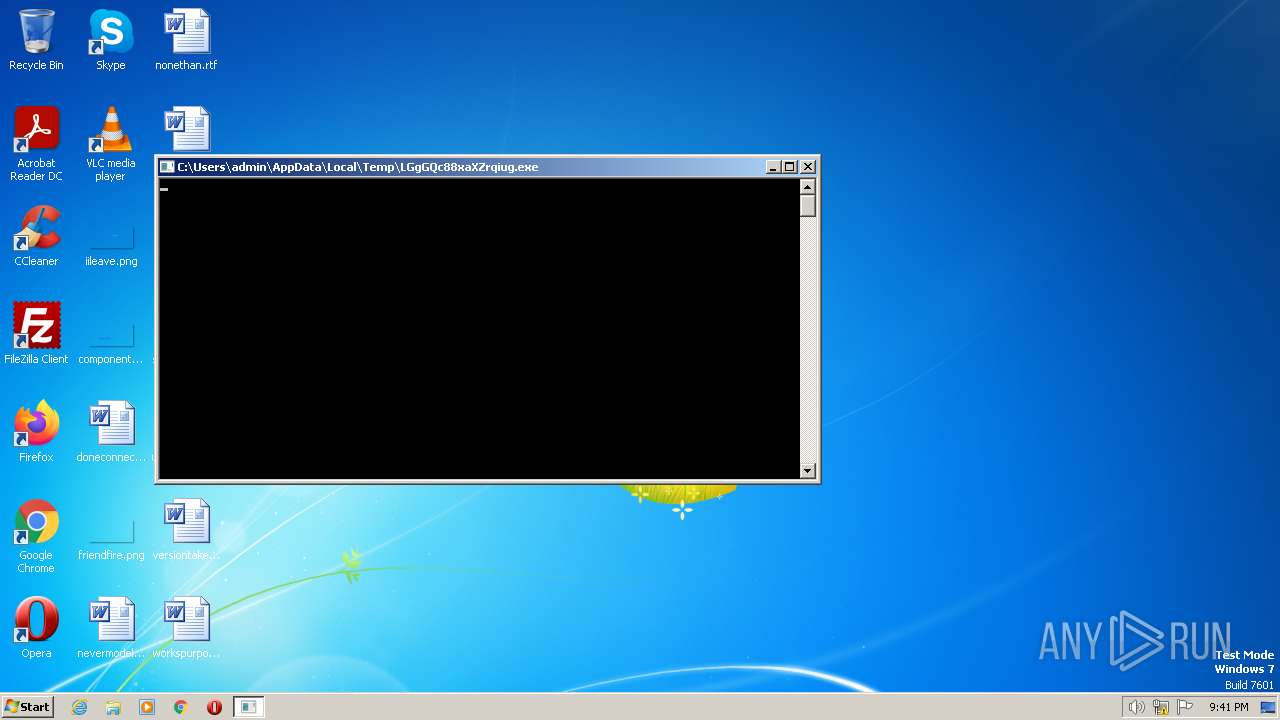
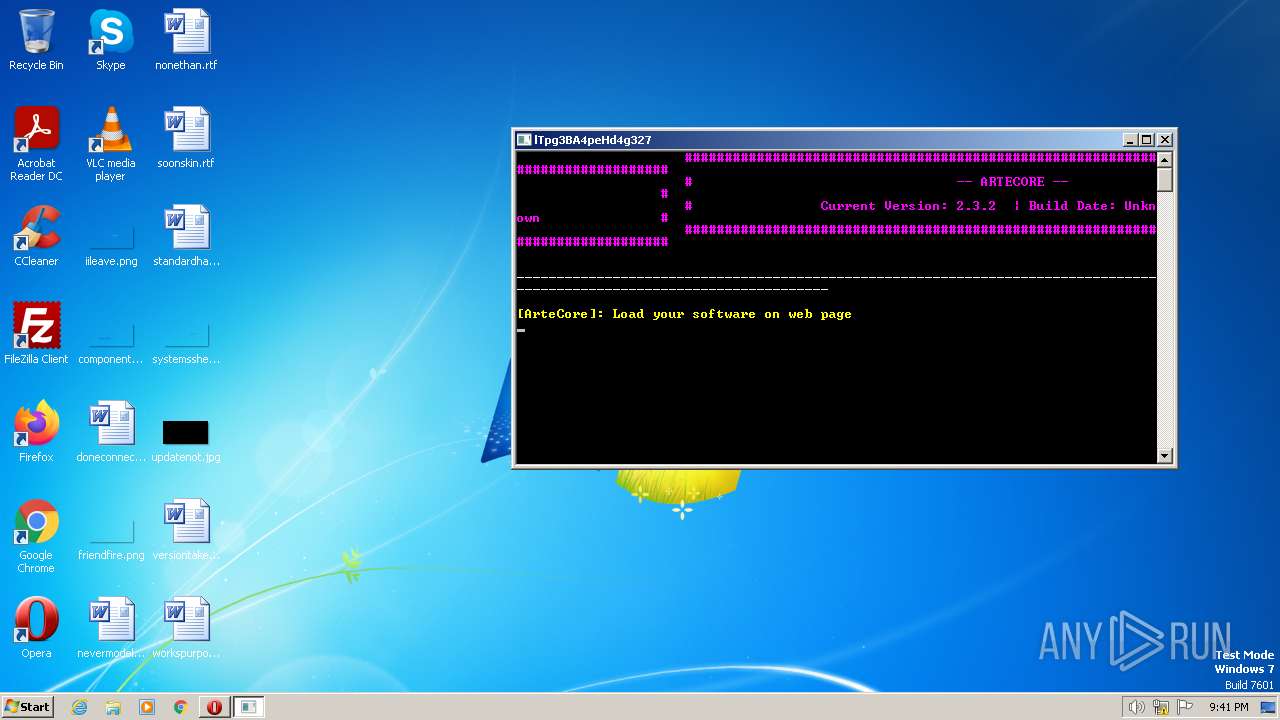
| File name: | LGgGQc88xaXZrqiug.exe |
| Full analysis: | https://app.any.run/tasks/a182b7a2-1c9e-4627-8215-9850d703effe |
| Verdict: | Malicious activity |
| Analysis date: | June 04, 2023, 20:41:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386, for MS Windows |
| MD5: | 28CB217D6565BE3D524C85C081F3D2AB |
| SHA1: | 20F33AD5CA5F1101987A9A950E538BF22EDA174F |
| SHA256: | AB4BE240A98C7BC132723842274182D5595F79B7C08CDF53DE7107DFFBC381A5 |
| SSDEEP: | 98304:Y/EiBPOgoT1ZkG3Y8S9bkcW15ExuBPy7DrabFgmgdF9ibOp7Uw9pBRPwhw:Y/E2O6p8S2NCey7a9gLEpqRPY |
MALICIOUS
Disables Windows Defender
- LGgGQc88xaXZrqiug.exe (PID: 2336)
SUSPICIOUS
Reads settings of System Certificates
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Reads security settings of Internet Explorer
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Reads the Internet Settings
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Checks Windows Trust Settings
- LGgGQc88xaXZrqiug.exe (PID: 2336)
INFO
Checks supported languages
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Reads the computer name
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Checks proxy server information
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Reads Environment values
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Reads Windows Product ID
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Application launched itself
- iexplore.exe (PID: 2216)
The process checks LSA protection
