| File name: | amsi.exe |
| Full analysis: | https://app.any.run/tasks/9a520342-8348-40c4-9d89-fc070ea56845 |
| Verdict: | Malicious activity |
| Analysis date: | June 11, 2019, 22:33:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 40C06C854E8D7F93D1E174FDC7ABF8BC |
| SHA1: | D45B97E06FFDFF3068F43F7695F3EAAE439B27A4 |
| SHA256: | AC2B263A850B69C01B2DFC8544B5196D3FC947F5E96D389A341DDC6CEE4E077E |
| SSDEEP: | 3072:8kiTRuLfL4RsuqUXNWOCWih8pnkNPR++ExeAK2oTgtcn0uxF5Rgex6MBRh/Do2k:HiTRuLgTNZ7u92Ogt4dx3dxpnhQ |
MALICIOUS
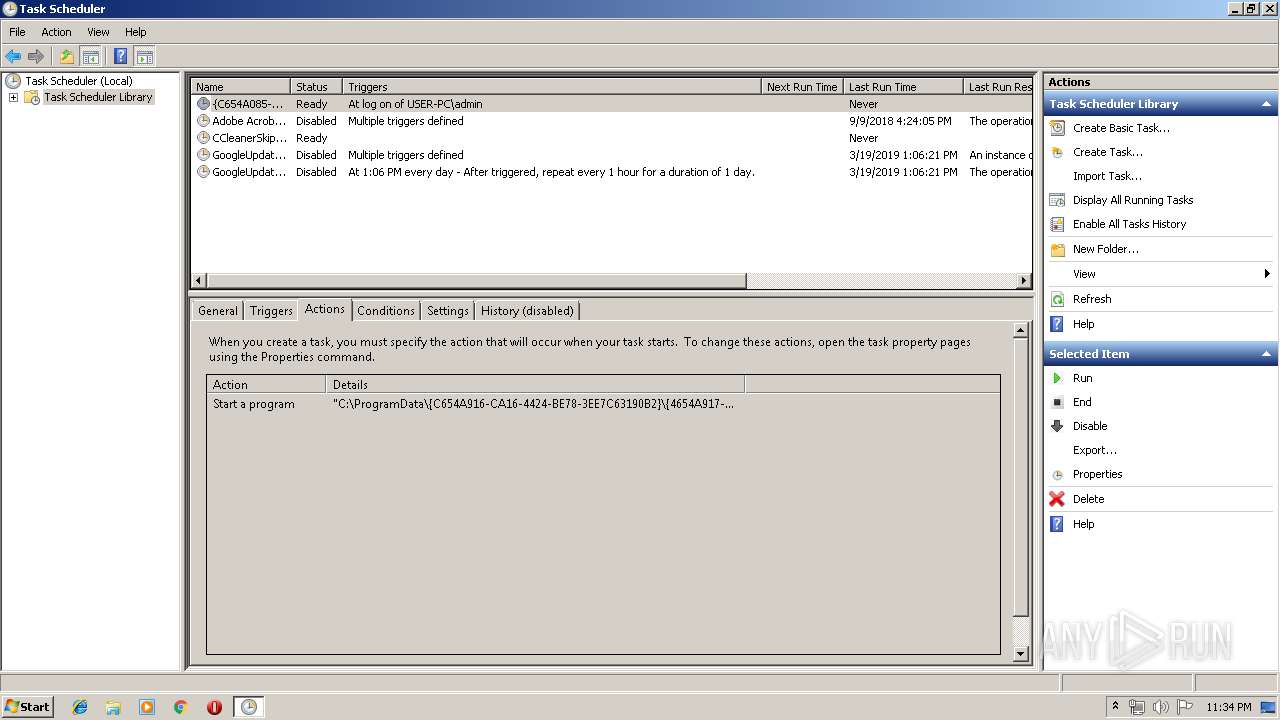
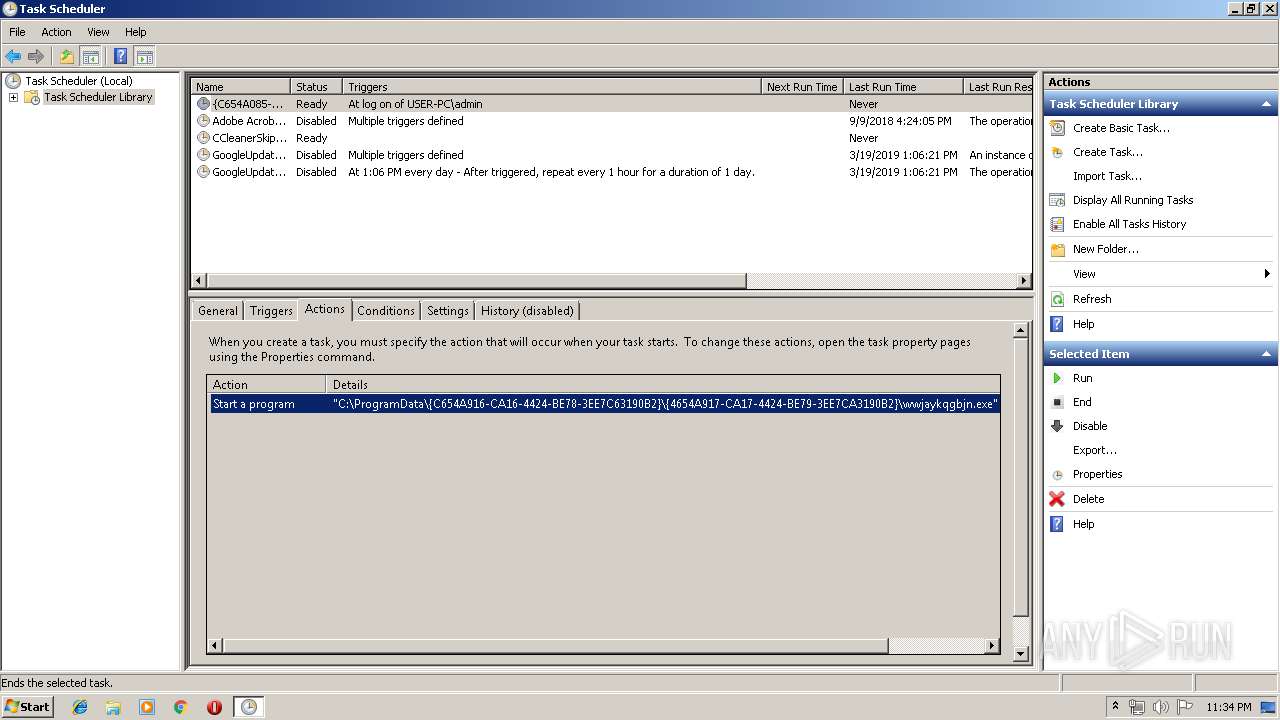
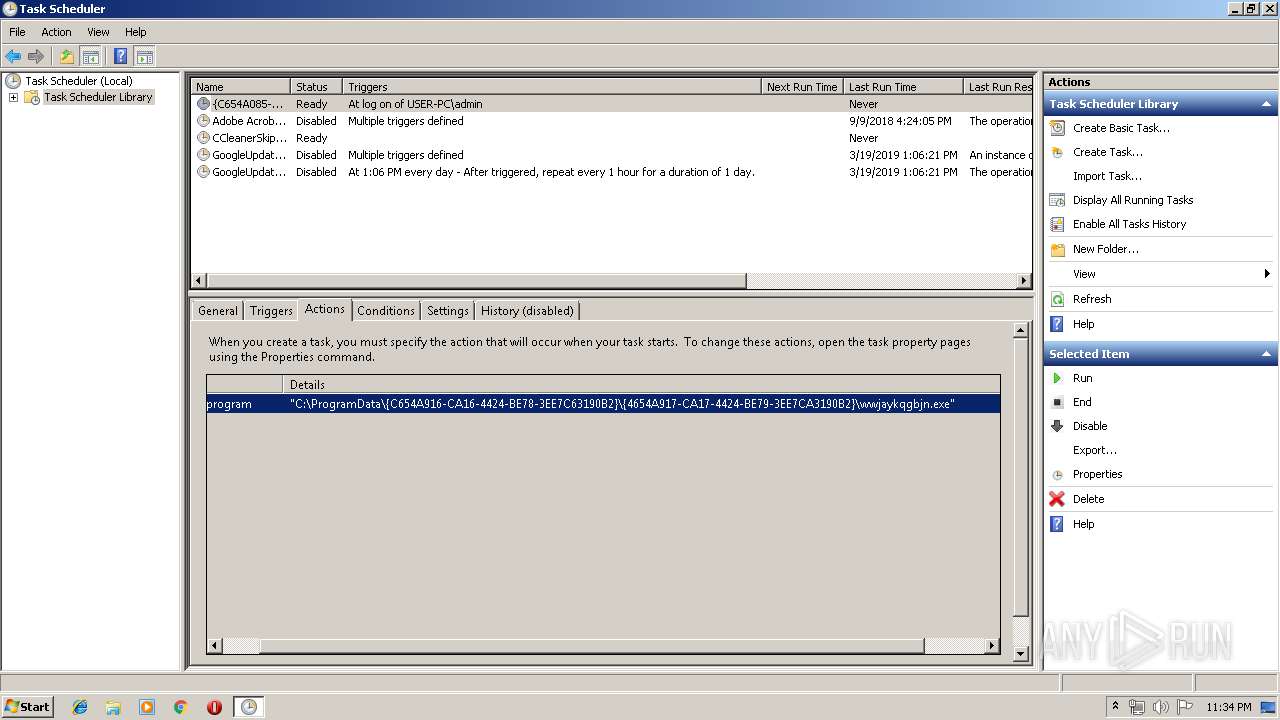
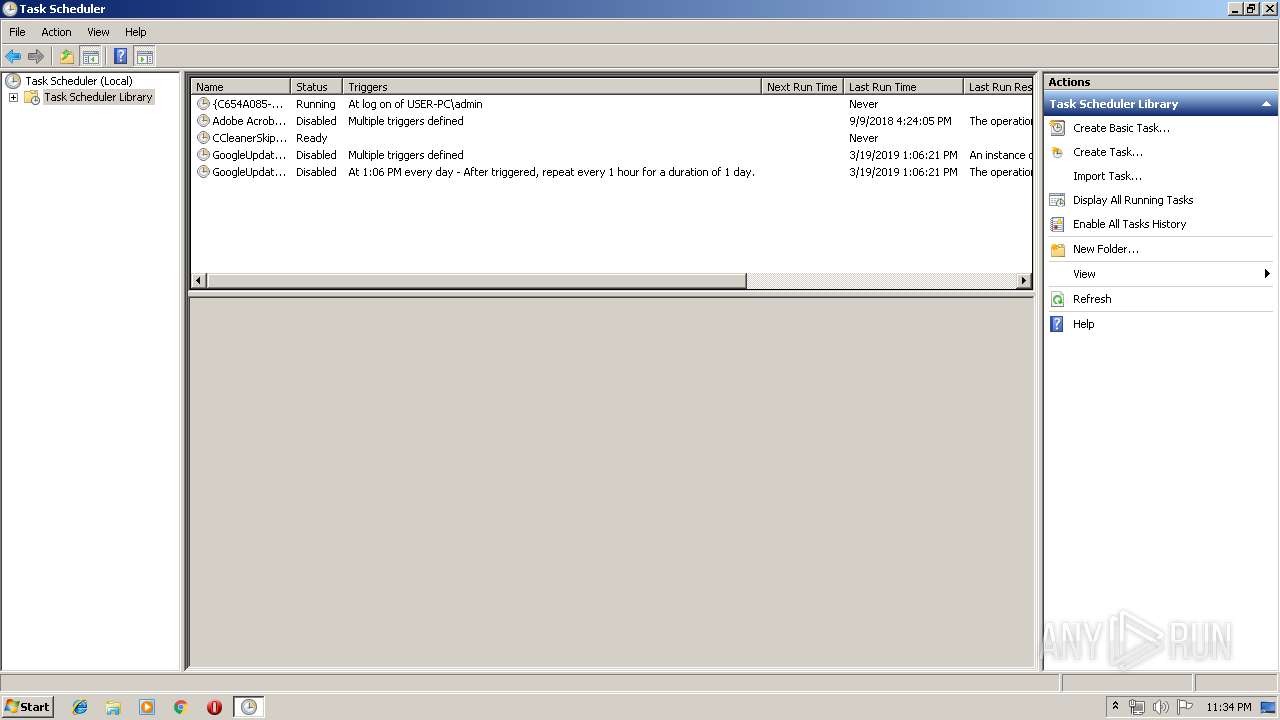
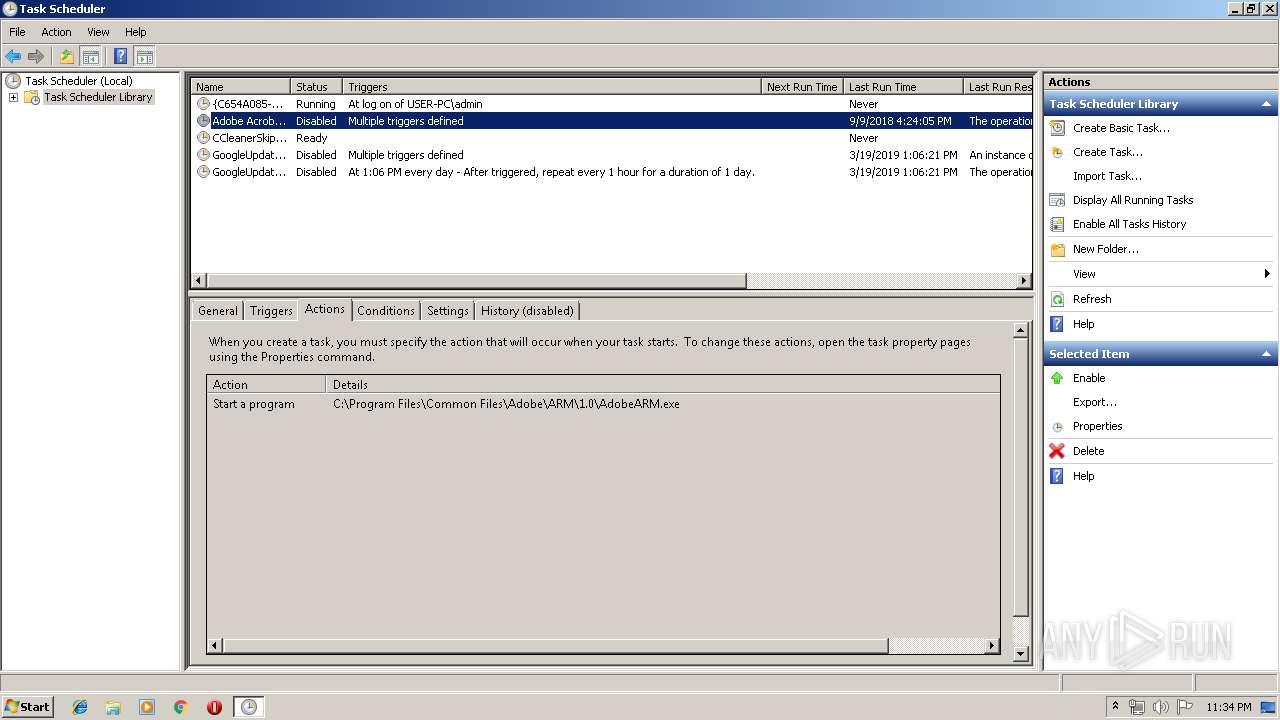
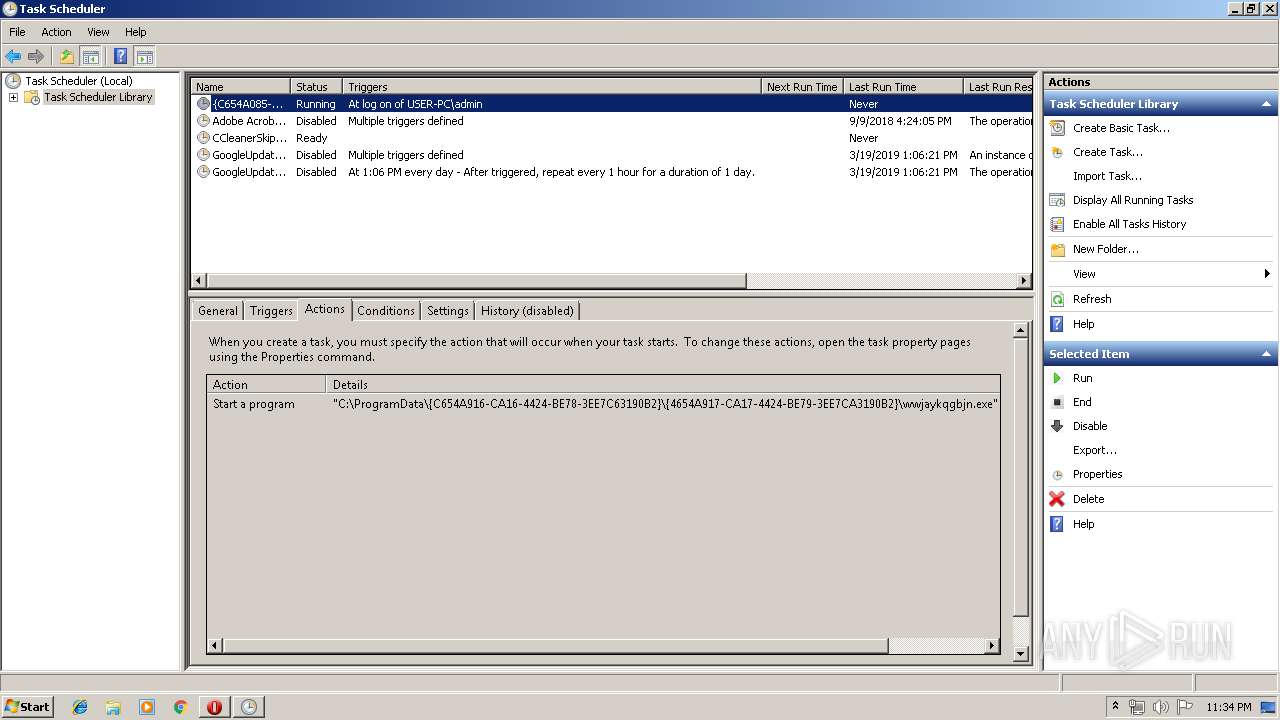
Loads the Task Scheduler COM API
- svchost.exe (PID: 2392)
- mmc.exe (PID: 1520)
Uses SVCHOST.EXE for hidden code execution
- amsi.exe (PID: 3436)
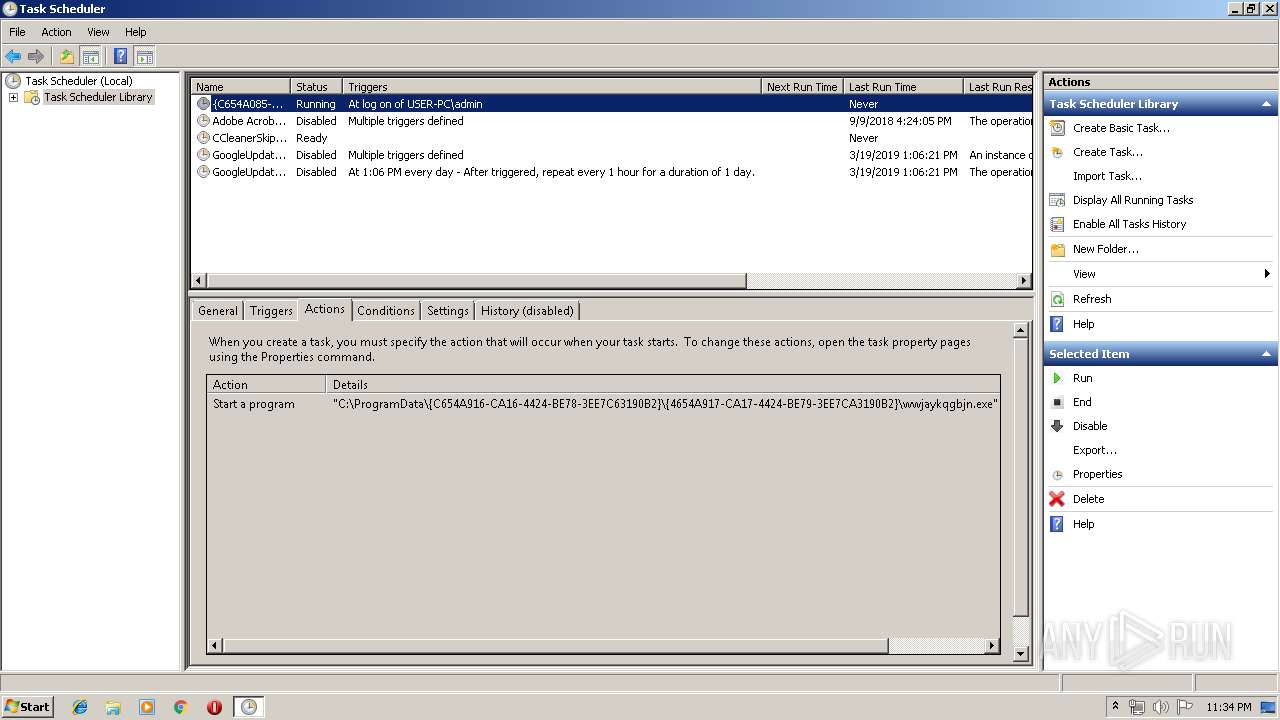
- wwjaykqgbjn.exe (PID: 2280)
Application was dropped or rewritten from another process
- wwjaykqgbjn.exe (PID: 1496)
- wwjaykqgbjn.exe (PID: 2280)
SUSPICIOUS
Application launched itself
- amsi.exe (PID: 3376)
- wwjaykqgbjn.exe (PID: 1496)
Creates files in the program directory
- svchost.exe (PID: 2392)
Executable content was dropped or overwritten
- svchost.exe (PID: 2392)
Executed via Task Scheduler
- wwjaykqgbjn.exe (PID: 1496)
INFO
Manual execution by user
- mmc.exe (PID: 1520)
- mmc.exe (PID: 2576)
- opera.exe (PID: 3972)
Creates files in the user directory
- opera.exe (PID: 3972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (42.2) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (37.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.8) |
| .exe | | | Win32 Executable (generic) (6) |
| .exe | | | Generic Win/DOS Executable (2.7) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:01:17 14:52:52+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 12 |
| CodeSize: | 83456 |
| InitializedDataSize: | 245248 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x71c9 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 17-Jan-2018 13:52:52 |
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000F0 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 17-Jan-2018 13:52:52 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x0003E000 | 0x0000D3AC | 0x0000C600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 5.99381 |
.rdata | 0x00016000 | 0x0000747C | 0x00007600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.74176 |
.data | 0x0001E000 | 0x0001F120 | 0x00002000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 2.59959 |
.rsrc | 0x0004C000 | 0x00007898 | 0x00007A00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 5.14073 |
.reloc | 0x00054000 | 0x00001434 | 0x00001600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.33793 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.84534 | 3752 | UNKNOWN | UNKNOWN | RT_ICON |
2 | 4.15234 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 3.96979 | 1736 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 3.85587 | 1384 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 4.30653 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
6 | 4.86693 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
7 | 4.52966 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
8 | 4.32105 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
22 | 3.22204 | 1266 | UNKNOWN | UNKNOWN | RT_STRING |
23 | 3.28327 | 1550 | UNKNOWN | UNKNOWN | RT_STRING |
Imports
ADVAPI32.dll |
KERNEL32.dll |
Total processes
43
Monitored processes
9
Malicious processes
3
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 536 | C:\Windows\system32\svchost.exe | C:\Windows\system32\svchost.exe | — | wwjaykqgbjn.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1496 | C:\ProgramData\{C654A916-CA16-4424-BE78-3EE7C63190B2}\{4654A917-CA17-4424-BE79-3EE7CA3190B2}\wwjaykqgbjn.exe | C:\ProgramData\{C654A916-CA16-4424-BE78-3EE7C63190B2}\{4654A917-CA17-4424-BE79-3EE7CA3190B2}\wwjaykqgbjn.exe | — | taskeng.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 1520 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\system32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2280 | C:\ProgramData\{C654A916-CA16-4424-BE78-3EE7C63190B2}\{4654A917-CA17-4424-BE79-3EE7CA3190B2}\wwjaykqgbjn.exe -q=2416793153 | C:\ProgramData\{C654A916-CA16-4424-BE78-3EE7C63190B2}\{4654A917-CA17-4424-BE79-3EE7CA3190B2}\wwjaykqgbjn.exe | — | wwjaykqgbjn.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 2392 | C:\Windows\system32\svchost.exe | C:\Windows\system32\svchost.exe | amsi.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2576 | "C:\Windows\system32\mmc.exe" "C:\Windows\system32\taskschd.msc" /s | C:\Windows\system32\mmc.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Management Console Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3376 | "C:\Users\admin\AppData\Local\Temp\amsi.exe" | C:\Users\admin\AppData\Local\Temp\amsi.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3436 | "C:\Users\admin\AppData\Local\Temp\amsi.exe" -q=2416788192 | C:\Users\admin\AppData\Local\Temp\amsi.exe | — | amsi.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3972 | "C:\Program Files\Opera\opera.exe" | C:\Program Files\Opera\opera.exe | explorer.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
Total events
268
Read events
208
Write events
60
Delete events
0
Modification events
| (PID) Process: | (1520) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | HelpTopic |
Value: C:\Windows\Help\taskscheduler.chm | |||
| (PID) Process: | (1520) mmc.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\MMC\SnapIns\FX:{c7b8fb06-bfe1-4c2e-9217-7a69a95bbac4} |
| Operation: | write | Name: | LinkedHelpTopics |
Value: C:\Windows\Help\taskscheduler.chm | |||
| (PID) Process: | (3972) opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\opera.exe | |||
| (PID) Process: | (3972) opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\62\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
1
Suspicious files
44
Text files
65
Unknown types
23
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3972 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr4266.tmp | — | |
MD5:— | SHA256:— | |||
| 3972 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr42A6.tmp | — | |
MD5:— | SHA256:— | |||
| 3972 | opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 3972 | opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\JISF5RFBQ0THNILN9E23.temp | — | |
MD5:— | SHA256:— | |||
| 3972 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprC082.tmp | — | |
MD5:— | SHA256:— | |||
| 3972 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprCC5A.tmp | — | |
MD5:— | SHA256:— | |||
| 2392 | svchost.exe | C:\ProgramData\{C654A916-CA16-4424-BE78-3EE7C63190B2}\{4654A917-CA17-4424-BE79-3EE7CA3190B2}\wwjaykqgbjn.exe | executable | |
MD5:— | SHA256:— | |||
| 3972 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\tasks.xml | xml | |
MD5:— | SHA256:— | |||
| 3972 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
| 3972 | opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
12
TCP/UDP connections
49
DNS requests
21
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
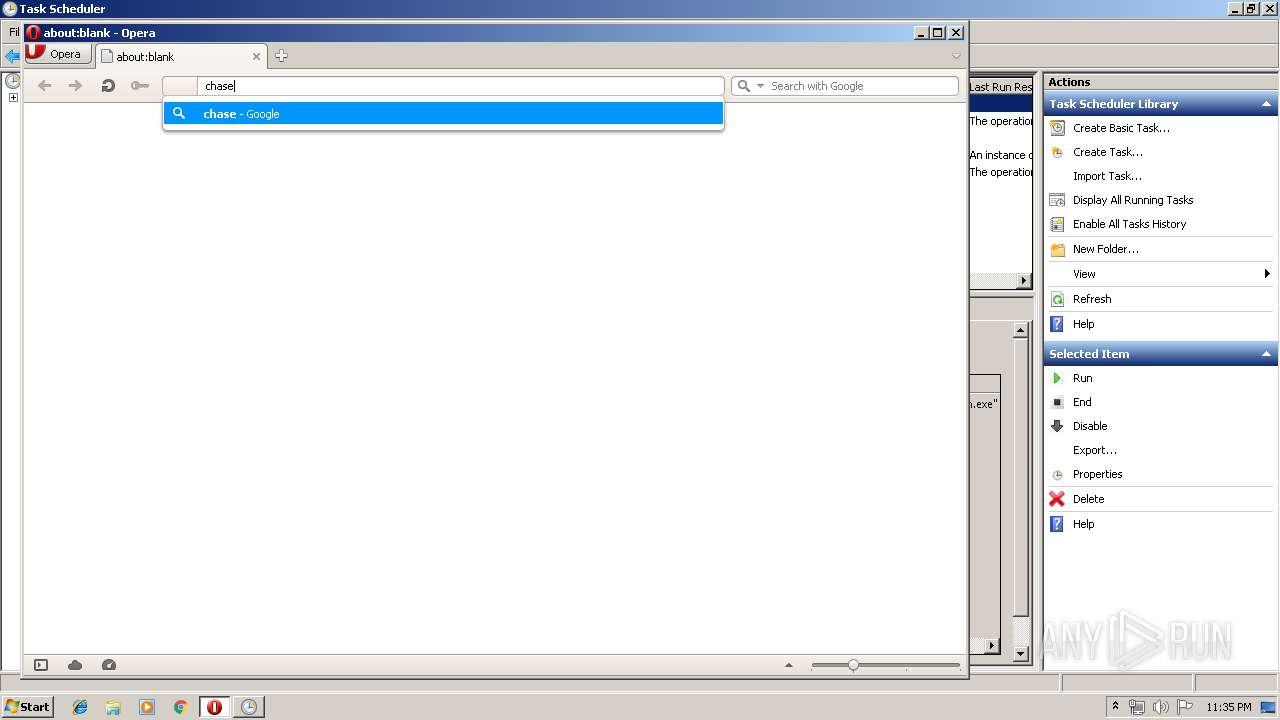
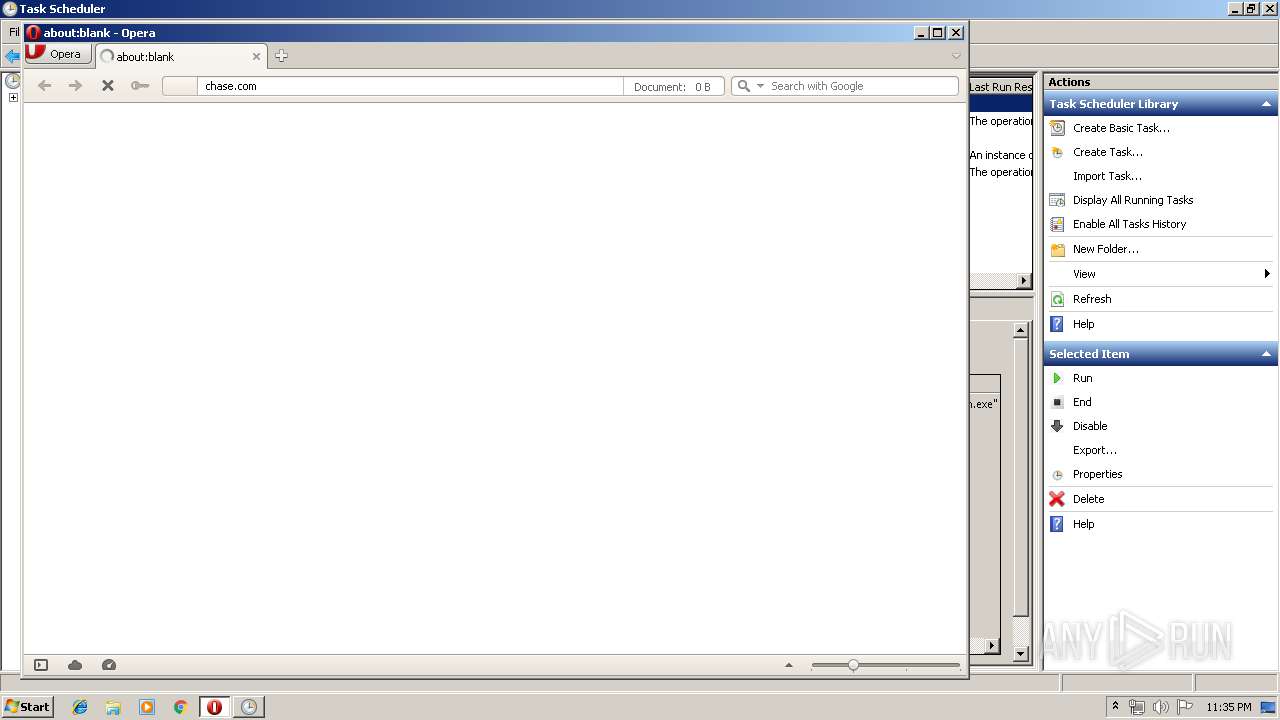
3972 | opera.exe | GET | 301 | 159.53.85.137:80 | http://chase.com/ | US | — | — | suspicious |
3972 | opera.exe | GET | 200 | 172.217.18.206:80 | http://clients1.google.com/complete/search?q=chas&client=opera-suggest-omnibox&hl=de | US | text | 112 b | whitelisted |
3972 | opera.exe | GET | 200 | 216.58.201.227:80 | http://crl.pki.goog/gsr2/gsr2.crl | US | der | 546 b | whitelisted |
3972 | opera.exe | GET | 200 | 104.121.24.251:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQnuEQcScL%2FkljKed%2BRzpzFYOq9kwQUw%2FfQtSowra8NkSFwOVTdvIlwxzoCEBy4c2rWq6eqAAAAAFTPYF4%3D | NL | der | 1.90 Kb | whitelisted |
