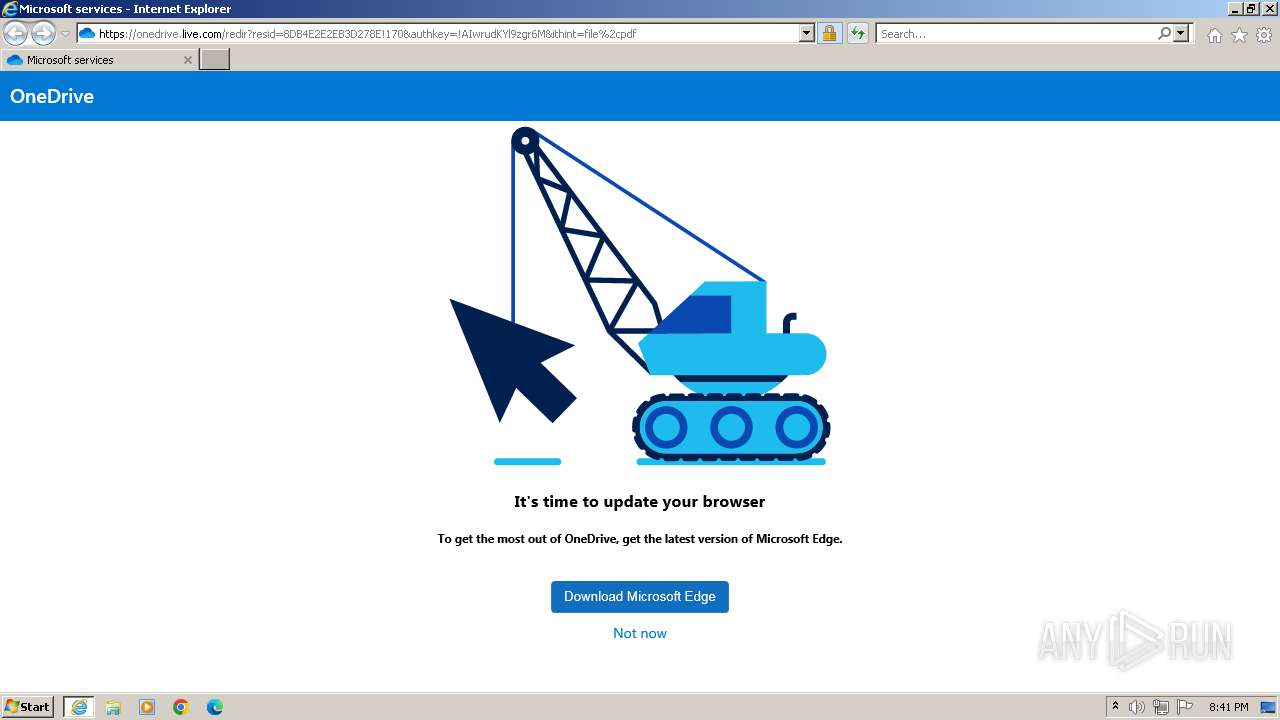
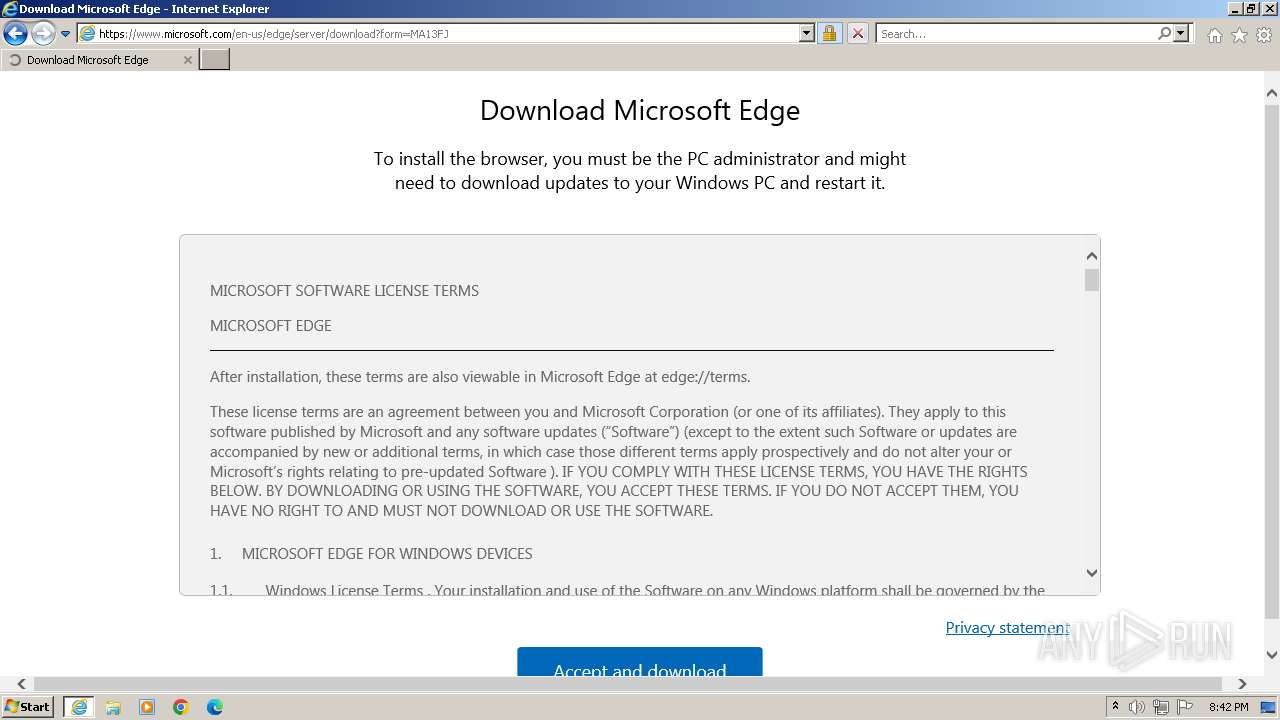
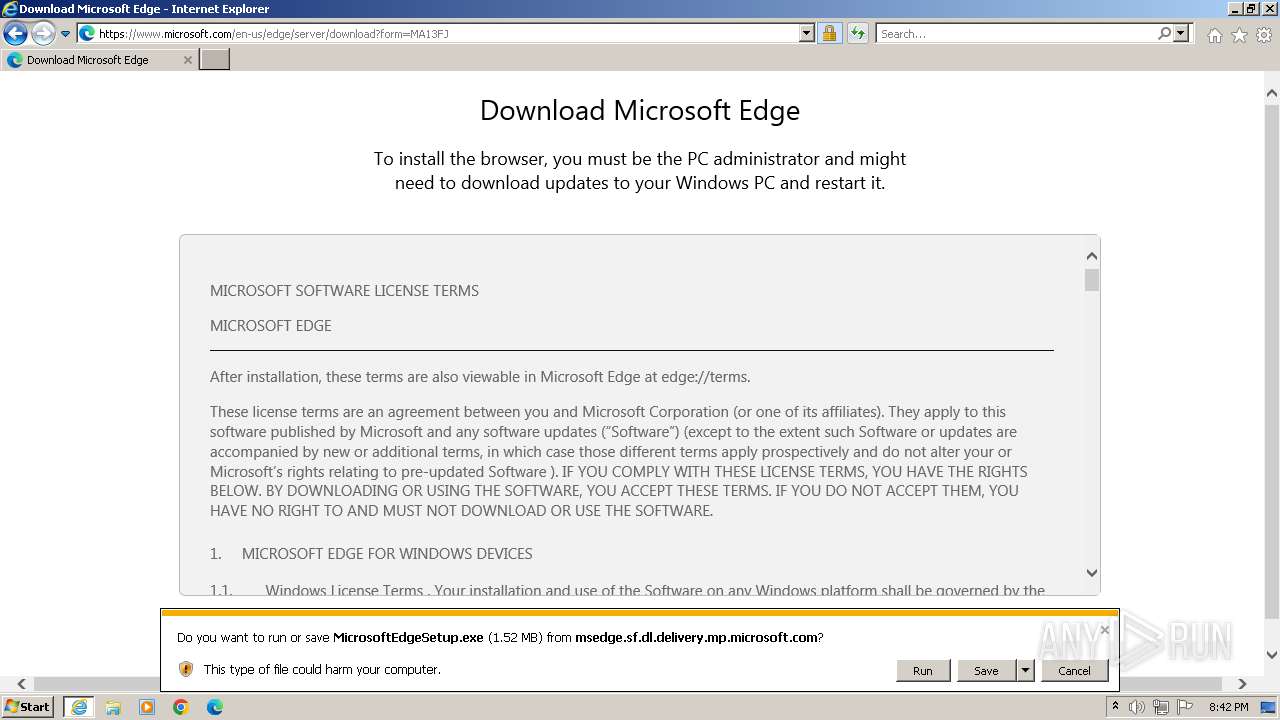
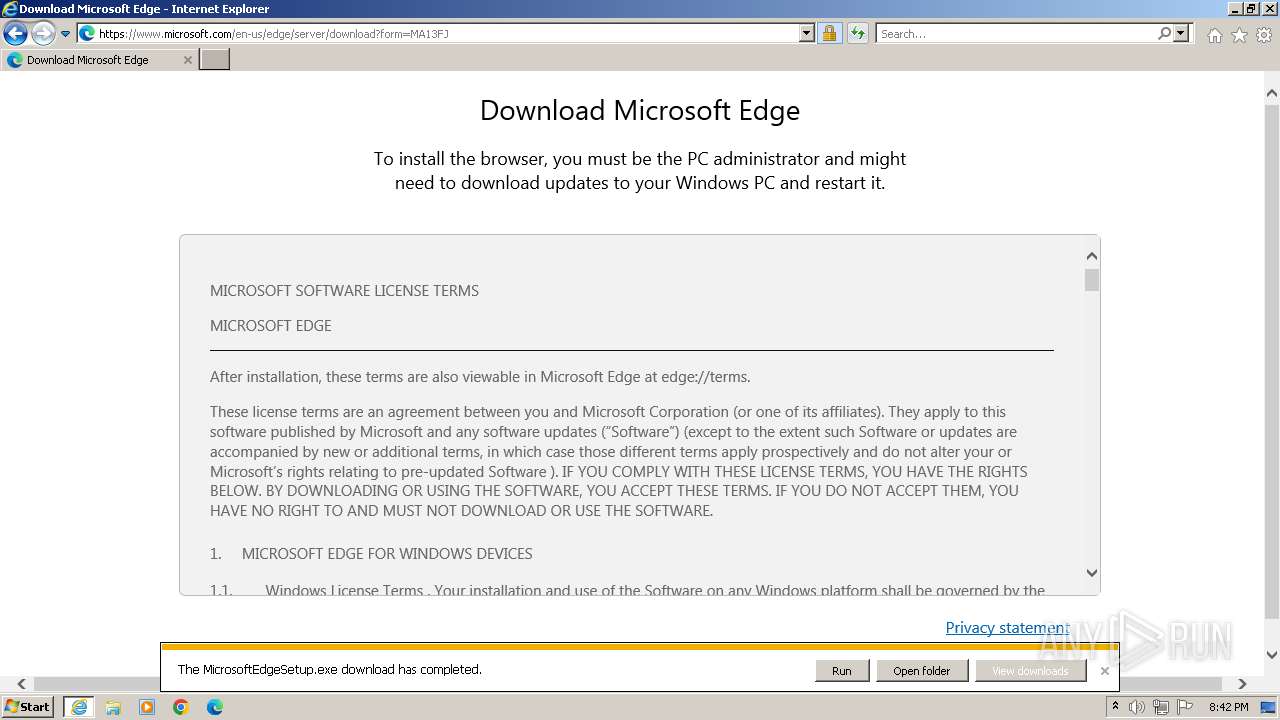
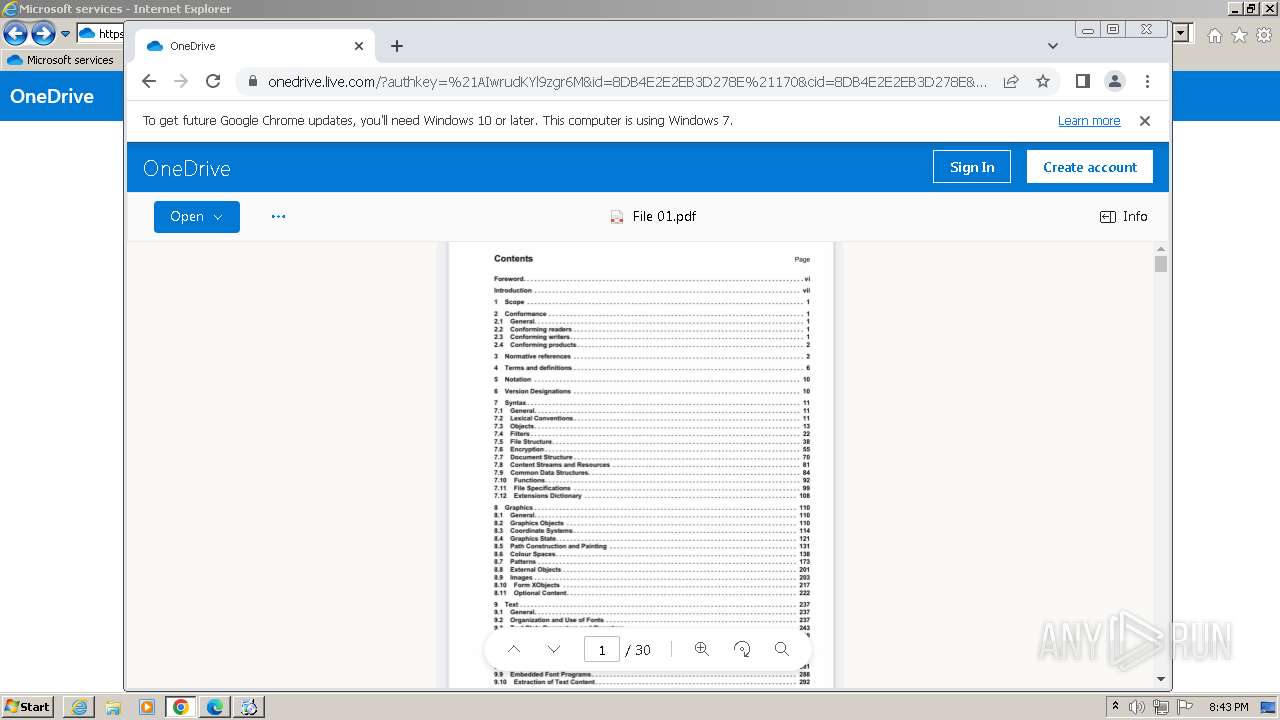
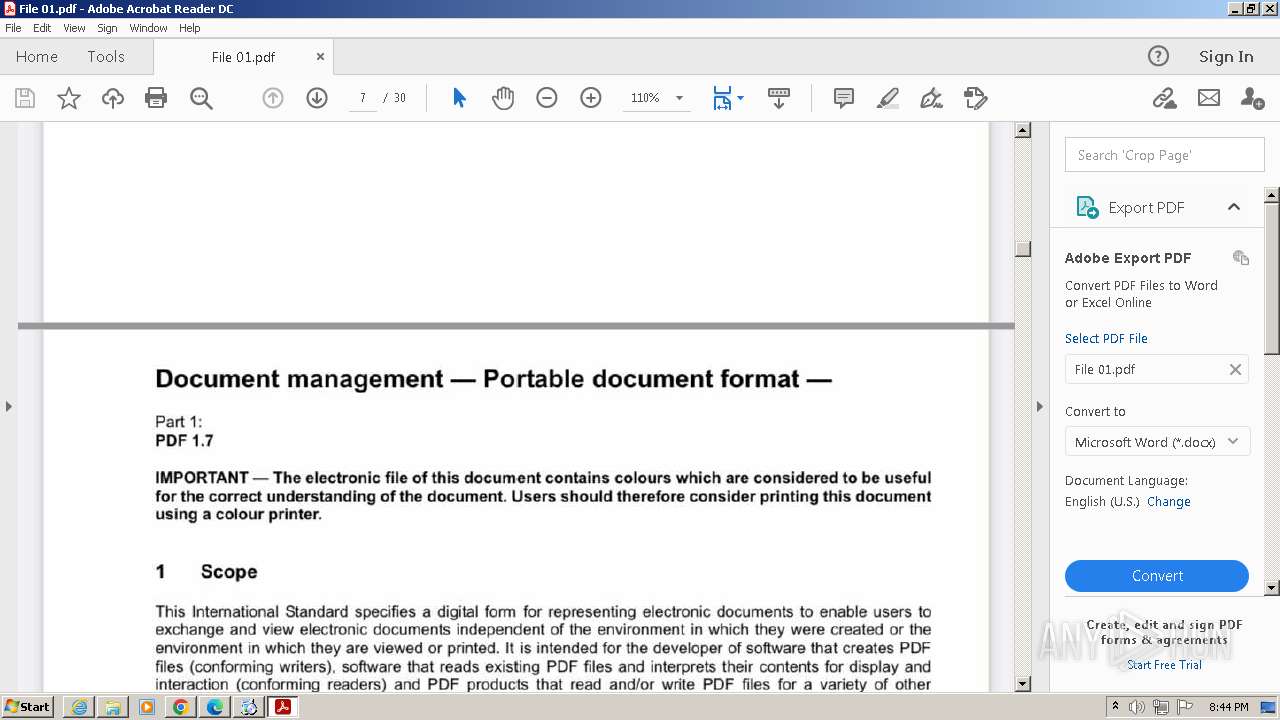
| URL: | https://1drv.ms/b/s!Ao4nPevi4rSNgSqMK7nSmJfc4K-j |
| Full analysis: | https://app.any.run/tasks/e9a41978-dd58-4fd2-81f0-2d02a718733f |
| Verdict: | Malicious activity |
| Analysis date: | October 22, 2023, 19:41:29 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| SHA1: | D3F3CE90ABC576AB1346467DC4E7E45E8A0079C8 |
| SHA256: | ABAD611A8E72626D921D366E04B778F3031B47C5B1CCDD2722DB11BC9F0B7B2A |
| SSDEEP: | 3:N8qDLIWKtYWQXMNbaIyn:2qXHiKn |
MALICIOUS
Application was dropped or rewritten from another process
- MicrosoftEdgeSetup.exe (PID: 2512)
- MicrosoftEdgeUpdate.exe (PID: 3980)
- MicrosoftEdgeUpdateSetup.exe (PID: 2984)
- MicrosoftEdgeUpdate.exe (PID: 1904)
- setup.exe (PID: 2620)
- setup.exe (PID: 4912)
Loads dropped or rewritten executable
- MicrosoftEdgeUpdate.exe (PID: 1904)
- MicrosoftEdgeUpdate.exe (PID: 3656)
- MicrosoftEdgeUpdate.exe (PID: 2476)
- MicrosoftEdgeUpdate.exe (PID: 3980)
- MicrosoftEdgeUpdate.exe (PID: 2732)
- MicrosoftEdgeUpdate.exe (PID: 2516)
- MicrosoftEdgeUpdate.exe (PID: 3324)
Drops the executable file immediately after the start
- MicrosoftEdgeSetup.exe (PID: 2512)
- MicrosoftEdgeUpdateSetup.exe (PID: 2984)
- MicrosoftEdge_X86_109.0.1518.140.exe (PID: 3184)
- setup.exe (PID: 2620)
Changes the autorun value in the registry
- setup.exe (PID: 2620)
Creates a writable file the system directory
- MicrosoftEdgeUpdate.exe (PID: 5692)
SUSPICIOUS
Process drops legitimate windows executable
- MicrosoftEdgeSetup.exe (PID: 2512)
- iexplore.exe (PID: 1560)
- MicrosoftEdgeUpdateSetup.exe (PID: 2984)
- MicrosoftEdgeUpdate.exe (PID: 1904)
- iexplore.exe (PID: 3820)
- MicrosoftEdge_X86_109.0.1518.140.exe (PID: 3184)
- setup.exe (PID: 2620)
Disables SEHOP
- MicrosoftEdgeUpdate.exe (PID: 1904)
Creates/Modifies COM task schedule object
- MicrosoftEdgeUpdate.exe (PID: 2476)
- setup.exe (PID: 2620)
Creates a software uninstall entry
- MicrosoftEdgeUpdate.exe (PID: 1904)
- setup.exe (PID: 2620)
Executes as Windows Service
- MicrosoftEdgeUpdate.exe (PID: 3324)
Reads settings of System Certificates
- MicrosoftEdgeUpdate.exe (PID: 2732)
Reads security settings of Internet Explorer
- MicrosoftEdgeUpdate.exe (PID: 2732)
Checks Windows Trust Settings
- MicrosoftEdgeUpdate.exe (PID: 2732)
- MicrosoftEdgeUpdate.exe (PID: 3324)
- MicrosoftEdgeUpdate.exe (PID: 5692)
Searches for installed software
- setup.exe (PID: 2620)
Application launched itself
- setup.exe (PID: 2620)
- MicrosoftEdgeUpdate.exe (PID: 3324)
Reads the Internet Settings
- MicrosoftEdgeUpdate.exe (PID: 2732)
INFO
Drops the executable file immediately after the start
- iexplore.exe (PID: 1560)
- iexplore.exe (PID: 3820)
Application launched itself
- iexplore.exe (PID: 3820)
- chrome.exe (PID: 2748)
- msedge.exe (PID: 2696)
- AcroRd32.exe (PID: 2004)
- RdrCEF.exe (PID: 4676)
The process uses the downloaded file
- iexplore.exe (PID: 3820)
- MicrosoftEdgeSetup.exe (PID: 2512)
- chrome.exe (PID: 3880)
- chrome.exe (PID: 1912)
- chrome.exe (PID: 2884)
- chrome.exe (PID: 2424)
Checks supported languages
- MicrosoftEdgeSetup.exe (PID: 2512)
- MicrosoftEdgeUpdateSetup.exe (PID: 2984)
- MicrosoftEdgeUpdate.exe (PID: 1904)
- MicrosoftEdgeUpdate.exe (PID: 2476)
- MicrosoftEdgeUpdate.exe (PID: 3980)
- MicrosoftEdgeUpdate.exe (PID: 3656)
- MicrosoftEdgeUpdate.exe (PID: 2732)
- MicrosoftEdgeUpdate.exe (PID: 2516)
- MicrosoftEdgeUpdate.exe (PID: 3324)
- MicrosoftEdge_X86_109.0.1518.140.exe (PID: 3184)
- setup.exe (PID: 2620)
- setup.exe (PID: 4912)
- MicrosoftEdgeUpdate.exe (PID: 5692)
Reads the computer name
- MicrosoftEdgeUpdate.exe (PID: 3980)
- MicrosoftEdgeUpdate.exe (PID: 1904)
- MicrosoftEdgeUpdate.exe (PID: 2476)
- MicrosoftEdgeUpdate.exe (PID: 2732)
- MicrosoftEdgeUpdate.exe (PID: 3324)
- MicrosoftEdgeUpdate.exe (PID: 2516)
- MicrosoftEdge_X86_109.0.1518.140.exe (PID: 3184)
- setup.exe (PID: 2620)
- MicrosoftEdgeUpdate.exe (PID: 3656)
- setup.exe (PID: 4912)
- MicrosoftEdgeUpdate.exe (PID: 5692)
Reads the machine GUID from the registry
- MicrosoftEdgeUpdate.exe (PID: 3980)
- setup.exe (PID: 2620)
Create files in a temporary directory
- MicrosoftEdgeSetup.exe (PID: 2512)
- MicrosoftEdgeUpdate.exe (PID: 2732)
Creates files in the program directory
- MicrosoftEdgeUpdateSetup.exe (PID: 2984)
- MicrosoftEdge_X86_109.0.1518.140.exe (PID: 3184)
- setup.exe (PID: 2620)
- setup.exe (PID: 4912)
Checks proxy server information
- MicrosoftEdgeUpdate.exe (PID: 2732)
Reads Environment values
- MicrosoftEdgeUpdate.exe (PID: 2732)
- MicrosoftEdgeUpdate.exe (PID: 5692)
Manual execution by a user
- msedge.exe (PID: 2696)
- chrome.exe (PID: 2748)
- AcroRd32.exe (PID: 2004)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
113
Monitored processes
69
Malicious processes
9
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 388 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --disable-gpu-compositing --lang=en-US --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=16 --mojo-platform-channel-handle=3920 --field-trial-handle=984,i,1130805073018807432,5976761390880598356,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 560 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1428 --field-trial-handle=984,i,1130805073018807432,5976761390880598356,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | chrome.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 592 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --pdf-renderer --disable-gpu-compositing --lang=en-US --js-flags=--jitless --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=18 --mojo-platform-channel-handle=4452 --field-trial-handle=984,i,1130805073018807432,5976761390880598356,131072 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 820 | "C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe" --type=gpu-process --field-trial-handle=1140,423157057720296761,12136664678514292670,131072 --disable-features=NetworkService,VizDisplayCompositor --disable-pack-loading --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --log-severity=disable --product-version="ReaderServices/20.13.20064 Chrome/80.0.0.0" --lang=en-US --gpu-preferences=KAAAAAAAAADgACAgAQAAAAAAAAAAAGAAAAAAABAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --use-gl=swiftshader-webgl --log-file="C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\debug.log" --service-request-channel-token=6531807286587262482 --mojo-platform-channel-handle=1348 --allow-no-sandbox-job --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Adobe\Acrobat Reader DC\Reader\AcroCEF\RdrCEF.exe | — | RdrCEF.exe | |||||||||||
User: admin Company: Adobe Systems Incorporated Integrity Level: LOW Description: Adobe RdrCEF Exit code: 1 Version: 20.13.20064.405839 Modules
| |||||||||||||||
| 1560 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3820 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 1772 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=chrome.mojom.UtilWin --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=4064 --field-trial-handle=984,i,1130805073018807432,5976761390880598356,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1792 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=3712 --field-trial-handle=984,i,1130805073018807432,5976761390880598356,131072 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1804 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --instant-process --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=5 --mojo-platform-channel-handle=2264 --field-trial-handle=1312,i,16762189898617854984,8715672472298469685,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1836 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Google\Chrome\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Google\Chrome\User Data\Crashpad" --url=https://clients2.google.com/cr/report --annotation=channel= --annotation=plat=Win32 --annotation=prod=Chrome --annotation=ver=109.0.5414.120 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd4,0x6b378b38,0x6b378b48,0x6b378b54 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 109.0.5414.120 Modules
| |||||||||||||||
| 1876 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=storage.mojom.StorageService --lang=en-US --service-sandbox-type=service --mojo-platform-channel-handle=1604 --field-trial-handle=1312,i,16762189898617854984,8715672472298469685,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
54 617
Read events
51 271
Write events
3 225
Delete events
121
Modification events
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPDaysSinceLastAutoMigration |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\TabbedBrowsing |
| Operation: | write | Name: | NTPLastLaunchHighDateTime |
Value: 30847387 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\UrlBlockManager |
| Operation: | write | Name: | NextCheckForUpdateHighDateTime |
Value: 30847437 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Internet Explorer\Main |
| Operation: | write | Name: | CompatibilityFlags |
Value: 0 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | ProxyBypass |
Value: 1 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | IntranetName |
Value: 1 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 1 | |||
| (PID) Process: | (3820) iexplore.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 0 | |||
Executable files
390
Suspicious files
1 675
Text files
122
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\80237EE4964FC9C409AAF55BF996A292_C0427F5F77D9B3A439FC620EDAAB6177 | binary | |
MD5:9EA3D39181B3239B6FA4CA27C0B72437 | SHA256:76ED31F9B31A3818A4F2457A63EDA60C54C71111CFB93B586ED513A84D12426B | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\Internet Explorer\Services\search_{0633EE93-D776-472f-A0FF-E1416B8B2E3A}.ico | image | |
MD5:DA597791BE3B6E732F0BC8B20E38EE62 | SHA256:5B2C34B3C4E8DD898B664DBA6C3786E2FF9869EFF55D673AA48361F11325ED07 | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\7423F88C7F265F0DEFC08EA88C3BDE45_AA1E8580D4EBC816148CE81268683776 | binary | |
MD5:8761D8CF2E90FD1D6AE690013BA77D5A | SHA256:C3B34D5D937929262C5FB874EA352A4B8982CBBFAE866209876D26B5F0AEA6FB | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\BQ0XZOGL.txt | text | |
MD5:B971653BEC03F4DDC330164AD6DE4E54 | SHA256:78FB8800E949A9E2A8A9D9D7ABC57E90D2AA2963AA349B06EA1502DC9496D74D | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\80237EE4964FC9C409AAF55BF996A292_C0427F5F77D9B3A439FC620EDAAB6177 | binary | |
MD5:68E5B3E3B1B00B2A5396F3AEB326B74D | SHA256:35305571D52A5BEC5664113C58F54B85F19F4C20C1A44A21ECC85908503D24A7 | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:A4FBAF9951E6FF79F12944A3AD53369D | SHA256:BCA2E18ABD4375B066A310DFB846F4FB1B7A54C1B9D376F9B1DFB38D68F6C021 | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\DY534W2X\redir[1].htm | html | |
MD5:F8BD9F01F5F9F7145F6F133C98EEEDFB | SHA256:C395133175D9E7535EA2A6336C91D2A504F915CC061ED2B601BF3DA663A7E271 | |||
| 1560 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:1BFE591A4FE3D91B03CDF26EAACD8F89 | SHA256:9CF94355051BF0F4A45724CA20D1CC02F76371B963AB7D1E38BD8997737B13D8 | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\VersionManager\ver3AB0.tmp | xml | |
MD5:CBD0581678FA40F0EDCBC7C59E0CAD10 | SHA256:159BD4343F344A08F6AF3B716B6FA679859C1BD1D7030D26FF5EF0255B86E1D9 | |||
| 3820 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Internet Explorer\imagestore\f7ruq93\imagestore.dat | binary | |
MD5:0F9B838A23C009B97F5AB2EAAEADA12D | SHA256:7176D6604FFCD90487BC39FBC49EAE81E593EAF6DF88A75AC59C3343494C4846 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
19
TCP/UDP connections
132
DNS requests
143
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
864 | svchost.exe | HEAD | 200 | 8.253.207.121:80 | http://msedge.f.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/d87a3bbd-7fe5-4ec3-b806-293cca78b363?P1=1698608555&P2=404&P3=2&P4=c0bttGp8ekgUvrnLoIYpP1xzd720fM%2bKAidoVhK8rAK6McZ213Jm03Id1DGod3UPNdlb8%2f03Cj7NhD1fAMTyDA%3d%3d | unknown | — | — | unknown |
1560 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAqvpsXKY8RRQeo74ffHUxc%3D | unknown | binary | 471 b | unknown |
3820 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAzlnDD9eoNTLi0BRrMy%2BWU%3D | unknown | binary | 314 b | unknown |
1560 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | binary | 471 b | unknown |
1560 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?f8f3bf607e1d79ae | unknown | compressed | 4.66 Kb | unknown |
864 | svchost.exe | GET | 206 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | binary | 8.92 Kb | unknown |
1560 | iexplore.exe | GET | 200 | 209.197.3.8:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?8f869686e34b7eef | unknown | compressed | 4.66 Kb | unknown |
1560 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | binary | 471 b | unknown |
864 | svchost.exe | HEAD | 200 | 34.104.35.123:80 | http://edgedl.me.gvt1.com/edgedl/release2/chrome_component/ad3rm3ciqs3fjr4bc4x5vwuildeq_9.49.1/gcmjkmgdlgnkkcocmoeiminaijmmjnii_9.49.1_all_ixzyrcu7pvmgu5pjv6enfqq6wa.crx3 | unknown | — | — | unknown |
1560 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA177el9ggmWelJjG4vdGL0%3D | unknown | binary | 471 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1560 | iexplore.exe | 13.107.42.12:443 | api.onedrive.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1560 | iexplore.exe | 209.197.3.8:80 | ctldl.windowsupdate.com | STACKPATH-CDN | US | whitelisted |
1560 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
1560 | iexplore.exe | 13.107.42.13:443 | onedrive.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
1560 | iexplore.exe | 51.105.104.217:443 | p.sfx.ms | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3820 | iexplore.exe | 51.105.104.217:443 | p.sfx.ms | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
3820 | iexplore.exe | 104.126.37.170:443 | www.bing.com | Akamai International B.V. | DE | unknown |
3820 | iexplore.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
onedrive.live.com |
| shared |
p.sfx.ms |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
iecvlist.microsoft.com |
| whitelisted |
r20swj13mr.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
ajax.aspnetcdn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
864 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
560 | chrome.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Downloading from a file sharing service is observed |
560 | chrome.exe | Potential Corporate Privacy Violation | POLICY [ANY.RUN] Downloading from a file sharing service is observed |