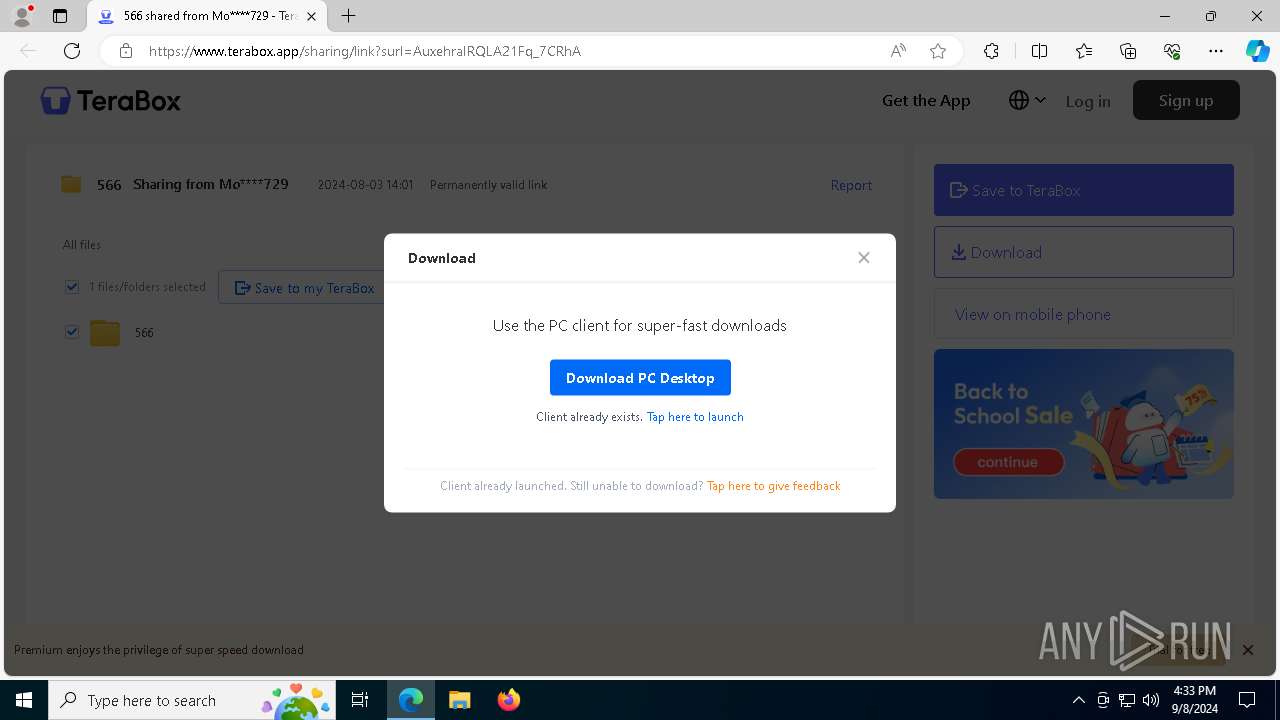
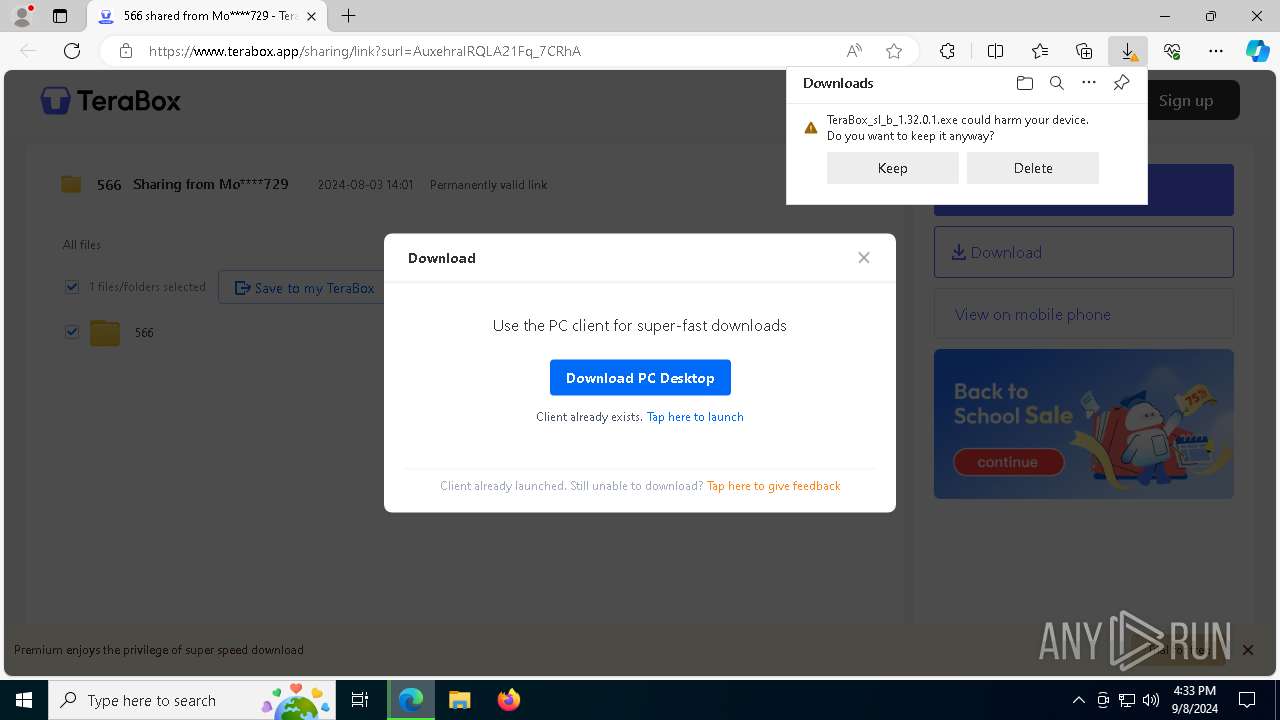
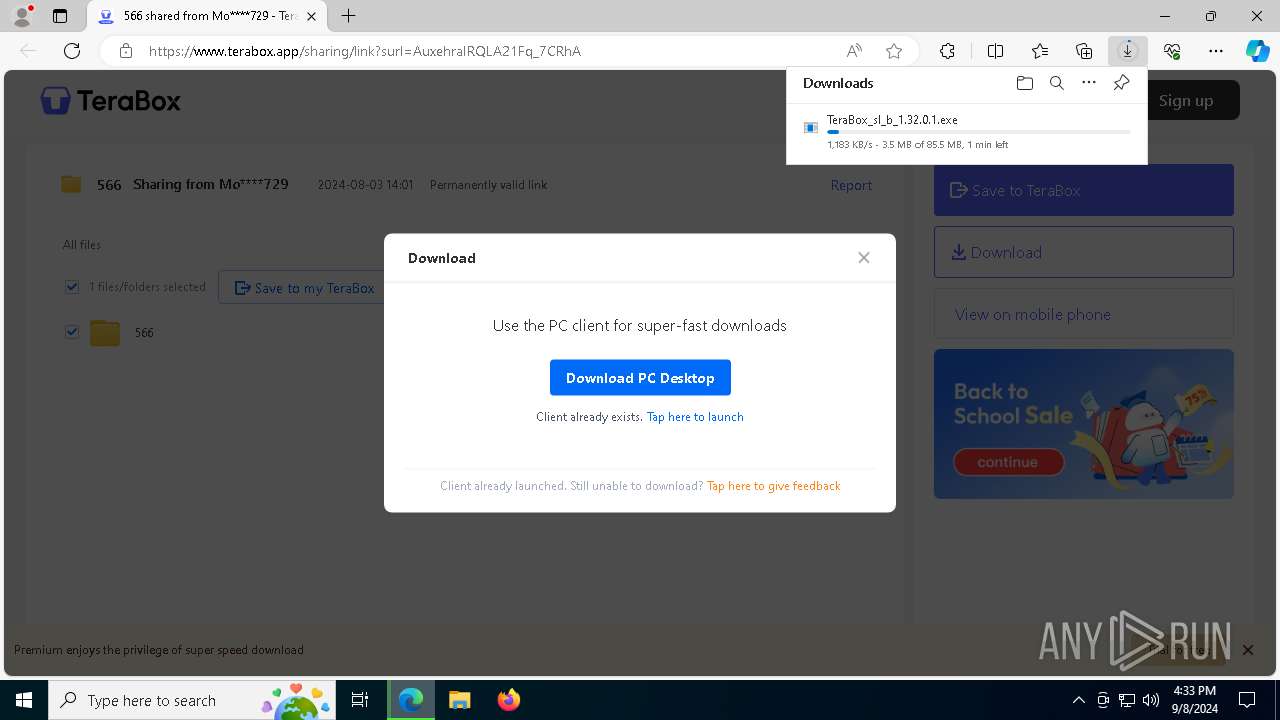
| URL: | https://1024terabox.com/s/1AuxehraIRQLA21Fq_7CRhA |
| Full analysis: | https://app.any.run/tasks/a6147b90-06e6-44e1-9fde-1643453ded0d |
| Verdict: | Malicious activity |
| Analysis date: | September 08, 2024, 16:33:22 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MD5: | 701A7786C46459AEDC66470A6E9BEA8A |
| SHA1: | FD5B570253511EEAEA21FDE344F968786966207A |
| SHA256: | ABEF97D676589BD0CE4DFC7BC165806D14F000F9CF5BD30CB487B6E3AC86748C |
| SSDEEP: | 3:N8+Xxc9AXIn:2+hBIn |
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
Changes the autorun value in the registry
- TeraBox.exe (PID: 5516)
SUSPICIOUS
Executable content was dropped or overwritten
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
- TeraBox_sl_b_1.32.0.1.exe (PID: 7456)
The process creates files with name similar to system file names
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
- TeraBox_sl_b_1.32.0.1.exe (PID: 7456)
- TeraBoxRender.exe (PID: 1688)
Malware-specific behavior (creating "System.dll" in Temp)
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
- TeraBox_sl_b_1.32.0.1.exe (PID: 7456)
Creates/Modifies COM task schedule object
- regsvr32.exe (PID: 2008)
- regsvr32.exe (PID: 2208)
- regsvr32.exe (PID: 5768)
The process drops C-runtime libraries
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
Process drops legitimate windows executable
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
Creates a software uninstall entry
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
The process checks if it is being run in the virtual environment
- TeraBox.exe (PID: 6356)
Reads security settings of Internet Explorer
- TeraBox.exe (PID: 6356)
- TeraBoxWebService.exe (PID: 1948)
- Autoupdate.exe (PID: 6512)
Checks Windows Trust Settings
- TeraBox.exe (PID: 6356)
- YunUtilityService.exe (PID: 2328)
- Autoupdate.exe (PID: 6512)
Executes as Windows Service
- YunUtilityService.exe (PID: 2328)
Adds/modifies Windows certificates
- YunUtilityService.exe (PID: 2328)
INFO
Checks supported languages
- identity_helper.exe (PID: 7196)
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
- TeraBox_sl_b_1.32.0.1.exe (PID: 7456)
- TeraBox.exe (PID: 5516)
- YunUtilityService.exe (PID: 3672)
- TeraBox.exe (PID: 6356)
- TeraBoxWebService.exe (PID: 2584)
- TeraBoxWebService.exe (PID: 1948)
- TeraBoxRender.exe (PID: 1688)
- TeraBoxRender.exe (PID: 7128)
- TeraBoxRender.exe (PID: 7868)
- TeraBoxRender.exe (PID: 7276)
- TeraBoxRender.exe (PID: 7208)
- YunUtilityService.exe (PID: 2328)
- TeraBoxHost.exe (PID: 940)
- TeraBoxRender.exe (PID: 2040)
- TeraBoxWebService.exe (PID: 2868)
- Autoupdate.exe (PID: 6512)
- TeraBoxRender.exe (PID: 6568)
- TeraBoxHost.exe (PID: 7972)
Reads Environment values
- identity_helper.exe (PID: 7196)
Reads the computer name
- identity_helper.exe (PID: 7196)
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
- TeraBox_sl_b_1.32.0.1.exe (PID: 7456)
- TeraBoxWebService.exe (PID: 1948)
- TeraBox.exe (PID: 5516)
- YunUtilityService.exe (PID: 3672)
- TeraBox.exe (PID: 6356)
- TeraBoxRender.exe (PID: 1688)
- TeraBoxRender.exe (PID: 7128)
- YunUtilityService.exe (PID: 2328)
- TeraBoxRender.exe (PID: 7868)
- TeraBoxHost.exe (PID: 7972)
- Autoupdate.exe (PID: 6512)
- TeraBoxHost.exe (PID: 940)
Creates files or folders in the user directory
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
- TeraBox.exe (PID: 5516)
- TeraBox.exe (PID: 6356)
- TeraBoxWebService.exe (PID: 1948)
- TeraBoxHost.exe (PID: 7972)
- TeraBoxHost.exe (PID: 940)
- Autoupdate.exe (PID: 6512)
Create files in a temporary directory
- TeraBox_sl_b_1.32.0.1.exe (PID: 7972)
- TeraBox_sl_b_1.32.0.1.exe (PID: 7456)
- TeraBox.exe (PID: 6356)
- TeraBoxRender.exe (PID: 7128)
Executable content was dropped or overwritten
- msedge.exe (PID: 7040)
Reads the software policy settings
- slui.exe (PID: 7292)
- TeraBox.exe (PID: 6356)
- YunUtilityService.exe (PID: 2328)
- TeraBoxRender.exe (PID: 7128)
- Autoupdate.exe (PID: 6512)
- slui.exe (PID: 7232)
The process uses the downloaded file
- iexplore.exe (PID: 5104)
- msedge.exe (PID: 7324)
- msedge.exe (PID: 7040)
- TeraBox.exe (PID: 6356)
- Autoupdate.exe (PID: 6512)
Application launched itself
- msedge.exe (PID: 7040)
Checks proxy server information
- TeraBoxWebService.exe (PID: 1948)
- TeraBox.exe (PID: 6356)
- slui.exe (PID: 7232)
- Autoupdate.exe (PID: 6512)
Reads the machine GUID from the registry
- TeraBox.exe (PID: 6356)
- YunUtilityService.exe (PID: 2328)
- TeraBoxRender.exe (PID: 7128)
- TeraBoxHost.exe (PID: 940)
- Autoupdate.exe (PID: 6512)
Process checks computer location settings
- TeraBox.exe (PID: 6356)
- TeraBoxRender.exe (PID: 7276)
- TeraBoxRender.exe (PID: 7208)
- TeraBoxRender.exe (PID: 2040)
- TeraBoxRender.exe (PID: 6568)
Sends debugging messages
- TeraBoxHost.exe (PID: 7972)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
233
Monitored processes
93
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 448 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_search_indexer.mojom.SearchIndexerInterfaceBroker --lang=en-US --service-sandbox-type=search_indexer --message-loop-type-ui --no-appcompat-clear --mojo-platform-channel-handle=6020 --field-trial-handle=2288,i,11145936175673558399,352652628353505505,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Version: 122.0.2365.59 Modules
| |||||||||||||||
| 940 | "C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxHost.exe" -PluginId 1502 -PluginPath "C:\Users\admin\AppData\Roaming\TeraBox\kernel.dll" -ChannelName terabox.6356.0.1055542588\125538543 -QuitEventName TERABOX_KERNEL_SDK_997C8EFA-C5ED-47A0-A6A8-D139CD6017F4 -TeraBoxId "" -IP "192.168.100.133" -PcGuid "TBIMXV2-O_3C9669FE16AB493E8D1F9EC42B8A5DFC-C_0-D_QM00001-M_52540053F70B-V_26B799FA" -Version "1.32.0.1" -DiskApiHttps 0 -StatisticHttps 0 -ReportCrash 1 | C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxHost.exe | TeraBox.exe | ||||||||||||
User: admin Company: Flextech Inc. Integrity Level: MEDIUM Description: TeraBoxHost Exit code: 0 Version: 1.32.0.1 Modules
| |||||||||||||||
| 1292 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6112 --field-trial-handle=2288,i,11145936175673558399,352652628353505505,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1480 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=8088 --field-trial-handle=2288,i,11145936175673558399,352652628353505505,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1688 | "C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxRender.exe" --type=gpu-process --field-trial-handle=2608,16447899419465441511,9108339912698016230,131072 --enable-features=CastMediaRouteProvider --no-sandbox --locales-dir-path="C:\Users\admin\AppData\Roaming\TeraBox\browserres\locales" --log-file="C:\Users\admin\AppData\Roaming\TeraBox\debug.log" --log-severity=disable --resources-dir-path="C:\Users\admin\AppData\Roaming\TeraBox\browserres" --user-agent="Mozilla/5.0; (Windows NT 10.0; WOW64); AppleWebKit/537.36; (KHTML, like Gecko); Chrome/86.0.4240.198; Safari/537.36; terabox;1.32.0.1;PC;PC-Windows;10.0.19045;WindowsTeraBox" --lang=en-US --gpu-preferences=MAAAAAAAAADgAAAwAAAAAAAAAAAAAAAAAABgAAAAAAAQAAAAAAAAAAAAAAAAAAAAKAAAAAQAAAAgAAAAAAAAACgAAAAAAAAAMAAAAAAAAAA4AAAAAAAAABAAAAAAAAAAAAAAAAUAAAAQAAAAAAAAAAAAAAAGAAAAEAAAAAAAAAABAAAABQAAABAAAAAAAAAAAQAAAAYAAAA= --log-file="C:\Users\admin\AppData\Roaming\TeraBox\debug.log" --mojo-platform-channel-handle=2616 /prefetch:2 | C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxRender.exe | — | TeraBox.exe | |||||||||||
User: admin Company: Flextech Inc. Integrity Level: MEDIUM Description: TeraBoxRender Exit code: 0 Version: 2.0.1.1 Modules
| |||||||||||||||
| 1688 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6960 --field-trial-handle=2288,i,11145936175673558399,352652628353505505,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1712 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=3700 --field-trial-handle=2288,i,11145936175673558399,352652628353505505,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1948 | C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxWebService.exe | C:\Users\admin\AppData\Roaming\TeraBox\TeraBoxWebService.exe | TeraBox_sl_b_1.32.0.1.exe | ||||||||||||
User: admin Company: Flextech Inc. Integrity Level: MEDIUM Description: TeraBoxWebService Version: 1.32.0.1 Modules
| |||||||||||||||
| 2008 | "/s" "C:\Users\admin\AppData\Roaming\TeraBox\YunShellExt64.dll" | C:\Windows\System32\regsvr32.exe | — | regsvr32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft(C) Register Server Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2032 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6496 --field-trial-handle=2288,i,11145936175673558399,352652628353505505,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
31 612
Read events
31 494
Write events
110
Delete events
8
Modification events
| (PID) Process: | (5104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (5104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (5104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (5104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (5104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\Zones |
| Operation: | write | Name: | SecuritySafe |
Value: 1 | |||
| (PID) Process: | (5104) iexplore.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | DisableFirstRunCustomize |
Value: 1 | |||
| (PID) Process: | (7040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (7040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (7040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (7040) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
Executable files
93
Suspicious files
795
Text files
186
Unknown types
2
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF129dbf.TMP | — | |
MD5:— | SHA256:— | |||
| 7040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF129dce.TMP | — | |
MD5:— | SHA256:— | |||
| 7040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF129dce.TMP | — | |
MD5:— | SHA256:— | |||
| 7040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF129dee.TMP | — | |
MD5:— | SHA256:— | |||
| 7040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 7040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF129dce.TMP | — | |
MD5:— | SHA256:— | |||
| 7040 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
50
TCP/UDP connections
206
DNS requests
167
Threats
36
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
6516 | svchost.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
7836 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7836 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6776 | svchost.exe | HEAD | 200 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/33525f64-900e-472b-82f7-b2841f9be572?P1=1726387802&P2=404&P3=2&P4=PPmctv6KOBud0FPo2iUWwm7r0QRl1TmJDcVLYxhjc3x2QwBYqpZu2h01R%2bhpFefG2HJIZPNTN%2b8F0HpdnAgaZg%3d%3d | unknown | — | — | whitelisted |
6776 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/33525f64-900e-472b-82f7-b2841f9be572?P1=1726387802&P2=404&P3=2&P4=PPmctv6KOBud0FPo2iUWwm7r0QRl1TmJDcVLYxhjc3x2QwBYqpZu2h01R%2bhpFefG2HJIZPNTN%2b8F0HpdnAgaZg%3d%3d | unknown | — | — | whitelisted |
1944 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
6776 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/33525f64-900e-472b-82f7-b2841f9be572?P1=1726387802&P2=404&P3=2&P4=PPmctv6KOBud0FPo2iUWwm7r0QRl1TmJDcVLYxhjc3x2QwBYqpZu2h01R%2bhpFefG2HJIZPNTN%2b8F0HpdnAgaZg%3d%3d | unknown | — | — | whitelisted |
6776 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/33525f64-900e-472b-82f7-b2841f9be572?P1=1726387802&P2=404&P3=2&P4=PPmctv6KOBud0FPo2iUWwm7r0QRl1TmJDcVLYxhjc3x2QwBYqpZu2h01R%2bhpFefG2HJIZPNTN%2b8F0HpdnAgaZg%3d%3d | unknown | — | — | whitelisted |
6776 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/33525f64-900e-472b-82f7-b2841f9be572?P1=1726387802&P2=404&P3=2&P4=PPmctv6KOBud0FPo2iUWwm7r0QRl1TmJDcVLYxhjc3x2QwBYqpZu2h01R%2bhpFefG2HJIZPNTN%2b8F0HpdnAgaZg%3d%3d | unknown | — | — | whitelisted |
6776 | svchost.exe | GET | 206 | 2.19.126.155:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/33525f64-900e-472b-82f7-b2841f9be572?P1=1726387802&P2=404&P3=2&P4=PPmctv6KOBud0FPo2iUWwm7r0QRl1TmJDcVLYxhjc3x2QwBYqpZu2h01R%2bhpFefG2HJIZPNTN%2b8F0HpdnAgaZg%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
6516 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6260 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5096 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7040 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
5096 | msedge.exe | 210.148.85.38:443 | 1024terabox.com | Internet Initiative Japan Inc. | JP | unknown |
5096 | msedge.exe | 13.107.21.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5096 | msedge.exe | 13.107.6.158:443 | business.bing.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
5096 | msedge.exe | 94.245.104.56:443 | api.edgeoffer.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
1024terabox.com |
| unknown |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
api.edgeoffer.microsoft.com |
| whitelisted |
business.bing.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
bzib.nelreports.net |
| whitelisted |
www.terabox.app |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
5096 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
5096 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
5096 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
5096 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
5096 | msedge.exe | Misc activity | ET INFO Observed File Sharing Domain (terabox .com in TLS SNI) |
5096 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
5096 | msedge.exe | Misc activity | ET INFO DNS Query to File Sharing Domain (terabox .com) |
5096 | msedge.exe | Misc activity | ET INFO Observed File Sharing Domain (terabox .com in TLS SNI) |
5096 | msedge.exe | Misc activity | ET INFO Observed File Sharing Domain (terabox .com in TLS SNI) |
5096 | msedge.exe | Misc activity | ET INFO Observed File Sharing Domain (terabox .com in TLS SNI) |
Process | Message |
|---|---|
TeraBoxHost.exe | vast_media--[2024-09-08 16:35:29:331] Initialized sdl_video_render_driver=software
|
TeraBoxHost.exe | vast_media--[2024-09-08 16:35:29:331] Initialized sdl_audio_play_driver=directsound
|
TeraBoxHost.exe | vast_media--[2024-09-08 16:35:29:331] Initialized hardware_type=3001
|