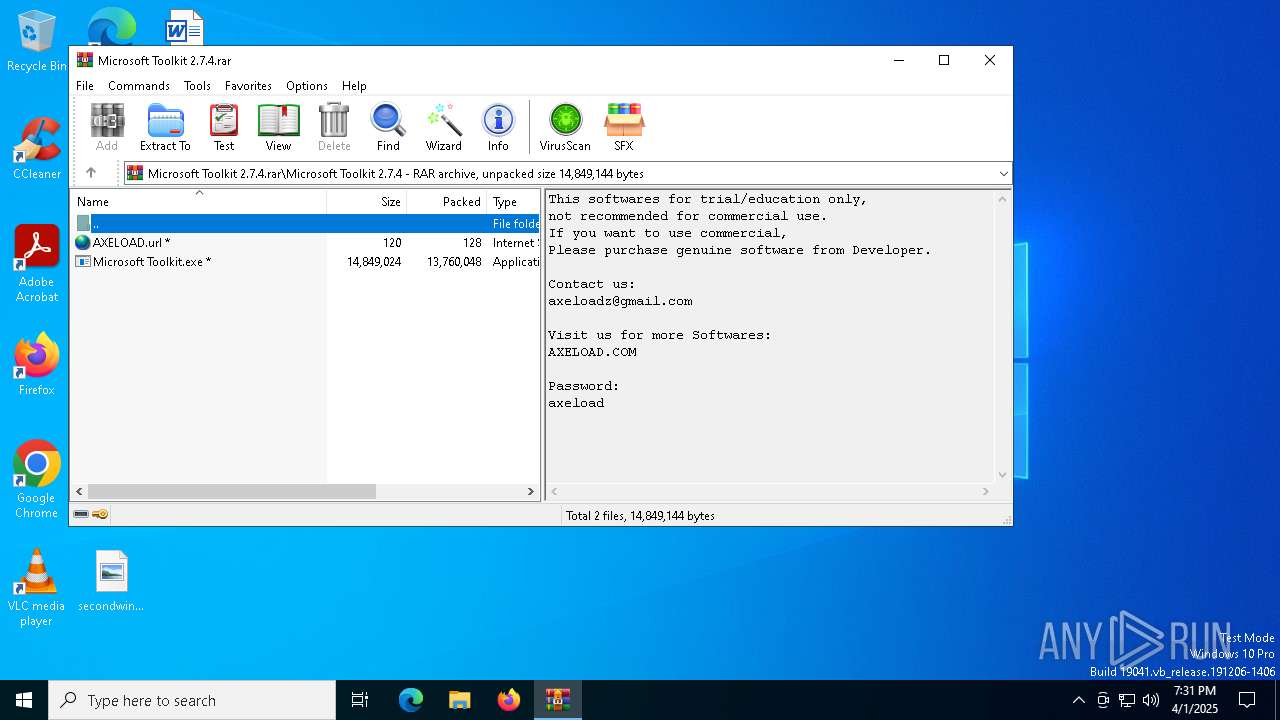
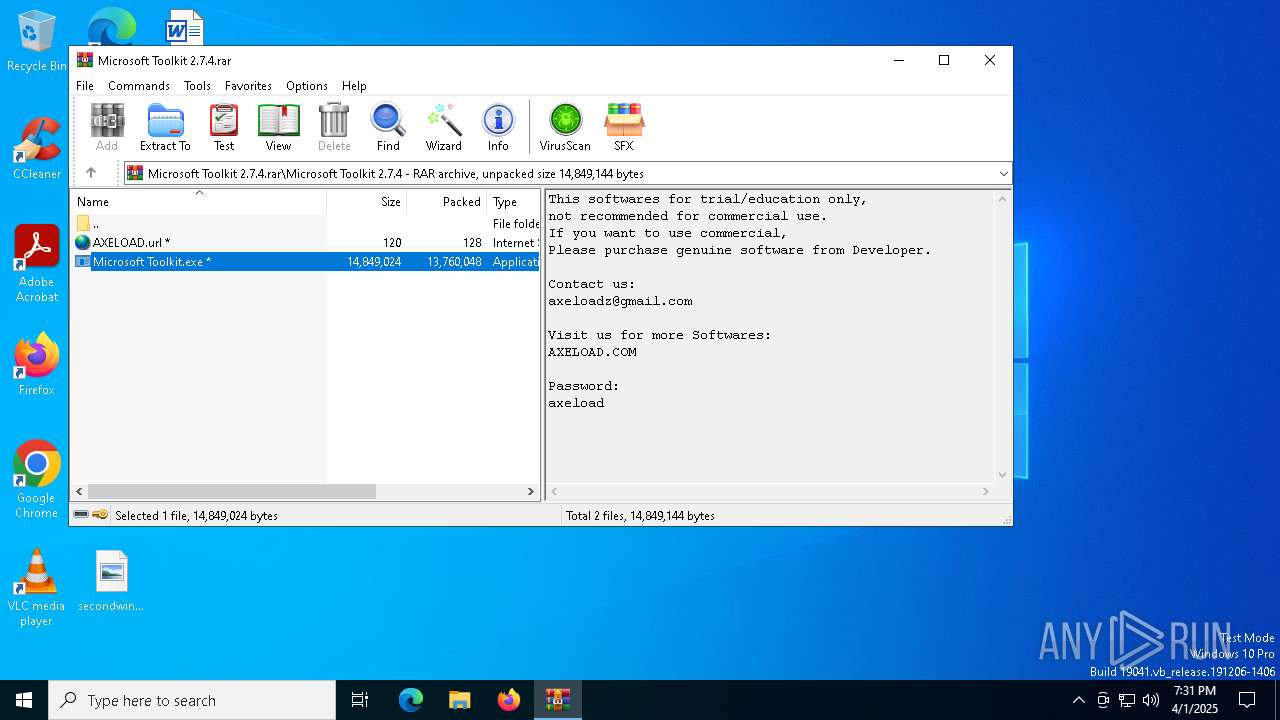
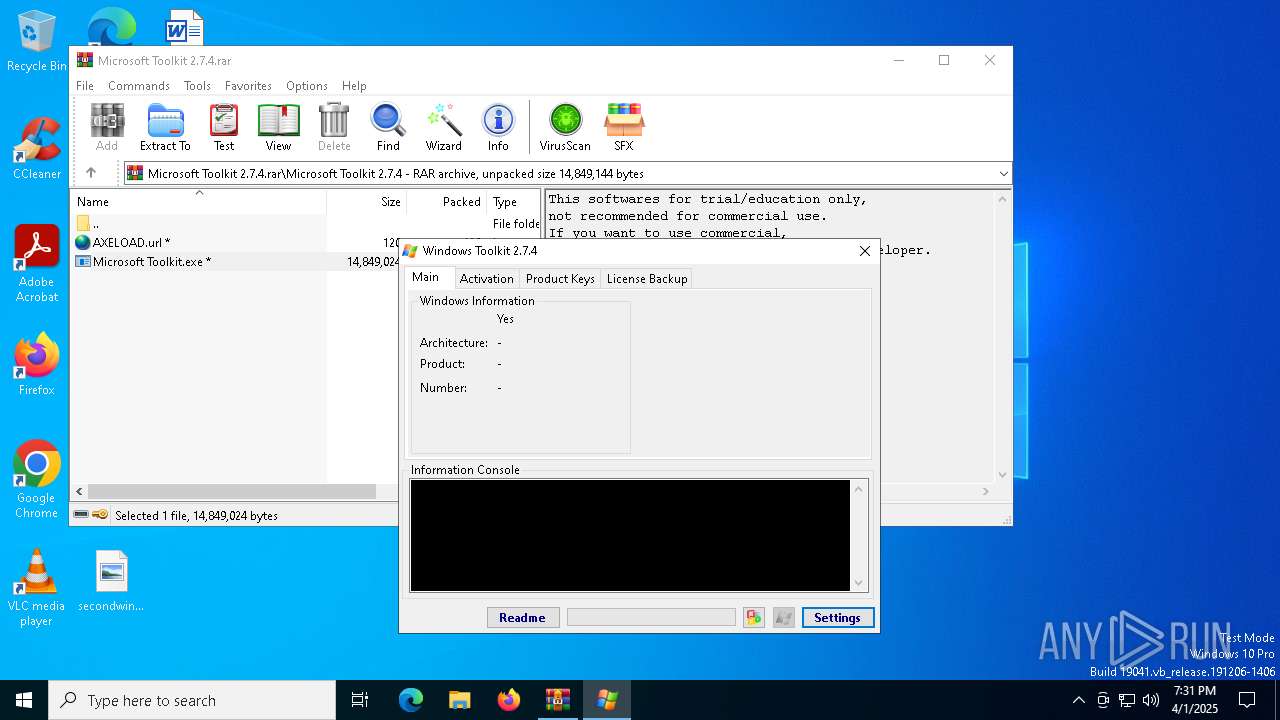
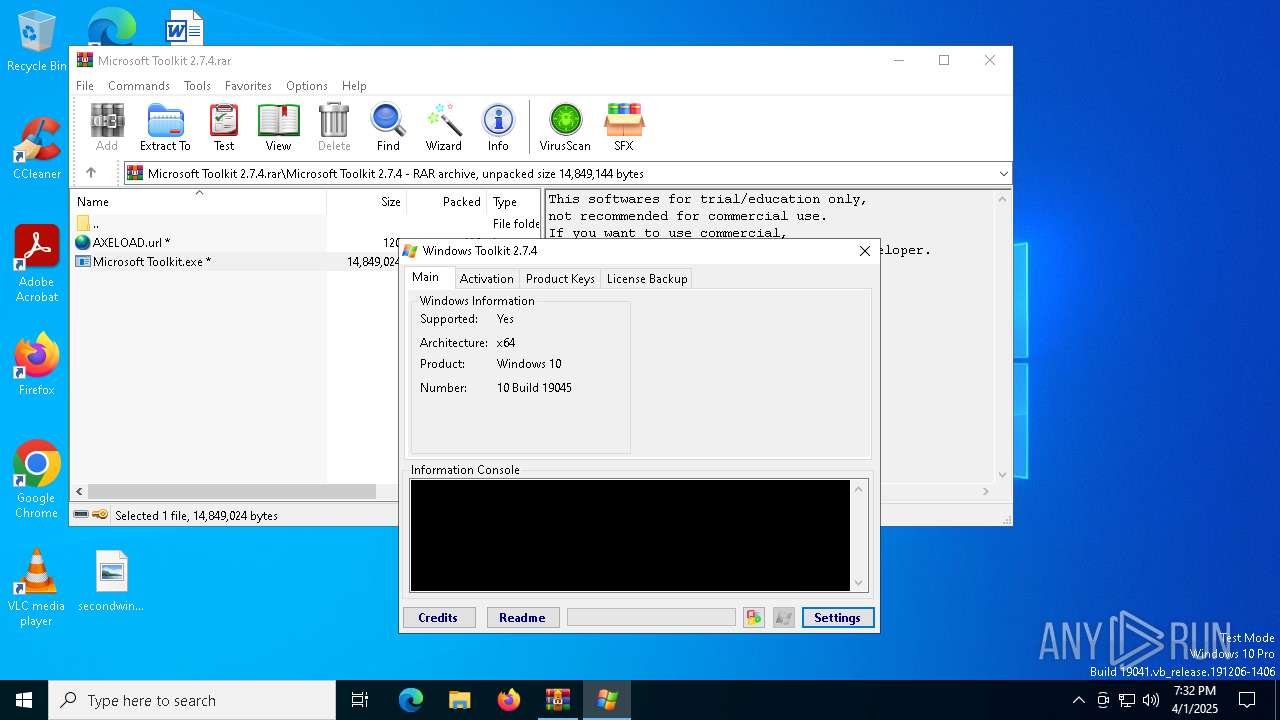
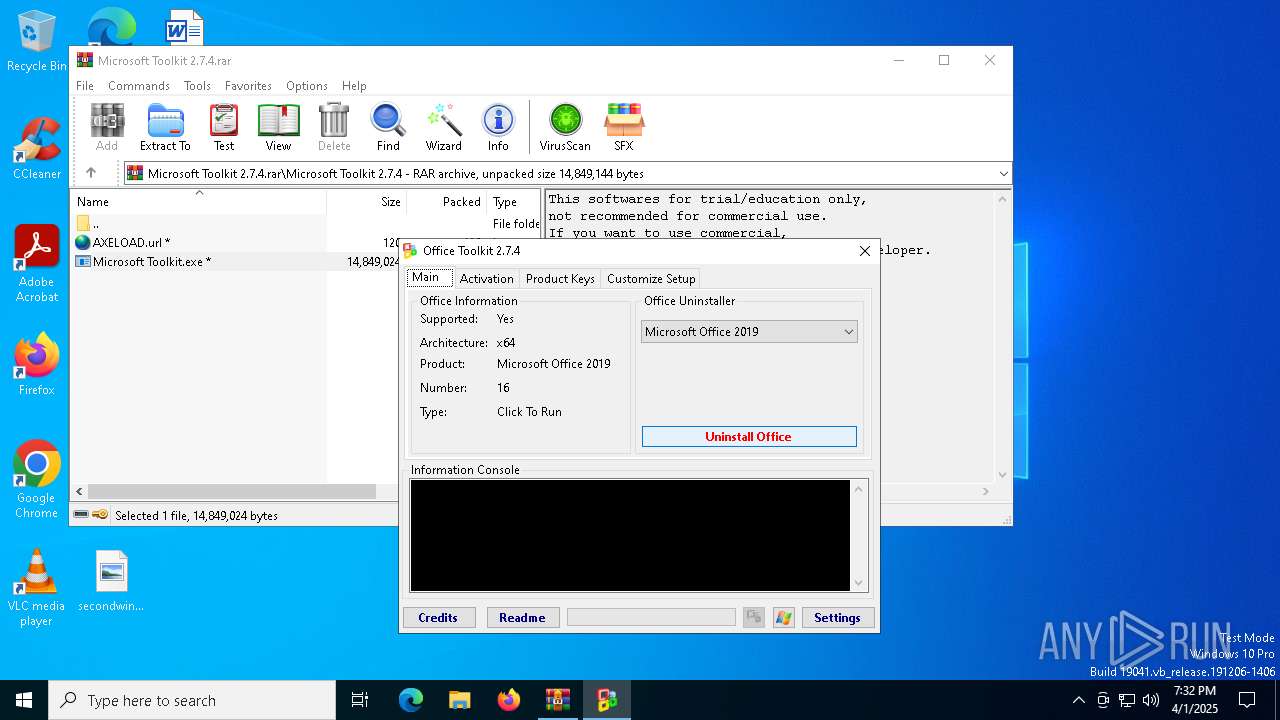
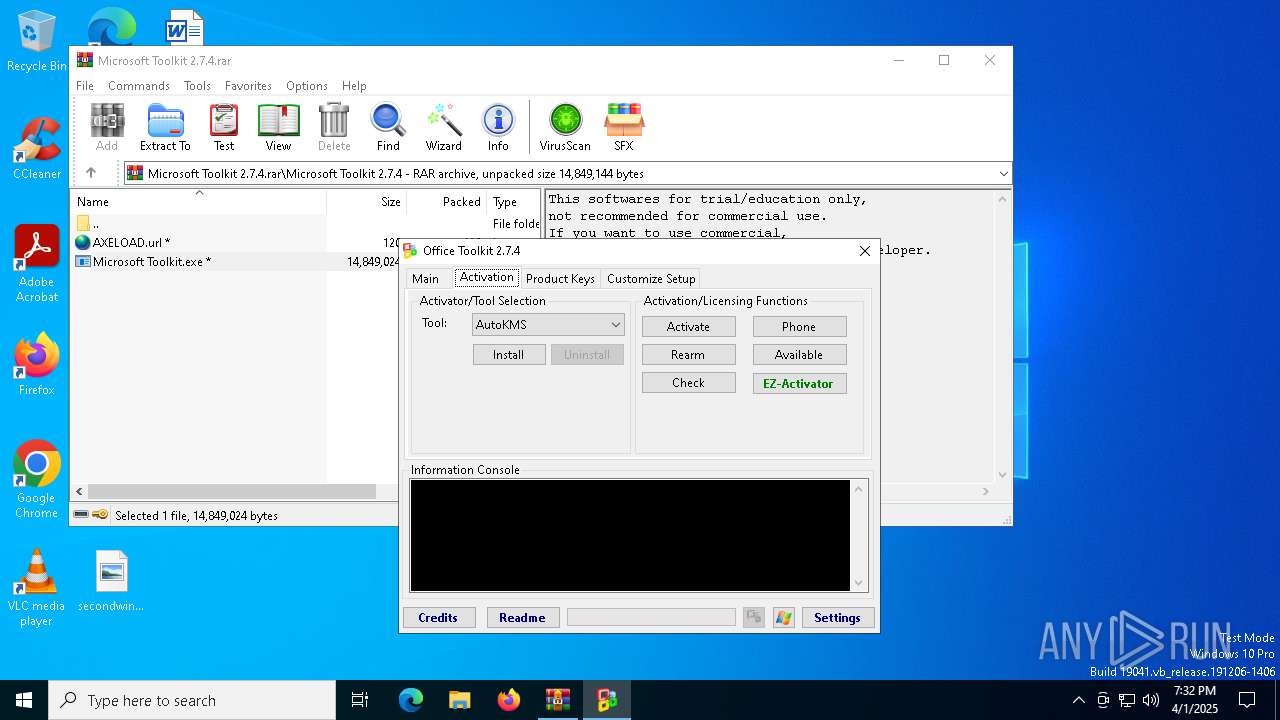
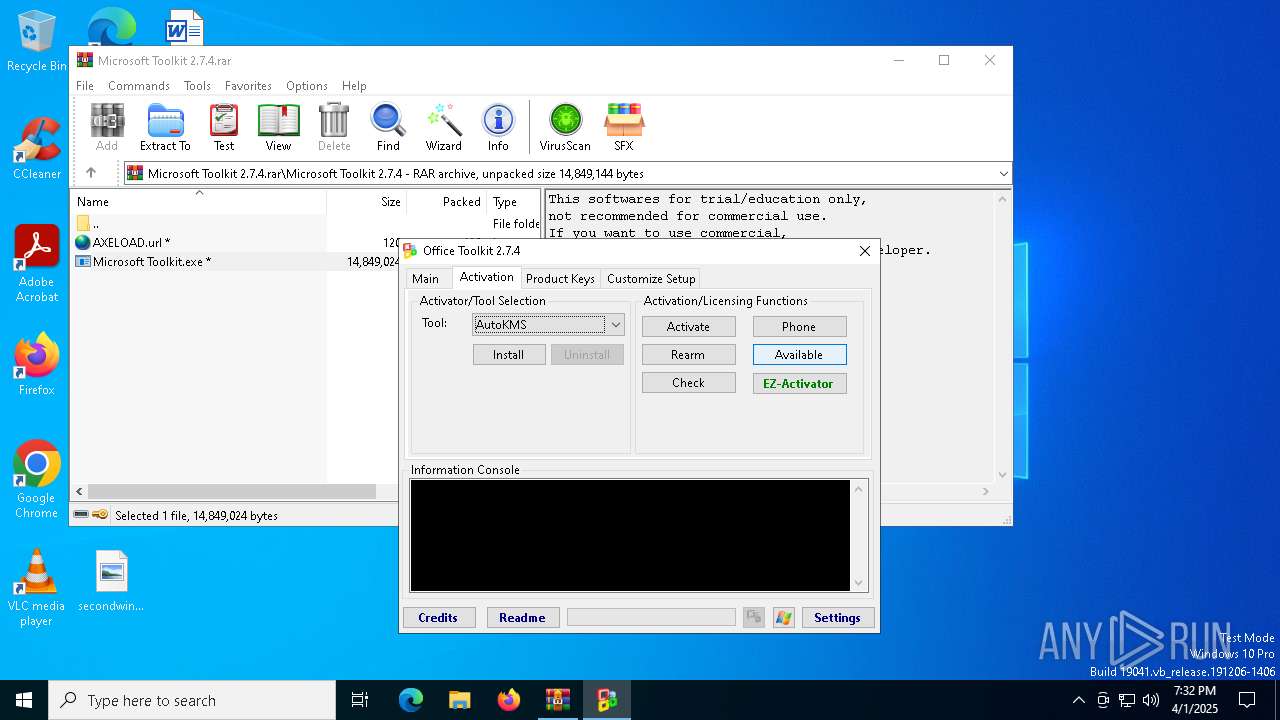
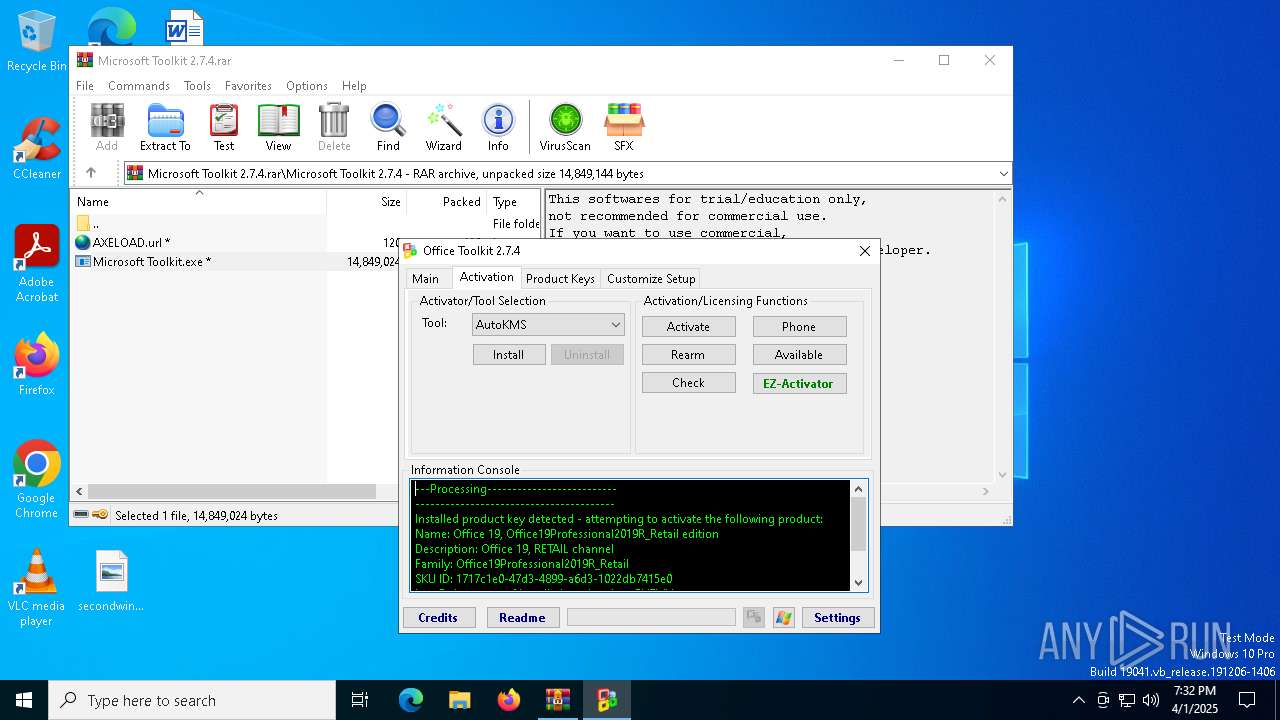
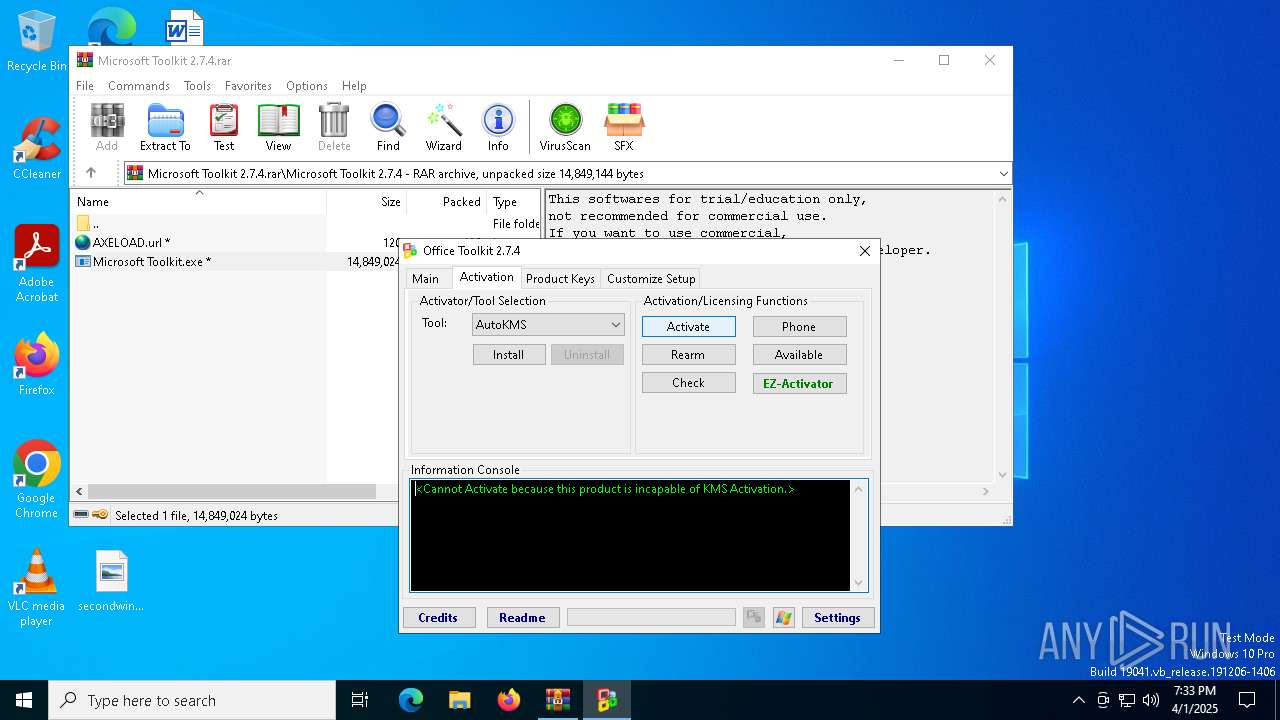
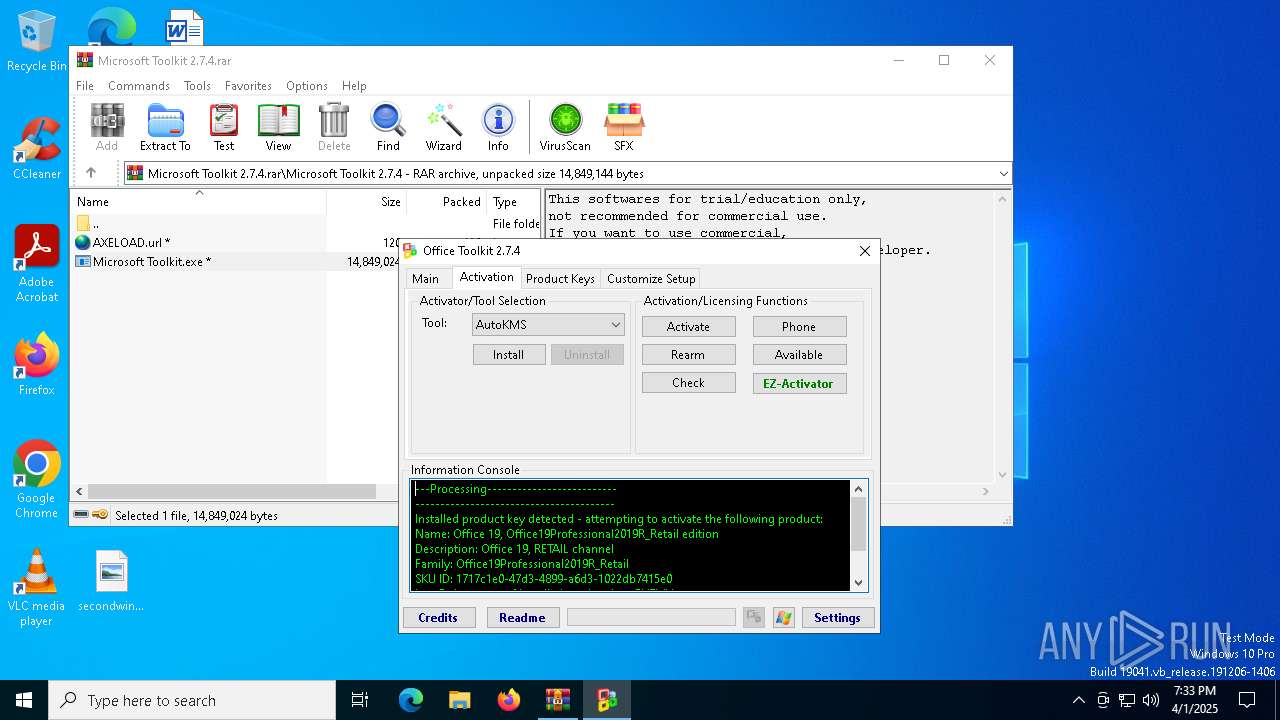
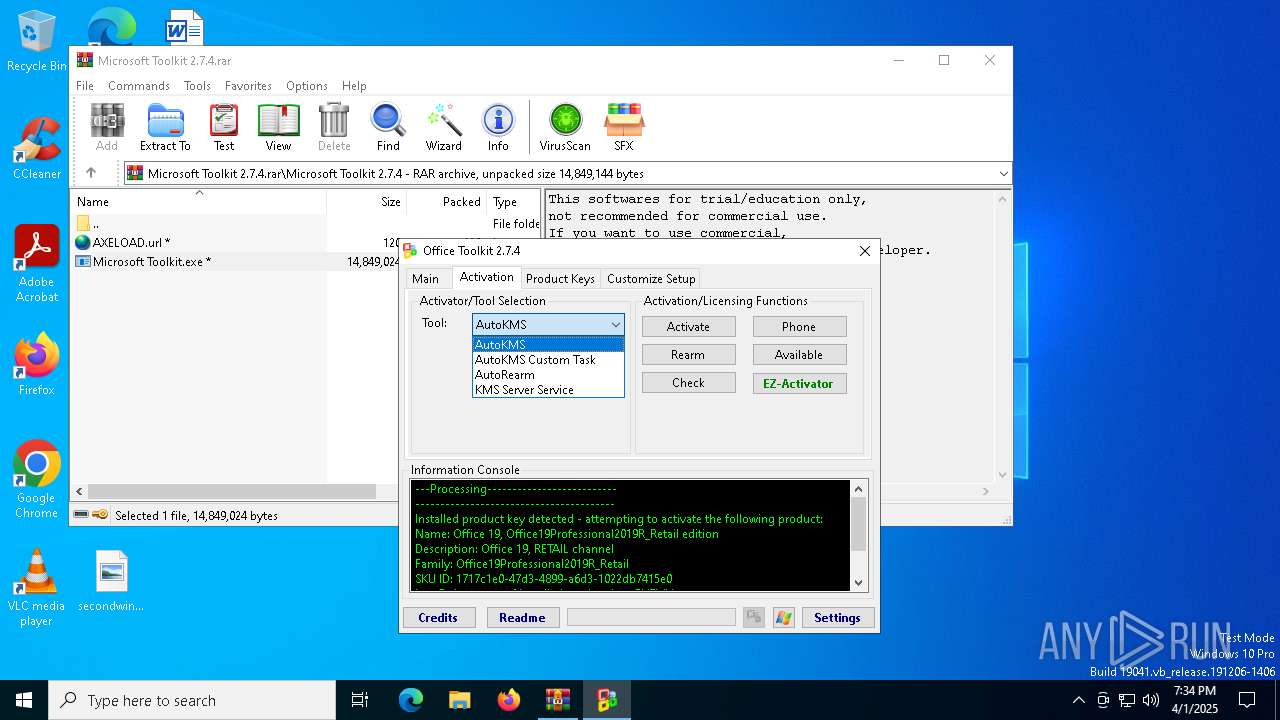
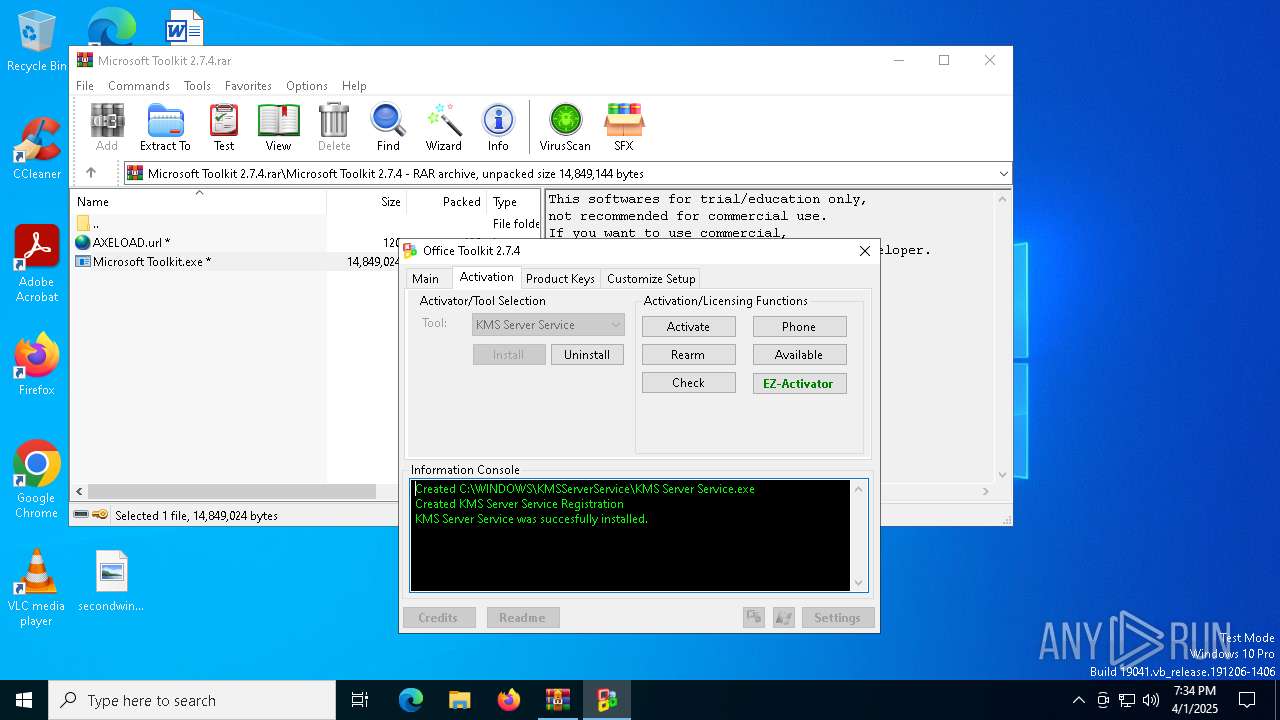
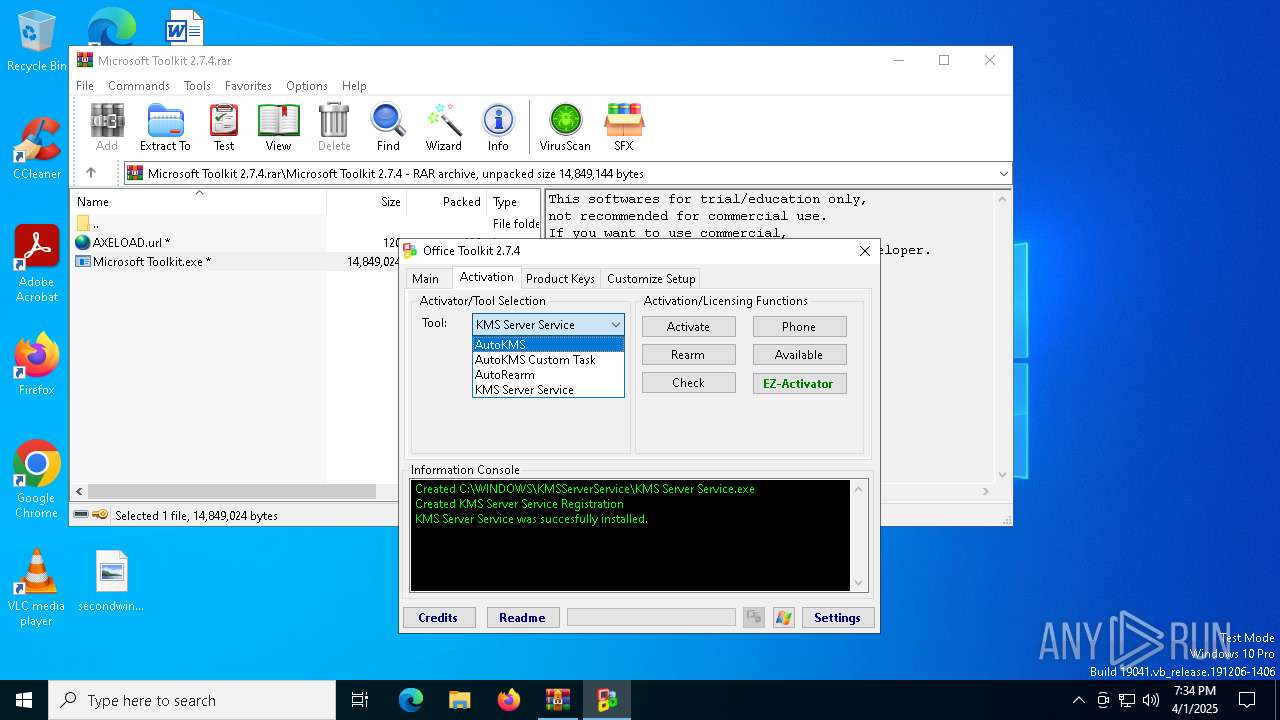
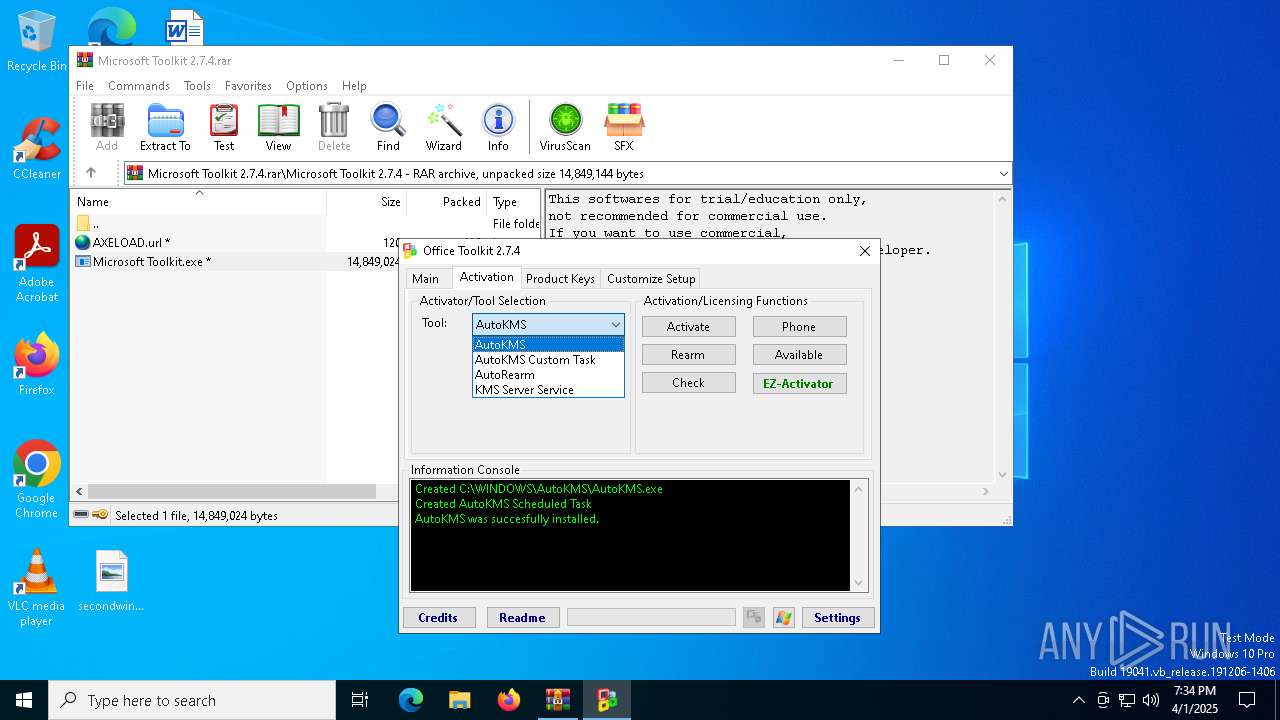
| File name: | Microsoft Toolkit 2.7.4.rar |
| Full analysis: | https://app.any.run/tasks/42b044e4-ebe7-4725-b90e-0fa7b91eaa15 |
| Verdict: | Malicious activity |
| Analysis date: | April 01, 2025, 19:31:29 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | D088E29796C8D4FAF8331D84B7C666BD |
| SHA1: | EFCE45F310CFF0E391DFA3B74BD76D5C747FF822 |
| SHA256: | AC14AF71AE41499F6C16E0DD38A290503641A7CE92A2AF003A2D959CFAD4501F |
| SSDEEP: | 196608:Wnb6Qh50/VpuyWWWkSNOiosPjUntNWHIgf95iV51b:WnbWuyQFOiItknji31b |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 7428)
- Microsoft Toolkit.exe (PID: 7764)
Uses NETSH.EXE to delete a firewall rule or allowed programs
- cmd.exe (PID: 7268)
- cmd.exe (PID: 7200)
- cmd.exe (PID: 1672)
- cmd.exe (PID: 4452)
- cmd.exe (PID: 5280)
- cmd.exe (PID: 7696)
Creates or modifies Windows services
- Microsoft Toolkit.exe (PID: 7764)
Starts CMD.EXE for commands execution
- Microsoft Toolkit.exe (PID: 7764)
Uses NETSH.EXE to add a firewall rule or allowed programs
- cmd.exe (PID: 7300)
- cmd.exe (PID: 7240)
- cmd.exe (PID: 5868)
- cmd.exe (PID: 1096)
Executable content was dropped or overwritten
- Microsoft Toolkit.exe (PID: 7764)
Executes as Windows Service
- KMS Server Service.exe (PID: 6828)
INFO
Executable content was dropped or overwritten
- WinRAR.exe (PID: 7428)
Local mutex for internet shortcut management
- WinRAR.exe (PID: 7428)
Reads the machine GUID from the registry
- Microsoft Toolkit.exe (PID: 7764)
Creates files in the program directory
- Microsoft Toolkit.exe (PID: 7764)
Reads the computer name
- Microsoft Toolkit.exe (PID: 7764)
- KMS Server Service.exe (PID: 6828)
Checks supported languages
- Microsoft Toolkit.exe (PID: 7764)
- KMS Server Service.exe (PID: 6828)
Found Base64 encoded reference to WMI classes (YARA)
- Microsoft Toolkit.exe (PID: 7764)
Reads the software policy settings
- slui.exe (PID: 7564)
- slui.exe (PID: 6744)
Checks proxy server information
- slui.exe (PID: 6744)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|
Total processes
167
Monitored processes
37
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 728 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1012 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1096 | "cmd.exe" /C netsh advfirewall firewall add rule name="Microsoft Toolkit" dir=out program="C:\Users\admin\AppData\Local\Temp\Rar$EXb7428.22190\Microsoft Toolkit 2.7.4\Microsoft Toolkit.exe" localport=1688 protocol=TCP action=allow remoteip=any | C:\Windows\System32\cmd.exe | — | Microsoft Toolkit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1616 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1672 | "cmd.exe" /C netsh advfirewall firewall delete rule name="Microsoft Toolkit" | C:\Windows\System32\cmd.exe | — | Microsoft Toolkit.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2108 | netsh advfirewall firewall delete rule name="Microsoft Toolkit" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2516 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3884 | netsh advfirewall firewall delete rule name=all program="C:\Users\admin\AppData\Local\Temp\Rar$EXb7428.22190\Microsoft Toolkit 2.7.4\Microsoft Toolkit.exe" | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4180 | netsh advfirewall firewall delete rule name=all localport=1688 | C:\Windows\System32\netsh.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Network Command Shell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4244 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
10 886
Read events
10 866
Write events
20
Delete events
0
Modification events
| (PID) Process: | (7428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (7428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (7428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (7428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (7428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\Microsoft Toolkit 2.7.4.rar | |||
| (PID) Process: | (7428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (7428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (7428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (7428) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (7764) Microsoft Toolkit.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\sppsvc |
| Operation: | write | Name: | Start |
Value: 2 | |||
Executable files
3
Suspicious files
1
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7428.22190\Microsoft Toolkit 2.7.4\AXELOAD.url | binary | |
MD5:F469C60BCB1308220EE4EA4F2AC4C82A | SHA256:F18C702154EF461727629BF2E7C1C79CABBBA3DE4140851B4B515BE627C8B62D | |||
| 7764 | Microsoft Toolkit.exe | C:\ProgramData\Microsoft Toolkit\Settings.xml | xml | |
MD5:A97C232B9BE25E5437B15E1EA7DE11D6 | SHA256:062592BB39713ABB43C09B0A1B35B45570E1581E82CD7A23AE9AD0338E01518C | |||
| 7428 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXb7428.22190\Microsoft Toolkit 2.7.4\Microsoft Toolkit.exe | executable | |
MD5:B0CAE37BB6ADF5312DC7856F2F194DBB | SHA256:3F05F92525D7CAC6F46FB6CDF2C89CF880B48C8EEAD766A35D86F16745247418 | |||
| 7764 | Microsoft Toolkit.exe | C:\Windows\AutoKMS\AutoKMS.exe | executable | |
MD5:BCE8EB8B41D61377C0001F84352B3F34 | SHA256:473F333E8E994F7CC9B882CFE642BB70C89F8444B5277BA27929037769AFA163 | |||
| 7764 | Microsoft Toolkit.exe | C:\Windows\KMSServerService\KMS Server Service.exe | executable | |
MD5:367225C42AB51DE3AC826731B0897047 | SHA256:9832003CD5E7DA41CFC2941952CBD8709240770CABF9E6BC57C5B60F696C139E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
22
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
8104 | SIHClient.exe | GET | 200 | 23.59.18.102:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
8104 | SIHClient.exe | GET | 200 | 23.59.18.102:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.48.23.188:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5352 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.48.23.188:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2104 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.172.255.216:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8104 | SIHClient.exe | 4.175.87.197:443 | slscr.update.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
8104 | SIHClient.exe | 23.59.18.102:80 | www.microsoft.com | AKAMAI-AS | US | whitelisted |
8104 | SIHClient.exe | 40.69.42.241:443 | fe3cr.delivery.mp.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
activation.sls.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |