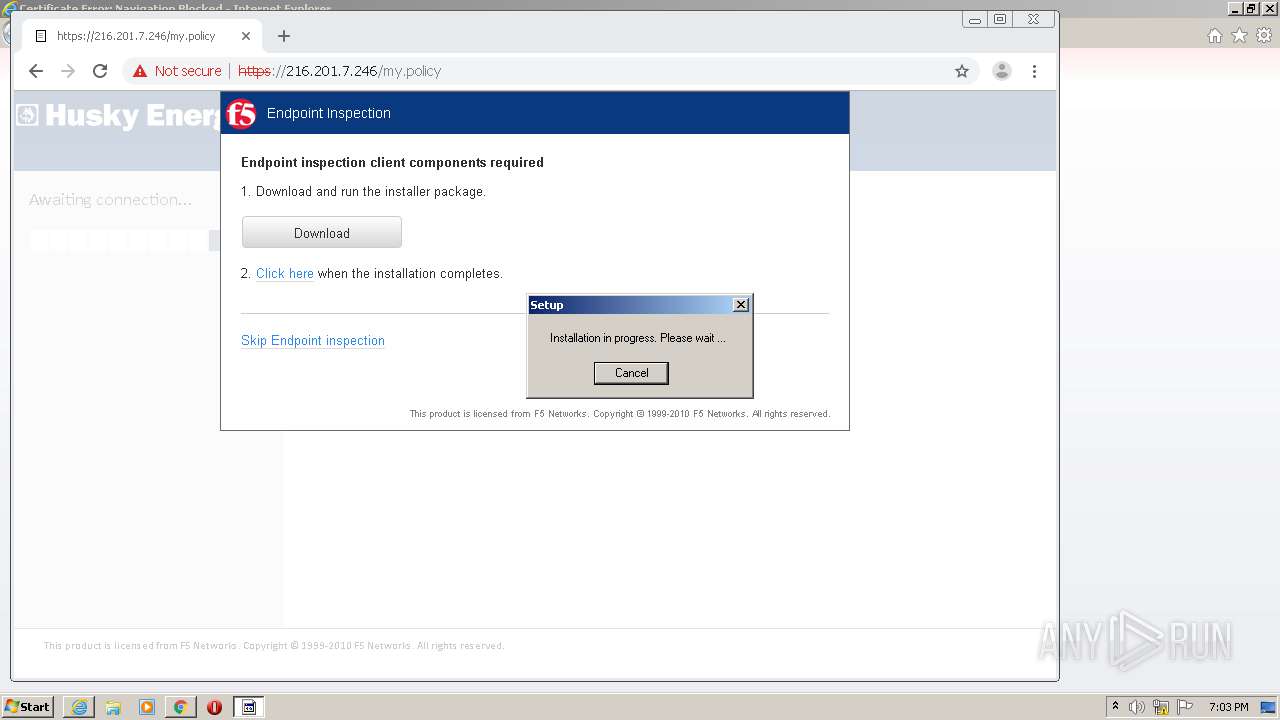
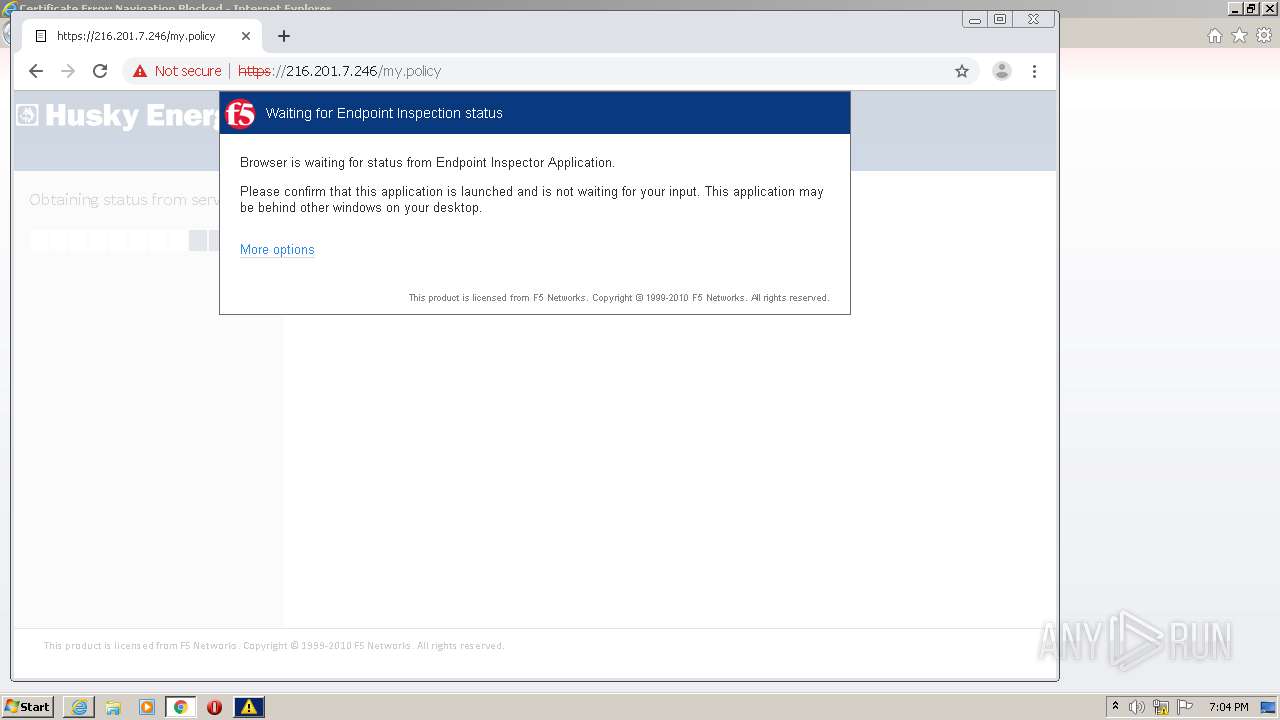
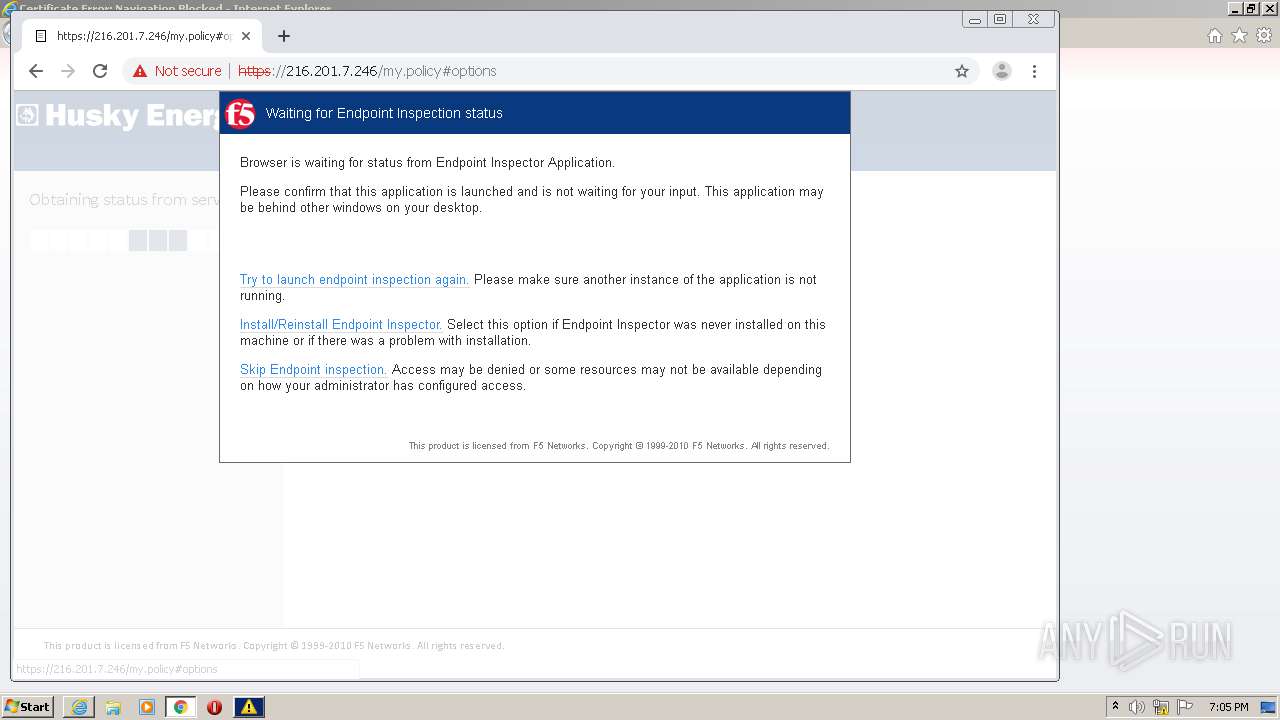
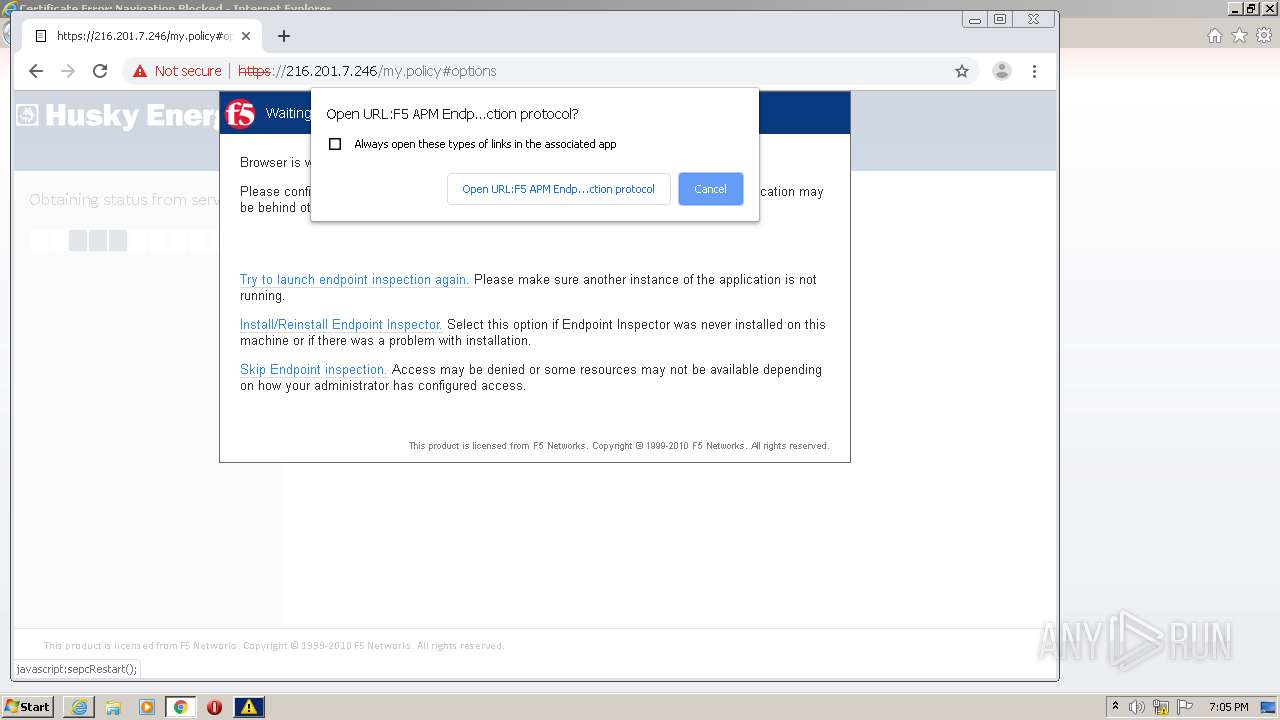
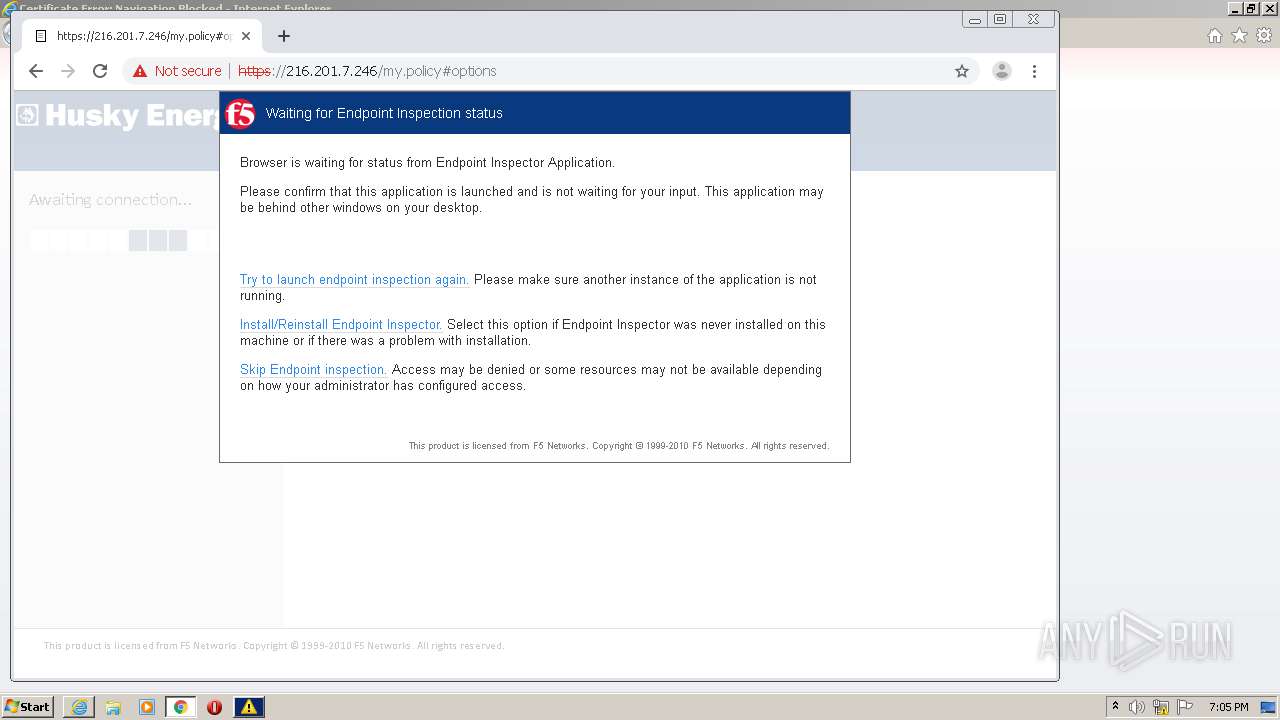
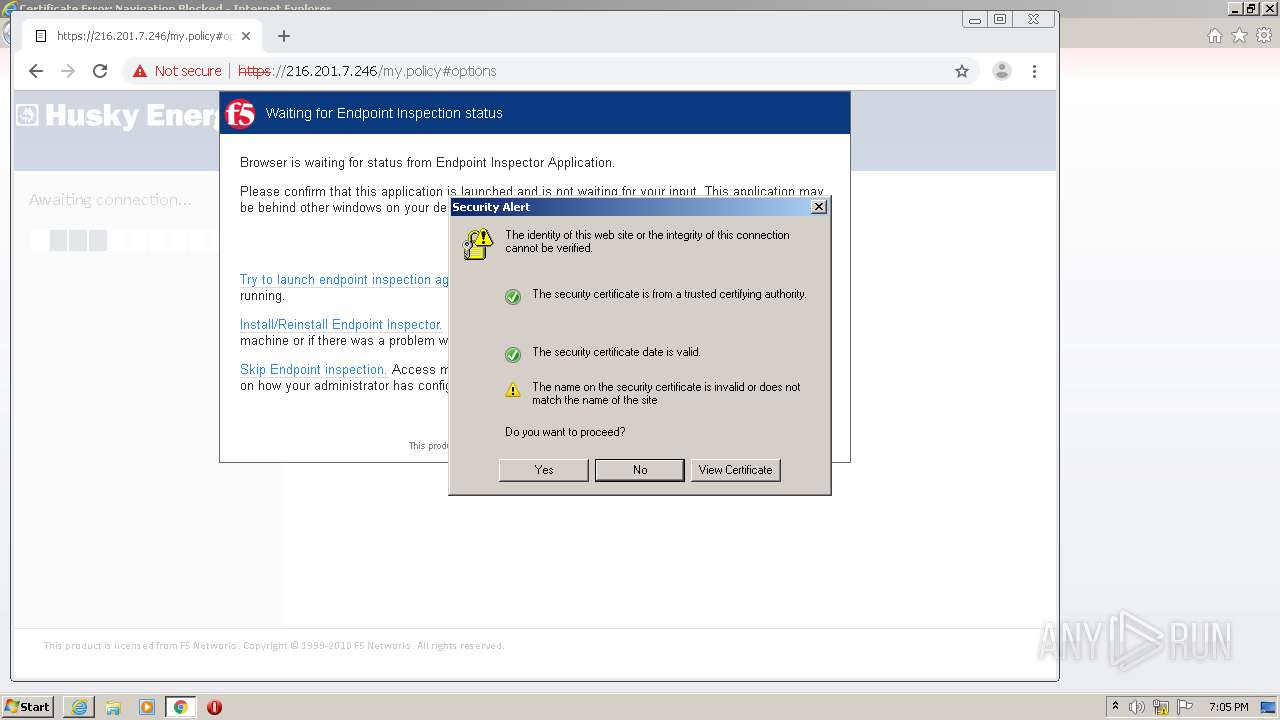
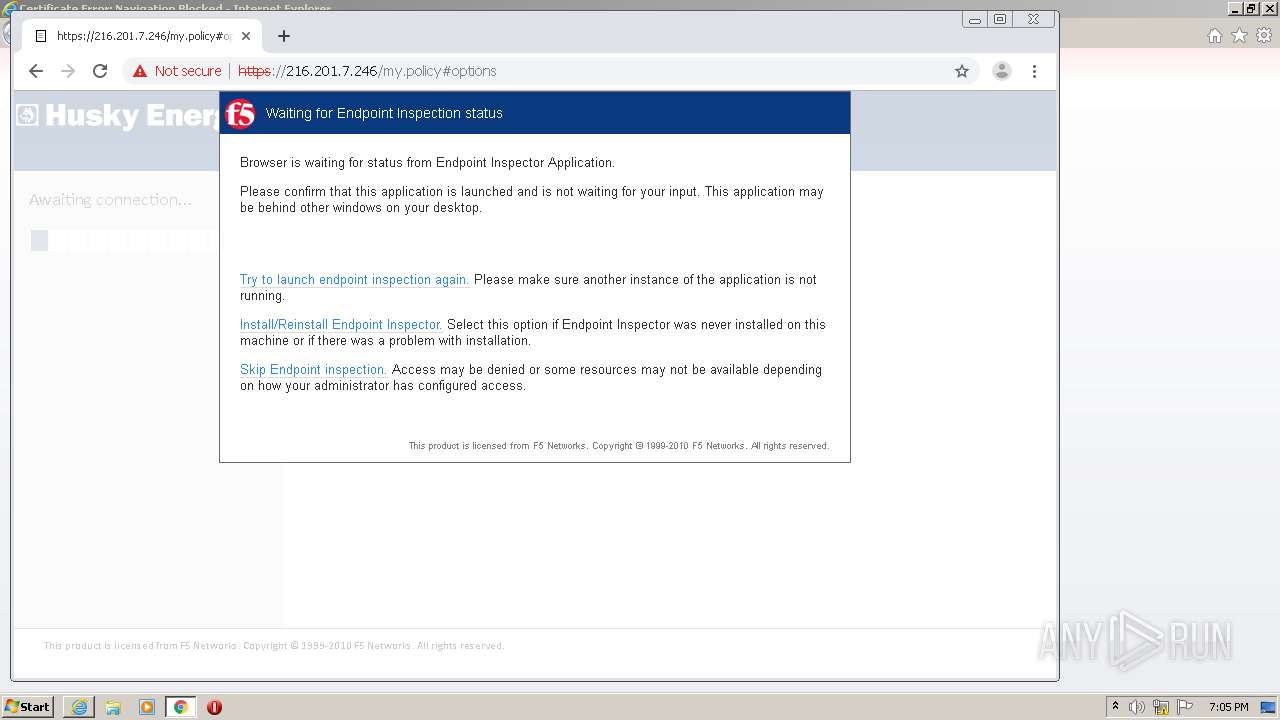
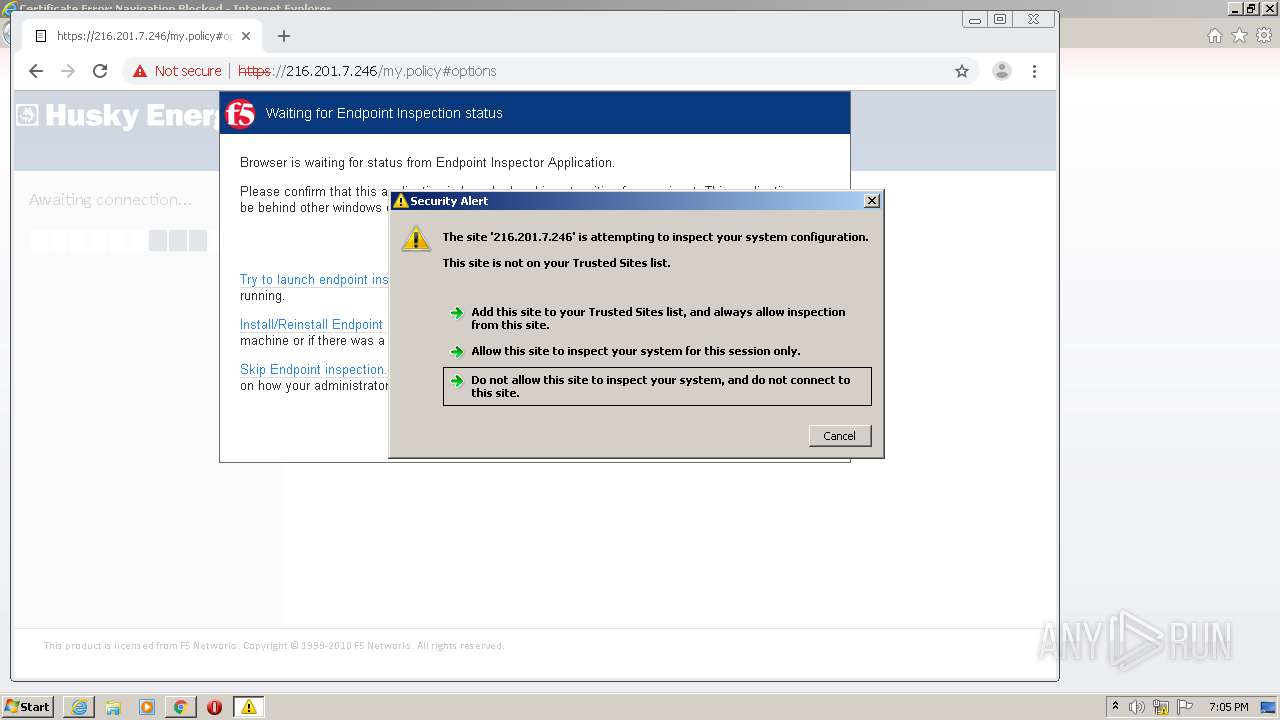
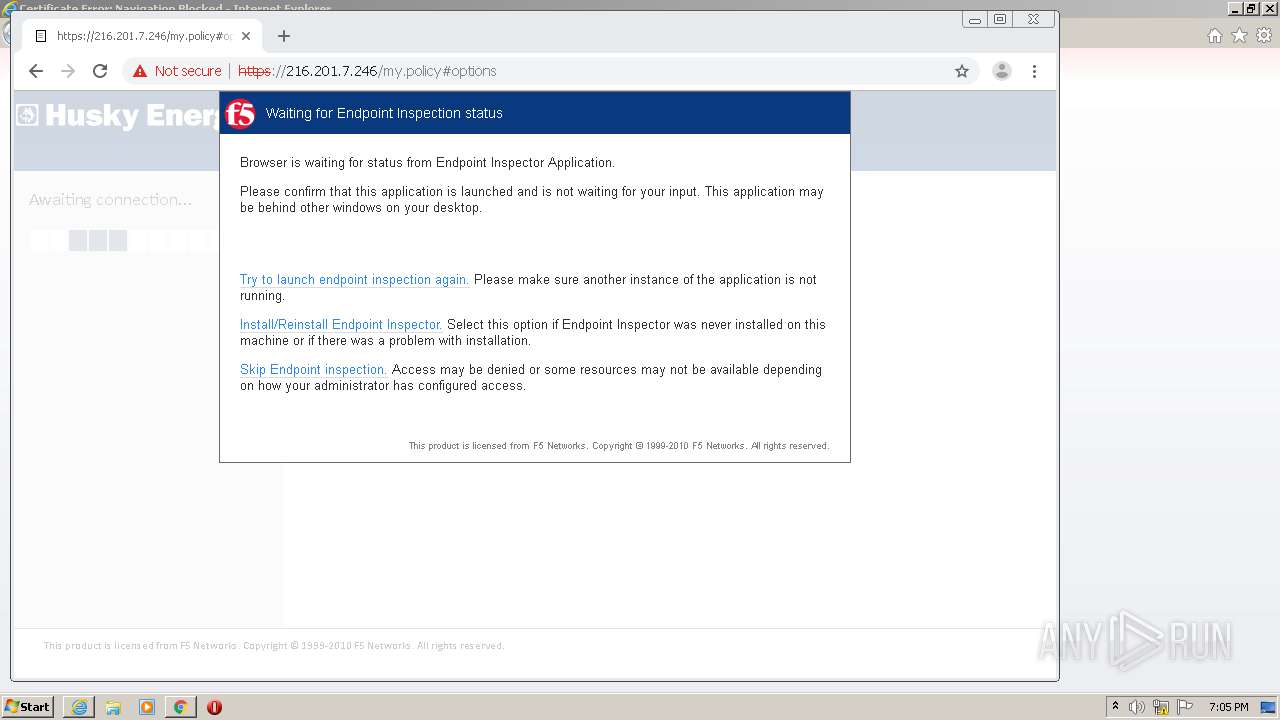
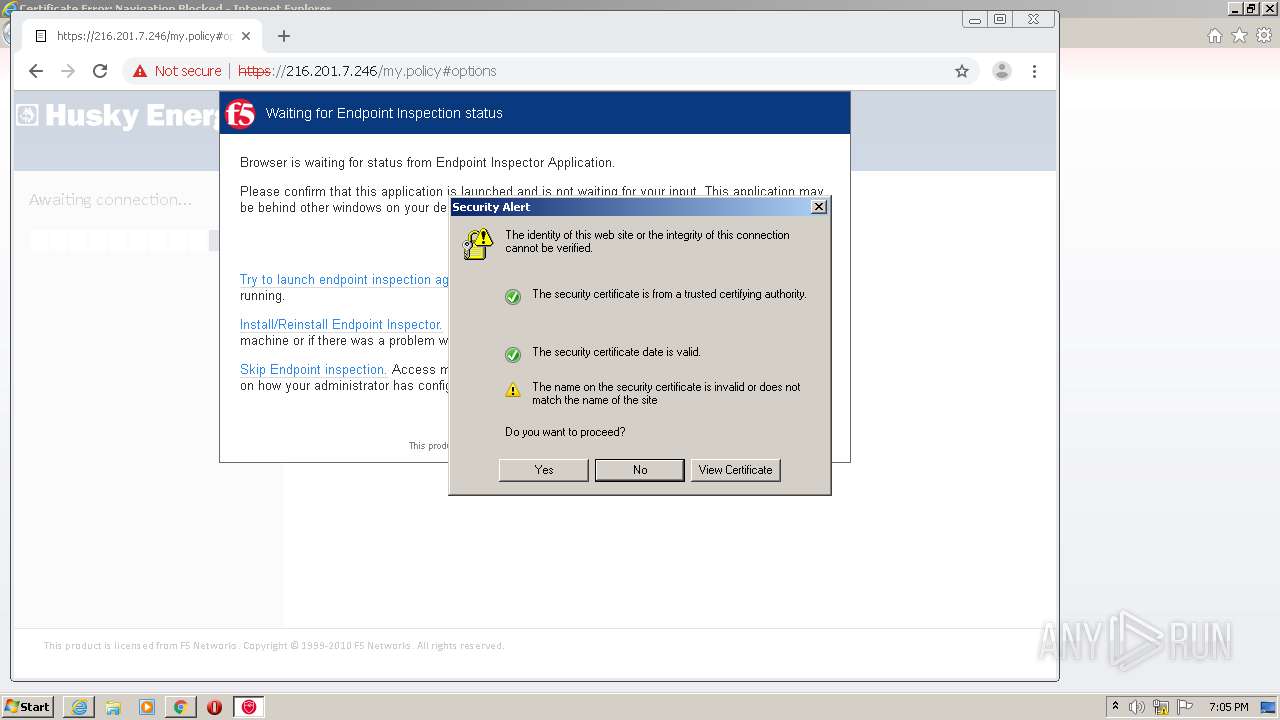
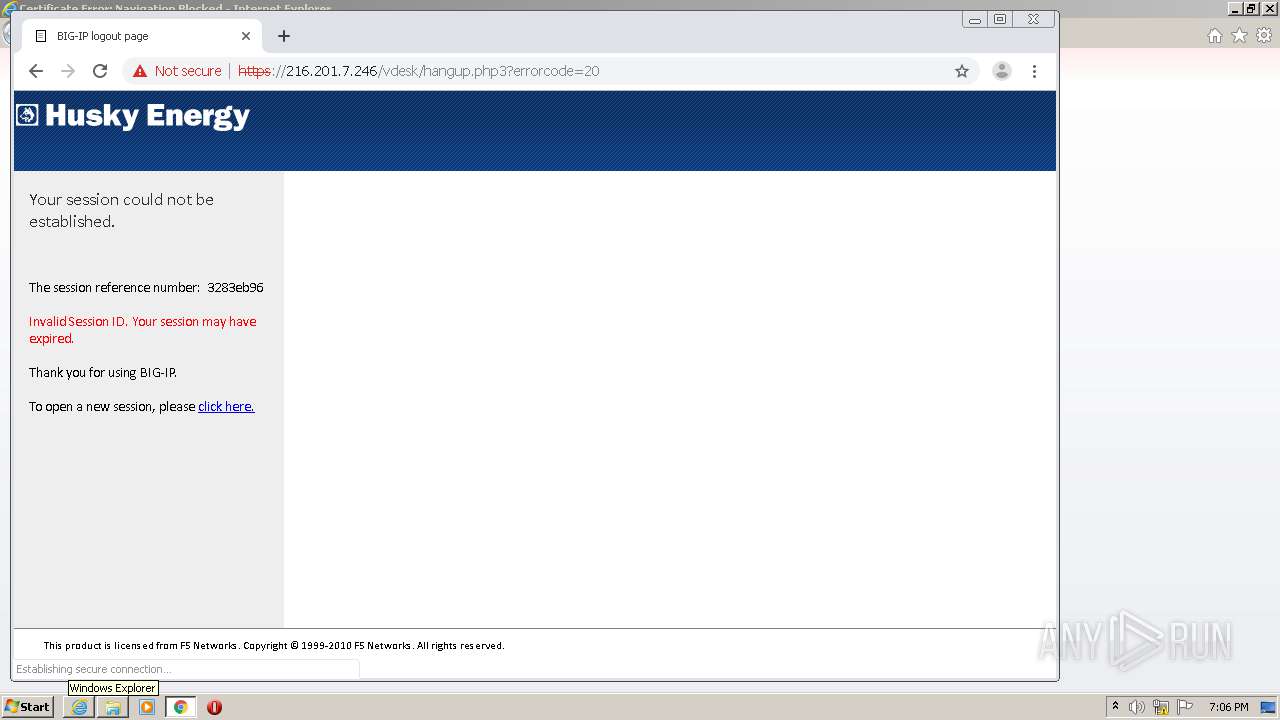
| URL: | http://216.201.7.246/QUERY/en-us/msdn/%20HTTP/1.1 |
| Full analysis: | https://app.any.run/tasks/39874049-1c64-436c-bc88-527147cfcfad |
| Verdict: | Malicious activity |
| Analysis date: | August 27, 2020, 18:01:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | A269C9B1EB0CD680551FAD9F35016615 |
| SHA1: | A69A4A90E45A71CBFA8209B0511D3E615BE5D04A |
| SHA256: | ACBB90628B6BF175D5731E2BA3DBEE96B81996B28ACB11DD2B7351FDEFC8D530 |
| SSDEEP: | 3:N1K5bhwg08DKL5Dz4:C90gK9Dk |
MALICIOUS
Application was dropped or rewritten from another process
- f5epi_setup.exe (PID: 2240)
- cabinstaller.exe (PID: 3936)
- cabinstaller.exe (PID: 2896)
- f5epi.exe (PID: 940)
- F5PolicyServer.exe (PID: 2304)
- f5unistall.exe (PID: 3232)
- F5InstH.exe (PID: 2784)
- f5epi.exe (PID: 272)
- f5epi.exe (PID: 3872)
- f5epi.exe (PID: 3376)
- f5epi.exe (PID: 1936)
Loads dropped or rewritten executable
- cabinstaller.exe (PID: 2896)
- f5epi.exe (PID: 3872)
