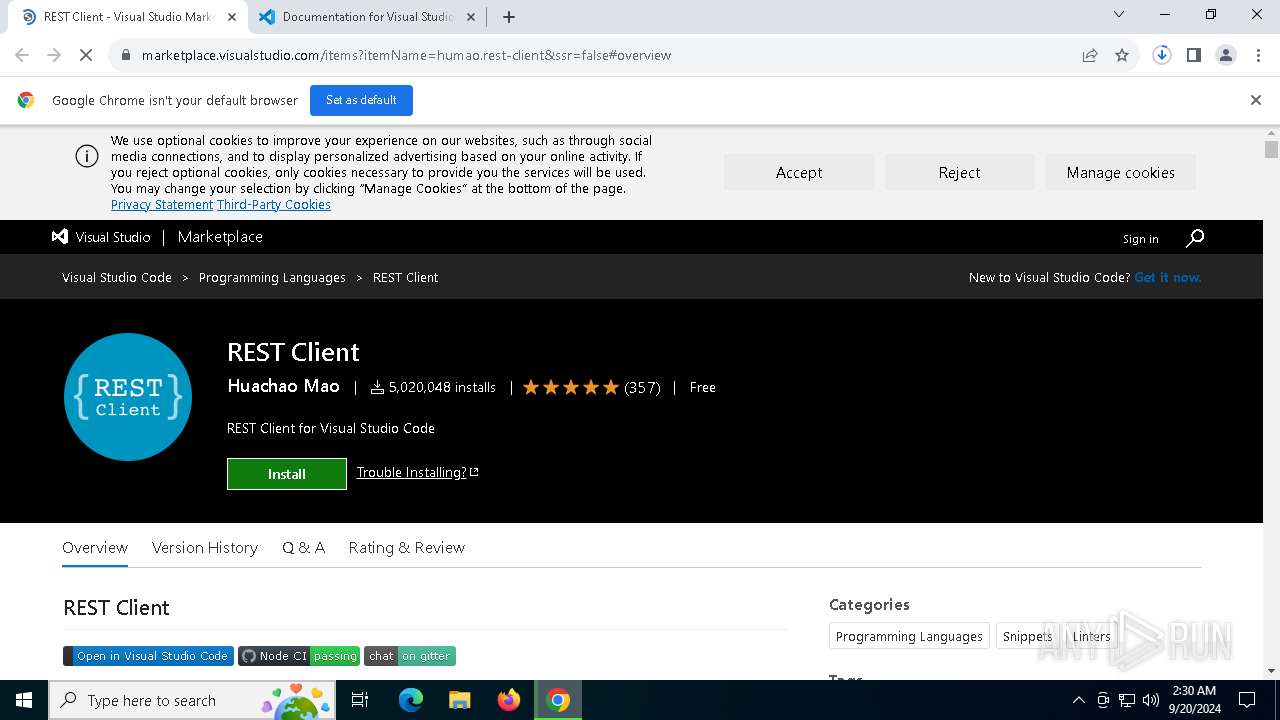
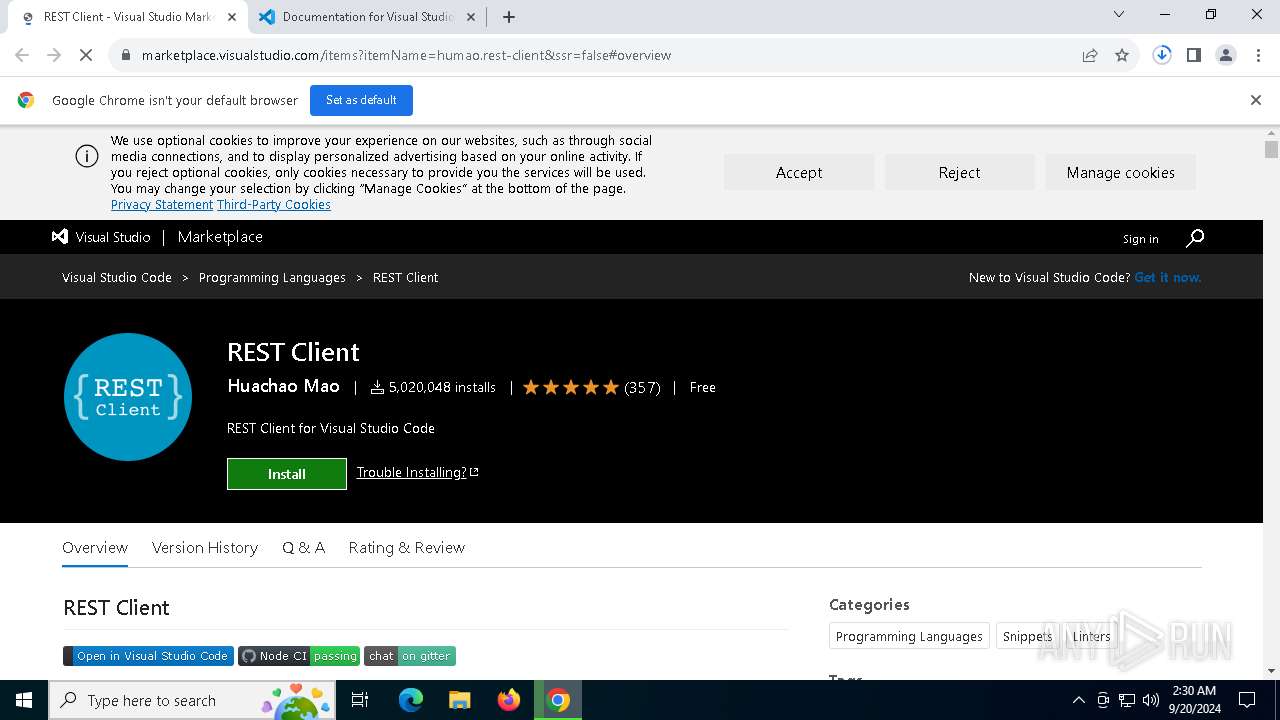
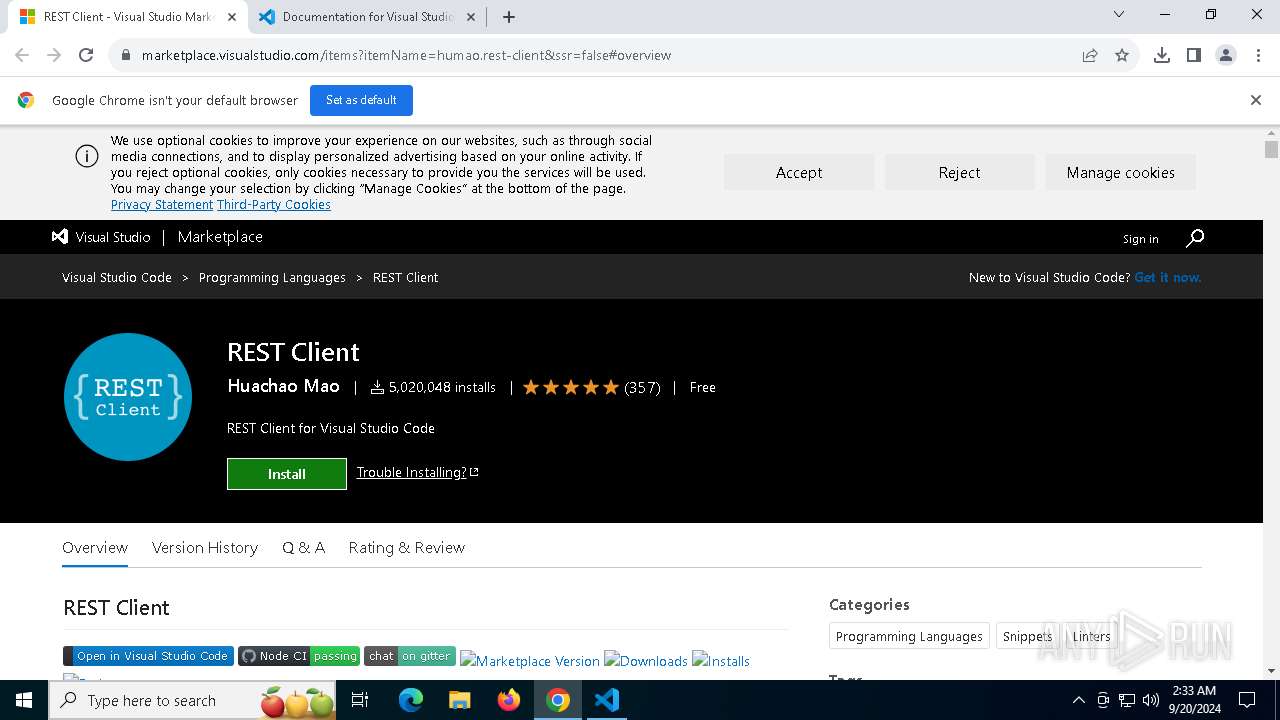
| URL: | https://marketplace.visualstudio.com/items?itemName=humao.rest-client&ssr=false#overview |
| Full analysis: | https://app.any.run/tasks/51535d1f-4201-40ac-a609-bf4896681cf9 |
| Verdict: | Malicious activity |
| Analysis date: | September 20, 2024, 02:29:39 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 6EA8EBAF79EDAEE24FF8018F5AF6FF6C |
| SHA1: | BAE0322CB5EF3933D3C67B9E0FB42E96205A9B0C |
| SHA256: | ACB93D8D4D2D170811E452C4905F984219DF42690FC42E8EA646CC302913C91B |
| SSDEEP: | 3:N8KAZALjWRQBLLM/ICYCIjj9IGCeNIDgWAG1lS:2K4FRU/2ZV4CWNWJI |
MALICIOUS
No malicious indicators.SUSPICIOUS
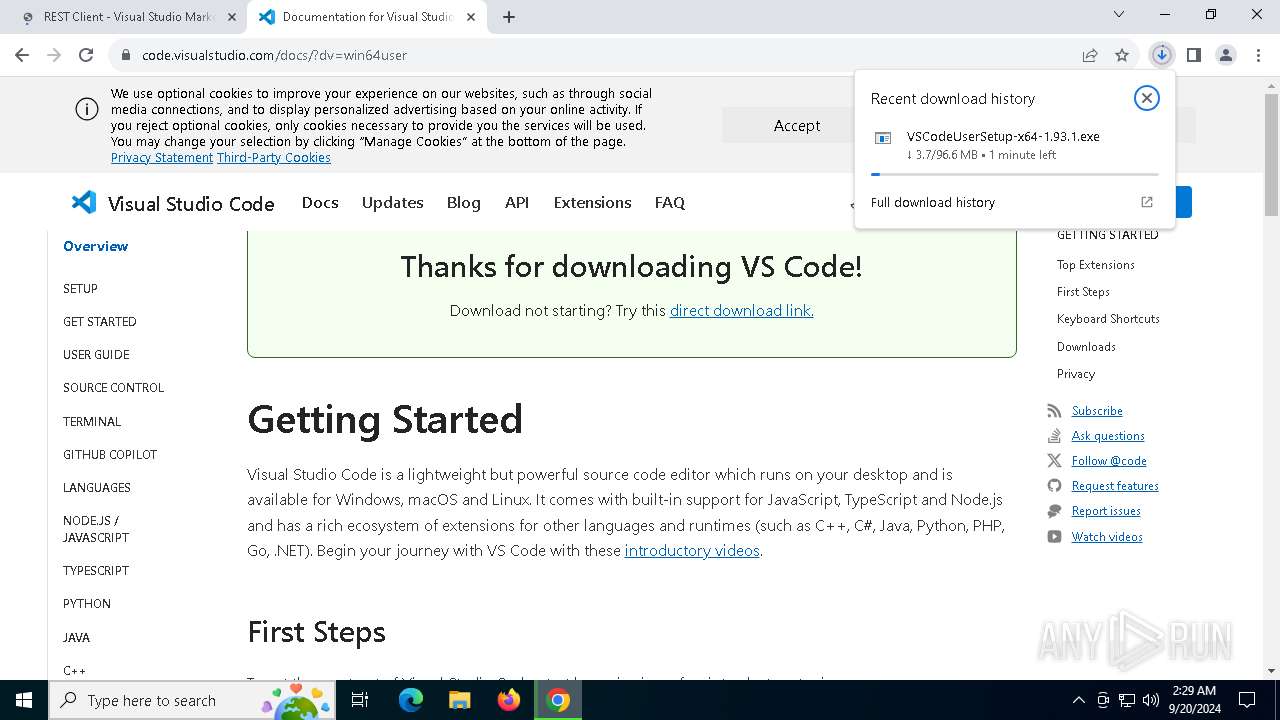
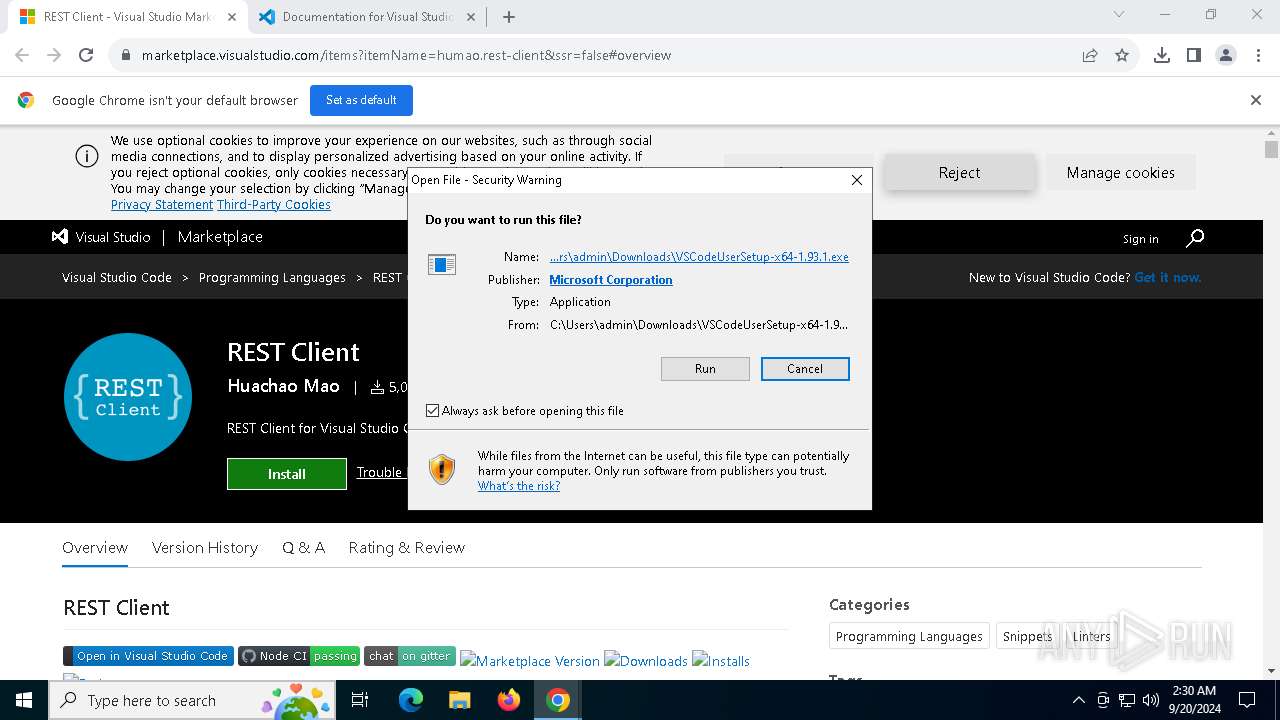
Executable content was dropped or overwritten
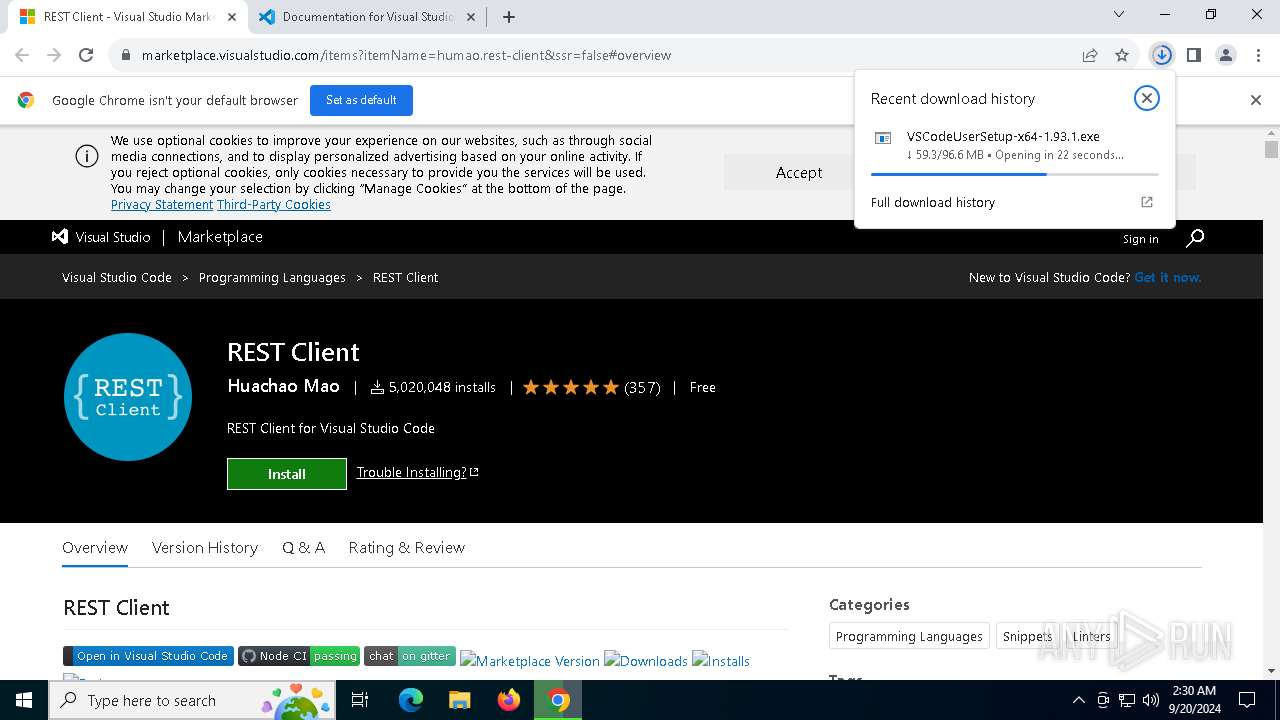
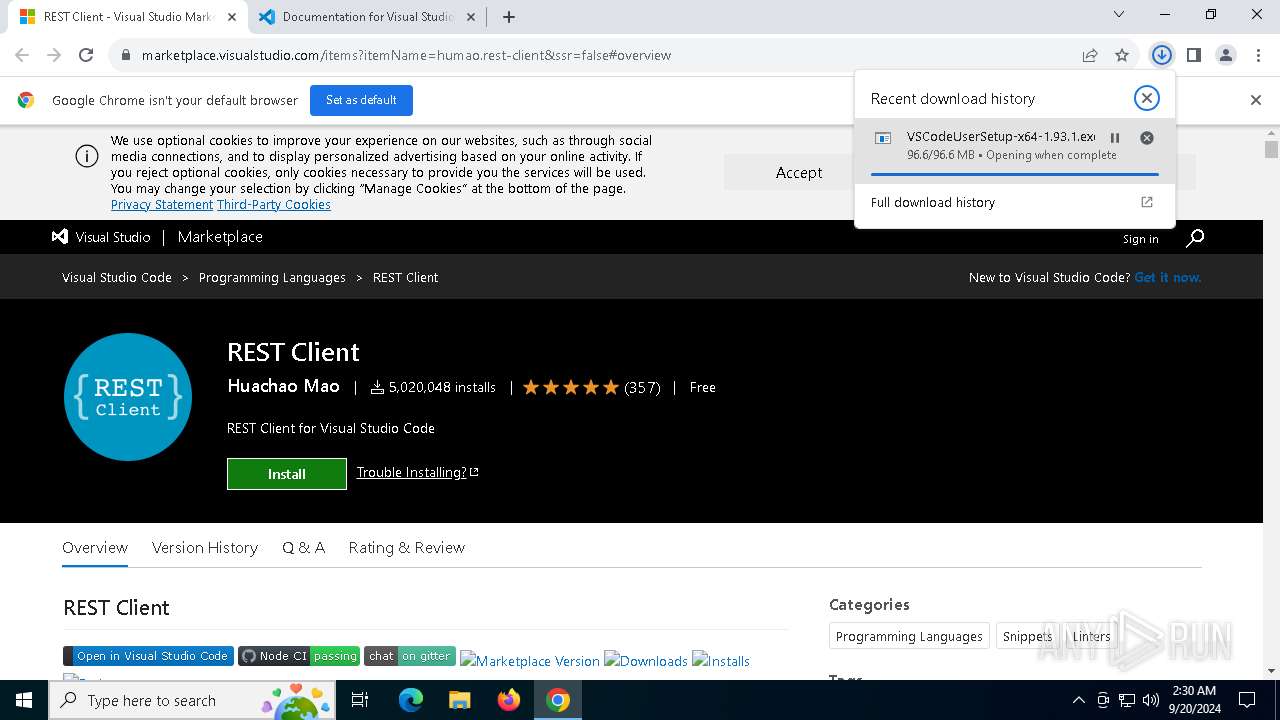
- VSCodeUserSetup-x64-1.93.1.exe (PID: 6244)
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Reads the Windows owner or organization settings
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Reads security settings of Internet Explorer
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Kill processes via PowerShell
- powershell.exe (PID: 6996)
Get information on the list of running processes
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Starts POWERSHELL.EXE for commands execution
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Uses ICACLS.EXE to modify access control lists
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
The process drops C-runtime libraries
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Starts CMD.EXE for commands execution
- Code.exe (PID: 3708)
Process drops legitimate windows executable
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Application launched itself
- Code.exe (PID: 3708)
- Code.exe (PID: 2328)
Found regular expressions for crypto-addresses (YARA)
- Code.exe (PID: 3708)
INFO
Application launched itself
- chrome.exe (PID: 4120)
The process uses the downloaded file
- chrome.exe (PID: 4120)
- chrome.exe (PID: 2988)
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Checks supported languages
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
- VSCodeUserSetup-x64-1.93.1.exe (PID: 6244)
Executable content was dropped or overwritten
- chrome.exe (PID: 4120)
- chrome.exe (PID: 3112)
- chrome.exe (PID: 6700)
Reads the computer name
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Create files in a temporary directory
- VSCodeUserSetup-x64-1.93.1.exe (PID: 6244)
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Reads the software policy settings
- slui.exe (PID: 6840)
Process checks computer location settings
- VSCodeUserSetup-x64-1.93.1.tmp (PID: 5468)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
197
Monitored processes
59
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 368 | "C:\Users\admin\AppData\Local\Programs\Microsoft VS Code\Code.exe" --type=renderer --user-data-dir="C:\Users\admin\AppData\Roaming\Code" --standard-schemes=vscode-webview,vscode-file --enable-sandbox --secure-schemes=vscode-webview,vscode-file --cors-schemes=vscode-webview,vscode-file --fetch-schemes=vscode-webview,vscode-file --service-worker-schemes=vscode-webview --code-cache-schemes=vscode-webview,vscode-file --app-user-model-id=Microsoft.VisualStudioCode --app-path="C:\Users\admin\AppData\Local\Programs\Microsoft VS Code\resources\app" --enable-sandbox --enable-blink-features=HighlightAPI --disable-gpu-compositing --disable-blink-features=FontMatchingCTMigration, --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=8 --field-trial-handle=3832,i,9195467774184282552,14876534691250652257,262144 --enable-features=kWebSQLAccess --disable-features=CalculateNativeWinOcclusion,SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=3836 --vscode-window-config=vscode:d8ef23a6-36aa-42f0-8868-cf5d3a85ddb6 /prefetch:1 | C:\Users\admin\AppData\Local\Programs\Microsoft VS Code\Code.exe | — | Code.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Visual Studio Code Exit code: 0 Version: 1.93.1 Modules
| |||||||||||||||
| 840 | "C:\Users\admin\AppData\Local\Programs\Microsoft VS Code\Code.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --user-data-dir="C:\Users\admin\AppData\Roaming\Code" --standard-schemes=vscode-webview,vscode-file --enable-sandbox --secure-schemes=vscode-webview,vscode-file --cors-schemes=vscode-webview,vscode-file --fetch-schemes=vscode-webview,vscode-file --service-worker-schemes=vscode-webview --code-cache-schemes=vscode-webview,vscode-file --field-trial-handle=1980,i,9195467774184282552,14876534691250652257,262144 --enable-features=kWebSQLAccess --disable-features=CalculateNativeWinOcclusion,SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=1976 /prefetch:3 | C:\Users\admin\AppData\Local\Programs\Microsoft VS Code\Code.exe | Code.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Studio Code Version: 1.93.1 Modules
| |||||||||||||||
| 940 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=6516 --field-trial-handle=1928,i,17485830686737594474,16419233466961194372,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 | |||||||||||||||
| 1116 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:4 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win64 --annotation=prod=Chrome --annotation=ver=122.0.6261.70 --initial-client-data=0x21c,0x220,0x224,0x1f8,0x228,0x7fffcaeedc40,0x7fffcaeedc4c,0x7fffcaeedc58 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1372 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=5804 --field-trial-handle=1928,i,17485830686737594474,16419233466961194372,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 122.0.6261.70 Modules
| |||||||||||||||
| 1932 | "C:\Users\admin\AppData\Local\Programs\Microsoft VS Code\Code.exe" --type=utility --utility-sub-type=node.mojom.NodeService --lang=en-US --service-sandbox-type=none --dns-result-order=ipv4first --inspect-port=0 --user-data-dir="C:\Users\admin\AppData\Roaming\Code" --standard-schemes=vscode-webview,vscode-file --enable-sandbox --secure-schemes=vscode-webview,vscode-file --cors-schemes=vscode-webview,vscode-file --fetch-schemes=vscode-webview,vscode-file --service-worker-schemes=vscode-webview --code-cache-schemes=vscode-webview,vscode-file --field-trial-handle=3732,i,9195467774184282552,14876534691250652257,262144 --enable-features=kWebSQLAccess --disable-features=CalculateNativeWinOcclusion,SpareRendererForSitePerProcess,WinDelaySpellcheckServiceInit,WinRetrieveSuggestionsOnlyOnDemand --variations-seed-version --mojo-platform-channel-handle=3728 /prefetch:8 | C:\Users\admin\AppData\Local\Programs\Microsoft VS Code\Code.exe | — | Code.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Studio Code Version: 1.93.1 Modules
| |||||||||||||||
| 2016 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --disable-quic --no-appcompat-clear --mojo-platform-channel-handle=2004 --field-trial-handle=1928,i,17485830686737594474,16419233466961194372,262144 --disable-features=OptimizationGuideModelDownloading,OptimizationHints,OptimizationHintsFetching,OptimizationTargetPrediction --variations-seed-version /prefetch:3 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Version: 122.0.6261.70 Modules
| |||||||||||||||
| 2328 | "C:\Users\admin\AppData\Local\Programs\Microsoft VS Code\Code.exe" "--open-url" "--" "vscode:extension/humao.rest-client" | C:\Users\admin\AppData\Local\Programs\Microsoft VS Code\Code.exe | — | chrome.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Visual Studio Code Exit code: 0 Version: 1.93.1 | |||||||||||||||
| 2340 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | code-tunnel.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 100
Read events
19 592
Write events
479
Delete events
29
Modification events
| (PID) Process: | (4120) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (4120) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (4120) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (4120) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Chrome\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (4120) chrome.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Google\Update\ClientStateMedium\{8A69D345-D564-463C-AFF1-A69D9E530F96} |
| Operation: | write | Name: | usagestats |
Value: 0 | |||
| (PID) Process: | (2988) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Shell Extensions\Cached |
| Operation: | write | Name: | {2781761E-28E0-4109-99FE-B9D127C57AFE} {56FFCC30-D398-11D0-B2AE-00A0C908FA49} 0xFFFF |
Value: 0100000000000000348EE61E050BDB01 | |||
| (PID) Process: | (4120) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1I |
Value: 1 | |||
| (PID) Process: | (4120) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C2I |
Value: 1 | |||
| (PID) Process: | (4120) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C7I |
Value: 1 | |||
| (PID) Process: | (4120) chrome.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Google\Common\Rlz\Events\C |
| Operation: | write | Name: | C1S |
Value: 1 | |||
Executable files
87
Suspicious files
1 451
Text files
1 134
Unknown types
16
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4120 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4120 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4120 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4120 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\chrome_cart_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4120 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old~RF1fc136.TMP | — | |
MD5:— | SHA256:— | |||
| 4120 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4120 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old~RF1fc136.TMP | — | |
MD5:— | SHA256:— | |||
| 4120 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\coupon_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 4120 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Last Version | text | |
MD5:FCE53E052E5CF7C20819320F374DEA88 | SHA256:CD95DE277E746E92CC2C53D9FC92A8F6F0C3EDFB7F1AD9A4E9259F927065BC89 | |||
| 4120 | chrome.exe | C:\Users\admin\AppData\Local\Google\Chrome\User Data\Default\Sync Data\LevelDB\LOG.old~RF1fc0f7.TMP | text | |
MD5:8F45965291AB2DA10EEB049FB6E917C6 | SHA256:8A0DE526945B27CDBBD87357C85FDDD37B572370F894CB0A5AC533FD465D2166 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
142
DNS requests
132
Threats
5
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2120 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
5524 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/imoffpf67hel7kbknqflao2oo4_1.0.2738.0/neifaoindggfcjicffkgpmnlppeffabd_1.0.2738.0_win64_kj4dp5kifwxbdodqls7e5nzhtm.crx3 | unknown | — | — | whitelisted |
2772 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
2824 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5524 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acltxtzzramufl6qm6t2ggr2zyca_9133/hfnkpimlhhgieaddgfemjhofmfblmnib_9133_all_adzdklsy63qkl675ec3ts7akhhzq.crx3 | unknown | — | — | whitelisted |
2772 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5524 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acltxtzzramufl6qm6t2ggr2zyca_9133/hfnkpimlhhgieaddgfemjhofmfblmnib_9133_all_adzdklsy63qkl675ec3ts7akhhzq.crx3 | unknown | — | — | whitelisted |
5524 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acltxtzzramufl6qm6t2ggr2zyca_9133/hfnkpimlhhgieaddgfemjhofmfblmnib_9133_all_adzdklsy63qkl675ec3ts7akhhzq.crx3 | unknown | — | — | whitelisted |
5524 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/acltxtzzramufl6qm6t2ggr2zyca_9133/hfnkpimlhhgieaddgfemjhofmfblmnib_9133_all_adzdklsy63qkl675ec3ts7akhhzq.crx3 | unknown | — | — | whitelisted |
4120 | chrome.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
608 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1848 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4120 | chrome.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
2108 | chrome.exe | 13.107.42.18:443 | marketplace.visualstudio.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
2108 | chrome.exe | 74.125.133.84:443 | accounts.google.com | GOOGLE | US | whitelisted |
2108 | chrome.exe | 152.199.19.160:443 | cdn.vsassets.io | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
marketplace.visualstudio.com |
| whitelisted |
accounts.google.com |
| whitelisted |
cdn.vsassets.io |
| whitelisted |
wcpstatic.microsoft.com |
| whitelisted |
fpt.microsoft.com |
| whitelisted |
content-autofill.googleapis.com |
| whitelisted |
api.github.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2108 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2108 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2108 | chrome.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
— | — | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |