| File name: | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe |
| Full analysis: | https://app.any.run/tasks/7723e233-5758-416e-ae7f-b0d40374b6c9 |
| Verdict: | Malicious activity |
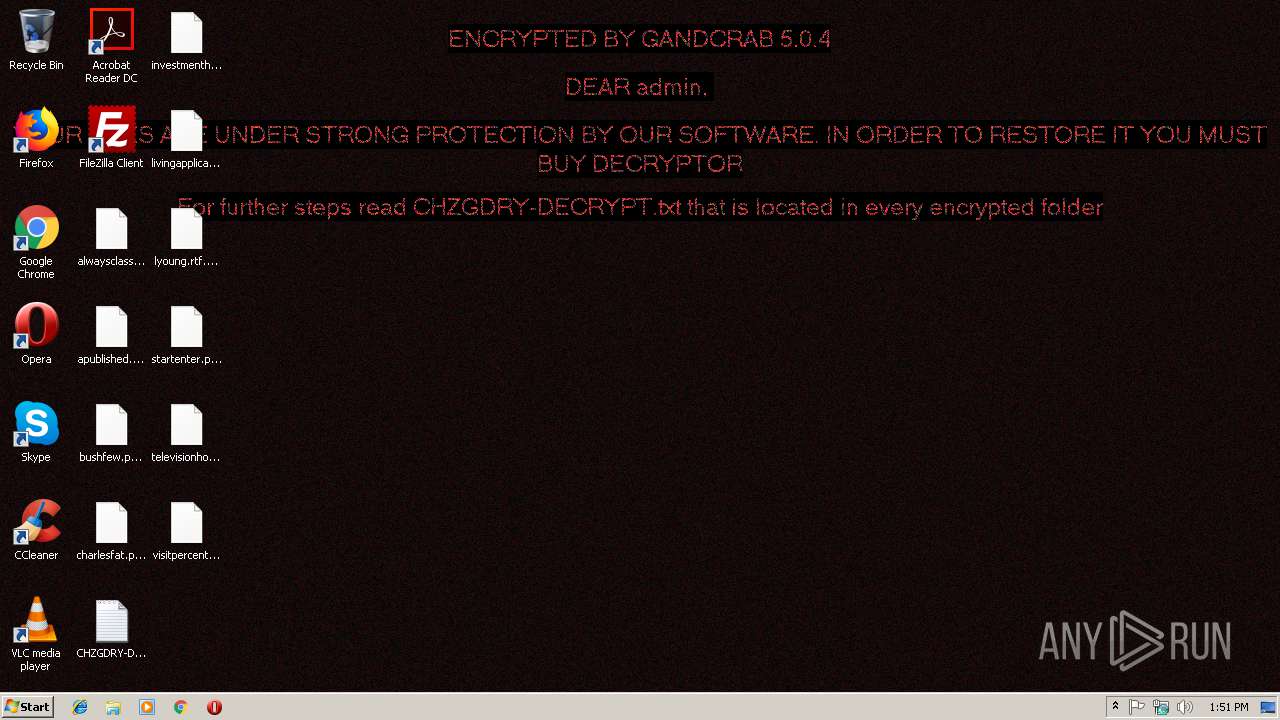
| Threats: | GandCrab is probably one of the most famous Ransomware. A Ransomware is a malware that asks the victim to pay money in order to restore access to encrypted files. If the user does not cooperate the files are forever lost. |
| Analysis date: | January 17, 2019, 13:51:21 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | ACD62C0620F91F1C9BA8DF9871E1D588 |
| SHA1: | 9079BD76ABB862B8851CDD36A56763D5AC3E4A75 |
| SHA256: | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC |
| SSDEEP: | 3072:3T0i4GjnC8TWewrm4yWgCM8BbDer3QbPWIiXrqfrhKFIc47eWN3K+Hq3j+ySN:Qi4G7VJ4B3LnecbPEbqTPYjiySN |
MALICIOUS
GandCrab keys found
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Writes file to Word startup folder
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Actions looks like stealing of personal data
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Dropped file may contain instructions of ransomware
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Deletes shadow copies
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Renames files like Ransomware
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Connects to CnC server
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Changes settings of System certificates
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
SUSPICIOUS
Creates files in the program directory
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Reads the cookies of Mozilla Firefox
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Creates files like Ransomware instruction
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Changes tracing settings of the file or console
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Creates files in the user directory
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Adds / modifies Windows certificates
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
INFO
Dropped object may contain TOR URL's
- ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe (PID: 2972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable MS Visual C++ (generic) (41) |
|---|---|---|
| .exe | | | Win64 Executable (generic) (36.3) |
| .dll | | | Win32 Dynamic Link Library (generic) (8.6) |
| .exe | | | Win32 Executable (generic) (5.9) |
| .exe | | | Clipper DOS Executable (2.6) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:06:02 11:55:49+02:00 |
| PEType: | PE32 |
| LinkerVersion: | 10 |
| CodeSize: | 207360 |
| InitializedDataSize: | 207360 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x206c8 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 7.0.0.0 |
| ProductVersionNumber: | 3.0.0.0 |
| FileFlagsMask: | 0x004f |
| FileFlags: | (none) |
| FileOS: | Unknown (0x40534) |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | Unknown (457A) |
| CharacterSet: | Unknown (A56B) |
| FileVersion: | 1.10.2.26 |
| InternalName: | gataja.exe |
| LegalCopyright: | Copyright (C) 2018, caradasa |
| ProductVersion: | 1.10.2.26 |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 02-Jun-2018 09:55:49 |
| Detected languages: |
|
| FileVersion: | 1.10.2.26 |
| InternalName: | gataja.exe |
| LegalCopyright: | Copyright (C) 2018, caradasa |
| ProductVersion: | 1.10.2.26 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000E8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 02-Jun-2018 09:55:49 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x000328E7 | 0x00032A00 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 6.89007 |
.data | 0x00034000 | 0x00023CEC | 0x00007600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0.483874 |
.mysec | 0x00058000 | 0x0000100A | 0x00000400 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
.rsrc | 0x0005A000 | 0x0000CF48 | 0x0000D000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 6.62571 |
.reloc | 0x00067000 | 0x00001652 | 0x00001800 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 5.9407 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 3.35745 | 480 | UNKNOWN | Croatian - Croatia | RT_VERSION |
109 | 6.55581 | 47992 | UNKNOWN | Croatian - Croatia | RT_BITMAP |
234 | 1.7815 | 20 | UNKNOWN | Croatian - Croatia | RT_GROUP_ICON |
Imports
GDI32.dll |
KERNEL32.dll |
SHELL32.dll |
USER32.dll |
Exports
Title | Ordinal | Address |
|---|---|---|
_MyFunc1@4 | 1 | 0x0001DDA4 |
Total processes
34
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2972 | "C:\Users\admin\AppData\Local\Temp\ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe" | C:\Users\admin\AppData\Local\Temp\ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 3672 | "C:\Windows\system32\wbem\wmic.exe" shadowcopy delete | C:\Windows\system32\wbem\wmic.exe | — | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: WMI Commandline Utility Exit code: 2147749908 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
126
Read events
89
Write events
35
Delete events
2
Modification events
| (PID) Process: | (2972) ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\ex_data\data |
| Operation: | write | Name: | ext |
Value: 2E00630068007A0067006400720079000000 | |||
| (PID) Process: | (2972) ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\keys_data\data |
| Operation: | write | Name: | public |
Value: 0602000000A400005253413100080000010001002D24DE988B4F912E3E712D1E7E50EC449BEF2D2646DCA53233506E76525F7F5E1C390C13924CAA492E897D2261A75A0D442F15EFAB08FC7DD3772BEB8DA0347DB4F6265F74DBF36B1FFCE1E0D021FA6C5BF969527E8872CA5571EA9D3780C1CE622121DA2EBDF288674C93CB8D3B79EE7023E76B44519FE89E52E07AE6929E07FE21CF6DF636F0B4CFF68BB096E2A4D2228EF8A628885D8E2DB948DF9946C003511E2044CB99B3BF7DFD2DA6496CFDD6B8F4AC25793079E347106589B9A7330CED192A84BC8308B59A59BA20681F96BA08EBD9DFD9DF071C234A27CB4D1604AC6B391640AD08CC3ECEFA6F92055011477CF7949FA79BD52D0546A8BC4B682BCB | |||
| (PID) Process: | (2972) ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\keys_data\data |
| Operation: | write | Name: | private |
Value: 94040000A0CA4E4BAF0D18B83338647558D708BABC8F014DE2E5748DA1D087DA35B80EC1F497CCD045D6351FBB833DBC3396C30B149544AB99EE0F9716DDF9C855E365B4337ED45A25BF29A3C1C73EDFFF5815EADB1BFA785FBCEA5971ADD1E182575157C1F6D86A4AB852FEBBF17452765924030DC7730860581F24C58DE7AA0B7AB2113116D68CCDA25A5839F2B7870870A084FF7BC90B9D4A37F12956864B7BA277FDF89258EE046F12F6D2B2718DF0E07FFBC2E3E10460D3FA984E960545009D7EB789D6AC54E3A357FA73519776786B07C96185411AEA4799E9657453AA6F946222DE7999DCAB49B3E889979B808AAA12528427A0B4899C6A1FFDD8D446DB2B9D97FD82B804622C1397A0DA99ADAAE03E74E2A81C9EF9588F1FCC302979441F60100C762BC4C6D6E5DE3EB2EC7D83E238FD93B979B9D19E75AF0D491408D9D15E6739CF4ED7891E027C435CD13C1B6702FC12B25EAF007123F3E5EEF92135EF1BB700FE92DB15303C0B5144497227EE01E51AE4AF01B07ED941D791A6B14272B71F24511D52EC68FF3ECE1BDC558D10D4A48A9864404F07218FA003F44A028D6A904397E412E430BB0F1B4417F0BB86B15598CCC8DA4C66FC5A445B3D785802FF35D2EFE0C09B733E1F2DC6ED3870FAC71A356525834498E875A14EBBC961E6CEA00CD79BAA2AF185DB47A62D6A10F3A2213454ABBF74379E82F958C7FC89C719748445AC461BE31F2540D2AE6D22144300DC3D581CE2E27B2D856C85ABC7B52DE319A050B1956C9F8EA93C1AD9CC23322DECCD766D67AF5D0FB2A82FAB7FCA7FCD27B334108EA2FD5FE2D349054DF95A4526059F0A72669DA01E54E9BFBA4FDFC58EAC3AB268A0A725E46FF9A213C224647C0B83156EB9ED6E074788373BE7ADD41853259B63399E3C86FA10E4F2A2C980D773F4CA3BEA6A3248F2E3D078807AEECCF8CCE4C0507B68E9D391EE359AD4EAFD0DDC9AB4B018987D7A37EA1A2EC123B23A40438E153DC81447FDBD006FFF6BF4547AB6BE586AFDE4A015B857A8F66C2DA25239515186BCAD82EB2ABE70A0BAFCE0883814F42F96105156983E17A0955A74C34E63CE2C4F62FE8A94755D948BE93E9A4AE9218FE8BEE3402A3A5CA4C43152FDEA3E7D5839D430A0BC191EE48028C889C1E000677F15F7412558484DA15E54F7B6138A4321E3187ACDACE7458211C677EA4EC4DBDA126799EE744090D9947209F13FC177B8C5864AEBF3EAA18596609CF5096C58CE1A772C5AA0AB9491EB1F94F49470532DD0F1FB20306D4F2F8C39E0229CDB9253259657B79FEE2AABE0A6A737E07557B429F314F27E041419106AD0293BE121354D5F01E269942DC4536688E202822FBC2B1C72268AD5929FE2797F0BEF3219497CD088001EB0EE4AECB4C7DC883E1F40363AB2C74A8747B46B595FA06EC5523360A6C7634CD243AAA926ABB3F7CC8319B0ECA1B4B677827260957A87053BF2D836E1C211003D495CC6FC5C9C649BAE2C102F0629BA23FEF22A27D8E259B3F2A9F5F0CAEA40F08336FF11FB41F13AEC1482EF0A79BE86A05874B345770C75EFDC8CF163F8EA2531CE9366E4272A05A1690E62CCD09564A1CE0BCC5D02070AA124971D065A54467E4C64C27082A045CC1E6076F88ECFDD3CEA7C1F17071C49AB89103EDCA173D7AD68333A887B8147F6CC338E3B4494B1711678A4961B4152404AF9456F04B9A73CC200460FD488F4963D74FFE883B269106A9581D77765E663FC3A14F4ACDEF41A2ED284DAC902B228D36A03FA460D19AAB51AED3A09F3F5A06F61DAFEDB404FBD5D337C29F11B6D59444A9E3A661A140369F9C145150A29BA2EB94AA699C35FC2CC22A295D4E60D7FB80399E51E31EFD4C7093C9B9A68B8CAC725F8F0ACE1EA88481F55F92751BF5C6092978C094EF79760026569FF9397512DA392FD68D35275D6F62C0D0968FFB11433FA9D8098B7044438F356DE1D106F9E26F658187E3E170342D81B8027BF61C9675321332FA55A27B4D9240B37AACBE4A013E058742EF39EB9BA1732B8D098804496677B86BA4C421919B7A08833C2A8F1144AF1433D7058F4340E2DF1CB2149D96749F475EC6E854E527ED0A62930E35EAF006B0094AA773F00A2F67C462DE65C6F28C871D6DBA8D89ED9167C0B8BA3AE0237C5F011E46A0FBC52DBF39DB99AC30DCCA324F4AE2C65E689E92B3D6E089691F59B5767346C056E080041F5ED7980FCCA47F9D5D2D126CD2C52D7415EDAF71C8BE591A1A4056EC8E1095C874947C5C297186713B9306506C3307EFFB775C03C33AF9E0B123F0588F8B83B93F16A7E8CD45C0CE384C329DFDE83B3263817D51FA96C8A405BB6EB0F73B65B3463700BD6B8D4DAE11B9A5F26754A | |||
| (PID) Process: | (2972) ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2972) ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2972) ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableFileTracing |
Value: 0 | |||
| (PID) Process: | (2972) ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | EnableConsoleTracing |
Value: 0 | |||
| (PID) Process: | (2972) ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | FileTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2972) ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | ConsoleTracingMask |
Value: 4294901760 | |||
| (PID) Process: | (2972) ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Tracing\RASAPI32 |
| Operation: | write | Name: | MaxFileSize |
Value: 1048576 | |||
Executable files
0
Suspicious files
276
Text files
208
Unknown types
4
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp | — | |
MD5:— | SHA256:— | |||
| 2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobData | — | |
MD5:— | SHA256:— | |||
| 2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\JSCache\GlobSettings | — | |
MD5:— | SHA256:— | |||
| 2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\addressbook.acrodata | — | |
MD5:— | SHA256:— | |||
| 2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\0FDED5CEB68C302B1CDB2BDDD9D0000E76539CB0.crl | — | |
MD5:— | SHA256:— | |||
| 2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | C:\Users\admin\.oracle_jre_usage\90737d32e3abaa4.timestamp.chzgdry | binary | |
MD5:— | SHA256:— | |||
| 2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\Security\CRLCache\CE338828149963DCEA4CD26BB86F0363B4CA0BA5.crl | — | |
MD5:— | SHA256:— | |||
| 2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | C:\Users\admin\AppData\Local\VirtualStore\CHZGDRY-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | C:\Users\admin\AppData\Roaming\Adobe\Acrobat\DC\CHZGDRY-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
