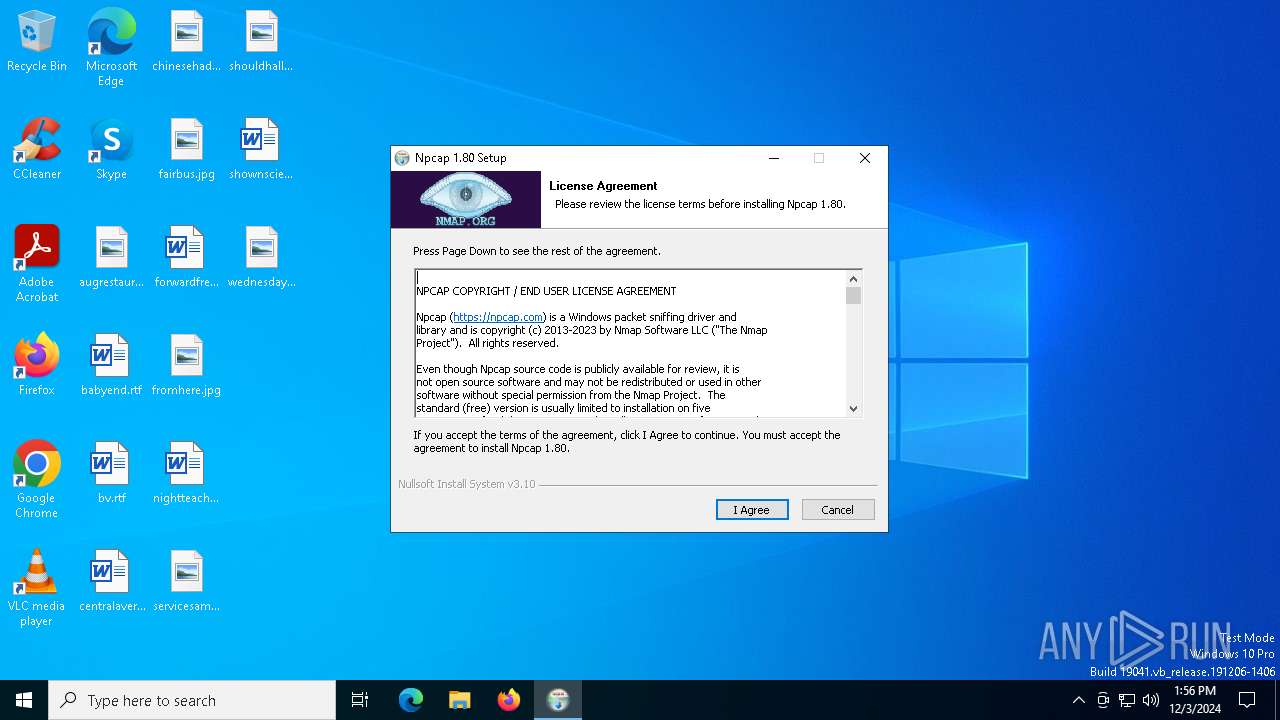
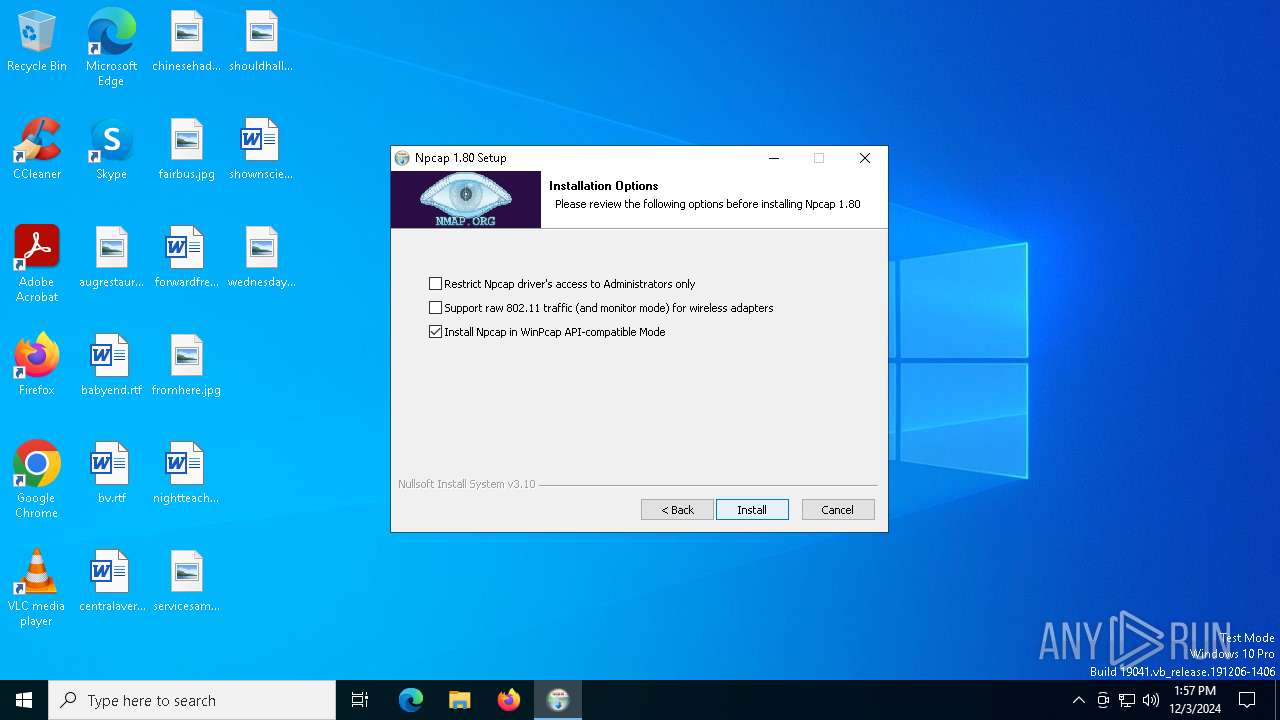
| File name: | npcap-1.80.exe |
| Full analysis: | https://app.any.run/tasks/0c871ab2-a1c9-41df-89cc-e15ca42e8cd3 |
| Verdict: | Malicious activity |
| Analysis date: | December 03, 2024, 13:56:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, Nullsoft Installer self-extracting archive, 5 sections |
| MD5: | BA04898D2FF0674CDF73164530E917A4 |
| SHA1: | BBC1525419B343DF6DD669104D2EA724CD428661 |
| SHA256: | AC4F26D7D9F994D6F04141B2266F02682DEF51AF63C09C96A7268552C94A6535 |
| SSDEEP: | 49152:Q+BLe8EW3DFd7vIzcWIZXF6pDkIDZx640ZM06Mvw9StzegP2A4Xygg21E8WY07Gl:QeLRD5dGtItqbl4MAvnzeS4Tg6JgGeJA |
MALICIOUS
Run PowerShell with an invisible window
- powershell.exe (PID: 3796)
- powershell.exe (PID: 6540)
- powershell.exe (PID: 1804)
- powershell.exe (PID: 6820)
- powershell.exe (PID: 6972)
- powershell.exe (PID: 5696)
SUSPICIOUS
Executable content was dropped or overwritten
- drvinst.exe (PID: 4972)
- npcap-1.80.exe (PID: 6284)
- NPFInstall.exe (PID: 2292)
Malware-specific behavior (creating "System.dll" in Temp)
- npcap-1.80.exe (PID: 6284)
Drops a system driver (possible attempt to evade defenses)
- npcap-1.80.exe (PID: 6284)
- NPFInstall.exe (PID: 2292)
- drvinst.exe (PID: 4972)
The process bypasses the loading of PowerShell profile settings
- npcap-1.80.exe (PID: 6284)
Starts POWERSHELL.EXE for commands execution
- npcap-1.80.exe (PID: 6284)
The process hide an interactive prompt from the user
- npcap-1.80.exe (PID: 6284)
Removes files via Powershell
- powershell.exe (PID: 1804)
- powershell.exe (PID: 6972)
INFO
Checks supported languages
- npcap-1.80.exe (PID: 6284)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2024:03:30 16:56:47+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 28672 |
| InitializedDataSize: | 150528 |
| UninitializedDataSize: | 2048 |
| EntryPoint: | 0x3ae9 |
| OSVersion: | 4 |
| ImageVersion: | 6 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.1.80.821 |
| ProductVersionNumber: | 5.1.80.821 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| FileDescription: | Npcap 1.80 installer |
| FileVersion: | 1.8 |
| LegalCopyright: | Copyright (c) 2023, Insecure.Com LLC. All rights reserved. |
| ProductName: | Npcap |
| ProductVersion: | 1.8 |
Total processes
170
Monitored processes
37
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1076 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | powershell.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1144 | "C:\Users\admin\AppData\Local\Temp\nsz5559.tmp\NPFInstall.exe" -n -check_dll | C:\Users\admin\AppData\Local\Temp\nsz5559.tmp\NPFInstall.exe | — | npcap-1.80.exe | |||||||||||
