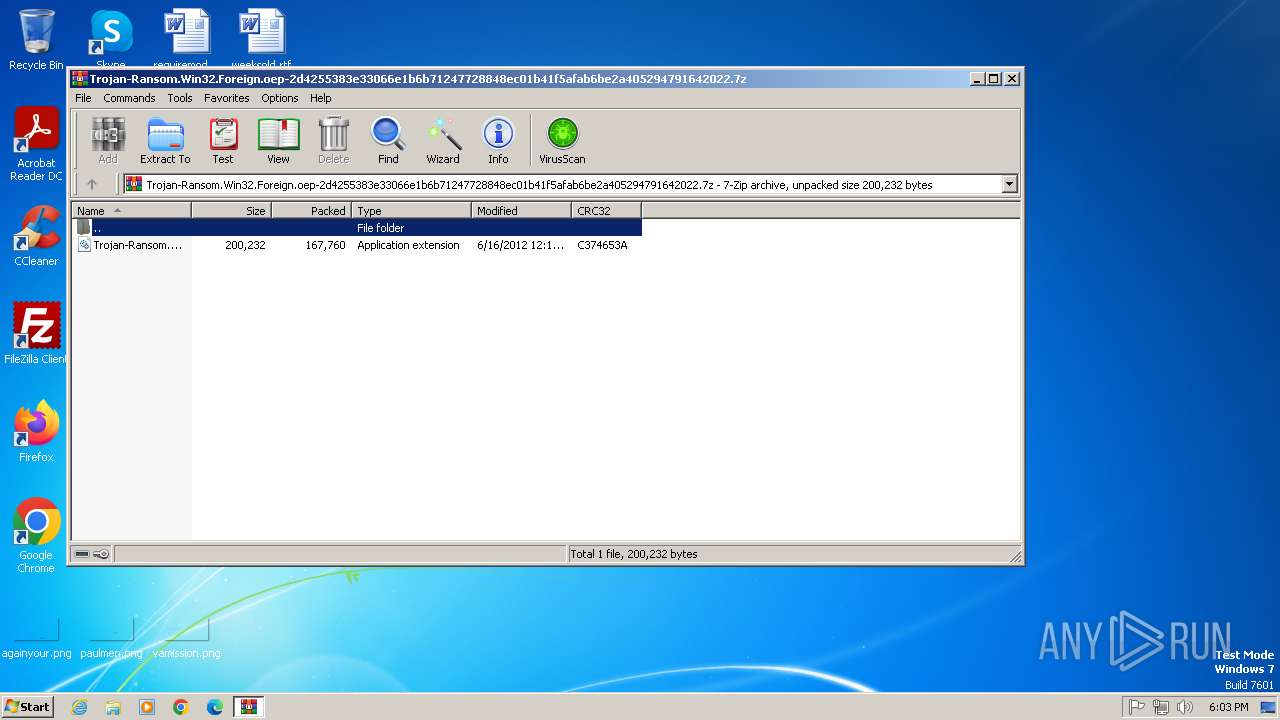
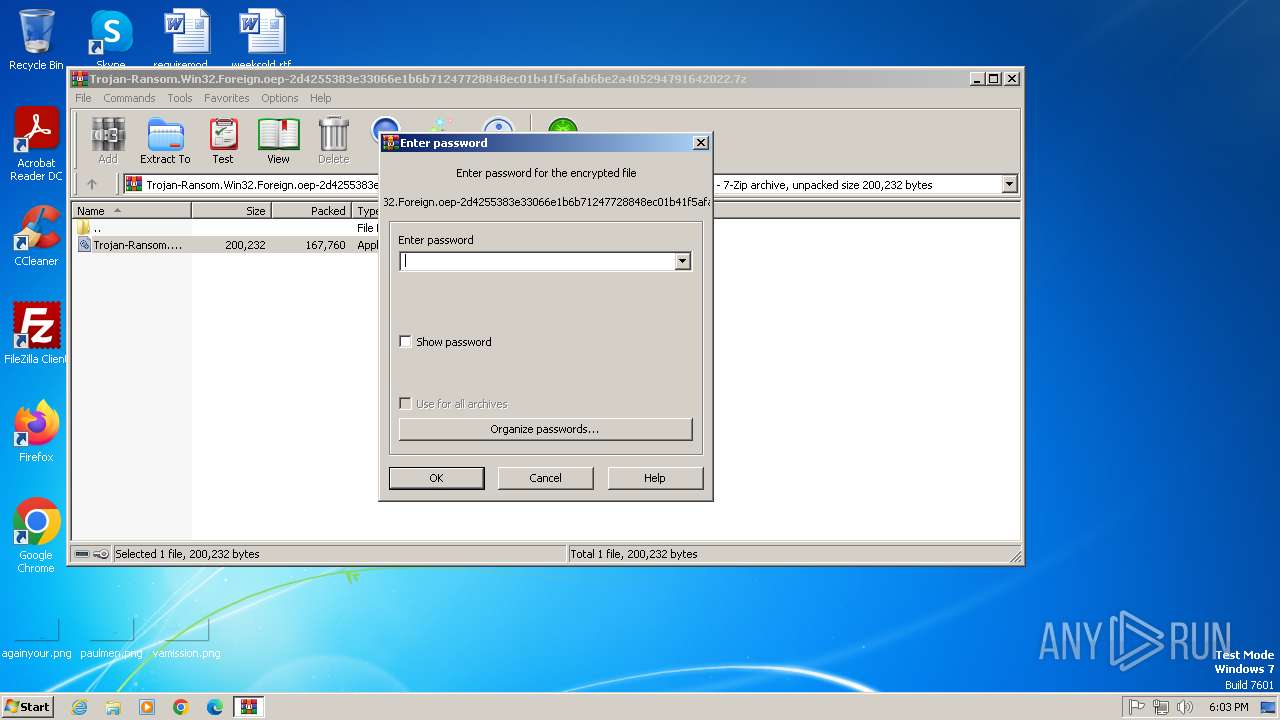
| File name: | Trojan-Ransom.Win32.Foreign.oep-2d4255383e33066e1b6b71247728848ec01b41f5afab6be2a405294791642022.7z |
| Full analysis: | https://app.any.run/tasks/3e49573f-e487-4a48-89a4-cb65c2a19cf9 |
| Verdict: | Malicious activity |
| Analysis date: | April 19, 2025, 17:03:16 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-7z-compressed |
| File info: | 7-zip archive data, version 0.4 |
| MD5: | 4D98714A63D5B398709723A6DA526362 |
| SHA1: | 78D71AB1B3EA69F5AD589D63BC128154F506EFA1 |
| SHA256: | AB83768372B9E3172F3E84062123A0EFFC314370092B01976C39ACE0573A0BA2 |
| SSDEEP: | 3072:pAaFpeZqxrD7eqjIhsoIxwqC9EK6nEZdZ7sWumqYx/EKc8LqsC0OnIKyYFXQxX1m:7OZqt3jIgxwlEK0EZdnZNpLqsgIYqxlm |
MALICIOUS
Disables task manager
- rundll32.exe (PID: 3800)
- notepad.exe (PID: 3296)
- iexplore.exe (PID: 3204)
- notepad.exe (PID: 4072)
Create files in the Startup directory
- rundll32.exe (PID: 3800)
Task Manager has been disabled (taskmgr)
- notepad.exe (PID: 3296)
- notepad.exe (PID: 4072)
- iexplore.exe (PID: 3204)
SUSPICIOUS
Reads the date of Windows installation
- pwsh.exe (PID: 2652)
Starts CMD.EXE for commands execution
- pwsh.exe (PID: 2652)
Uses RUNDLL32.EXE to load library
- cmd.exe (PID: 2956)
Changes internet zones settings
- notepad.exe (PID: 3296)
- rundll32.exe (PID: 3800)
- notepad.exe (PID: 4072)
INFO
Checks supported languages
- pwsh.exe (PID: 2652)
Reads the computer name
- pwsh.exe (PID: 2652)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 2692)
Creates files or folders in the user directory
- rundll32.exe (PID: 3800)
Application launched itself
- iexplore.exe (PID: 3204)
Manual execution by a user
- pwsh.exe (PID: 2652)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .7z | | | 7-Zip compressed archive (v0.4) (57.1) |
|---|---|---|
| .7z | | | 7-Zip compressed archive (gen) (42.8) |
EXIF
ZIP
| FileVersion: | 7z v0.04 |
|---|---|
| ModifyDate: | 2012:06:16 11:19:20+00:00 |
| ArchivedFileName: | Trojan-Ransom.Win32.Foreign.oep-2d4255383e33066e1b6b71247728848ec01b41f5afab6be2a405294791642022.dll |
Total processes
51
Monitored processes
9
Malicious processes
6
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2652 | "C:\Program Files\PowerShell\7\pwsh.exe" -WorkingDirectory ~ | C:\Program Files\PowerShell\7\pwsh.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: pwsh Version: 7.2.11.500 Modules
| |||||||||||||||
| 2692 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\Trojan-Ransom.Win32.Foreign.oep-2d4255383e33066e1b6b71247728848ec01b41f5afab6be2a405294791642022.7z | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 2956 | "C:\Windows\system32\cmd.exe" | C:\Windows\System32\cmd.exe | — | pwsh.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Command Processor Version: 6.1.7601.17514 (win7sp1_rtm.101119-1850) Modules
| |||||||||||||||
| 2992 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:3204 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3204 | "C:\Program Files\Internet Explorer\iexplore.exe" -Embedding | C:\Program Files\Internet Explorer\iexplore.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3296 | notepad.exe | C:\Windows\System32\notepad.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3632 | explorer.exe | C:\Windows\explorer.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows Explorer Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 3800 | rundll32 a.dll, #1 | C:\Windows\System32\rundll32.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 4072 | notepad.exe | C:\Windows\System32\notepad.exe | — | rundll32.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Notepad Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
22 634
Read events
22 292
Write events
324
Delete events
18
Modification events
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\Trojan-Ransom.Win32.Foreign.oep-2d4255383e33066e1b6b71247728848ec01b41f5afab6be2a405294791642022.7z | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2692) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
1
Suspicious files
7
Text files
3
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2652 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\7.2.11\update1_v7.5.0_2025-01-23 | — | |
MD5:— | SHA256:— | |||
| 2652 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_0u05lwhy.rpb.ps1 | text | |
MD5:1502353AA88DE581E87DA70A4A16FA59 | SHA256:4A6C3C5EB717C24D8DFB687C988BFD262063C266C6F624092A3294A397306E13 | |||
| 2652 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\PowerShell\PSReadLine\ConsoleHost_history.txt | text | |
MD5:C8DDA74C4EDB47A4041CF6F601E063E3 | SHA256:9FE87E55A1B1EEC04D5431F7BCAC738F155319D310690038A4108274991D75D5 | |||
| 3800 | rundll32.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\a.dll.lnk | binary | |
MD5:5B1ECE85696748FA266B7961489211E5 | SHA256:CBC46E8734A3DFEAF030782D1655778137BABD355D0EEFE11E342E23F9FE6C10 | |||
| 3204 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:B52DD8AD45A837013069F181574C2532 | SHA256:CE3505CE15C4B84039ED1D5FD2153AE3EE880E0F30A2093DC1F1D897F22F38F1 | |||
| 2652 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\RW5Y9W3CI5T3WBMJEZWL.temp | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
| 2652 | pwsh.exe | C:\Users\admin\AppData\Local\Temp\__PSScriptPolicyTest_duvka5xg.1se.psm1 | text | |