- f5epi.exe (PID: 1936)
Changes settings of System certificates
- cabinstaller.exe (PID: 2896)
SUSPICIOUS
Executable content was dropped or overwritten
- chrome.exe (PID: 2924)
- f5epi_setup.exe (PID: 2240)
- f5unistall.exe (PID: 3232)
- cabinstaller.exe (PID: 2896)
Application launched itself
- cabinstaller.exe (PID: 3936)
- f5epi.exe (PID: 272)
- f5epi.exe (PID: 3376)
Adds / modifies Windows certificates
- cabinstaller.exe (PID: 2896)
Creates files in the Windows directory
- cabinstaller.exe (PID: 2896)
- f5unistall.exe (PID: 3232)
Reads Internet Cache Settings
- cabinstaller.exe (PID: 2896)
- f5epi.exe (PID: 3872)
- f5epi.exe (PID: 1936)
Creates COM task schedule object
- cabinstaller.exe (PID: 2896)
- F5InstH.exe (PID: 2784)
Modifies the open verb of a shell class
- f5epi.exe (PID: 940)
Creates files in the program directory
- f5unistall.exe (PID: 3232)
- f5epi.exe (PID: 3872)
Creates a software uninstall entry
- f5unistall.exe (PID: 3232)
Reads internet explorer settings
- f5epi.exe (PID: 1936)
INFO
Application launched itself
- iexplore.exe (PID: 2656)
- chrome.exe (PID: 2924)
Changes internet zones settings
- iexplore.exe (PID: 2656)
Reads Internet Cache Settings
- iexplore.exe (PID: 2132)
- iexplore.exe (PID: 2656)
- chrome.exe (PID: 2924)
Reads internet explorer settings
- iexplore.exe (PID: 2132)
Reads the hosts file
- chrome.exe (PID: 2924)
- chrome.exe (PID: 3192)
