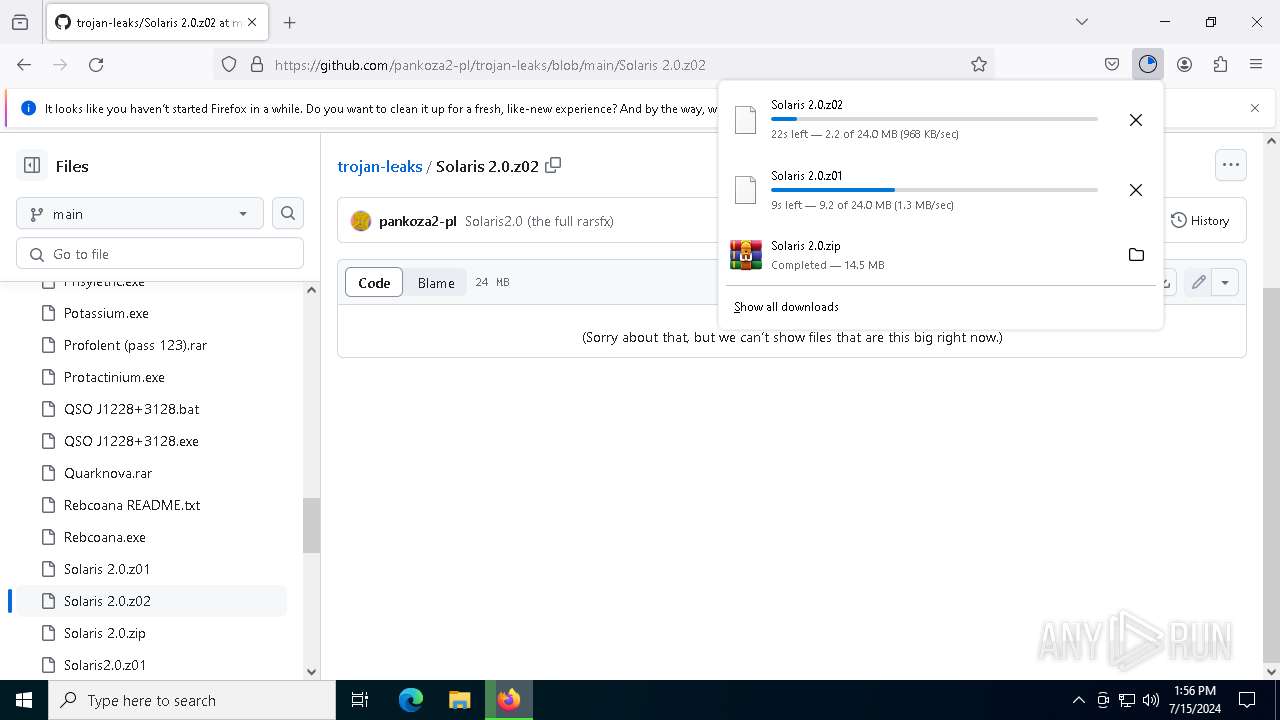
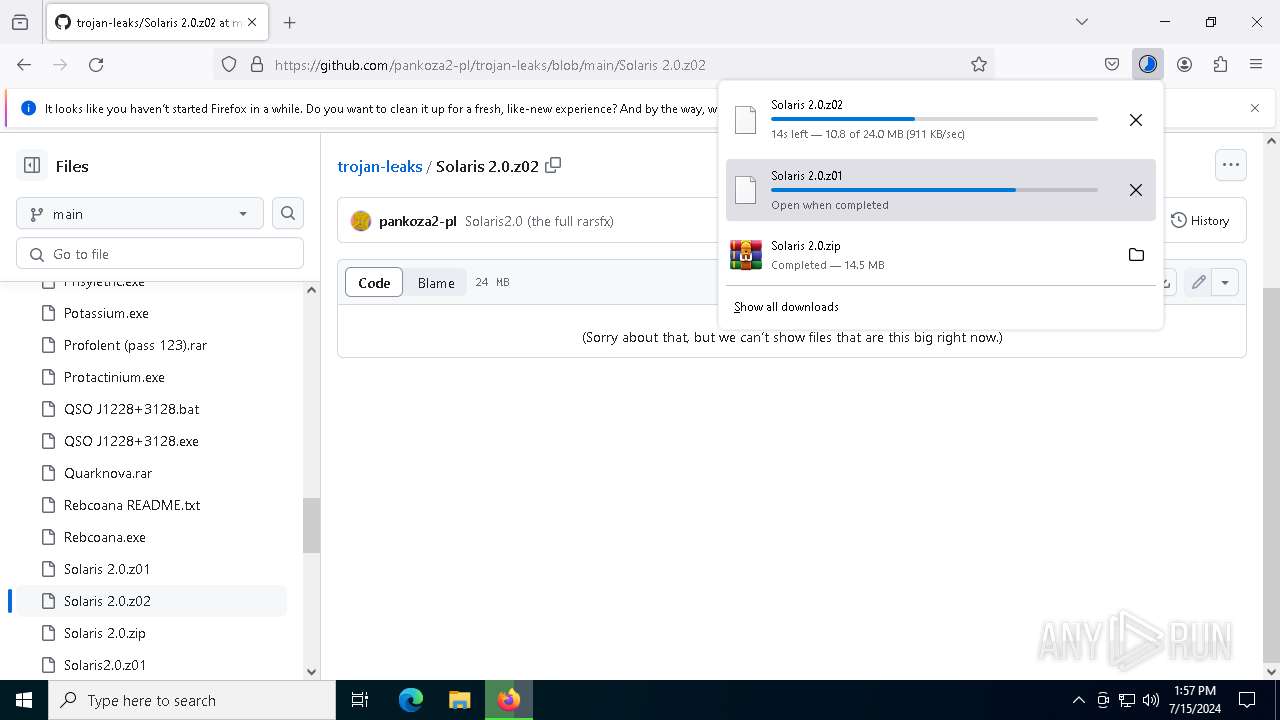
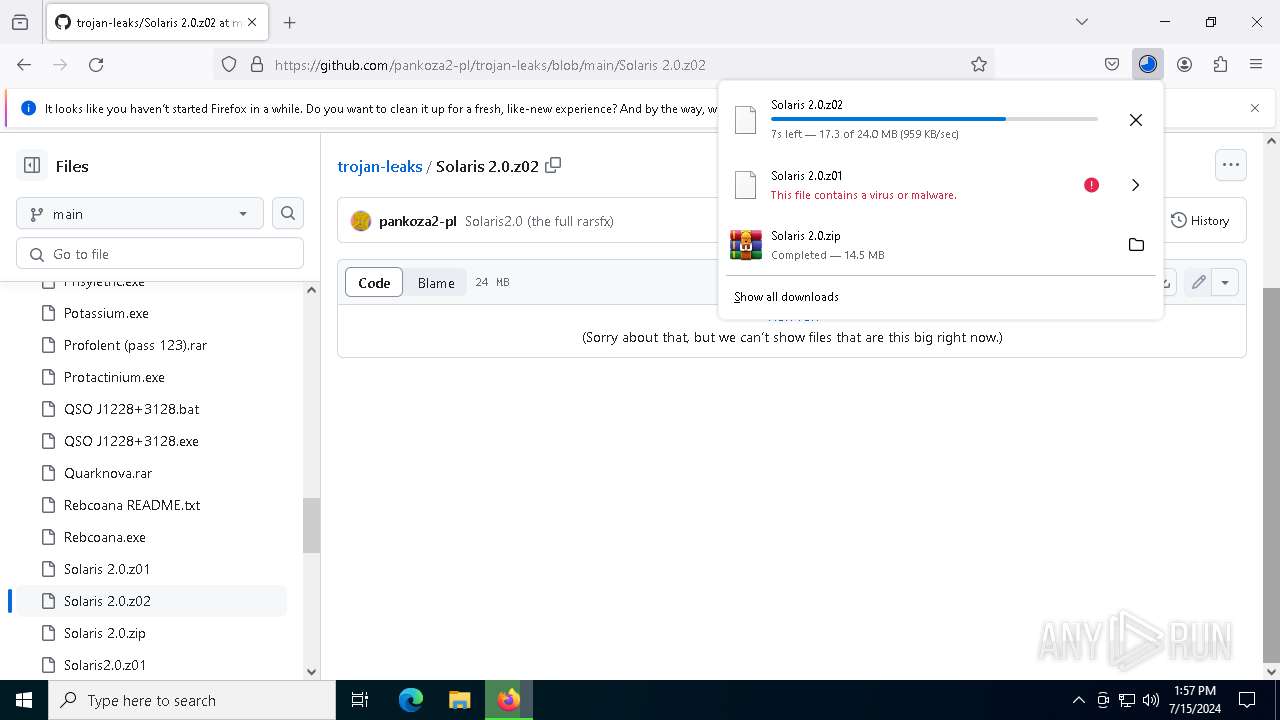
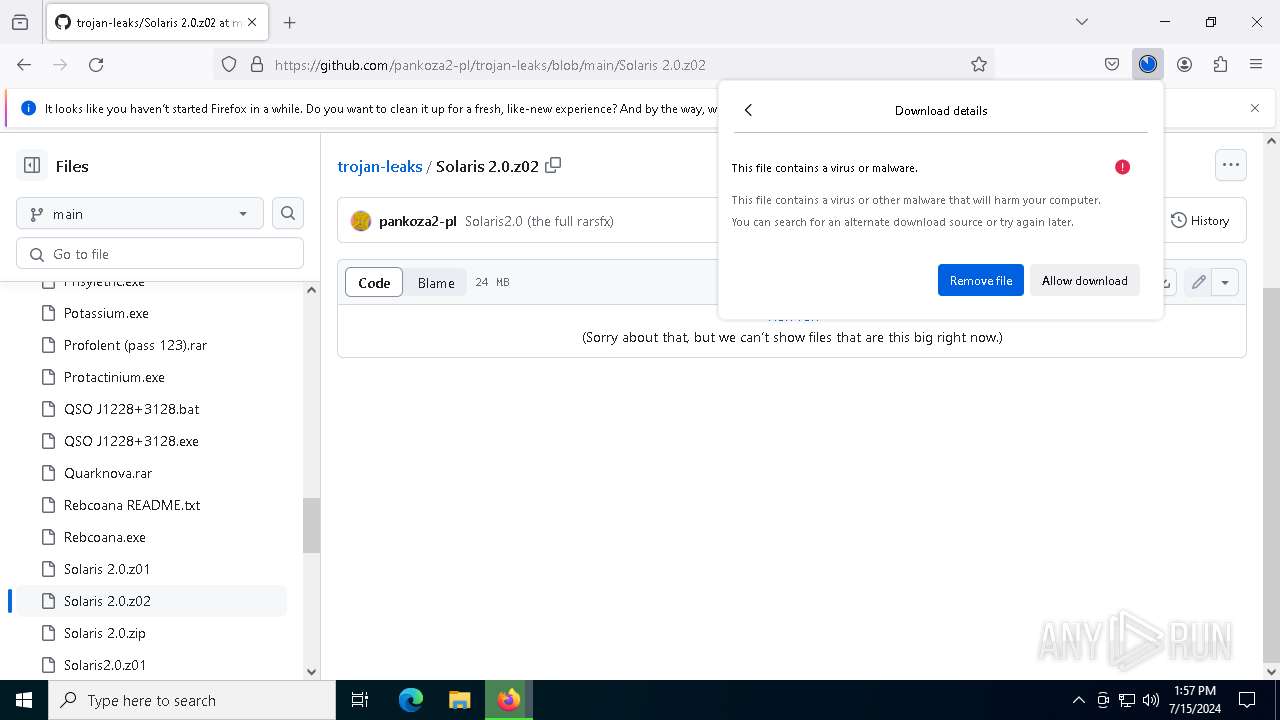
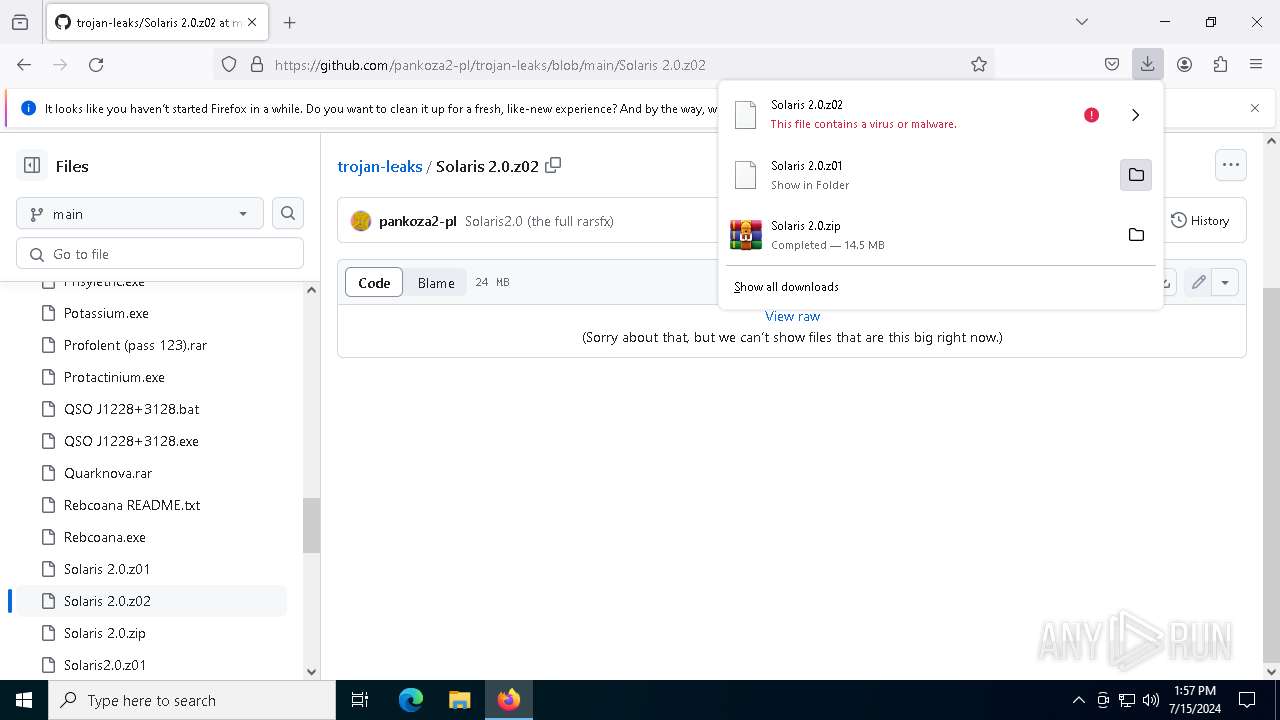
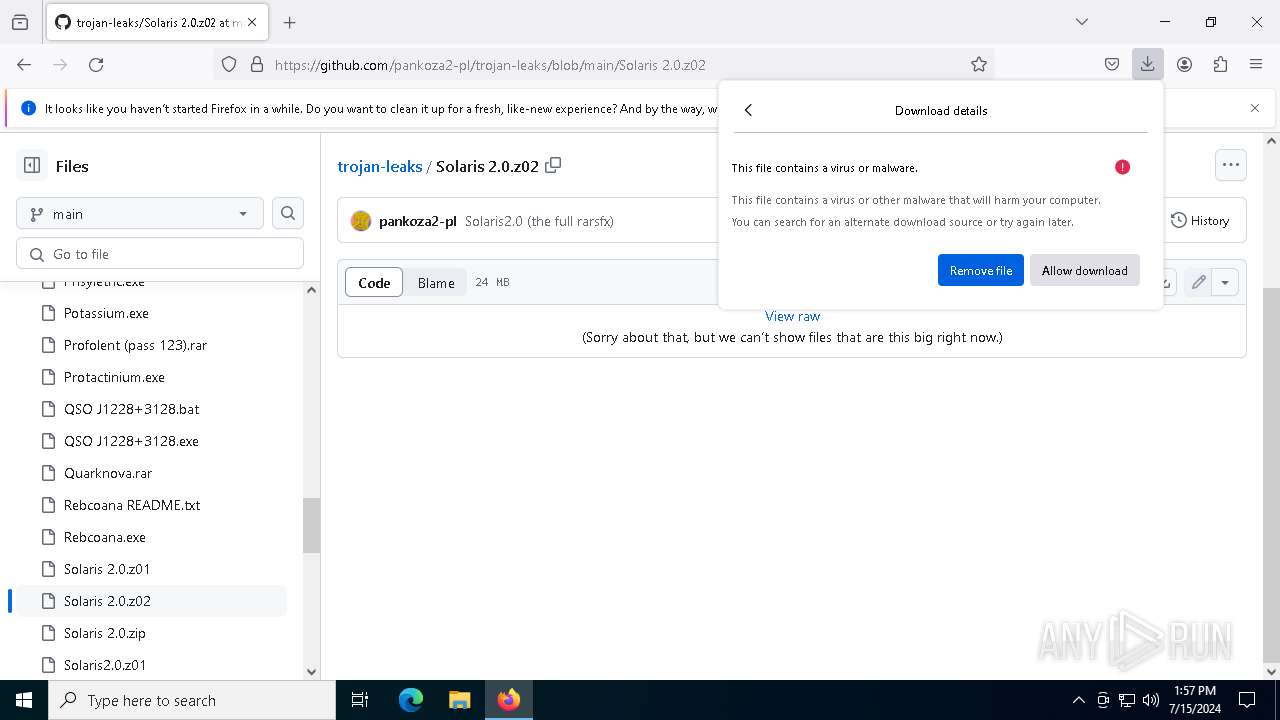
| URL: | https://github.com/pankoza2-pl/trojan-leaks/blob/main/Solaris%202.0.zip |
| Full analysis: | https://app.any.run/tasks/4180e219-09e1-40fe-8554-15452d9dfaf3 |
| Verdict: | Malicious activity |
| Analysis date: | July 15, 2024, 13:55:47 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | 9FCB0680425F7EE06B626634A8C0E0EB |
| SHA1: | 0C7A32D9CBE396D7718A20AF57467BCD28A59E26 |
| SHA256: | AC3584F770C57A1120811DE769BFA26601622DF9E661D3FFC2CA243F1A9A5E94 |
| SSDEEP: | 3:N8tEdlELlf3VJ6WKpKzERAXXGXLhc:2uoLFlqkzsyWbW |
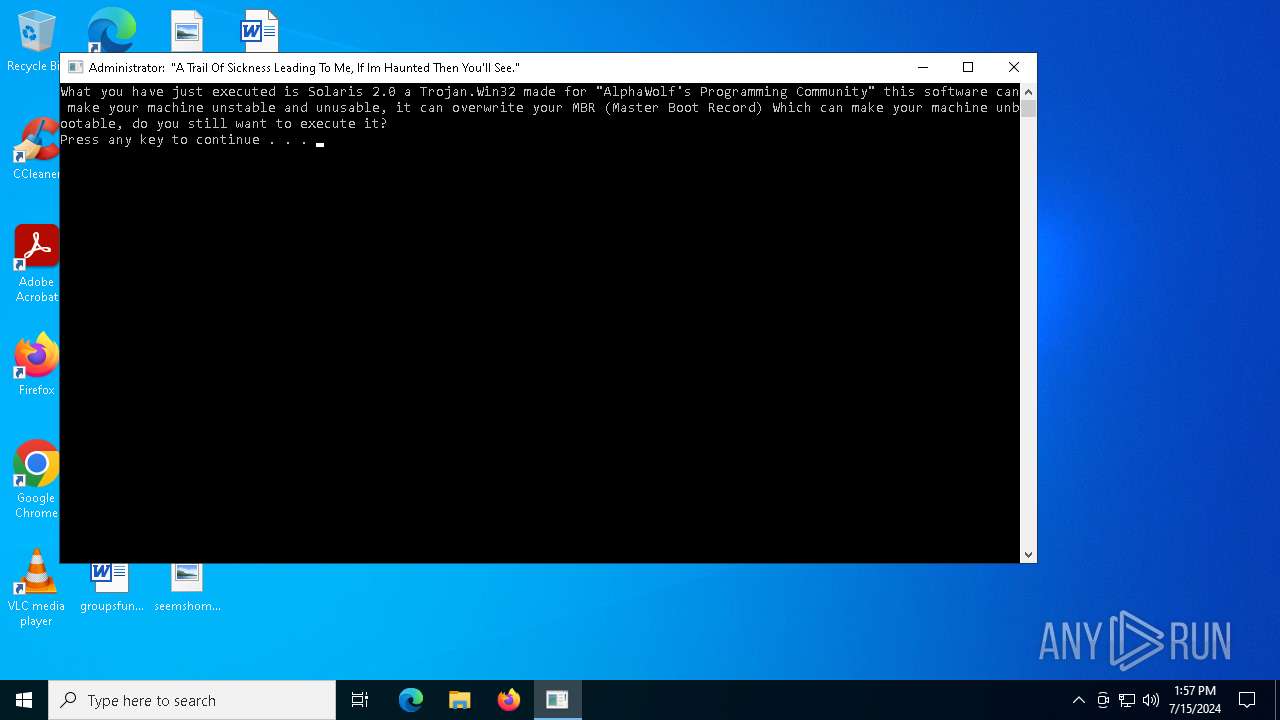
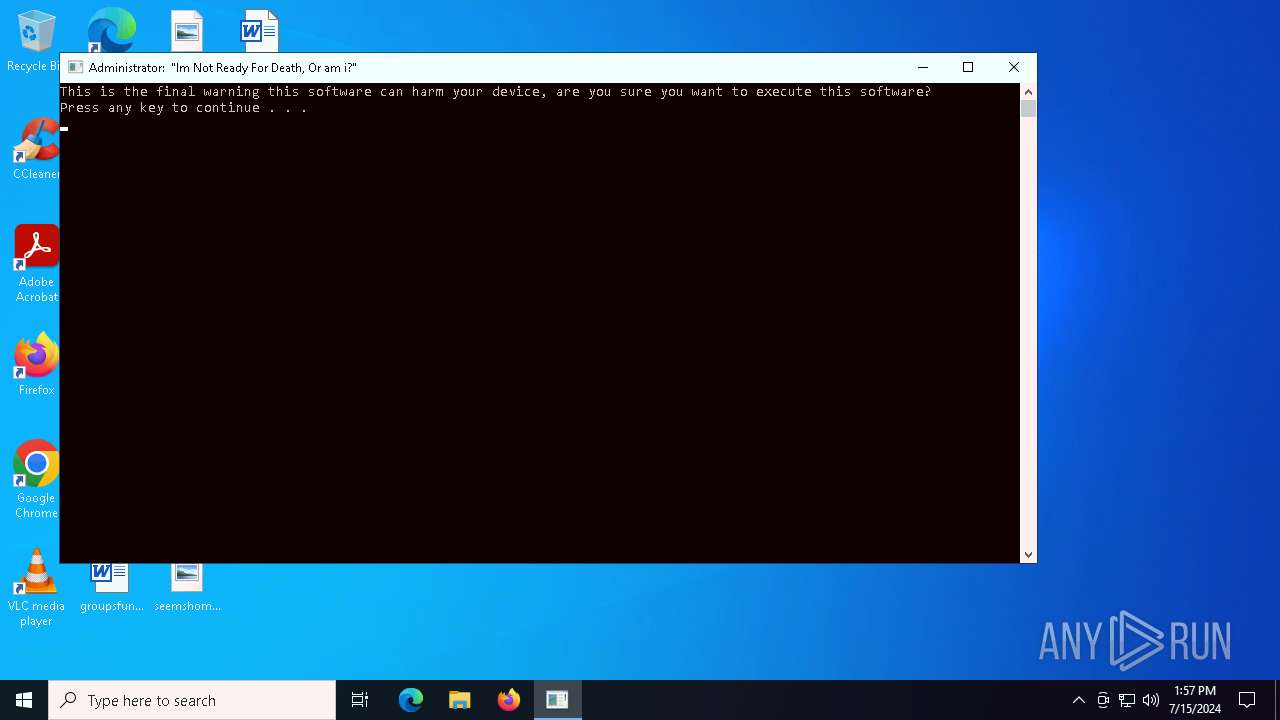
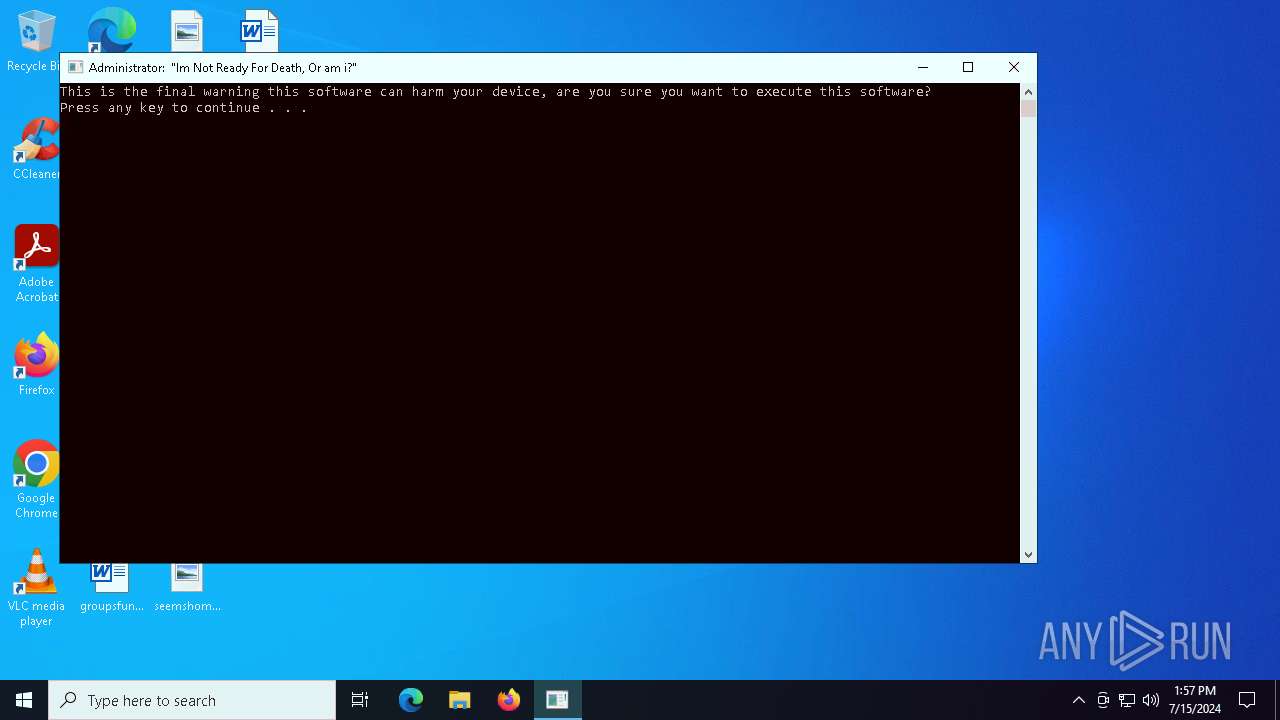
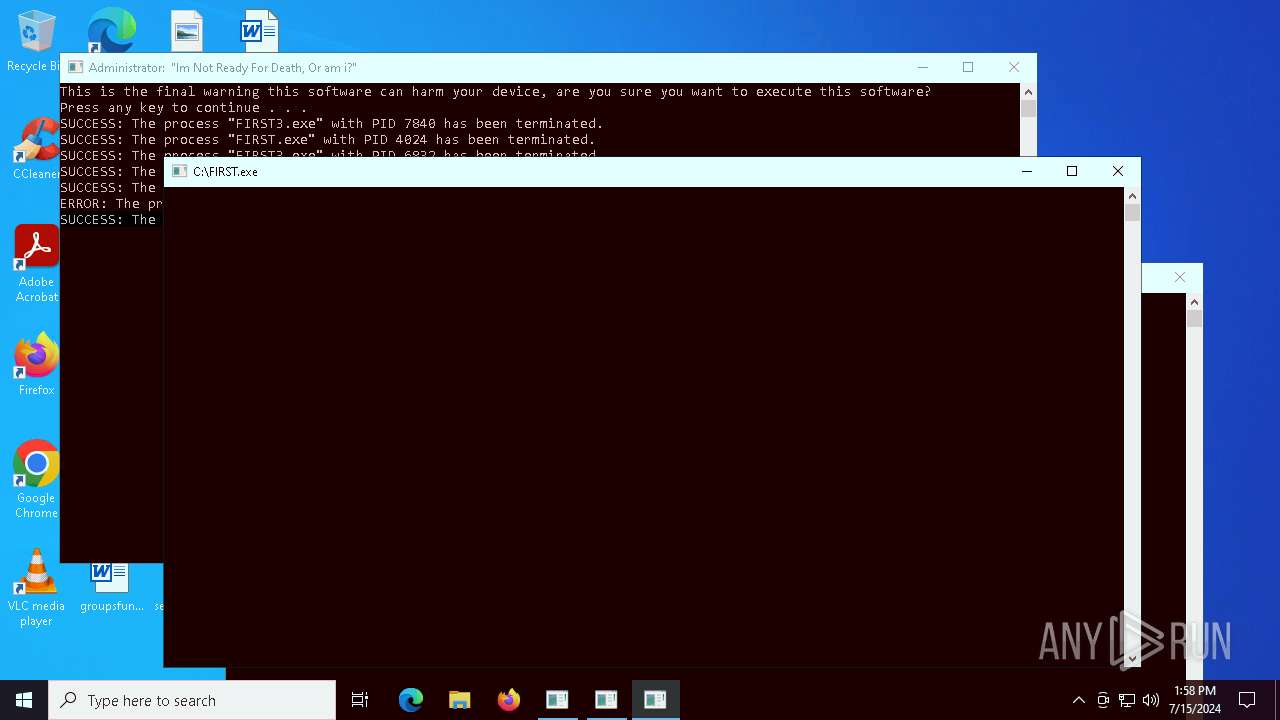
MALICIOUS
Drops the executable file immediately after the start
- Solaris 2.0.exe (PID: 2764)
SUSPICIOUS
Executable content was dropped or overwritten
- Solaris 2.0.exe (PID: 2764)
Creates file in the systems drive root
- Solaris 2.0.exe (PID: 2764)
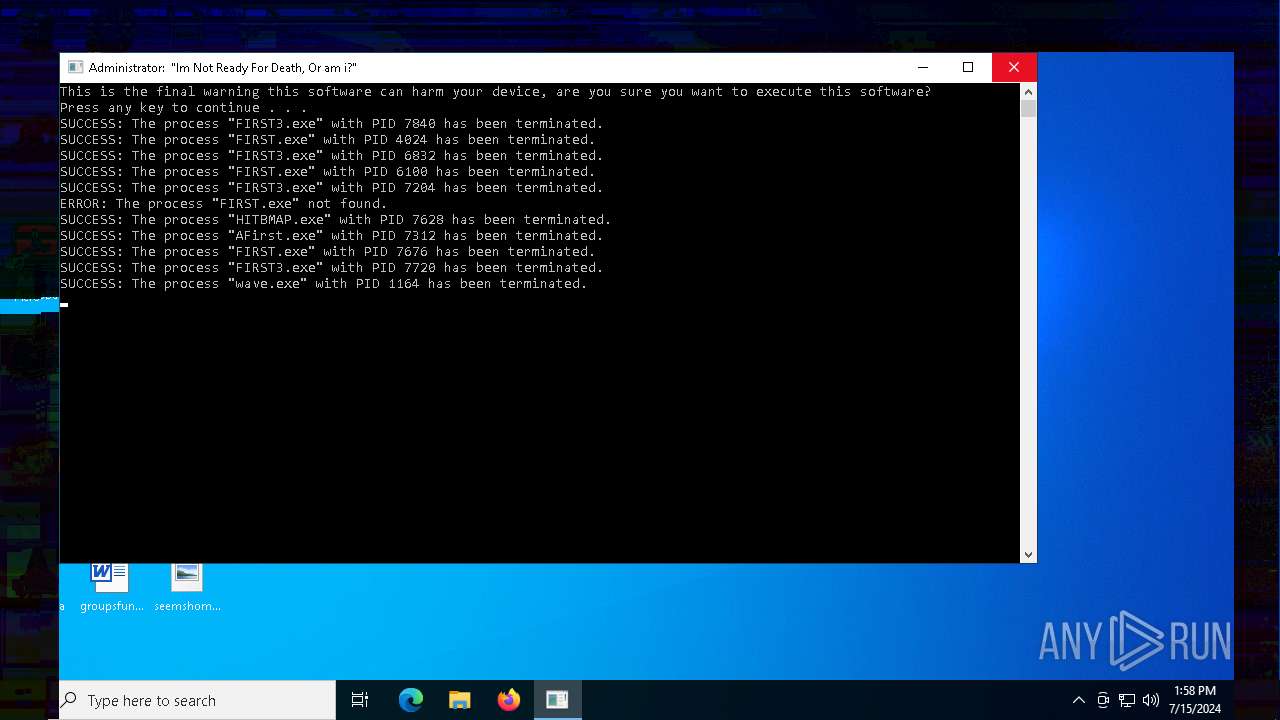
- HITBMAP.exe (PID: 7628)
- AFirst.exe (PID: 7312)
- conhost.exe (PID: 8048)
- wave.exe (PID: 1164)
- FIRST3.exe (PID: 7840)
- cmd.exe (PID: 7560)
- conhost.exe (PID: 5732)
- Solaris.exe (PID: 3540)
- conhost.exe (PID: 2204)
- FIRST.exe (PID: 4024)
- conhost.exe (PID: 6676)
- FIRST.exe (PID: 6100)
- FIRST3.exe (PID: 7204)
- FIRST3.exe (PID: 7720)
- conhost.exe (PID: 7116)
- FIRST.exe (PID: 7676)
- ATohou.exe (PID: 6944)
- FIRST3.exe (PID: 6832)
- conhost.exe (PID: 6212)
- conhost.exe (PID: 6508)
- RGB2.exe (PID: 4320)
- Circle2.exe (PID: 6196)
Reads security settings of Internet Explorer
- Solaris 2.0.exe (PID: 2764)
Runs PING.EXE to delay simulation
- cmd.exe (PID: 7560)
Starts CMD.EXE for commands execution
- Solaris.exe (PID: 3540)
Reads the date of Windows installation
- Solaris 2.0.exe (PID: 2764)
Executing commands from a ".bat" file
- Solaris.exe (PID: 3540)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 7560)
INFO
Application launched itself
- firefox.exe (PID: 480)
- firefox.exe (PID: 5864)
Reads Microsoft Office registry keys
- firefox.exe (PID: 5864)
Manual execution by a user
- Solaris 2.0.exe (PID: 2764)
- WinRAR.exe (PID: 3928)
- Solaris 2.0.exe (PID: 3836)
Checks supported languages
- Solaris 2.0.exe (PID: 2764)
- Solaris.exe (PID: 3540)
- HITBMAP.exe (PID: 7628)
- wave.exe (PID: 1164)
- AFirst.exe (PID: 7312)
- FIRST3.exe (PID: 7840)
- FIRST.exe (PID: 4024)
- FIRST3.exe (PID: 6832)
- FIRST.exe (PID: 6100)
- FIRST3.exe (PID: 7204)
- FIRST.exe (PID: 7676)
- ATohou.exe (PID: 6944)
- FIRST3.exe (PID: 7720)
- RGB2.exe (PID: 4320)
- Circle2.exe (PID: 6196)
The process uses the downloaded file
- WinRAR.exe (PID: 3928)
- firefox.exe (PID: 5864)
Process checks computer location settings
- Solaris 2.0.exe (PID: 2764)
Create files in a temporary directory
- Solaris.exe (PID: 3540)
Reads the computer name
- AFirst.exe (PID: 7312)
- Solaris 2.0.exe (PID: 2764)
- ATohou.exe (PID: 6944)
Reads the software policy settings
- slui.exe (PID: 5940)
- slui.exe (PID: 2716)
Checks proxy server information
- slui.exe (PID: 2716)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
208
Monitored processes
65
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 480 | "C:\Program Files\Mozilla Firefox\firefox.exe" "https://github.com/pankoza2-pl/trojan-leaks/blob/main/Solaris%202.0.zip" | C:\Program Files\Mozilla Firefox\firefox.exe | — | explorer.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 123.0 Modules
| |||||||||||||||
| 992 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Exit code: 0 Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1164 | C:\wave.exe | C:\wave.exe | — | cmd.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 1 Modules
| |||||||||||||||
| 1296 | taskkill /f /im FIRST3.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1320 | taskkill /f /im FIRST.exe | C:\Windows\System32\taskkill.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Terminates Processes Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2204 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | FIRST.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2716 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2764 | "C:\Users\admin\Desktop\Solaris 2.0.exe" | C:\Users\admin\Desktop\Solaris 2.0.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3540 | "C:\Solaris.exe" | C:\Solaris.exe | — | Solaris 2.0.exe | |||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 3836 | "C:\Users\admin\Desktop\Solaris 2.0.exe" | C:\Users\admin\Desktop\Solaris 2.0.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
Total events
28 110
Read events
28 031
Write events
78
Delete events
1
Modification events
| (PID) Process: | (480) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: EE88E19301000000 | |||
| (PID) Process: | (5864) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 3737E39301000000 | |||
| (PID) Process: | (5864) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Progress |
Value: 0 | |||
| (PID) Process: | (5864) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Progress |
Value: 1 | |||
| (PID) Process: | (5864) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Installer\308046B0AF4A39CB |
| Operation: | delete value | Name: | installer.taskbarpin.win10.enabled |
Value: | |||
| (PID) Process: | (5864) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 0 | |||
| (PID) Process: | (5864) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\DllPrefetchExperiment |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe |
Value: 0 | |||
| (PID) Process: | (5864) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Theme |
Value: 1 | |||
| (PID) Process: | (5864) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\PreXULSkeletonUISettings |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Enabled |
Value: 1 | |||
| (PID) Process: | (5864) firefox.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Mozilla\Firefox\Default Browser Agent |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox|DisableTelemetry |
Value: 1 | |||
Executable files
33
Suspicious files
196
Text files
41
Unknown types
6
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 5864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\prefs.js | text | |
MD5:7A97B8DBC4F98D175F958C00F463A52A | SHA256:92074D2ED1AA1FD621287E35DB9EF1AE3DC04777EFAE5F09E7A3B4534C201548 | |||
| 5864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\3870112724rsegmnoittet-es.sqlite | — | |
MD5:— | SHA256:— | |||
| 5864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cert9.db-journal | binary | |
MD5:CFBB8CC55B0F9BBE32C0193967CF7A84 | SHA256:A0CE1E0E1B743F201BC738C6E76F704AF416A59F851AC2329919ADCE556DB97E | |||
| 5864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\cookies.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\1657114595AmcateirvtiSty.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
| 5864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\SiteSecurityServiceState.bin | binary | |
MD5:B32F74291A41DC87967B0C632EE27C8D | SHA256:6A9DD9BC01BEF77EA0E9089AFD1F831267C9EE2D5CE23FD1452EDBC8D8284144 | |||
| 5864 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\9kie7cg6.default-release\storage\permanent\chrome\idb\2823318777ntouromlalnodry--naod.sqlite-shm | binary | |
MD5:B7C14EC6110FA820CA6B65F5AEC85911 | SHA256:FD4C9FDA9CD3F9AE7C962B0DDF37232294D55580E1AA165AA06129B8549389EB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
33
TCP/UDP connections
127
DNS requests
134
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5864 | firefox.exe | POST | 200 | 184.24.77.53:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
5864 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/success.txt?ipv4 | unknown | — | — | whitelisted |
5864 | firefox.exe | POST | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/ | unknown | — | — | unknown |
5864 | firefox.exe | POST | 200 | 184.24.77.57:80 | http://r3.o.lencr.org/ | unknown | — | — | unknown |
5864 | firefox.exe | POST | 200 | 142.250.181.227:80 | http://o.pki.goog/wr2 | unknown | — | — | unknown |
5864 | firefox.exe | GET | 200 | 34.107.221.82:80 | http://detectportal.firefox.com/canonical.html | unknown | — | — | whitelisted |
4656 | SearchApp.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
5864 | firefox.exe | POST | 200 | 184.24.77.53:80 | http://r10.o.lencr.org/ | unknown | — | — | unknown |
5864 | firefox.exe | POST | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/ | unknown | — | — | unknown |
5864 | firefox.exe | POST | 200 | 184.24.77.83:80 | http://r11.o.lencr.org/ | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5680 | svchost.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
2252 | RUXIMICS.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4752 | MoUsoCoreWorker.exe | 40.127.240.158:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
4656 | SearchApp.exe | 104.126.37.144:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4032 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4656 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5864 | firefox.exe | 34.107.243.93:443 | push.services.mozilla.com | — | — | unknown |
5864 | firefox.exe | 34.117.188.166:443 | contile.services.mozilla.com | — | — | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
detectportal.firefox.com |
| whitelisted |
github.com |
| shared |
prod.detectportal.prod.cloudops.mozgcp.net |
| whitelisted |
contile.services.mozilla.com |
| whitelisted |
example.org |
| whitelisted |
ipv4only.arpa |
| whitelisted |
spocs.getpocket.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |
2168 | svchost.exe | Not Suspicious Traffic | INFO [ANY.RUN] Attempting to access raw user content on GitHub |