| URL: | https://drive.google.com/uc?id=1SUwCgmd6jhwI0yHwMaKU8vyWvniP_E99&export=download |
| Full analysis: | https://app.any.run/tasks/cf7245b9-0a99-447b-b4eb-c443f504432f |
| Verdict: | Malicious activity |
| Analysis date: | November 16, 2019, 14:12:35 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MD5: | 0503C0BAA5C1DD1B2196AD15432F4F72 |
| SHA1: | 43AF65E89D820F4946F6A24CB4C87F37E424C39D |
| SHA256: | ABAB5938A1E0B7563B38CEE29D1A1C8DF8A162AC17C7CFAEEB09F2B243722DDE |
| SSDEEP: | 3:N8PMMtZJu2NMuvnm1T1qOz0KdVKlM:2A2HvnCR9hdVK+ |
MALICIOUS
Loads dropped or rewritten executable
- regsvr32.exe (PID: 3508)
SUSPICIOUS
Creates files in the program directory
- firefox.exe (PID: 4044)
Executed via COM
- iexplore.exe (PID: 1788)
- iexplore.exe (PID: 3804)
- iexplore.exe (PID: 1992)
- iexplore.exe (PID: 1772)
- iexplore.exe (PID: 1584)
- iexplore.exe (PID: 2108)
- iexplore.exe (PID: 748)
- iexplore.exe (PID: 1536)
- iexplore.exe (PID: 620)
- iexplore.exe (PID: 3416)
Executed via WMI
- regsvr32.exe (PID: 3508)
Executable content was dropped or overwritten
- WScript.exe (PID: 2308)
INFO
Application launched itself
- firefox.exe (PID: 4044)
- iexplore.exe (PID: 1788)
- iexplore.exe (PID: 3804)
- iexplore.exe (PID: 1772)
- iexplore.exe (PID: 2108)
- iexplore.exe (PID: 748)
- iexplore.exe (PID: 620)
- iexplore.exe (PID: 3416)
Manual execution by user
- explorer.exe (PID: 3908)
- WScript.exe (PID: 2308)
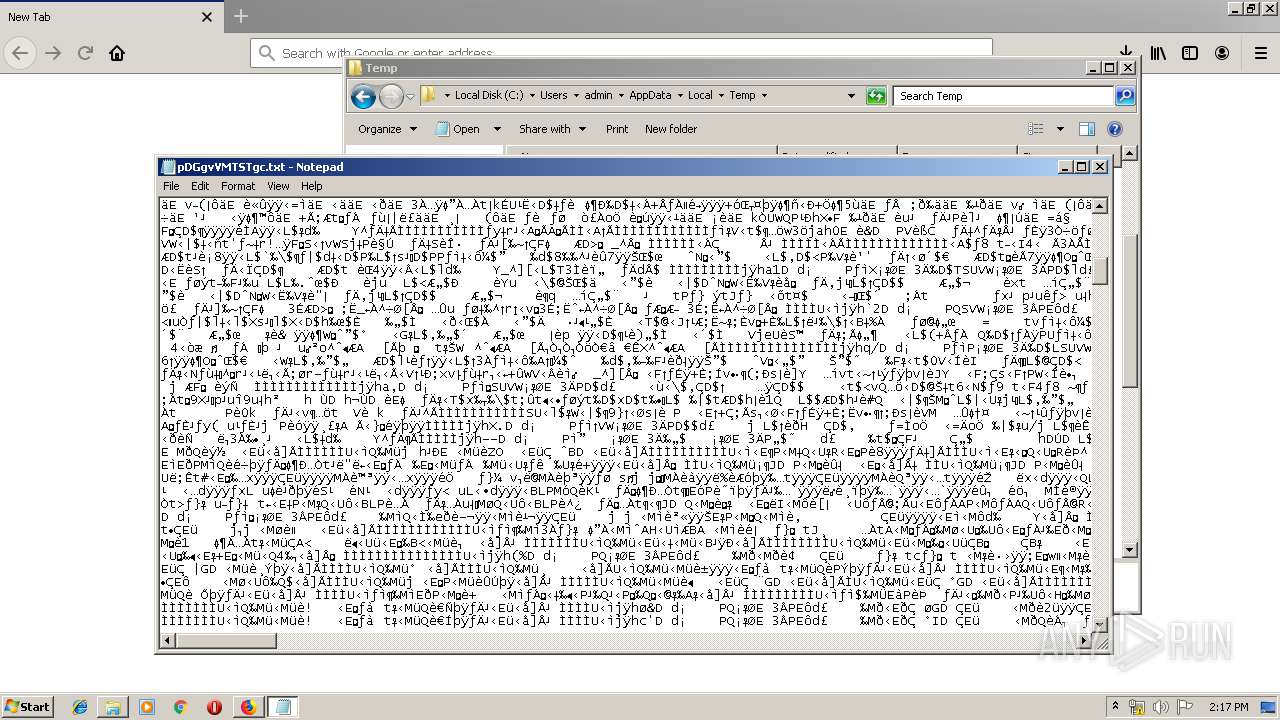
- NOTEPAD.EXE (PID: 2544)
- NOTEPAD.EXE (PID: 3500)
Changes internet zones settings
- iexplore.exe (PID: 1788)
- iexplore.exe (PID: 1992)
- iexplore.exe (PID: 3804)
- iexplore.exe (PID: 1772)
- iexplore.exe (PID: 1584)
- iexplore.exe (PID: 2108)
- iexplore.exe (PID: 748)
- iexplore.exe (PID: 620)
- iexplore.exe (PID: 3416)
- iexplore.exe (PID: 1536)
Reads the hosts file
- regsvr32.exe (PID: 3508)
Reads internet explorer settings
- iexplore.exe (PID: 3080)
- iexplore.exe (PID: 3244)
- iexplore.exe (PID: 3180)
- iexplore.exe (PID: 3836)
- iexplore.exe (PID: 3032)
- iexplore.exe (PID: 3296)
- iexplore.exe (PID: 2712)
- iexplore.exe (PID: 3700)
- iexplore.exe (PID: 2144)
- iexplore.exe (PID: 3476)
