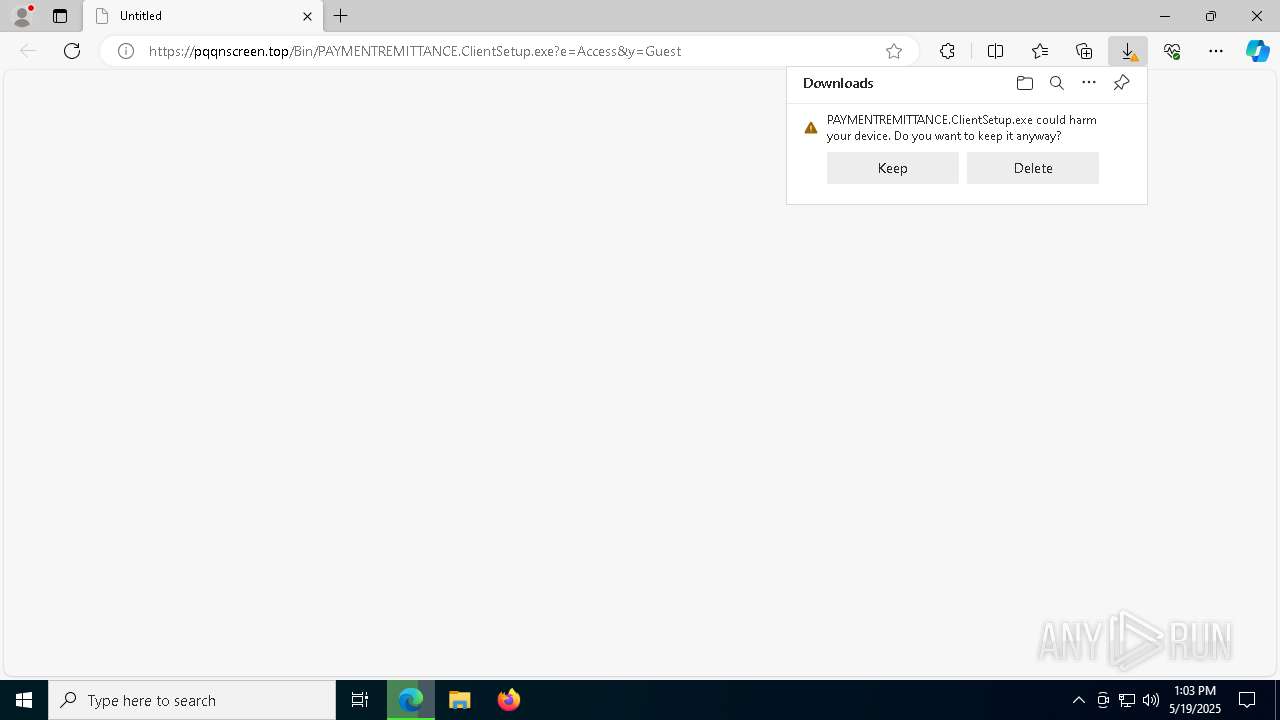
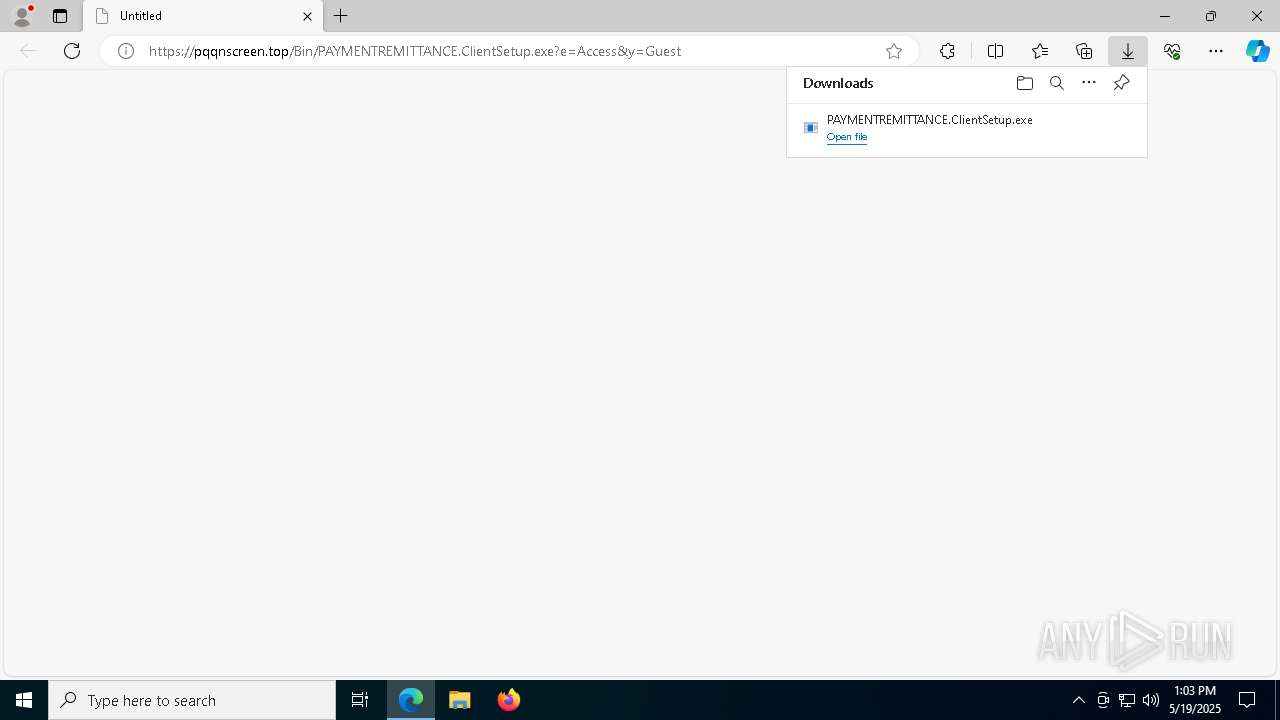
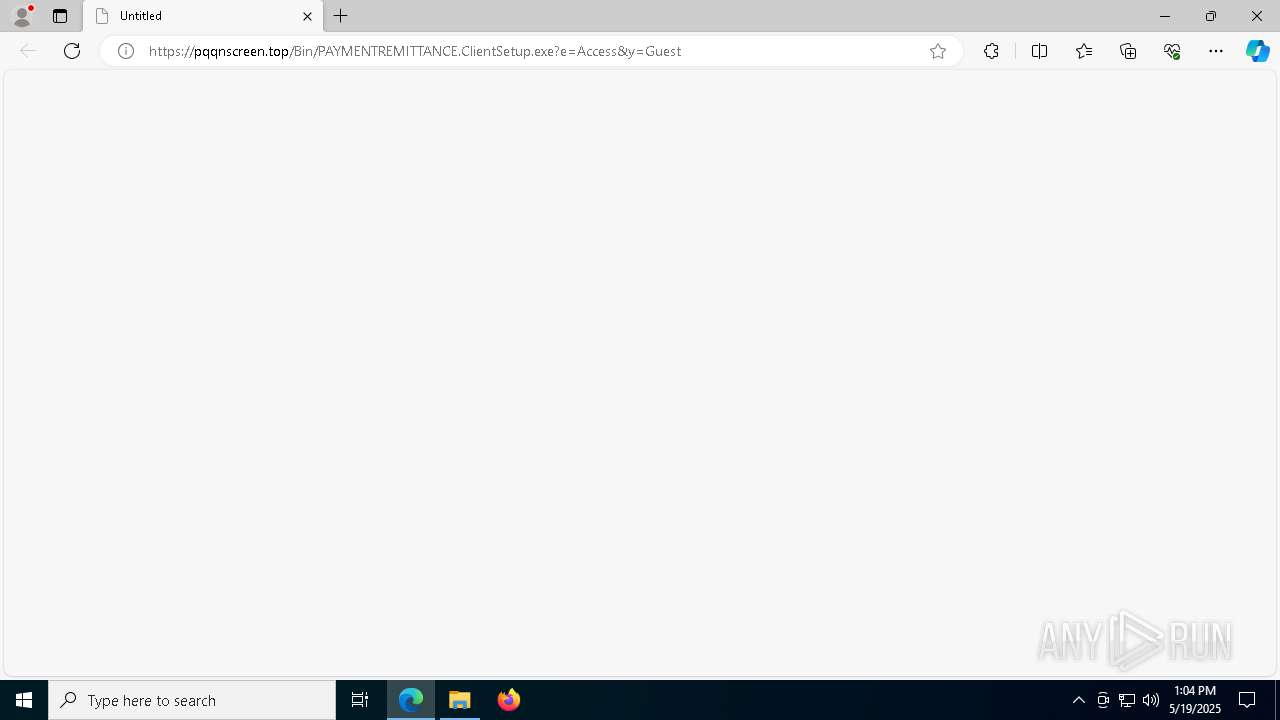
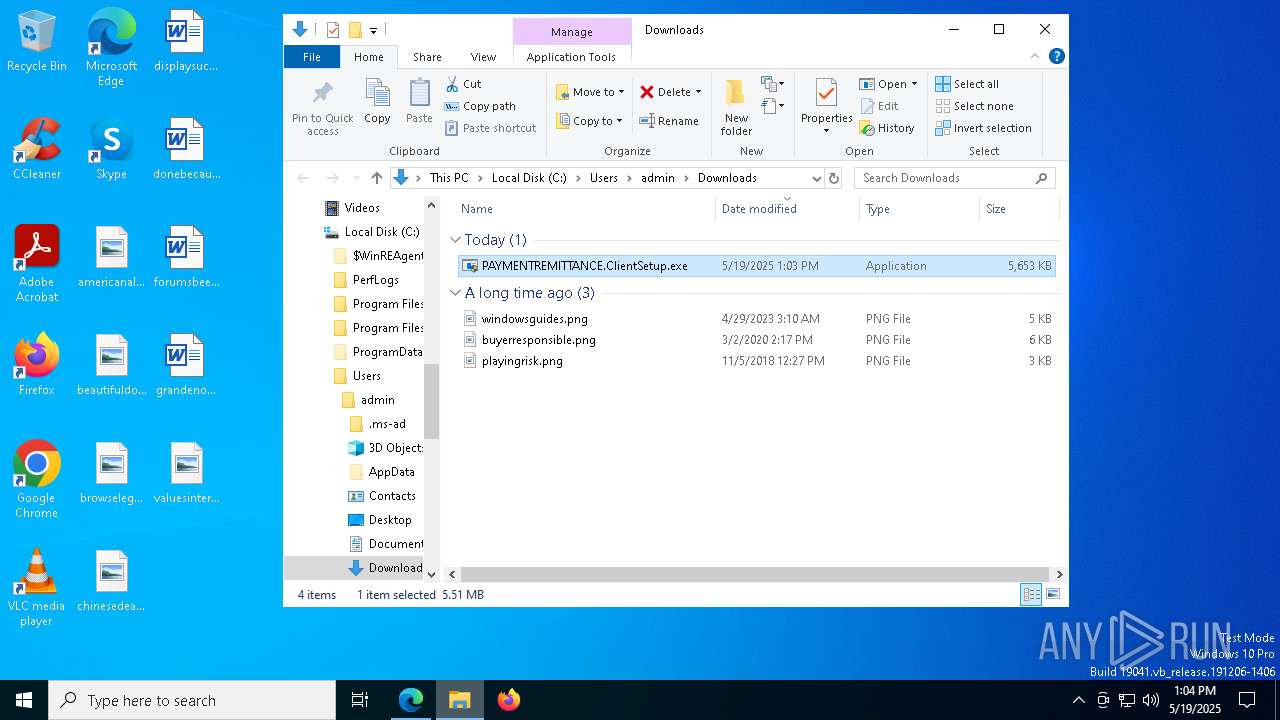
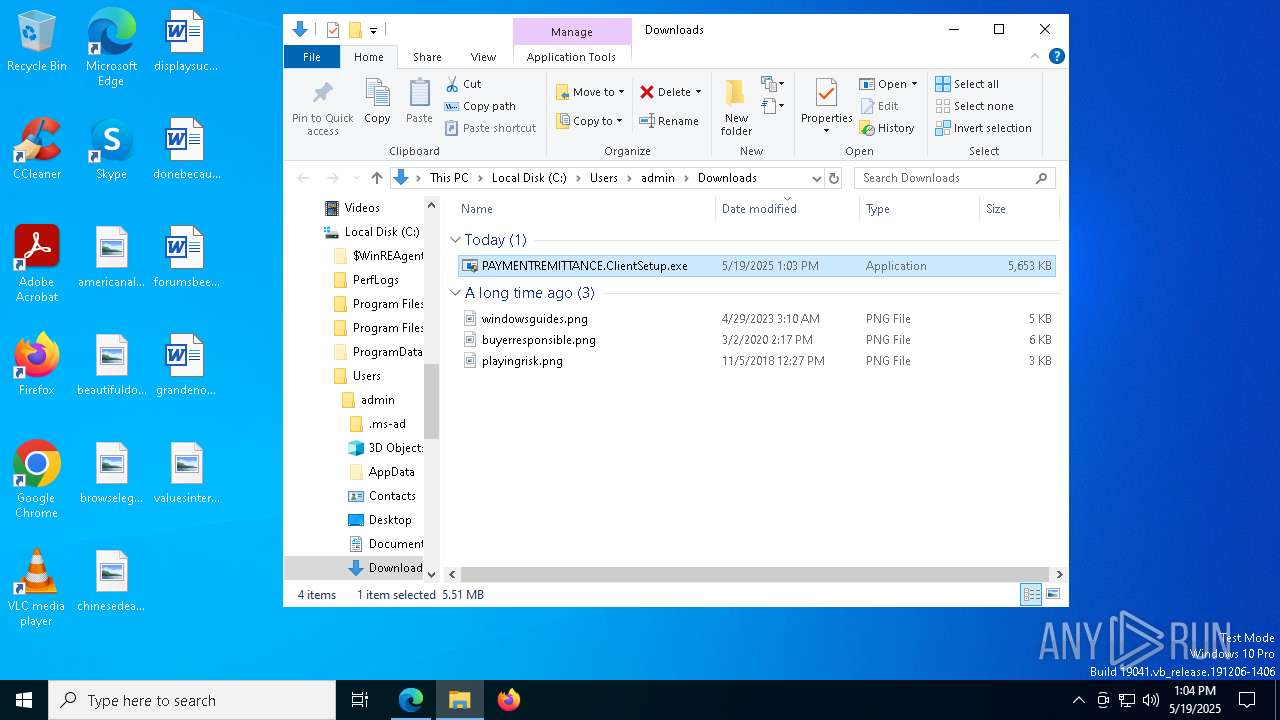
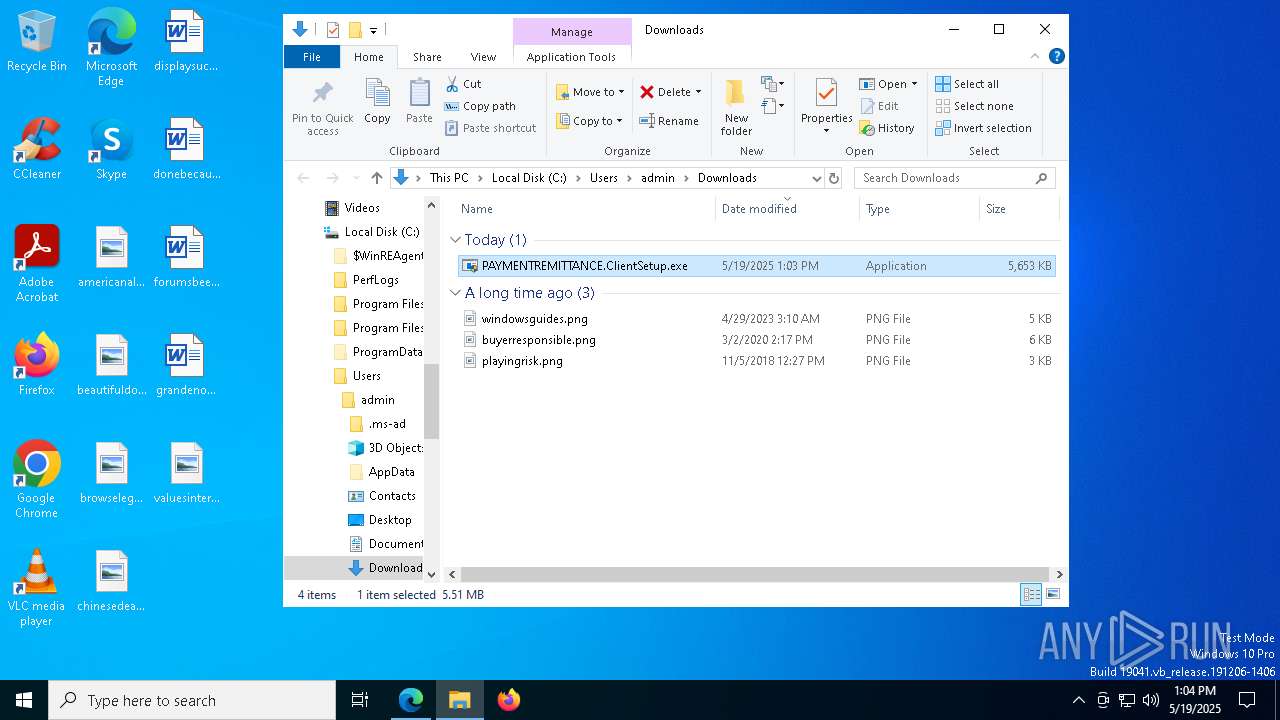
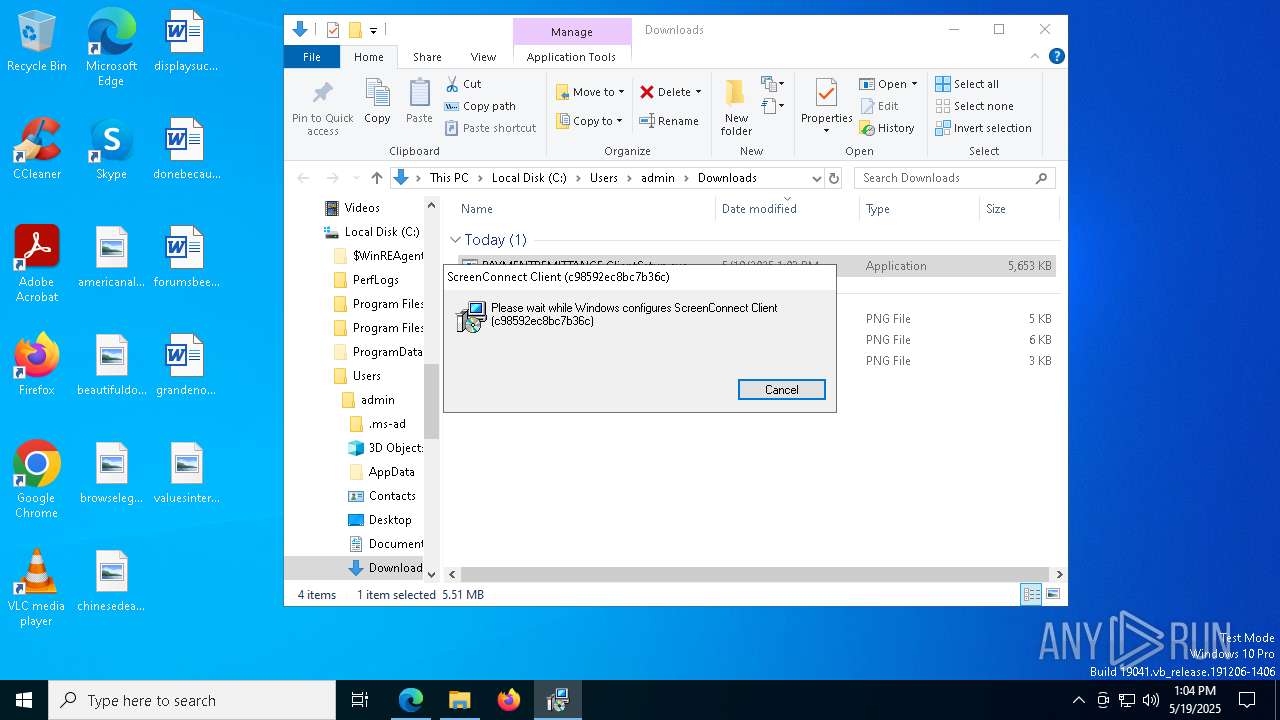
| URL: | https://pqqnscreen.top/Bin/PAYMENTREMITTANCE.ClientSetup.exe?e=Access&y=Guest |
| Full analysis: | https://app.any.run/tasks/6fd0a65f-068c-4ea7-9654-aec687224e8f |
| Verdict: | Malicious activity |
| Analysis date: | May 19, 2025, 13:03:04 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MD5: | A5A585B6E526ACC8429ED2BADBFBAE17 |
| SHA1: | 7B6E3832EA09540D5BE80C86677BB6213C3C46C8 |
| SHA256: | AB9049502B9EF99BA34CB41FA5CFD98A3D9FB2A3419BF1FA63C28ECACDCB76BB |
| SSDEEP: | 3:N8QShAA/sVckbSzne20Qa/GMh:2Q3AvkWzC/G0 |
MALICIOUS
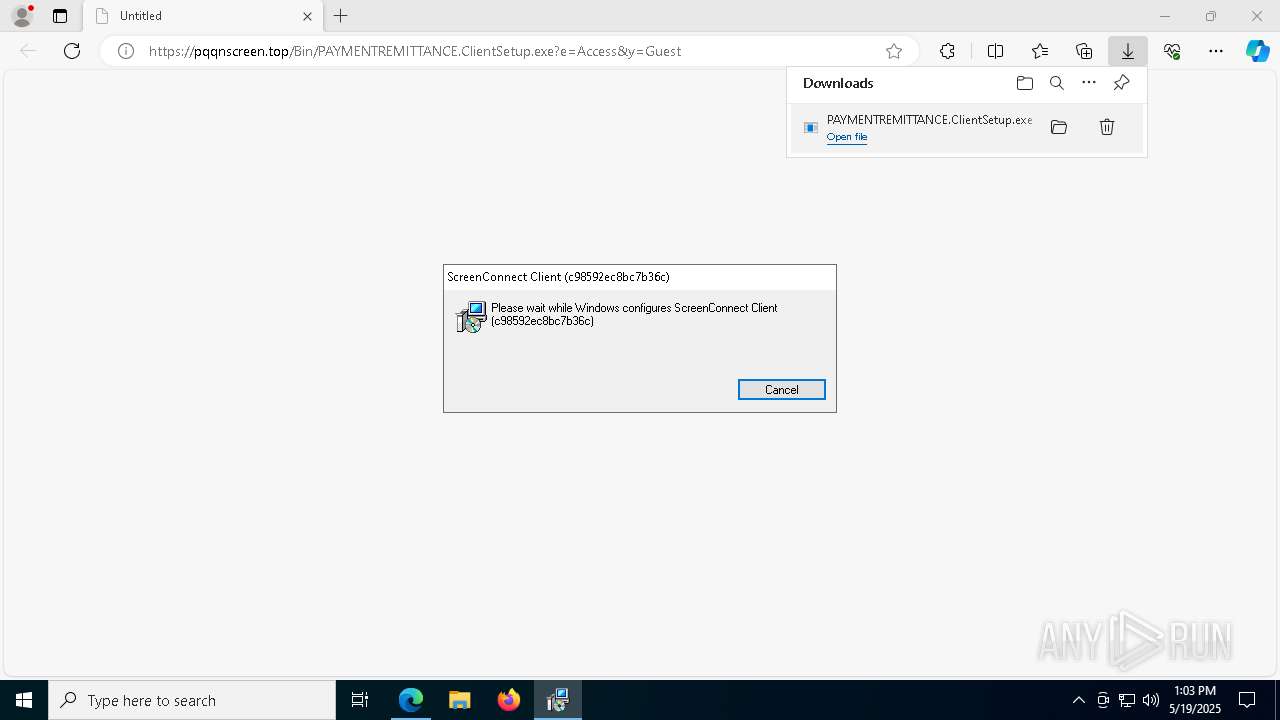
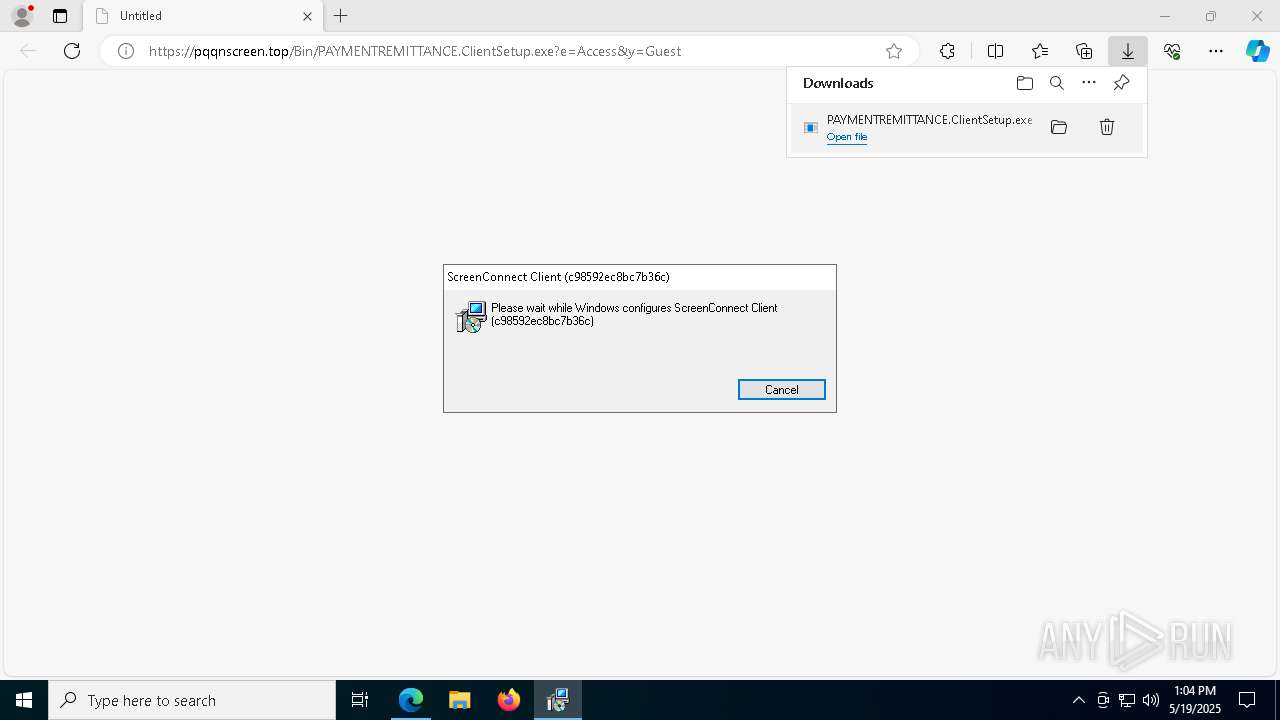
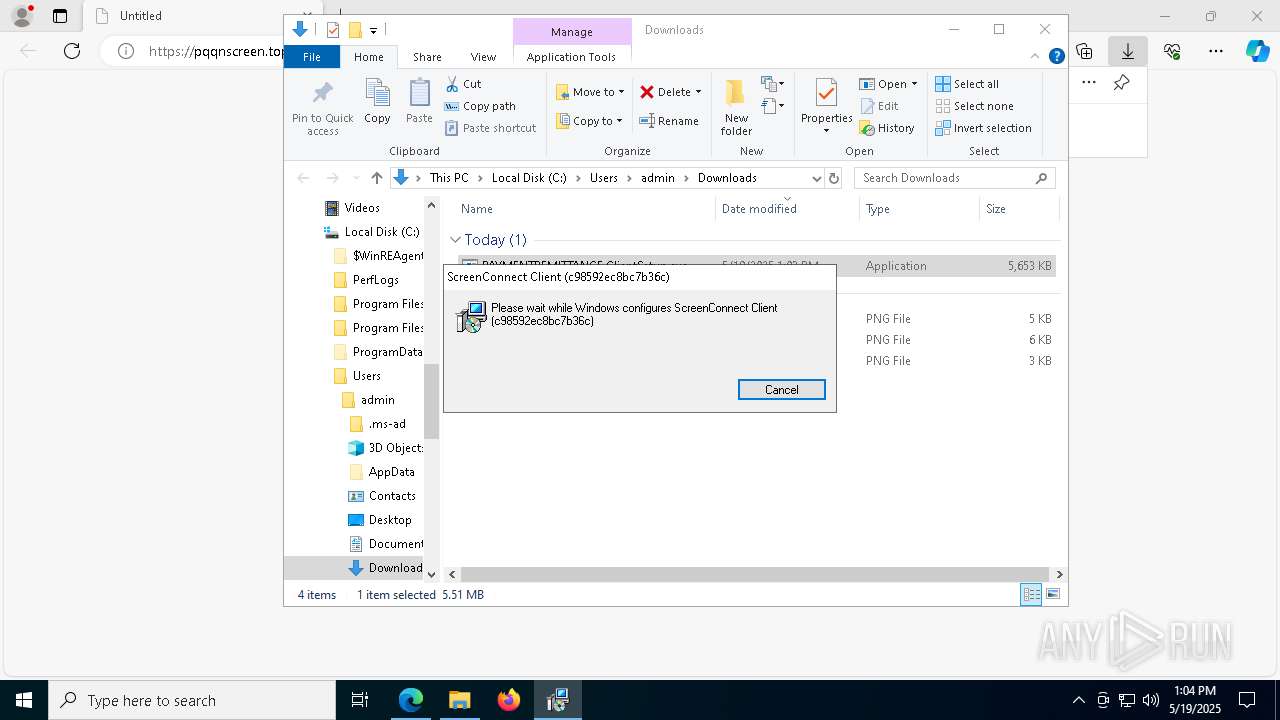
SCREENCONNECT has been detected (SURICATA)
- ScreenConnect.ClientService.exe (PID: 8104)
SUSPICIOUS
Reads security settings of Internet Explorer
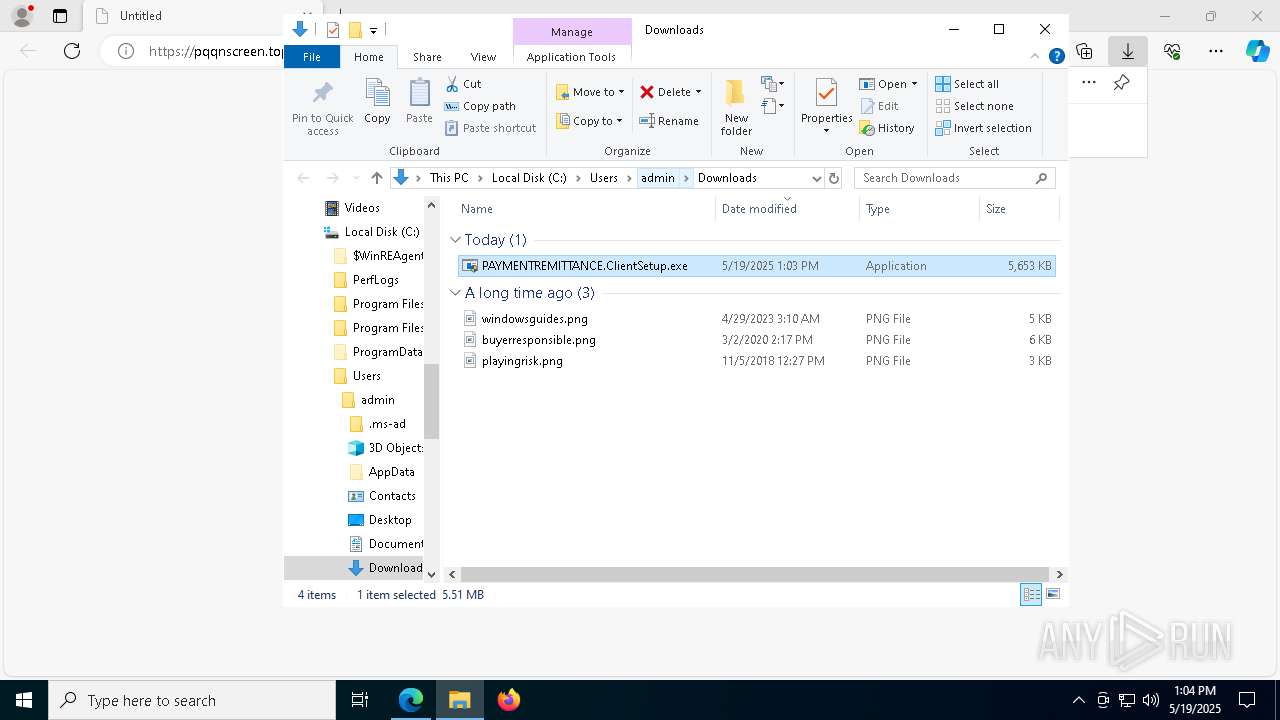
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 1052)
Executable content was dropped or overwritten
- rundll32.exe (PID: 2984)
- rundll32.exe (PID: 3332)
- rundll32.exe (PID: 7872)
- rundll32.exe (PID: 1096)
- rundll32.exe (PID: 7100)
- rundll32.exe (PID: 2596)
- rundll32.exe (PID: 4040)
Executes as Windows Service
- VSSVC.exe (PID: 2340)
- ScreenConnect.ClientService.exe (PID: 8104)
Executes application which crashes
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 5772)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 4988)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 5256)
Potential Corporate Privacy Violation
- ScreenConnect.ClientService.exe (PID: 8104)
Screenconnect has been detected
- ScreenConnect.ClientService.exe (PID: 8104)
Connects to unusual port
- ScreenConnect.ClientService.exe (PID: 8104)
INFO
Application launched itself
- msedge.exe (PID: 2384)
Executable content was dropped or overwritten
- msedge.exe (PID: 2384)
- msedge.exe (PID: 7344)
- msiexec.exe (PID: 3020)
- msiexec.exe (PID: 1628)
- msiexec.exe (PID: 7944)
- msiexec.exe (PID: 5512)
- msiexec.exe (PID: 6476)
- msiexec.exe (PID: 7500)
- msiexec.exe (PID: 5780)
- msedge.exe (PID: 1324)
- msiexec.exe (PID: 5156)
Checks supported languages
- identity_helper.exe (PID: 864)
- msiexec.exe (PID: 5260)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 1052)
- msiexec.exe (PID: 1628)
Reads Environment values
- identity_helper.exe (PID: 864)
Reads the machine GUID from the registry
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 1052)
Reads the computer name
- identity_helper.exe (PID: 864)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 1052)
- msiexec.exe (PID: 1628)
- msiexec.exe (PID: 5260)
Process checks computer location settings
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 1052)
Create files in a temporary directory
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 1052)
- rundll32.exe (PID: 2984)
CONNECTWISE has been detected
- msiexec.exe (PID: 3020)
Manages system restore points
- SrTasks.exe (PID: 3676)
Manual execution by a user
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 4284)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 5232)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 7736)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 8012)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 4180)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 1240)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 7968)
- PAYMENTREMITTANCE.ClientSetup.exe (PID: 5380)
The sample compiled with english language support
- msedge.exe (PID: 1324)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
240
Monitored processes
94
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 664 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5236 --field-trial-handle=2288,i,4861025875300497452,2298004279442187756,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 728 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=6216 --field-trial-handle=2288,i,4861025875300497452,2298004279442187756,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 736 | C:\Windows\syswow64\MsiExec.exe -Embedding 088539D3578E8F0F158FDA76F7C3BAFC C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 864 | "C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe" --type=utility --utility-sub-type=winrt_app_id.mojom.WinrtAppIdService --lang=en-US --service-sandbox-type=none --no-appcompat-clear --mojo-platform-channel-handle=6320 --field-trial-handle=2288,i,4861025875300497452,2298004279442187756,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\122.0.2365.59\identity_helper.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: PWA Identity Proxy Host Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 924 | C:\Windows\syswow64\MsiExec.exe -Embedding D6F83E0963D59176D437DF1DAFDCA106 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 924 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=data_decoder.mojom.DataDecoderService --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5400 --field-trial-handle=2288,i,4861025875300497452,2298004279442187756,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
| 1052 | "C:\Users\admin\Downloads\PAYMENTREMITTANCE.ClientSetup.exe" | C:\Users\admin\Downloads\PAYMENTREMITTANCE.ClientSetup.exe | msedge.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 1096 | rundll32.exe "C:\Users\admin\AppData\Local\Temp\MSIA594.tmp",zzzzInvokeManagedCustomActionOutOfProc SfxCA_1156562 1 ScreenConnect.InstallerActions!ScreenConnect.ClientInstallerActions.FixupServiceArguments | C:\Windows\SysWOW64\rundll32.exe | msiexec.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1228 | "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=unzip.mojom.Unzipper --lang=en-US --service-sandbox-type=service --no-appcompat-clear --mojo-platform-channel-handle=5964 --field-trial-handle=2288,i,4861025875300497452,2298004279442187756,262144 --variations-seed-version /prefetch:8 | C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 122.0.2365.59 Modules
| |||||||||||||||
Total events
28 461
Read events
28 019
Write events
350
Delete events
92
Modification events
| (PID) Process: | (2384) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | failed_count |
Value: 0 | |||
| (PID) Process: | (2384) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 2 | |||
| (PID) Process: | (2384) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\BLBeacon |
| Operation: | write | Name: | state |
Value: 1 | |||
| (PID) Process: | (2384) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Edge\StabilityMetrics |
| Operation: | write | Name: | user_experience_metrics.stability.exited_cleanly |
Value: 0 | |||
| (PID) Process: | (2384) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: BE7AAC0913942F00 | |||
| (PID) Process: | (2384) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: 0F8ABA0913942F00 | |||
| (PID) Process: | (2384) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197390 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {270B6DE7-E055-47D2-B33E-5A4BE231461A} | |||
| (PID) Process: | (2384) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\WindowProperties\197390 |
| Operation: | write | Name: | WindowTabManagerFileMappingId |
Value: {3F7163D6-A248-4331-870B-5DBFD55DAC3C} | |||
| (PID) Process: | (2384) msedge.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Microsoft\EdgeUpdate\ClientStateMedium\{56EB18F8-B008-4CBD-B6D2-8C97FE7E9062}\LastWasDefault |
| Operation: | write | Name: | S-1-5-21-1693682860-607145093-2874071422-1001 |
Value: E3AFF70913942F00 | |||
| (PID) Process: | (2384) msedge.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | MicrosoftEdgeAutoLaunch_29EBC4579851B72EE312C449CF839B1A |
Value: "C:\Program Files (x86)\Microsoft\Edge\Application\msedge.exe" --no-startup-window --win-session-start | |||
Executable files
86
Suspicious files
188
Text files
50
Unknown types
8
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RF10c48a.TMP | — | |
MD5:— | SHA256:— | |||
| 2384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old~RF10c48a.TMP | — | |
MD5:— | SHA256:— | |||
| 2384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RF10c48a.TMP | — | |
MD5:— | SHA256:— | |||
| 2384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\discounts_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old~RF10c48a.TMP | — | |
MD5:— | SHA256:— | |||
| 2384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\parcel_tracking_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 2384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old~RF10c4a9.TMP | — | |
MD5:— | SHA256:— | |||
| 2384 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\PersistentOriginTrials\LOG.old | — | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
23
TCP/UDP connections
50
DNS requests
50
Threats
2
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5496 | MoUsoCoreWorker.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
8004 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
1040 | svchost.exe | HEAD | 200 | 208.89.74.19:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/3aeadfbf-fadd-43ac-a5d9-c143db5f63d8?P1=1747694795&P2=404&P3=2&P4=QAz%2fZ5Y5yB0AeQsz%2b%2bLvVmHUIB8SuOHCOvWLiXoVD4CFtT46jswFp5kysp%2bqtY3ChBecDKvstGZaJYIuqJDICw%3d%3d | unknown | — | — | whitelisted |
1040 | svchost.exe | GET | 206 | 208.89.74.19:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/3aeadfbf-fadd-43ac-a5d9-c143db5f63d8?P1=1747694795&P2=404&P3=2&P4=QAz%2fZ5Y5yB0AeQsz%2b%2bLvVmHUIB8SuOHCOvWLiXoVD4CFtT46jswFp5kysp%2bqtY3ChBecDKvstGZaJYIuqJDICw%3d%3d | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
1040 | svchost.exe | GET | 206 | 208.89.74.19:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/3aeadfbf-fadd-43ac-a5d9-c143db5f63d8?P1=1747694795&P2=404&P3=2&P4=QAz%2fZ5Y5yB0AeQsz%2b%2bLvVmHUIB8SuOHCOvWLiXoVD4CFtT46jswFp5kysp%2bqtY3ChBecDKvstGZaJYIuqJDICw%3d%3d | unknown | — | — | whitelisted |
8004 | SIHClient.exe | GET | 200 | 23.35.229.160:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
1040 | svchost.exe | GET | 206 | 208.89.74.19:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/3aeadfbf-fadd-43ac-a5d9-c143db5f63d8?P1=1747694795&P2=404&P3=2&P4=QAz%2fZ5Y5yB0AeQsz%2b%2bLvVmHUIB8SuOHCOvWLiXoVD4CFtT46jswFp5kysp%2bqtY3ChBecDKvstGZaJYIuqJDICw%3d%3d | unknown | — | — | whitelisted |
1040 | svchost.exe | HEAD | 200 | 208.89.74.19:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1747694794&P2=404&P3=2&P4=PSMdiqydUFpssZ4gopAklnatfOzk8DzYWqglQG%2bb19mJGUVOz8%2f3SVVjvWVq7%2bWb539ZBqfNONhJTKYrGL2kSA%3d%3d | unknown | — | — | whitelisted |
1040 | svchost.exe | GET | 206 | 208.89.74.19:80 | http://msedge.b.tlu.dl.delivery.mp.microsoft.com/filestreamingservice/files/84d3e481-77df-49da-bc37-0a994069ddb9?P1=1747694794&P2=404&P3=2&P4=PSMdiqydUFpssZ4gopAklnatfOzk8DzYWqglQG%2bb19mJGUVOz8%2f3SVVjvWVq7%2bWb539ZBqfNONhJTKYrGL2kSA%3d%3d | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
5496 | MoUsoCoreWorker.exe | 23.35.229.160:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
7344 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2384 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
7344 | msedge.exe | 104.21.20.221:443 | pqqnscreen.top | — | — | unknown |
7344 | msedge.exe | 150.171.27.11:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
7344 | msedge.exe | 13.107.253.45:443 | edge-mobile-static.azureedge.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
edge-mobile-static.azureedge.net |
| whitelisted |
pqqnscreen.top |
| unknown |
business.bing.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
7344 | msedge.exe | Potentially Bad Traffic | ET DNS Query to a *.top domain - Likely Hostile |
8104 | ScreenConnect.ClientService.exe | Potential Corporate Privacy Violation | REMOTE [ANY.RUN] ScreenConnect Server Response |