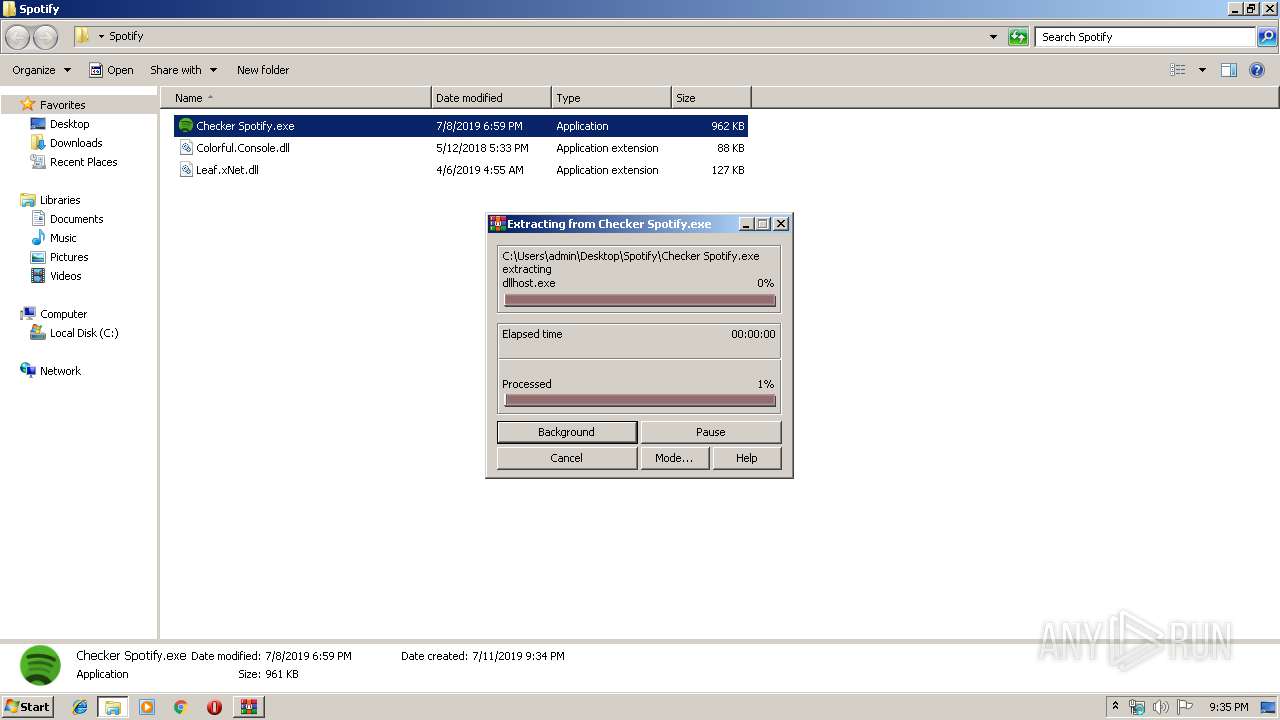
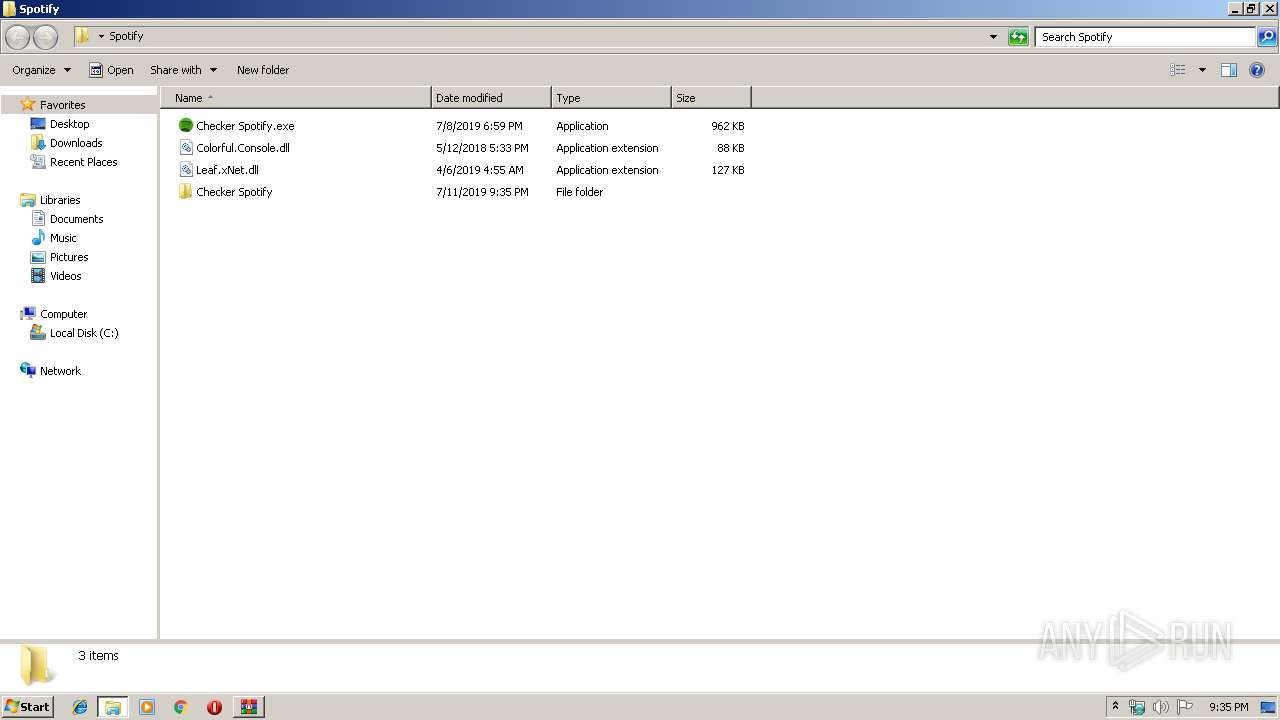
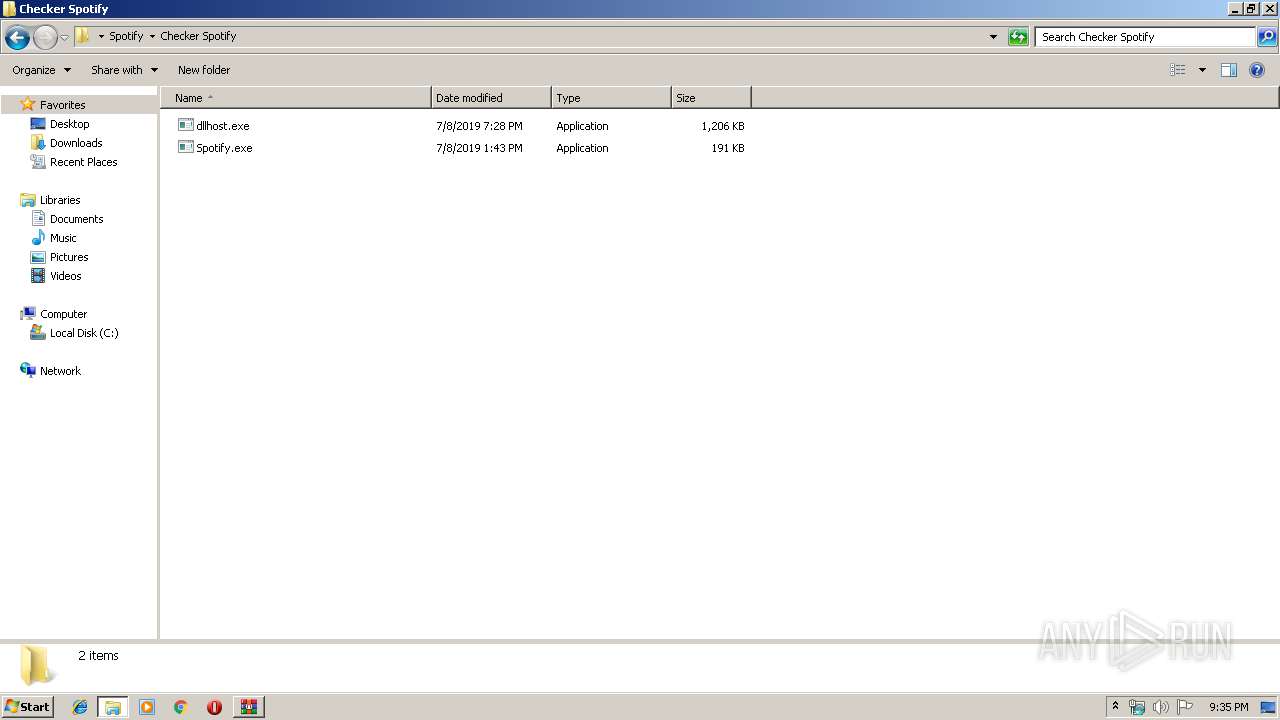
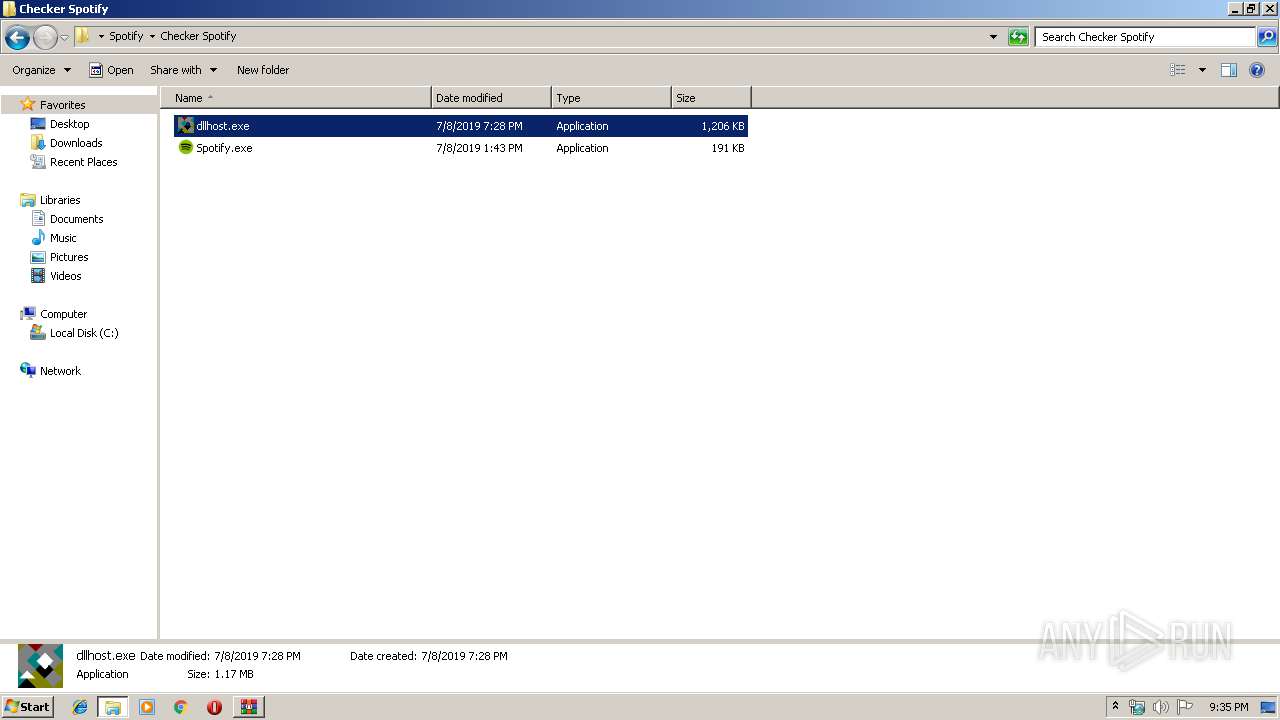
| File name: | 1.rar |
| Full analysis: | https://app.any.run/tasks/df22e793-9888-4f94-a67c-71aaeb807306 |
| Verdict: | Malicious activity |
| Analysis date: | July 11, 2019, 20:34:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | A1DC147712F228848BF6AECD3FEFA12A |
| SHA1: | 7D76F4DFE3DFA4E6B71BE3105260B32F0E504740 |
| SHA256: | ABB10A861AB09D6AF6E65833FFF839BFD9840917BA247BB819075BCBBBA3FE36 |
| SSDEEP: | 12288:jAPP7Ac8cy04l0UJfRycpKHwFx9u5MPF1gEpUqLVgp3hNHXwfic0AW5M9P6hMzHW:G8xc4Vo0xQm91gEpUYG3KxMK6hIGO2 |
MALICIOUS
Loads dropped or rewritten executable
- SearchProtocolHost.exe (PID: 2452)
Application was dropped or rewritten from another process
- dllhost.exe (PID: 1468)
- dllhost.exe (PID: 3248)
Known privilege escalation attack
- dllhost.exe (PID: 1468)
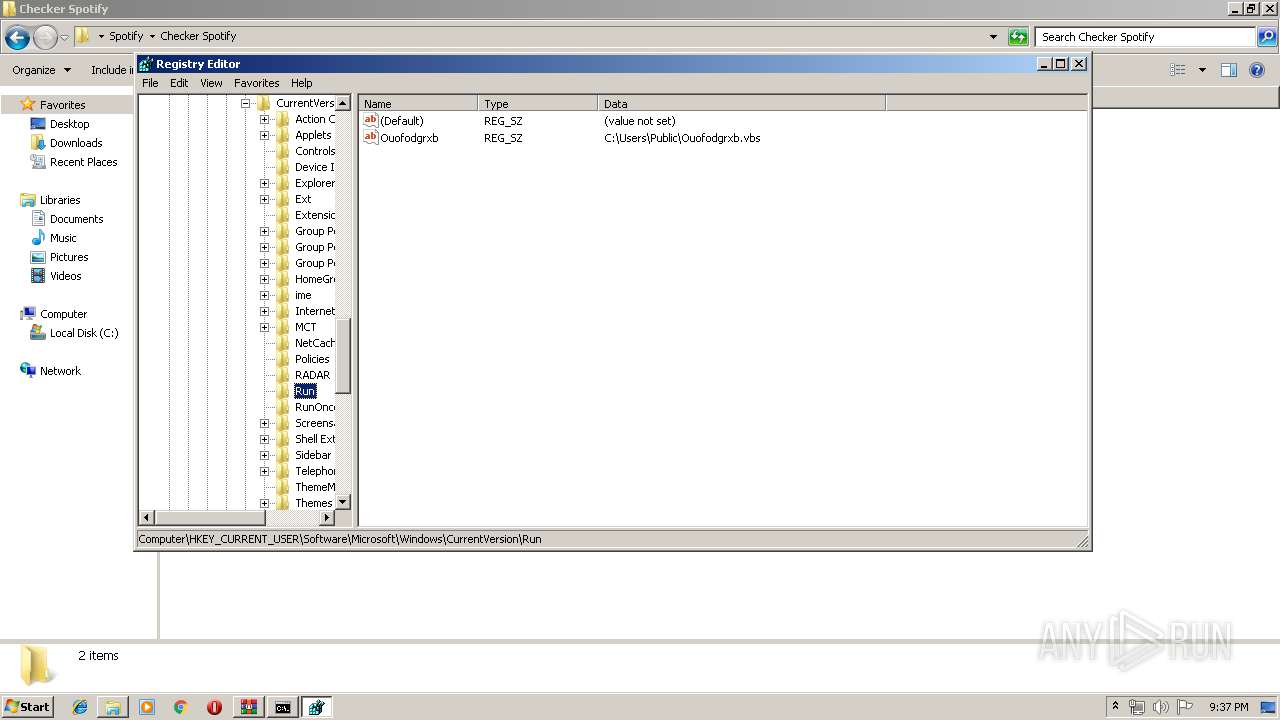
Changes the autorun value in the registry
- dllhost.exe (PID: 3248)
SUSPICIOUS
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3692)
- WinRAR.exe (PID: 3152)
- dllhost.exe (PID: 3248)
Modifies the open verb of a shell class
- dllhost.exe (PID: 1468)
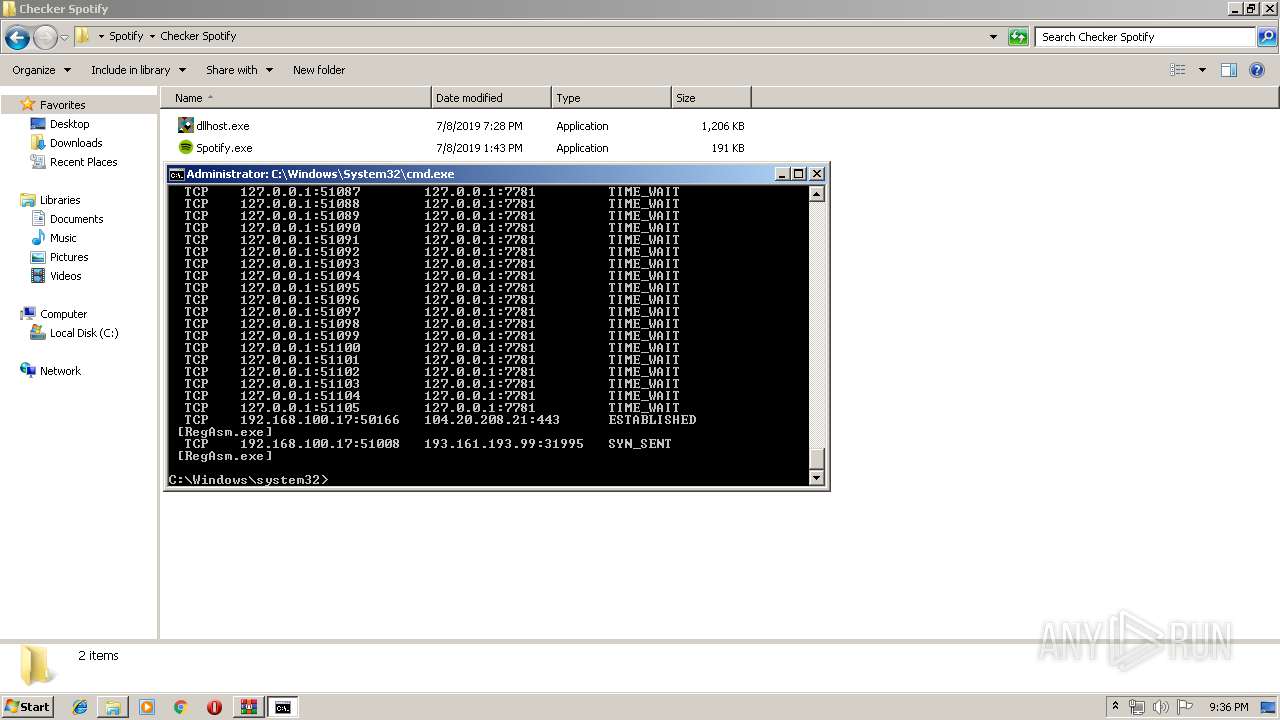
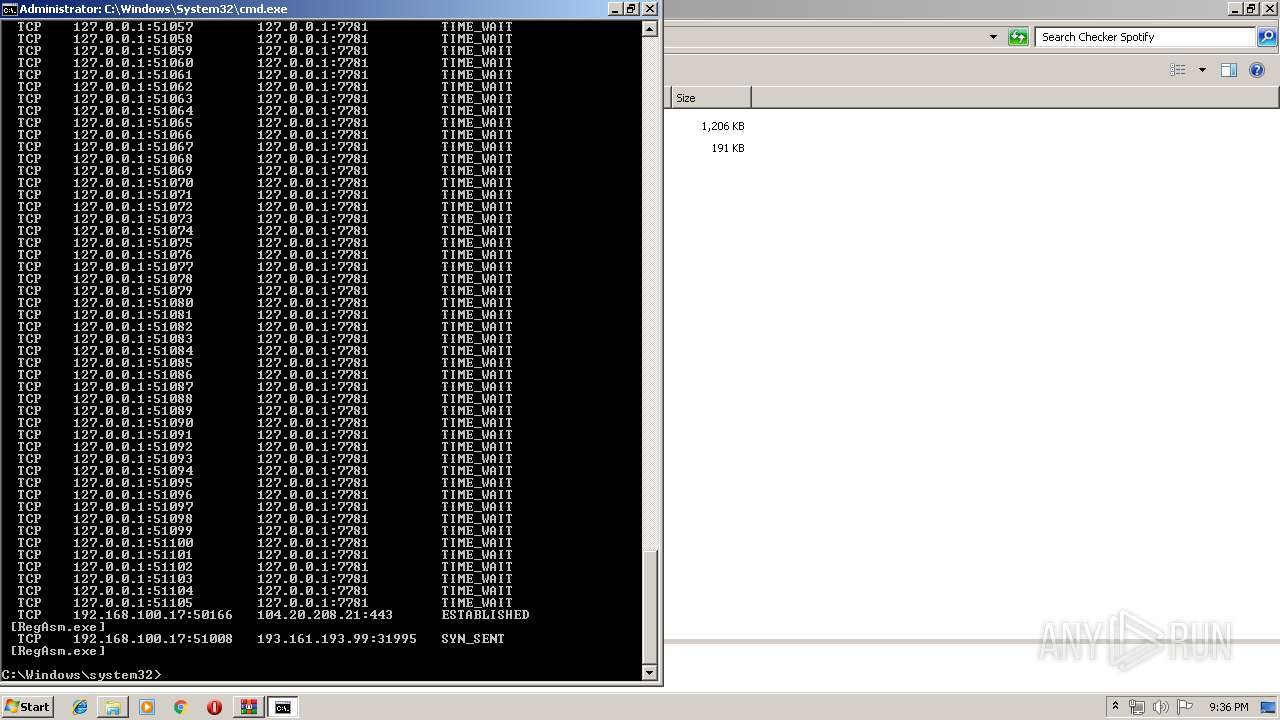
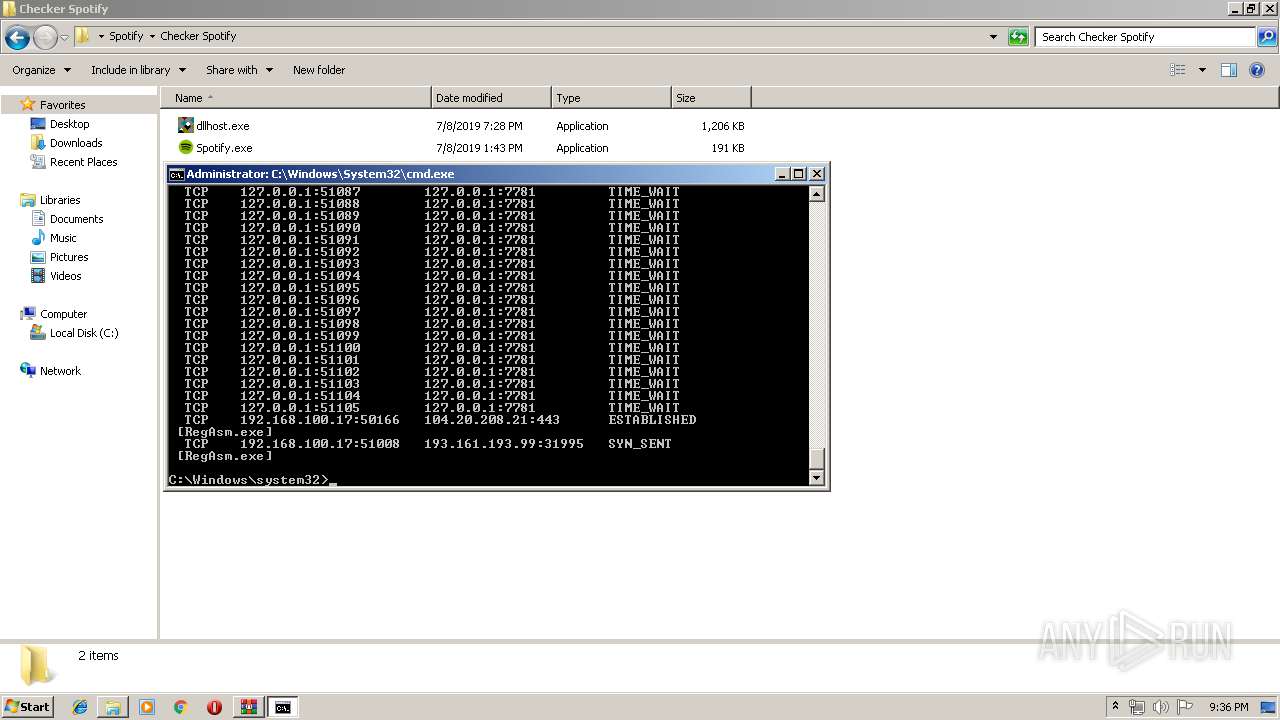
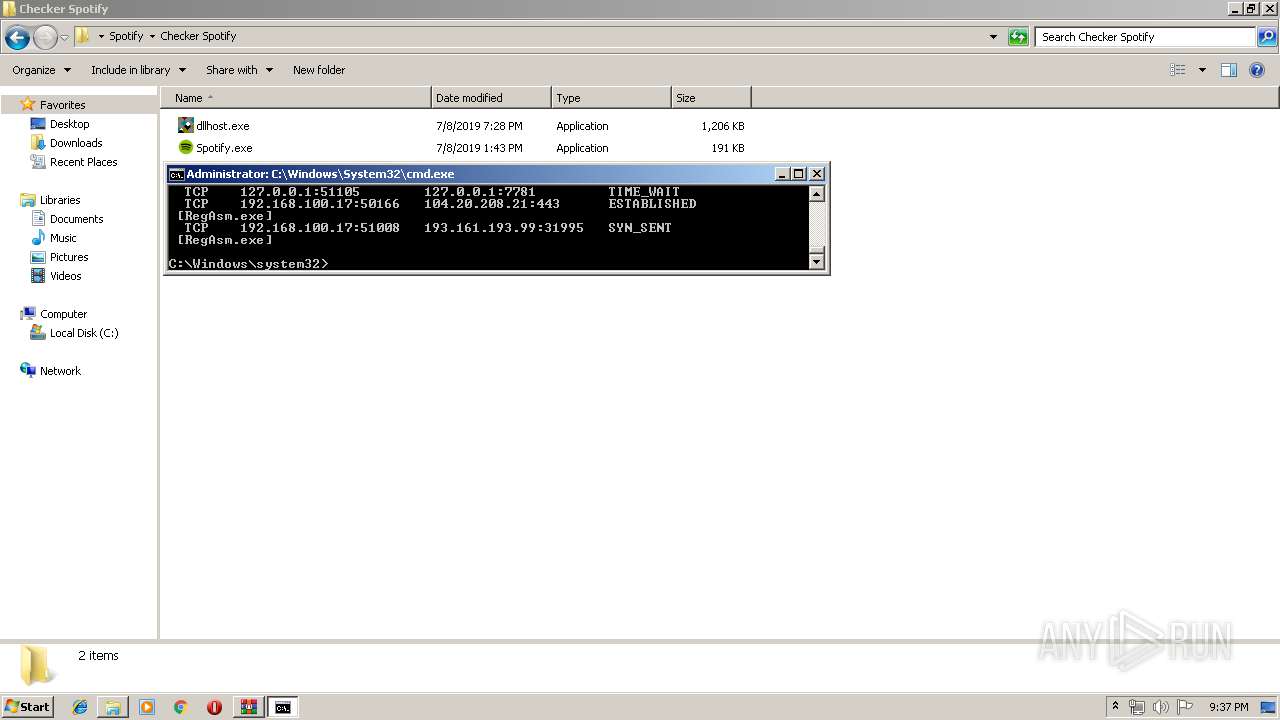
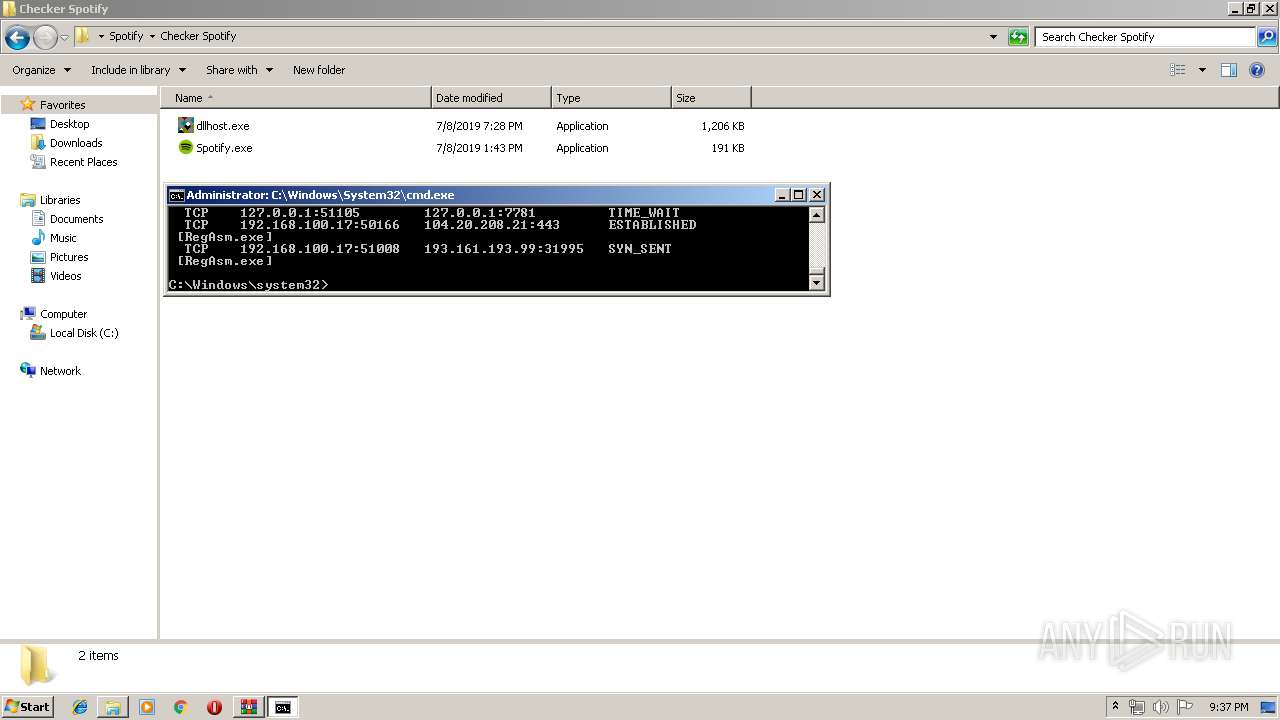
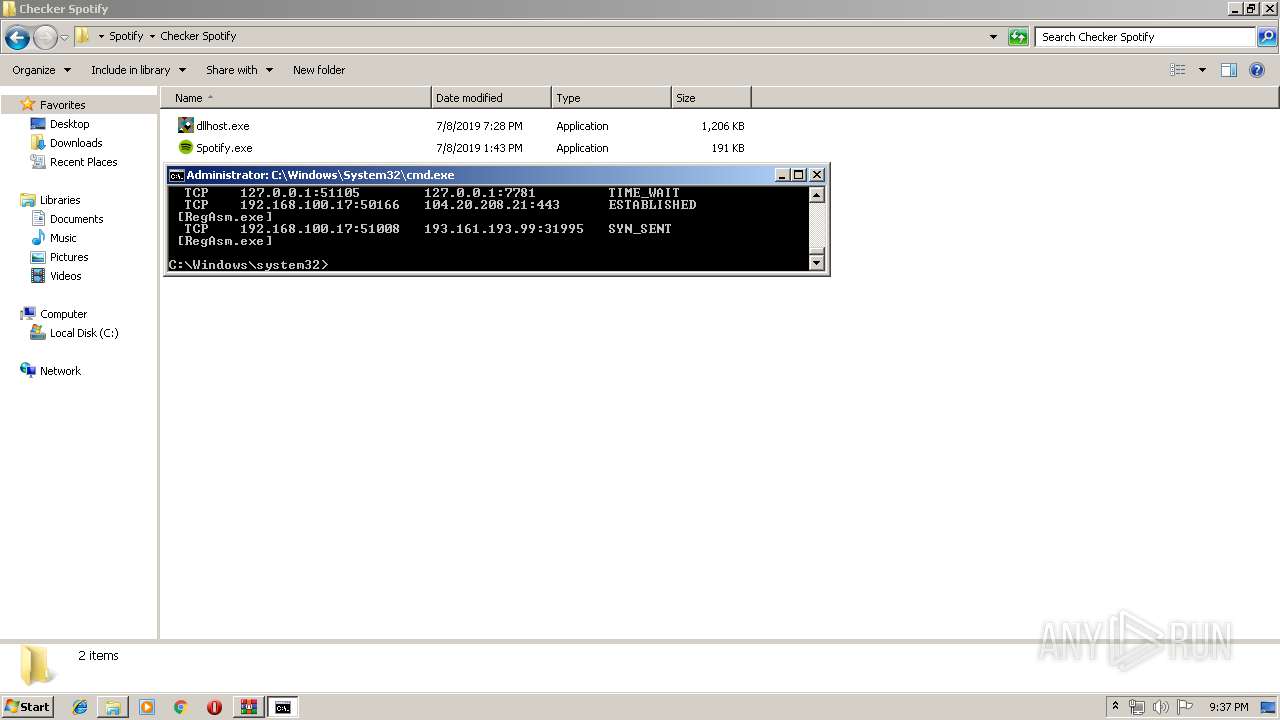
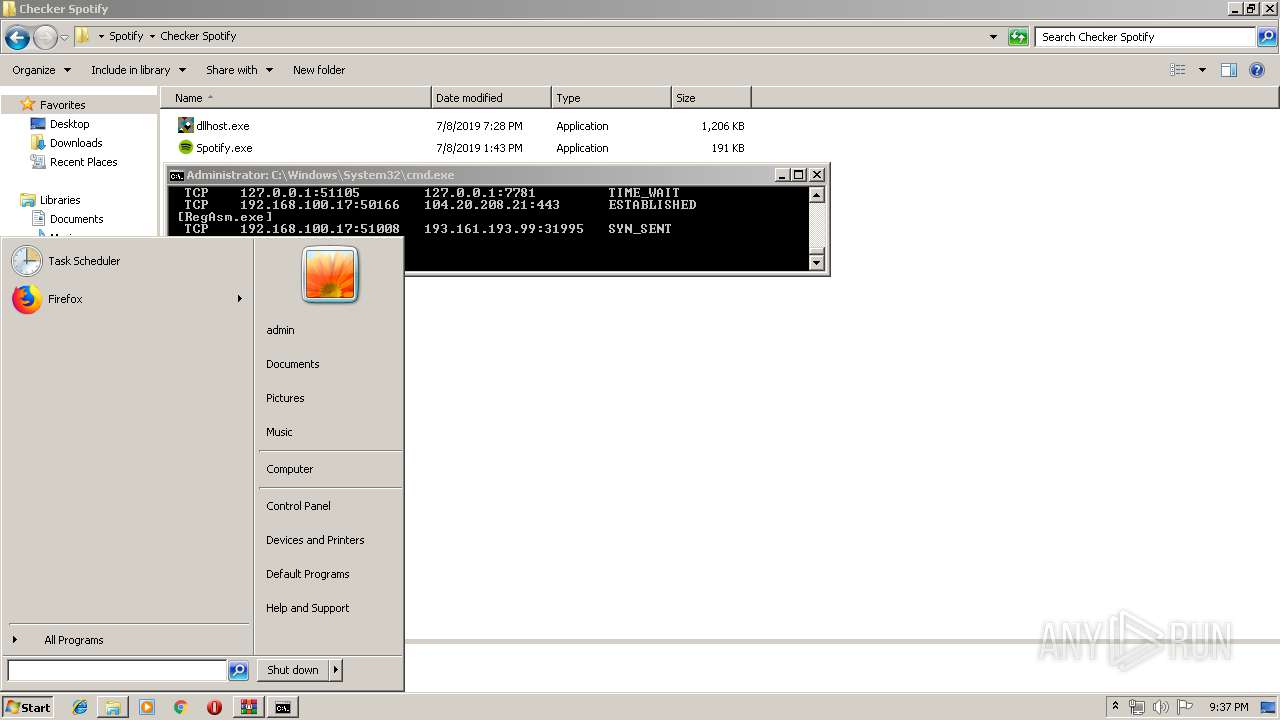
Uses NETSTAT.EXE to discover network connections
- cmd.exe (PID: 2320)
Creates files in the user directory
- dllhost.exe (PID: 3248)
Suspicious files were dropped or overwritten
- dllhost.exe (PID: 3248)
INFO
Manual execution by user
- WinRAR.exe (PID: 3152)
- dllhost.exe (PID: 1468)
- cmd.exe (PID: 2320)
- regedit.exe (PID: 3624)
- regedit.exe (PID: 2684)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
Total processes
64
Monitored processes
12
Malicious processes
2
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1136 | "C:\Windows\System32\eventvwr.exe" | C:\Windows\System32\eventvwr.exe | dllhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Event Viewer Snapin Launcher Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
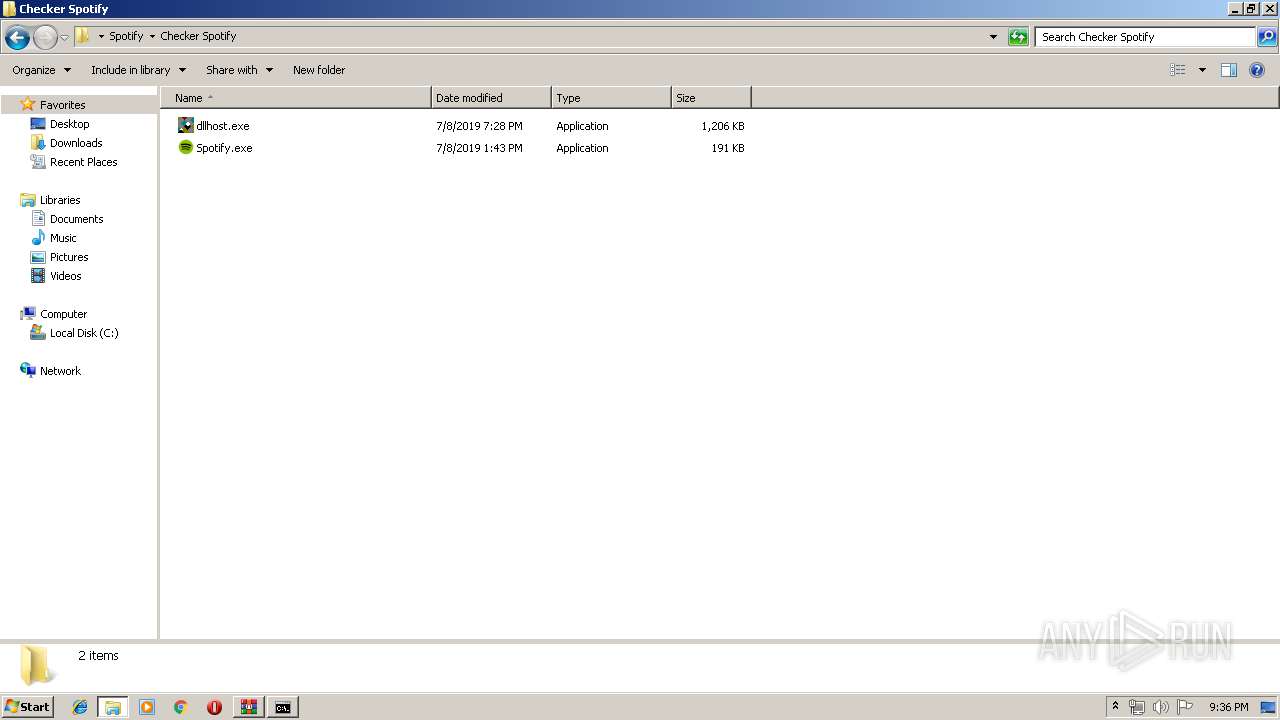
| 1468 | "C:\Users\admin\Desktop\Spotify\Checker Spotify\dllhost.exe" | C:\Users\admin\Desktop\Spotify\Checker Spotify\dllhost.exe | — | explorer.exe | |||||||||||
User: admin Company: NVIDIA_Services Integrity Level: MEDIUM Description: NVIDIA_Services Exit code: 0 Version: 91.325.103.414 Modules
| |||||||||||||||
| 2320 | "C:\Windows\System32\cmd.exe" | C:\Windows\System32\cmd.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Exit code: 0 Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2452 | "C:\Windows\system32\SearchProtocolHost.exe" Global\UsGthrFltPipeMssGthrPipe8_ Global\UsGthrCtrlFltPipeMssGthrPipe8 1 -2147483646 "Software\Microsoft\Windows Search" "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT; MS Search 4.0 Robot)" "C:\ProgramData\Microsoft\Search\Data\Temp\usgthrsvc" "DownLevelDaemon" | C:\Windows\System32\SearchProtocolHost.exe | — | SearchIndexer.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft Windows Search Protocol Host Exit code: 0 Version: 7.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 2684 | "C:\Windows\regedit.exe" | C:\Windows\regedit.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Registry Editor Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3060 | "C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\RegAsm.exe | dllhost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft .NET Assembly Registration Utility Exit code: 0 Version: 4.7.3062.0 built by: NET472REL1 Modules
| |||||||||||||||
| 3064 | netstat -nb | C:\Windows\system32\NETSTAT.EXE | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: TCP/IP Netstat Command Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
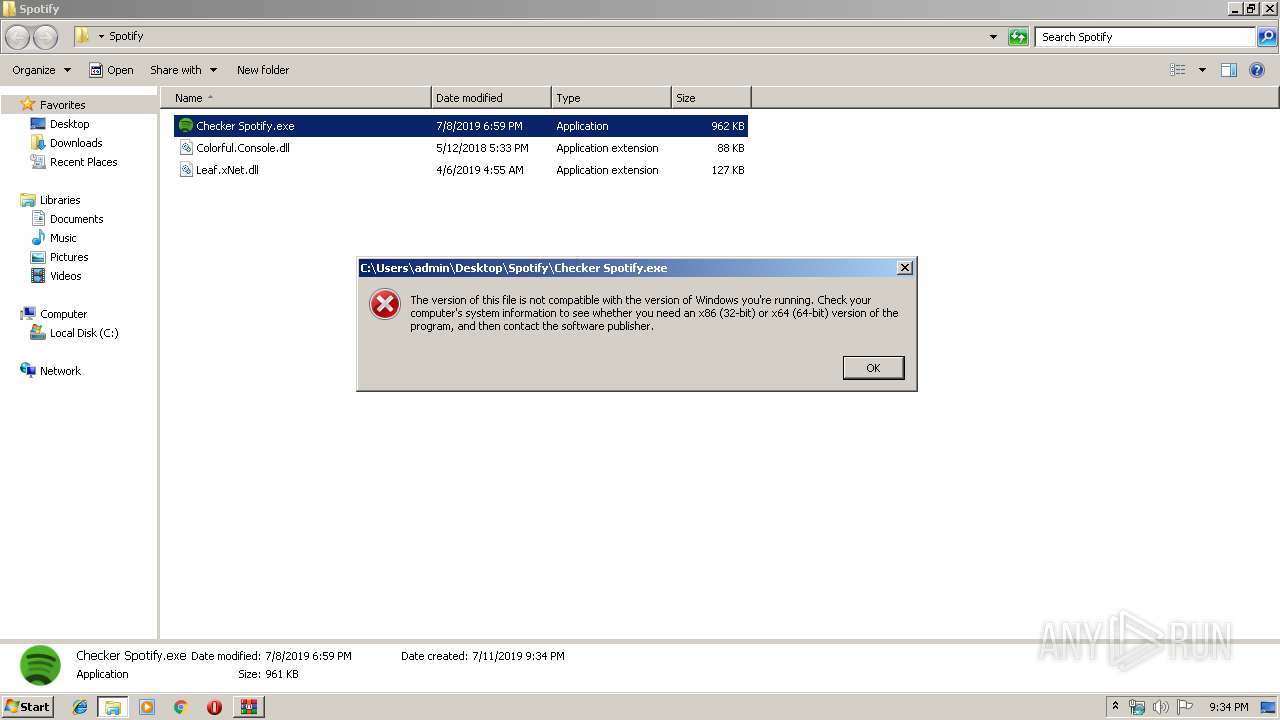
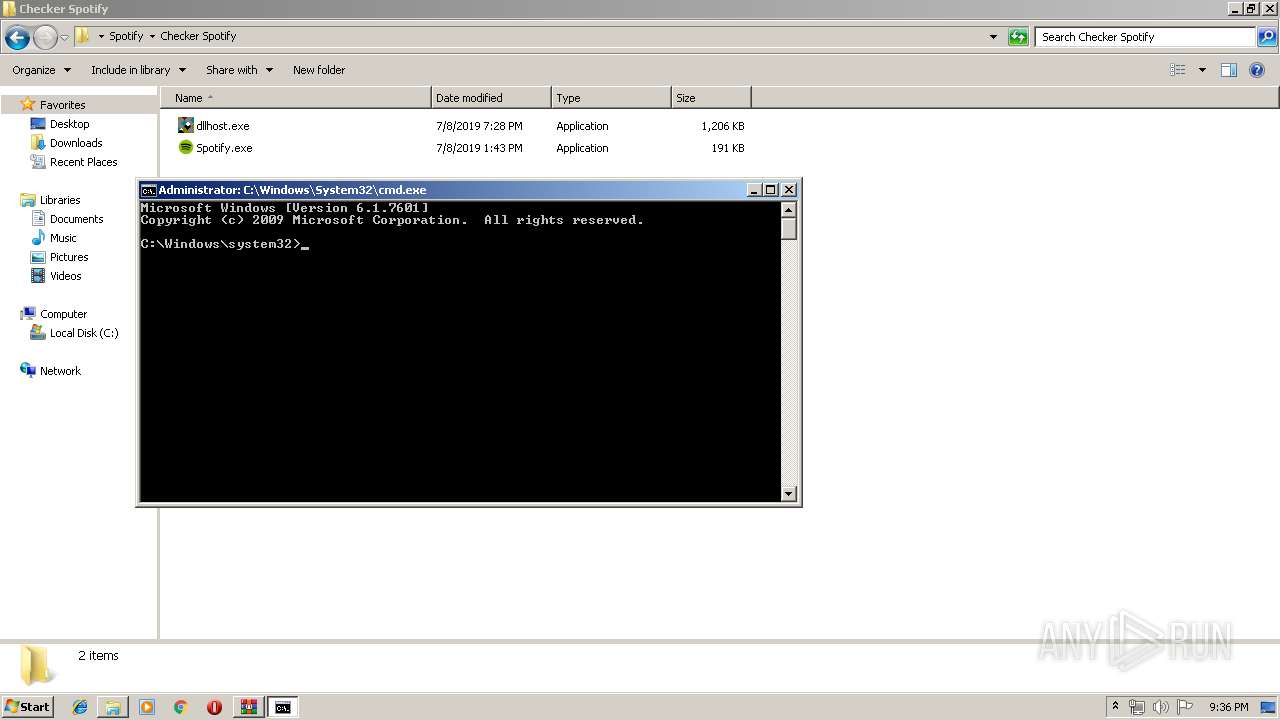
| 3152 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\Spotify\Checker Spotify.exe" "C:\Users\admin\Desktop\Spotify\Checker Spotify\" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 3248 | "C:\Users\admin\Desktop\Spotify\Checker Spotify\dllhost.exe" | C:\Users\admin\Desktop\Spotify\Checker Spotify\dllhost.exe | eventvwr.exe | ||||||||||||
User: admin Company: NVIDIA_Services Integrity Level: HIGH Description: NVIDIA_Services Exit code: 0 Version: 91.325.103.414 Modules
| |||||||||||||||
| 3624 | "C:\Windows\regedit.exe" | C:\Windows\regedit.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Editor Exit code: 3221226540 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
990
Read events
939
Write events
51
Delete events
0
Modification events
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\70\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\1.rar | |||
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3152) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3152) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
6
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3692.29512\Spotify\Colorful.Console.dll | executable | |
MD5:5F3D2CFBC21591B8FEEF1EFA3E59A4D0 | SHA256:F31D4FD7E729FC6CF4ECAB972B6B1EE897918A325B1CA572030966F831E768FB | |||
| 3248 | dllhost.exe | C:\Users\admin\AppData\Roaming\NVIDIA_Services\NVIDIA_Services.bat | executable | |
MD5:— | SHA256:— | |||
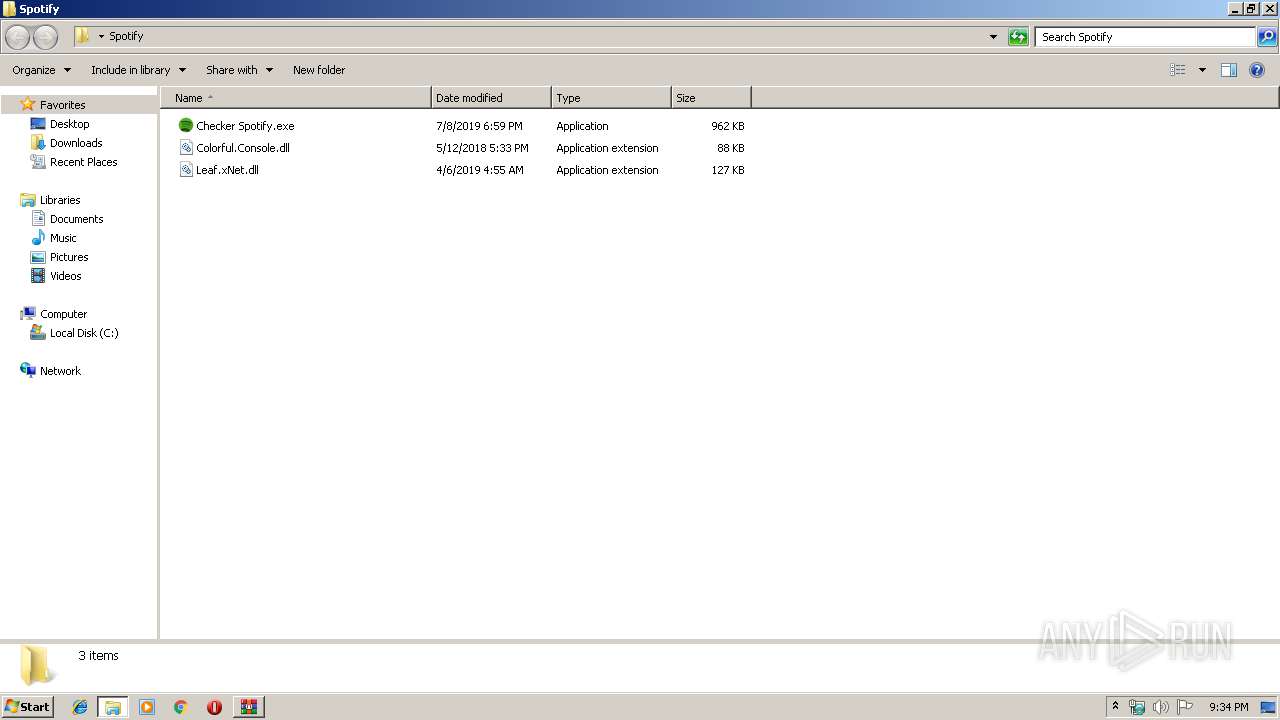
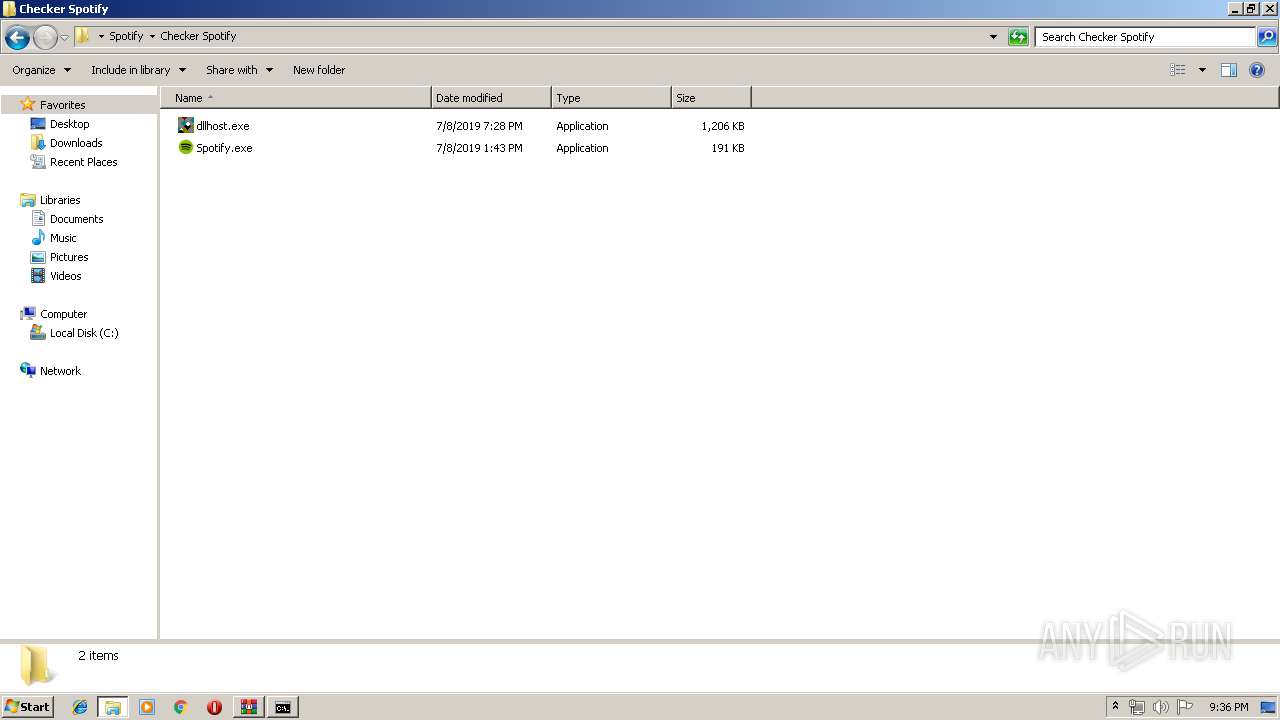
| 3152 | WinRAR.exe | C:\Users\admin\Desktop\Spotify\Checker Spotify\Spotify.exe | executable | |
MD5:7ED186D960FC7C79E8B0D62B792075EF | SHA256:7AD78C09342BDE3ABB189A631B30620E9069C84CCF5E6E4E3AF1800E0DA28EB1 | |||
| 3152 | WinRAR.exe | C:\Users\admin\Desktop\Spotify\Checker Spotify\dllhost.exe | executable | |
MD5:— | SHA256:— | |||
| 3692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3692.29512\Spotify\Checker Spotify.exe | executable | |
MD5:— | SHA256:— | |||
| 3248 | dllhost.exe | C:\Users\Public\Ouofodgrxb.vbs | text | |
MD5:— | SHA256:— | |||
| 3692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRa3692.29512\Spotify\Leaf.xNet.dll | executable | |
MD5:B5CB88DE9FE40B6645496F9543CE8E26 | SHA256:A91293829D0A4A0F2F34787FC1BA13B9D3AA4F640D0FCA652B24A88F464BC343 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
58
DNS requests
4
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3060 | RegAsm.exe | 104.20.208.21:443 | pastebin.com | Cloudflare Inc | US | shared |
3060 | RegAsm.exe | 193.161.193.99:31995 | tkmremi-31995.portmap.io | OOO Bitree Networks | RU | malicious |
— | — | 193.161.193.99:31995 | tkmremi-31995.portmap.io | OOO Bitree Networks | RU | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
pastebin.com |
| malicious |
tkmremi-31995.portmap.io |
| malicious |