MD5:1502353AA88DE581E87DA70A4A16FA59 | SHA256:4A6C3C5EB717C24D8DFB687C988BFD262063C266C6F624092A3294A397306E13 | |||
| 2692 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb2692.1226\Trojan-Ransom.Win32.Foreign.oep-2d4255383e33066e1b6b71247728848ec01b41f5afab6be2a405294791642022.dll | executable | |
MD5:66FCFA90B354B5022CC9F1E8ACF6D655 | SHA256:2D4255383E33066E1B6B71247728848EC01B41F5AFAB6BE2A405294791642022 | |||
| 2652 | pwsh.exe | C:\Users\admin\AppData\Local\Microsoft\PowerShell\StartupProfileData-Interactive | binary | |
MD5:A38AE9F36E51E9621D0AD589FDD91C45 | SHA256:E0883D68C9A7C96767EFD3DB8637C3372A16C7644FA43B147342ADA8380E8F70 | |||
| 2652 | pwsh.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\e1a648060a327b80.customDestinations-ms~RF187c8e.TMP | binary | |
MD5:A20A86C096ADCB3F2B94729E95AC8359 | SHA256:9B6C50119EFA806C4BD1CD2C2B0A8524F261AA19EC2B882AD52677A2A0ADC273 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
16
DNS requests
9
Threats
1
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3204 | iexplore.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?b9a76800a9b7dc19 | unknown | — | — | whitelisted |
3204 | iexplore.exe | GET | 200 | 23.50.131.200:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?653aa7bc651cdf0a | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
— | — | 224.0.0.252:5355 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
2652 | pwsh.exe | 23.193.246.7:443 | aka.ms | Akamai International B.V. | MX | whitelisted |
2652 | pwsh.exe | 13.107.246.45:443 | powershellinfraartifacts-gkhedzdeaghdezhr.z01.azurefd.net | MICROSOFT-CORP-MSN-AS-BLOCK | US | malicious |
2992 | iexplore.exe | 91.195.254.35:80 | — | WEB LLC | AM | unknown |
3204 | iexplore.exe | 92.123.104.32:443 | www.bing.com | Akamai International B.V. | DE | whitelisted |
3204 | iexplore.exe | 23.50.131.200:80 | ctldl.windowsupdate.com | Akamai International B.V. | DE | whitelisted |
2652 | pwsh.exe | 20.50.88.244:443 | dc.services.visualstudio.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
google.com |
| whitelisted |
aka.ms |
| whitelisted |
powershellinfraartifacts-gkhedzdeaghdezhr.z01.azurefd.net |
| unknown |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
ctldl.windowsupdate.com |
| whitelisted |
dc.services.visualstudio.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2652 | pwsh.exe | Not Suspicious Traffic | INFO [ANY.RUN] Azure Front Door domain observed in TLS SNI ( .azurefd .net) |
Process | Message |
|---|---|
pwsh.exe | Profiler was prevented from loading notification profiler due to app settings.
Process ID (decimal): 2652. Message ID: [0x2509].
|