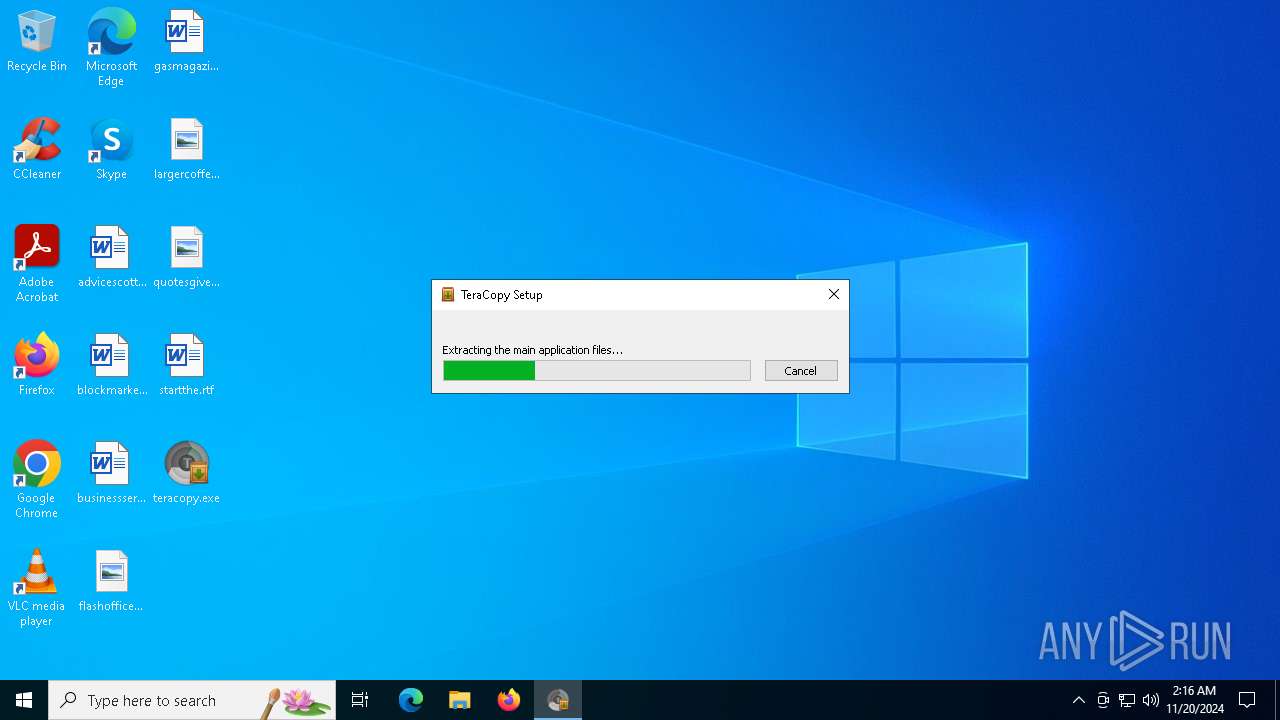
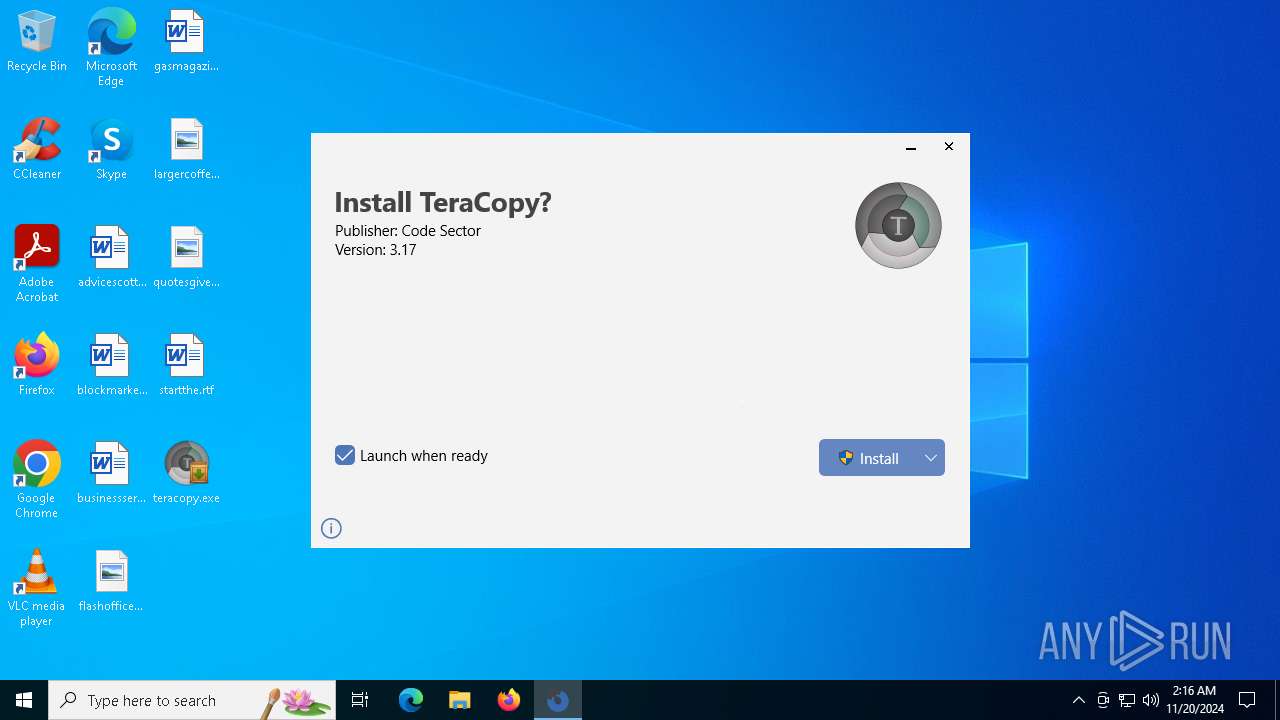
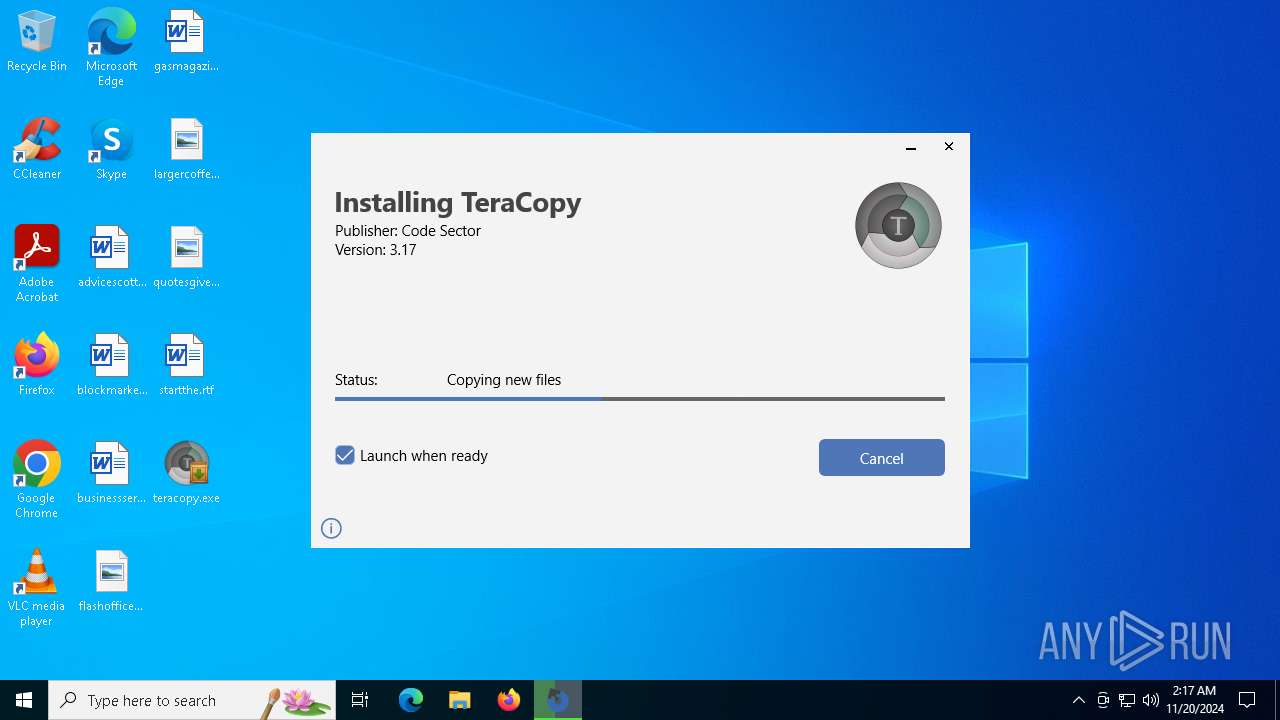
| File name: | teracopy.exe |
| Full analysis: | https://app.any.run/tasks/19eaec95-647d-4f35-a109-98ba35fb9e5c |
| Verdict: | Malicious activity |
| Analysis date: | November 20, 2024, 02:16:12 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 5 sections |
| MD5: | D704E453E065A23ED414927D9B203086 |
| SHA1: | 352E4B98FAEBC35F5C8CFEAEBB7BCB36D7C7FBFC |
| SHA256: | AC03DB52BB68A013D3A8BF4DB703EC11976FA1D0AA557EB988E3F926A26656CF |
| SSDEEP: | 98304:2O7UY7BGRmoqWseW/sygVXIGdPdjhfXAooL2x5olv2Ex7SCIVKLp0If6DRj4dpq5:ZgAZQ5xoG2KU9bzkzl |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads security settings of Internet Explorer
- teracopy.exe (PID: 3208)
Checks Windows Trust Settings
- teracopy.exe (PID: 3208)
Application launched itself
- teracopy.exe (PID: 3208)
Process drops legitimate windows executable
- teracopy.exe (PID: 3640)
- teracopy.exe (PID: 3208)
Executable content was dropped or overwritten
- teracopy.exe (PID: 3640)
- teracopy.exe (PID: 3208)
Executes as Windows Service
- VSSVC.exe (PID: 3632)
- TeraCopyService.exe (PID: 6372)
INFO
Checks supported languages
- teracopy.exe (PID: 3208)
Creates files or folders in the user directory
- teracopy.exe (PID: 3208)
Checks proxy server information
- teracopy.exe (PID: 3208)
Reads the computer name
- teracopy.exe (PID: 3208)
Reads the software policy settings
- teracopy.exe (PID: 3208)
Reads Environment values
- teracopy.exe (PID: 3208)
Reads the machine GUID from the registry
- teracopy.exe (PID: 3208)
Manages system restore points
- SrTasks.exe (PID: 2860)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1488)
Application launched itself
- msiexec.exe (PID: 1488)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable (generic) (52.9) |
|---|---|---|
| .exe | | | Generic Win/DOS Executable (23.5) |
| .exe | | | DOS Executable Generic (23.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2023:11:15 13:33:00+00:00 |
| ImageFileCharacteristics: | Executable, Large address aware, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.37 |
| CodeSize: | 2604032 |
| InitializedDataSize: | 1142272 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x1f0aa6 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 3.17.0.0 |