User: admin Company: Insecure.Com LLC. Integrity Level: HIGH Description: A LWF & WFP driver installation tool Exit code: 0 Version: 1.80 Modules
| |||||||||||||||
| 1804 | powershell.exe -NoProfile -WindowStyle Hidden -NonInteractive -Command "If (Get-ChildItem Cert:\LocalMachine\Root\0563b8630d62d75abbc8ab1e4bdfb5a899b24d43){certutil.exe -verifystore 'Root' '0563b8630d62d75abbc8ab1e4bdfb5a899b24d43';If($LASTEXITCODE -ne 0){Remove-Item Cert:\LocalMachine\Root\0563b8630d62d75abbc8ab1e4bdfb5a899b24d43}}" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | npcap-1.80.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2292 | "C:\Program Files\Npcap\NPFInstall.exe" -n -i | C:\Program Files\Npcap\NPFInstall.exe | npcap-1.80.exe | ||||||||||||
User: admin Company: Insecure.Com LLC. Integrity Level: HIGH Description: A LWF & WFP driver installation tool Exit code: 0 Version: 1.80 Modules
| |||||||||||||||
| 2572 | certutil.exe -addstore -f "TrustedPublisher" "C:\Users\admin\AppData\Local\Temp\nsz5559.tmp\signing.p7b" | C:\Windows\SysWOW64\certutil.exe | — | npcap-1.80.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: CertUtil.exe Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2776 | pnputil.exe -e | C:\Windows\System32\pnputil.exe | — | NPFInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft PnP Utility - Tool to add, delete, export, and enumerate driver packages. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2972 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NPFInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3060 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | pnputil.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3796 | powershell.exe -NoProfile -WindowStyle Hidden -NonInteractive -Command "Microsoft.PowerShell.Management\Start-Service -Name npcap -PassThru | Microsoft.PowerShell.Management\Stop-Service -PassThru | Microsoft.PowerShell.Management\Start-Service" | C:\Windows\SysWOW64\WindowsPowerShell\v1.0\powershell.exe | — | npcap-1.80.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows PowerShell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3840 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | NPFInstall.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
44 971
Read events
44 913
Write events
51
Delete events
7
Modification events
| (PID) Process: | (6284) npcap-1.80.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Npcap |
| Operation: | write | Name: | AdminOnly |
Value: 0 | |||
| (PID) Process: | (6284) npcap-1.80.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Npcap |
| Operation: | write | Name: | WinPcapCompatible |
Value: 1 | |||
| (PID) Process: | (6284) npcap-1.80.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\NpcapInst |
| Operation: | write | Name: | UninstallString |
Value: "C:\Program Files\Npcap\uninstall.exe" | |||
| (PID) Process: | (6284) npcap-1.80.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\NpcapInst |
| Operation: | write | Name: | QuietUninstallString |
Value: "C:\Program Files\Npcap\uninstall.exe" /S | |||
| (PID) Process: | (6284) npcap-1.80.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\NpcapInst |
| Operation: | write | Name: | DisplayIcon |
Value: C:\Program Files\Npcap\uninstall.exe | |||
| (PID) Process: | (6284) npcap-1.80.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Windows\CurrentVersion\Uninstall\NpcapInst |
| Operation: | write | Name: | UninstallPath |
Value: C:\Program Files\Npcap | |||
| (PID) Process: | (6764) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.1!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_CA_REVOCATION | |||
| (PID) Process: | (6764) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.2!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_AUTO_UPDATE_END_REVOCATION | |||
| (PID) Process: | (6764) certutil.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\Cryptography\OID\EncodingType 0\CryptDllFindOIDInfo\1.3.6.1.4.1.311.60.3.3!7 |
| Operation: | write | Name: | Name |
Value: szOID_ROOT_PROGRAM_NO_OCSP_FAILOVER_TO_CRL | |||
| (PID) Process: | (1804) powershell.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\0563B8630D62D75ABBC8AB1E4BDFB5A899B24D43 |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
32
Suspicious files
17
Text files
20
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6284 | npcap-1.80.exe | C:\Users\admin\AppData\Local\Temp\nsz5559.tmp\options.ini | text | |
MD5:825DC90C454EF29D15B3340FD9B5E691 | SHA256:F9FB88B64E7C8845FB2F4DE82D18474B4AAB1B49B03F4D79EA1D143DC0168D8A | |||
| 6284 | npcap-1.80.exe | C:\Users\admin\AppData\Local\Temp\nsz5559.tmp\System.dll | executable | |
MD5:192639861E3DC2DC5C08BB8F8C7260D5 | SHA256:23D618A0293C78CE00F7C6E6DD8B8923621DA7DD1F63A070163EF4C0EC3033D6 | |||
| 6284 | npcap-1.80.exe | C:\Users\admin\AppData\Local\Temp\nsz5559.tmp\nsExec.dll | executable | |
MD5:11092C1D3FBB449A60695C44F9F3D183 | SHA256:2CD3A2D4053954DB1196E2526545C36DFC138C6DE9B81F6264632F3132843C77 | |||
| 6284 | npcap-1.80.exe | C:\Users\admin\AppData\Local\Temp\nsz5559.tmp\NPFInstall.exe | executable | |
MD5:010B8ADC38CFAA9C905ED94281D398FD | SHA256:284BA5A2C487DC1CF764F1491D6A6BEADFB394C700357E4CA71F04EB324AFC07 | |||
| 1144 | NPFInstall.exe | C:\Program Files\Npcap\NPFInstall.log | text | |
MD5:ECAA88F7FA0BF610A5A26CF545DCD3AA | SHA256:F1945CD6C19E56B3C1C78943EF5EC18116907A4CA1EFC40A57D48AB1DB7ADFC5 | |||
| 6284 | npcap-1.80.exe | C:\Program Files\Npcap\DiagReport.bat | text | |
MD5:B82606A6AFB3777D62E35E8D9850FAED | SHA256:0843361F05255E3970ED955171C20003238756C57137FEF9AC19D29FBD49F9F6 | |||
| 6284 | npcap-1.80.exe | C:\Users\admin\AppData\Local\Temp\nsz5559.tmp\final.ini | text | |
MD5:C2992DF0C584A29B8FB2107D5697A730 | SHA256:8AE8385DCC63A47B0EA21BB971E2BFA463DD17F20966F61C8A77E080859F80BD | |||
| 6284 | npcap-1.80.exe | C:\Users\admin\AppData\Local\Temp\nsz5559.tmp\modern-header.bmp | image | |
MD5:B514F98A3DF2F23FB0FDF170FA772F5C | SHA256:F22D49EEC7926CDE60DAD056A3A9FA844327F759F38E76BAD4C3119A57E37888 | |||
| 6284 | npcap-1.80.exe | C:\Program Files\Npcap\DiagReport.ps1 | text | |
MD5:0B4DF7D19ADE75BEE930D54BE31AC09C | SHA256:27EB36CB165C6EDD2F55B72A6856E4BF32AE2FA6CADFFCD267F5DF96EEA0B011 | |||
| 6284 | npcap-1.80.exe | C:\Users\admin\AppData\Local\Temp\nsz5559.tmp\InstallOptions.dll | executable | |
MD5:D1EEFB07ABC2577DFB92EB2E95A975E4 | SHA256:89DD7D646278D8BFC41D5446BDC348B9A9AFAA832ABF02C1396272BB7AC7262A | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
32
DNS requests
18
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5004 | svchost.exe | GET | 200 | 23.48.23.176:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1176 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
5004 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6364 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
3836 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3836 | SIHClient.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5004 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3508 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5064 | SearchApp.exe | 92.123.104.10:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1176 | svchost.exe | 40.126.32.76:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
1176 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1076 | svchost.exe | 69.192.162.125:443 | go.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
login.live.com |
| whitelisted |
go.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |