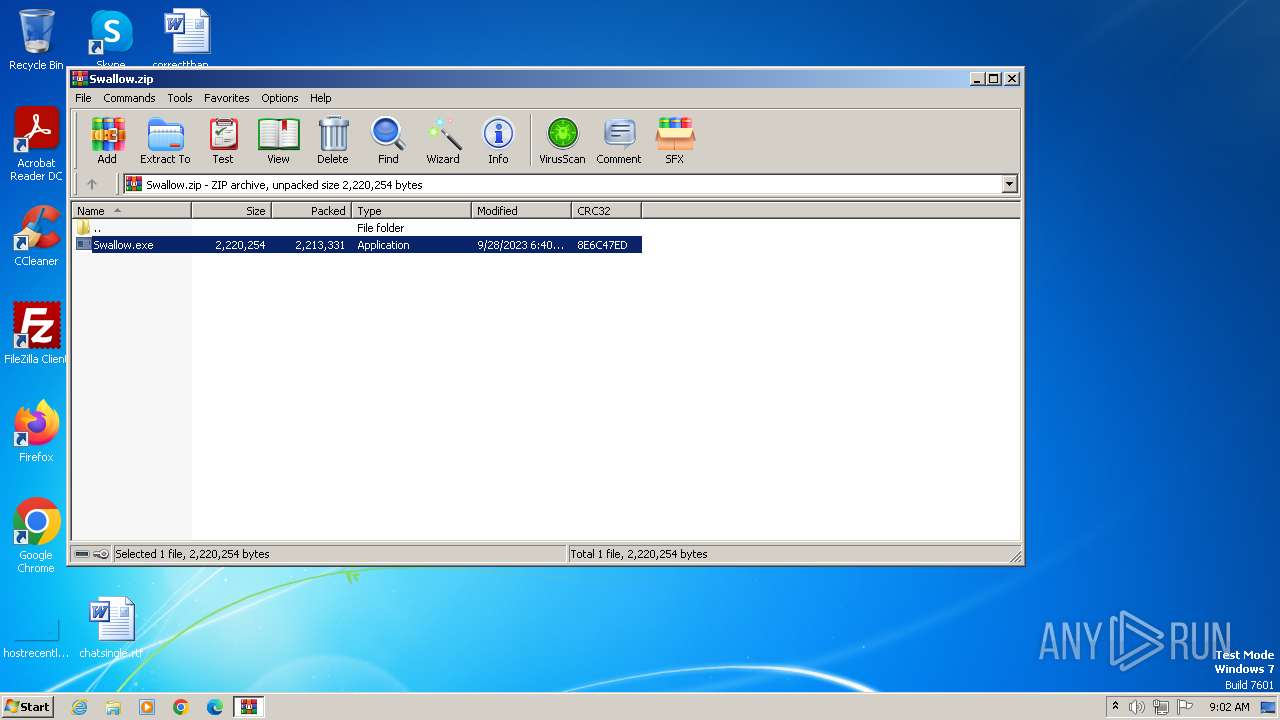
| File name: | Swallow.zip |
| Full analysis: | https://app.any.run/tasks/e8975693-8e64-4519-a995-0d8064db6ea3 |
| Verdict: | Malicious activity |
| Analysis date: | October 08, 2023, 08:02:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | F5B07D383D6432B84311FE1AB2398EAB |
| SHA1: | C71166478B35BFD79A681C22CD7FC8A5A6722E2D |
| SHA256: | AC40EBEA5D01F113CCBFD6BD11913D0C8E73E4606827F6BACF4A871EF367ACC9 |
| SSDEEP: | 98304:FFTJ2TCvCXlzEymvJvK9GdKoI/AA5qqtNqV0TSc8u1xRhYKoKXLVVEcRUHLugiyN:FPyzByZgMX |
MALICIOUS
Application was dropped or rewritten from another process
- Swallow.exe (PID: 3644)
- Swallow.exe (PID: 3440)
Creates a writable file the system directory
- Swallow.exe (PID: 3440)
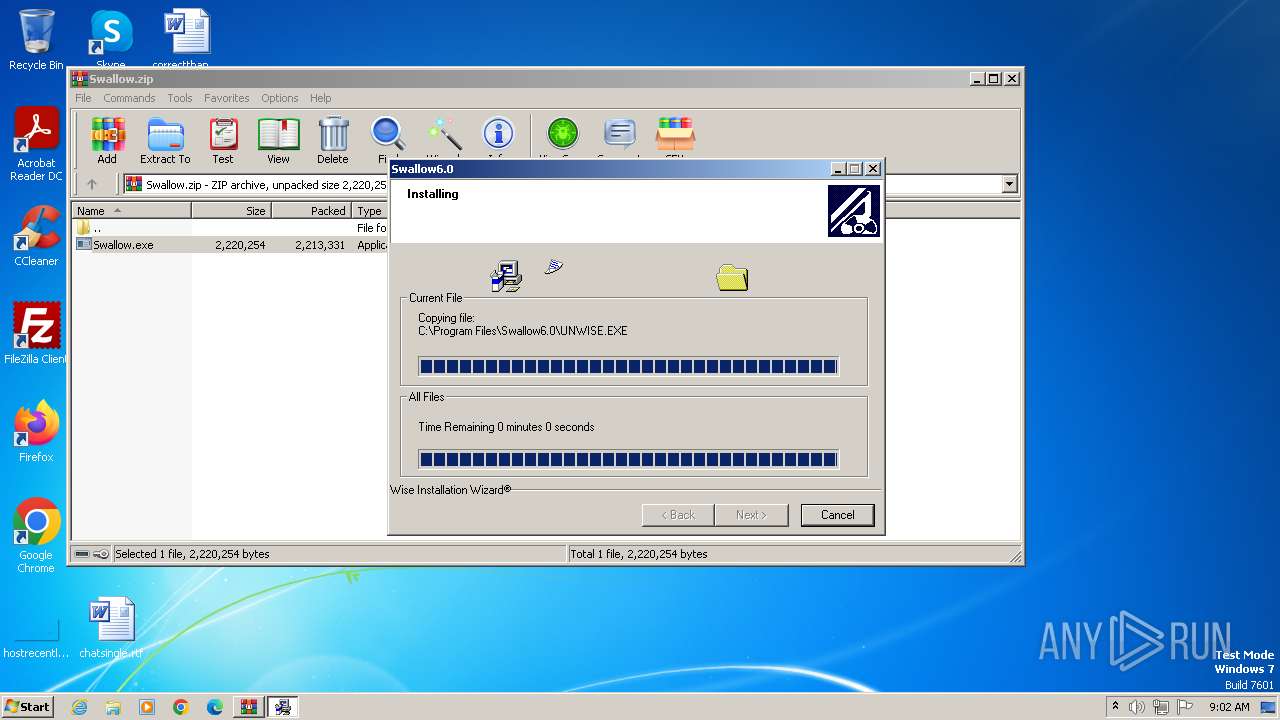
Drops the executable file immediately after the start
- Swallow.exe (PID: 3440)
Registers / Runs the DLL via REGSVR32.EXE
- cmd.exe (PID: 3140)
SUSPICIOUS
Starts CMD.EXE for commands execution
- cmd.exe (PID: 3140)
- Swallow.exe (PID: 3440)
Executing commands from a ".bat" file
- Swallow.exe (PID: 3440)
Reads the Internet Settings
- Swallow.exe (PID: 3440)
Using 'findstr.exe' to search for text patterns in files and output
- cmd.exe (PID: 3140)
Application launched itself
- cmd.exe (PID: 3140)
INFO
Drops the executable file immediately after the start
- WinRAR.exe (PID: 2484)
- expand.exe (PID: 1828)
Creates files in the program directory
- cmd.exe (PID: 3140)
- Swallow.exe (PID: 3440)
Checks supported languages
- Swallow.exe (PID: 3440)
Create files in a temporary directory
- Swallow.exe (PID: 3440)
Reads the computer name
- Swallow.exe (PID: 3440)
Checks operating system version
- cmd.exe (PID: 3140)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2023:09:29 00:41:00 |
| ZipCRC: | 0x8e6c47ed |
| ZipCompressedSize: | 2213331 |
| ZipUncompressedSize: | 2220254 |
| ZipFileName: | Swallow.exe |
Total processes
49
Monitored processes
12
Malicious processes
4
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1828 | EXPAND [-r] Swallow.cab . | C:\Windows\System32\expand.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: LZ Expansion Utility Exit code: 0 Version: 6.1.7601.24535 (win7sp1_ldr_escrow.191105-1059) Modules
| |||||||||||||||
| 2392 | regsvr32 "C:\Program Files\Swallow6.0\Swallow.ocx" /s | C:\Windows\System32\regsvr32.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2476 | C:\Windows\system32\cmd.exe /S /D /c" ver" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2484 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\Swallow.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2520 | findstr "3\.[0-9]\.[0-9][0-9]*" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3044 | C:\Windows\system32\cmd.exe /S /D /c" ver" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3140 | C:\Windows\system32\cmd.exe /c ""C:\PROGRA~1\Swallow6.0\SWALLO~1.BAT" " | C:\Windows\System32\cmd.exe | — | Swallow.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 1 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 3304 | findstr "4\.[0-9]\.[0-9][0-9]*" | C:\Windows\System32\findstr.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Find String (QGREP) Utility Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3440 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa2484.13000\Swallow.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa2484.13000\Swallow.exe | WinRAR.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3568 | C:\Windows\system32\cmd.exe /S /D /c" ver" | C:\Windows\System32\cmd.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
Total events
1 247
Read events
1 210
Write events
37
Delete events
0
Modification events
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\178\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (2484) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
Executable files
34
Suspicious files
2
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3440 | Swallow.exe | C:\Program Files\Swallow6.0\~GLH0000.TMP | compressed | |
MD5:38832AAC6D2F2CDCA4848B90F7F4D4CB | SHA256:3C1F856B185875A705AE338ED25E89FD866A6EF61B33F65CD3D2ED6DF63FA7C0 | |||
| 3440 | Swallow.exe | C:\Users\admin\AppData\Local\Temp\GLC50AA.tmp | executable | |
MD5:09E59D00DF5D2EFFD8DD9B30385CB9D2 | SHA256:1C574EAB5E83CCFE5A0BB7B59E028CC5FA2F4E77868051E305D83C709711FF77 | |||
| 3440 | Swallow.exe | C:\Program Files\Swallow6.0\~GLH0001.TMP | text | |
MD5:203E2D4404A30BE3CC993AAD57E16219 | SHA256:F95C7061D0165C55C03A36FF59FEC107EBDF2E4F20BCE56D06313E1ACEF378A0 | |||
| 3440 | Swallow.exe | C:\Program Files\Swallow6.0\Swallow.cab | compressed | |
MD5:38832AAC6D2F2CDCA4848B90F7F4D4CB | SHA256:3C1F856B185875A705AE338ED25E89FD866A6EF61B33F65CD3D2ED6DF63FA7C0 | |||
| 3440 | Swallow.exe | C:\Program Files\Swallow6.0\UNWISE.EXE | executable | |
MD5:2B85FE26CA828485BFF6A454B881A295 | SHA256:7128574752F0A7DA1284D589C195AAFE25C29F825D7028CEBDB21A7ECC44DC00 | |||
| 3440 | Swallow.exe | C:\Program Files\Swallow6.0\Swallow6.0.bat | text | |
MD5:203E2D4404A30BE3CC993AAD57E16219 | SHA256:F95C7061D0165C55C03A36FF59FEC107EBDF2E4F20BCE56D06313E1ACEF378A0 | |||
| 1828 | expand.exe | C:\Program Files\Swallow6.0\AudioDecV33.dll | executable | |
MD5:FDC8349520BAA65559E4B9F2FF3121E9 | SHA256:47AD405C0891861CFDE2B25ADF4EAB5B8F0DF30745156BECC8DC865EA3F53534 | |||
| 3440 | Swallow.exe | C:\Program Files\Swallow6.0\~GLH0002.TMP | executable | |
MD5:2B85FE26CA828485BFF6A454B881A295 | SHA256:7128574752F0A7DA1284D589C195AAFE25C29F825D7028CEBDB21A7ECC44DC00 | |||
| 1828 | expand.exe | C:\Program Files\Swallow6.0\AVDecSDK.dll | executable | |
MD5:E2E63D308FFE7ABBBED521C8A4014B20 | SHA256:13A9DBDCA1A38E130343C56552405298A93D9FE0B434ACA35338C15C91D580FC | |||
| 2484 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa2484.13000\Swallow.exe | executable | |
MD5:3DFF1C825031CA2D174CE57857AFE1C6 | SHA256:2B70E7D8E8CFBB7D86CA4B8F4FA6894F501D165D39EEB68EC0AC2D73E6C134F8 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
3
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2656 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |