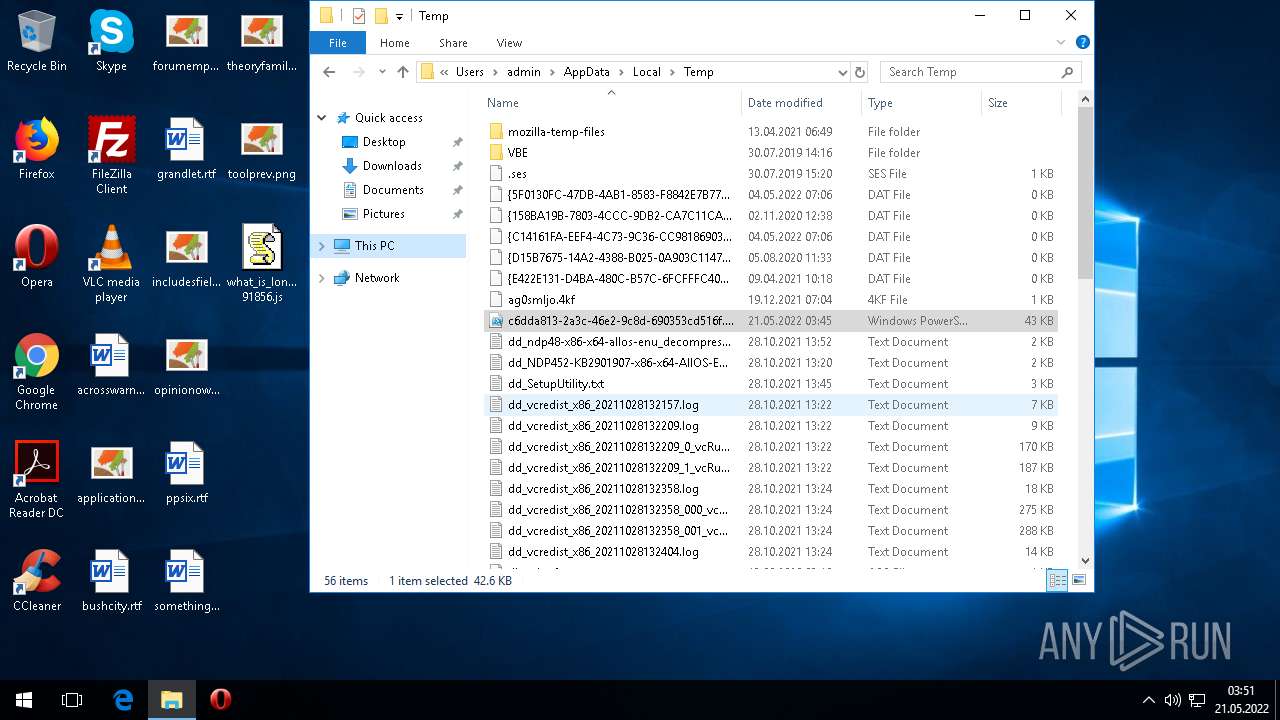
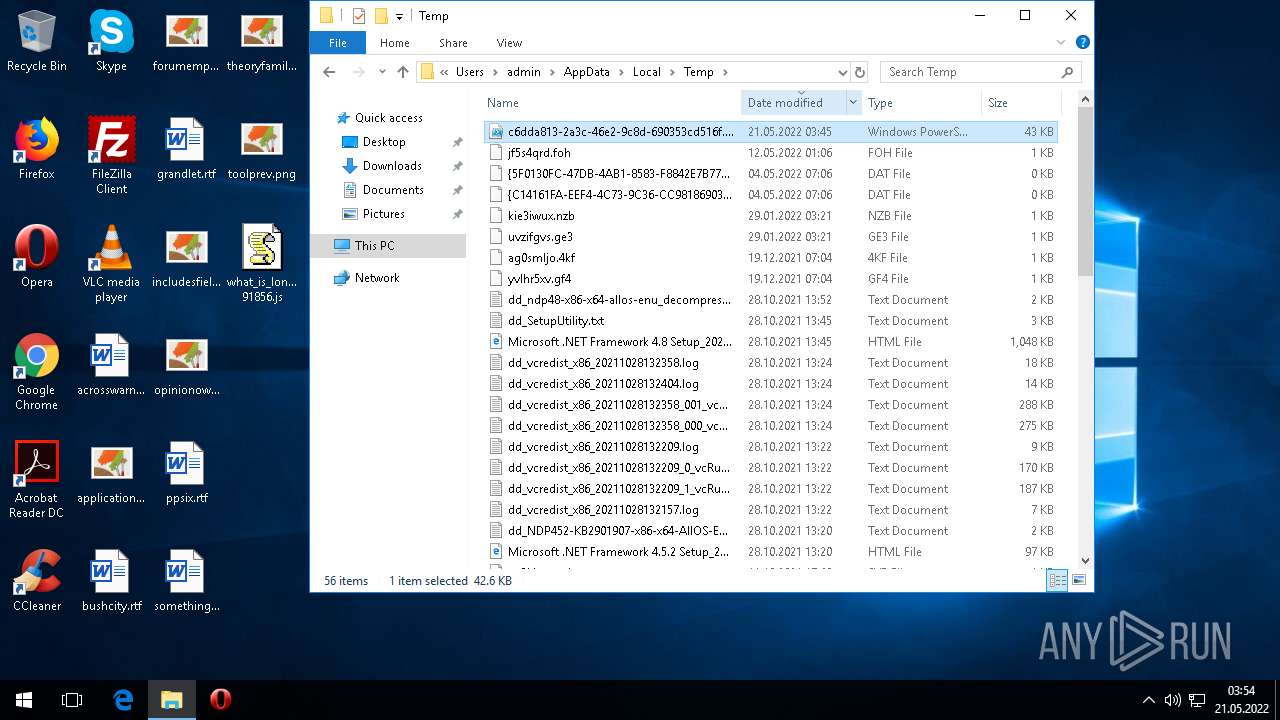
| File name: | what is long stop date in a contract(50123).zip |
| Full analysis: | https://app.any.run/tasks/198502ef-f4b4-4f3b-8fba-b7cb477865d6 |
| Verdict: | Malicious activity |
| Analysis date: | May 21, 2022, 03:46:57 |
| OS: | Windows 10 Professional (build: 16299, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract |
| MD5: | 631F5FD55CACB7D31FE915D35A9FD657 |
| SHA1: | 9E6DE102E3D63BBC42EAF2B414601A9C5A981EF4 |
| SHA256: | AB9A1B589EF81C2855D16F3B63DDDDD90D05D2DFD8CF2EEE79BD11B3330CEBE9 |
| SSDEEP: | 1536:bZnxS4G8k2PL9646ivJzvQ1fvf/gO/T+iyqcpqhUocwdC0SNSu9dT+D0Ln0:bRxS4M2PhJtvCfvf/gk+qiswSuDT+m0 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Checks supported languages
- WinRAR.exe (PID: 3968)
- SDXHelper.exe (PID: 304)
- WScript.exe (PID: 960)
- notepad++.exe (PID: 1604)
- WinRAR.exe (PID: 972)
- gup.exe (PID: 1360)
- conhost.exe (PID: 404)
- powershell.exe (PID: 304)
- WinRAR.exe (PID: 1312)
- notepad++.exe (PID: 2568)
Reads the computer name
- WinRAR.exe (PID: 3968)
- SDXHelper.exe (PID: 304)
- WScript.exe (PID: 960)
- notepad++.exe (PID: 1604)
- gup.exe (PID: 1360)
- WinRAR.exe (PID: 972)
- conhost.exe (PID: 404)
- powershell.exe (PID: 304)
- WinRAR.exe (PID: 1312)
- notepad++.exe (PID: 2568)
Executed via COM
- SDXHelper.exe (PID: 304)
