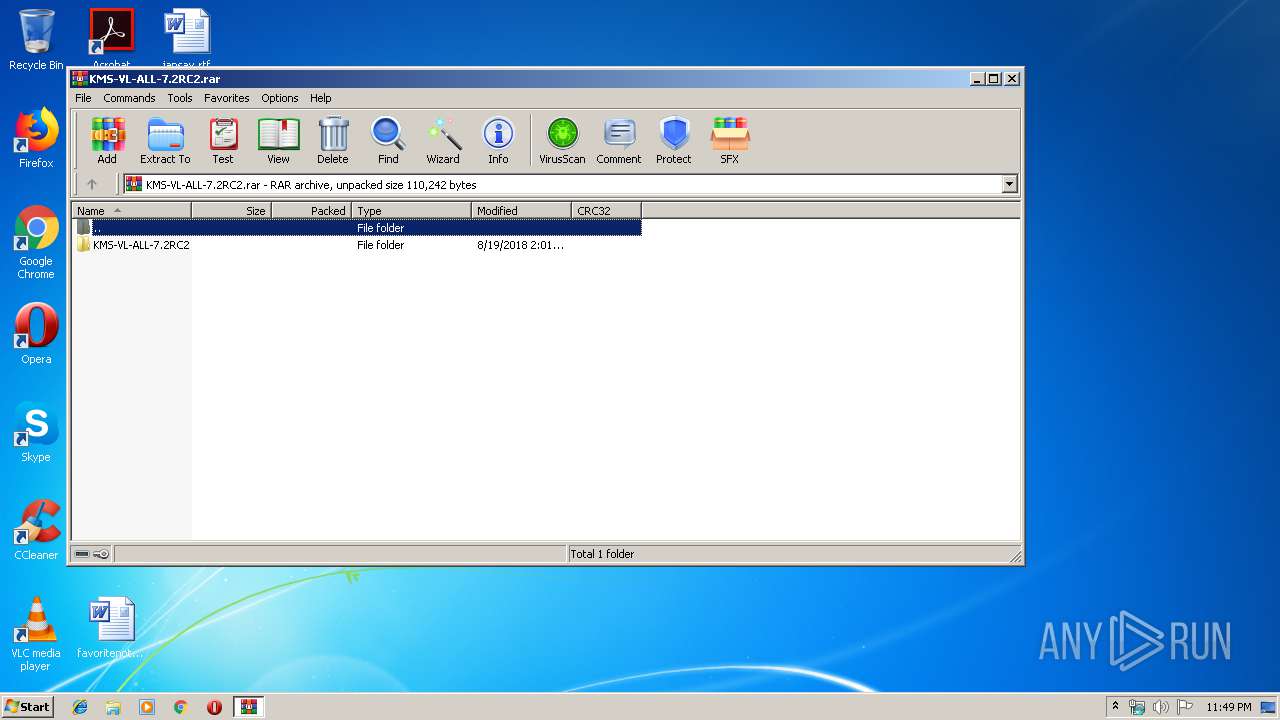
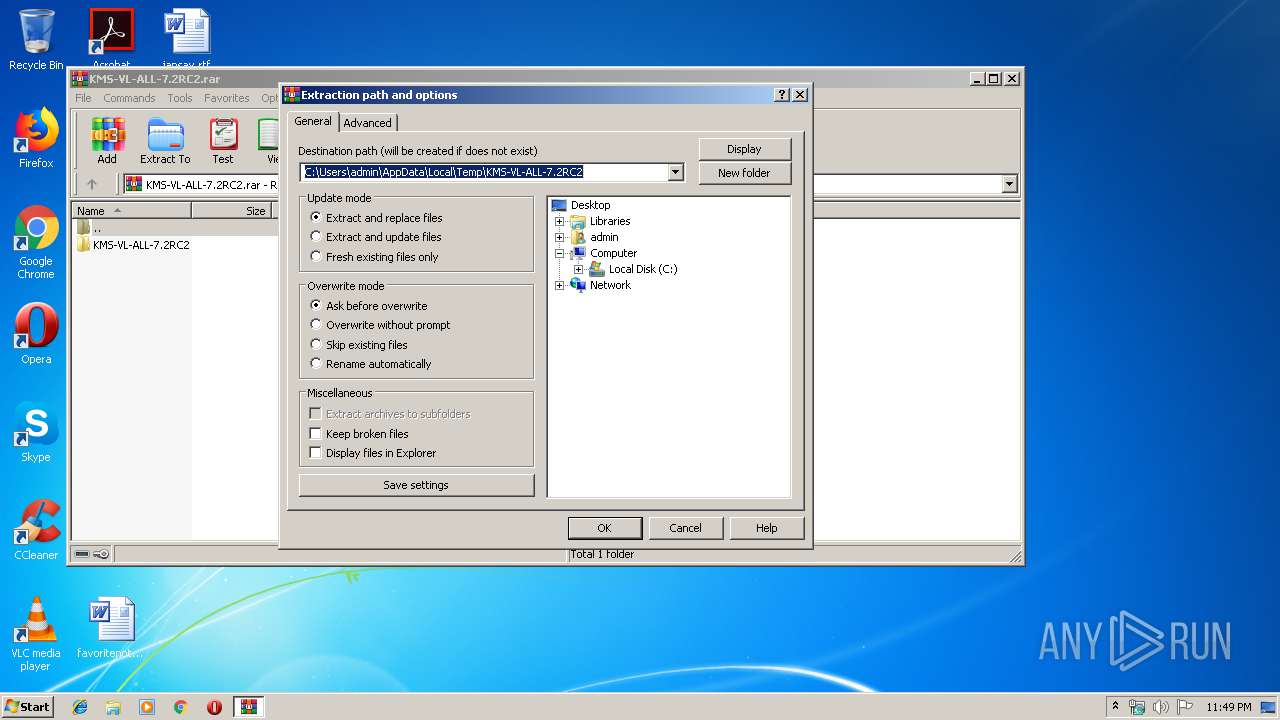
| File name: | KMS-VL-ALL-7.2RC2.rar |
| Full analysis: | https://app.any.run/tasks/51e68c78-6bc7-4013-98f8-679c38ca1fe5 |
| Verdict: | Malicious activity |
| Analysis date: | October 03, 2019, 22:48:53 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | BF77BD08C97554AF6D10804CF8E71AE8 |
| SHA1: | F783AFADDD36C8872DD58F9ED6F5ECC81CEFCD3D |
| SHA256: | AC4C6AAFAC3C7239DE74F35DABECEC343C29B826AFB4EED3BAF02FDB7C0685AD |
| SSDEEP: | 768:ALa5Du7wjtsuttodTvWyRhJE2Y8X3U2GoD+Lh6K8YyhNbWMHh6+TfXYLMqVWBEl2:ALqq7O2izh8BG4+LKYaHh6QfXUVAF |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 1908)
Uses Task Scheduler to run other applications
- cmd.exe (PID: 4032)
Loads the Task Scheduler COM API
- schtasks.exe (PID: 3228)
Runs PING.EXE for delay simulation
- cmd.exe (PID: 4032)
Application was dropped or rewritten from another process
- vlmcsd.exe (PID: 3596)
- vlmcsd.exe (PID: 3580)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2936)
Application launched itself
- cmd.exe (PID: 2560)
- cmd.exe (PID: 4032)
Starts CMD.EXE for commands execution
- cmd.exe (PID: 2560)
- WScript.exe (PID: 2520)
- cmd.exe (PID: 4032)
Executes scripts
- cmd.exe (PID: 2560)
Uses WMIC.EXE to obtain a system information
- cmd.exe (PID: 4032)
- cmd.exe (PID: 2516)
- cmd.exe (PID: 3396)
- cmd.exe (PID: 3408)
- cmd.exe (PID: 3660)
- cmd.exe (PID: 4024)
- cmd.exe (PID: 3048)
- cmd.exe (PID: 2656)
Uses REG.EXE to modify Windows registry
- cmd.exe (PID: 2216)
- cmd.exe (PID: 2876)
- cmd.exe (PID: 3656)
- cmd.exe (PID: 2316)
- cmd.exe (PID: 2444)
- cmd.exe (PID: 3840)
- cmd.exe (PID: 3904)
- cmd.exe (PID: 2692)
- cmd.exe (PID: 3076)
- cmd.exe (PID: 4032)
Uses NETSH.EXE for network configuration
- cmd.exe (PID: 4032)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 4032)
INFO
Manual execution by user
- cmd.exe (PID: 2560)
- vlmcsd.exe (PID: 3580)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
135
Monitored processes
92
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 616 | reg query HKLM\SOFTWARE\Microsoft\Office\14.0\Common\InstallRoot /v Path | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 972 | wmic path Win32_Processor get AddressWidth /value | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1040 | wmic path SoftwareLicensingProduct where (Description like '%KMSCLIENT%' and PartialProductKey is not NULL) get Name /value | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1492 | reg query HKLM\SOFTWARE\Microsoft\VisualStudio\14.0 /v InstallDir | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1908 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe4_ Global\UsGthrCtrlFltPipeMssGthrPipe4 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2148 | findstr /i "KMS_VL_ALL" | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2148 | findstr /i "Windows" | C:\Windows\system32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2200 | reg delete "HKLM\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SoftwareProtectionPlatform\55c92734-d682-4d71-983e-d6ec3f16059f" /f | C:\Windows\system32\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Console Tool Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2216 | C:\Windows\system32\cmd.exe /c "reg query HKLM\SOFTWARE\Microsoft\Office\14.0\Common\InstallRoot /v Path" 2>nul | C:\Windows\system32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2220 | wmic path SoftwareLicensingProduct where ID='b92e9980-b9d5-4821-9c94-140f632f6312' get LicenseStatus | C:\Windows\System32\Wbem\WMIC.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: WMI Commandline Utility Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
2 155
Read events
1 982
Write events
173
Delete events
0
Modification events
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\KMS-VL-ALL-7.2RC2.rar | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2936) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\DialogEditHistory\ExtrPath |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop | |||
| (PID) Process: | (1908) SearchProtocolHost.exe | Key: | HKEY_USERS\.DEFAULT\Software\Classes\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
3
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2936 | WinRAR.exe | C:\Users\admin\Desktop\KMS-VL-ALL-7.2RC2\32-bit\SECOPatcher.dll | executable | |
MD5:E0F0683BB8CFD4413ECCD777034E6A20 | SHA256:31CFC14E37DF7DECE15E696966AF362098BF04D6CFFFAE780412D98CC90EADD4 | |||
| 2560 | cmd.exe | C:\Users\admin\AppData\Local\Temp\GetAdmin.vbs | binary | |
MD5:— | SHA256:— | |||
| 2936 | WinRAR.exe | C:\Users\admin\Desktop\KMS-VL-ALL-7.2RC2\KMS-VL-ALL.cmd | text | |
MD5:3884E33482ADEFBC15D0D5A4CCBF6EF6 | SHA256:801350DAE74DAF1EF4CB61685EAE51464AC02D910C6A2371D60D75A214CE7D6F | |||
| 2936 | WinRAR.exe | C:\Users\admin\Desktop\KMS-VL-ALL-7.2RC2\64-bit\SECOPatcher.dll | executable | |
MD5:5C5DC1D8085A9DF4CC44F5F39630297D | SHA256:A6B7BCC8E941A7AAFB8C077DC4B17344A965E7E0DA0F012D24F27B982434850E | |||
| 2936 | WinRAR.exe | C:\Users\admin\Desktop\KMS-VL-ALL-7.2RC2\32-bit\vlmcsd.exe | executable | |
MD5:3199D660B6D2DA836FCABCA41ECBC0E5 | SHA256:BFC3DB2E8D0BCA6F4E189191D5500D6D6B5D9CE83C3EE379253CC20505FA24C3 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report