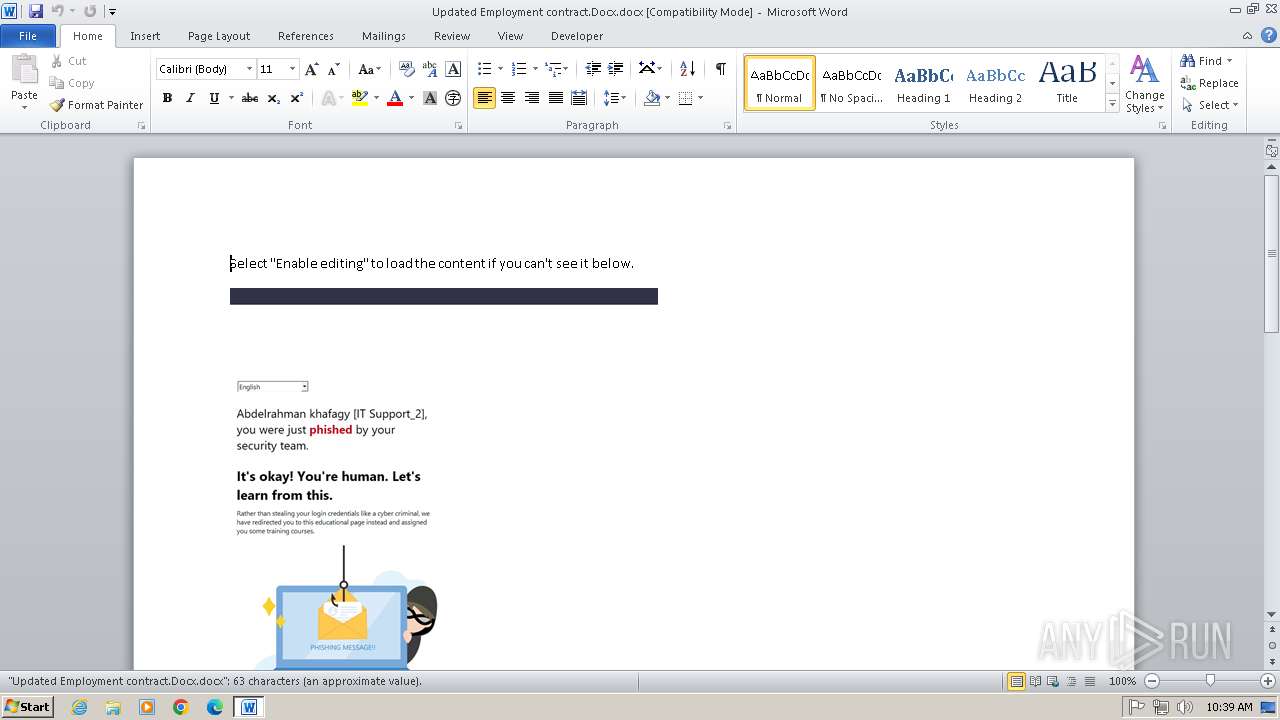
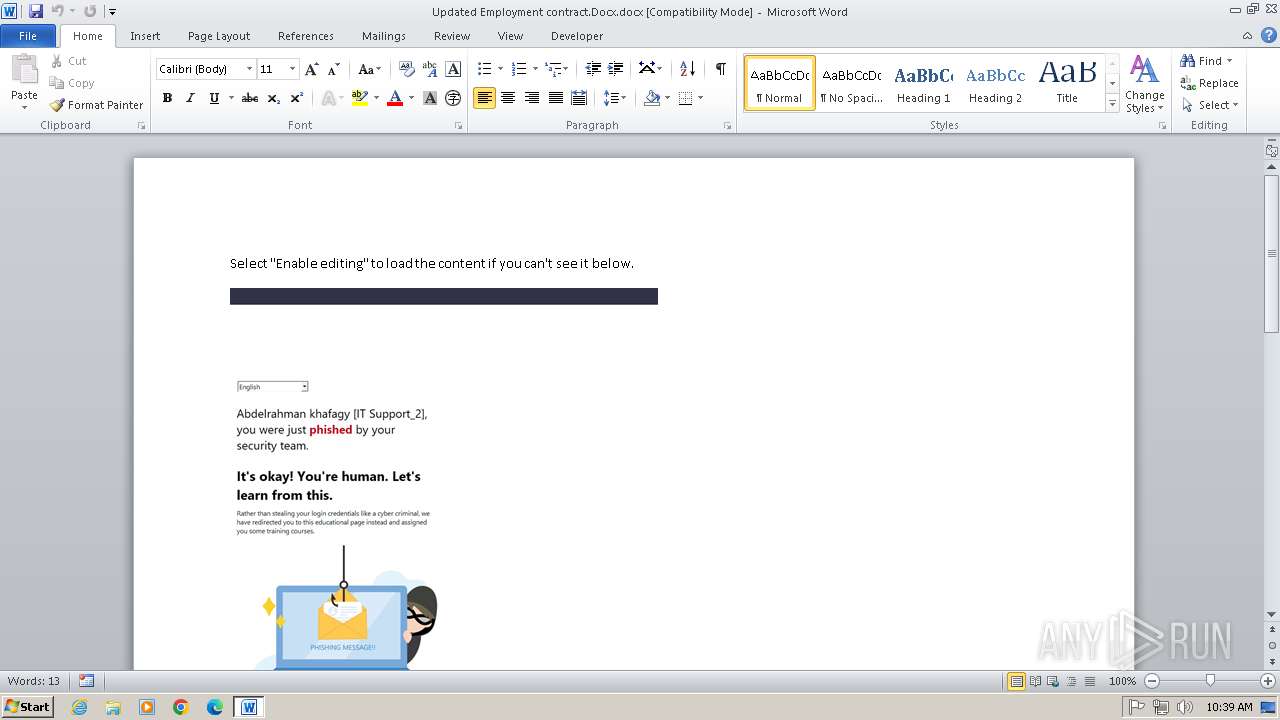
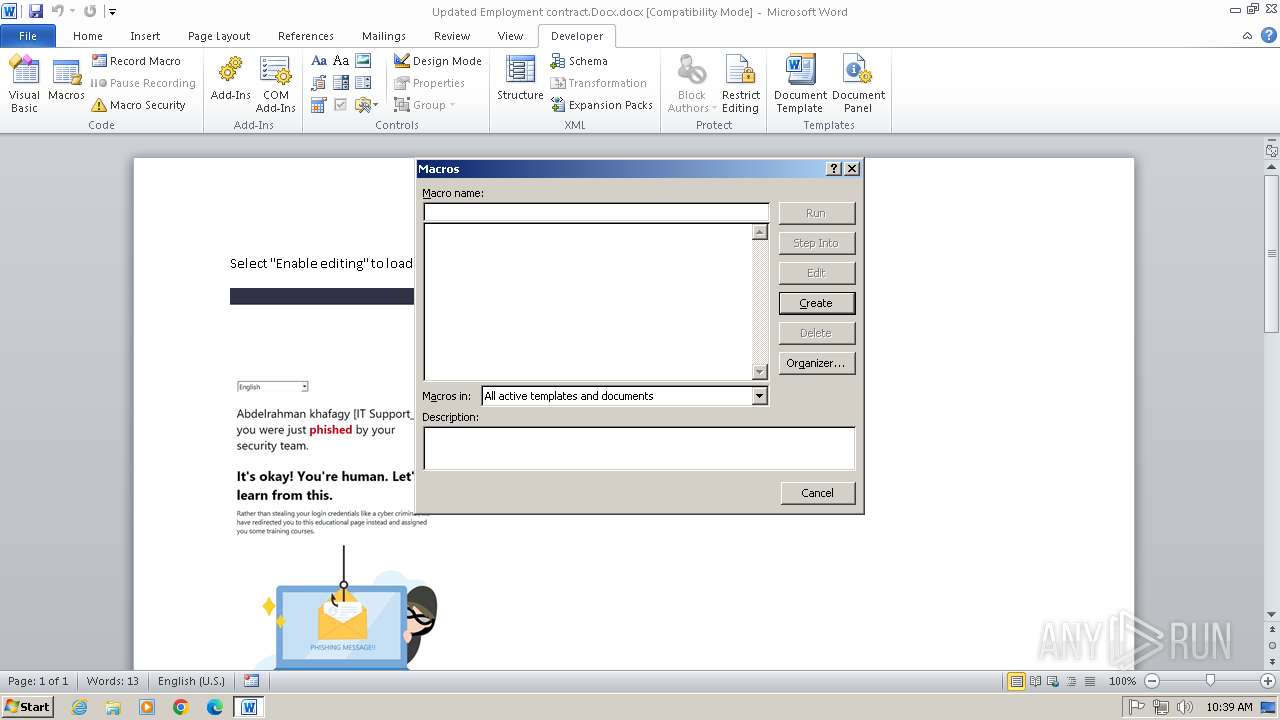
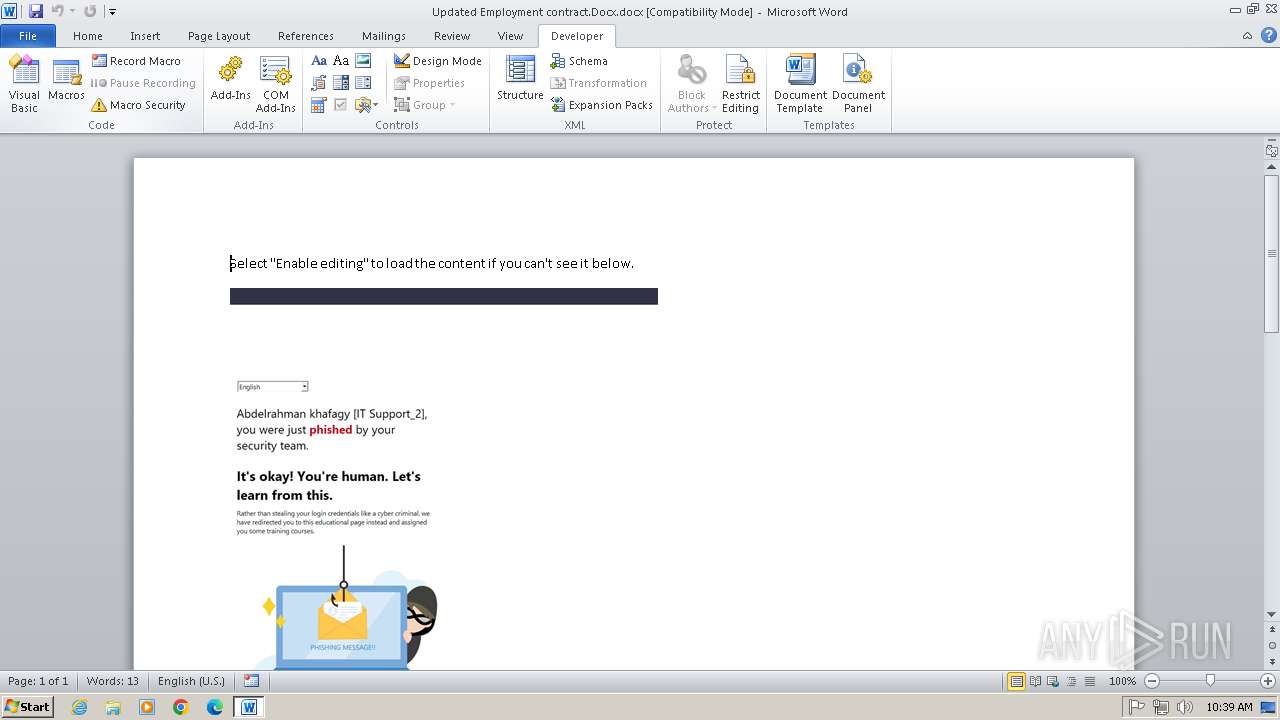
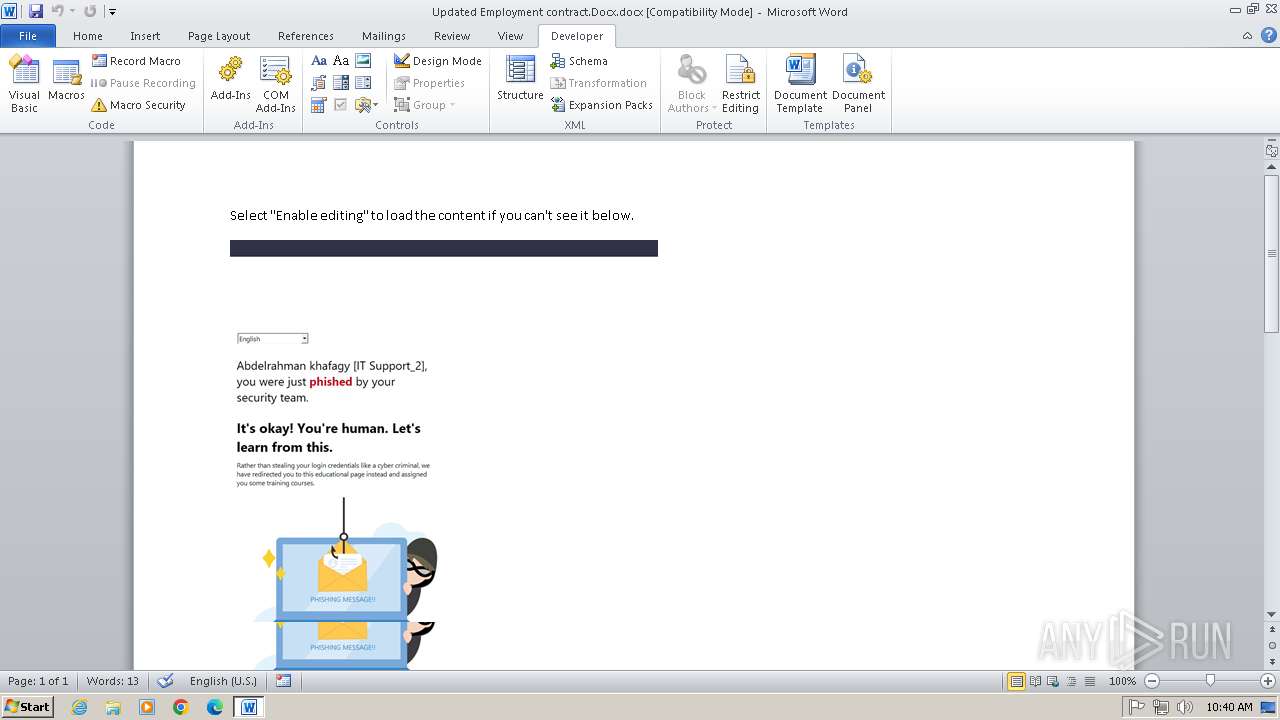
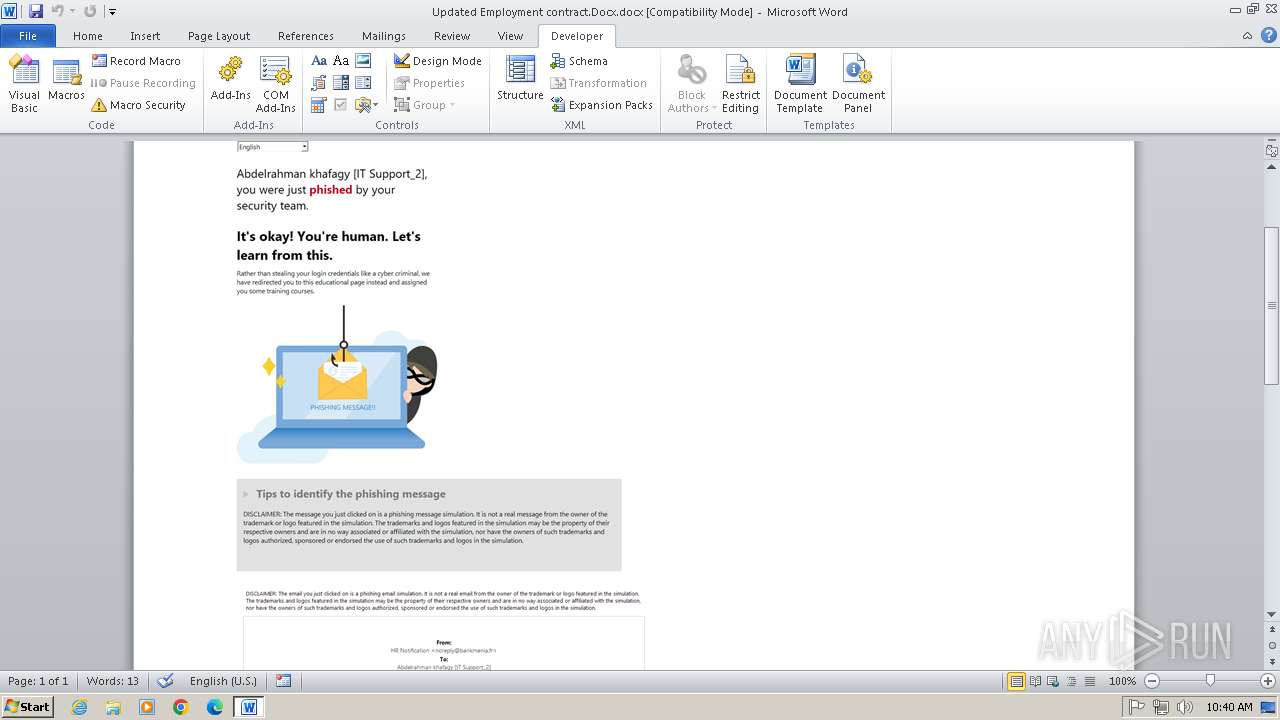
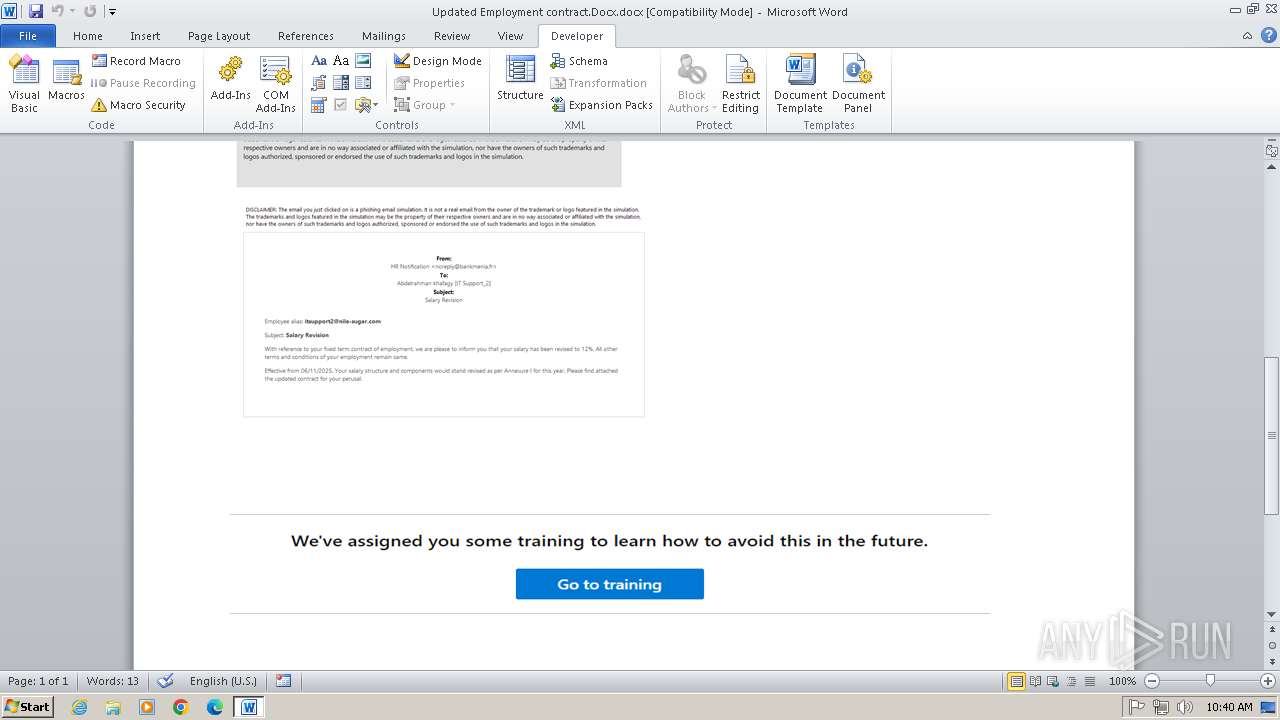
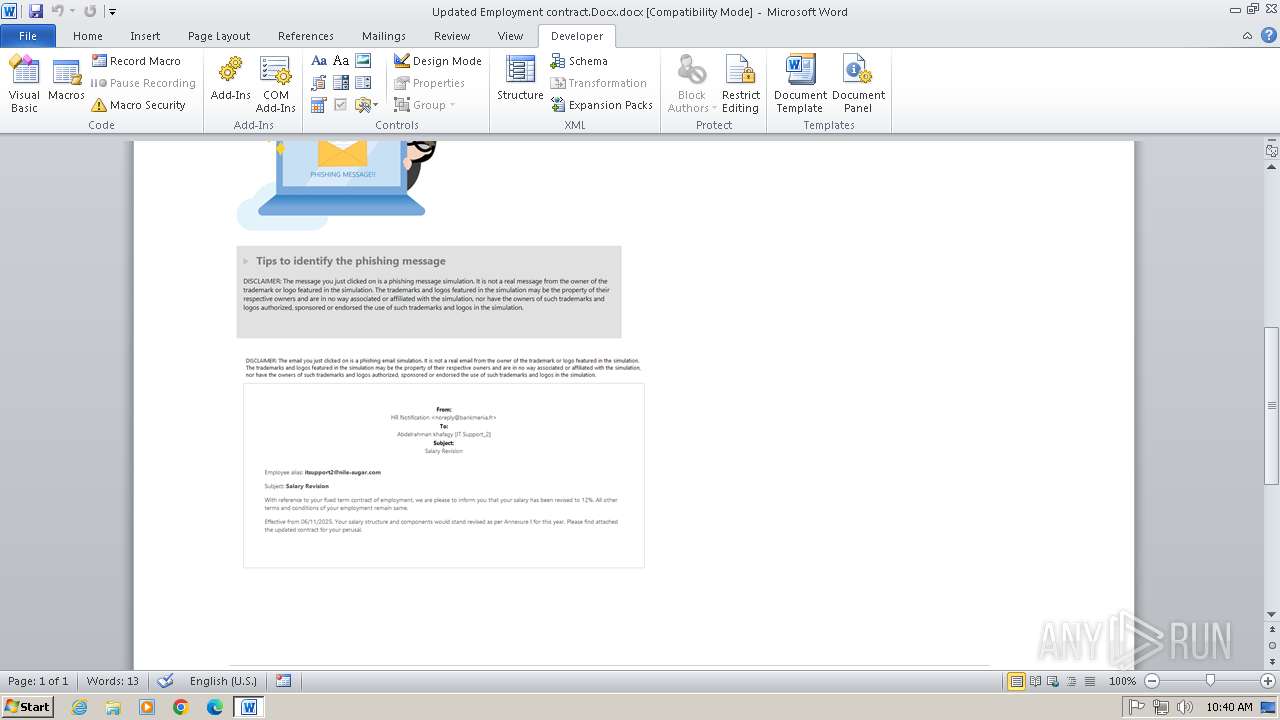
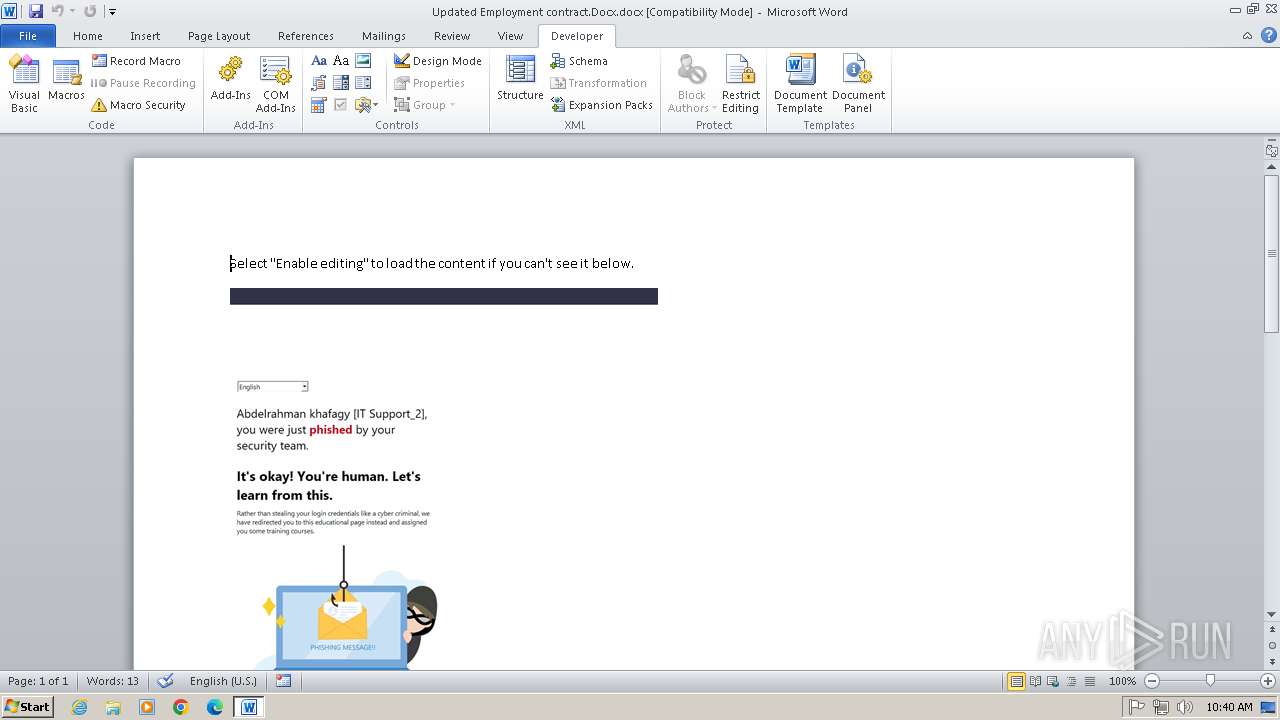
| File name: | Updated Employment contract.Docx |
| Full analysis: | https://app.any.run/tasks/ce5caac6-8794-41b6-a36d-b7c477c03cb7 |
| Verdict: | Malicious activity |
| Analysis date: | June 18, 2025, 09:39:36 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.openxmlformats-officedocument.wordprocessingml.document |
| File info: | Microsoft Word 2007+ |
| MD5: | 0357F7CFC5448BAF54C563749B72206D |
| SHA1: | B4A3E1FF27D4BCDC0DEE3E4122FF8D0B97FA729F |
| SHA256: | AC4B652892CB42CD724C79765B95B22EF9E70DA46140B45186884641532A344B |
| SSDEEP: | 192:mCLU+siYLnXbfwknN/M1naj6mbj6nblnH6un2XVUjhQ:mXjzrnN/wVpblHZ2ahQ |
MALICIOUS
PHISHING has been detected (SURICATA)
- svchost.exe (PID: 1080)
SUSPICIOUS
No suspicious indicators.INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .docx | | | Word Microsoft Office Open XML Format document (52.2) |
|---|---|---|
| .zip | | | Open Packaging Conventions container (38.8) |
| .zip | | | ZIP compressed archive (8.8) |
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2025:06:11 10:24:24 |
| ZipCRC: | 0xfdb6e475 |
| ZipCompressedSize: | 306 |
| ZipUncompressedSize: | 713 |
| ZipFileName: | word/document.xml |
Total processes
35
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1080 | C:\Windows\system32\svchost.exe -k NetworkService | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3068 | "C:\Program Files\Microsoft Office\Office14\WINWORD.EXE" /n "C:\Users\admin\AppData\Local\Temp\Updated Employment contract.Docx.docx" | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Word Version: 14.0.6024.1000 Modules
| |||||||||||||||
Total events
13 899
Read events
13 006
Write events
611
Delete events
282
Modification events
| (PID) Process: | (3068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3068) WINWORD.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
15
Text files
3
Unknown types
5
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3068 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\CVR2110.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3068 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | pgc | |
MD5:19C57C60E19DBCE27F6478C3B6BDAE0E | SHA256:CEB02504CF0662570FDB98ACC49BDC2063F3C3132141553F455C1E39945554E9 | |||
| 3068 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\~$dated Employment contract.Docx.docx | pgc | |
MD5:7E219B6749B0572271CD29D15F952B9B | SHA256:CE00898E8F5BD0741104E9BE99FB689D583F1B08491EA7D9BD1A8F0528323AEF | |||
| 3068 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:875F18517F94EA206523A2B86E85D418 | SHA256:330CD2FD551CFADBAAC00555E7EE7B20F56A04BD58DD0C69F89381710CD2F215 | |||
| 3068 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_CBDCCBFE4F7A916411C1E69BDD97BB04 | der | |
MD5:32B51762E7CB871F2422CF926160C554 | SHA256:590D2A41004120B54D0485B038CE3571B23C63F5EECFD197E3DA85A50D3166E5 | |||
| 3068 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\2CB6B8BACCDF3D4DD9099BF71ACA4698_C09F435942F02F8C48E9E63624A37C5B | binary | |
MD5:CF8EDD99185705A846A91AF05618FB3F | SHA256:72780C7DCE24E570530CA91113E20A68457133705F5780A6136E060D8C48ED0E | |||
| 3068 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:77B20B5CD41BC6BB475CCA3F91AE6E3C | SHA256:5511A9B9F9144ED7BDE4CCB074733B7C564D918D2A8B10D391AFC6BE5B3B1509 | |||
| 3068 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\2CB6B8BACCDF3D4DD9099BF71ACA4698_C09F435942F02F8C48E9E63624A37C5B | der | |
MD5:AECB8278B9CB816CBF1FFDA451711688 | SHA256:CEAA62F8866DBC054950B1EDA29FA3E1EB5626844BD50812B941E44169C4B4DE | |||
| 3068 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSD-{112104A0-0496-4123-A8A9-3DBB07136638}.FSD | binary | |
MD5:CE70E5BA4D3B2520A28D112CAA7EDE8D | SHA256:09F792AB55D282C3A58A455D1E4E1042067641FD70C11E519FABAA4525F158EF | |||
| 3068 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\14.0\OfficeFileCache\LocalCacheFileEditManager\FSF-{0E1EEE64-E8C6-4E2A-9759-63CF07FD8988}.FSF | binary | |
MD5:D471A0BB5F0B8A9AC834E0172491B7F9 | SHA256:418B6AE0A39787583DCD77DA0ED040F8C3DDA03410E71D04C235EE6E736F298F | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
15
DNS requests
5
Threats
10
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3068 | WINWORD.EXE | GET | 200 | 199.232.210.172:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f06851bd0f7fc773 | unknown | — | — | whitelisted |
3068 | WINWORD.EXE | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEApDqVCbATUviZV57HIIulA%3D | unknown | — | — | whitelisted |
3068 | WINWORD.EXE | GET | 200 | 204.79.197.203:80 | http://oneocsp.microsoft.com/ocsp/MFQwUjBQME4wTDAJBgUrDgMCGgUABBR2JNtr0JxEvYySpbyBWaqBmealCgQUzhUWO%2BoCo6Zr2tkr%2FeWMUr56UKgCEzMBzZx466XemkKEB7sAAAHNnHg%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
3068 | WINWORD.EXE | 13.107.253.45:443 | www.mcsharepoint.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | suspicious |
3068 | WINWORD.EXE | 199.232.210.172:80 | ctldl.windowsupdate.com | FASTLY | US | whitelisted |
3068 | WINWORD.EXE | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
3068 | WINWORD.EXE | 204.79.197.203:80 | oneocsp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.mcsharepoint.com |
| unknown |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
oneocsp.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
3068 | WINWORD.EXE | Misc activity | ET INFO Observed Microsoft Attack Simulation Training SSL Cert (attemplate .com) |
1080 | svchost.exe | Misc activity | ET INFO Microsoft Attack Simulation Training Domain in DNS Lookup (mcsharepoint .com) |
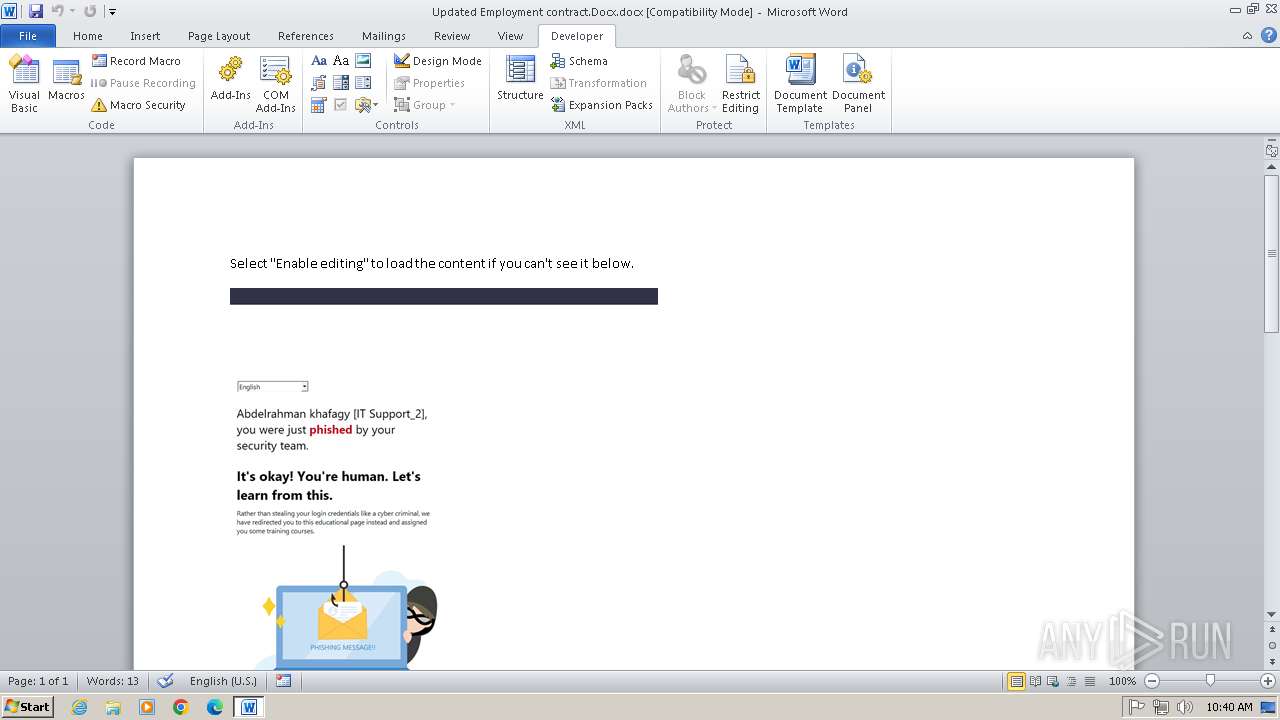
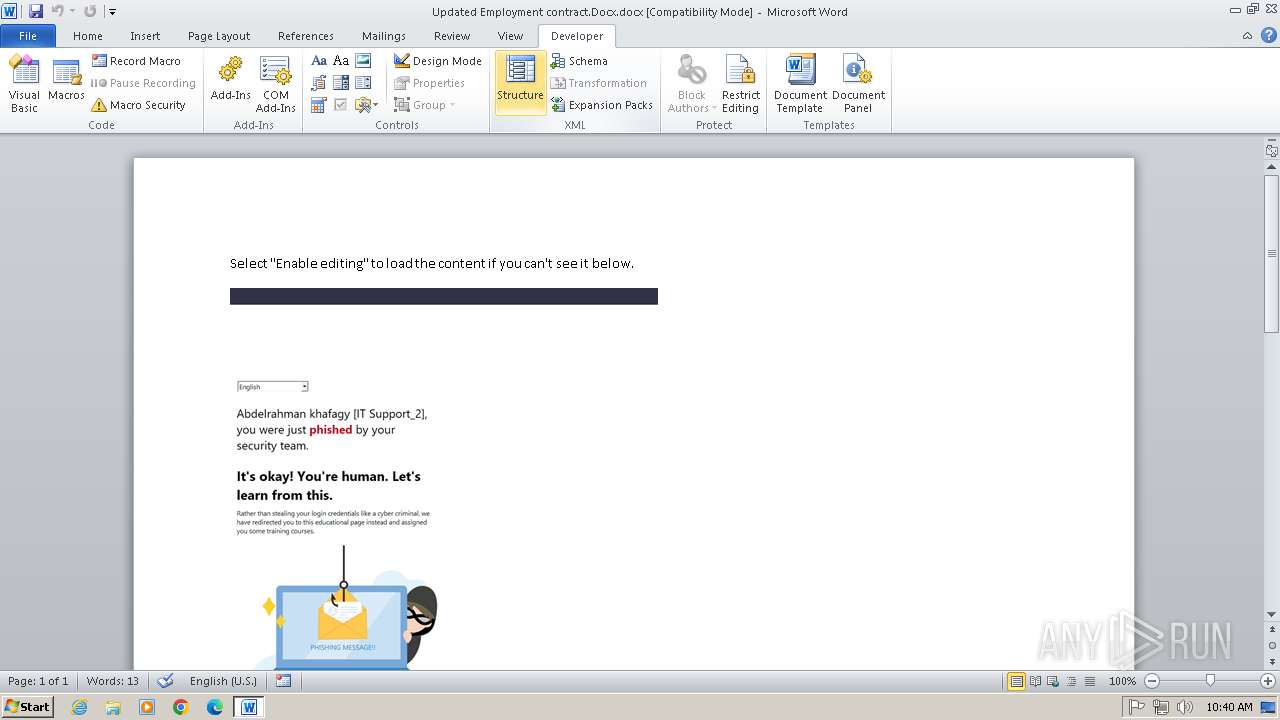
1080 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Suspected Microsoft Phishing Training (www .mcsharepoint .com) |
1080 | svchost.exe | Possible Social Engineering Attempted | PHISHING [ANY.RUN] Domain identified as part of Phishing Training (mcsharepoint .com) |
3068 | WINWORD.EXE | Misc activity | ET INFO Observed Microsoft Attack Simulation Training SSL Cert (attemplate .com) |
3068 | WINWORD.EXE | Misc activity | ET INFO Observed Microsoft Attack Simulation Training SSL Cert (attemplate .com) |
3068 | WINWORD.EXE | Misc activity | ET INFO Observed Microsoft Attack Simulation Training SSL Cert (attemplate .com) |
3068 | WINWORD.EXE | Misc activity | ET INFO Observed Microsoft Attack Simulation Training SSL Cert (attemplate .com) |
3068 | WINWORD.EXE | Misc activity | ET INFO Observed Microsoft Attack Simulation Training SSL Cert (attemplate .com) |
3068 | WINWORD.EXE | Misc activity | ET INFO Observed Microsoft Attack Simulation Training SSL Cert (attemplate .com) |