- rundll32.exe (PID: 3776)
Reads CPU info
- SDXHelper.exe (PID: 304)
Reads the date of Windows installation
- taskmgr.exe (PID: 260)
- powershell.exe (PID: 304)
Executes PowerShell scripts
- WinRAR.exe (PID: 972)
Creates files in the user directory
- notepad++.exe (PID: 1604)
- powershell.exe (PID: 304)
INFO
Reads settings of System Certificates
- SDXHelper.exe (PID: 304)
- WScript.exe (PID: 960)
- powershell.exe (PID: 304)
Manual execution by user
- WScript.exe (PID: 960)
- taskmgr.exe (PID: 2884)
- taskmgr.exe (PID: 260)
- WinRAR.exe (PID: 972)
- notepad++.exe (PID: 1604)
- notepad++.exe (PID: 2568)
- WinRAR.exe (PID: 1312)
Reads the software policy settings
- SDXHelper.exe (PID: 304)
- WScript.exe (PID: 960)
- powershell.exe (PID: 304)
Checks Windows Trust Settings
- WScript.exe (PID: 960)
- powershell.exe (PID: 304)
Reads the computer name
- taskmgr.exe (PID: 260)
Checks supported languages
- taskmgr.exe (PID: 260)
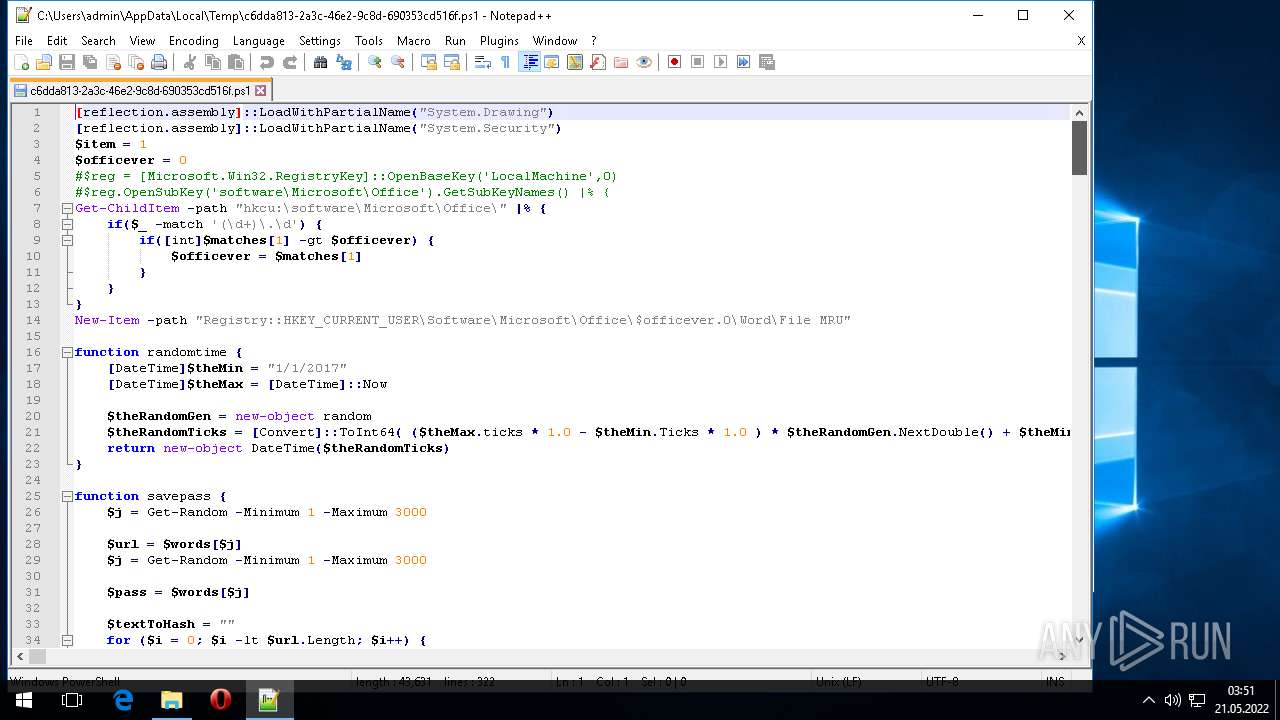
Reads Microsoft Office registry keys
- powershell.exe (PID: 304)
- SDXHelper.exe (PID: 304)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
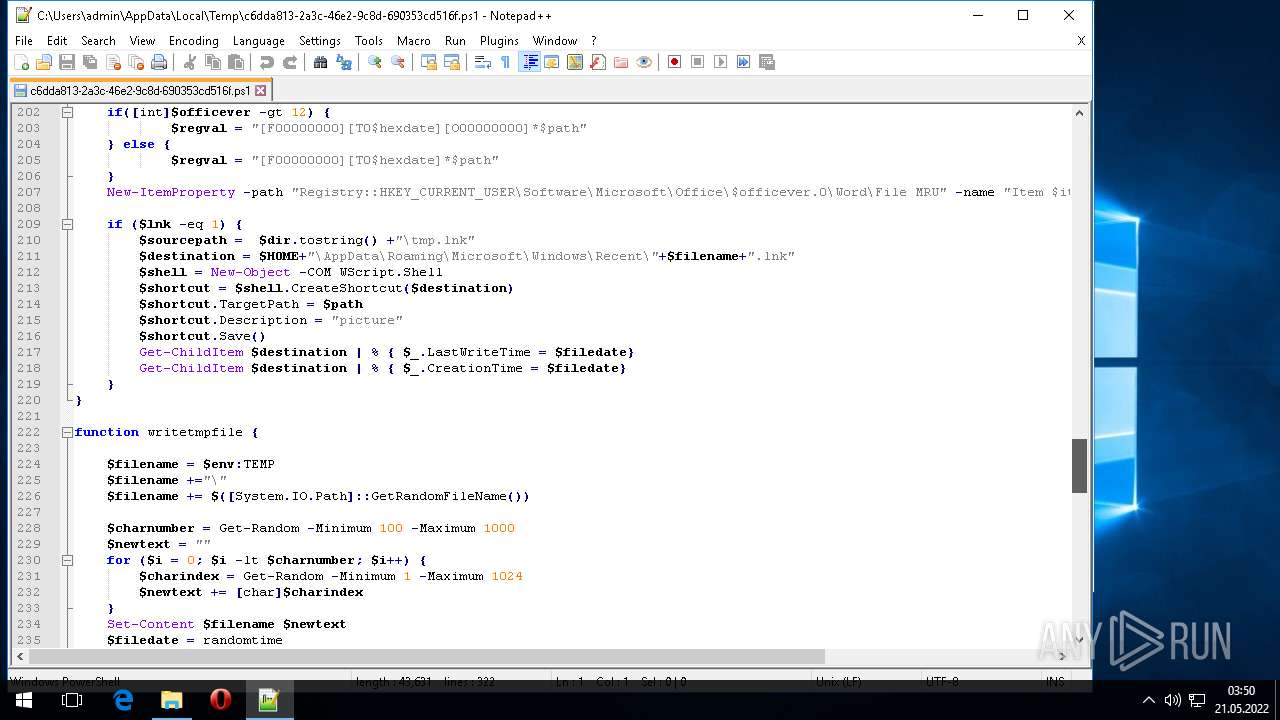
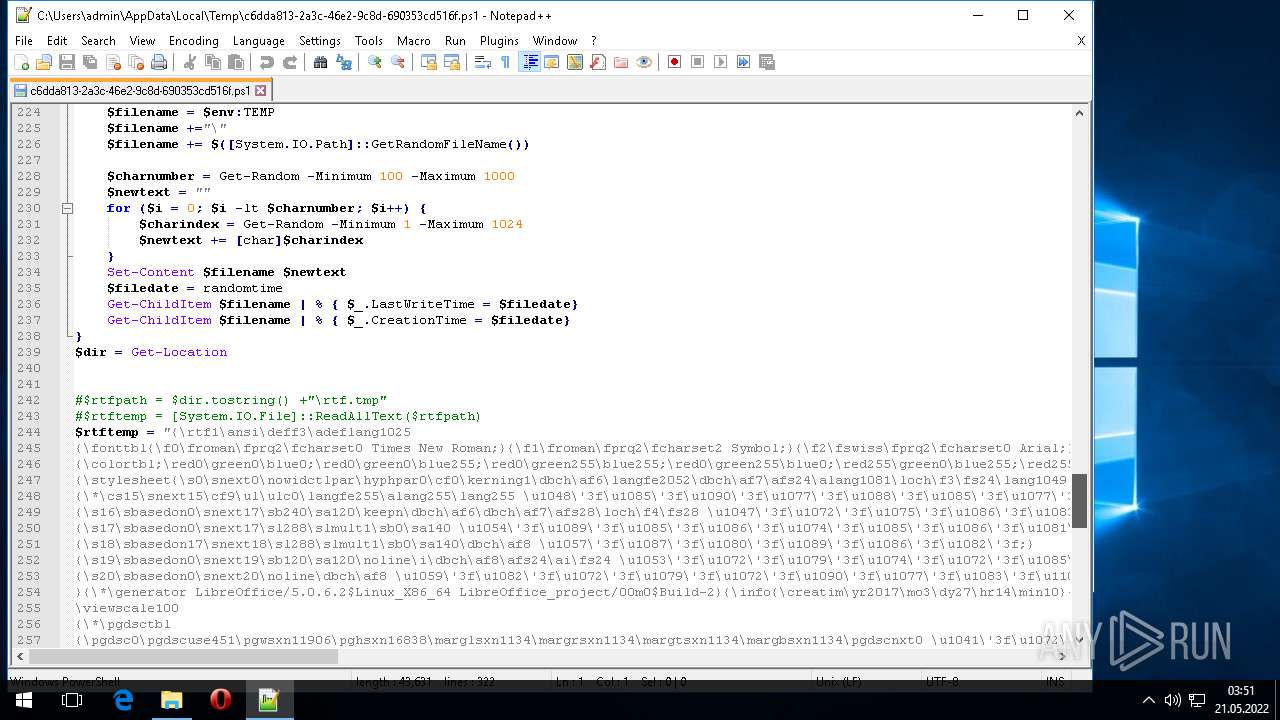
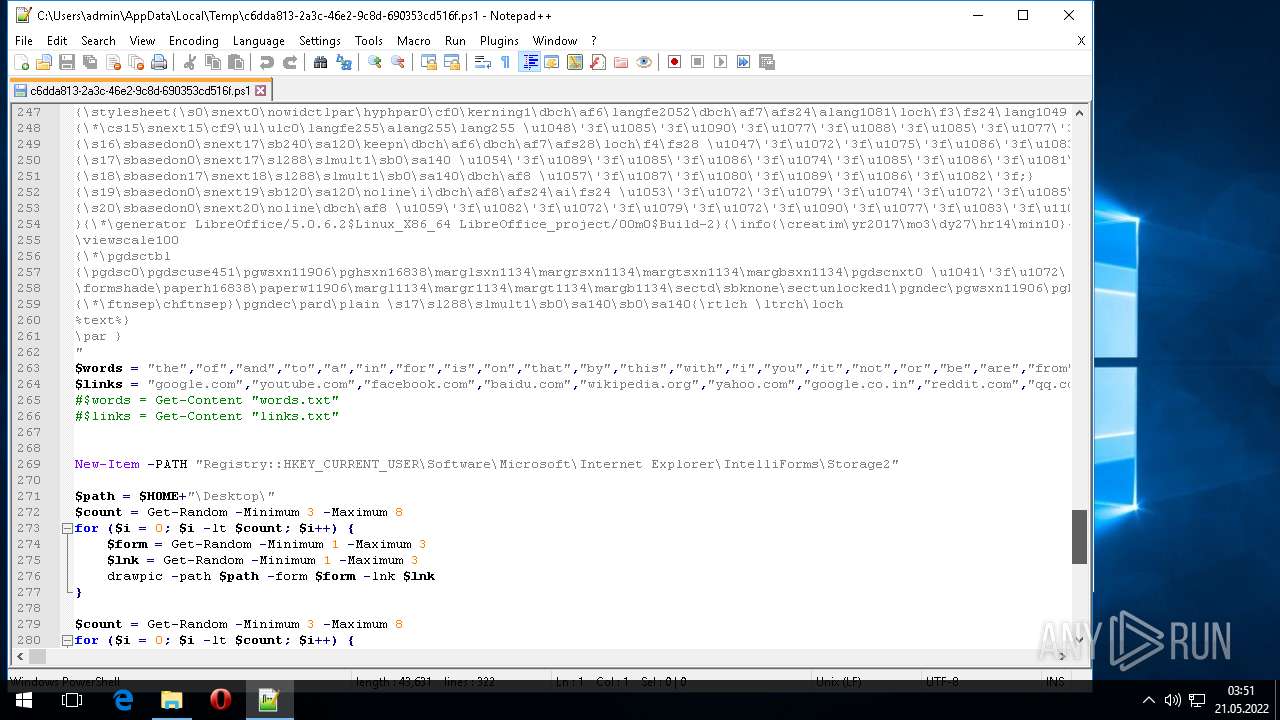
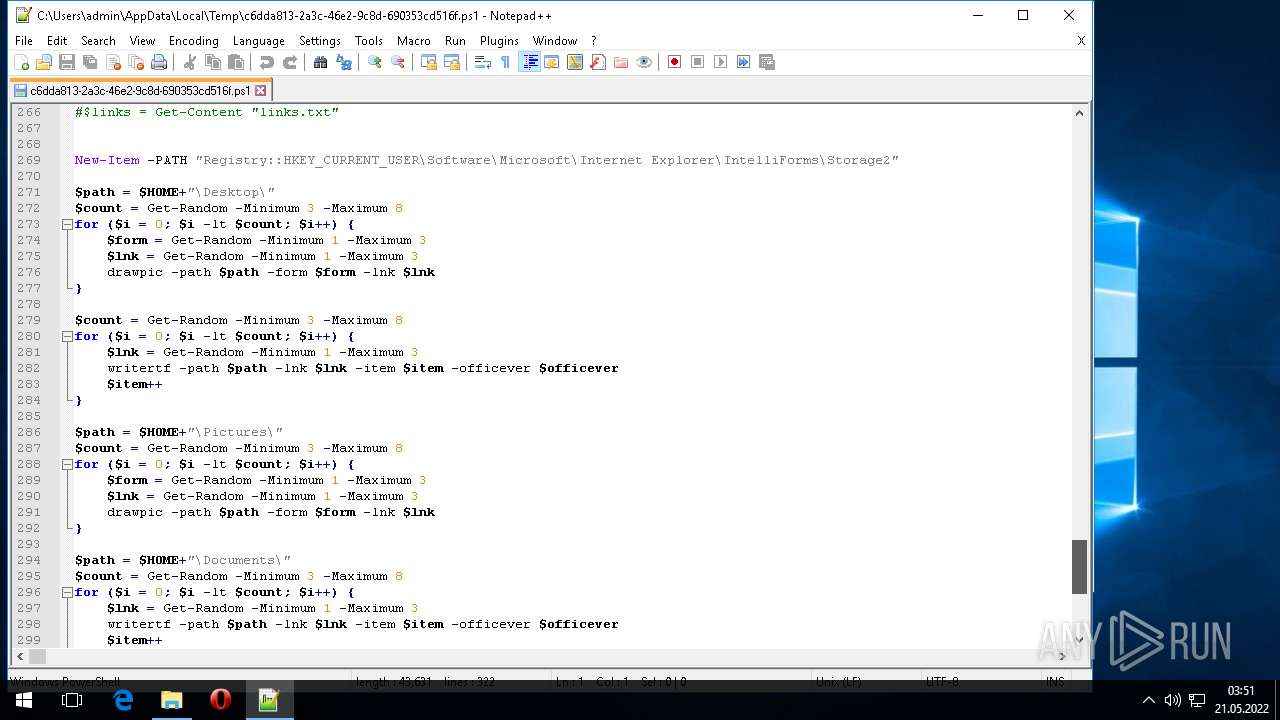
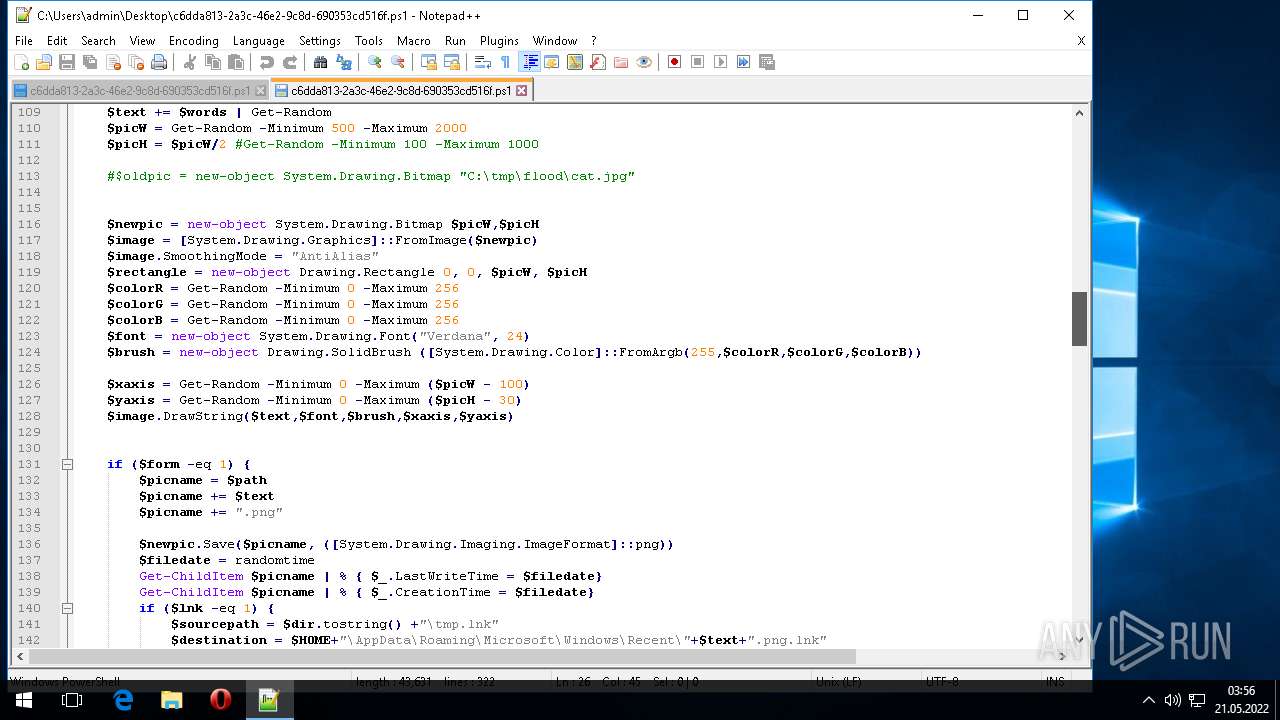
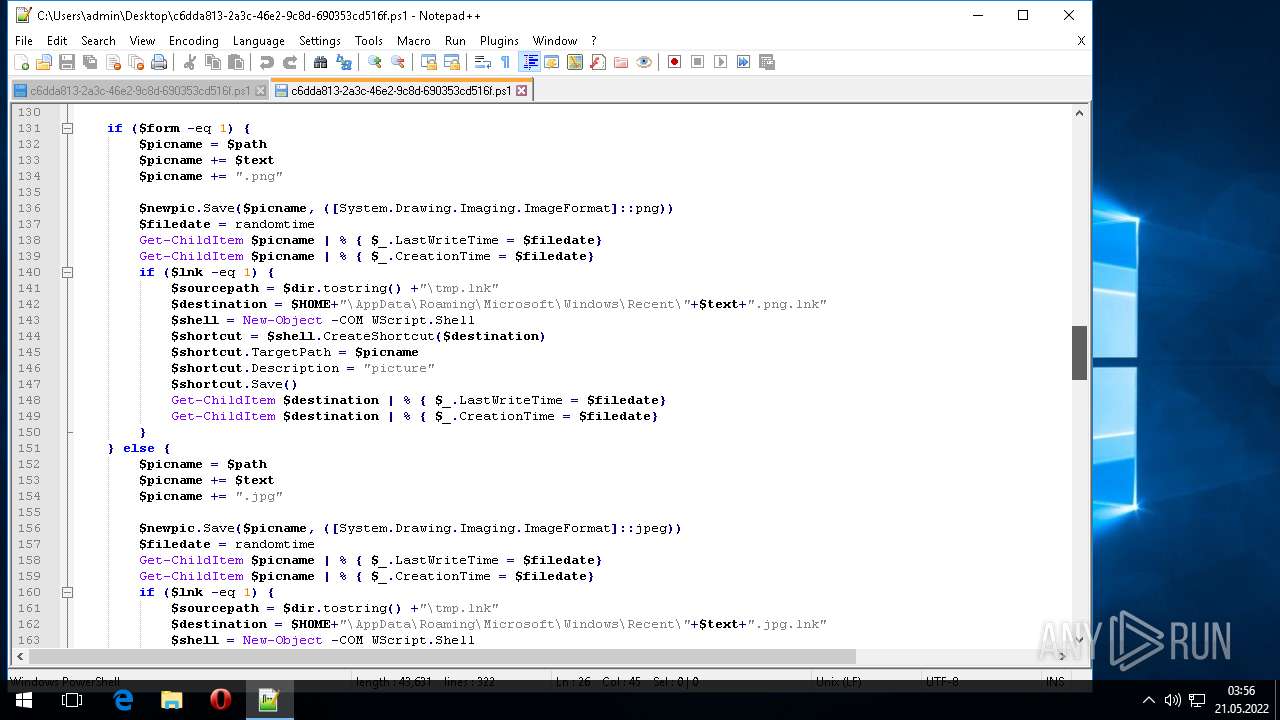
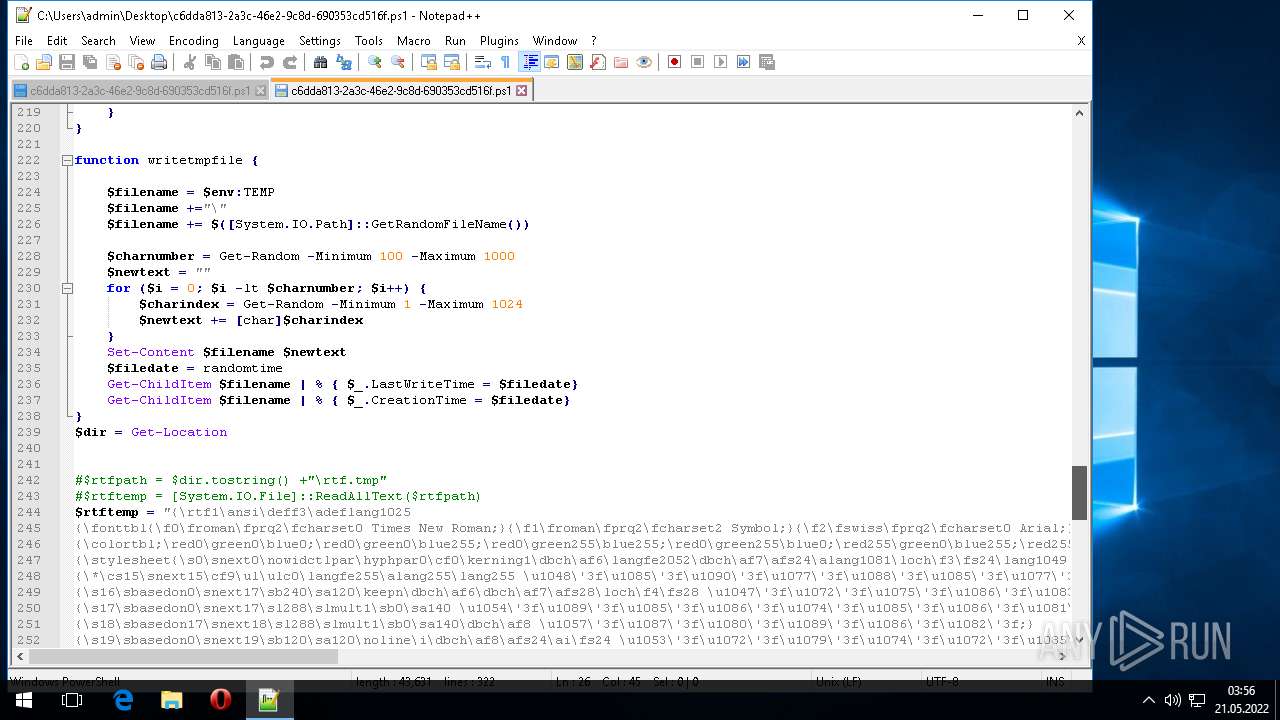
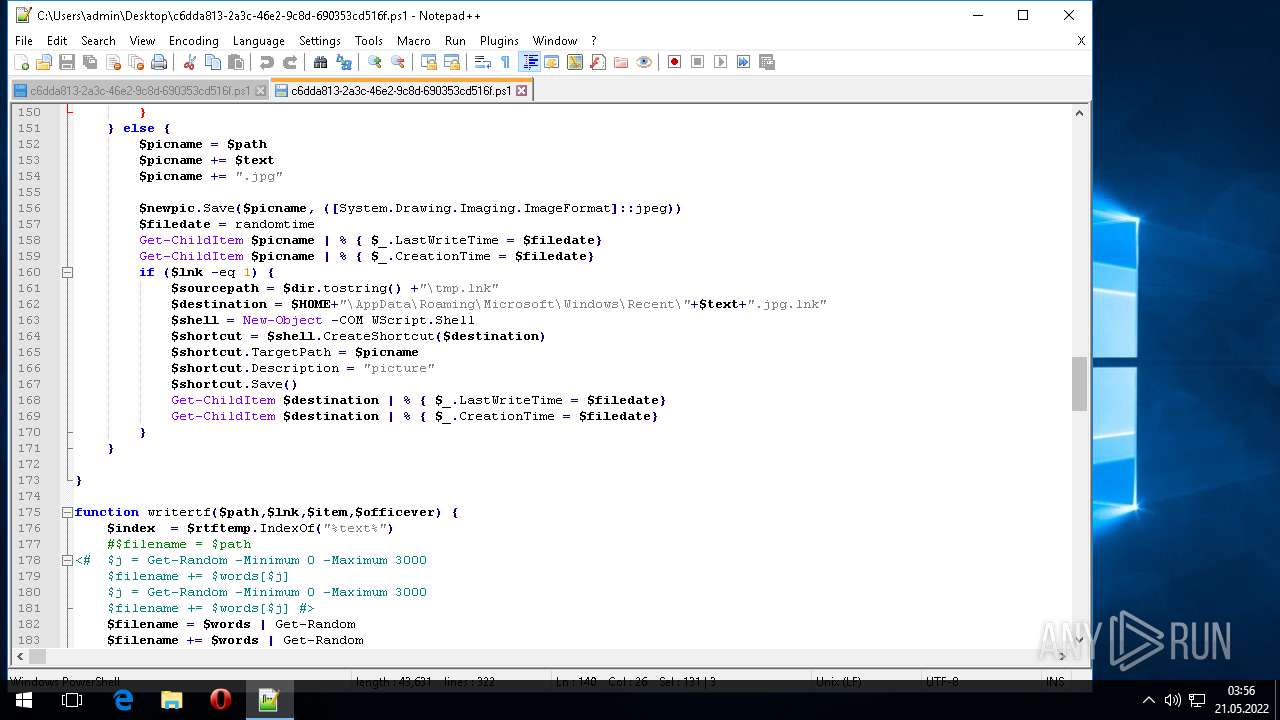
| ZipFileName: | what_is_long_stop_date_in_a_contract 91856.js |
|---|---|
| ZipUncompressedSize: | 293211 |
| ZipCompressedSize: | 87634 |
| ZipCRC: | 0x80ff9c5c |
| ZipModifyDate: | 2022:05:20 20:47:00 |
| ZipCompression: | Deflated |
| ZipBitFlag: | 0x0002 |
| ZipRequiredVersion: | 20 |
Total processes
67
Monitored processes
13
Malicious processes
1
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 260 | "C:\WINDOWS\system32\taskmgr.exe" /4 | C:\WINDOWS\system32\taskmgr.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Task Manager Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 304 | "C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX86\Microsoft Shared\OFFICE16\SDXHelper.exe" -Embedding | C:\Program Files\Microsoft Office\Root\VFS\ProgramFilesCommonX86\Microsoft Shared\OFFICE16\SDXHelper.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Office SDX Helper Exit code: 0 Version: 16.0.11929.20300 Modules
| |||||||||||||||
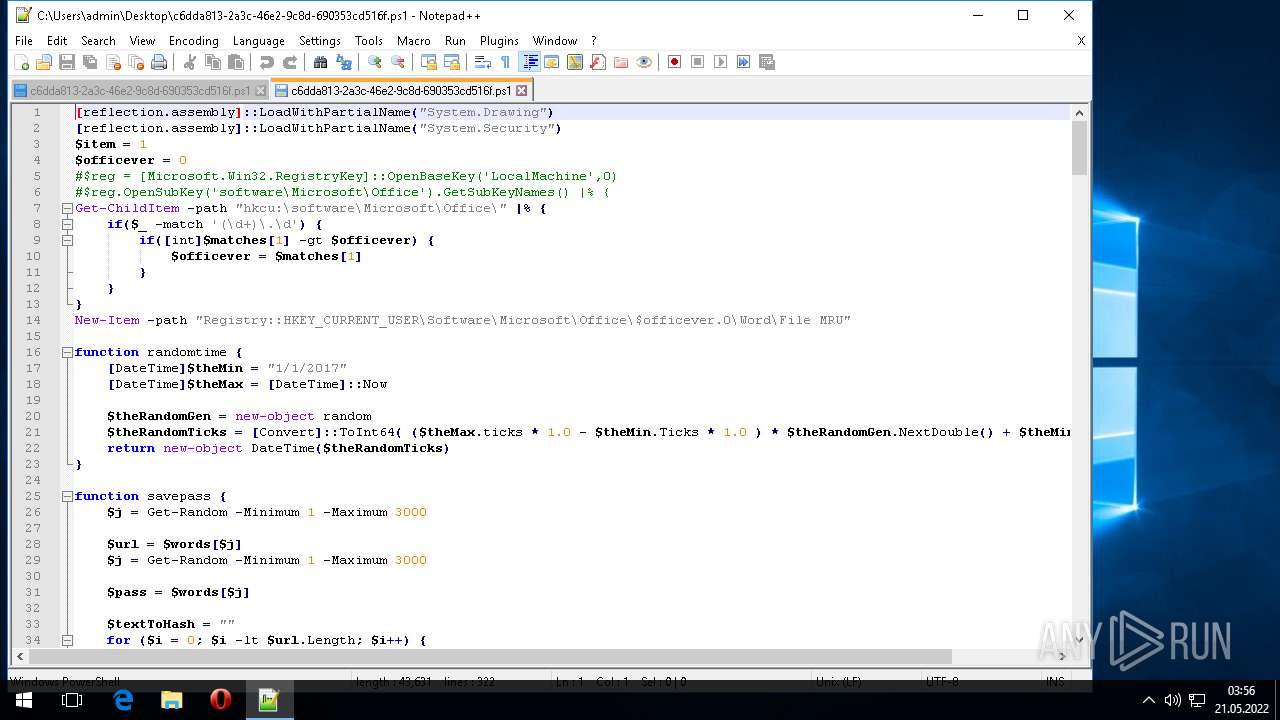
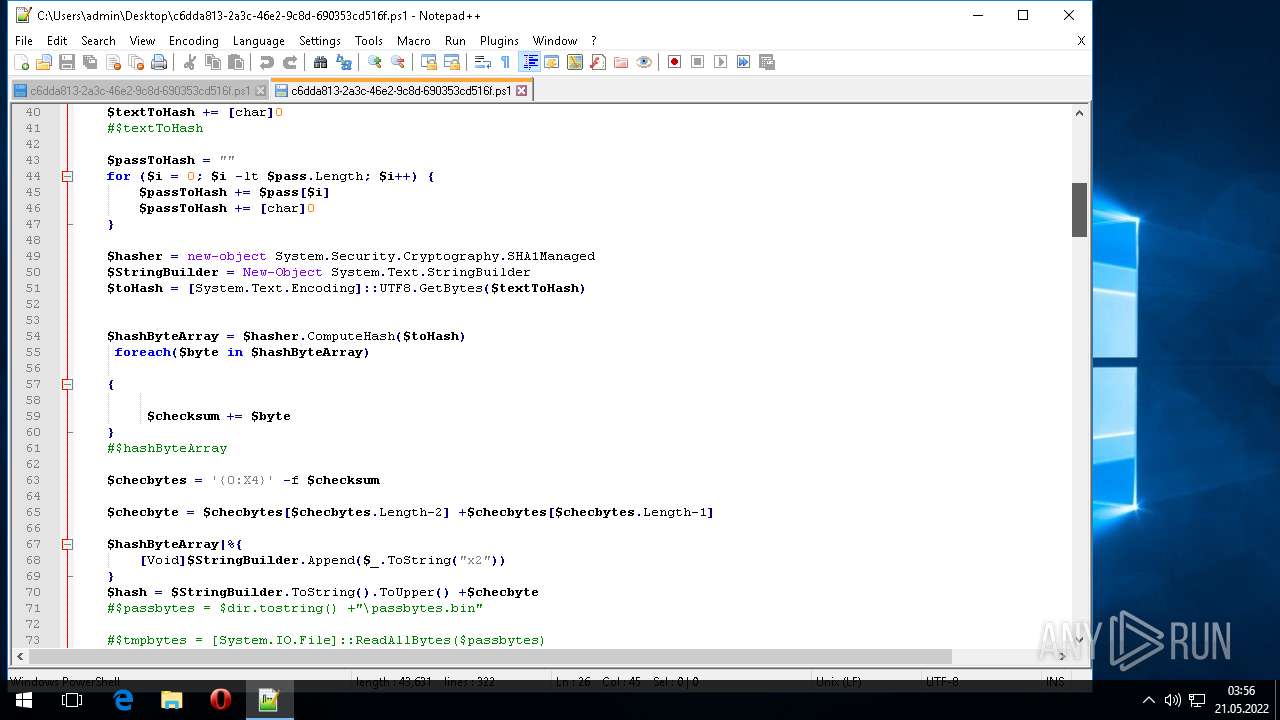
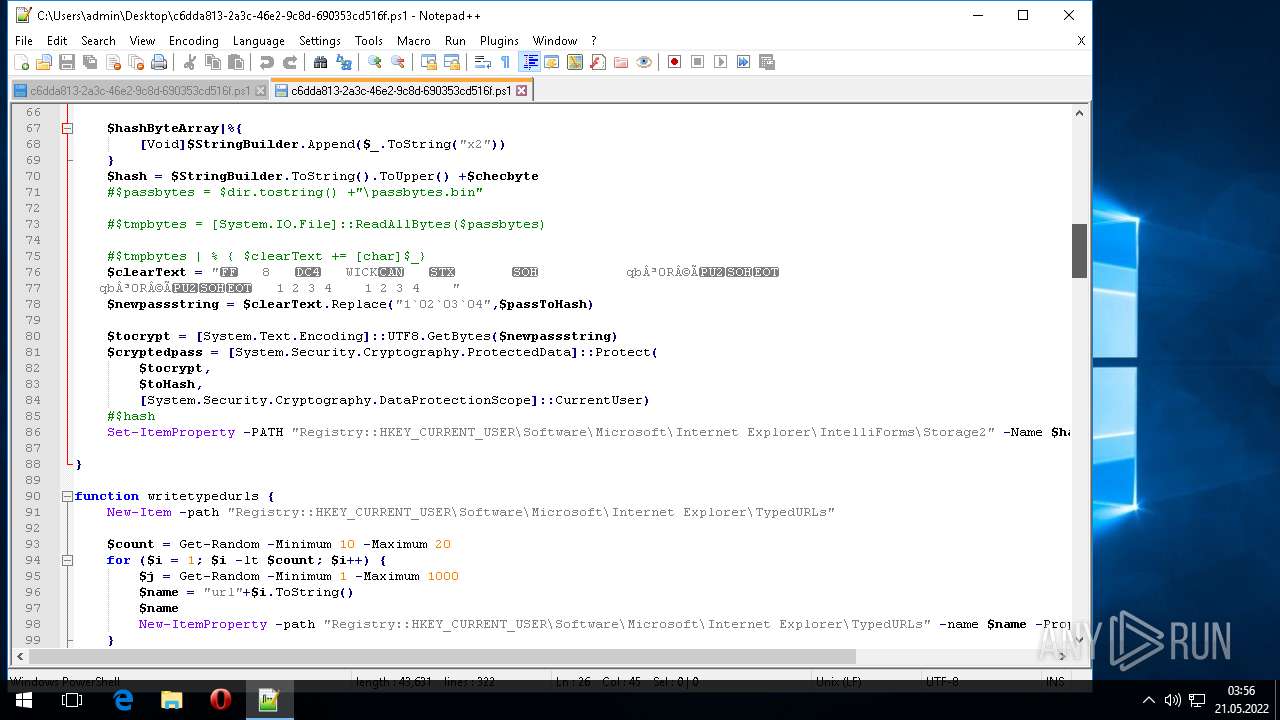
| 304 | "C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe" "-Command" "if((Get-ExecutionPolicy ) -ne 'AllSigned') { Set-ExecutionPolicy -Scope Process Bypass }; & 'C:\Users\admin\AppData\Local\Temp\Rar$DIa972.46921\c6dda813-2a3c-46e2-9c8d-690353cd516f.ps1'" | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | WinRAR.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 0 Version: 10.0.16299.15 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 404 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | \??\C:\WINDOWS\system32\conhost.exe | powershell.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Modules
| |||||||||||||||
| 960 | "C:\Windows\System32\WScript.exe" "C:\Users\admin\Desktop\what_is_long_stop_date_in_a_contract 91856.js" | C:\Windows\System32\WScript.exe | Explorer.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 972 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\c6dda813-2a3c-46e2-9c8d-690353cd516f.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1312 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\c6dda813-2a3c-46e2-9c8d-690353cd516f.zip" C:\Users\admin\Desktop\ | C:\Program Files\WinRAR\WinRAR.exe | — | Explorer.EXE | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.60.0 Modules
| |||||||||||||||
| 1360 | "C:\Program Files\Notepad++\updater\gup.exe" -v7.51 | C:\Program Files\Notepad++\updater\gup.exe | notepad++.exe | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: GUP : a free (LGPL) Generic Updater Exit code: 0 Version: 4.1 Modules
| |||||||||||||||
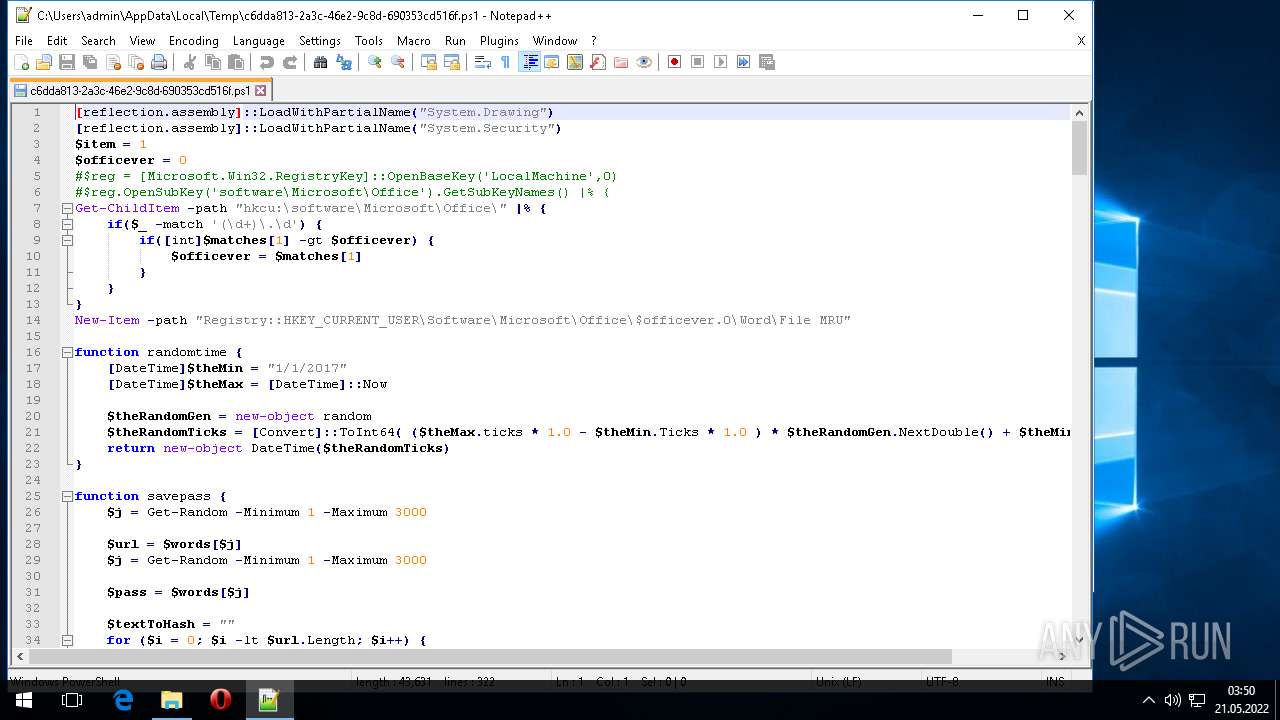
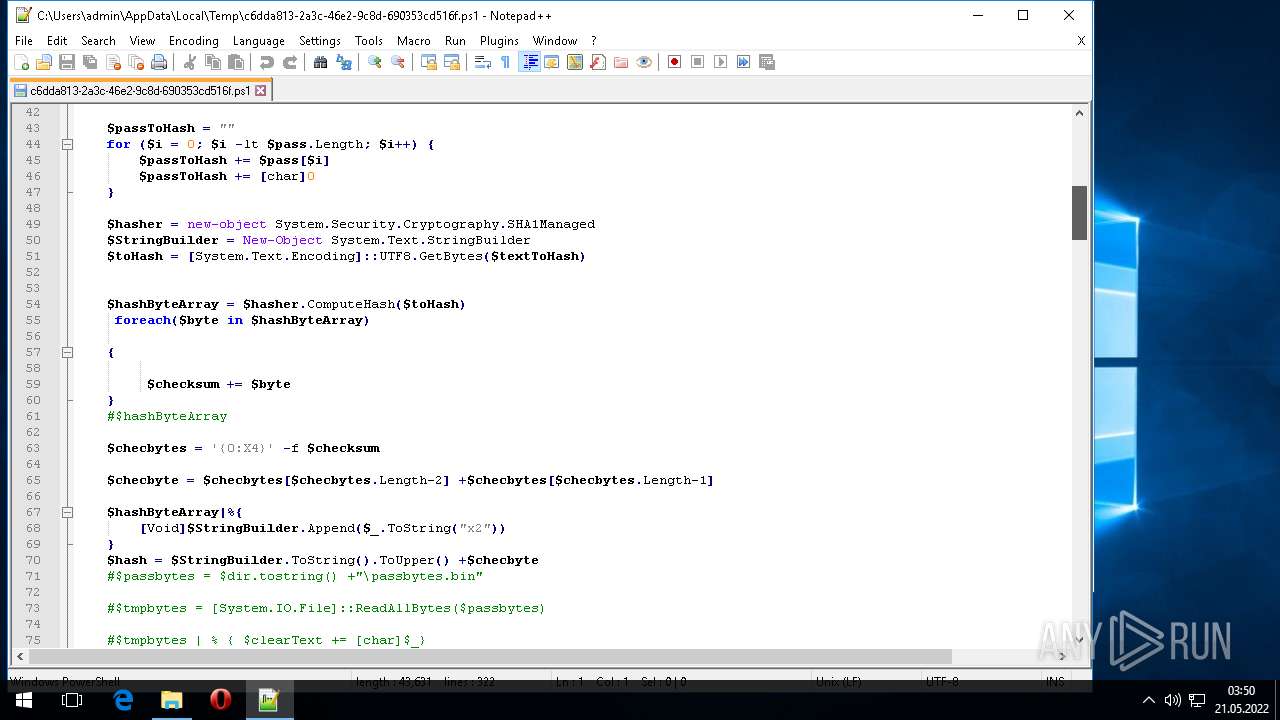
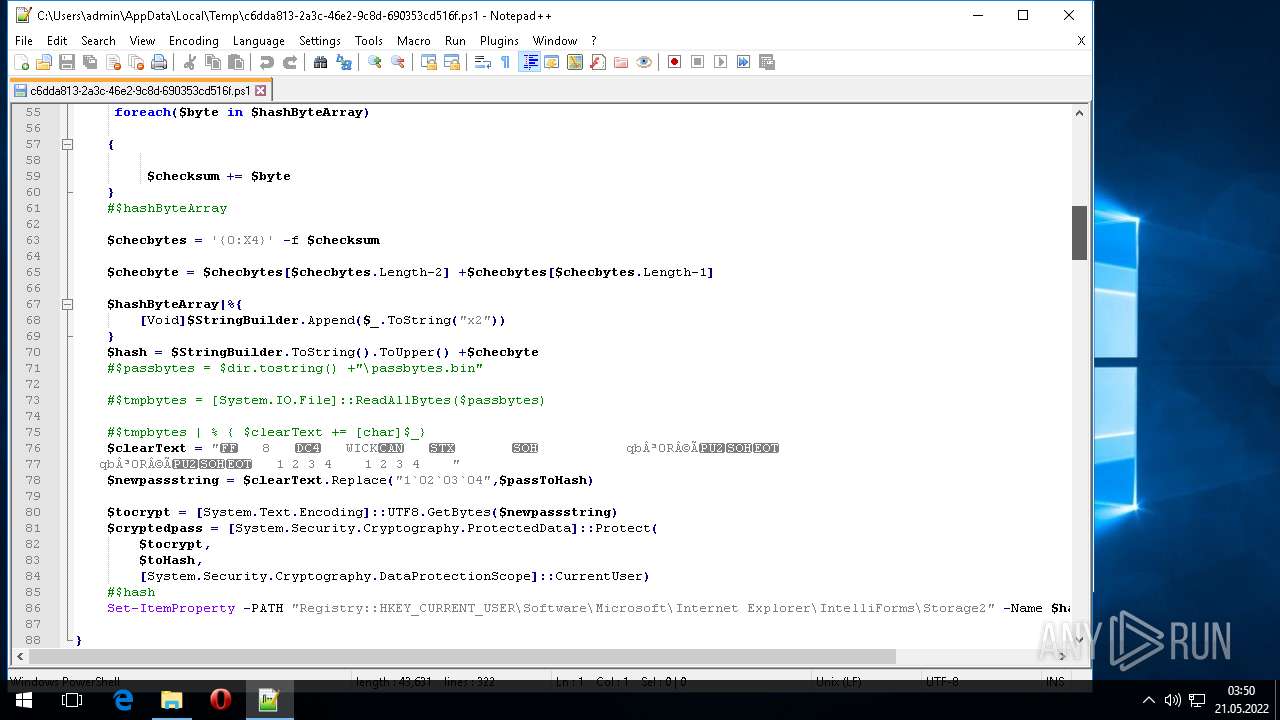
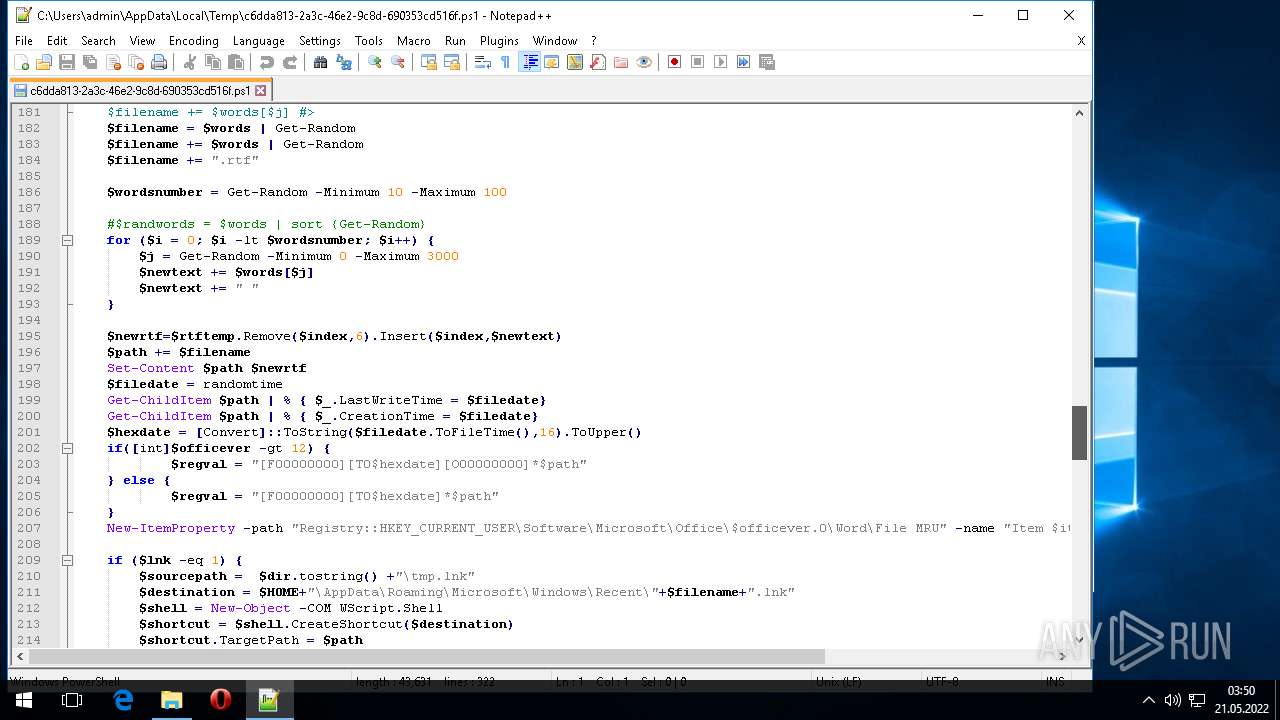
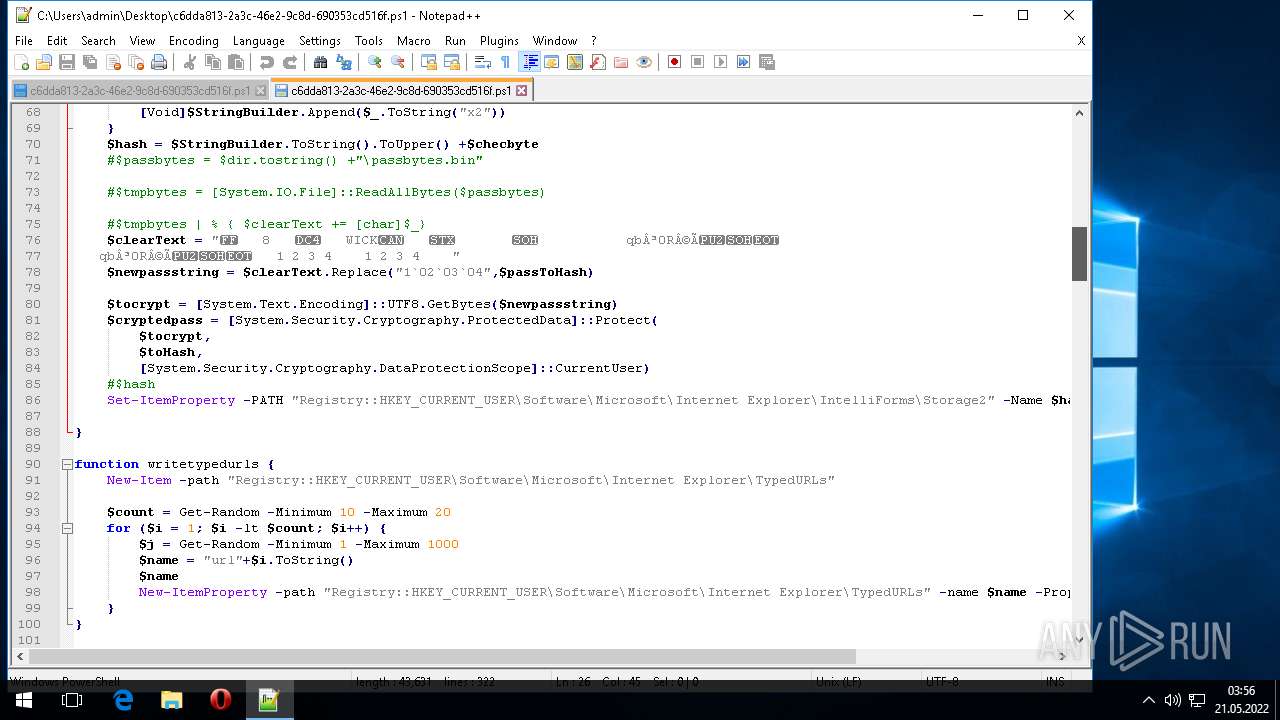
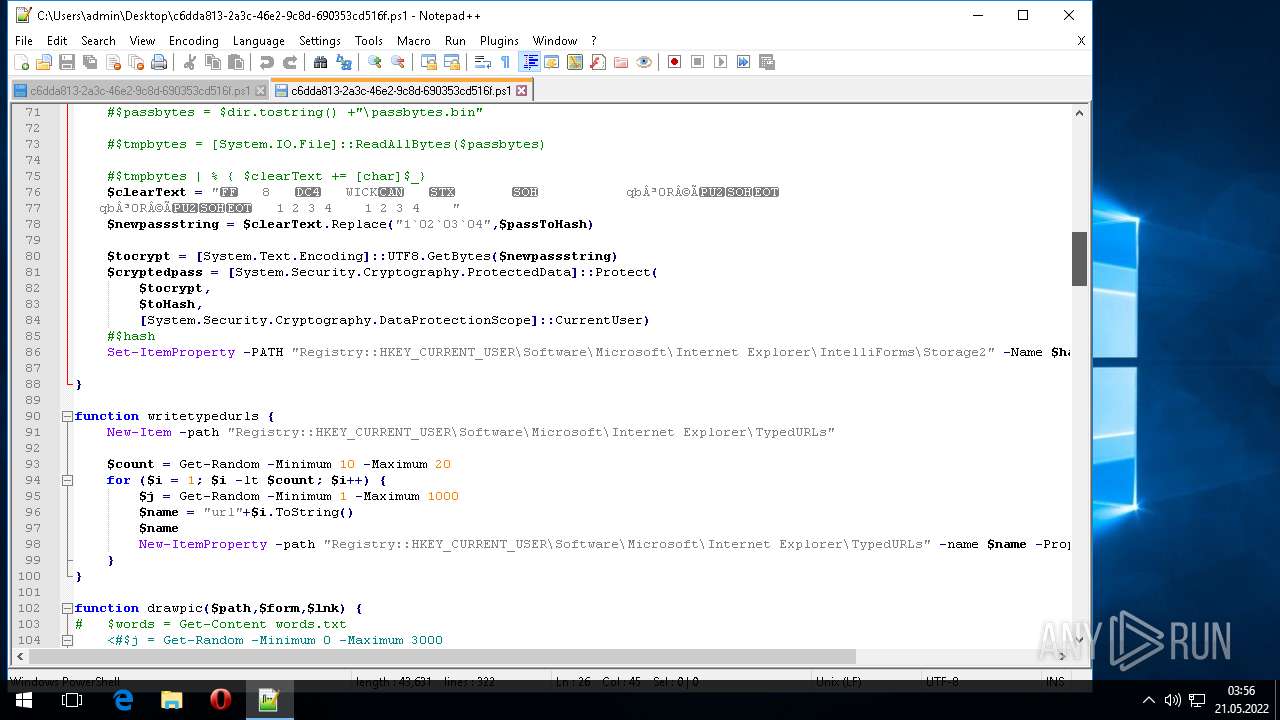
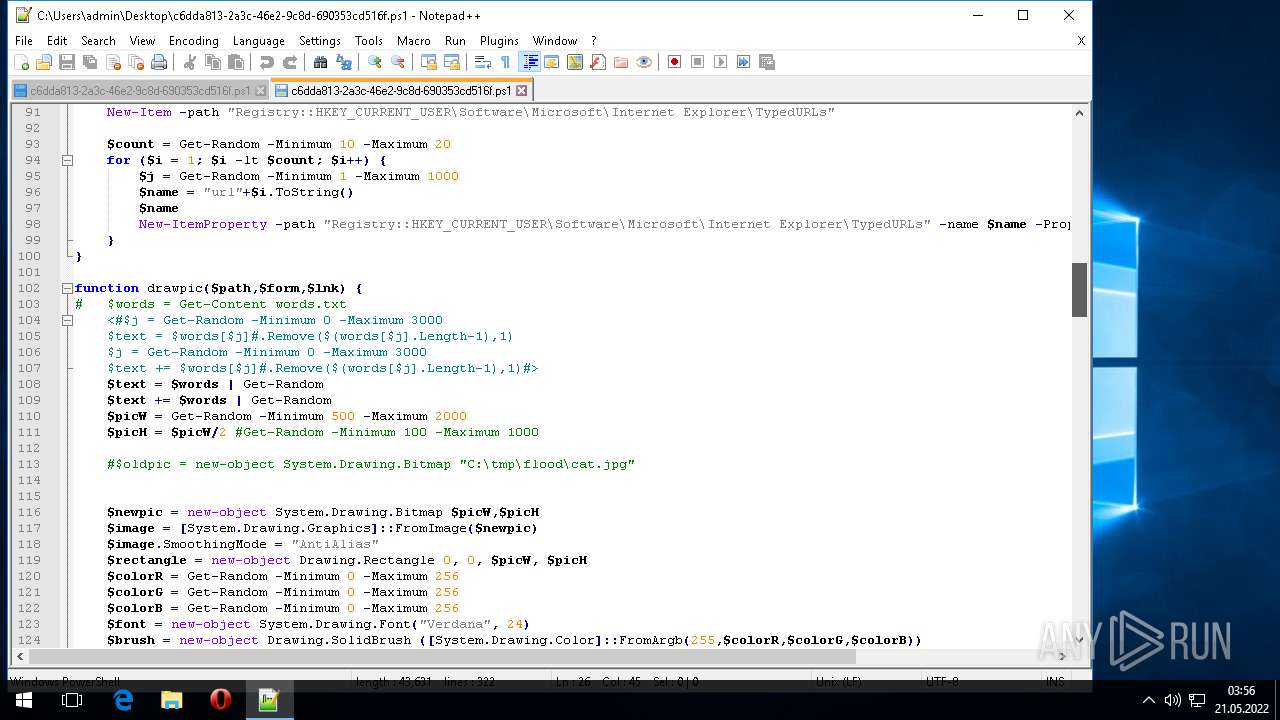
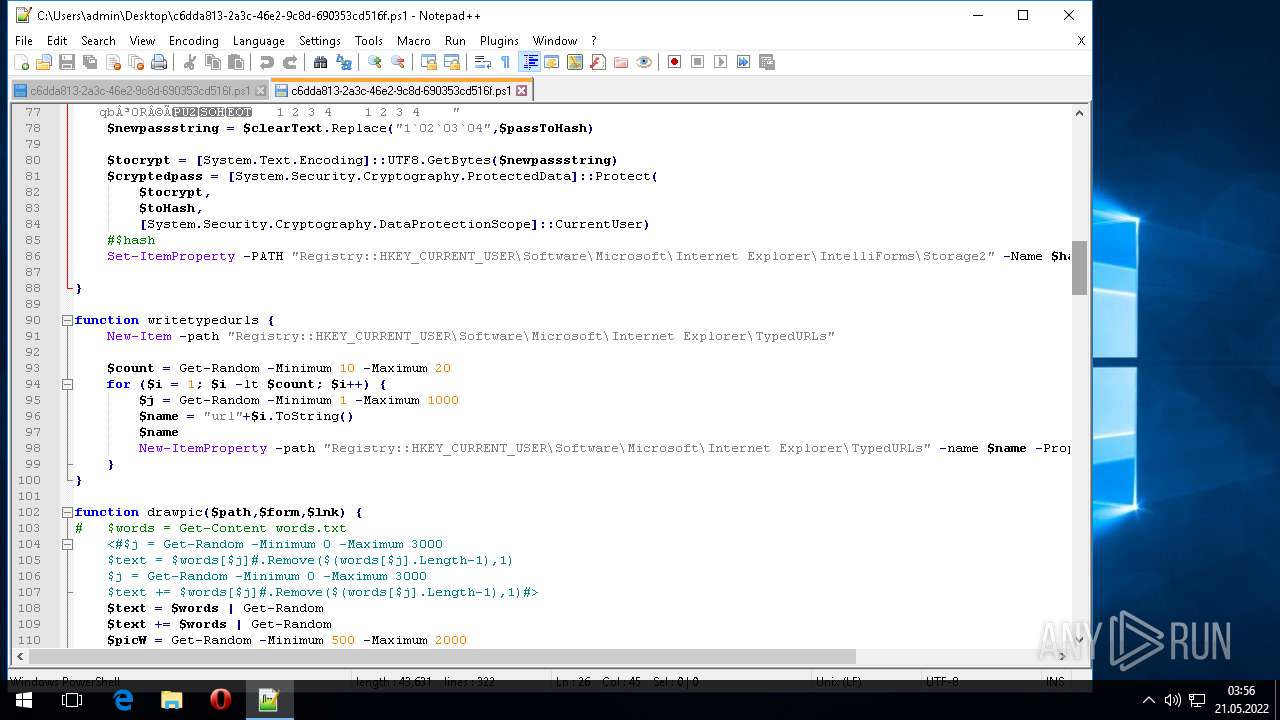
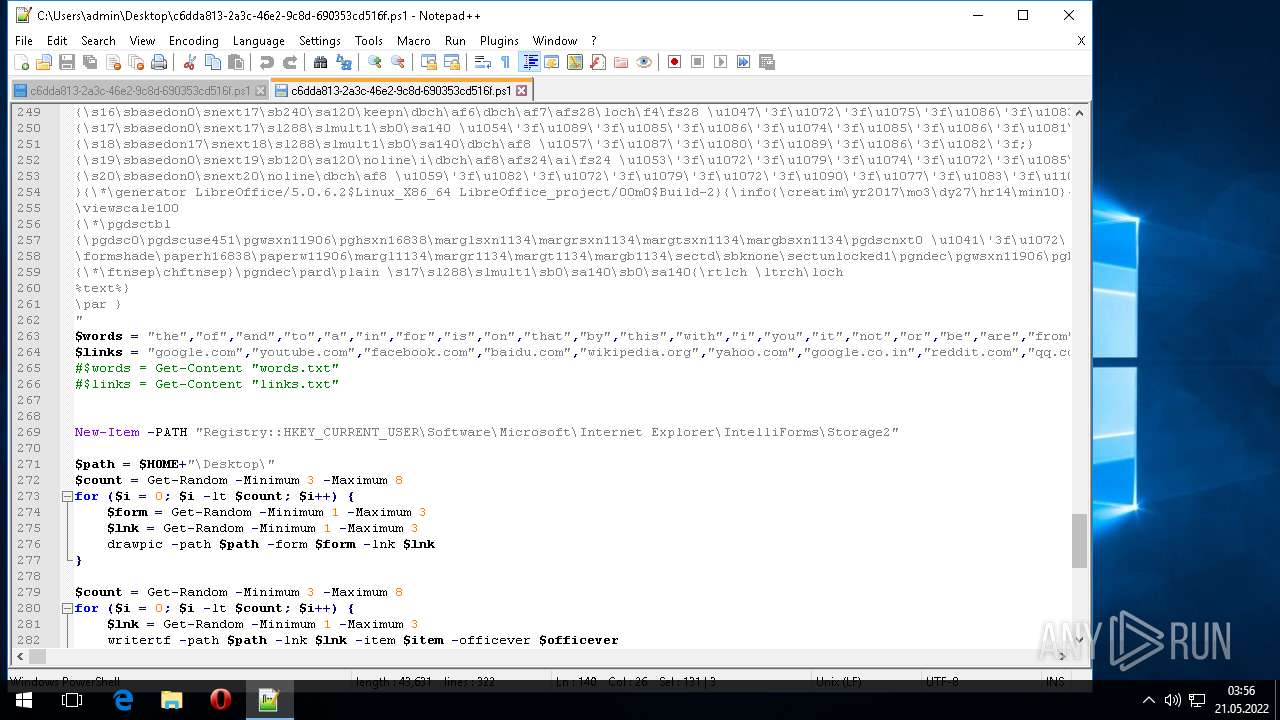
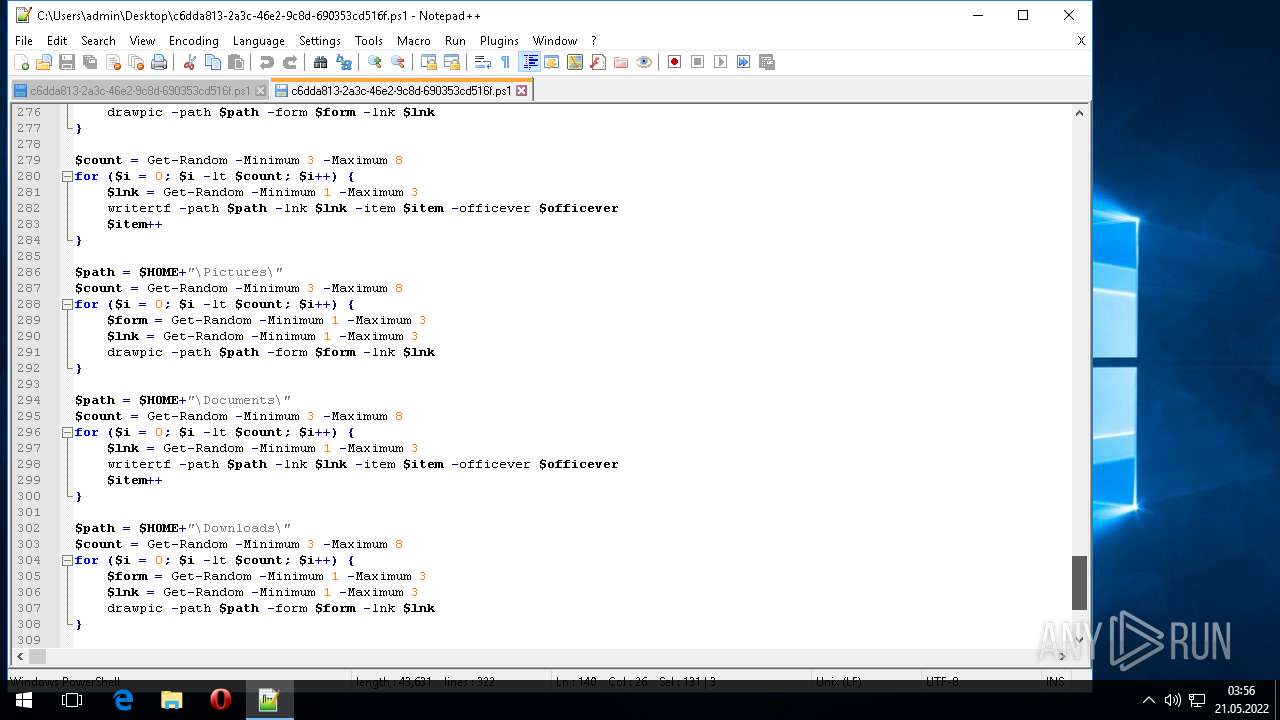
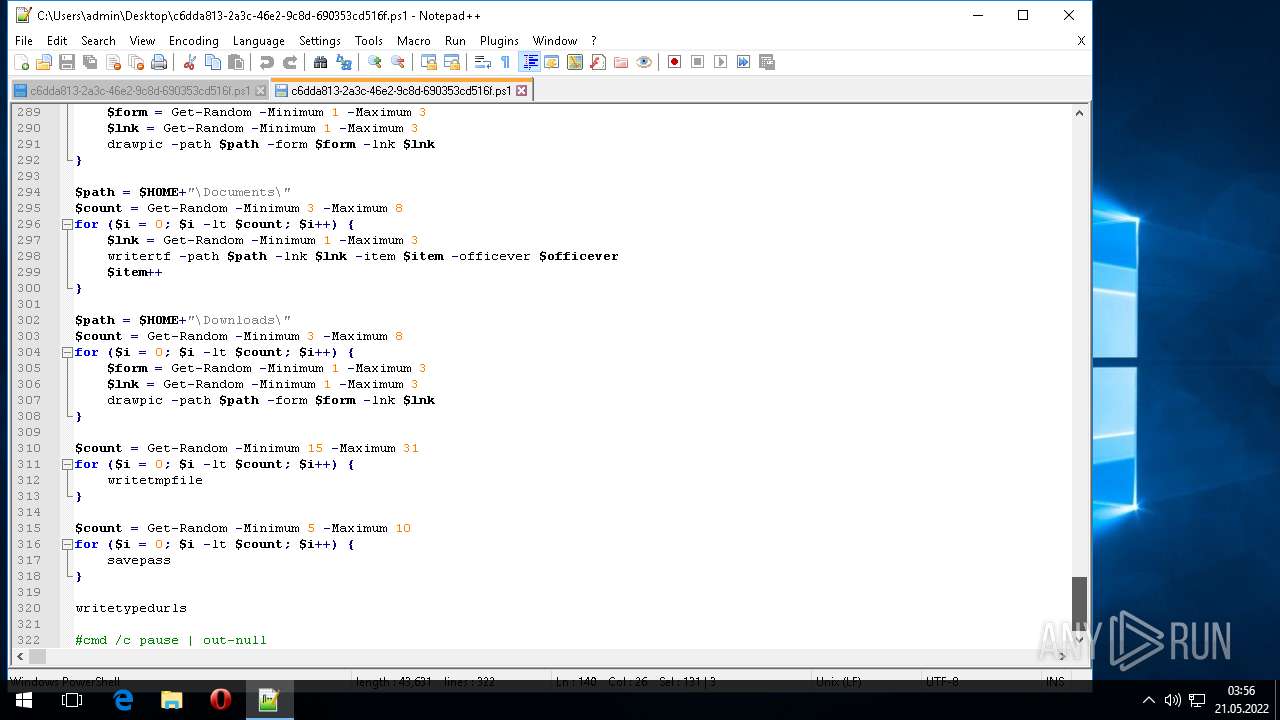
| 1604 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\AppData\Local\Temp\c6dda813-2a3c-46e2-9c8d-690353cd516f.ps1" | C:\Program Files\Notepad++\notepad++.exe | Explorer.EXE | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
| 2568 | "C:\Program Files\Notepad++\notepad++.exe" "C:\Users\admin\Desktop\c6dda813-2a3c-46e2-9c8d-690353cd516f.ps1" | C:\Program Files\Notepad++\notepad++.exe | Explorer.EXE | ||||||||||||
User: admin Company: Don HO don.h@free.fr Integrity Level: MEDIUM Description: Notepad++ : a free (GNU) source code editor Exit code: 0 Version: 7.51 Modules
| |||||||||||||||
Total events
36 604
Read events
34 712
Write events
939
Delete events
953
Modification events
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\73\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\73\52C64B7E |
| Operation: | write | Name: | @windows.storage.dll,-21825 |
Value: 3D Objects | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
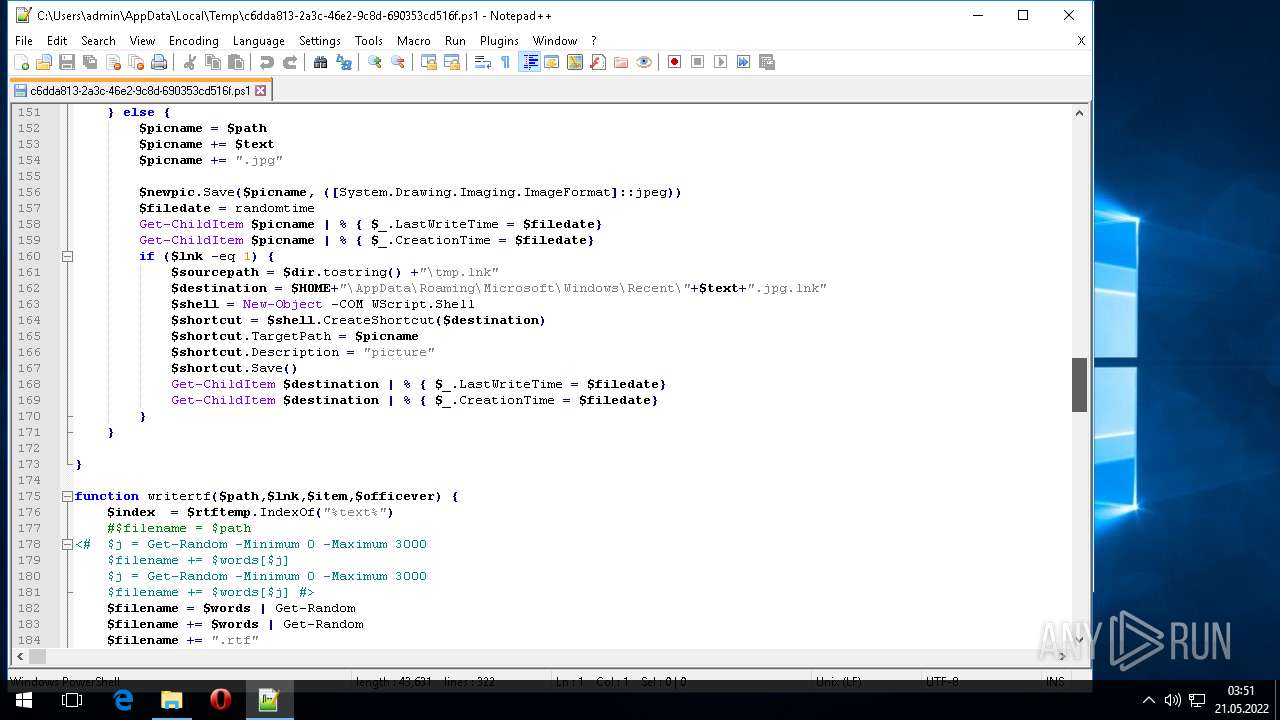
Value: C:\Users\admin\Downloads\what is long stop date in a contract(50123).zip | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3968) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
Executable files
0
Suspicious files
245
Text files
756
Unknown types
26
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3968 | WinRAR.exe | C:\Users\admin\Desktop\what_is_long_stop_date_in_a_contract 91856.js | text | |
MD5:— | SHA256:— | |||
| 304 | SDXHelper.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\45cfa0ff7e2dbd7b6089b3990c58a2ad\Package.appx | compressed | |
MD5:— | SHA256:— | |||
| 304 | SDXHelper.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\3cdc9d5f248d6d7506214ff391c8c3\Package.appx | compressed | |
MD5:— | SHA256:— | |||
| 304 | SDXHelper.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\ba773cbae5b9ee1cf4b831c30121b551\Package.appx | compressed | |
MD5:— | SHA256:— | |||
| 304 | SDXHelper.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\e6ec30329225bb49c9a13ed193ce8f50\Package.appx | compressed | |
MD5:— | SHA256:— | |||
| 304 | SDXHelper.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\f26db7bd8dbff792e75835c683dcb52c\Package.appx | compressed | |
MD5:— | SHA256:— | |||
| 304 | SDXHelper.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\819fb485a17719be1a6514b0586bad55\Package.appx | compressed | |
MD5:— | SHA256:— | |||
| 304 | SDXHelper.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\297d816682165b8eee0b3371d74a59d8\Package.appx | compressed | |
MD5:— | SHA256:— | |||
| 304 | SDXHelper.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\d226ad8293cd11d5fb2ac743a0d861a4\Package.appx | compressed | |
MD5:— | SHA256:— | |||
| 304 | SDXHelper.exe | C:\Users\admin\AppData\Local\Microsoft\Office\SolutionPackages\590b7ea04daf428bf1a2a504bd30e016\Package.appx | compressed | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
30
DNS requests
12
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1436 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
1244 | lsass.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEAo3h2ReX7SMIk79G%2B0UDDw%3D | US | der | 1.47 Kb | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3816 | sdxhelper.exe | 52.109.12.18:443 | nexusrules.officeapps.live.com | Microsoft Corporation | US | whitelisted |
304 | SDXHelper.exe | 52.109.32.63:443 | officeclient.microsoft.com | Microsoft Corporation | GB | whitelisted |
3816 | sdxhelper.exe | 13.107.42.16:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
1456 | svchost.exe | 52.152.110.14:443 | sls.update.microsoft.com | Microsoft Corporation | US | whitelisted |
1436 | svchost.exe | 40.126.32.136:443 | — | Microsoft Corporation | US | suspicious |
1436 | svchost.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
304 | SDXHelper.exe | 13.107.42.16:443 | config.edge.skype.com | Microsoft Corporation | US | whitelisted |
304 | SDXHelper.exe | 20.126.153.54:443 | mrodevicemgr.officeapps.live.com | — | US | suspicious |
304 | SDXHelper.exe | 52.109.12.18:443 | nexusrules.officeapps.live.com | Microsoft Corporation | US | whitelisted |
304 | SDXHelper.exe | 2.22.32.65:443 | officecdn.microsoft.com | Orange | — | suspicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
officeclient.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
config.edge.skype.com |
| malicious |
sls.update.microsoft.com |
| whitelisted |
self.events.data.microsoft.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
mrodevicemgr.officeapps.live.com |
| whitelisted |
officecdn.microsoft.com |
| whitelisted |
www.lintelconsulting.co.uk |
| unknown |
www.labbunnies.eu |
| unknown |
Threats
Process | Message |
|---|---|
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|
conhost.exe | InitSideBySide failed create an activation context. Error: 1814 |
notepad++.exe | VerifyLibrary: C:\Program Files\Notepad++\SciLexer.dll
|
notepad++.exe | VerifyLibrary: certificate revocation checking is disabled
|
notepad++.exe | 42C4C5846BB675C74E2B2C90C69AB44366401093
|