| ProductVersionNumber: | 3.17.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Debug |
| FileOS: | Win32 |
| ObjectFileType: | Dynamic link library |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Code Sector |
| FileDescription: | TeraCopy Installer |
| FileVersion: | 3.17 |
| InternalName: | teracopy3.17 |
| LegalCopyright: | Copyright (C) 2023 Code Sector |
| OriginalFileName: | teracopy3.17.exe |
| ProductName: | TeraCopy |
| ProductVersion: | 3.17 |
Total processes
132
Monitored processes
16
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1488 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2860 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 3208 | "C:\Users\admin\Desktop\teracopy.exe" | C:\Users\admin\Desktop\teracopy.exe | explorer.exe | ||||||||||||
User: admin Company: Code Sector Integrity Level: MEDIUM Description: TeraCopy Installer Exit code: 3221225477 Version: 3.17 Modules
| |||||||||||||||
| 3560 | C:\Windows\syswow64\MsiExec.exe -Embedding ACA26E6CDFC0F6DFF793A9B8EB22E754 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3632 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3640 | "C:\Users\admin\Desktop\teracopy.exe" /i "C:\Users\admin\AppData\Roaming\Code Sector\TeraCopy 3.17\install\53E6B13\TeraCopy.x64.msi" AI_EUIMSI=1 APPDIR="C:\Program Files\TeraCopy" SHORTCUTDIR="C:\ProgramData\Microsoft\Windows\Start Menu\Programs" SECONDSEQUENCE="1" CLIENTPROCESSID="3208" CHAINERUIPROCESSID="3208Chainer" ACTION="INSTALL" EXECUTEACTION="INSTALL" CLIENTUILEVEL="0" ADDLOCAL="Required,AI64BitFiles,AI32BitFiles,LangFiles,bk3,blake2sp,blake3,exf,hash,md2,xxh64,xxh32,sha3,sha3224,sha3256,sha3384,sha3512,md4,md5,sfv,sha1,sha256,xxh,sha384,sha,xxh3,sha256sum,FileTypeAssociations" ALLUSERS="1" PRIMARYFOLDER="APPDIR" ROOTDRIVE="C:\" AI_DETECTED_ADMIN_USER="1" AI_SETUPEXEPATH="C:\Users\admin\Desktop\teracopy.exe" SETUPEXEDIR="C:\Users\admin\Desktop\" EXE_CMD_LINE="/exenoupdates /forcecleanup /wintime 1732068022 " AI_SETUPEXEPATH_ORIGINAL="C:\Users\admin\Desktop\teracopy.exe" TARGETDIR="C:\" AI_INSTALL="1" | C:\Users\admin\Desktop\teracopy.exe | teracopy.exe | ||||||||||||
User: admin Company: Code Sector Integrity Level: HIGH Description: TeraCopy Installer Exit code: 0 Version: 3.17 Modules
| |||||||||||||||