Reads settings of System Certificates
- iexplore.exe (PID: 2656)
- chrome.exe (PID: 3192)
- chrome.exe (PID: 2924)
Manual execution by user
- chrome.exe (PID: 2924)
Changes settings of System certificates
- iexplore.exe (PID: 2656)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2656)
Creates files in the user directory
- iexplore.exe (PID: 2656)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
82
Monitored processes
39
Malicious processes
8
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 272 | "C:\Windows\Downloaded Program Files\f5epi.exe" "f5-epi://216.201.7.246/?server=216.201.7.246&version0=7183,2020,108,2059&id0=%7B45B69029-F3AB-4204-92DE-D5140C3E8E74%7D&package0=/public/download/InstallerControl.cab&version1=7120,2015,1230,1&id1=Service:F5+Networks+Component+Installer&package1=/public/download/2015/InstallerService.cab&version2=7183,2020,108,2059&id2=Service:F5+Networks+Component+Installer&package2=/public/download/InstallerService.cab&version3=7183,2020,108,2059&id3=%7B57C76689-F052-487B-A19F-855AFDDF28EE%7D&package3=/public/download/f5InspectionHost.cab&version4=7183,2020,108,2059&id4=Service:MachineCertService&package4=/public/download/MachineCertService.cab&version5=7183,2020,108,2059&id5=Service:F5InspectorService&package5=/public/download/f5is.cab&protocol=https&port=443&sid=b76cb7ea5b38bca30b5818d33283eb96" | C:\Windows\Downloaded Program Files\f5epi.exe | — | chrome.exe | |||||||||||
User: admin Company: F5 Networks, Inc. Integrity Level: MEDIUM Description: F5 Networks Endpoint Inspector Exit code: 0 Version: 7183, 2020, 0108, 2059 Modules
| |||||||||||||||
| 940 | "C:\Windows\Downloaded Program Files\f5epi.exe" /RegServer | C:\Windows\Downloaded Program Files\f5epi.exe | — | cabinstaller.exe | |||||||||||
User: admin Company: F5 Networks, Inc. Integrity Level: HIGH Description: F5 Networks Endpoint Inspector Exit code: 0 Version: 7183, 2020, 0108, 2059 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1052,13863317411026134772,387760503784772141,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=1390358591438272865 --mojo-platform-channel-handle=2804 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1000 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1052,13863317411026134772,387760503784772141,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=11024889868596520203 --mojo-platform-channel-handle=3020 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1664 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,13863317411026134772,387760503784772141,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15135738344205919553 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2268 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1708 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,13863317411026134772,387760503784772141,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=1947971788114974760 --renderer-client-id=25 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3132 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1720 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1052,13863317411026134772,387760503784772141,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=5289568253037006470 --mojo-platform-channel-handle=3328 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1936 | "C:\Windows\Downloaded Program Files\f5epi.exe" | C:\Windows\Downloaded Program Files\f5epi.exe | f5epi.exe | ||||||||||||
User: admin Company: F5 Networks, Inc. Integrity Level: MEDIUM Description: F5 Networks Endpoint Inspector Exit code: 0 Version: 7183, 2020, 0108, 2059 Modules
| |||||||||||||||
| 2044 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1052,13863317411026134772,387760503784772141,131072 --enable-features=PasswordImport --lang=en-US --extension-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=15207029756215189781 --renderer-client-id=4 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2484 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2128 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1052,13863317411026134772,387760503784772141,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=4087487507304496822 --mojo-platform-channel-handle=2468 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 233
