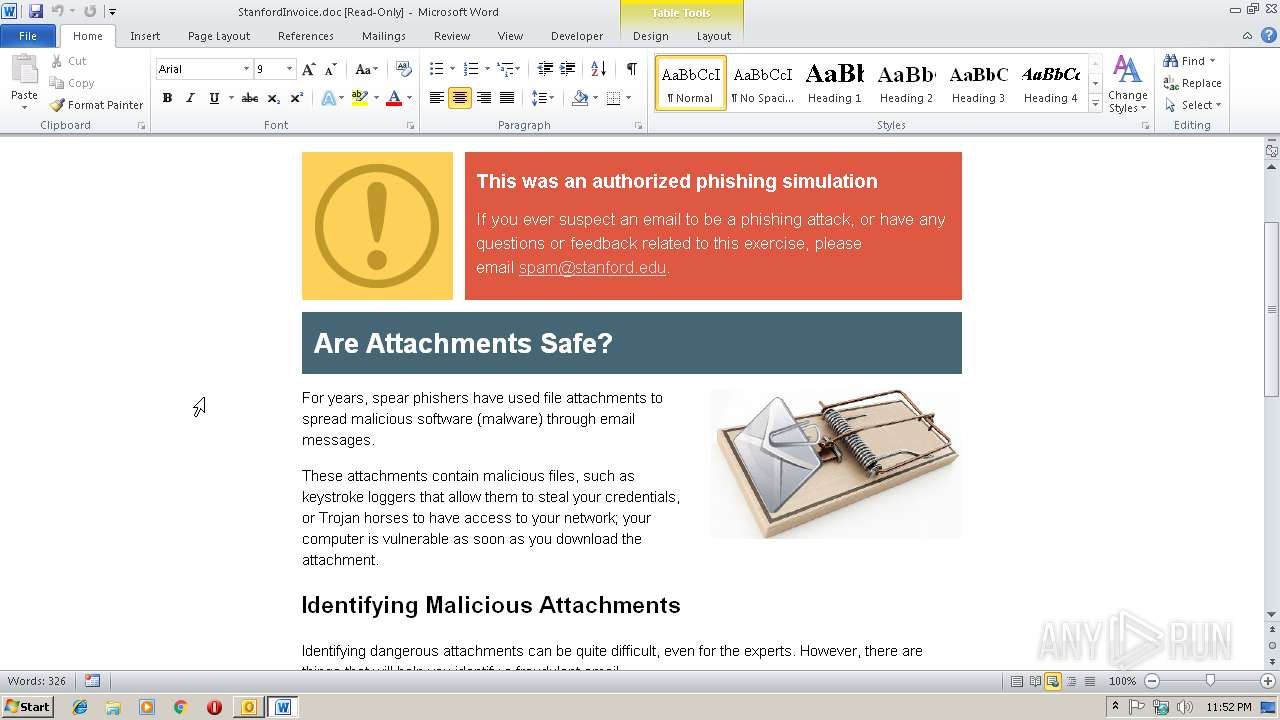
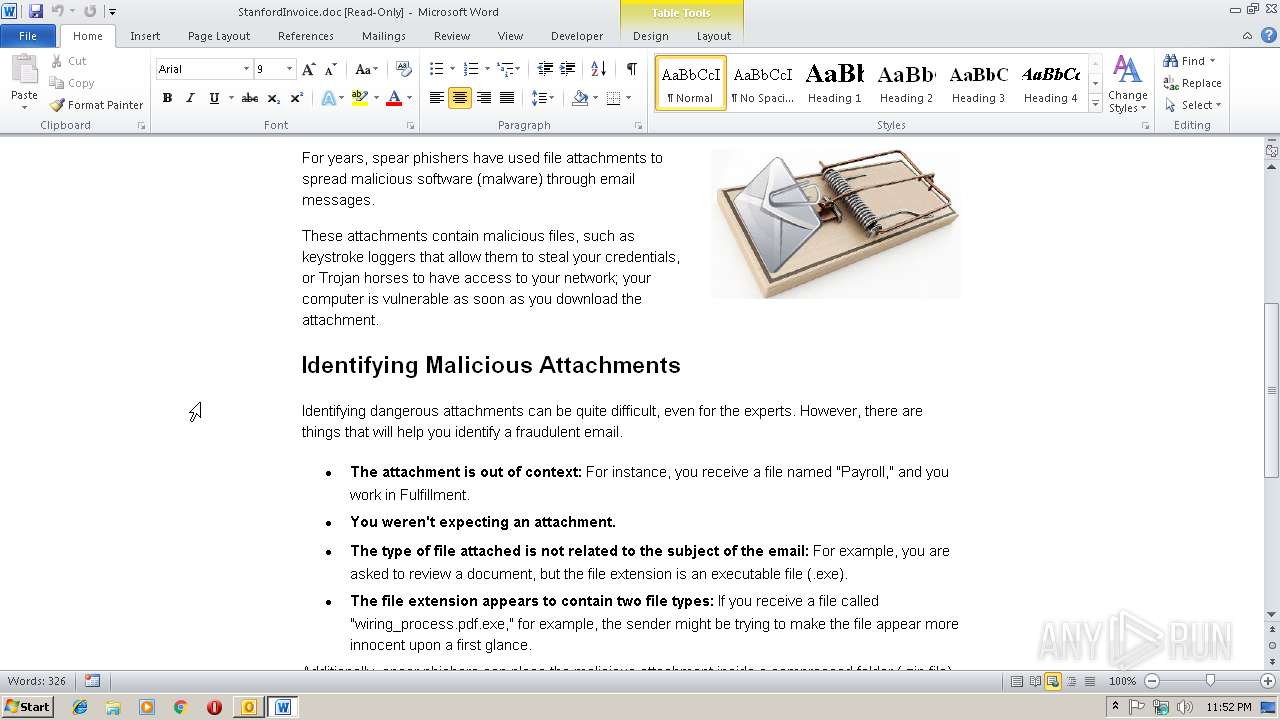
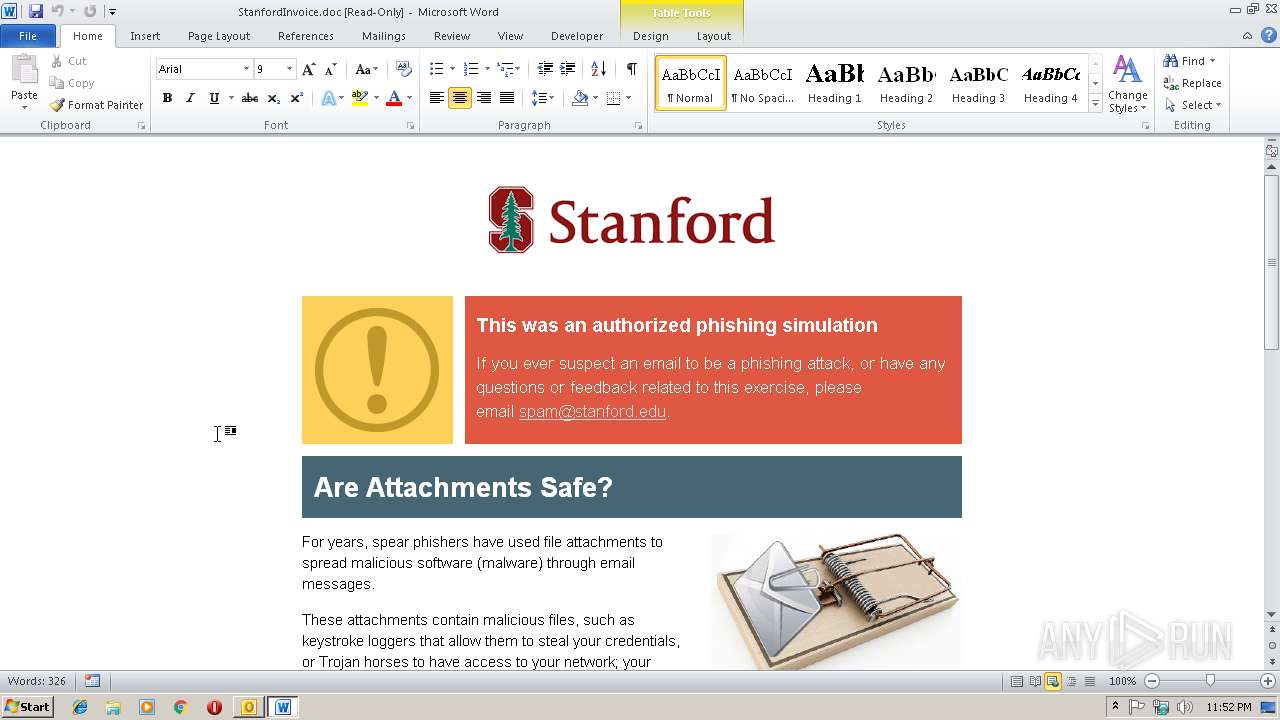
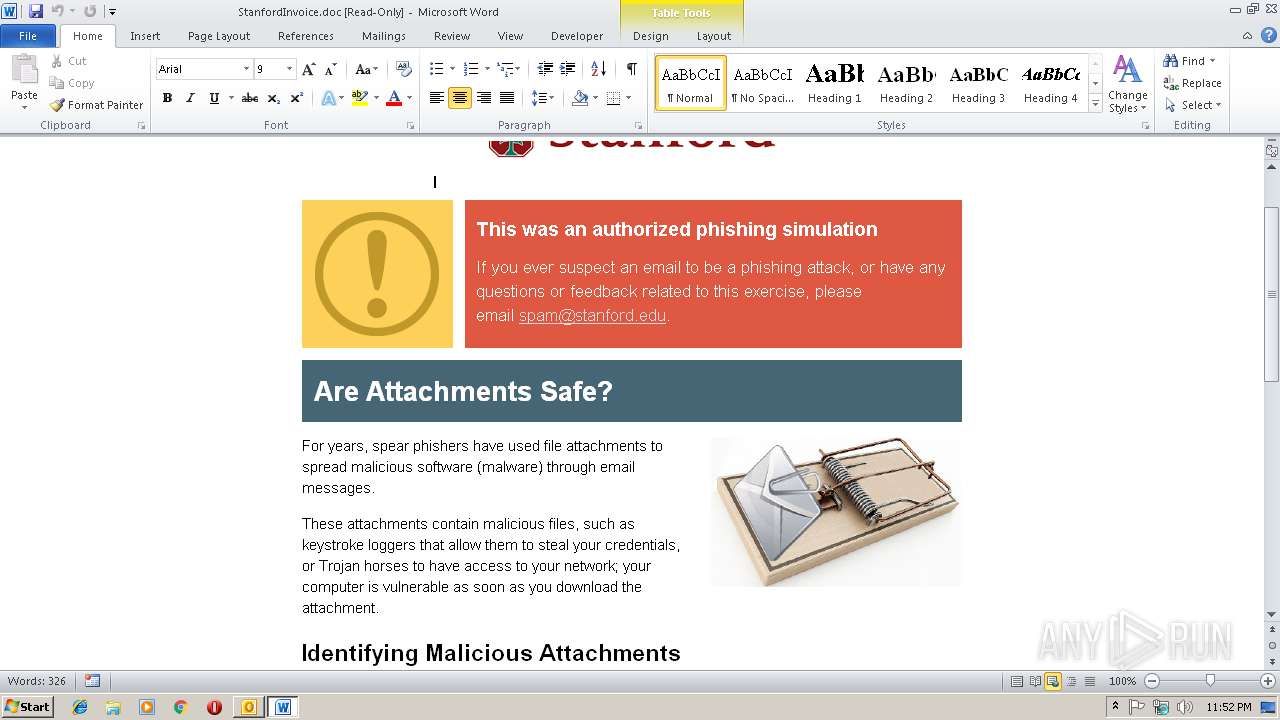
| File name: | Fw Unpaid invoice #4806.msg |
| Full analysis: | https://app.any.run/tasks/7e47a930-cb01-448c-9da6-0c832603d737 |
| Verdict: | Malicious activity |
| Analysis date: | January 17, 2019, 23:51:17 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/vnd.ms-outlook |
| File info: | CDFV2 Microsoft Outlook Message |
| MD5: | DAB0C4205DB908DE8F7A71DB2F60EC1B |
| SHA1: | AAB8B00BAF9F2E1FEB7DDAE18C56091B75D0DC18 |
| SHA256: | AC5D32B43E692F7856B433F002C85D282071F52D9F076EB0165BE437B48A2015 |
| SSDEEP: | 1536:FNAiWBWTlk4iTlsctGmfWDcSZfyceOQY5osWilsH7j55+Ck2shaPmK:FfsxsctnSZfyceOQ7sWilsbje84aPmK |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 2976)
Starts Microsoft Office Application
- OUTLOOK.EXE (PID: 2976)
Creates files in the user directory
- OUTLOOK.EXE (PID: 2976)
Unusual connect from Microsoft Office
- WINWORD.EXE (PID: 3496)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 2976)
- WINWORD.EXE (PID: 3496)
Creates files in the user directory
- WINWORD.EXE (PID: 3496)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msg | | | Outlook Message (58.9) |
|---|---|---|
| .oft | | | Outlook Form Template (34.4) |
Total processes
33
Monitored processes
2
Malicious processes
0
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2976 | "C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE" /f "C:\Users\admin\AppData\Local\Temp\Fw Unpaid invoice #4806.msg" | C:\Program Files\Microsoft Office\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 3496 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\3XT7OR7I\StanfordInvoice.doc" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Exit code: 0 Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
2 686
Read events
1 933
Write events
730
Delete events
23
Modification events
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: On | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\Resiliency\StartupItems |
| Operation: | write | Name: | j-, |
Value: 6A2D2C00A00B0000010000000000000000000000 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook |
| Operation: | write | Name: | MTTT |
Value: A00B00005AD73293BFAED40100000000 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionNumber |
Value: 0 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Outlook\SQM |
| Operation: | write | Name: | SQMSessionDate |
Value: 219869280 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\0a0d020000000000c000000000000046 |
| Operation: | write | Name: | 00030429 |
Value: 03000000 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | {ED475418-B0D6-11D2-8C3B-00104B2A6676} |
Value: | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows NT\CurrentVersion\Windows Messaging Subsystem\Profiles\NoMail\9375CFF0413111d3B88A00104B2A6676 |
| Operation: | write | Name: | LastChangeVer |
Value: 1200000000000000 | |||
| (PID) Process: | (2976) OUTLOOK.EXE | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\UserData\S-1-5-18\Products\00004109A10090400000000000F01FEC\Usage |
| Operation: | write | Name: | OutlookMAPI2Intl_1033 |
Value: 1311834133 | |||
Executable files
0
Suspicious files
24
Text files
31
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE96A.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\3XT7OR7I\StanfordInvoice (2).doc\:Zone.Identifier:$DATA | — | |
MD5:— | SHA256:— | |||
| 3496 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVRFFA1.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3496 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\mso290.tmp | — | |
MD5:— | SHA256:— | |||
| 3496 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{CC0FAB83-29B5-407D-896D-E1B07419E011} | — | |
MD5:— | SHA256:— | |||
| 3496 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\{2CB053D2-B92F-4218-A1AD-496B33EB5434} | — | |
MD5:— | SHA256:— | |||
| 2976 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
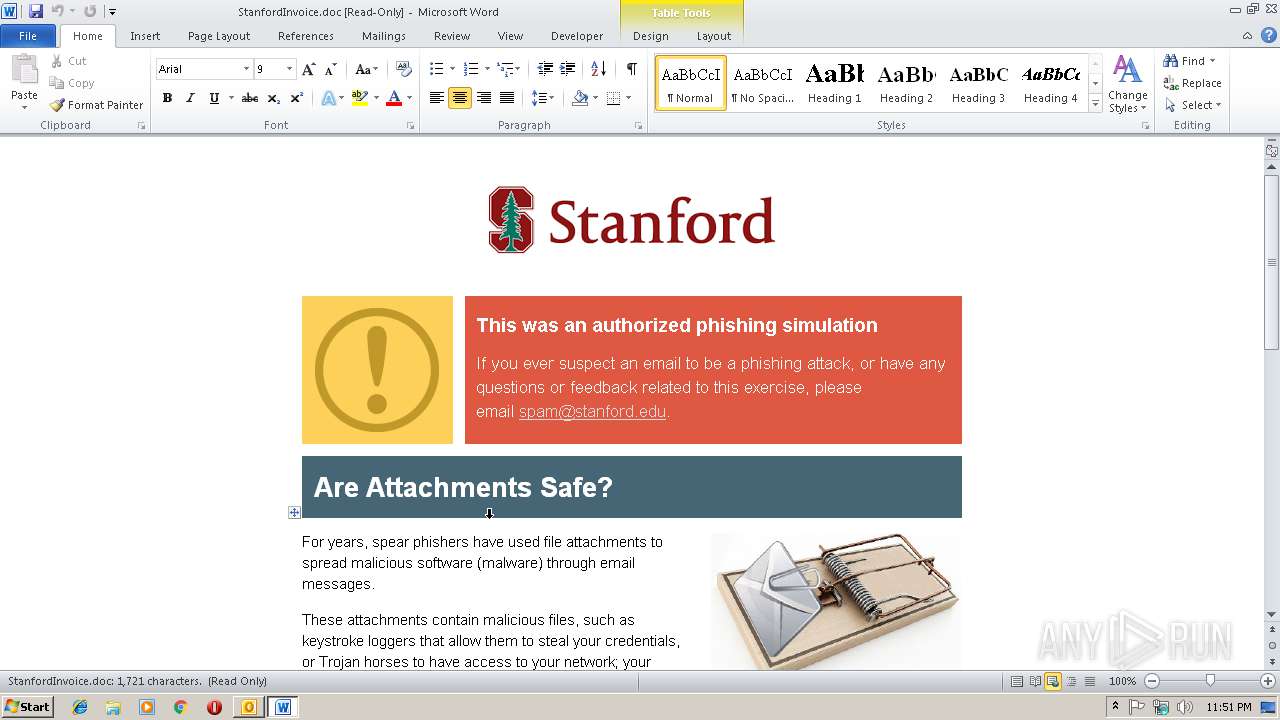
| 2976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.Outlook\3XT7OR7I\StanfordInvoice.doc | html | |
MD5:— | SHA256:— | |||
| 2976 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Microsoft\Outlook\mapisvc.inf | text | |
MD5:48DD6CAE43CE26B992C35799FCD76898 | SHA256:7BFE1F3691E2B4FB4D61FBF5E9F7782FBE49DA1342DBD32201C2CC8E540DBD1A | |||
| 3496 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.MSO\45A8F4CF.png | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
16
TCP/UDP connections
3
DNS requests
3
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2976 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3496 | WINWORD.EXE | OPTIONS | 403 | 13.32.112.152:80 | http://images.pmeimg.com/public/user_assets/db4af2ae-f16b-4e77-bf02-fc3a0b4a8e15/ | US | html | 694 b | shared |
3496 | WINWORD.EXE | OPTIONS | 403 | 13.32.112.152:80 | http://images.pmeimg.com/public/user_assets/db4af2ae-f16b-4e77-bf02-fc3a0b4a8e15/ | US | html | 694 b | shared |
3496 | WINWORD.EXE | GET | 200 | 13.32.112.152:80 | http://images.pmeimg.com/public/user_assets/db4af2ae-f16b-4e77-bf02-fc3a0b4a8e15/su-wide.png | US | image | 4.41 Kb | shared |
3496 | WINWORD.EXE | GET | 200 | 100.24.100.138:80 | http://hbm5g0fj5xh.lucrativehiring.com/c156cdeb-3985-48ae-ba29-af07b04e8b70.png | US | image | 68 b | malicious |
3496 | WINWORD.EXE | OPTIONS | 403 | 100.24.100.138:80 | http://hbm5g0fj5xh.lucrativehiring.com/ | US | text | 16 b | malicious |
3496 | WINWORD.EXE | OPTIONS | 403 | 13.32.112.152:80 | http://images.pmeimg.com/system/content_images/uploads/173/6c8/9c-/original/ | US | html | 694 b | shared |
3496 | WINWORD.EXE | GET | 200 | 13.32.112.152:80 | http://images.pmeimg.com/system/content_images/uploads/173/6c8/9c-/original/warning.png | US | image | 2.57 Kb | shared |
3496 | WINWORD.EXE | GET | 200 | 13.32.112.152:80 | http://images.pmeimg.com/system/content_images/uploads/62e/5fe/03-/original/open-attach.png | US | image | 53.2 Kb | shared |
3496 | WINWORD.EXE | OPTIONS | 403 | 13.32.112.152:80 | http://images.pmeimg.com/system/content_images/uploads/62e/5fe/03-/original/ | US | html | 694 b | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3496 | WINWORD.EXE | 13.32.112.152:80 | images.pmeimg.com | Amazon.com, Inc. | US | malicious |
3496 | WINWORD.EXE | 100.24.100.138:80 | hbm5g0fj5xh.lucrativehiring.com | — | US | suspicious |
2976 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
hbm5g0fj5xh.lucrativehiring.com |
| malicious |
images.pmeimg.com |
| shared |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3496 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |
3496 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |
3496 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |
3496 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |
3496 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |
3496 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |
3496 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |
3496 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |
3496 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |
3496 | WINWORD.EXE | A Network Trojan was detected | SC TROJAN_DOWNLOADER Suspicious DOC loader of embedded OLE from external source |