3972 | opera.exe | GET | 200 | 104.121.24.251:80 | http://ocsp.entrust.net/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQnuEQcScL%2FkljKed%2BRzpzFYOq9kwQUw%2FfQtSowra8NkSFwOVTdvIlwxzoCEEhX3tOSiXkaAAAAAFTPzbw%3D | NL | der | 1.90 Kb | whitelisted |
3972 | opera.exe | GET | 200 | 104.123.50.17:80 | http://crl.entrust.net/g2ca.crl | US | der | 1.45 Kb | whitelisted |
3972 | opera.exe | GET | 200 | 104.121.24.251:80 | http://ocsp.entrust.net/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQnuEQcScL%2FkljKed%2BRzpzFYOq9kwQUw%2FfQtSowra8NkSFwOVTdvIlwxzoCEQD9e1BR8AutbgAAAABUz5cI | NL | der | 1.90 Kb | whitelisted |
3972 | opera.exe | GET | 200 | 216.58.201.227:80 | http://ocsp.pki.goog/GTSGIAG3/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT27bBjYjKBmjX2jXWgnQJKEapsrQQUd8K4UJpndnaxLcKG0IOgfqZ%2BuksCEDYVemzAwWFsVOgYEZWLA1k%3D | US | der | 471 b | whitelisted |
3972 | opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 543 b | whitelisted |
3972 | opera.exe | GET | — | 104.123.50.17:80 | http://crl.entrust.net/g2ca.crl | US | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3972 | opera.exe | 185.26.182.93:443 | certs.opera.com | Opera Software AS | — | whitelisted |
3972 | opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3972 | opera.exe | 172.217.18.206:80 | clients1.google.com | Google Inc. | US | whitelisted |
3972 | opera.exe | 159.53.85.137:80 | chase.com | JPMorgan Chase & Co. | US | suspicious |
3972 | opera.exe | 185.26.182.112:80 | sitecheck2.opera.com | Opera Software AS | — | malicious |
3972 | opera.exe | 185.26.182.112:443 | sitecheck2.opera.com | Opera Software AS | — | malicious |
3972 | opera.exe | 104.121.24.251:80 | ocsp.entrust.net | Akamai Technologies, Inc. | NL | whitelisted |
3972 | opera.exe | 104.123.50.17:80 | crl.entrust.net | Akamai Technologies, Inc. | US | whitelisted |
3972 | opera.exe | 159.53.98.41:443 | sites.chase.com | JPMorgan Chase & Co. | US | unknown |
3972 | opera.exe | 159.53.119.16:443 | rf15.chase.com | JPMorgan Chase & Co. | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
clients1.google.com |
| whitelisted |
chase.com |
| suspicious |
sitecheck2.opera.com |
| whitelisted |
www.chase.com |
| whitelisted |
ocsp.entrust.net |
| whitelisted |
crl.entrust.net |
| whitelisted |
sites.chase.com |
| unknown |
rf15.chase.com |
| unknown |
Threats
Process | Message |
|---|---|
mmc.exe | Constructor: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | OnInitialize: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | AddIcons: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|
mmc.exe | ProcessCommandLineArguments: Microsoft.TaskScheduler.SnapIn.TaskSchedulerSnapIn
|