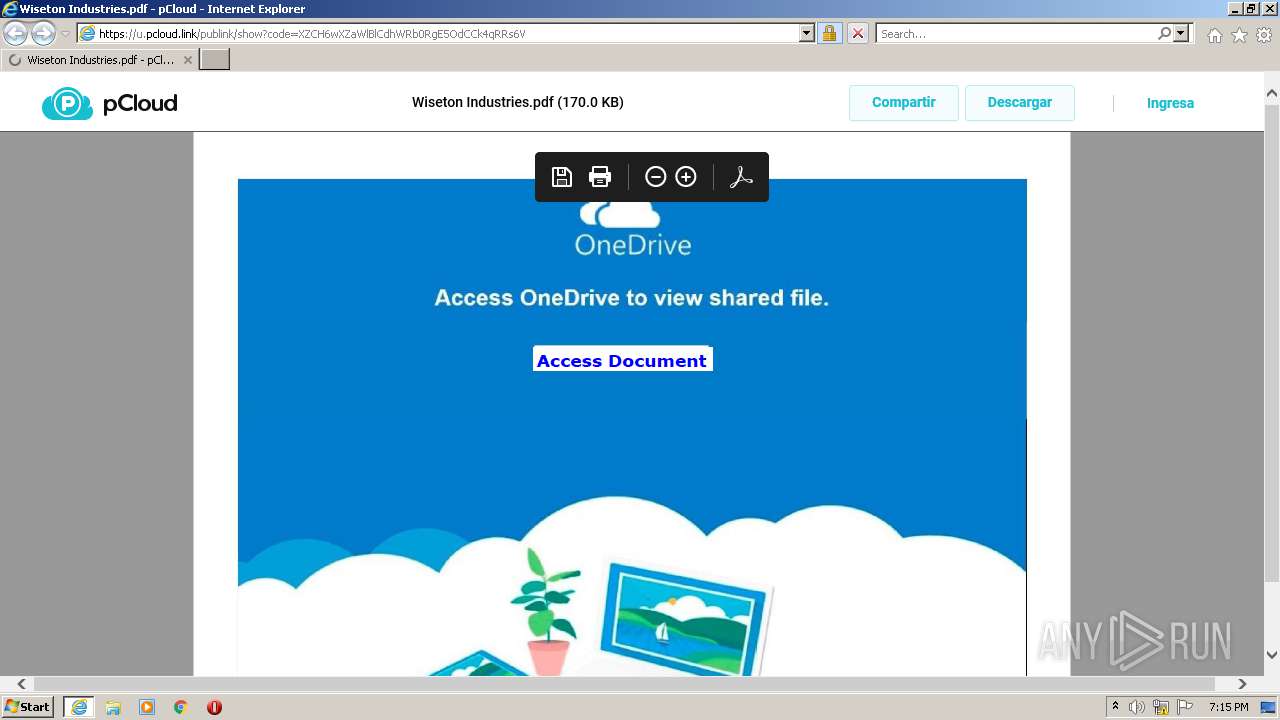
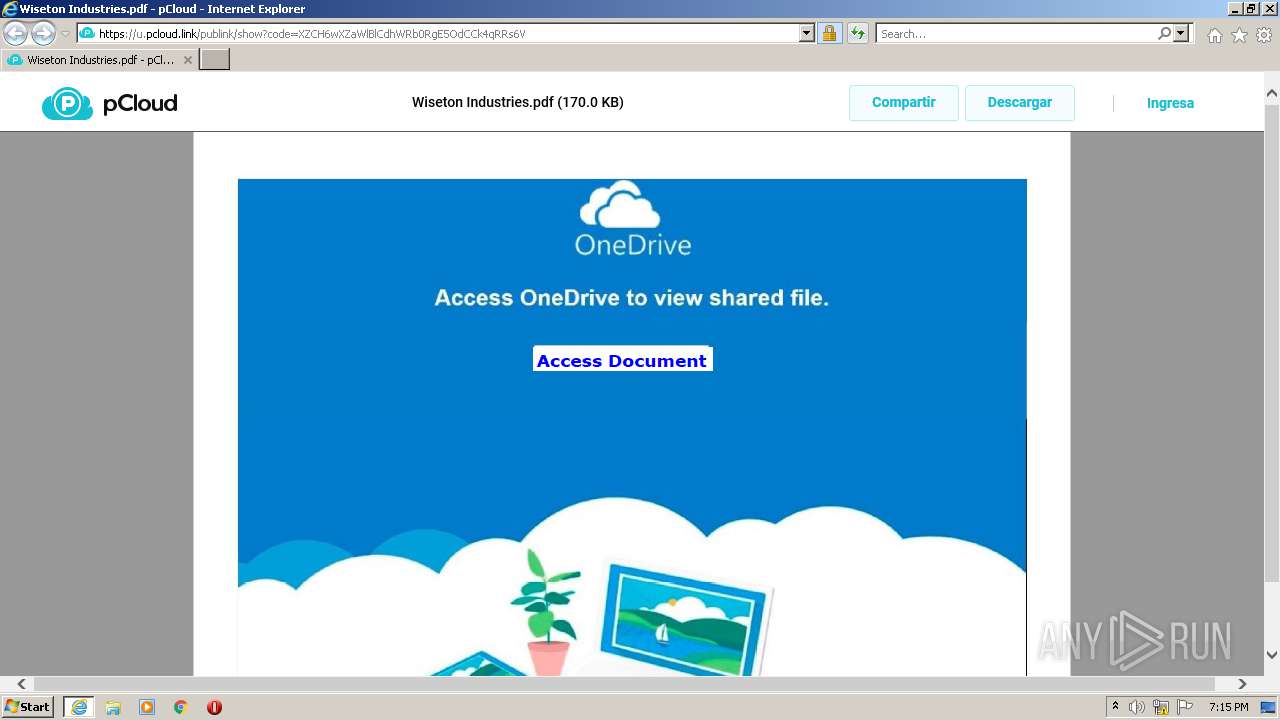
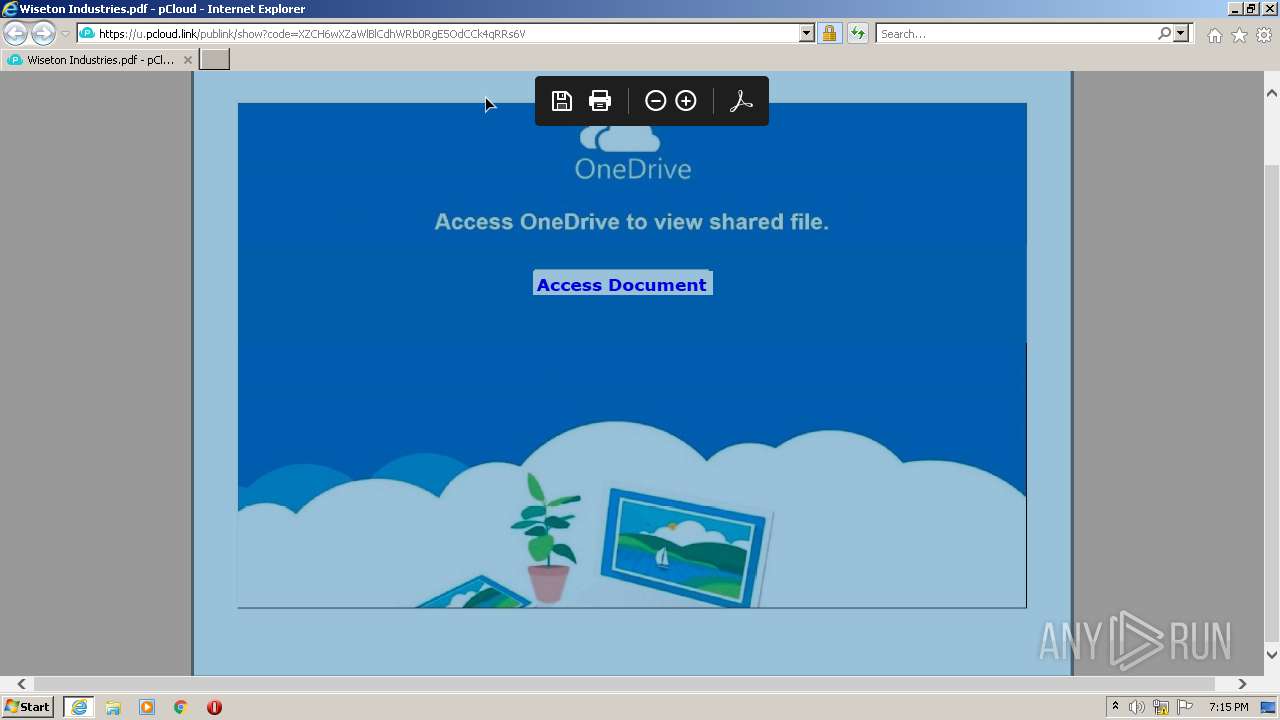
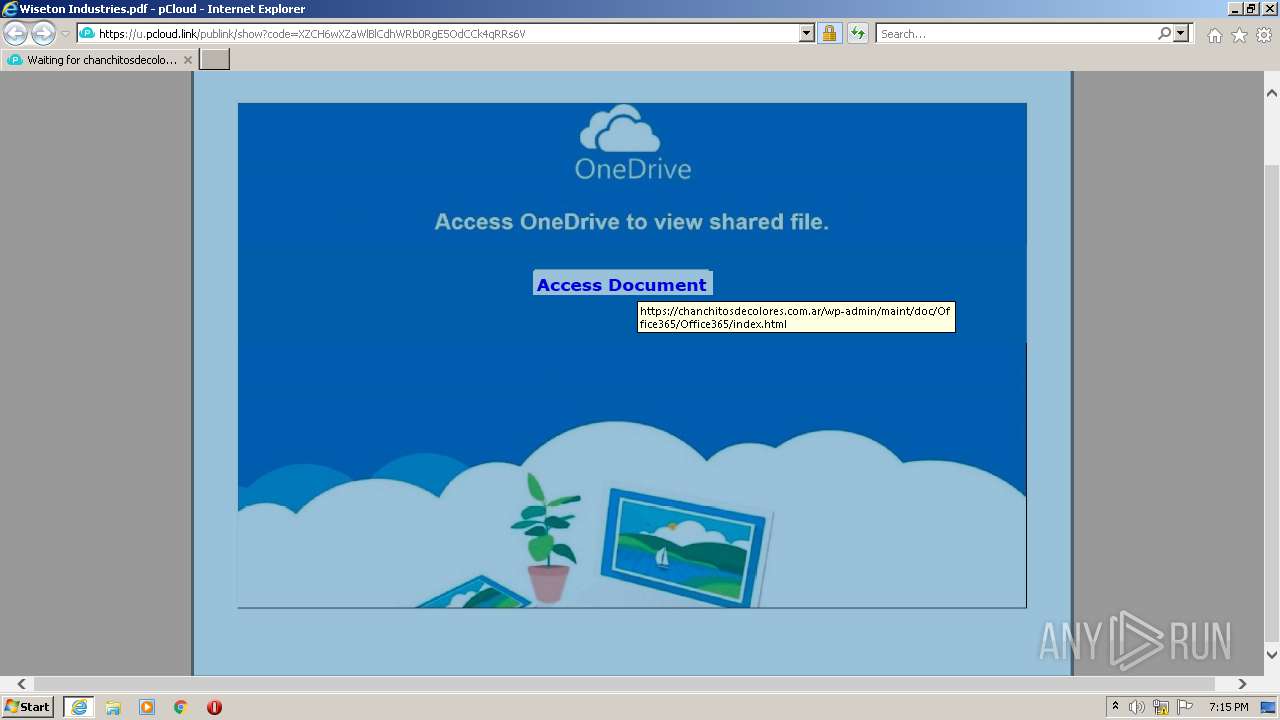
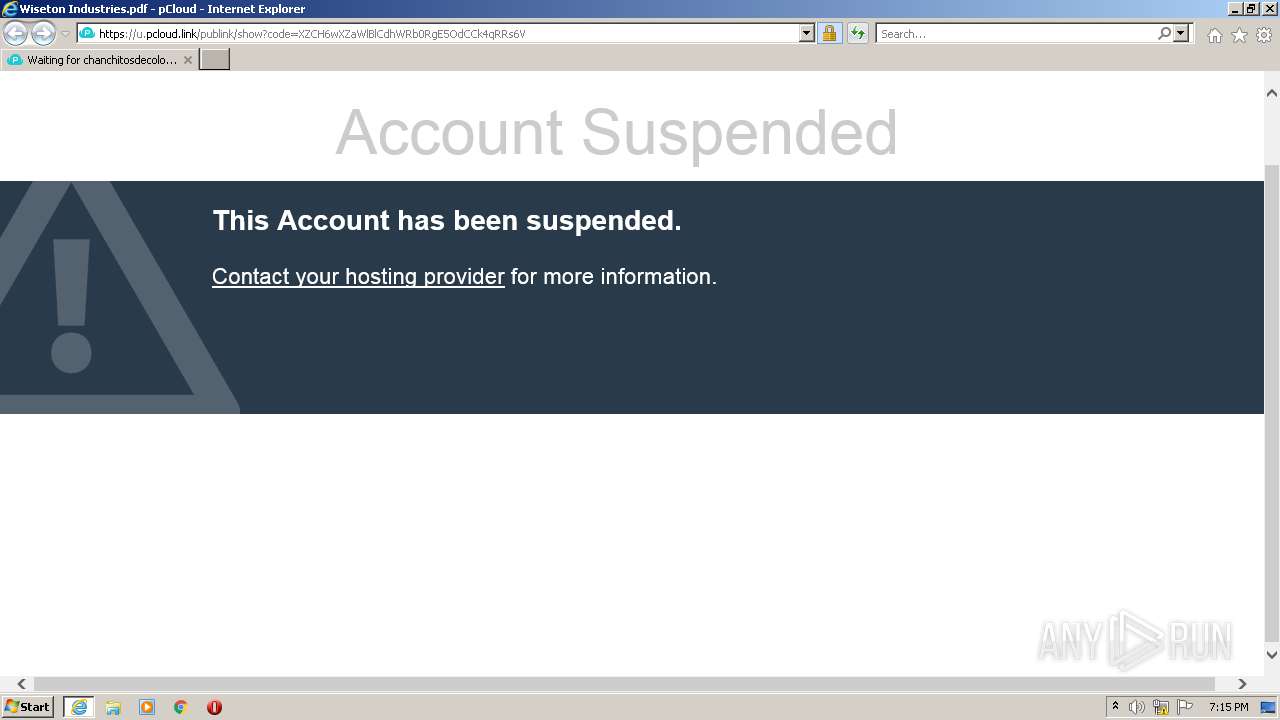
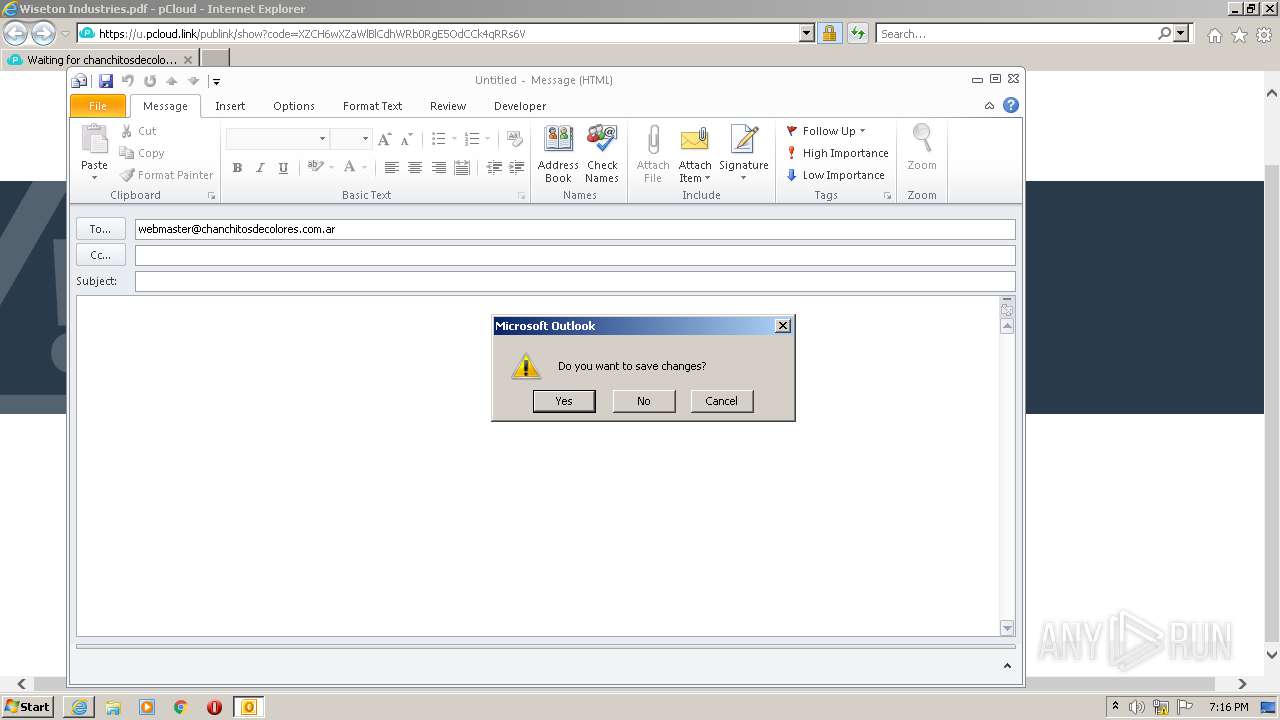
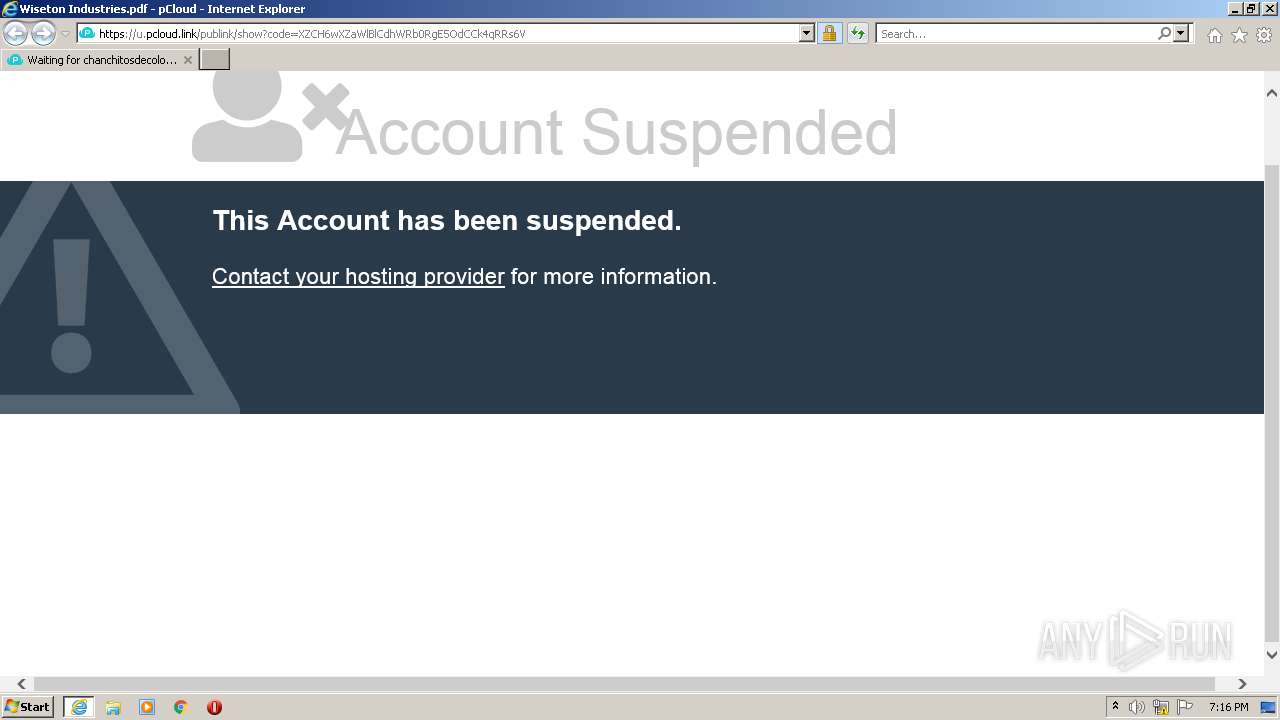
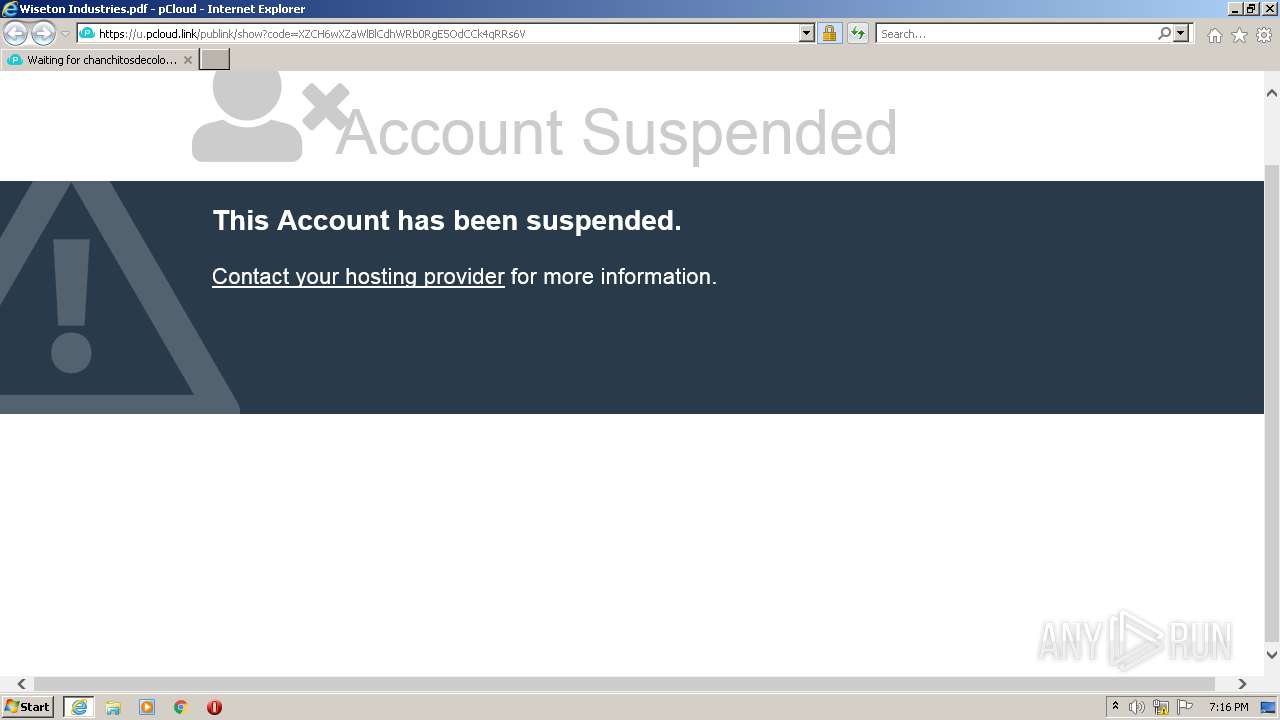
| URL: | https://u.pcloud.link/publink/show?code=XZCH6wXZaWlBlCdhWRb0RgE5OdCCk4qRRs6V |
| Full analysis: | https://app.any.run/tasks/5e896cb8-000f-48d2-903f-935aeb3fff40 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2021, 18:14:27 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8A68E81993A1D1CC799A214B3E877506 |
| SHA1: | 8078A939A19834C6BA0FFB4D7F10C3DEDCC197AE |
| SHA256: | ACA16E8D667D260B57188FF7E2E6BCA8A96566783917D11FB799FF39D199096C |
| SSDEEP: | 3:N8sVnLoHCokkTRsoV6MD:2sCioHygD |
MALICIOUS
No malicious indicators.SUSPICIOUS
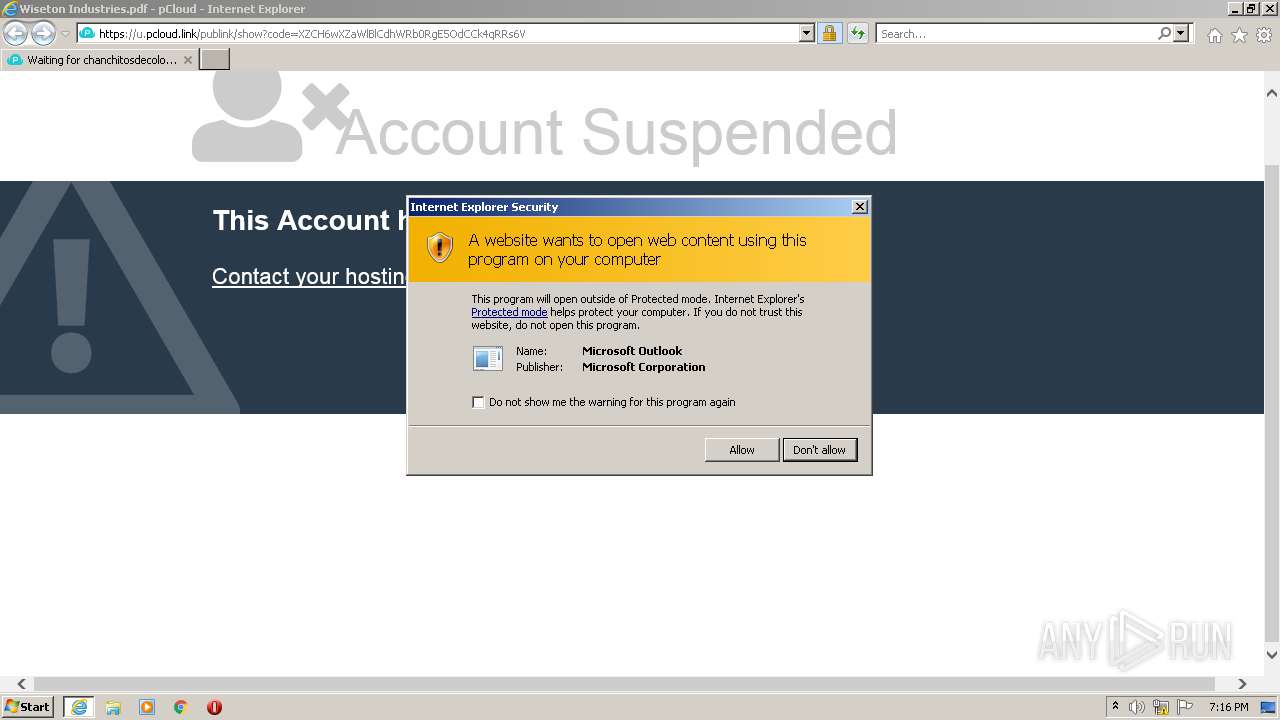
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 992)
Reads the computer name
- OUTLOOK.EXE (PID: 3656)
Checks supported languages
- OUTLOOK.EXE (PID: 3656)
Searches for installed software
- OUTLOOK.EXE (PID: 3656)
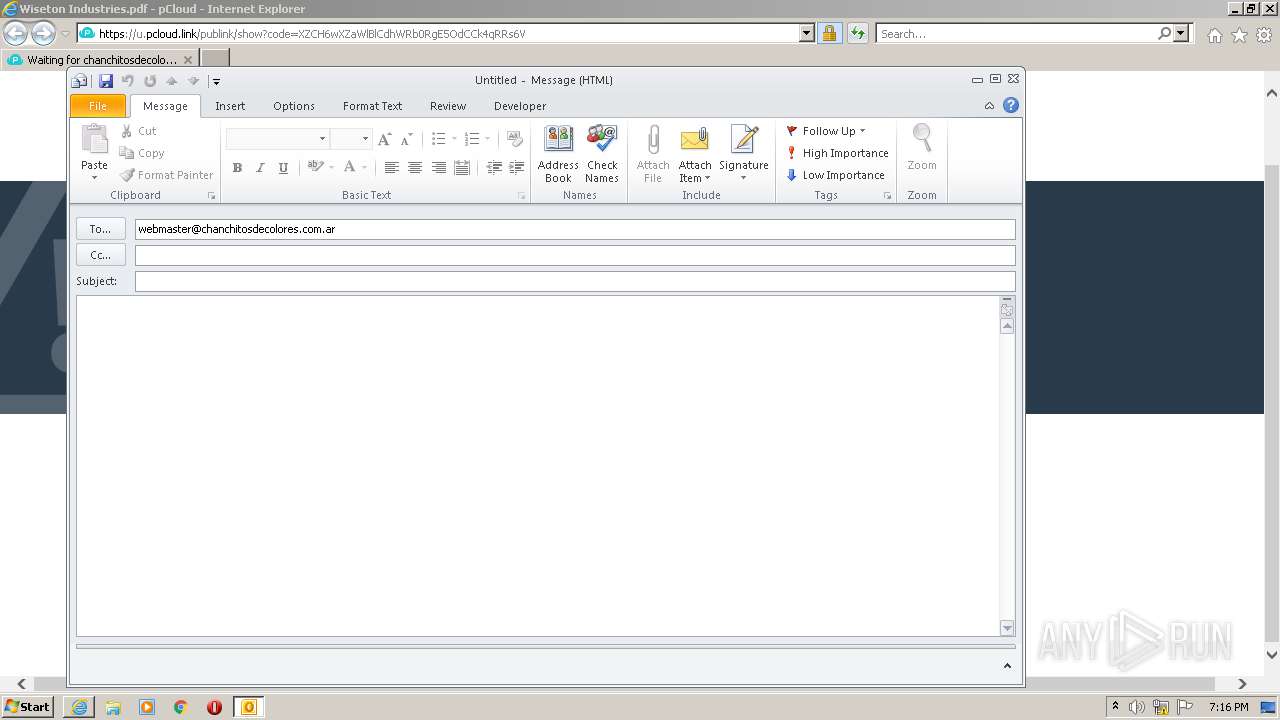
Creates files in the user directory
- OUTLOOK.EXE (PID: 3656)
INFO
Application launched itself
- iexplore.exe (PID: 1388)
- AcroRd32.exe (PID: 1928)
- RdrCEF.exe (PID: 3932)
Checks supported languages
- iexplore.exe (PID: 992)
- iexplore.exe (PID: 1388)
- AcroRd32.exe (PID: 1928)
- AcroRd32.exe (PID: 508)
- RdrCEF.exe (PID: 3932)
- RdrCEF.exe (PID: 2552)
- RdrCEF.exe (PID: 3296)
- RdrCEF.exe (PID: 1968)
- RdrCEF.exe (PID: 2688)
- RdrCEF.exe (PID: 3040)
Changes internet zones settings
- iexplore.exe (PID: 1388)
Reads internet explorer settings
- iexplore.exe (PID: 992)
Reads the computer name
- iexplore.exe (PID: 992)
- iexplore.exe (PID: 1388)
- AcroRd32.exe (PID: 1928)
- AcroRd32.exe (PID: 508)
- RdrCEF.exe (PID: 3932)
Checks Windows Trust Settings
- iexplore.exe (PID: 1388)
- iexplore.exe (PID: 992)
- AcroRd32.exe (PID: 1928)
Reads settings of System Certificates
- iexplore.exe (PID: 1388)
- iexplore.exe (PID: 992)
- AcroRd32.exe (PID: 1928)
- RdrCEF.exe (PID: 3932)
Reads CPU info
- AcroRd32.exe (PID: 508)
Creates files in the user directory
- iexplore.exe (PID: 992)
- AcroRd32.exe (PID: 1928)
- iexplore.exe (PID: 1388)
Searches for installed software
- AcroRd32.exe (PID: 1928)
- AcroRd32.exe (PID: 508)
Reads the hosts file
- RdrCEF.exe (PID: 3932)
Changes settings of System certificates
- iexplore.exe (PID: 1388)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3656)