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Modifies the phishing filter of IE
- iexplore.exe (PID: 2216)
Creates files or folders in the user directory
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Write to the desktop.ini file (may be used to cloak folders)
- iexplore.exe (PID: 2216)
Reads the machine GUID from the registry
- LGgGQc88xaXZrqiug.exe (PID: 2336)
Create files in a temporary directory
- iexplore.exe (PID: 2216)
- iexplore.exe (PID: 2772)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win64 Executable (generic) (61.6) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (14.6) |
| .exe | | | Win32 Executable (generic) (10) |
| .exe | | | Win16/32 Executable Delphi generic (4.6) |
| .exe | | | Generic Win/DOS Executable (4.4) |
EXIF
EXE
| Subsystem: | Windows command line |
|---|---|
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 6 |
| EntryPoint: | 0x7952ca |
| UninitializedDataSize: | - |
| InitializedDataSize: | 1466880 |
| CodeSize: | 2412032 |
| LinkerVersion: | 14.29 |
| PEType: | PE32 |
| ImageFileCharacteristics: | No relocs, Executable, 32-bit |
| TimeStamp: | 2023:03:21 02:18:05+00:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 21-Mar-2023 02:18:05 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 6 |
| Time date stamp: | 21-Mar-2023 02:18:05 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x0024CC80 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
.rdata | 0x0024E000 | 0x0008C49C | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 0 |
.data | 0x002DB000 | 0x000BE92C | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.10 | 0x0039A000 | 0x00314DA6 | 0x00000000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 0 |
.11 | 0x006AF000 | 0x005BB6A0 | 0x005BB800 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 7.96058 |
.rsrc | 0x00C6B000 | 0x000001E0 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.77204 |
Imports
ADVAPI32.dll |
CRYPT32.dll |
KERNEL32.dll |
MSWSOCK.dll |
Normaliz.dll |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
WININET.dll |
WLDAP32.dll |
Total processes
47
Monitored processes
5
Malicious processes
1
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1248 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2216 CREDAT:209936 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2028 | "C:\Users\admin\AppData\Local\Temp\LGgGQc88xaXZrqiug.exe" | C:\Users\admin\AppData\Local\Temp\LGgGQc88xaXZrqiug.exe | — | explorer.exe | |||||||||||
User: admin Integrity Level: MEDIUM Exit code: 3221226540 Modules
| |||||||||||||||
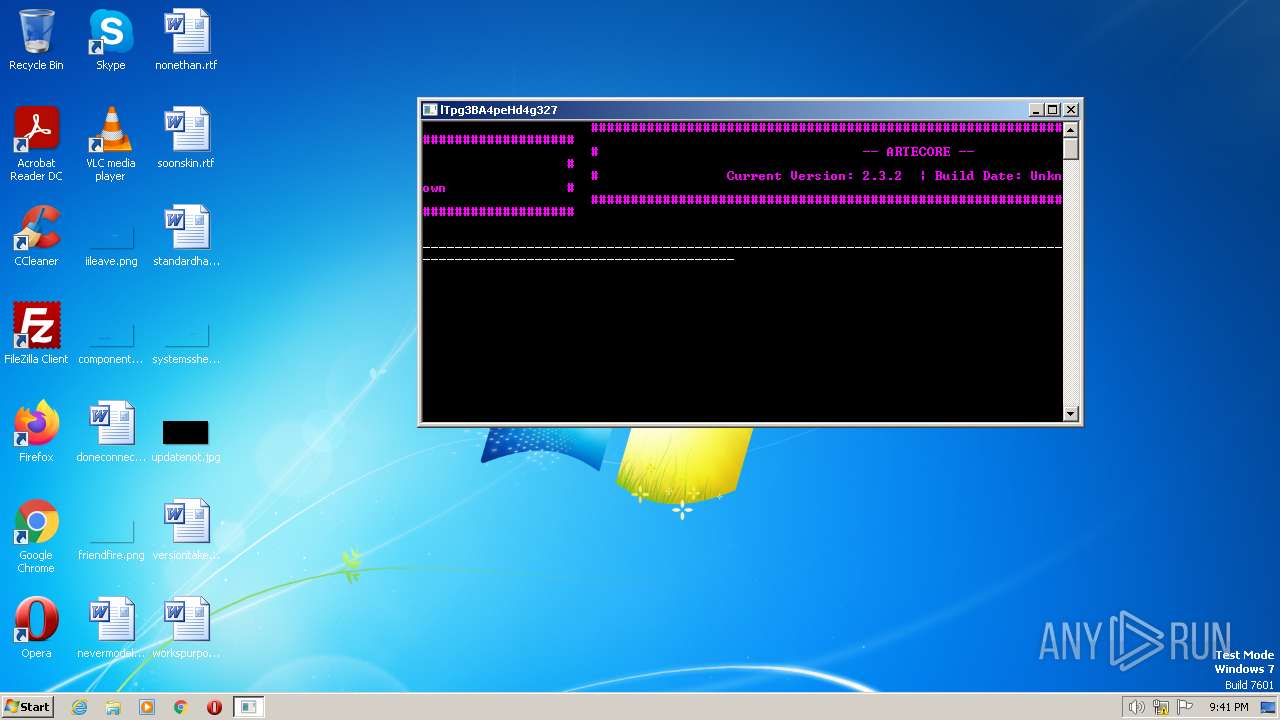
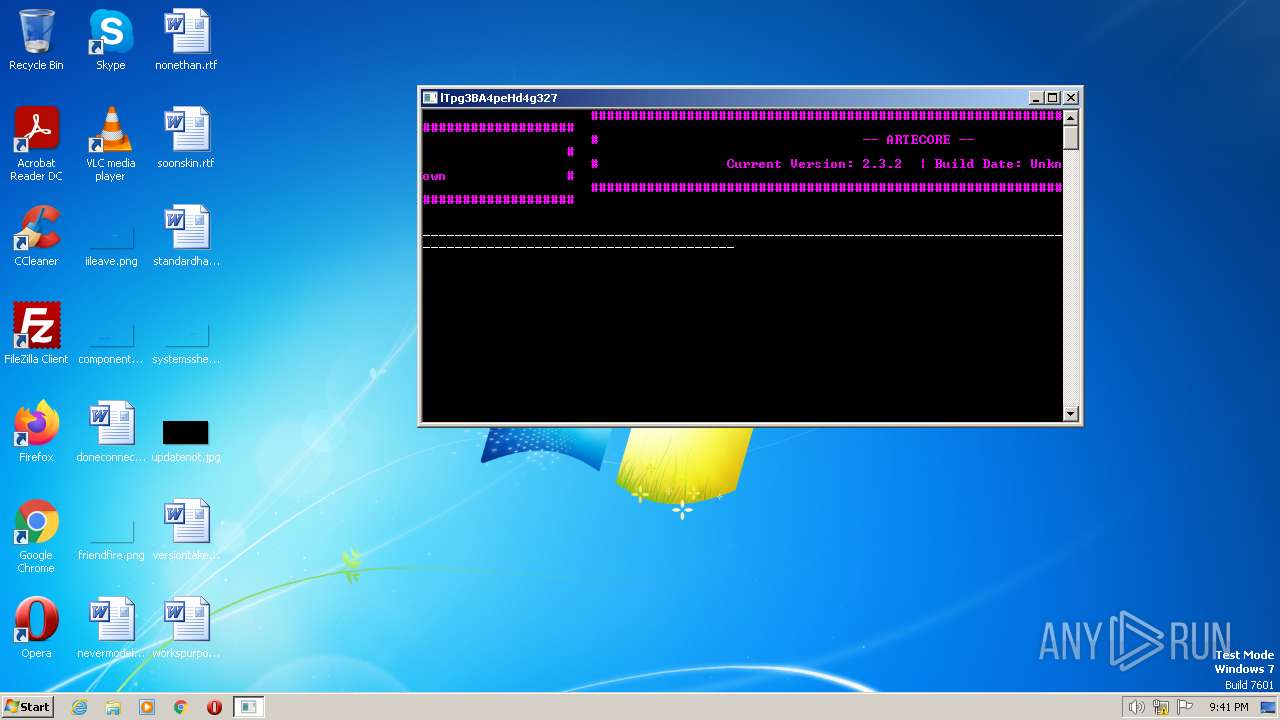
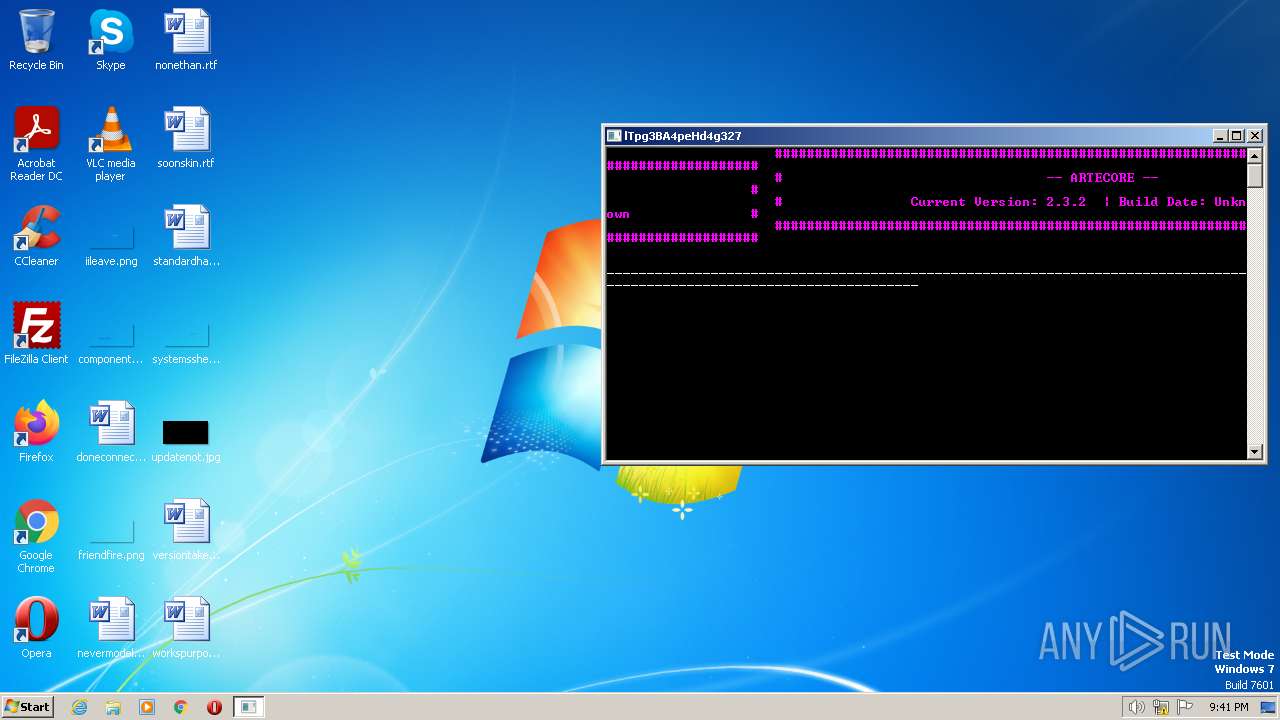
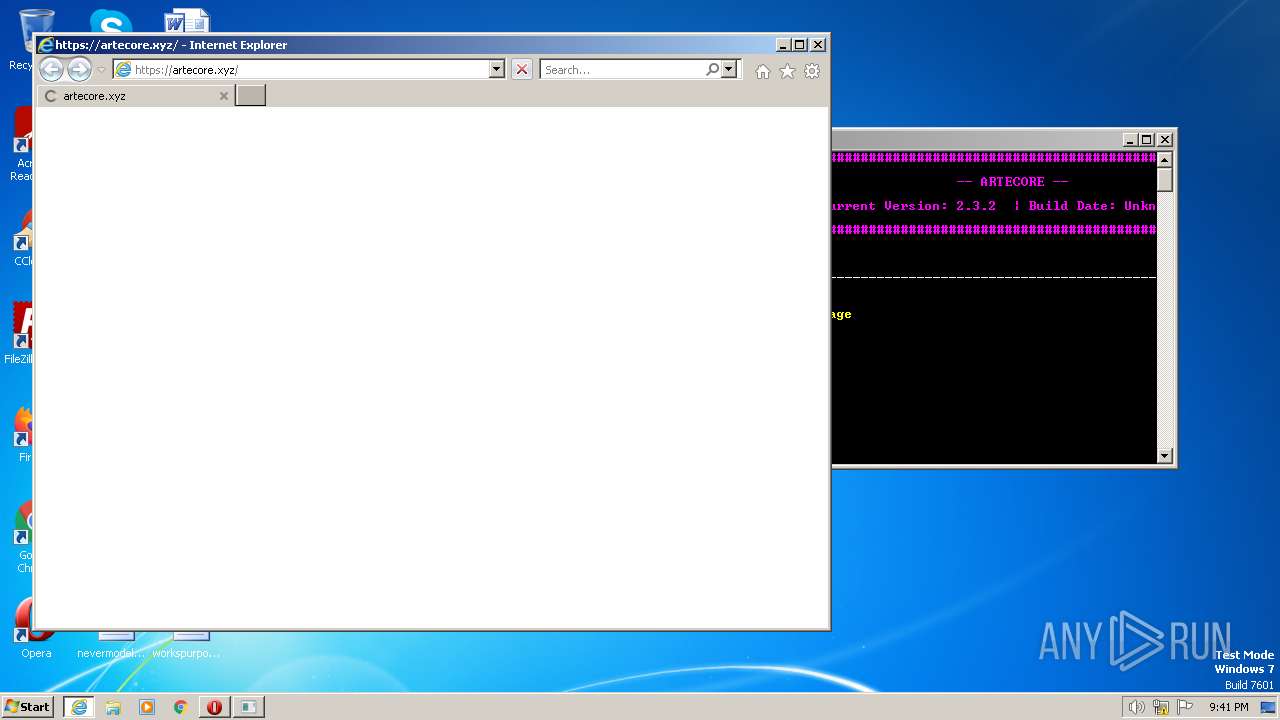
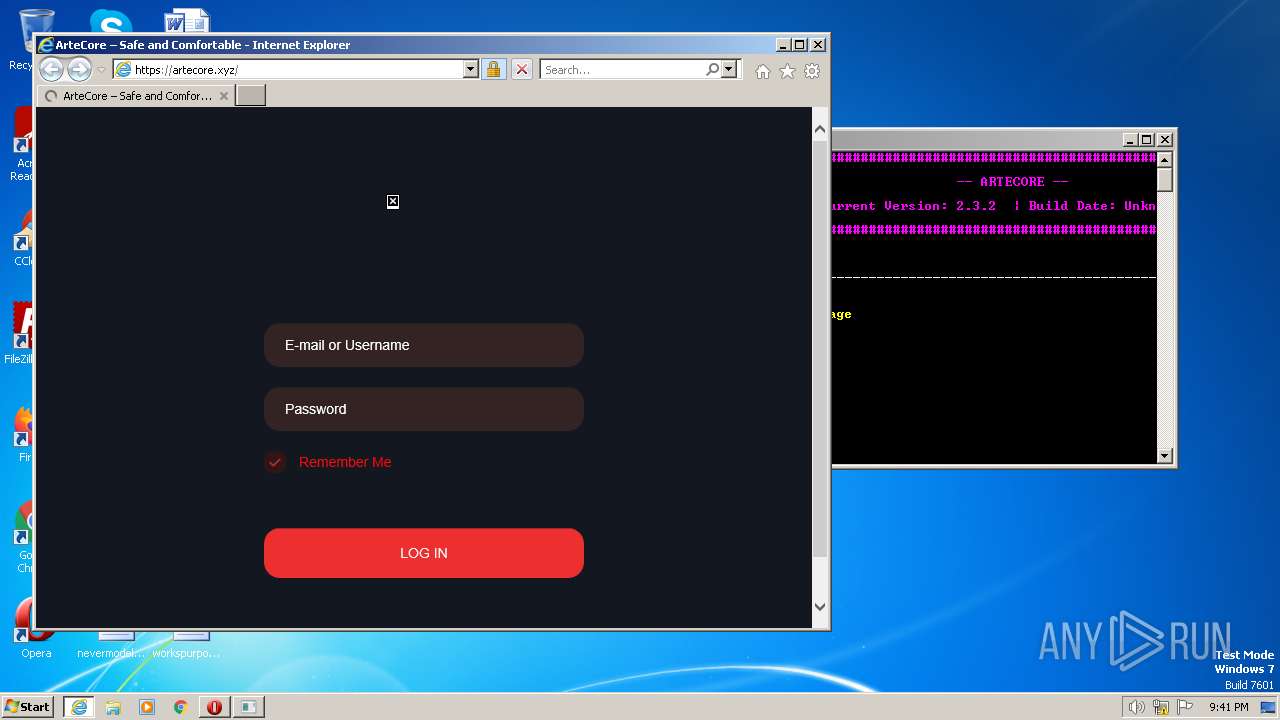
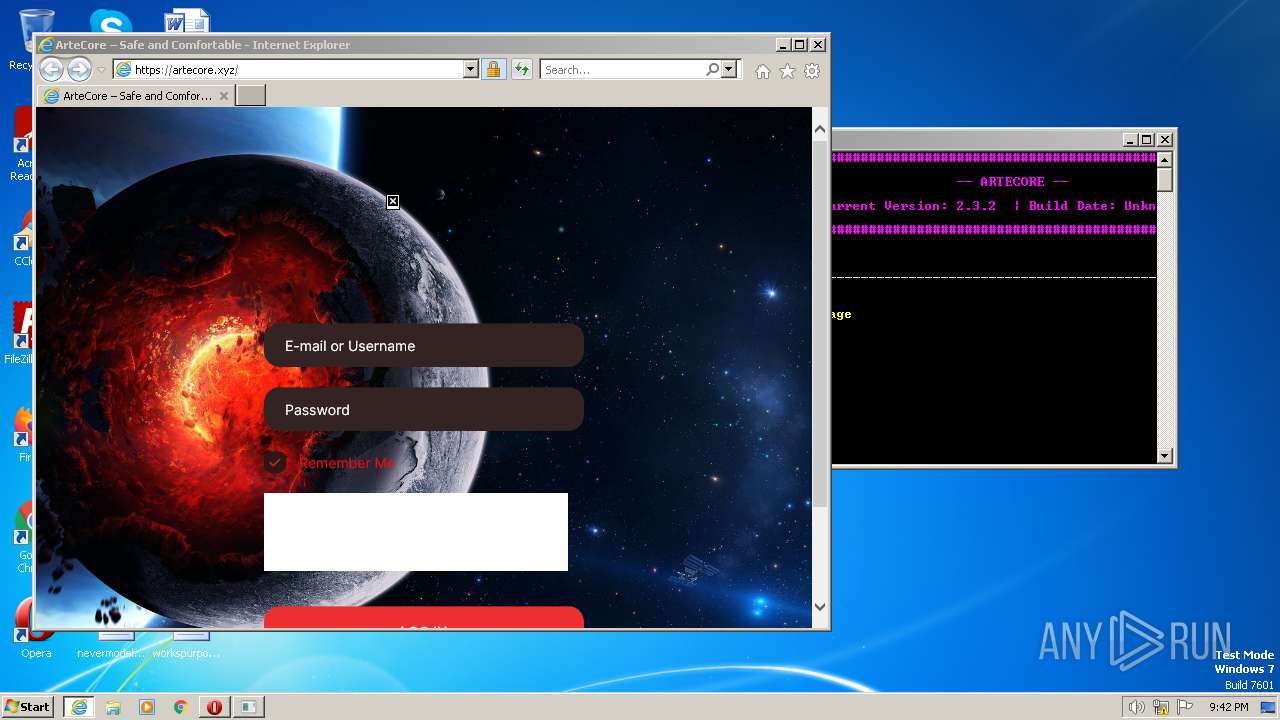
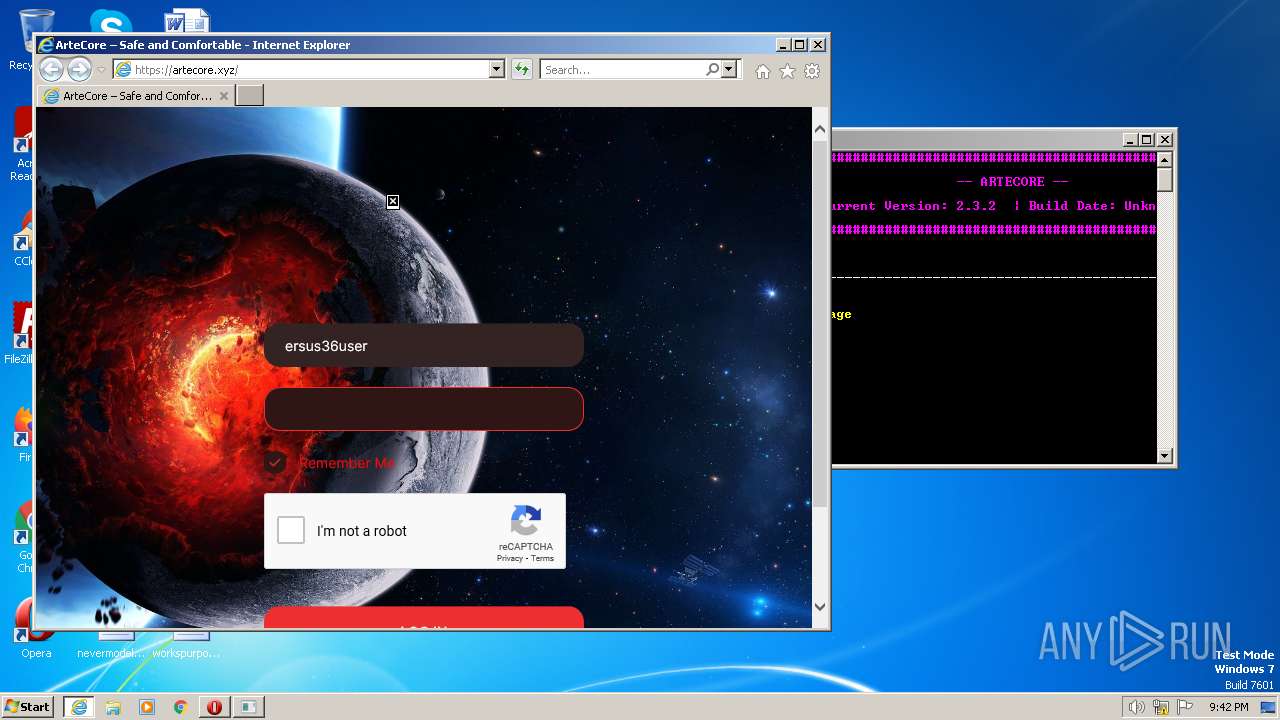
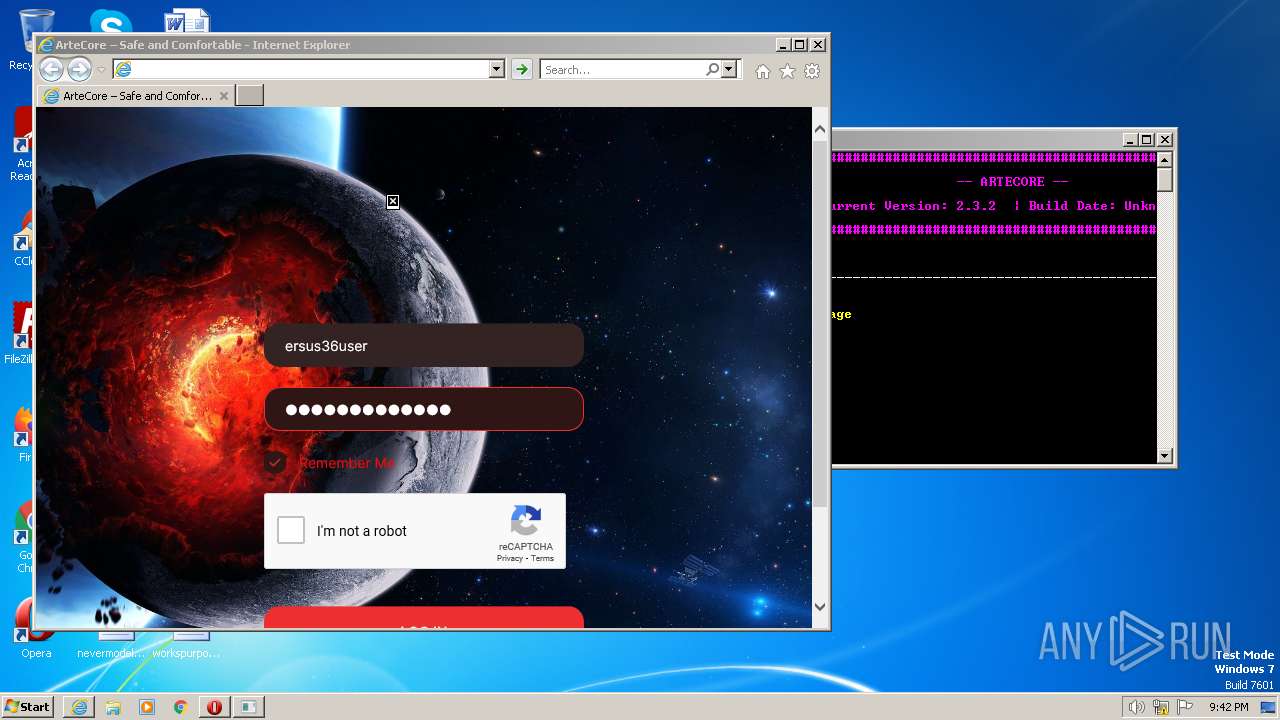
| 2216 | "C:\Program Files\Internet Explorer\iexplore.exe" https://artecore.xyz/ | C:\Program Files\Internet Explorer\iexplore.exe | LGgGQc88xaXZrqiug.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 2336 | "C:\Users\admin\AppData\Local\Temp\LGgGQc88xaXZrqiug.exe" | C:\Users\admin\AppData\Local\Temp\LGgGQc88xaXZrqiug.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: HIGH Exit code: 0 Modules
| |||||||||||||||
| 2772 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2216 CREDAT:275457 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
Total events
38 174
Read events
37 890
Write events
264
Delete events
20
Modification events
| (PID) Process: | (2336) LGgGQc88xaXZrqiug.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: Explorer.EXE | |||
| (PID) Process: | (2336) LGgGQc88xaXZrqiug.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender |
| Operation: | write | Name: | DisableAntiSpyware |
Value: 1 | |||
| (PID) Process: | (2336) LGgGQc88xaXZrqiug.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Policies\Microsoft\Windows Defender\Real-time Protection |
| Operation: | write | Name: | DisableRealtimeMonitoring |
Value: 1 | |||
| (PID) Process: | (2336) LGgGQc88xaXZrqiug.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\MountedDevices |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2336) LGgGQc88xaXZrqiug.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Dfrg\Statistics\Volume{e1a82db4-a9f0-11e7-b142-806e6f6e6963} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2336) LGgGQc88xaXZrqiug.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Dfrg\Statistics\Volume{e1a82db3-a9f0-11e7-b142-806e6f6e6963} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2336) LGgGQc88xaXZrqiug.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Dfrg\Statistics |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2336) LGgGQc88xaXZrqiug.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\BitBucket\Volume\{e1a82db4-a9f0-11e7-b142-806e6f6e6963} |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2336) LGgGQc88xaXZrqiug.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\BitBucket\Volume |
| Operation: | delete key | Name: | (default) |
Value: | |||
| (PID) Process: | (2336) LGgGQc88xaXZrqiug.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\MountPoints2\CPC\Volume\{e1a82db4-a9f0-11e7-b142-806e6f6e6963} |
| Operation: | delete key | Name: | (default) |
Value: | |||
Executable files
2
Suspicious files
49
Text files
67
Unknown types
3
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2772 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar9AD9.tmp | cat | |
MD5:4FF65AD929CD9A367680E0E5B1C08166 | SHA256:C8733C93CC5AAF5CA206D06AF22EE8DBDEC764FB5085019A6A9181FEB9DFDEE6 | |||
| 2772 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Cab9807.tmp | compressed | |
MD5:3AC860860707BAAF32469FA7CC7C0192 | SHA256:D015145D551ECD14916270EFAD773BBC9FD57FAD2228D2C24559F696C961D904 | |||
| 2772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:790B96AA13B96B7006D0912205FB6408 | SHA256:5469E81C456464966AC55775DA948F7DAD164107974253A305232B30BD778E77 | |||
| 2772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | compressed | |
MD5:F7DCB24540769805E5BB30D193944DCE | SHA256:6B88C6AC55BBD6FEA0EBE5A760D1AD2CFCE251C59D0151A1400701CB927E36EA | |||
| 2772 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Tar9808.tmp | cat | |
MD5:4FF65AD929CD9A367680E0E5B1C08166 | SHA256:C8733C93CC5AAF5CA206D06AF22EE8DBDEC764FB5085019A6A9181FEB9DFDEE6 | |||
| 2336 | LGgGQc88xaXZrqiug.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\B398B80134F72209547439DB21AB308D_A4CF52CCA82D7458083F7280801A3A04 | binary | |
MD5:29E12077C9460CA83A3BA3E4B3534CA8 | SHA256:8AB2DD06E4569674A3C4A6F99CE9AB6D50735F3EF9DC22560C59039E741C8A0E | |||
| 2772 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\PO2HN1X2\bootstrap-reboot.min[1].css | text | |
MD5:F4BB20280E13EE6DC0D67BB75D999671 | SHA256:2FF8C41B99B922A7904F5F50BD69925F1E1CD88B9E641CD66134FC0173FE6358 | |||
| 2772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\103621DE9CD5414CC2538780B4B75751 | der | |
MD5:60FE01DF86BE2E5331B0CDBE86165686 | SHA256:C08CCBC876CD5A7CDFA9670F9637DA57F6A1282198A9BC71FC7D7247A6E5B7A8 | |||
| 2772 | iexplore.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\Temporary Internet Files\Content.IE5\6Z2BCOUL\slider-radio[1].css | text | |
MD5:CB8301DE430930088B08AE0A0A62B2CD | SHA256:B4DAA2E18CF6D9B4E54E8AA0B6739CCC7328443086A5F1D87211F130F1249CCC | |||
| 2772 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\77EC63BDA74BD0D0E0426DC8F8008506 | compressed | |
MD5:3AC860860707BAAF32469FA7CC7C0192 | SHA256:D015145D551ECD14916270EFAD773BBC9FD57FAD2228D2C24559F696C961D904 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
18
TCP/UDP connections
54
DNS requests
22
Threats
6
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2336 | LGgGQc88xaXZrqiug.exe | GET | 301 | 185.199.109.133:80 | http://raw.githubusercontent.com/ripped0/hRoot/main/sinsiatak.nw | NL | — | — | shared |
2336 | LGgGQc88xaXZrqiug.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAbY2QTVWENG9oovp1QifsQ%3D | US | der | 471 b | whitelisted |
2772 | iexplore.exe | GET | 200 | 23.201.254.55:80 | http://x1.c.lencr.org/ | CH | der | 717 b | whitelisted |
2772 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?f3938129dd11b95c | US | compressed | 62.3 Kb | whitelisted |
2772 | iexplore.exe | GET | 200 | 142.250.181.227:80 | http://ocsp.pki.goog/gtsr1/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBQwkcLWD4LqGJ7bE7B1XZsEbmfwUAQU5K8rJnEaK0gnhS9SZizv8IkTcT4CDQIDvFNZazTHGPUBUGY%3D | US | der | 724 b | whitelisted |
2216 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA8Ull8gIGmZT9XHrHiJQeI%3D | US | binary | 1.47 Kb | whitelisted |
2216 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEALnkXH7gCHpP%2BLZg4NMUMA%3D | US | binary | 471 b | whitelisted |
2772 | iexplore.exe | GET | 200 | 93.184.221.240:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/authrootstl.cab?eaa4a059cf1eaa57 | US | compressed | 62.3 Kb | whitelisted |
2772 | iexplore.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | US | der | 471 b | whitelisted |
2772 | iexplore.exe | GET | 200 | 23.201.254.55:80 | http://x2.c.lencr.org/ | CH | der | 300 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
