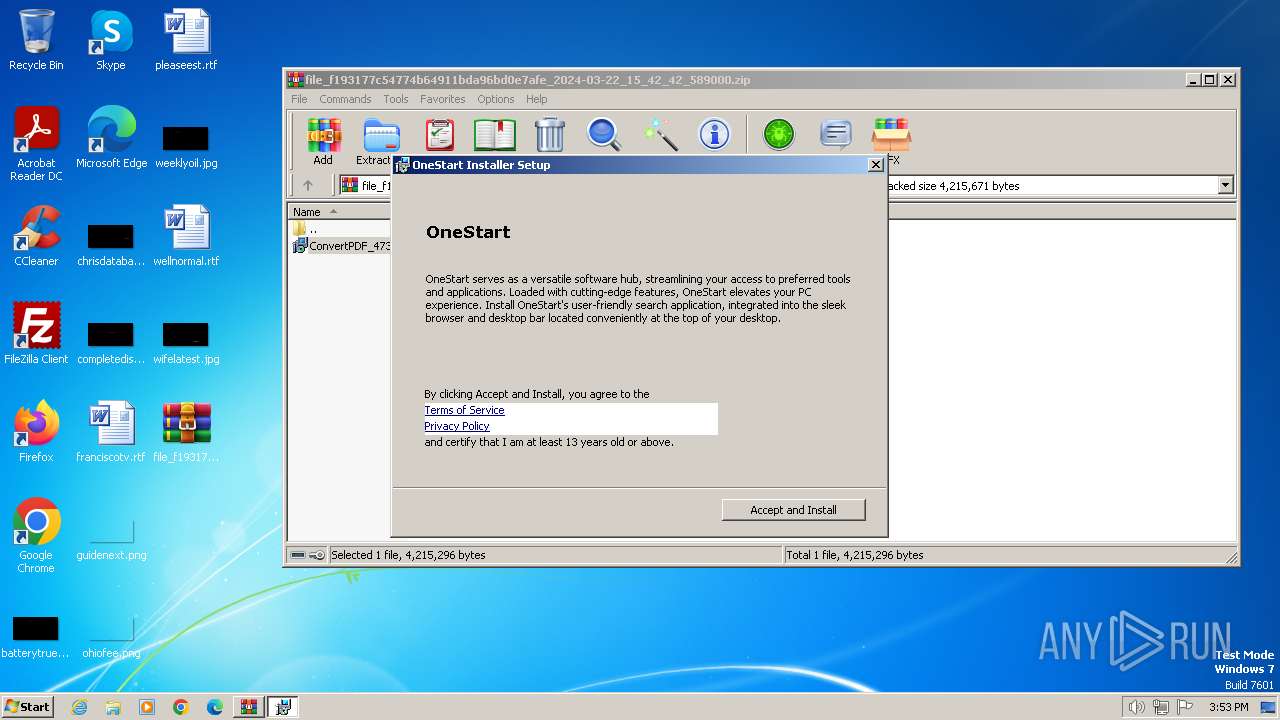
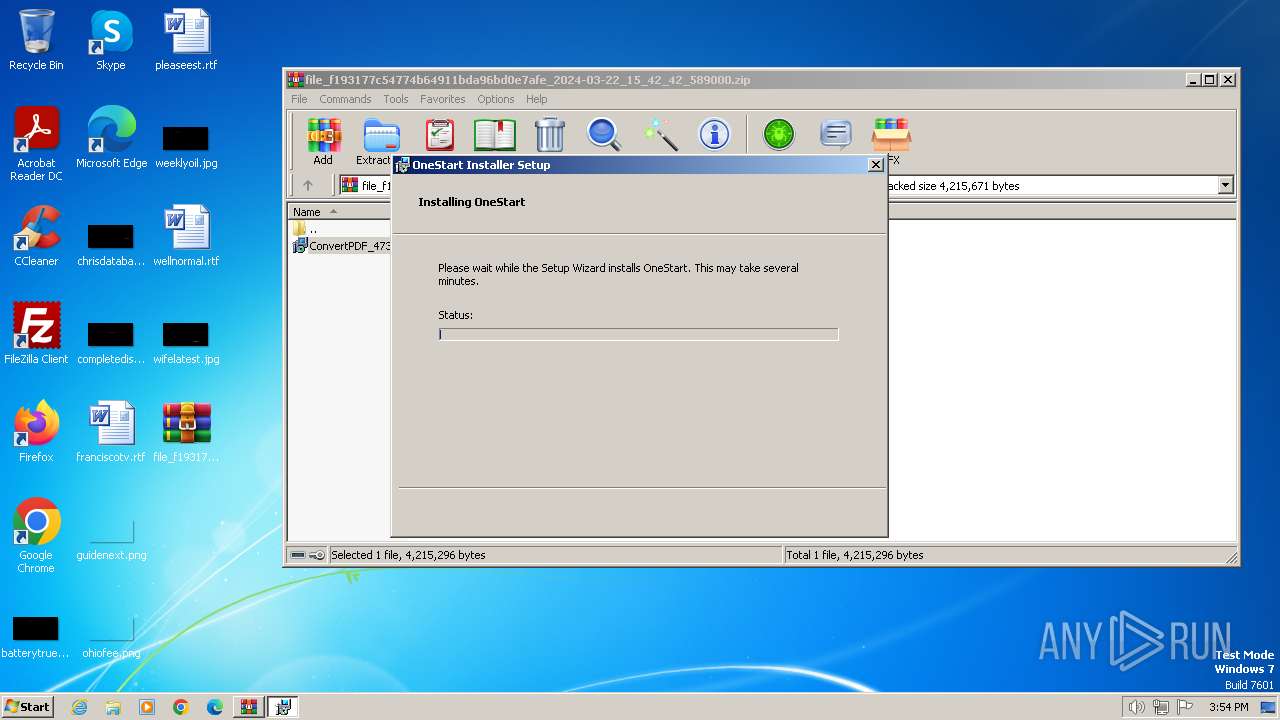
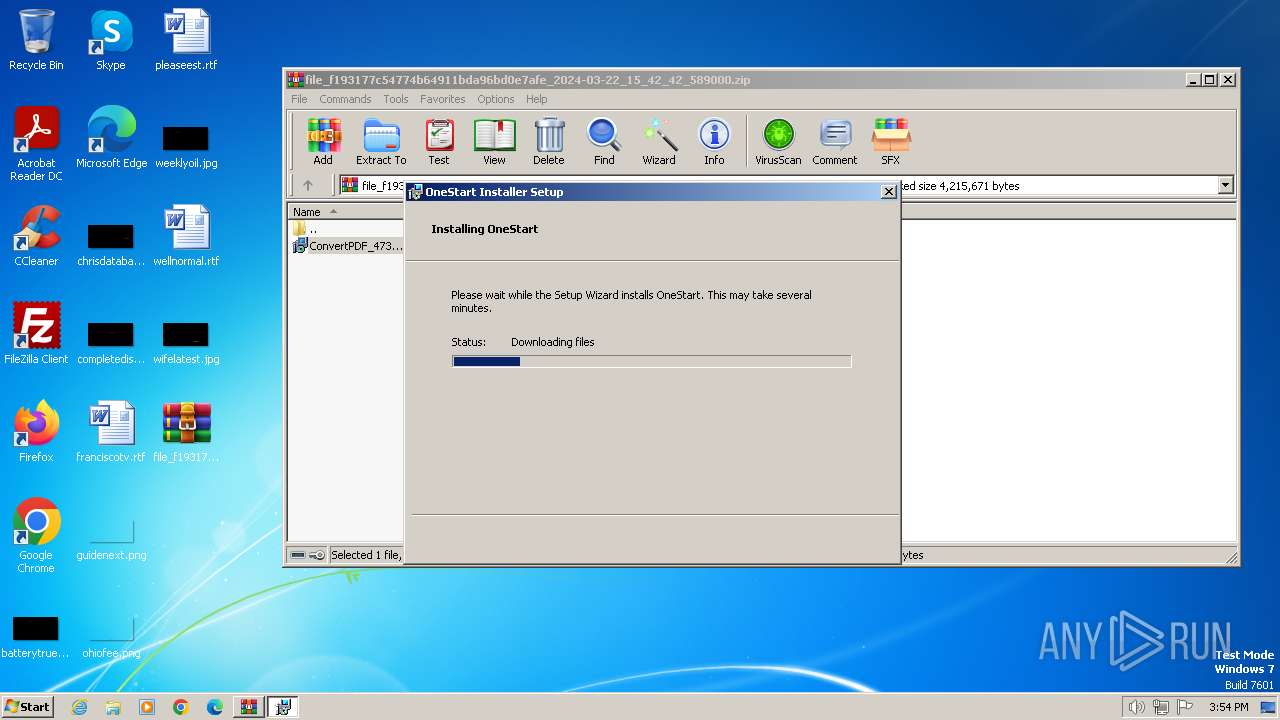
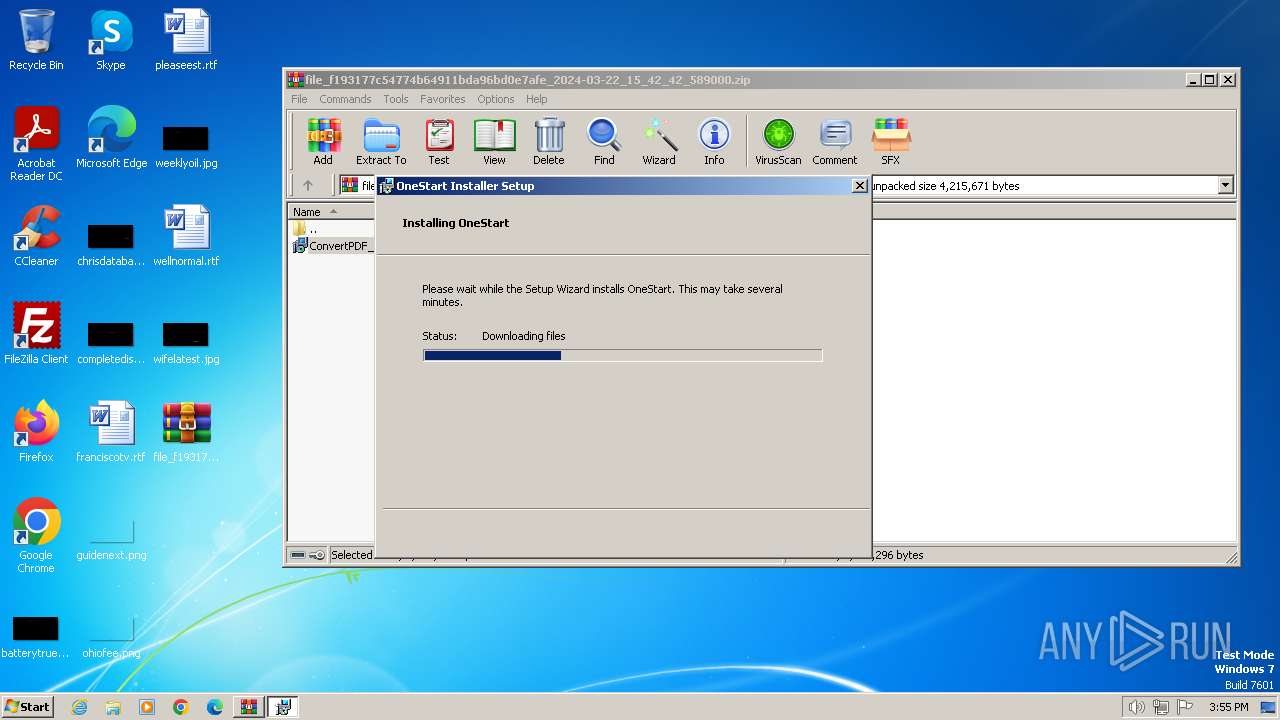
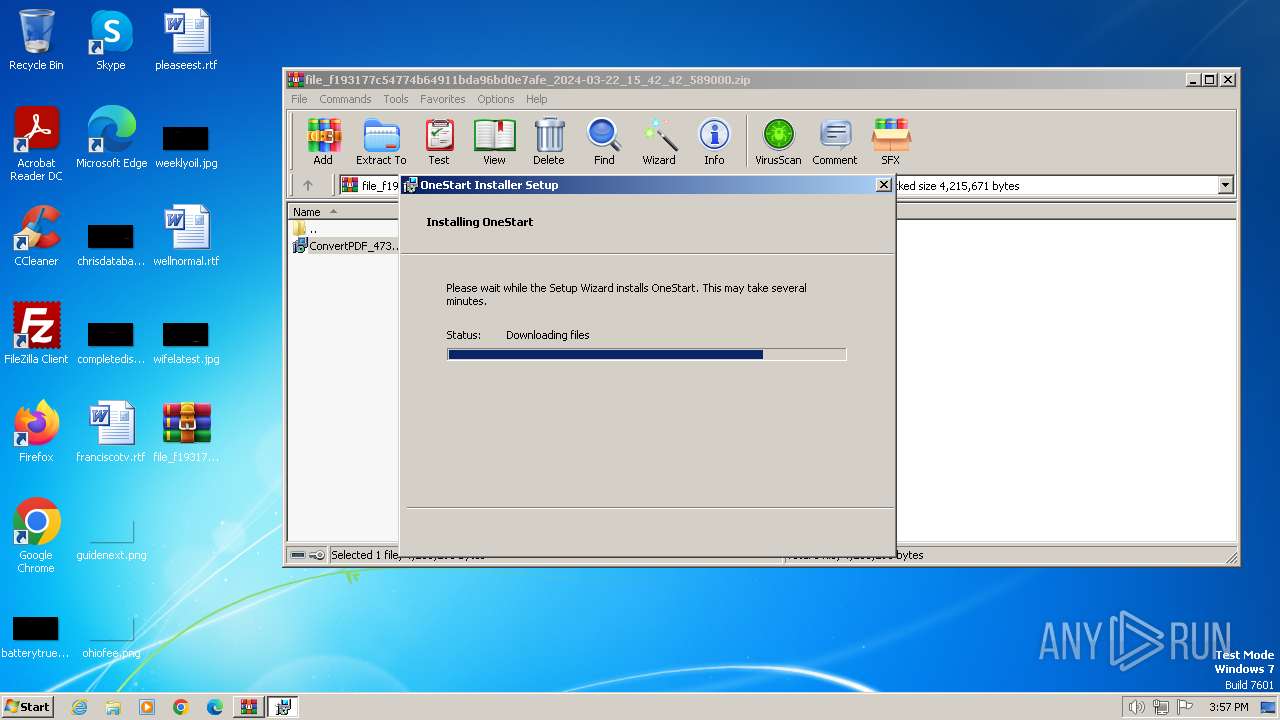
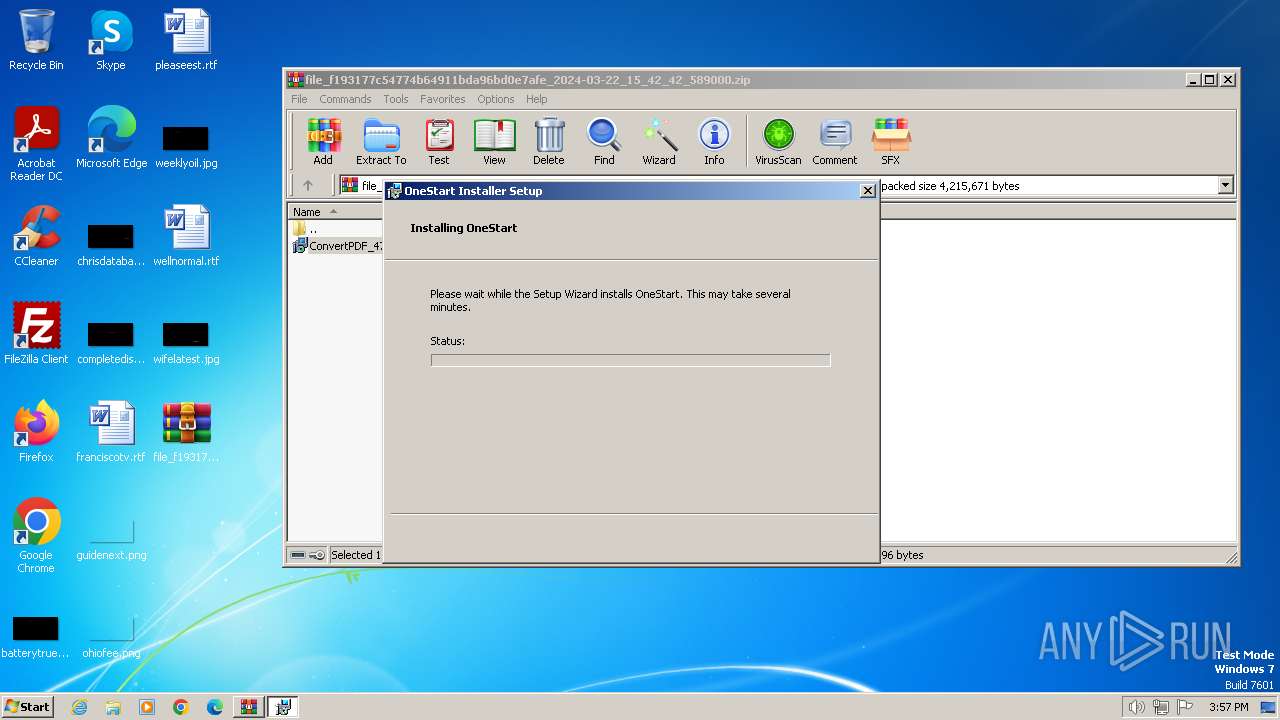
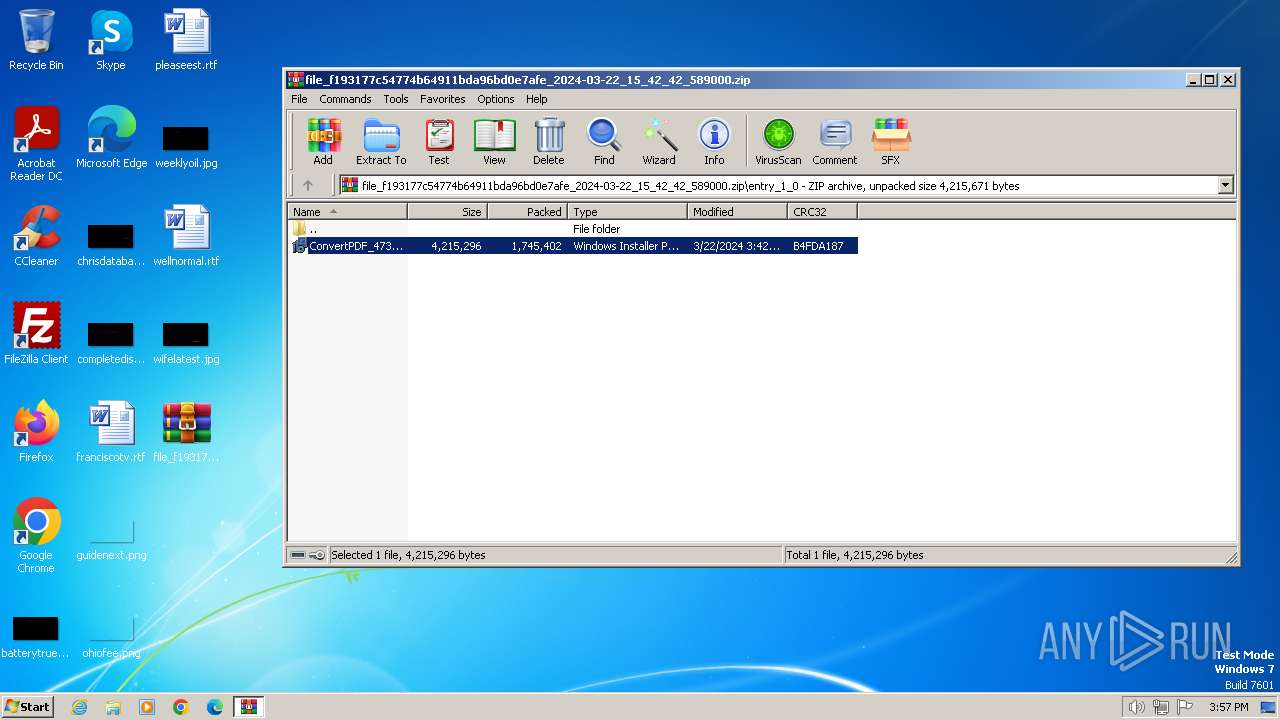
| File name: | file_f193177c54774b64911bda96bd0e7afe_2024-03-22_15_42_42_589000.zip |
| Full analysis: | https://app.any.run/tasks/6667748d-e02c-42ab-9676-e620b7106192 |
| Verdict: | Malicious activity |
| Analysis date: | March 22, 2024, 15:53:39 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=deflate |
| MD5: | 64048182254D24AF1630A8E1673DB039 |
| SHA1: | 9CA424CE04354F961C6A3FC529156C5CD73D34D8 |
| SHA256: | AB882B85082EC2BB88B8E445682CDDD5D01ACD5221A6234121C3DD03128F950C |
| SSDEEP: | 98304:gibFR2dWE5RDDJFlvvkxhxUHzA6dZuPxuuv3ZktY8CB1i4c0SQDDrgjQosMguxvl:UoT5C |
MALICIOUS