Adds / modifies Windows certificates
- iexplore.exe (PID: 1388)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
51
Monitored processes
13
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 508 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" --type=renderer /o /eo /l /b /id 992 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | AcroRd32.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 992 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:1388 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1388 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://u.pcloud.link/publink/show?code=XZCH6wXZaWlBlCdhWRb0RgE5OdCCk4qRRs6V" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1928 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" /o /eo /l /b /id 992 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | iexplore.exe | ||||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: MEDIUM Description: Adobe Acrobat Reader DC Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1968 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1172,16579255474698872392,11940867520390991149,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=5383798758880901657 --renderer-client-id=6 --mojo-platform-channel-handle=1440 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2408 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe" /o /eo /l /b /id 992 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroRd32.exe | — | iexplore.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe Acrobat Reader DC Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2552 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=renderer --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --touch-events=enabled --field-trial-handle=1172,16579255474698872392,11940867520390991149,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-gpu-compositing --lang=en-US --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=7084716576729133567 --renderer-client-id=2 --mojo-platform-channel-handle=1180 --allow-no-sandbox-job /prefetch:1 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 0 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 2688 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1172,16579255474698872392,11940867520390991149,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=11909676939458235857 --mojo-platform-channel-handle=1200 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3040 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1172,16579255474698872392,11940867520390991149,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=15163540348374325956 --mojo-platform-channel-handle=1216 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 3296 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1172,16579255474698872392,11940867520390991149,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=12822778141744505725 --mojo-platform-channel-handle=1372 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
Total events
28 620
Read events
27 801
Write events
790
Delete events
29
Modification events
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30904229 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: 29085967 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30904230 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (1388) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
120
Text files
57
Unknown types
29
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 992 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 1388 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\82CB34DD3343FE727DF8890D352E0D8F | binary | |
MD5:— | SHA256:— | |||
| 992 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2EE749B7E1A15635422518BB5EBFD338_954F2B09506D1D49A629A06193BBB92E | der | |
MD5:— | SHA256:— | |||
| 992 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 992 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\07CEF2F654E3ED6050FFC9B6EB844250_3F26ED5DE6B4E859CCCA6035ECB8D9CB | binary | |
MD5:— | SHA256:— | |||
| 992 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\07CEF2F654E3ED6050FFC9B6EB844250_3F26ED5DE6B4E859CCCA6035ECB8D9CB | der | |
MD5:— | SHA256:— | |||
| 1388 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\82CB34DD3343FE727DF8890D352E0D8F | der | |
MD5:— | SHA256:— | |||
| 992 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\204C1AA6F6114E6A513754A2AB5760FA_AD59C201C52F2EA45B60DE6C0B473A40 | binary | |
MD5:— | SHA256:— | |||
| 992 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 992 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2EE749B7E1A15635422518BB5EBFD338_954F2B09506D1D49A629A06193BBB92E | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
87
DNS requests
35
Threats
15
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3656 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
992 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRyyuDOSqb8BtprWZSAvBT9kFoYdwQU%2BftQxItnu2dk%2FoMhpqnOP1WEk5kCECDJGUwBrGnx4AjOSmT2OJk%3D | US | der | 471 b | whitelisted |
992 | iexplore.exe | GET | 200 | 35.156.236.11:80 | http://ocsp.quovadisglobal.com/MFUwUzBRME8wTTAJBgUrDgMCGgUABBTyhcKR1A4XhQLFZRt5u%2BT8TDsYdQQUGoRivEhMMyUE1O7Q9gPEGUbRlGsCFBpu6JPDdJc44SrMx3qMCssWfq8U | DE | der | 1.71 Kb | whitelisted |
992 | iexplore.exe | GET | 200 | 142.250.186.35:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEBtpDEx%2Fx4YJCgAAAADyw4g%3D | US | der | 471 b | whitelisted |
992 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAtb9ltrp%2FvQiykNkEU33uA%3D | US | der | 471 b | whitelisted |
1388 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.68 Kb | whitelisted |
1388 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
992 | iexplore.exe | GET | 200 | 35.156.236.11:80 | http://ocsp.quovadisglobal.com/MFUwUzBRME8wTTAJBgUrDgMCGgUABBQizVAdki5cQPHmWNk6O3DgVg1ovgQUkRlirVsXpzD78N45JbG9jLm4UScCFCQaPeAVhxCmyWGJqV9iMv93uJYJ | DE | der | 1.47 Kb | whitelisted |
992 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.usertrust.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTNMNJMNDqCqx8FcBWK16EHdimS6QQUU3m%2FWqorSs9UgOHYm8Cd8rIDZssCEQCTi7COYph7T3X5jLalBFyW | US | der | 728 b | whitelisted |
992 | iexplore.exe | GET | 200 | 104.18.20.226:80 | http://ocsp2.globalsign.com/rootr3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT1nGh%2FJBjWKnkPdZIzB1bqhelHBwQUj%2FBLf6guRSSuTVD6Y5qL3uLdG7wCEHgDGCDPAjbzpoUYuu%2B39wE%3D | US | der | 1.40 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
992 | iexplore.exe | 74.120.8.104:443 | u.pcloud.link | Lemuria Communications Inc. | US | suspicious |
992 | iexplore.exe | 151.139.128.14:80 | ocsp.usertrust.com | Highwinds Network Group, Inc. | US | suspicious |
1388 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
992 | iexplore.exe | 67.27.235.126:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
1388 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
992 | iexplore.exe | 172.255.6.177:443 | pcdn-u.pcloud.com | — | NL | malicious |
992 | iexplore.exe | 142.250.186.35:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
992 | iexplore.exe | 35.156.236.11:80 | ocsp.quovadisglobal.com | Amazon.com, Inc. | DE | whitelisted |
992 | iexplore.exe | 142.250.186.163:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
— | — | 35.156.236.11:80 | ocsp.quovadisglobal.com | Amazon.com, Inc. | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
u.pcloud.link |
| suspicious |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.usertrust.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
crl3.digicert.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
pcdn-u.pcloud.com |
| suspicious |
polyfill.io |
| whitelisted |
Threats
15 ETPRO signatures available at the full report