| 4992 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 6176 | C:\Windows\syswow64\MsiExec.exe -Embedding D310A459D65D2E7EB87186D6B46FADF2 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
| 6276 | "C:\Windows\System32\MsiExec.exe" /Y "C:\Program Files\TeraCopy\TeraCopy.dll" | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) | |||||||||||||||
| 6296 | "C:\Windows\syswow64\MsiExec.exe" /Y "C:\Program Files\TeraCopy\32-bit\Context.dll" | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) | |||||||||||||||
Total events
9 876
Read events
9 838
Write events
27
Delete events
11
Modification events
| (PID) Process: | (3640) teracopy.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates |
| Operation: | delete value | Name: | D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
Value: | |||
| (PID) Process: | (3640) teracopy.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
| Operation: | write | Name: | Blob |
Value: 040000000100000010000000497904B0EB8719AC47B0BC11519B74D0140000000100000014000000A0110A233E96F107ECE2AF29EF82A57FD030A4B4620000000100000020000000D7A7A0FB5D7E2731D771E9484EBCDEF71D5F0C3E0A2948782BC83EE0EA699EF4090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B060105050703080F00000001000000140000003E8E6487F8FD27D322A269A71EDAAC5D57811286030000000100000014000000D1EB23A46D17D68FD92564C2F1F1601764D8E3491900000001000000100000002AA1C05E2AE606F198C2C5E937C97AA253000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C00B000000010000001C0000005300650063007400690067006F0020002800410041004100290000001D00000001000000100000002E0D6875874A44C820912E85E964CFDB200000000100000036040000308204323082031AA003020102020101300D06092A864886F70D0101050500307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C18414141204365727469666963617465205365727669636573301E170D3034303130313030303030305A170D3238313233313233353935395A307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C1841414120436572746966696361746520536572766963657330820122300D06092A864886F70D01010105000382010F003082010A0282010100BE409DF46EE1EA76871C4D45448EBE46C883069DC12AFE181F8EE402FAF3AB5D508A16310B9A06D0C57022CD492D5463CCB66E68460B53EACB4C24C0BC724EEAF115AEF4549A120AC37AB23360E2DA8955F32258F3DEDCCFEF8386A28C944F9F68F29890468427C776BFE3CC352C8B5E07646582C048B0A891F9619F762050A891C766B5EB78620356F08A1A13EA31A31EA099FD38F6F62732586F07F56BB8FB142BAFB7AACCD6635F738CDA0599A838A8CB17783651ACE99EF4783A8DCF0FD942E2980CAB