Read events
1 763
Write events
459
Delete events
11
Modification events
| (PID) Process: | (2656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 746319280 | |||
| (PID) Process: | (2656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30833820 | |||
| (PID) Process: | (2656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (2656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 46000000A3000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (2656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2656) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
Executable files
27
Suspicious files
62
Text files
137
Unknown types
13
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2132 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab4116.tmp | — | |
MD5:— | SHA256:— | |||
| 2132 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar4117.tmp | — | |
MD5:— | SHA256:— | |||
| 2656 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | — | |
MD5:— | SHA256:— | |||
| 2132 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | der | |
MD5:— | SHA256:— | |||
| 2132 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\invalidcert[1] | html | |
MD5:— | SHA256:— | |||
| 2132 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\YTOWV792\errorPageStrings[2] | text | |
MD5:— | SHA256:— | |||
| 2132 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\1E11E75149C17A93653DA7DC0B8CF53F_DE4A9834DA7C4F8DEE2494F4C4354858 | der | |
MD5:— | SHA256:— | |||
| 2132 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\7423F88C7F265F0DEFC08EA88C3BDE45_D975BBA8033175C8D112023D8A7A8AD6 | binary | |
MD5:— | SHA256:— | |||
| 2924 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\BudgetDatabase\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2132 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\5IWPIAR9\invalidcert[1] | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
8
TCP/UDP connections
95
DNS requests
26
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3192 | chrome.exe | GET | 302 | 216.201.7.246:80 | http://216.201.7.246/QUERY/en-us/msdn/%20HTTP/1.1 | US | — | — | malicious |
2132 | iexplore.exe | GET | 302 | 216.201.7.246:80 | http://216.201.7.246/QUERY/en-us/msdn/%20HTTP/1.1 | US | — | — | malicious |
3192 | chrome.exe | GET | 302 | 216.201.7.246:80 | http://216.201.7.246/QUERY/en-us/msdn/%20HTTP/1.1 | US | — | — | malicious |
2656 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2656 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
2656 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8sEMlbBsCTf7jUSfg%2BhWk%3D | US | der | 1.47 Kb | whitelisted |
1048 | svchost.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/GTSGIAG3/MEkwRzBFMEMwQTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCCB1hFTiyruqn | US | binary | 5 b | whitelisted |
2656 | iexplore.exe | GET | 200 | 204.79.197.200:80 | http://www.bing.com/favicon.ico | US | image | 237 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3192 | chrome.exe | 172.217.21.227:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
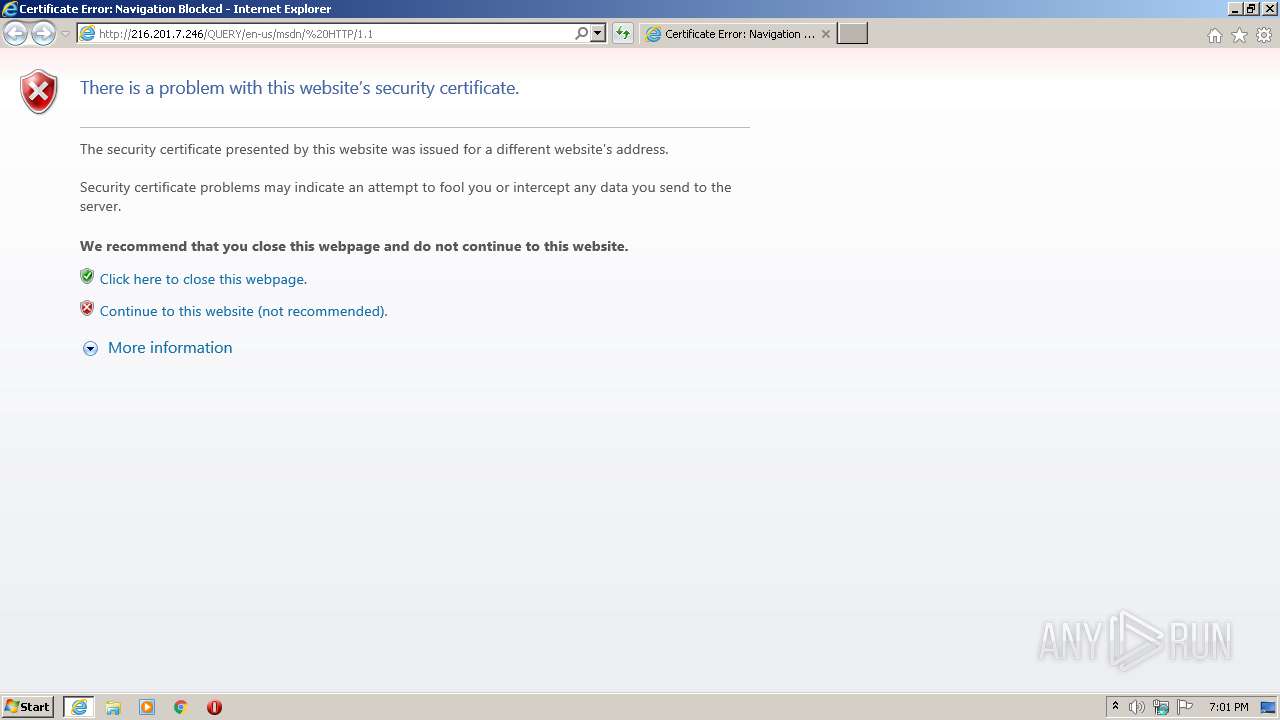
2132 | iexplore.exe | 216.201.7.246:80 | — | Com Net, Inc. | US | malicious |
2132 | iexplore.exe | 216.201.7.246:443 | — | Com Net, Inc. | US | malicious |
2132 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2656 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3192 | chrome.exe | 216.58.206.3:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
3192 | chrome.exe | 216.58.208.45:443 | accounts.google.com | Google Inc. | US | whitelisted |
3192 | chrome.exe | 216.58.208.35:443 | www.google.com.ua | Google Inc. | US | whitelisted |
3192 | chrome.exe | 172.217.23.170:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
3192 | chrome.exe | 216.201.7.246:443 | — | Com Net, Inc. | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ocsp.digicert.com |
| whitelisted |
www.bing.com |
| whitelisted |
api.bing.com |
| whitelisted |
clientservices.googleapis.com |
| whitelisted |
accounts.google.com |
| shared |
www.google.com.ua |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com.ua |
| whitelisted |