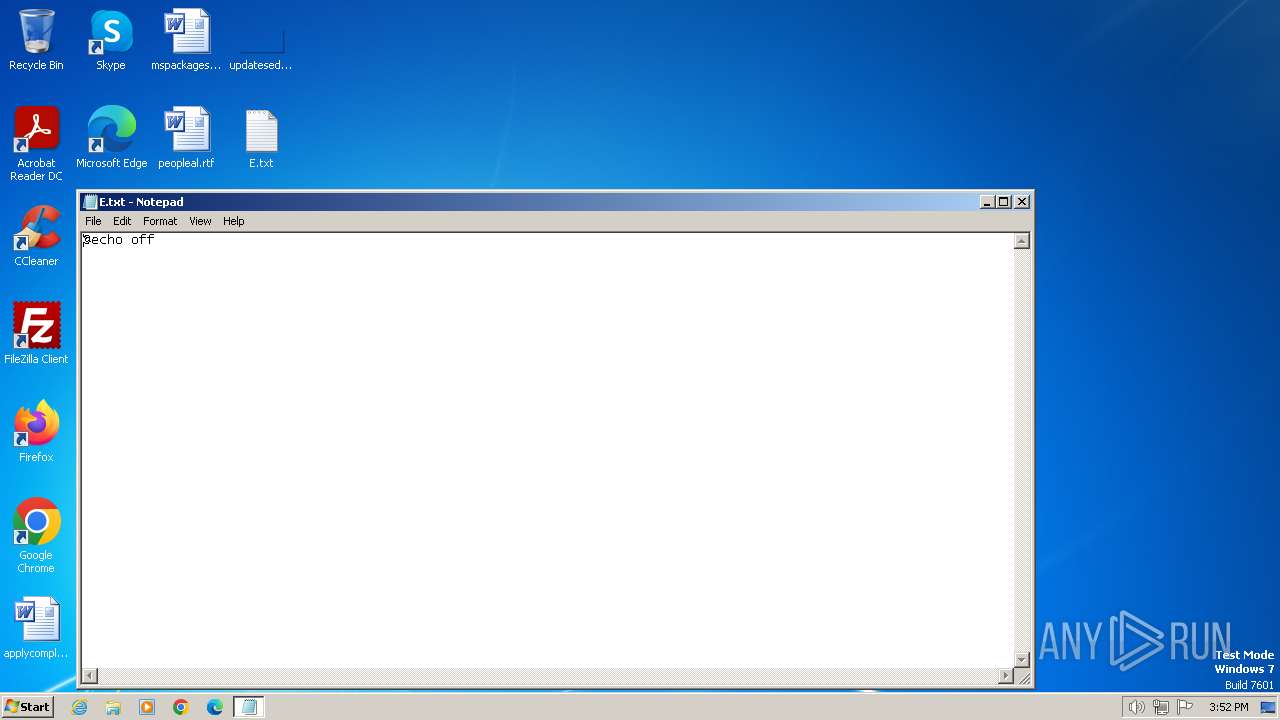
| File name: | E.txt |
| Full analysis: | https://app.any.run/tasks/afe41ea4-597a-4871-a004-275d23196d0b |
| Verdict: | Malicious activity |
| Analysis date: | February 05, 2024, 15:52:22 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/x-msdos-batch |
| File info: | DOS batch file, ASCII text, with no line terminators |
| MD5: | B0001C00A961B45A4D467FF7B0DB34F9 |
| SHA1: | 93BB6B09C9007AC568B39A77F4AA10D5DFC59FB9 |
| SHA256: | ABB30B0A70E39DE39CE0790C6C157FD04BCFB998705EC1672FE8070FF2D34573 |
| SSDEEP: | 3:mKDDn:hD |
MALICIOUS
Creates a writable file in the system directory
- mmc.exe (PID: 3040)
SUSPICIOUS
Reads the Internet Settings
- mmc.exe (PID: 3040)
Reads Internet Explorer settings
- mmc.exe (PID: 3040)
Reads Microsoft Outlook installation path
- mmc.exe (PID: 3040)
INFO
Checks proxy server information
- mmc.exe (PID: 3040)
Manual execution by a user
- mmc.exe (PID: 3040)
Creates files or folders in the user directory
- mmc.exe (PID: 3040)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
44
Monitored processes
2
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1632 | "C:\Windows\system32\NOTEPAD.EXE" "C:\Users\admin\Desktop\E.txt" | C:\Windows\System32\notepad.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3040 | "C:\Windows\system32\mmc.exe" "C:\Windows\System32\gpedit.msc" | C:\Windows\System32\mmc.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Management Console Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
1 284
Read events
1 256
Write events
28
Delete events
0
Modification events
| (PID) Process: | (3040) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3040) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3040) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3040) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
| (PID) Process: | (3040) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3040) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3040) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Editor\ADMX Filter.Cache |
| Operation: | write | Name: | IsConfigured |
Value: 0 | |||
| (PID) Process: | (3040) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Editor\ADMX Filter.Cache |
| Operation: | write | Name: | IsManaged |
Value: 1 | |||
| (PID) Process: | (3040) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Editor\ADMX Filter.Cache |
| Operation: | write | Name: | IsCommented |
Value: 0 | |||
| (PID) Process: | (3040) mmc.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Group Policy Editor\ADMX Filter.Cache |
| Operation: | write | Name: | MatchOption |
Value: 0 | |||
Executable files
0
Suspicious files
1
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3040 | mmc.exe | C:\Windows\System32\GroupPolicy\gpt.ini | text | |
MD5:FED929AE34422010496B5B4A1827A501 | SHA256:2DDA40A266ECA9DDD736701EFA24C6FE186EDD6737DB7BF52BFFE32D614667ED | |||
| 3040 | mmc.exe | C:\Windows\System32\GroupPolicy\User\Registry.pol | binary | |
MD5:30B03ACF12E3E81E46BB5D549811A980 | SHA256:70D81D3650F1BC22A1ECD1B184FC9BB2DE9BC8F0CC186E200C578765BEC07420 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |