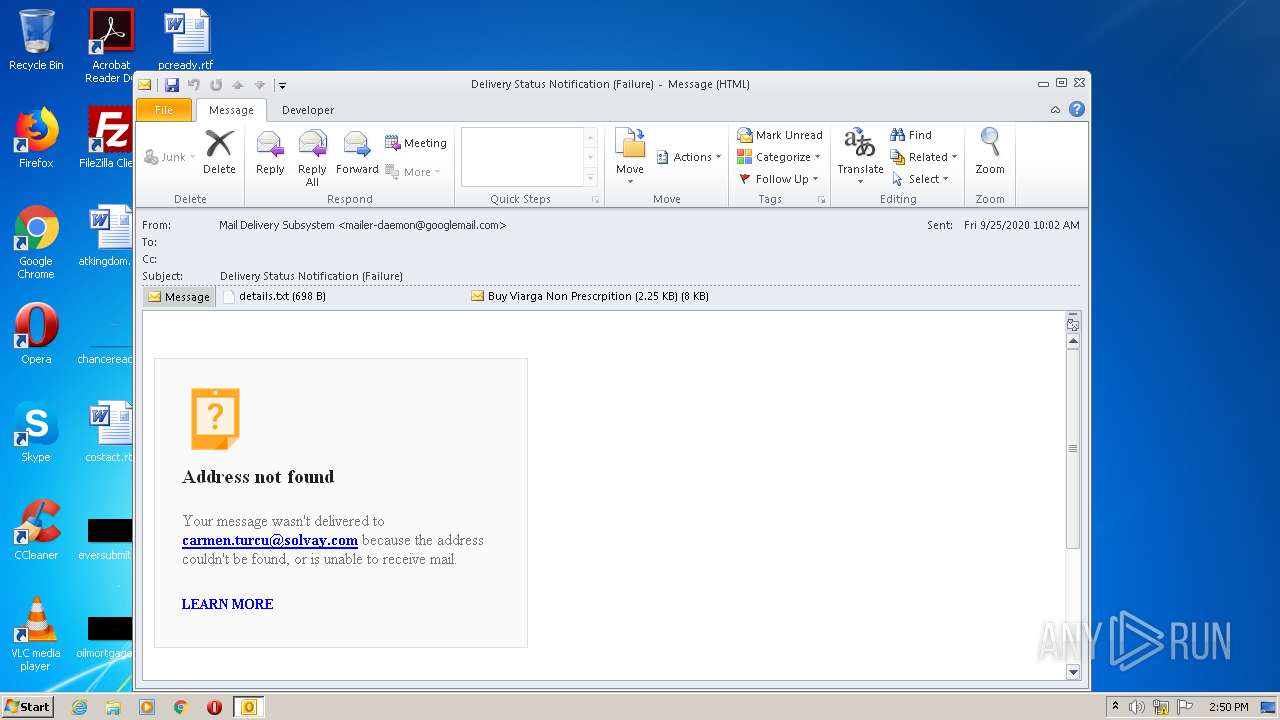
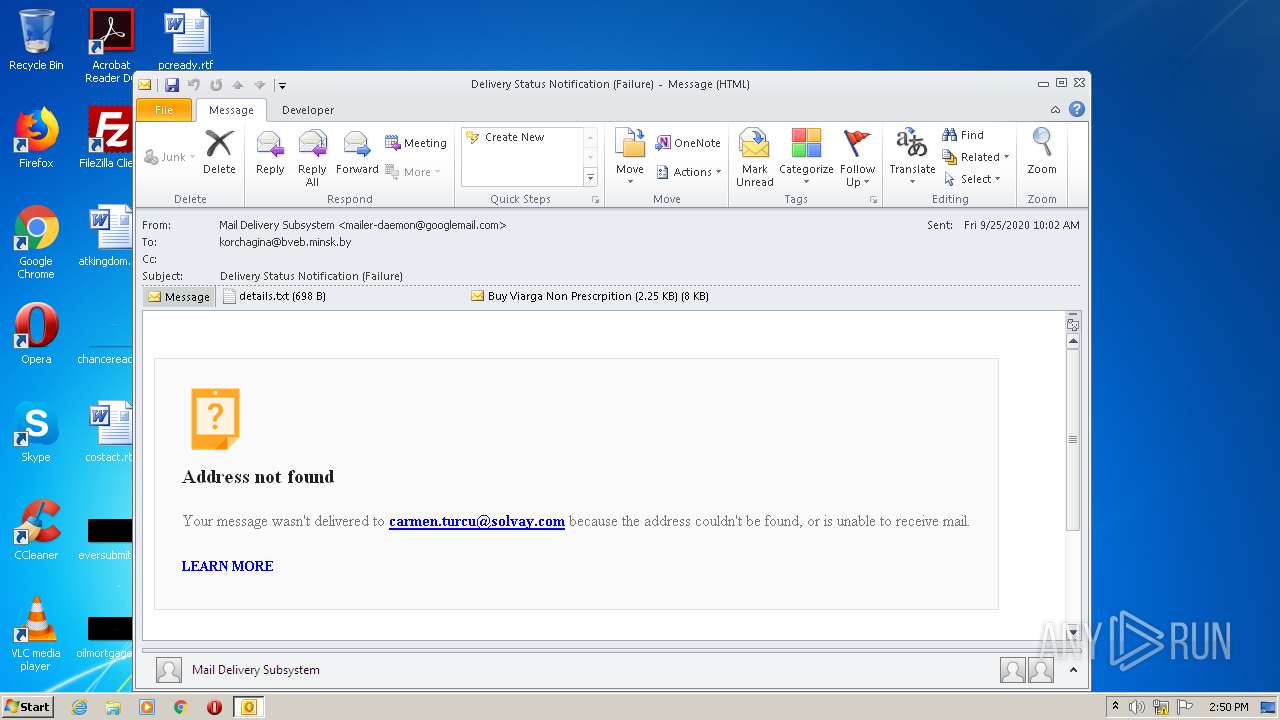
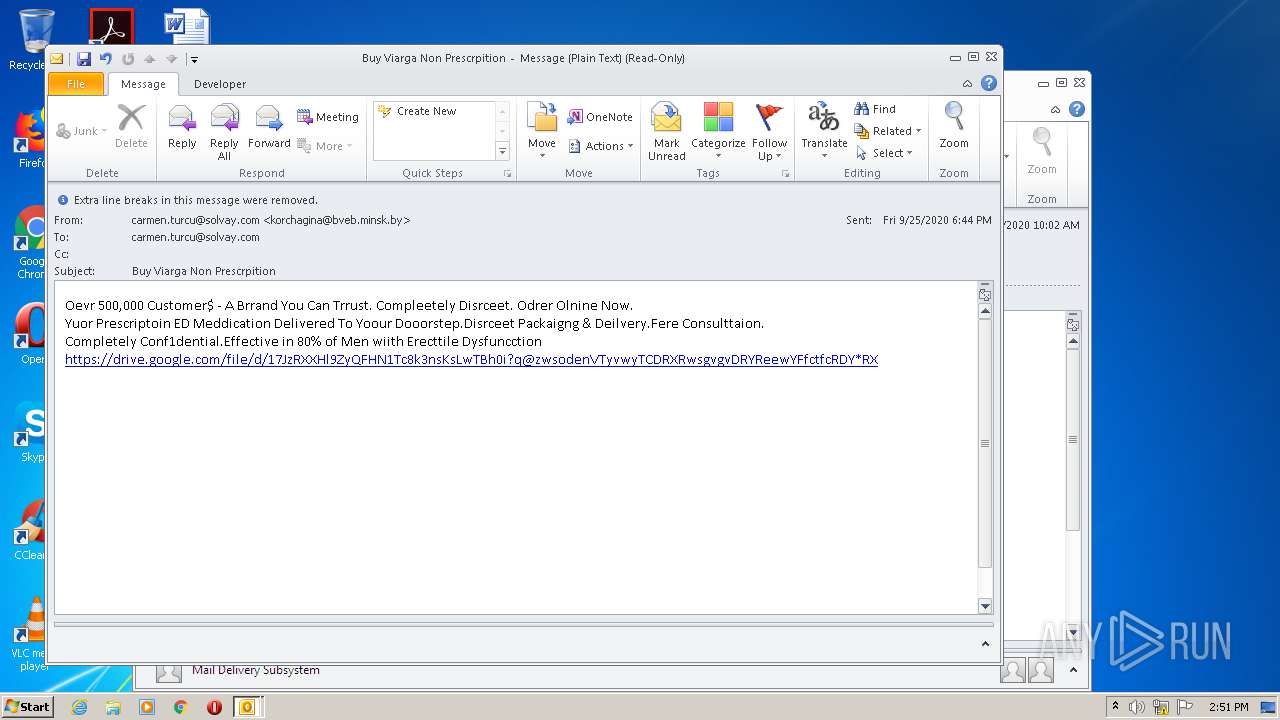
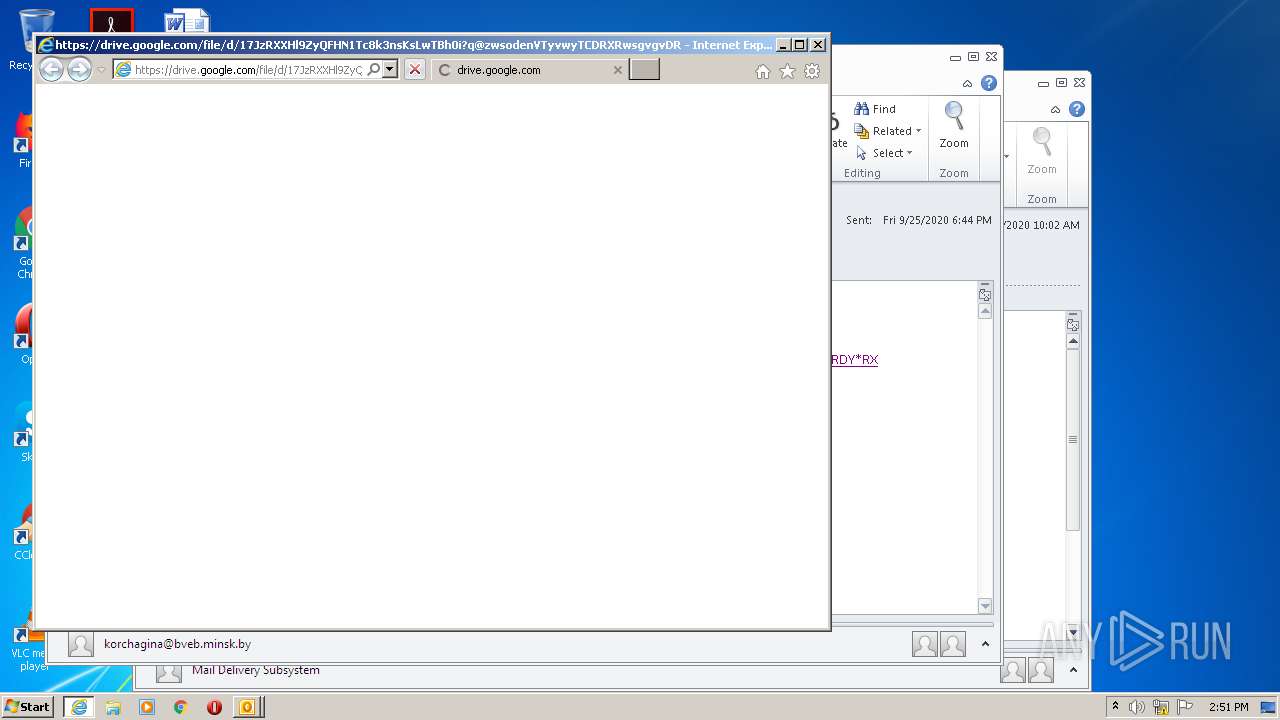
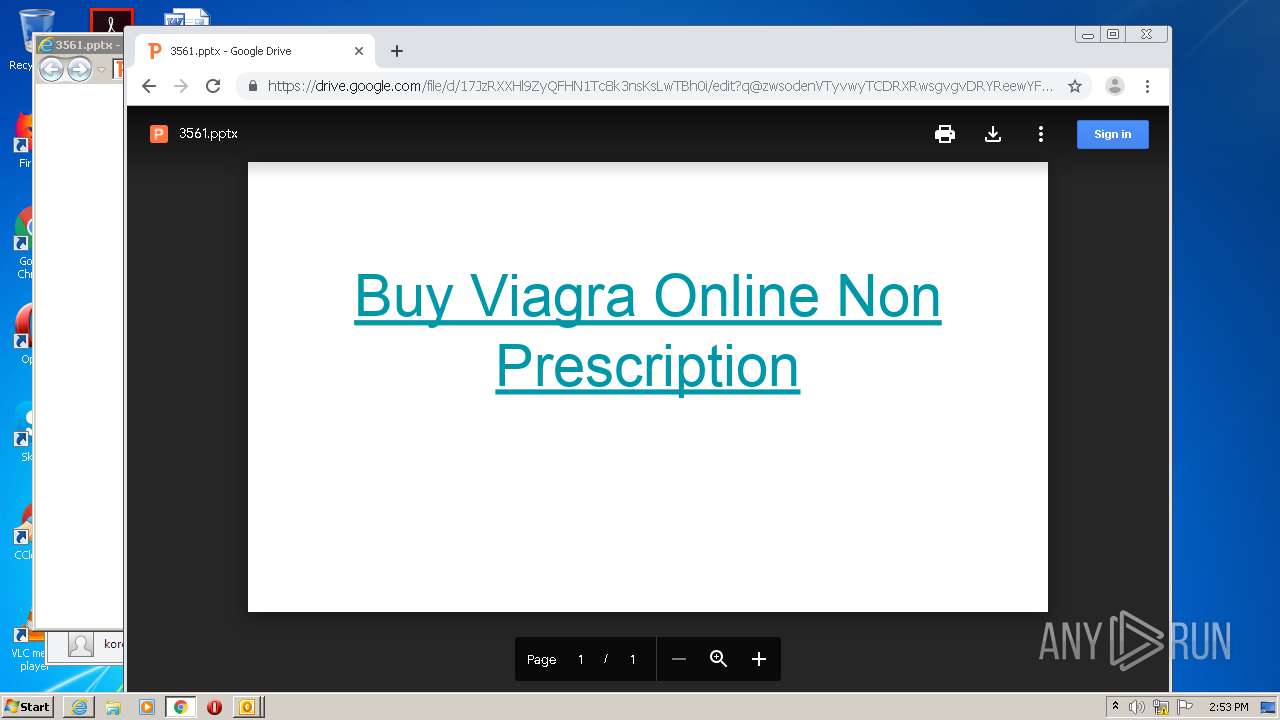
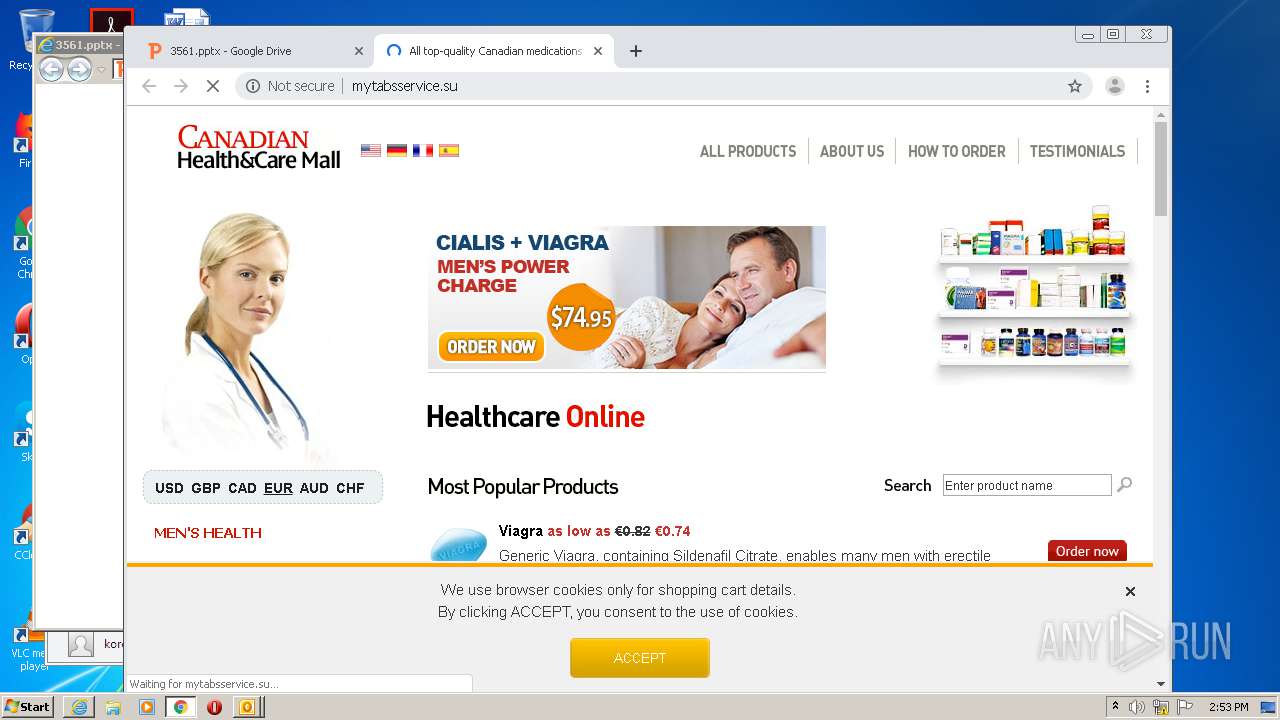
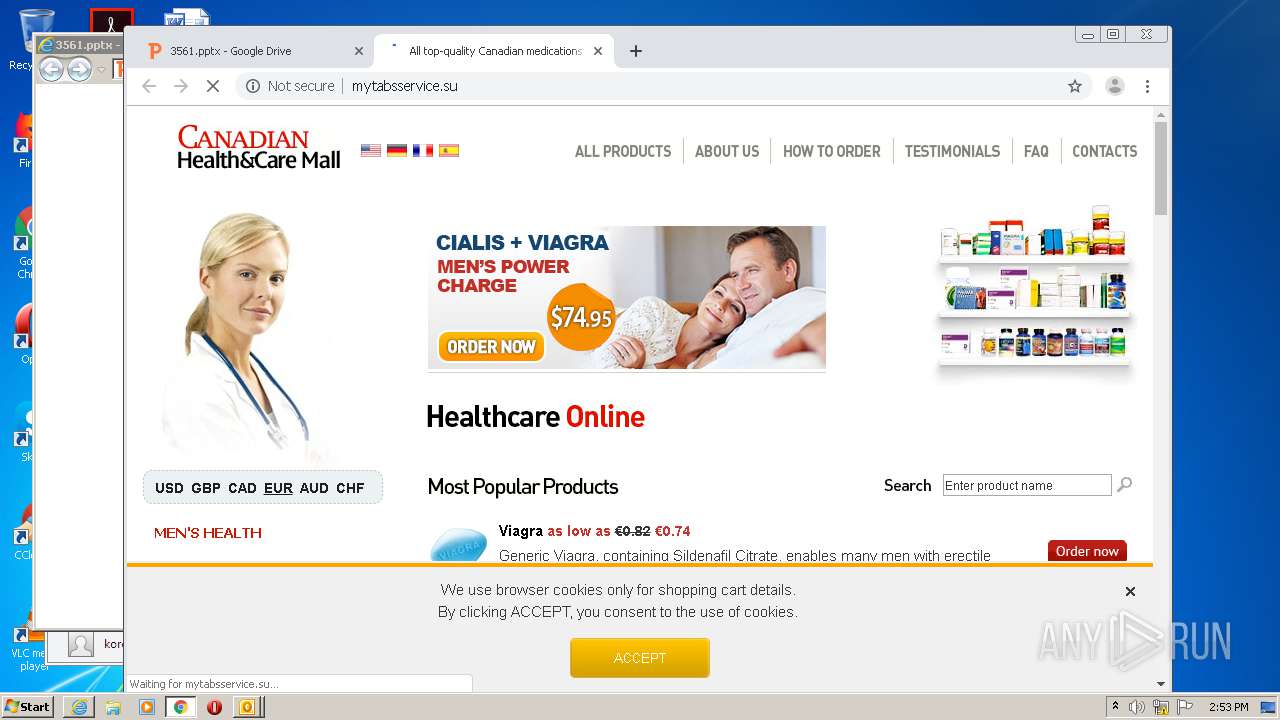
| File name: | 67D99BCC-B01F-9005-A20E-B31E518772C1.eml |
| Full analysis: | https://app.any.run/tasks/c84eed15-f01b-450d-89a8-a3e7615f57f8 |
| Verdict: | Malicious activity |
| Analysis date: | September 30, 2020, 13:50:18 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 3168F70B7A23A459DD8D4B54A99BCE1A |
| SHA1: | 47299674569A4F9B527B7124C2198CD1383BCE07 |
| SHA256: | AB94F99EA933F7AEB609D5A7D0950709ABEECAB865EB02EB740866109561ED52 |
| SSDEEP: | 192:5gm1jqbuqdrXt6mEb2/320avFYLMZy4mT9c9K2H02Q8kGDsatcxMoZLES9Dxoo3:5gm1OikdzEb2e0aOLMTbpsaOxMoZgSB3 |
MALICIOUS
No malicious indicators.SUSPICIOUS
Starts Internet Explorer
- OUTLOOK.EXE (PID: 1264)
Creates files in the user directory
- OUTLOOK.EXE (PID: 1264)
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 1264)
INFO
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 1264)
Reads Internet Cache Settings
- iexplore.exe (PID: 876)
- iexplore.exe (PID: 2116)
Application launched itself
- iexplore.exe (PID: 876)
- chrome.exe (PID: 2364)
Changes internet zones settings
- iexplore.exe (PID: 876)
Adds / modifies Windows certificates
- iexplore.exe (PID: 876)
Reads the hosts file
- chrome.exe (PID: 2364)
- chrome.exe (PID: 3076)
Reads settings of System Certificates
- iexplore.exe (PID: 876)
- iexplore.exe (PID: 2116)
Creates files in the user directory
- iexplore.exe (PID: 876)
- iexplore.exe (PID: 2116)
Manual execution by user
- chrome.exe (PID: 2364)
Reads internet explorer settings
- iexplore.exe (PID: 2116)
Changes settings of System certificates
- iexplore.exe (PID: 876)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
64
Monitored processes
26
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 628 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,1175698914356214414,12430275573869043835,131072 --enable-features=PasswordImport --disable-gpu-compositing --lang=en-US --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=10368502052690491218 --renderer-client-id=15 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=3752 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
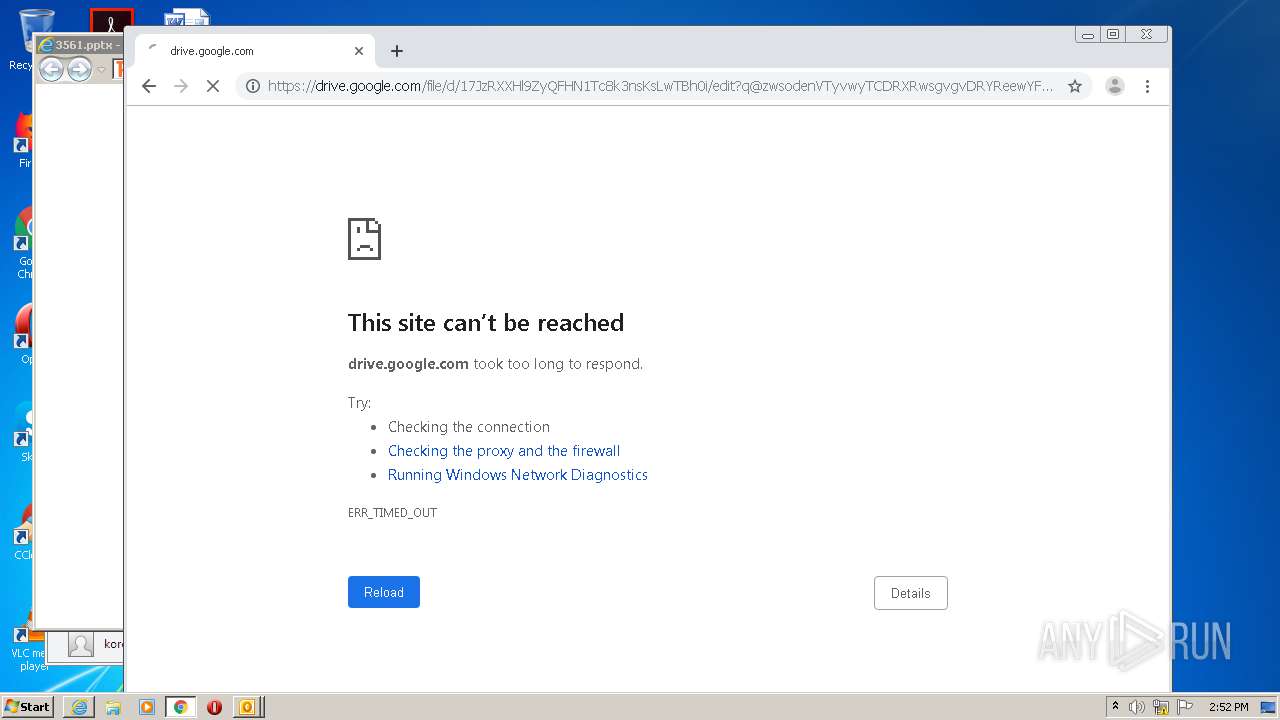
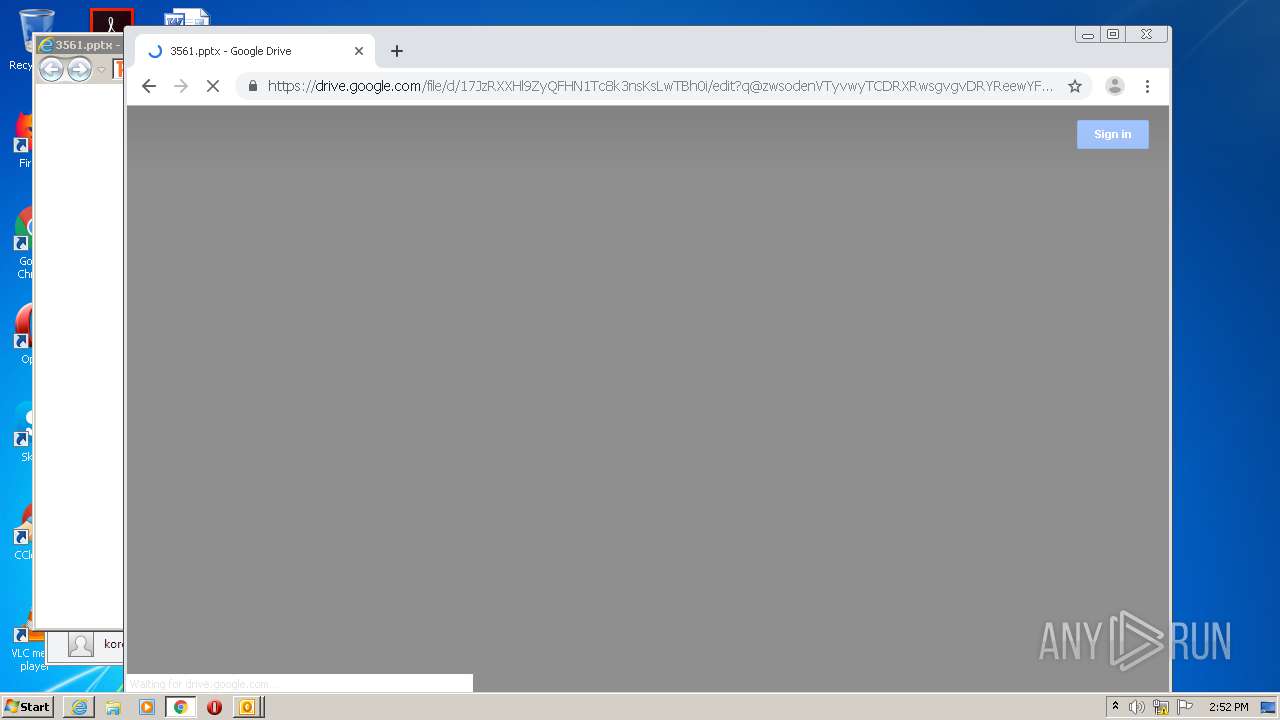
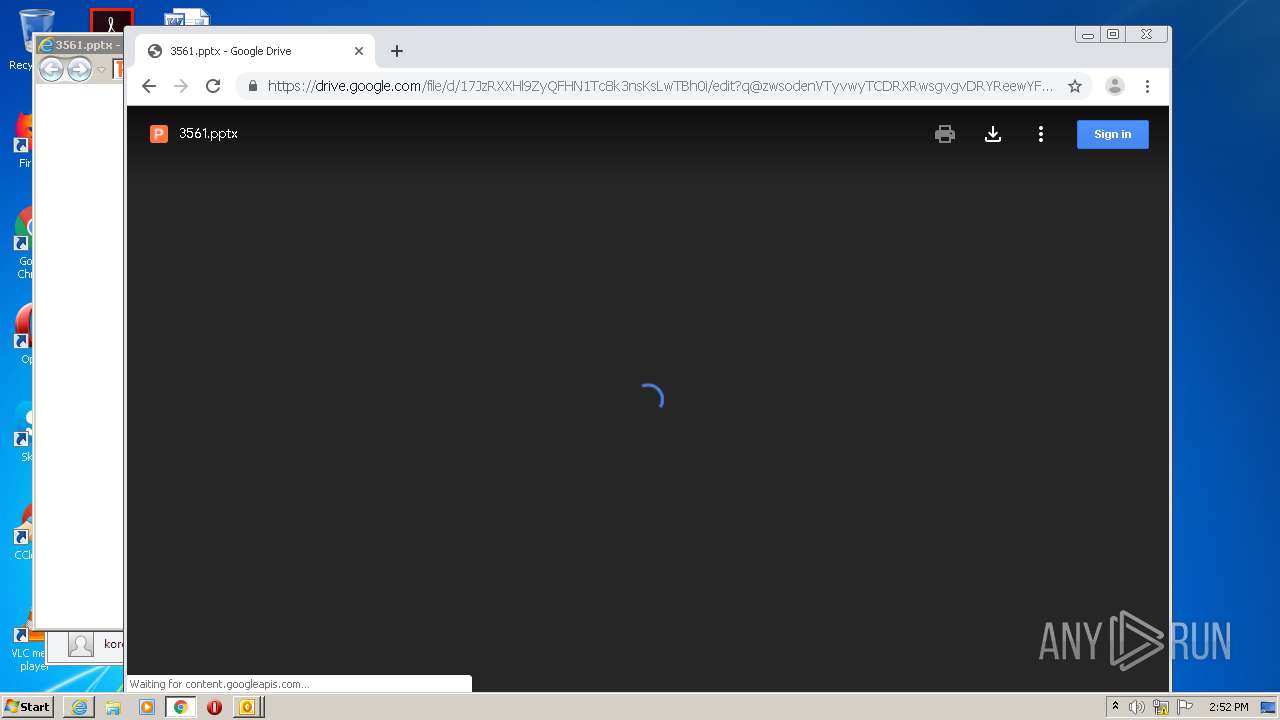
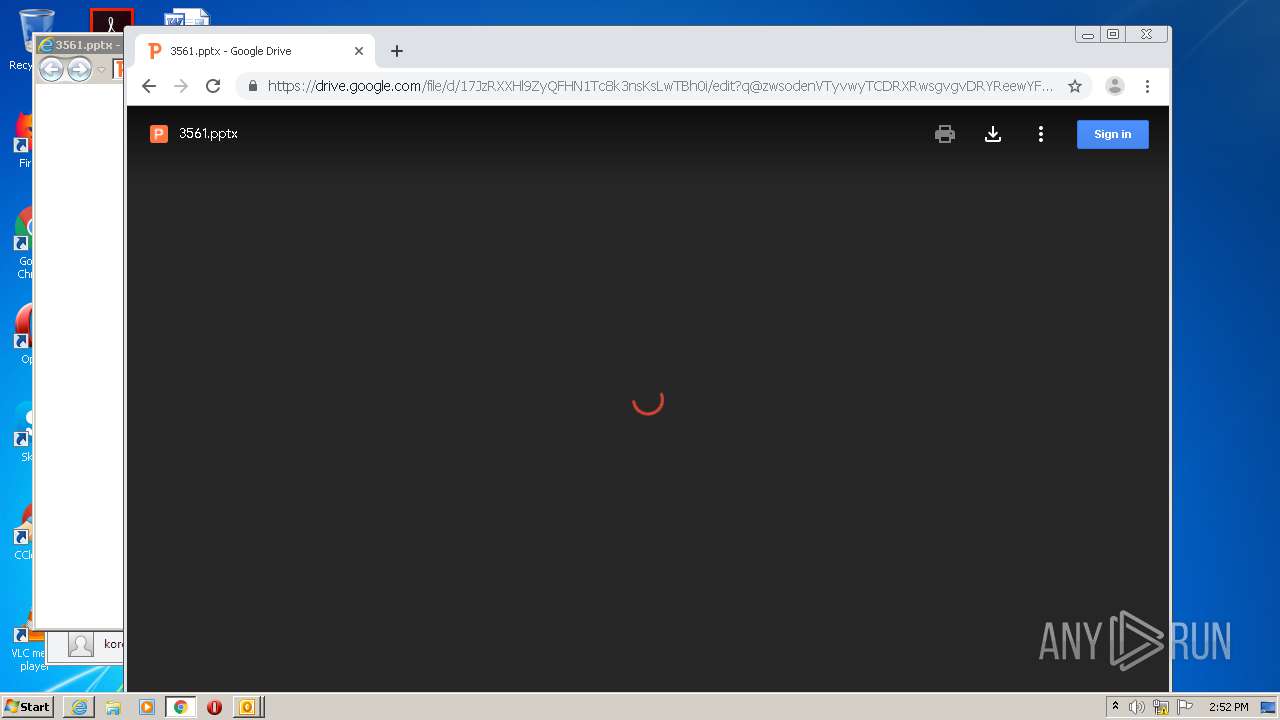
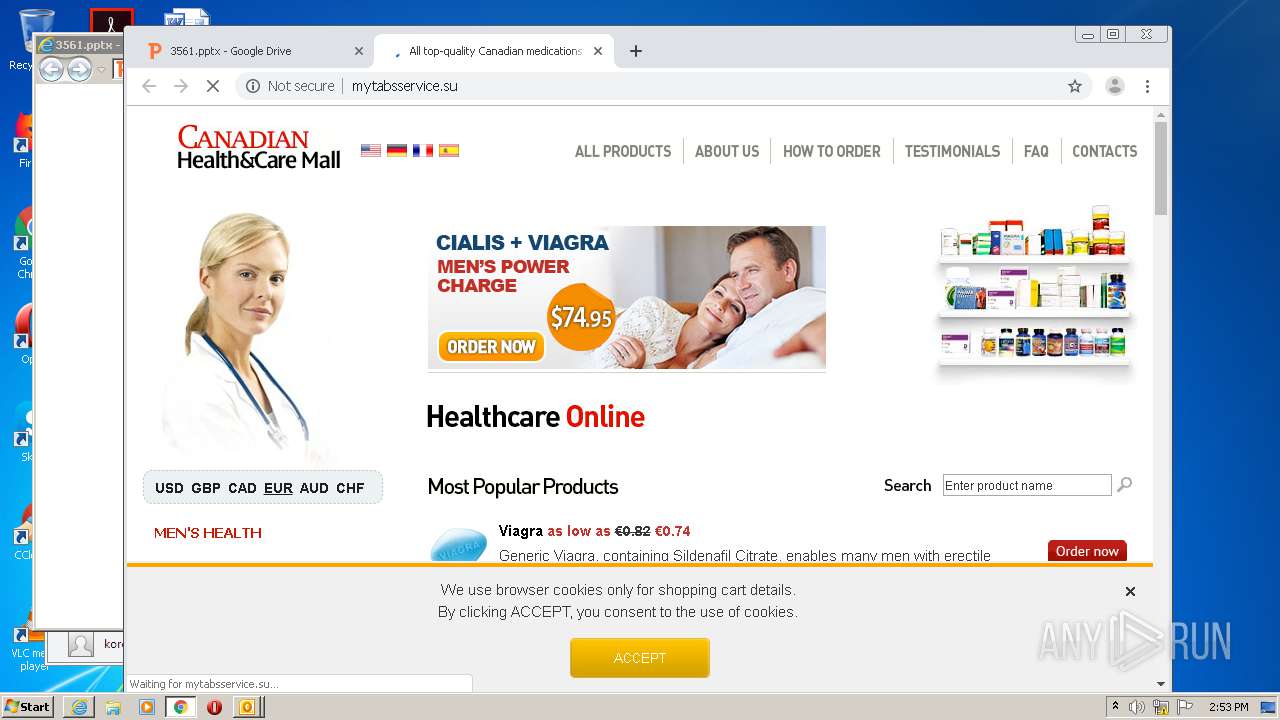
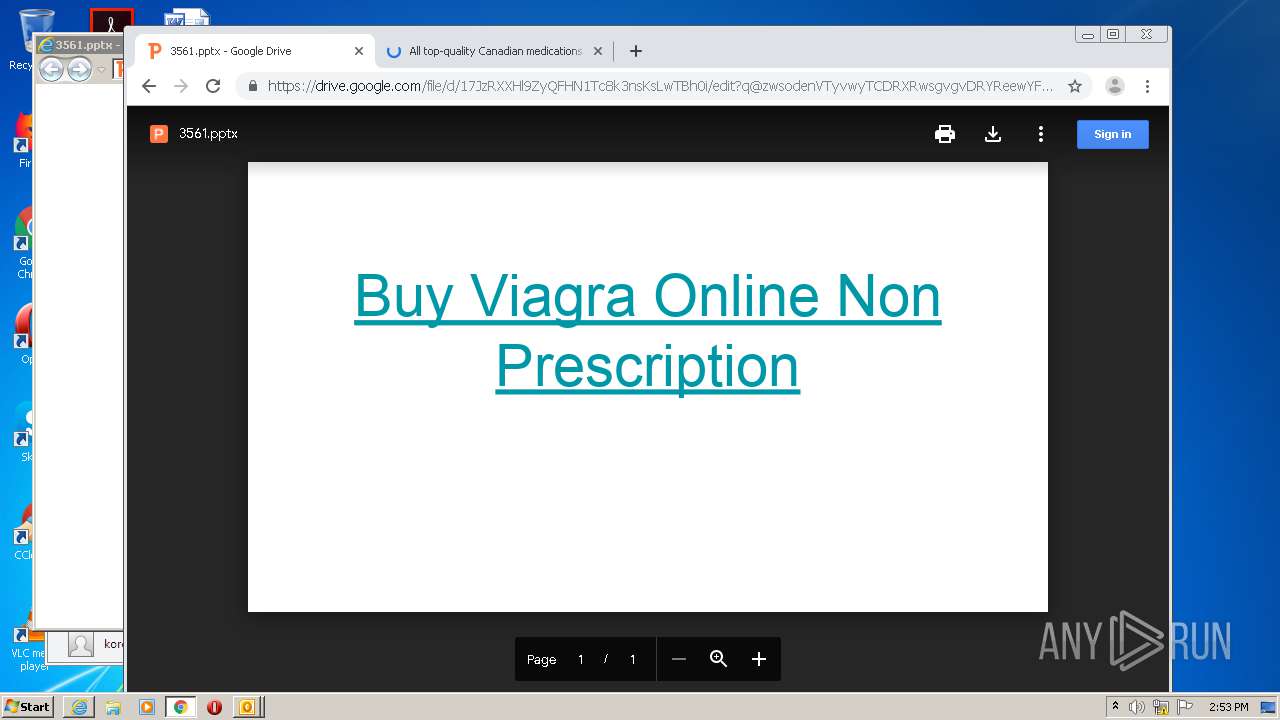
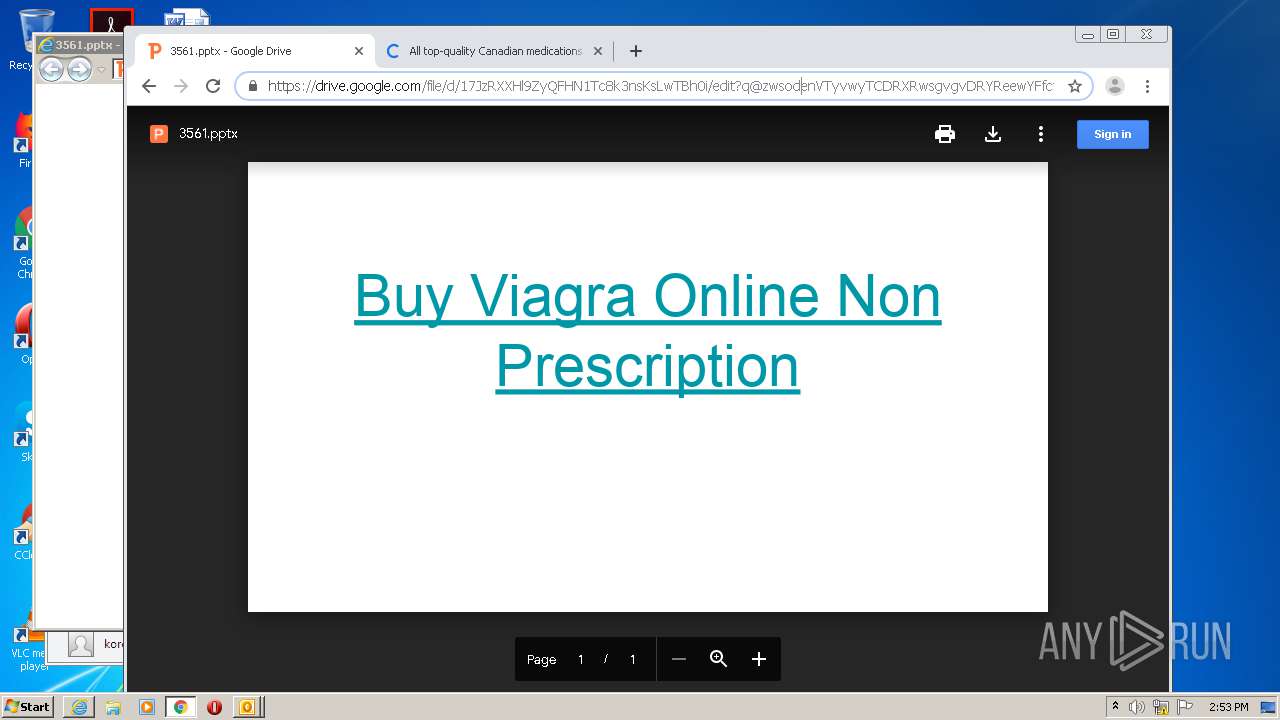
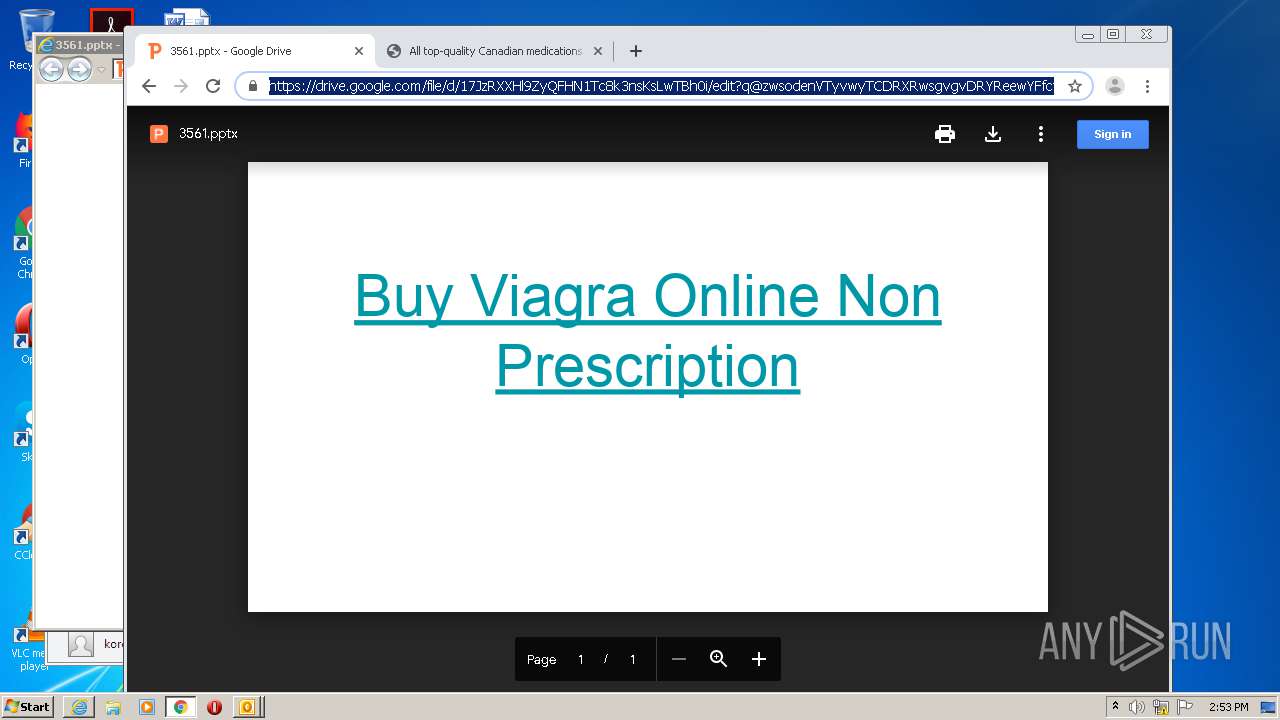
| 876 | "C:\Program Files\Internet Explorer\iexplore.exe" https://drive.google.com/file/d/17JzRXXHl9ZyQFHN1Tc8k3nsKsLwTBh0i?q@zwsodenVTyvwyTCDRXRwsgvgvDRYReewYFfctfcRDY*RX | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 952 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=gpu-process --field-trial-handle=1040,1175698914356214414,12430275573869043835,131072 --enable-features=PasswordImport --gpu-preferences=KAAAAAAAAADgAAAgAQAAAAAAAAAAAGAAAAAAAAAAAAAIAAAAAAAAACgAAAAEAAAAIAAAAAAAAAAoAAAAAAAAADAAAAAAAAAAOAAAAAAAAAAQAAAAAAAAAAAAAAAFAAAAEAAAAAAAAAAAAAAABgAAABAAAAAAAAAAAQAAAAUAAAAQAAAAAAAAAAEAAAAGAAAA --service-request-channel-token=9238068227584329913 --mojo-platform-channel-handle=1032 --ignored=" --type=renderer " /prefetch:2 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 1264 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\67D99BCC-B01F-9005-A20E-B31E518772C1.eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
| 1340 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,1175698914356214414,12430275573869043835,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=12974773110793289958 --mojo-platform-channel-handle=3060 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2064 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,1175698914356214414,12430275573869043835,131072 --enable-features=PasswordImport --lang=en-US --no-sandbox --service-request-channel-token=17768662947066988177 --mojo-platform-channel-handle=3996 /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2104 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=renderer --field-trial-handle=1040,1175698914356214414,12430275573869043835,131072 --enable-features=PasswordImport --lang=en-US --instant-process --enable-offline-auto-reload --enable-offline-auto-reload-visible-only --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --service-request-channel-token=3861524664151247096 --renderer-client-id=6 --no-v8-untrusted-code-mitigations --mojo-platform-channel-handle=2224 /prefetch:1 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2116 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:876 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2364 | "C:\Program Files\Google\Chrome\Application\chrome.exe" | C:\Program Files\Google\Chrome\Application\chrome.exe | explorer.exe | ||||||||||||
User: admin Company: Google LLC Integrity Level: MEDIUM Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
| 2424 | "C:\Program Files\Google\Chrome\Application\chrome.exe" --type=utility --field-trial-handle=1040,1175698914356214414,12430275573869043835,131072 --enable-features=PasswordImport --lang=en-US --service-sandbox-type=utility --service-request-channel-token=17009159778493447367 --mojo-platform-channel-handle=3952 --ignored=" --type=renderer " /prefetch:8 | C:\Program Files\Google\Chrome\Application\chrome.exe | — | chrome.exe | |||||||||||
User: admin Company: Google LLC Integrity Level: LOW Description: Google Chrome Exit code: 0 Version: 75.0.3770.100 Modules
| |||||||||||||||
Total events
2 820
Read events
2 099
Write events
695
Delete events
26
Modification events
| (PID) Process: | (1264) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (1264) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (1264) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (1264) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (1264) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (1264) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (1264) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (1264) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (1264) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (1264) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
78
Text files
130
Unknown types
28
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1264 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRB00C.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 2116 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab9387.tmp | — | |
MD5:— | SHA256:— | |||
| 2116 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar9388.tmp | — | |
MD5:— | SHA256:— | |||
| 1264 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\outlook logging\firstrun.log | text | |
MD5:— | SHA256:— | |||
| 1264 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 2116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CFE86DBBE02D859DC92F1E17E0574EE8_46766FC45507C0B9E264E4C18BC7288B | der | |
MD5:— | SHA256:— | |||
| 2116 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low\Content.IE5\MFAQUS6V\edit[1].htm | html | |
MD5:— | SHA256:— | |||
| 2116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\CC197601BE0898B7B0FCC91FA15D8A69_93BB5A29A73AA40D558BAE7D8E0C12DD | der | |
MD5:— | SHA256:— | |||
| 2116 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\CC197601BE0898B7B0FCC91FA15D8A69_B692386BB395D0D1B54DEE15DF22E03C | binary | |
MD5:— | SHA256:— | |||
| 2116 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\Z7V1LJ0F.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
72
TCP/UDP connections
134
DNS requests
41
Threats
57
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2116 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDOs%2FDKHsIMiAIAAAAAeksR | US | der | 472 b | whitelisted |
1052 | svchost.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQS14tALDViBvqCf47YkiQRtKz1BAQUpc436uuwdQ6UZ4i0RfrZJBCHlh8CEA7yTSbUNi7CXXtef0luXqk%3D | US | der | 279 b | whitelisted |
2116 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2116 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEDM8p7YwCDvUCAAAAABXoPk%3D | US | der | 471 b | whitelisted |
2116 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
2116 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQCoziyTHasflwIAAAAAekur | US | der | 472 b | whitelisted |
2116 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDOs%2FDKHsIMiAIAAAAAeksR | US | der | 472 b | whitelisted |
2116 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEBedu0%2BUKJj8CAAAAABXoSI%3D | US | der | 471 b | whitelisted |
2116 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEDM8p7YwCDvUCAAAAABXoPk%3D | US | der | 471 b | whitelisted |
2116 | iexplore.exe | GET | 200 | 216.58.206.3:80 | http://ocsp.pki.goog/gts1o1core/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDqXuNQ97mPtAIAAAAAektt | US | der | 472 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2116 | iexplore.exe | 142.250.74.206:443 | drive.google.com | Google Inc. | US | whitelisted |
1264 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
2116 | iexplore.exe | 216.58.206.3:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2116 | iexplore.exe | 172.217.18.106:443 | fonts.googleapis.com | Google Inc. | US | whitelisted |
2116 | iexplore.exe | 172.217.16.195:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
876 | iexplore.exe | 204.79.197.200:80 | www.bing.com | Microsoft Corporation | US | whitelisted |
3076 | chrome.exe | 216.58.212.163:443 | clientservices.googleapis.com | Google Inc. | US | whitelisted |
876 | iexplore.exe | 172.217.22.67:443 | ssl.gstatic.com | Google Inc. | US | whitelisted |
3076 | chrome.exe | 172.217.23.132:443 | www.google.com | Google Inc. | US | whitelisted |
2116 | iexplore.exe | 172.217.18.14:443 | apis.google.com | Google Inc. | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
drive.google.com |
| shared |
ocsp.pki.goog |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
fonts.gstatic.com |
| whitelisted |
apis.google.com |
| whitelisted |
ogs.google.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
1052 | svchost.exe | Potentially Bad Traffic | ET DNS Query for .su TLD (Soviet Union) Often Malware Related |
3076 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3076 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3076 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3076 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3076 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3076 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3076 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |
3076 | chrome.exe | Potentially Bad Traffic | ET POLICY HTTP Request to .su TLD (Soviet Union) Often Malware Related |