1076 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
3624 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2336 | LGgGQc88xaXZrqiug.exe | 185.199.108.133:80 | raw.githubusercontent.com | FASTLY | US | malicious |
2336 | LGgGQc88xaXZrqiug.exe | 185.199.109.133:80 | raw.githubusercontent.com | FASTLY | US | malicious |
2336 | LGgGQc88xaXZrqiug.exe | 185.199.109.133:443 | raw.githubusercontent.com | FASTLY | US | malicious |
2336 | LGgGQc88xaXZrqiug.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
2772 | iexplore.exe | 188.114.96.3:443 | artecore.xyz | CLOUDFLARENET | NL | malicious |
2772 | iexplore.exe | 23.201.254.55:80 | x1.c.lencr.org | AKAMAI-AS | CH | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
raw.githubusercontent.com |
| shared |
ctldl.windowsupdate.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
artecore.xyz |
| malicious |
x1.c.lencr.org |
| whitelisted |
x2.c.lencr.org |
| whitelisted |
www.google.com |
| malicious |
ocsp.pki.goog |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
www.gstatic.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
2772 | iexplore.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2772 | iexplore.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2772 | iexplore.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2772 | iexplore.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2772 | iexplore.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |
2772 | iexplore.exe | Potentially Bad Traffic | ET HUNTING Observed Let's Encrypt Certificate for Suspicious TLD (.xyz) |