Creates files in the user directory
- firefox.exe (PID: 4044)
Reads Internet Cache Settings
- iexplore.exe (PID: 3244)
- iexplore.exe (PID: 3080)
- iexplore.exe (PID: 3180)
- iexplore.exe (PID: 3836)
- iexplore.exe (PID: 3032)
- iexplore.exe (PID: 3296)
- iexplore.exe (PID: 3700)
- iexplore.exe (PID: 2144)
- iexplore.exe (PID: 3476)
- iexplore.exe (PID: 2712)
Reads CPU info
- firefox.exe (PID: 4044)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
72
Monitored processes
32
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 620 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 640 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4044.3.697681666\1313555930" -childID 1 -isForBrowser -prefsHandle 1768 -prefMapHandle 1640 -prefsLen 1 -prefMapSize 191824 -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 4044 "\\.\pipe\gecko-crash-server-pipe.4044" 1788 tab | C:\Program Files\Mozilla Firefox\firefox.exe | firefox.exe | ||||||||||||
User: admin Company: Mozilla Corporation Integrity Level: LOW Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
| 748 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1028 | "C:\Program Files\Mozilla Firefox\firefox.exe" -contentproc --channel="4044.0.43858104\646726711" -parentBuildID 20190717172542 -greomni "C:\Program Files\Mozilla Firefox\omni.ja" -appomni "C:\Program Files\Mozilla Firefox\browser\omni.ja" -appdir "C:\Program Files\Mozilla Firefox\browser" - 4044 "\\.\pipe\gecko-crash-server-pipe.4044" 1176 gpu | C:\Program Files\Mozilla Firefox\firefox.exe | — | firefox.exe | |||||||||||
User: admin Company: Mozilla Corporation Integrity Level: MEDIUM Description: Firefox Exit code: 0 Version: 68.0.1 Modules
| |||||||||||||||
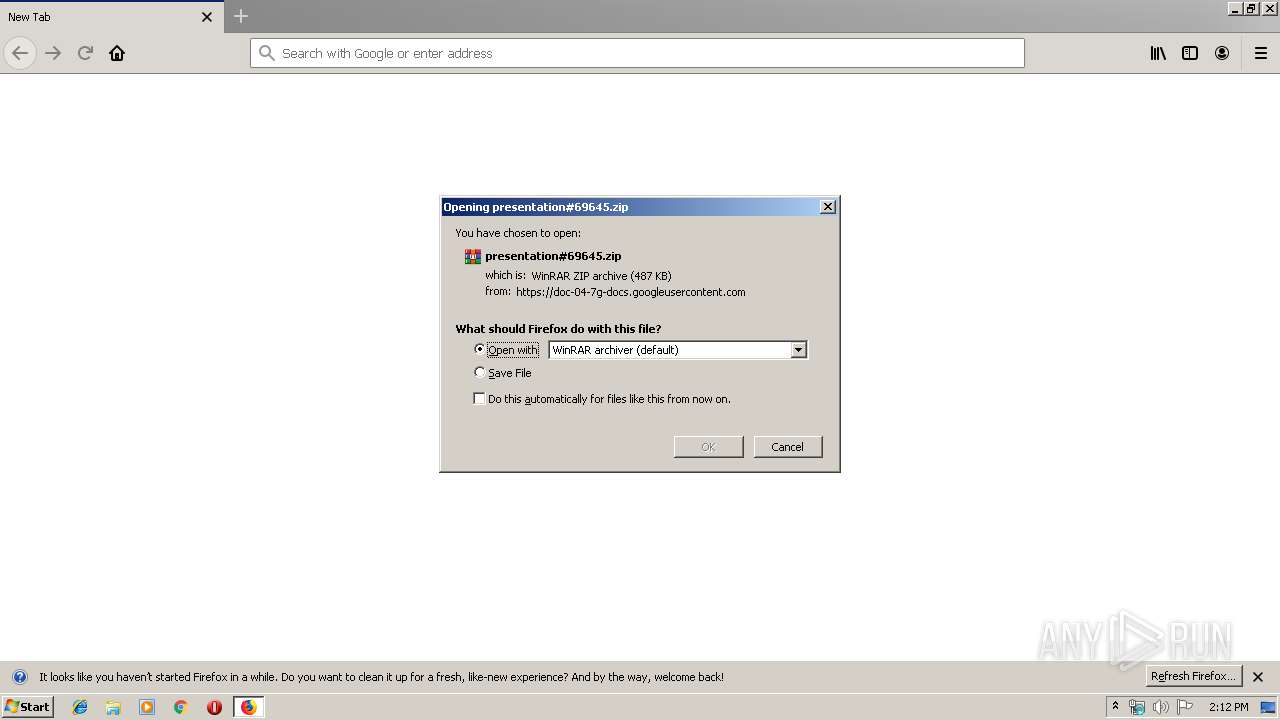
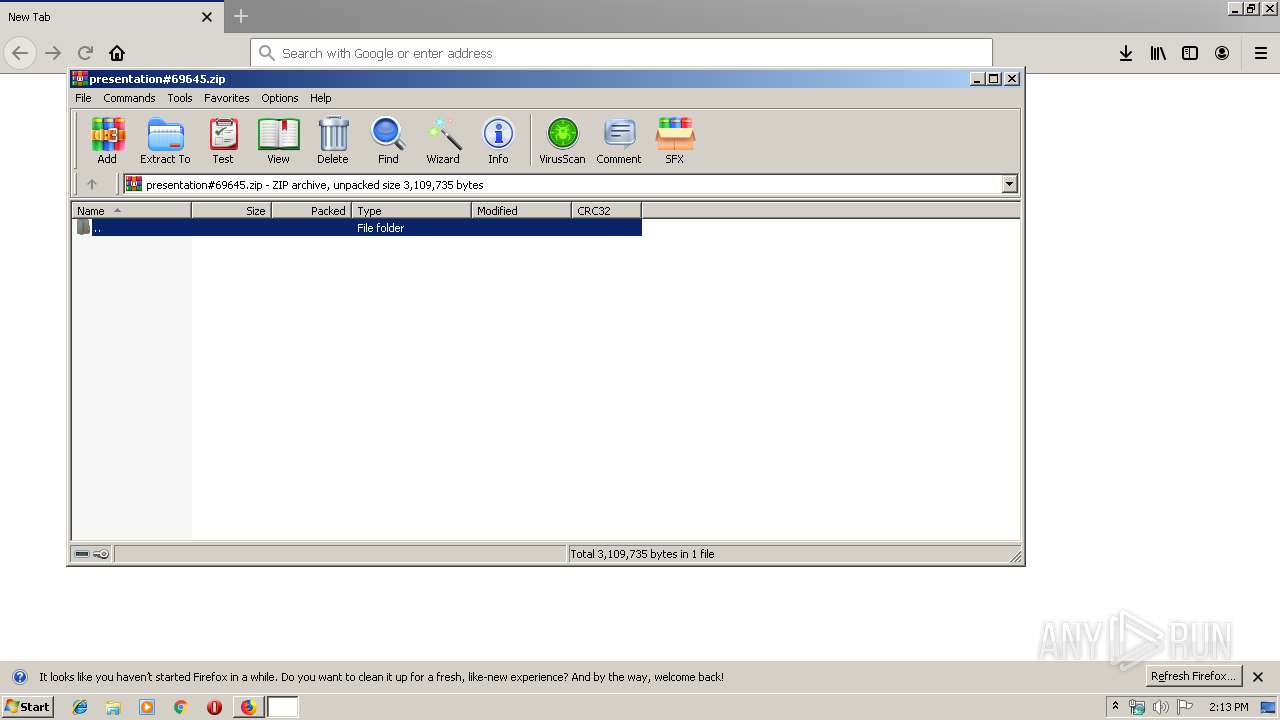
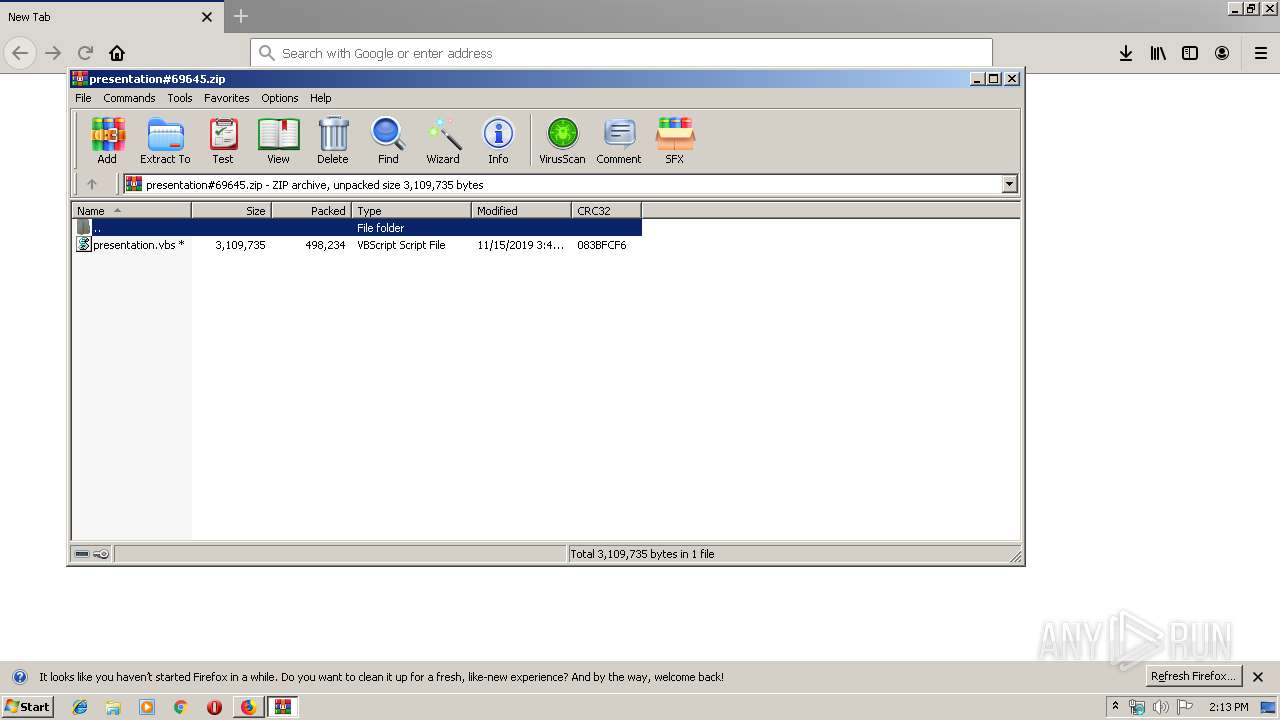
| 1324 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Downloads\presentation#69645.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | firefox.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1536 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1584 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1772 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1788 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1992 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 1 Version: 8.00.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
5 028
Read events
4 614
Write events
404
Delete events
10
Modification events
| (PID) Process: | (4044) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Browser |
Value: 6122041803000000 | |||
| (PID) Process: | (2172) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Launcher |
Value: ABB7001803000000 | |||
| (PID) Process: | (4044) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Mozilla\Firefox\Launcher |
| Operation: | write | Name: | C:\Program Files\Mozilla Firefox\firefox.exe|Telemetry |
Value: 1 | |||
| (PID) Process: | (4044) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings |
| Operation: | write | Name: | ProxyEnable |
Value: 0 | |||
| (PID) Process: | (4044) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\Connections |
| Operation: | write | Name: | SavedLegacySettings |
Value: 4600000092000000010000000000000000000000000000000000000000000000C0E333BBEAB1D301000000000000000000000000020000001700000000000000FE800000000000007D6CB050D9C573F70B000000000000006D00330032005C004D00530049004D004700330032002E0064006C000100000004AA400014AA4000040000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000002000000C0A8016400000000000000000000000000000000000000000800000000000000805D3F00983740000008000002000000000000600000002060040000B8A94000020000008802000060040000B8A9400004000000F8010000B284000088B64000B84B400043003A000000000000000000000000000000000000000000 | |||
| (PID) Process: | (4044) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (4044) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (4044) firefox.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.zip\OpenWithProgids |
| Operation: | write | Name: | WinRAR.ZIP |
Value: | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (1324) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
Executable files
1
Suspicious files
72
Text files
47
Unknown types
50
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 4044 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\startupCache\scriptCache-current.bin | — | |
MD5:— | SHA256:— | |||
| 4044 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\cookies.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 4044 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\prefs-1.js | — | |
MD5:— | SHA256:— | |||
| 4044 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\sessionCheckpoints.json.tmp | — | |
MD5:— | SHA256:— | |||
| 4044 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\2918063365piupsah.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 4044 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\storage\permanent\chrome\idb\1451318868ntouromlalnodry--epcr.sqlite-shm | — | |
MD5:— | SHA256:— | |||
| 4044 | firefox.exe | C:\Users\admin\AppData\Roaming\Mozilla\Firefox\Profiles\qldyz51w.default\search.json.mozlz4.tmp | — | |
MD5:— | SHA256:— | |||
| 4044 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\base-track-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
| 4044 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\block-flash-digest256.pset | — | |
MD5:— | SHA256:— | |||
| 4044 | firefox.exe | C:\Users\admin\AppData\Local\Mozilla\Firefox\Profiles\qldyz51w.default\safebrowsing-updating\block-flash-digest256.sbstore | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
20
TCP/UDP connections
41
DNS requests
83
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
4044 | firefox.exe | POST | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1 | US | der | 472 b | whitelisted |
4044 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4044 | firefox.exe | POST | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
4044 | firefox.exe | POST | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
4044 | firefox.exe | POST | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1 | US | der | 471 b | whitelisted |
4044 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4044 | firefox.exe | GET | 200 | 2.16.186.112:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
4044 | firefox.exe | POST | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/ | US | der | 471 b | whitelisted |
4044 | firefox.exe | GET | 200 | 2.16.186.112:80 | http://detectportal.firefox.com/success.txt | unknown | text | 8 b | whitelisted |
3836 | iexplore.exe | GET | 404 | 5.53.124.190:80 | http://w8.wensa.at/api1/uN0MyLT9fTA_/2BFS_2BJQOB/3ovz_2Bjgdl_2B/MP941orIpiH0Tmc_2BswJ/fLQoiQ53mUeYcaf8/3WBDyxn7vGRhZKI/EjdfVvIKNFRCkirApg/eSxXE27vC/H9j2oeB61KWLWlndEMet/Wp_2BzFbI_2FKrfiyUv/xJZvmPqpxV3lq3mF_2FZMS/_2FyOdgnL82hi/pzZXwmnY/gwsvtayBF6z2jdOHtyRQGOO/tpxKgyGALT/_2Bo69U7x_2FeP46Y/J3wBhz44rsFp/fCRo0ld0rMF/Jzr_0A_0Dquynp/3UCrj54SZGyC2mMaQY/djw | RU | html | 167 b | malicious |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4044 | firefox.exe | 52.89.218.39:443 | search.services.mozilla.com | Amazon.com, Inc. | US | unknown |
4044 | firefox.exe | 2.16.186.112:80 | detectportal.firefox.com | Akamai International B.V. | — | whitelisted |
4044 | firefox.exe | 52.35.84.106:443 | push.services.mozilla.com | Amazon.com, Inc. | US | malicious |
4044 | firefox.exe | 35.162.117.80:443 | tiles.services.mozilla.com | Amazon.com, Inc. | US | unknown |
4044 | firefox.exe | 143.204.214.5:443 | snippets.cdn.mozilla.net | — | US | malicious |
4044 | firefox.exe | 172.217.18.174:443 | drive.google.com | Google Inc. | US | whitelisted |
4044 | firefox.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
4044 | firefox.exe | 216.58.206.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
4044 | firefox.exe | 172.217.18.170:443 | safebrowsing.googleapis.com | Google Inc. | US | whitelisted |
4044 | firefox.exe | 143.204.214.45:443 | firefox.settings.services.mozilla.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
detectportal.firefox.com |
| whitelisted |
a1089.dscd.akamai.net |
| whitelisted |
search.services.mozilla.com |
| whitelisted |
search.r53-2.services.mozilla.com |
| whitelisted |
push.services.mozilla.com |
| whitelisted |
autopush.prod.mozaws.net |
| whitelisted |
snippets.cdn.mozilla.net |
| whitelisted |
d228z91au11ukj.cloudfront.net |
| whitelisted |
tiles.services.mozilla.com |
| whitelisted |
tiles.r53-2.services.mozilla.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |
1080 | svchost.exe | Potentially Bad Traffic | ET INFO Observed DNS Query to .cloud TLD |