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3992)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3992)
Executes as Windows Service
- VSSVC.exe (PID: 3544)
INFO
Executable content was dropped or overwritten
- msiexec.exe (PID: 2692)
Reads the software policy settings
- msiexec.exe (PID: 2692)
Reads security settings of Internet Explorer
- msiexec.exe (PID: 2692)
Drops the executable file immediately after the start
- msiexec.exe (PID: 2692)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | Deflated |
| ZipModifyDate: | 2024:03:22 15:42:44 |
| ZipCRC: | 0xe64f0037 |
| ZipCompressedSize: | 222 |
| ZipUncompressedSize: | 375 |
| ZipFileName: | manifest.json |
Total processes
57
Monitored processes
3
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2692 | "C:\Windows\System32\msiexec.exe" /i "C:\Users\admin\AppData\Local\Temp\Rar$EXa3992.31704\entry_1_0\ConvertPDF_47314555.msi" | C:\Windows\System32\msiexec.exe | WinRAR.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3544 | C:\Windows\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3992 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\Desktop\file_f193177c54774b64911bda96bd0e7afe_2024-03-22_15_42_42_589000.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
Total events
7 896
Read events
7 743
Write events
153
Delete events
0
Modification events
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\file_f193177c54774b64911bda96bd0e7afe_2024-03-22_15_42_42_589000.zip | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3992) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
14
Suspicious files
0
Text files
1
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3992.31704\entry_1_0\ConvertPDF_47314555.msi | — | |
MD5:— | SHA256:— | |||
| 2692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI3C3C.tmp | executable | |
MD5:BE5389608D3421D962BF9042BEE3E734 | SHA256:4B29B8DF4E3A7AEAF4CF33DAABC53DF8FB2DD099C7A215FB445B9E8EF050F558 | |||
| 2692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI3BEC.tmp | executable | |
MD5:36CD2870D577FF917BA93C9F50F86374 | SHA256:8D3E94C47AF3DA706A9FE9E4428B2FEFD5E9E6C7145E96927FFFDF3DD5E472B8 | |||
| 2692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI4A58.tmp | executable | |
MD5:7E4EF4BC701A5F46A1FEE1A9FDC403F1 | SHA256:34FE948E2B005A424F4E8AFF9D9EF847D5623B99196FE5F5E9BFF4983770D95A | |||
| 2692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSIC355.tmp | executable | |
MD5:BE5389608D3421D962BF9042BEE3E734 | SHA256:4B29B8DF4E3A7AEAF4CF33DAABC53DF8FB2DD099C7A215FB445B9E8EF050F558 | |||
| 2692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI4AB8.tmp | executable | |
MD5:36CD2870D577FF917BA93C9F50F86374 | SHA256:8D3E94C47AF3DA706A9FE9E4428B2FEFD5E9E6C7145E96927FFFDF3DD5E472B8 | |||
| 2692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI4372.tmp | executable | |
MD5:BE5389608D3421D962BF9042BEE3E734 | SHA256:4B29B8DF4E3A7AEAF4CF33DAABC53DF8FB2DD099C7A215FB445B9E8EF050F558 | |||
| 2692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI3B9D.tmp | executable | |
MD5:36CD2870D577FF917BA93C9F50F86374 | SHA256:8D3E94C47AF3DA706A9FE9E4428B2FEFD5E9E6C7145E96927FFFDF3DD5E472B8 | |||
| 2692 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI3C0C.tmp | executable | |
MD5:36CD2870D577FF917BA93C9F50F86374 | SHA256:8D3E94C47AF3DA706A9FE9E4428B2FEFD5E9E6C7145E96927FFFDF3DD5E472B8 | |||
| 3992 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3992.31704\manifest.json | text | |
MD5:D6704E1FB5165545E757C466897DF0E5 | SHA256:A0A7C08411C250B5D8EB5A2F0F749958AD7FADAC30AAD567672D8C99B05EB1DB | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
6
TCP/UDP connections
10
DNS requests
3
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1576 | powershell.exe | POST | 200 | 108.138.24.54:80 | http://dpseqd9pkrc26.cloudfront.net/ | unknown | binary | 19 b | unknown |
992 | msiexec.exe | GET | — | 143.204.102.79:80 | http://d1d5z5o20zse2h.cloudfront.net/onestart_installer_prod.exe | unknown | — | — | unknown |
992 | msiexec.exe | GET | — | 143.204.102.79:80 | http://d1d5z5o20zse2h.cloudfront.net/onestart_installer_prod.exe | unknown | — | — | unknown |
992 | msiexec.exe | GET | — | 143.204.102.79:80 | http://d1d5z5o20zse2h.cloudfront.net/onestart_installer_prod.exe | unknown | — | — | unknown |
992 | msiexec.exe | GET | 206 | 143.204.102.79:80 | http://d1d5z5o20zse2h.cloudfront.net/onestart_installer_prod.exe | unknown | binary | 19.9 Mb | unknown |
2612 | powershell.exe | POST | 200 | 108.138.24.54:80 | http://dpseqd9pkrc26.cloudfront.net/ | unknown | binary | 19 b | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | unknown |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
1576 | powershell.exe | 108.138.24.54:80 | dpseqd9pkrc26.cloudfront.net | AMAZON-02 | US | unknown |
992 | msiexec.exe | 143.204.102.79:80 | d1d5z5o20zse2h.cloudfront.net | AMAZON-02 | US | unknown |
2612 | powershell.exe | 108.138.24.54:80 | dpseqd9pkrc26.cloudfront.net | AMAZON-02 | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
dpseqd9pkrc26.cloudfront.net |
| unknown |
d1d5z5o20zse2h.cloudfront.net |
| unknown |
Threats
PID | Process | Class | Message |
|---|---|---|---|
992 | msiexec.exe | Potentially Bad Traffic | ET POLICY Executable served from Amazon S3 |
992 | msiexec.exe | Potential Corporate Privacy Violation | ET POLICY PE EXE or DLL Windows file download HTTP |
4 ETPRO signatures available at the full report