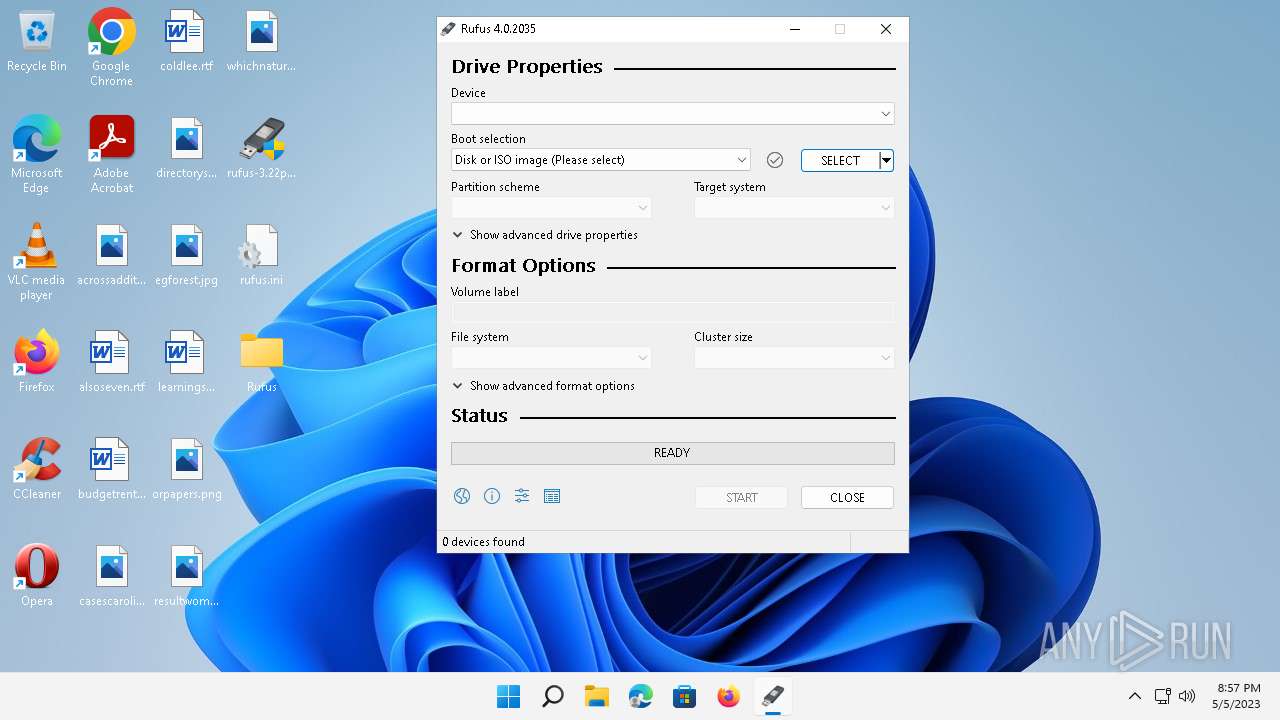
| File name: | rufus-3.22p.exe |
| Full analysis: | https://app.any.run/tasks/d5853a1f-0cbc-4e4d-905b-c4723b72eb26 |
| Verdict: | Malicious activity |
| Analysis date: | May 05, 2023, 20:56:21 |
| OS: | Windows 11 Professional (build: 22000, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, UPX compressed |
| MD5: | F3A93569CE2AA9409E2FFBA3D7EDB4DB |
| SHA1: | F68E9D61523742E40FF2760972FEB40286BDEF55 |
| SHA256: | AC2A1743BBFC19268C36280B50A003366D41854863D4808099CD87F77FA5F433 |
| SSDEEP: | 24576:hqGBPKaIPx+wa6cu0gQYBGHsk/ujEsLKhN33sYhXvDW2VIPIwzxcbMycXJnGjTXB:kGBPKaX5TkWnU5KhyaDHYIoHXcB |
MALICIOUS
No malicious indicators.SUSPICIOUS
Executable content was dropped or overwritten
- rufus-3.22p.exe (PID: 3280)
Executes as Windows Service
- vds.exe (PID: 6236)
- vds.exe (PID: 4088)
INFO
No info indicators.