| 2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | C:\Users\admin\AppData\Roaming\Adobe\CHZGDRY-DECRYPT.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
15
TCP/UDP connections
22
DNS requests
11
Threats
12
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | GET | 302 | 192.185.159.253:80 | http://www.pizcam.com/ | US | — | — | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | GET | — | 212.59.186.61:80 | http://www.hotelweisshorn.com/ | CH | — | — | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | GET | 301 | 83.138.82.107:80 | http://www.swisswellness.com/ | DE | — | — | whitelisted |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | GET | 301 | 83.166.138.7:80 | http://www.whitepod.com/ | CH | — | — | whitelisted |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | GET | 200 | 74.220.215.73:80 | http://www.bizziniinfissi.com/ | US | html | 6.96 Kb | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | POST | 404 | 217.26.53.161:80 | http://www.haargenau.biz/static/pictures/sokeke.bmp | CH | html | 11.8 Kb | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | GET | 200 | 136.243.13.215:80 | http://www.holzbock.biz/ | DE | html | 1.78 Kb | suspicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | POST | 510 | 136.243.13.215:80 | http://www.holzbock.biz/includes/pictures/imfude.gif | DE | html | 740 b | suspicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | POST | 404 | 212.59.186.61:80 | http://www.hotelweisshorn.com/news/tmp/sezukerumo.jpg | CH | html | 221 b | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | GET | 301 | 104.24.23.22:80 | http://www.belvedere-locarno.com/ | US | — | — | shared |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | 78.46.77.98:80 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | 78.46.77.98:443 | www.2mmotorsport.biz | Hetzner Online GmbH | DE | suspicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | 217.26.53.161:80 | www.haargenau.biz | Hostpoint AG | CH | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | 74.220.215.73:80 | www.bizziniinfissi.com | Unified Layer | US | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | 136.243.13.215:80 | www.holzbock.biz | Hetzner Online GmbH | DE | suspicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | 138.201.162.99:80 | www.fliptray.biz | Hetzner Online GmbH | DE | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | 138.201.162.99:443 | www.fliptray.biz | Hetzner Online GmbH | DE | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | 192.185.159.253:80 | www.pizcam.com | CyrusOne LLC | US | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | 192.185.159.253:443 | www.pizcam.com | CyrusOne LLC | US | malicious |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | 83.138.82.107:443 | www.swisswellness.com | hostNET Medien GmbH | DE | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
www.2mmotorsport.biz |
| unknown |
www.haargenau.biz |
| unknown |
www.bizziniinfissi.com |
| malicious |
www.holzbock.biz |
| unknown |
www.fliptray.biz |
| malicious |
www.pizcam.com |
| unknown |
www.swisswellness.com |
| whitelisted |
www.hotelweisshorn.com |
| unknown |
www.whitepod.com |
| whitelisted |
www.hardrockhoteldavos.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | A Network Trojan was detected | ET TROJAN [eSentire] Win32/GandCrab v4/5 Ransomware CnC Activity |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (gif) |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | A Network Trojan was detected | MALWARE [PTsecurity] Win32/GandCrab Ransomware CnC Activity |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | A Network Trojan was detected | MALWARE [PTsecurity] GandCrab Ransomware HTTP |
2972 | ABF3FDB17799F468E850D823F845647738B6674451383156473F1742FFBD61EC.exe | A Network Trojan was detected | ET POLICY Data POST to an image file (jpg) |