2F9F0E01DEEF9F9949F12DDFAC744D1B98B547C5E529D1F99018C7629CBE83C7267B3E8A25C7C0DD9DE6356810209D8FD8DED2C3849C0D5EE82FC90203010001A381C03081BD301D0603551D0E04160414A0110A233E96F107ECE2AF29EF82A57FD030A4B4300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF307B0603551D1F047430723038A036A0348632687474703A2F2F63726C2E636F6D6F646F63612E636F6D2F414141436572746966696361746553657276696365732E63726C3036A034A0328630687474703A2F2F63726C2E636F6D6F646F2E6E65742F414141436572746966696361746553657276696365732E63726C300D06092A864886F70D010105050003820101000856FC02F09BE8FFA4FAD67BC64480CE4FC4C5F60058CCA6B6BC1449680476E8E6EE5DEC020F60D68D50184F264E01E3E6B0A5EEBFBC745441BFFDFC12B8C74F5AF48960057F60B7054AF3F6F1C2BFC4B97486B62D7D6BCCD2F346DD2FC6E06AC3C334032C7D96DD5AC20EA70A99C1058BAB0C2FF35C3ACF6C37550987DE53406C58EFFCB6AB656E04F61BDC3CE05A15C69ED9F15948302165036CECE92173EC9B03A1E037ADA015188FFABA02CEA72CA910132CD4E50826AB229760F8905E74D4A29A53BDF2A968E0A26EC2D76CB1A30F9EBFEB68E756F2AEF2E32B383A0981B56B85D7BE2DED3F1AB7B263E2F5622C82D46A004150F139839F95E93696986E | |||
| (PID) Process: | (3640) teracopy.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\SystemCertificates\AuthRoot\Certificates\D1EB23A46D17D68FD92564C2F1F1601764D8E349 |
| Operation: | write | Name: | Blob |
Value: 5C0000000100000004000000000800001D00000001000000100000002E0D6875874A44C820912E85E964CFDB0B000000010000001C0000005300650063007400690067006F00200028004100410041002900000053000000010000004300000030413022060C2B06010401B231010201050130123010060A2B0601040182373C0101030200C0301B060567810C010330123010060A2B0601040182373C0101030200C01900000001000000100000002AA1C05E2AE606F198C2C5E937C97AA2030000000100000014000000D1EB23A46D17D68FD92564C2F1F1601764D8E3490F00000001000000140000003E8E6487F8FD27D322A269A71EDAAC5D57811286090000000100000054000000305206082B0601050507030206082B06010505070303060A2B0601040182370A030406082B0601050507030406082B0601050507030606082B0601050507030706082B0601050507030106082B06010505070308620000000100000020000000D7A7A0FB5D7E2731D771E9484EBCDEF71D5F0C3E0A2948782BC83EE0EA699EF4140000000100000014000000A0110A233E96F107ECE2AF29EF82A57FD030A4B4040000000100000010000000497904B0EB8719AC47B0BC11519B74D0200000000100000036040000308204323082031AA003020102020101300D06092A864886F70D0101050500307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C18414141204365