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (64.2) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (15.6) |
| .exe | | | Win32 Executable (generic) (10.6) |
| .exe | | | Generic Win/DOS Executable (4.7) |
| .exe | | | DOS Executable Generic (4.7) |
EXIF
EXE
| ProductVersion: | 3.22.2009 |
|---|---|
| ProductName: | Rufus |
| OriginalFileName: | rufus-3.22.exe |
| LegalTrademarks: | https://www.gnu.org/licenses/gpl-3.0.html |
| LegalCopyright: | © 2011-2023 Pete Batard (GPL v3) |
| InternalName: | Rufus |
| FileVersion: | 3.22.2009 |
| FileDescription: | Rufus |
| CompanyName: | Akeo Consulting |
| Comments: | https://rufus.ie |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Windows NT 32-bit |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 3.22.2009.0 |
| FileVersionNumber: | 3.22.2009.0 |
| Subsystem: | Windows GUI |
| SubsystemVersion: | 4 |
| ImageVersion: | 1 |
| OSVersion: | 4 |
| EntryPoint: | 0x3e8ef0 |
| UninitializedDataSize: | 2732032 |
| InitializedDataSize: | 45056 |
| CodeSize: | 1368064 |
| LinkerVersion: | 2.4 |
| PEType: | PE32 |
| ImageFileCharacteristics: | Executable, No line numbers, No symbols, 32-bit, No debug |
| TimeStamp: | 2023:03:25 13:50:29+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 25-Mar-2023 13:50:29 |
| TLS Callbacks: | 1 callback(s) detected. |
| Comments: | https://rufus.ie |
| CompanyName: | Akeo Consulting |
| FileDescription: | Rufus |
| FileVersion: | 3.22.2009 |
| InternalName: | Rufus |
| LegalCopyright: | © 2011-2023 Pete Batard (GPL v3) |
| LegalTrademarks: | https://www.gnu.org/licenses/gpl-3.0.html |
| OriginalFilename: | rufus-3.22.exe |
| ProductName: | Rufus |
| ProductVersion: | 3.22.2009 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 25-Mar-2023 13:50:29 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
UPX0 | 0x00001000 | 0x0029B000 | 0x00000000 | IMAGE_SCN_CNT_UNINITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
UPX1 | 0x0029C000 | 0x0014E000 | 0x0014DC00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 7.99981 |
.rsrc | 0x003EA000 | 0x0000B000 | 0x0000A600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 3.94705 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.21284 | 2238 | UNKNOWN | UNKNOWN | RT_MANIFEST |
2 | 3.68423 | 9640 | UNKNOWN | UNKNOWN | RT_ICON |
3 | 3.77127 | 4264 | UNKNOWN | UNKNOWN | RT_ICON |
4 | 3.98144 | 2440 | UNKNOWN | UNKNOWN | RT_ICON |
5 | 4.04318 | 1128 | UNKNOWN | UNKNOWN | RT_ICON |
101 | 7.92154 | 2398 | UNKNOWN | UNKNOWN | RT_DIALOG |
102 | 7.32466 | 316 | UNKNOWN | UNKNOWN | RT_DIALOG |
103 | 7.59008 | 470 | UNKNOWN | UNKNOWN | RT_DIALOG |
104 | 7.83572 | 1300 | UNKNOWN | UNKNOWN | RT_DIALOG |
105 | 6.84179 | 172 | UNKNOWN | UNKNOWN | RT_DIALOG |
Imports
ADVAPI32.dll |
COMCTL32.dll |
COMDLG32.DLL |
CRYPT32.dll |
GDI32.dll |
KERNEL32.DLL |
SETUPAPI.dll |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
Total processes
141
Monitored processes
7
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3280 | "C:\Users\admin\Desktop\rufus-3.22p.exe" | C:\Users\admin\Desktop\rufus-3.22p.exe | explorer.exe | ||||||||||||
User: admin Company: Akeo Consulting Integrity Level: HIGH Description: Rufus Exit code: 0 Version: 3.22.2009 Modules
| |||||||||||||||
| 3612 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.22000.653 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4088 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 258 Version: 10.0.22000.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6236 | C:\Windows\System32\vds.exe | C:\Windows\System32\vds.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Virtual Disk Service Exit code: 0 Version: 10.0.22000.1 (WinBuild.160101.0800) | |||||||||||||||
| 6788 | C:\Windows\System32\vdsldr.exe -Embedding | C:\Windows\System32\vdsldr.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Virtual Disk Service Loader Exit code: 0 Version: 10.0.22000.653 (WinBuild.160101.0800) | |||||||||||||||
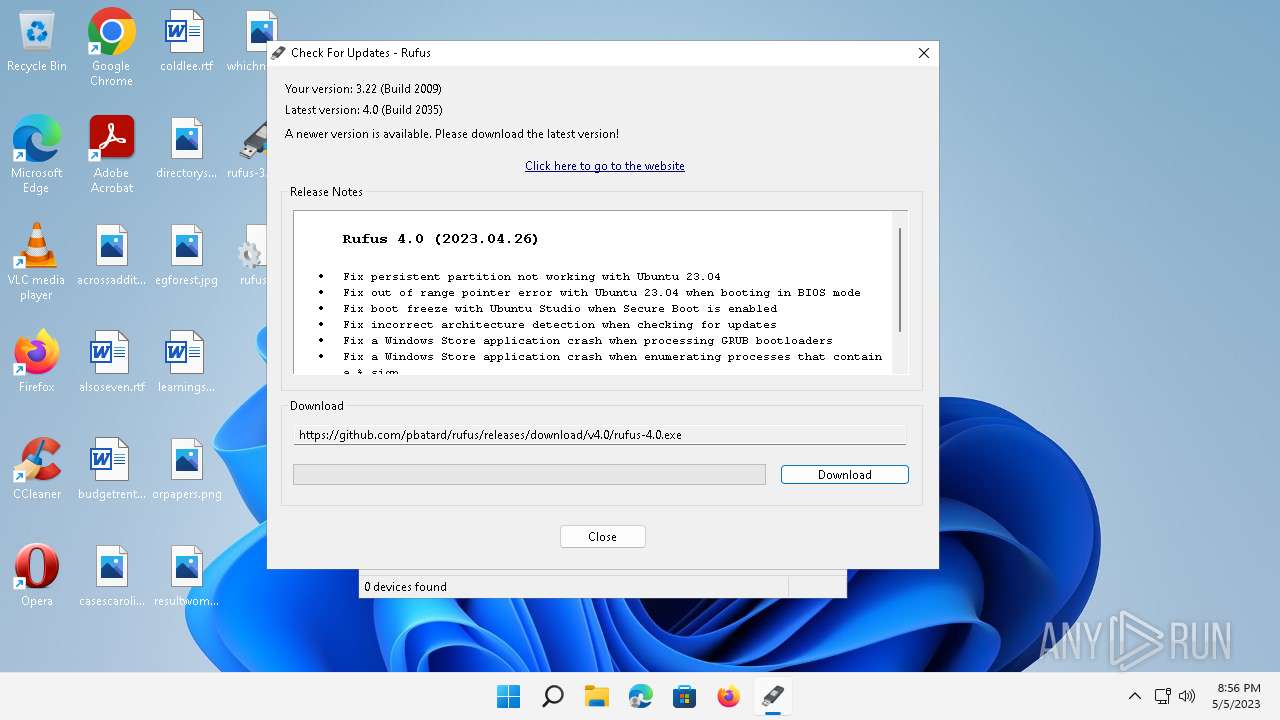
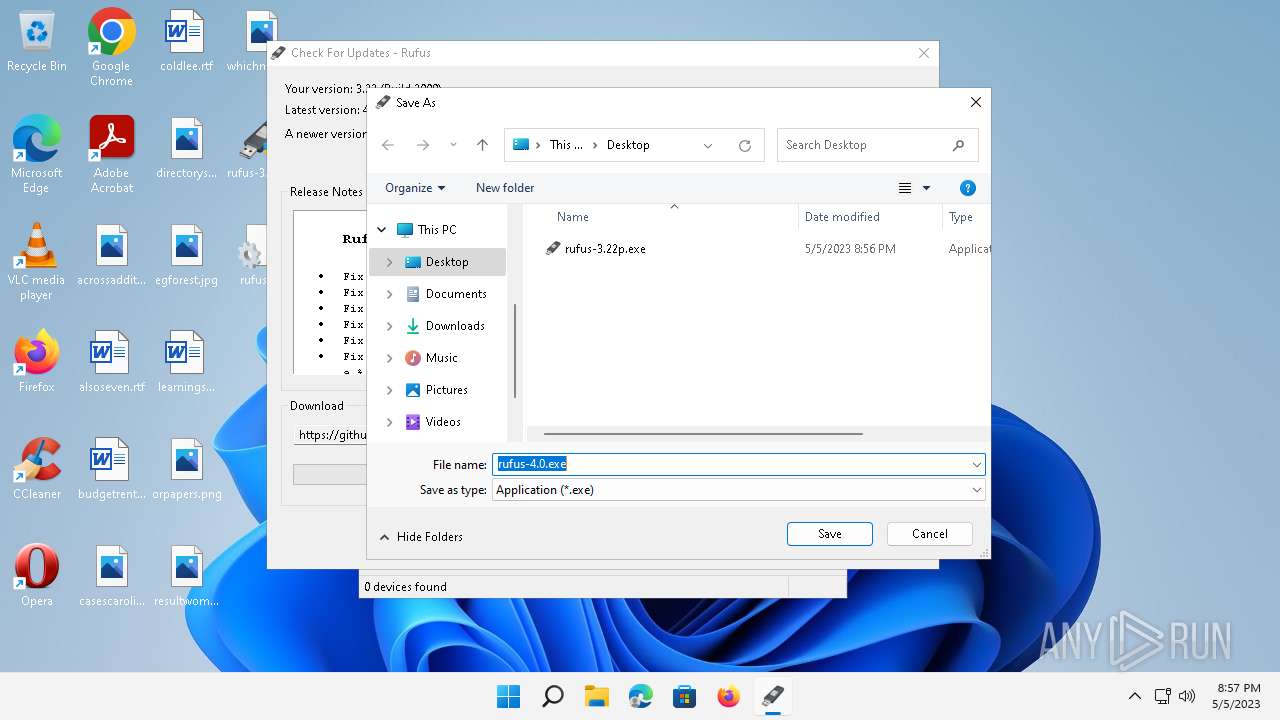
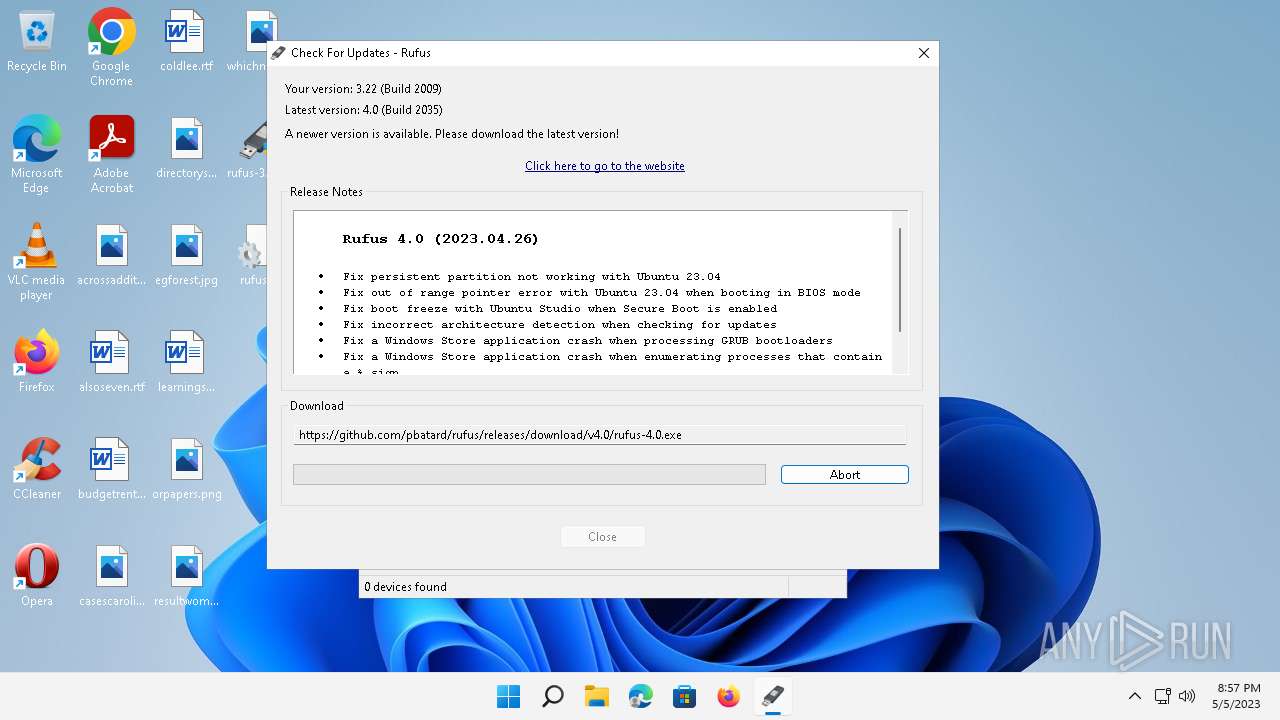
| 6928 | Rufus -w 150 | C:\Users\admin\Downloads\rufus-4.0.exe | — | rufus-3.22p.exe | |||||||||||
User: admin Company: Akeo Consulting Integrity Level: HIGH Description: Rufus Exit code: 0 Version: 4.0.2035 | |||||||||||||||
| 7008 | "C:\Users\admin\Desktop\rufus-3.22p.exe" | C:\Users\admin\Desktop\rufus-3.22p.exe | — | explorer.exe | |||||||||||
User: admin Company: Akeo Consulting Integrity Level: MEDIUM Description: Rufus Exit code: 3221226540 Version: 3.22.2009 Modules
| |||||||||||||||
Total events
404
Read events
340
Write events
0
Delete events
64
Modification events
| (PID) Process: | (3280) rufus-3.22p.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{396DE638-D98A-4680-8EDA-662627DB2776}User |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3280) rufus-3.22p.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3280) rufus-3.22p.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{396DE638-D98A-4680-8EDA-662627DB2776}Machine |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3280) rufus-3.22p.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{396DE638-D98A-4680-8EDA-662627DB2776}Machine\Software |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3280) rufus-3.22p.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{396DE638-D98A-4680-8EDA-662627DB2776}Machine\Software\Microsoft |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3280) rufus-3.22p.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{396DE638-D98A-4680-8EDA-662627DB2776}Machine\Software\Microsoft\Windows |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3280) rufus-3.22p.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{396DE638-D98A-4680-8EDA-662627DB2776}Machine\Software\Microsoft\Windows\CurrentVersion |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3280) rufus-3.22p.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{396DE638-D98A-4680-8EDA-662627DB2776}Machine\Software\Microsoft\Windows\CurrentVersion\Policies |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3280) rufus-3.22p.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{396DE638-D98A-4680-8EDA-662627DB2776}Machine\Software\Microsoft\Windows\CurrentVersion\Policies\Explorer |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (3280) rufus-3.22p.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Objects\{396DE638-D98A-4680-8EDA-662627DB2776}Machine\Software\Policies |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
4
Suspicious files
44
Text files
26
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3280 | rufus-3.22p.exe | C:\Windows\SysWOW64\GroupPolicy\gpt.ini | text | |
MD5:39DFFC602ED934569F26BE44EC645814 | SHA256:B57A88E5B1ACF3A784BE88B87FA3EE1F0991CB7C1C66DA423F3595FFC6E0C5C2 | |||
| 3280 | rufus-3.22p.exe | C:\Windows\System32\GroupPolicy\GPT.INI | text | |
MD5:48C02A03271BE85C9EAE887B14E647F4 | SHA256:3245BD59627D59177281E8DF3BAA58CF1DF2809E37E9EEFE9B88A1C340E11097 | |||
