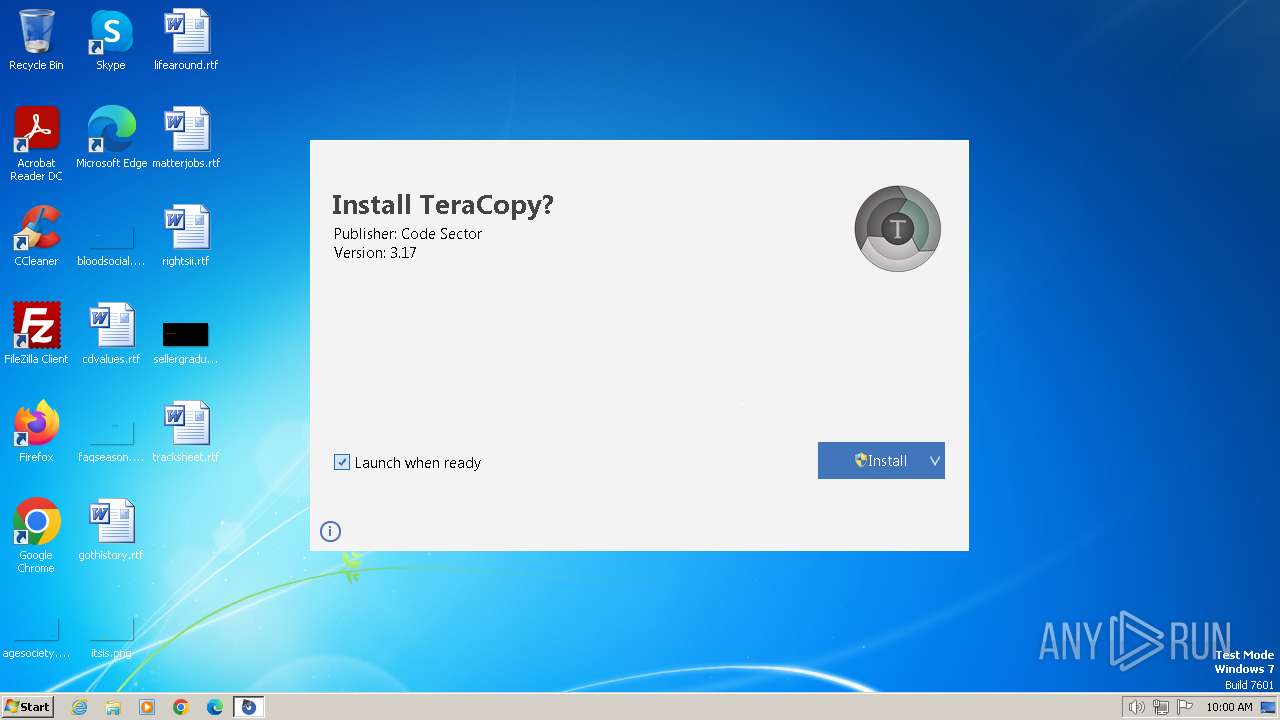
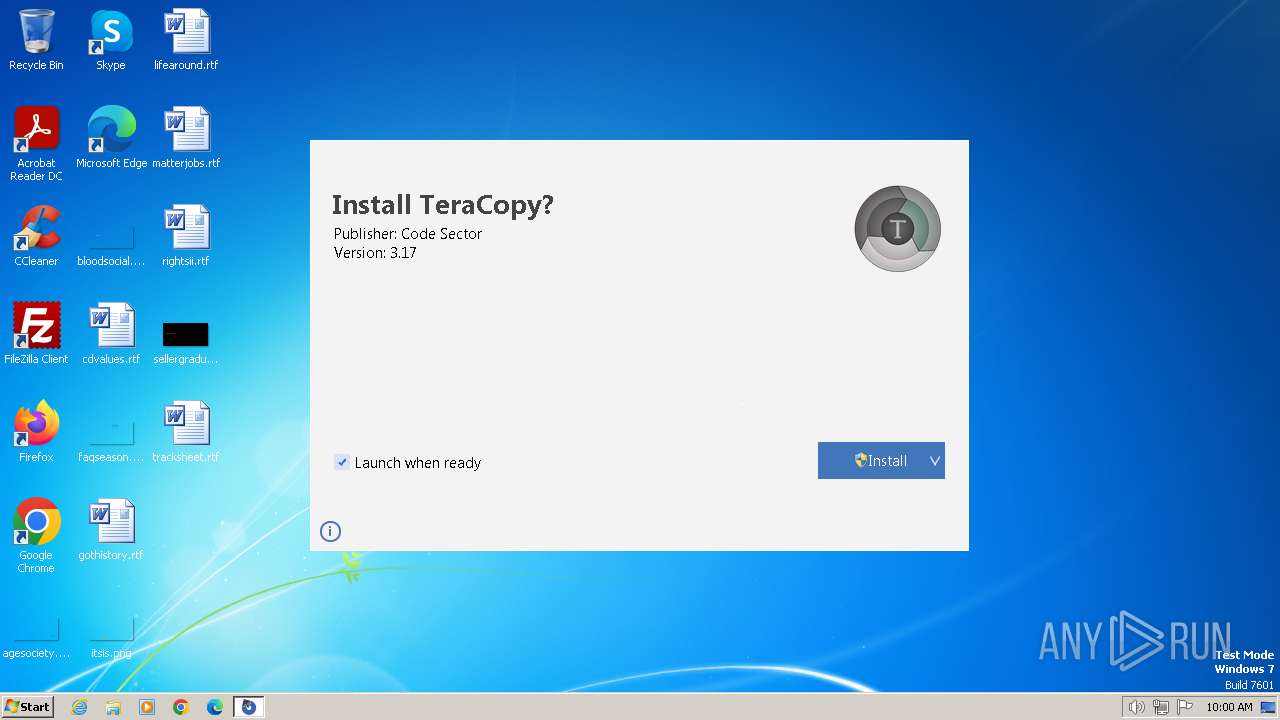
| download: | /files/teracopy.exe |
| Full analysis: | https://app.any.run/tasks/1d7ccc6c-5951-4287-97d3-4b31a5275a78 |
| Verdict: | Malicious activity |
| Analysis date: | April 15, 2024, 09:00:02 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | D704E453E065A23ED414927D9B203086 |
| SHA1: | 352E4B98FAEBC35F5C8CFEAEBB7BCB36D7C7FBFC |
| SHA256: | AC03DB52BB68A013D3A8BF4DB703EC11976FA1D0AA557EB988E3F926A26656CF |
| SSDEEP: | 98304:2O7UY7BGRmoqWseW/sygVXIGdPdjhfXAooL2x5olv2Ex7SCIVKLp0If6DRj4dpq5:ZgAZQ5xoG2KU9bzkzl |
MALICIOUS
Drops the executable file immediately after the start
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
SUSPICIOUS
Reads the Internet Settings
- teracopy.exe (PID: 3212)
- updater.exe (PID: 3352)
- TeraCopy.exe (PID: 2740)
Reads security settings of Internet Explorer
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
- updater.exe (PID: 3352)
- TeraCopy.exe (PID: 2740)
Reads settings of System Certificates
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
- updater.exe (PID: 3352)
Checks Windows Trust Settings
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
- updater.exe (PID: 3352)
Reads the Windows owner or organization settings
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
Executable content was dropped or overwritten
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
Application launched itself
- teracopy.exe (PID: 3212)
- TeraCopy.exe (PID: 2740)
Adds/modifies Windows certificates
- teracopy.exe (PID: 1808)
Executes as Windows Service
- VSSVC.exe (PID: 1336)
INFO
Reads the computer name
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
- updater.exe (PID: 3352)
- TeraCopy.exe (PID: 2740)
- TeraCopy.exe (PID: 908)
Checks supported languages
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
- updater.exe (PID: 3352)
- TeraCopy.exe (PID: 908)
- TeraCopy.exe (PID: 2740)
Checks proxy server information
- teracopy.exe (PID: 3212)
- updater.exe (PID: 3352)
Reads the machine GUID from the registry
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
- updater.exe (PID: 3352)
Reads the software policy settings
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
- updater.exe (PID: 3352)
Reads Environment values
- teracopy.exe (PID: 3212)
- teracopy.exe (PID: 1808)
Create files in a temporary directory
- teracopy.exe (PID: 3212)
Creates files or folders in the user directory
- teracopy.exe (PID: 3212)
- TeraCopy.exe (PID: 2740)
- TeraCopy.exe (PID: 908)
Creates files in the program directory
- teracopy.exe (PID: 1808)
- updater.exe (PID: 3352)
Manual execution by a user
- TeraCopy.exe (PID: 2740)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:15 13:33:00+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.37 |
| CodeSize: | 2604032 |
| InitializedDataSize: | 1142272 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f0aa6 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.17.0.0 |
| ProductVersionNumber: | 3.17.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Code Sector |
| FileDescription: | TeraCopy Installer |
| FileVersion: | 3.17 |
| InternalName: | teracopy3.17 |
| LegalCopyright: | Copyright (C) 2023 Code Sector |
| OriginalFileName: | teracopy3.17.exe |
| ProductName: | TeraCopy |
| ProductVersion: | 3.17 |
Total processes
56
Monitored processes
6
Malicious processes
3
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 908 | "C:\Program Files\TeraCopy\teracopy.exe" | C:\Program Files\TeraCopy\TeraCopy.exe | TeraCopy.exe | ||||||||||||
User: admin Integrity Level: HIGH Description: TeraCopy Exit code: 0 Modules
| |||||||||||||||
| 1336 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1808 | "C:\Users\admin\AppData\Local\Temp\teracopy.exe" /i "C:\Users\admin\AppData\Roaming\Code Sector\TeraCopy 3.17\install\53E6B13\TeraCopy.msi" AI_EUIMSI=1 APPDIR="C:\Program Files\TeraCopy" SHORTCUTDIR="C:\ProgramData\Microsoft\Windows\Start Menu\Programs" SECONDSEQUENCE="1" CLIENTPROCESSID="3212" CHAINERUIPROCESSID="3212Chainer" ACTION="INSTALL" EXECUTEACTION="INSTALL" CLIENTUILEVEL="0" ADDLOCAL="Required,AI32BitFiles,LangFiles,bk3,blake2sp,blake3,exf,hash,md2,xxh64,xxh32,sha3,sha3224,sha3256,sha3384,sha3512,md4,md5,sfv,sha1,sha256,xxh,sha384,sha,xxh3,sha256sum,FileTypeAssociations" ALLUSERS="1" PRIMARYFOLDER="APPDIR" ROOTDRIVE="C:\" AI_DETECTED_ADMIN_USER="1" AI_SETUPEXEPATH="C:\Users\admin\AppData\Local\Temp\teracopy.exe" SETUPEXEDIR="C:\Users\admin\AppData\Local\Temp\" EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1713170031 " AI_SETUPEXEPATH_ORIGINAL="C:\Users\admin\AppData\Local\Temp\teracopy.exe" TARGETDIR="C:\" AI_INSTALL="1" | C:\Users\admin\AppData\Local\Temp\teracopy.exe | teracopy.exe | ||||||||||||
User: admin Company: Code Sector Integrity Level: HIGH Description: TeraCopy Installer Exit code: 0 Version: 3.17 Modules
| |||||||||||||||
| 2740 | "C:\Program Files\TeraCopy\TeraCopy.exe" | C:\Program Files\TeraCopy\TeraCopy.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Description: TeraCopy Exit code: 0 Modules
| |||||||||||||||
| 3212 | "C:\Users\admin\AppData\Local\Temp\teracopy.exe" | C:\Users\admin\AppData\Local\Temp\teracopy.exe | explorer.exe | ||||||||||||
User: admin Company: Code Sector Integrity Level: MEDIUM Description: TeraCopy Installer Exit code: 0 Version: 3.17 Modules
| |||||||||||||||
| 3352 | "C:\Program Files\TeraCopy\updater.exe" /silent | C:\Program Files\TeraCopy\updater.exe | TeraCopy.exe | ||||||||||||
User: admin Company: Code Sector Integrity Level: MEDIUM Description: updater 3.17 Exit code: 3758096401 Version: 3.17 Modules
| |||||||||||||||
Total events
17 017
Read events
16 737
Write events
253
Delete events
27
Modification events
| (PID) Process: | (3212) teracopy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (3212) teracopy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyServer |
Value: | |||
| (PID) Process: | (3212) teracopy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | ProxyOverride |
Value: | |||
| (PID) Process: | (3212) teracopy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoConfigURL |
Value: | |||
| (PID) Process: | (3212) teracopy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | delete value | Name: | AutoDetect |
Value: | |||
| (PID) Process: | (3212) teracopy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 460000005C010000090000000000000000000000000000000400000000000000C0E333BBEAB1D3010000000000000000000000000100000002000000C0A8016B000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (3212) teracopy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3212) teracopy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3212) teracopy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3212) teracopy.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
31
Suspicious files
53
Text files
90
Unknown types
19
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3212 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3212 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 3212 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\24BD96D5497F70B3F510A6B53CD43F3E_3A89246FB90C5EE6620004F1AE0EB0EA | binary | |
MD5:— | SHA256:— | |||
| 3212 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CAF4703619713E3F18D8A9D5D88D6288_45E3C223BCF135987E4038FB6B0DBA13 | binary | |
MD5:— | SHA256:— | |||
| 3212 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CAF4703619713E3F18D8A9D5D88D6288_45E3C223BCF135987E4038FB6B0DBA13 | binary | |
MD5:— | SHA256:— | |||
| 3212 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80A16DAF421EE6AB95634E54F4251FD8_D6EB3494A2CDAB77E5CFCB1D30C59BCB | binary | |
MD5:— | SHA256:— | |||
| 3212 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80A16DAF421EE6AB95634E54F4251FD8_D6EB3494A2CDAB77E5CFCB1D30C59BCB | binary | |
MD5:— | SHA256:— | |||
| 3212 | teracopy.exe | C:\Users\admin\AppData\Local\Temp\upd313C.tmp.part | text | |
MD5:— | SHA256:— | |||
| 3212 | teracopy.exe | C:\Users\admin\AppData\Local\Temp\upd313C.tmp | text | |
MD5:— | SHA256:— | |||
| 3212 | teracopy.exe | C:\Users\admin\AppData\Roaming\Code Sector\TeraCopy 3.17\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
9
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3212 | teracopy.exe | GET | 304 | 23.218.239.13:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?0d45a3ebc56b6f21 | unknown | — | — | unknown |
3212 | teracopy.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gsr1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBS3V7W2nAf4FiMTjpDJKg6%2BMgGqMQQUYHtmGkUNl8qJUC99BM00qP%2F8%2FUsCEHe9DWzbNvka6iEPxPBY0w0%3D | unknown | — | — | unknown |
1080 | svchost.exe | GET | — | 23.218.239.13:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?3e412f7b4eff0943 | unknown | — | — | unknown |
3212 | teracopy.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIAjrICMzZli2TN25s%3D | unknown | — | — | unknown |
1080 | svchost.exe | GET | 200 | 23.218.239.13:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?c503292d7802e201 | unknown | — | — | unknown |
3212 | teracopy.exe | GET | 200 | 142.250.184.227:80 | http://ocsp.pki.goog/s/gts1d4/QbUlIyx8izs/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSMBFDqU0NJQdZdEGU3bkhj0FoRrQQUJeIYDrJXkZQq5dRdhpCD3lOzuJICEC7zWCcs4XNyEswk2oG62xw%3D | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | unknown |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
3212 | teracopy.exe | 216.239.34.21:443 | codesector.com | GOOGLE | US | whitelisted |
3212 | teracopy.exe | 23.218.239.13:80 | ctldl.windowsupdate.com | Akamai International B.V. | CA | unknown |
3212 | teracopy.exe | 142.250.184.227:80 | ocsp.pki.goog | GOOGLE | US | whitelisted |
3352 | updater.exe | 216.239.34.21:443 | codesector.com | GOOGLE | US | whitelisted |
1080 | svchost.exe | 23.218.239.13:80 | ctldl.windowsupdate.com | Akamai International B.V. | CA | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
codesector.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.pki.goog |
| whitelisted |
Threats
Process | Message |
|---|---|
updater.exe | Logger::SetLogFile( C:\ProgramData\Code Sector\TeraCopy\updates\updater.log ) while OLD path is: |