727469666963617465205365727669636573301E170D3034303130313030303030305A170D3238313233313233353935395A307B310B3009060355040613024742311B301906035504080C1247726561746572204D616E636865737465723110300E06035504070C0753616C666F7264311A3018060355040A0C11436F6D6F646F204341204C696D697465643121301F06035504030C1841414120436572746966696361746520536572766963657330820122300D06092A864886F70D01010105000382010F003082010A0282010100BE409DF46EE1EA76871C4D45448EBE46C883069DC12AFE181F8EE402FAF3AB5D508A16310B9A06D0C57022CD492D5463CCB66E68460B53EACB4C24C0BC724EEAF115AEF4549A120AC37AB23360E2DA8955F32258F3DEDCCFEF8386A28C944F9F68F29890468427C776BFE3CC352C8B5E07646582C048B0A891F9619F762050A891C766B5EB78620356F08A1A13EA31A31EA099FD38F6F62732586F07F56BB8FB142BAFB7AACCD6635F738CDA0599A838A8CB17783651ACE99EF4783A8DCF0FD942E2980CAB2F9F0E01DEEF9F9949F12DDFAC744D1B98B547C5E529D1F99018C7629CBE83C7267B3E8A25C7C0DD9DE6356810209D8FD8DED2C3849C0D5EE82FC90203010001A381C03081BD301D0603551D0E04160414A0110A233E96F107ECE2AF29EF82A57FD030A4B4300E0603551D0F0101FF040403020106300F0603551D130101FF040530030101FF307B0603551D1F047430723038A036A0348632687474703A2F2F63726C2E636F6D6F646F63612E636F6D2F414141436572746966696361746553657276696365732E63726C3036A034A0328630687474703A2F2F63726C2E636F6D6F646F2E6E65742F414141436572746966696361746553657276696365732E63726C300D06092A864886F70D010105050003820101000856FC02F09BE8FFA4FAD67BC64480CE4FC4C5F60058CCA6B6BC1449680476E8E6EE5DEC020F60D68D50184F264E01E3E6B0A5EEBFBC745441BFFDFC12B8C74F5AF48960057F60B7054AF3F6F1C2BFC4B97486B62D7D6BCCD2F346DD2FC6E06AC3C334032C7D96DD5AC20EA70A99C1058BAB0C2FF35C3ACF6C37550987DE53406C58EFFCB6AB656E04F61BDC3CE05A15C69ED9F15948302165036CECE92173EC9B03A1E037ADA015188FFABA02CEA72CA910132CD4E50826AB229760F8905E74D4A29A53BDF2A968E0A26EC2D76CB1A30F9EBFEB68E756F2AEF2E32B383A0981B56B85D7BE2DED3F1AB7B263E2F5622C82D46A004150F139839F95E93696986E | |||
| (PID) Process: | (1488) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 480000000000000015315C3EF23ADB01D0050000AC140000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1488) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 480000000000000015315C3EF23ADB01D0050000AC140000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1488) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 48000000000000007A32B93EF23ADB01D0050000AC140000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1488) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 48000000000000007A32B93EF23ADB01D0050000AC140000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1488) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000F696BB3EF23ADB01D0050000AC140000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1488) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 48000000000000006CFABD3EF23ADB01D0050000AC140000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (1488) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
Executable files
57
Suspicious files
92
Text files
154
Unknown types
42
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3208 | teracopy.exe | C:\Users\admin\AppData\Roaming\Code Sector\TeraCopy 3.17\install\holder0.aiph | — | |
MD5:— | SHA256:— | |||
| 3208 | teracopy.exe | C:\Users\admin\AppData\Roaming\Code Sector\TeraCopy 3.17\install\53E6B13\TeraCopy.msi | — | |
MD5:— | SHA256:— | |||
| 3208 | teracopy.exe | C:\Users\admin\AppData\Roaming\Code Sector\TeraCopy 3.17\install\53E6B13\TeraCopy.x64.msi | — | |
MD5:— | SHA256:— | |||
| 3208 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\B2FAF7692FD9FFBD64EDE317E42334BA_93702E680A5530C052C8D2BA33A2225F | binary | |
MD5:3F791DDE430559CD55435F06CEB37A6A | SHA256:758EE44AF645A3DDE14F97E430E8A8C8F06B2BDCA2C31649BEF14ED6FB722322 | |||
| 3208 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B2FAF7692FD9FFBD64EDE317E42334BA_93702E680A5530C052C8D2BA33A2225F | der | |
MD5:362F9B80FDC2B3BB2CF7EE350A3124E4 | SHA256:86812DA6E5EC489C2F6FD040FF59888D1AC83B63604004F79989EE8F475046B1 | |||
| 3208 | teracopy.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_3208\buttonimgsdark | image | |
MD5:D2CEE1442309FE99E978F0316395D970 | SHA256:75FEA1443A0AF73756270C1840ED88B22301530AE5B9418A6BD1F45B62F8F1CD | |||
| 3208 | teracopy.exe | C:\Users\admin\AppData\Local\Temp\MSIBEA1.tmp | executable | |
MD5:5A1F2196056C0A06B79A77AE981C7761 | SHA256:52F41817669AF7AC55B1516894EE705245C3148F2997FA0E6617E9CC6353E41E | |||
| 3208 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\18E6B4A57A6BC7EC9B861CDF2D6D0D02_C3B142D2C5374581DC2FDFFDEDBDEDDB | der | |
MD5:D407D5257D0D53A96538F1A7E9B169BC | SHA256:5B1C8C416405DDC51D5E35E23978B9A1CA0BEA6EA6B26EF7B38771FF491ADC22 | |||