| 3280 | rufus-3.22p.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | der | |
MD5:5E6C2D7CD3C07FA6C9A18DE4322212D4 | SHA256:245BADC5C7B935B91CDA6E0FBED06140705B58161C8486E55A0DD9F0F50F1ACC | |||
| 3280 | rufus-3.22p.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | binary | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 3280 | rufus-3.22p.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:2B98084E593C634913B8B76D8AA852ED | SHA256:03EFE16165BF50D13499486BA522E4AA078D7EC913CF75AA5E7E3D1ACE233052 | |||
| 3280 | rufus-3.22p.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:10E0B4A9845D361EF88AE08EC87605DA | SHA256:F27337E0DBAC0E083486379AAE40A5AD9DFBD7E371F7B6B028B8DFE4620FF908 | |||
| 3280 | rufus-3.22p.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\50CD3D75D026C82E2E718570BD6F44D0_D222662A57BAA60D2F5EA0D2CC7B2F1C | binary | |
MD5:328614BF76BC292BF10C65887254E90E | SHA256:A06DED41B2BA6368DFA35DDBC3F44DD7C3016321DE762519945B5D4651C2D016 | |||
| 3280 | rufus-3.22p.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B398B80134F72209547439DB21AB308D_ADE4E4D3A3BCBCA5C39C54D362D88565 | binary | |
MD5:10318B083FB7E82F46EFC311E3DD4552 | SHA256:DF7BE8EBCE39619512513436928E82252C059F9565B2D8DAF2308AAC61257D54 | |||
| 3280 | rufus-3.22p.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\5C651ZXJ\Rufus_win[1].ver | text | |
MD5:9B0BB58D410A957B49995DB0FC2417FB | SHA256:22B2E6AAB7E2DEAE7C55A2143090D7EFE811CDEAEEC2F89AB30F621873BEA03A | |||
| 3280 | rufus-3.22p.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\5C651ZXJ\Rufus_win.ver[1].sig | binary | |
MD5:5E0841A336C7D7DAD4A3E70131431163 | SHA256:F0711B1C2A23A74C07A18685532F5A5769E432CE5CC2EBFDC004B7190E152FE0 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
14
TCP/UDP connections
20
DNS requests
18
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 304 | 8.248.131.254:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?9c054bc903043d8b | US | — | — | whitelisted |
— | — | GET | 200 | 23.56.202.135:80 | http://x1.c.lencr.org/ | GB | binary | 717 b | whitelisted |
— | — | GET | 200 | 104.18.32.68:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEDPXCKiRQFMZ4qW70zm5rW4%3D | US | der | 765 b | whitelisted |
— | — | GET | 200 | 152.199.19.74:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FYHKj6JjF6UBieQioTYpFsuEriQQUtnf6aUhHn1MS1cLqBzJ2B9GXBxkCEHsFsdRJaFFE98mJ0pwZnRI%3D | US | binary | 5 b | shared |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | binary | 471 b | whitelisted |
— | — | GET | 200 | 104.18.32.68:80 | http://crl.comodoca.com/AAACertificateServices.crl | US | binary | 506 b | whitelisted |
— | — | GET | 200 | 152.199.19.74:80 | http://s.symcd.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ%2FYHKj6JjF6UBieQioTYpFsuEriQQUtnf6aUhHn1MS1cLqBzJ2B9GXBxkCEHsFsdRJaFFE98mJ0pwZnRI%3D | US | binary | 5 b | shared |
— | — | GET | 200 | 104.18.32.68:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRd0JozUYXMqqW4y4zJTrLcMCRSkAQUgTKSQSsozUbIxKLGKjkS7EipPxQCEQC%2FsVABu%2FWS1JYqd5fqc2%2Bj | US | der | 638 b | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQrHR6YzPN2BNbByL0VoiTIBBMAOAQUCrwIKReMpTlteg7OM8cus%2B37w3oCEAzQqL7GMs%2FmReygqbCE%2Bxw%3D | US | binary | 313 b | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://s.symcb.com/universal-root.crl | US | der | 1.23 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 40.126.32.72:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | suspicious |
— | — | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
— | — | 185.199.108.133:443 | objects.githubusercontent.com | FASTLY | US | malicious |
— | — | 8.248.131.254:80 | ctldl.windowsupdate.com | LEVEL3 | US | suspicious |
— | — | 40.126.32.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | suspicious |
— | — | 104.18.32.68:80 | crl.comodoca.com | CLOUDFLARENET | — | suspicious |
— | — | 185.199.108.153:443 | rufus.ie | FASTLY | US | shared |
— | — | 185.199.111.153:443 | rufus.ie | FASTLY | US | shared |
— | — | 185.199.111.133:443 | objects.githubusercontent.com | FASTLY | US | suspicious |
— | — | 140.82.121.4:443 | github.com | GITHUB | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
login.live.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
rufus.ie |
| suspicious |
x1.c.lencr.org |
| whitelisted |
github.com |
| malicious |
objects.githubusercontent.com |
| shared |
www.msftconnecttest.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
crl.comodoca.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
— | — | Misc activity | ET INFO Microsoft Connection Test |