| 3208 | teracopy.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\AEACCDA8653DD8D7B2EA32F21D15D44F_29FEFA71A8995944ED77F14BD3246071 | binary | |
MD5:AA6770B0315B6952822C4A3EE39A8C0B | SHA256:C9357A7AA033822BAA34FE1D621EF8B9FAE6859522F3D1B48F8C0291AEFD0904 | |||
| 3208 | teracopy.exe | C:\Users\admin\AppData\Local\Temp\AI_EXTUI_BIN_3208\aboutbtndark | image | |
MD5:B51B54B77E9CBFDB1063F7487C1C07EC | SHA256:9D7243C688264329A8CB9E22DA00B651E0A9407741D722E03DD67CC8B3EE1335 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
9
TCP/UDP connections
22
DNS requests
11
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4932 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
4932 | svchost.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
3208 | teracopy.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEEj8k7RgVZSNNqfJionWlBY%3D | unknown | — | — | whitelisted |
3208 | teracopy.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSdE3gf41WAic8Uh9lF92%2BIJqh5qwQUMuuSmv81lkgvKEBCcCA2kVwXheYCEGIdbQxSAZ47kHkVIIkhHAo%3D | unknown | — | — | whitelisted |
3208 | teracopy.exe | GET | 200 | 172.64.149.23:80 | http://ocsp.sectigo.com/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBQVD%2BnGf79Hpedv3mhy6uKMVZkPCQQUDyrLIIcouOxvSK4rVKYpqhekzQwCEQDG1n8v3OsBZV0hg%2FBJyvbo | unknown | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | POST | 204 | 104.126.37.128:443 | https://www.bing.com/threshold/xls.aspx | unknown | — | — | whitelisted |
— | — | GET | 200 | 216.239.34.21:443 | https://codesector.com/updates/teracopy.txt | unknown | text | 822 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4932 | svchost.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
4712 | MoUsoCoreWorker.exe | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 20.73.194.208:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4932 | svchost.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 23.216.77.6:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
3208 | teracopy.exe | 104.18.38.233:80 | ocsp.comodoca.com | CLOUDFLARENET | — | whitelisted |
4932 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4712 | MoUsoCoreWorker.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
ocsp.comodoca.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ocsp.sectigo.com |
| whitelisted |
www.bing.com |
| whitelisted |
codesector.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |