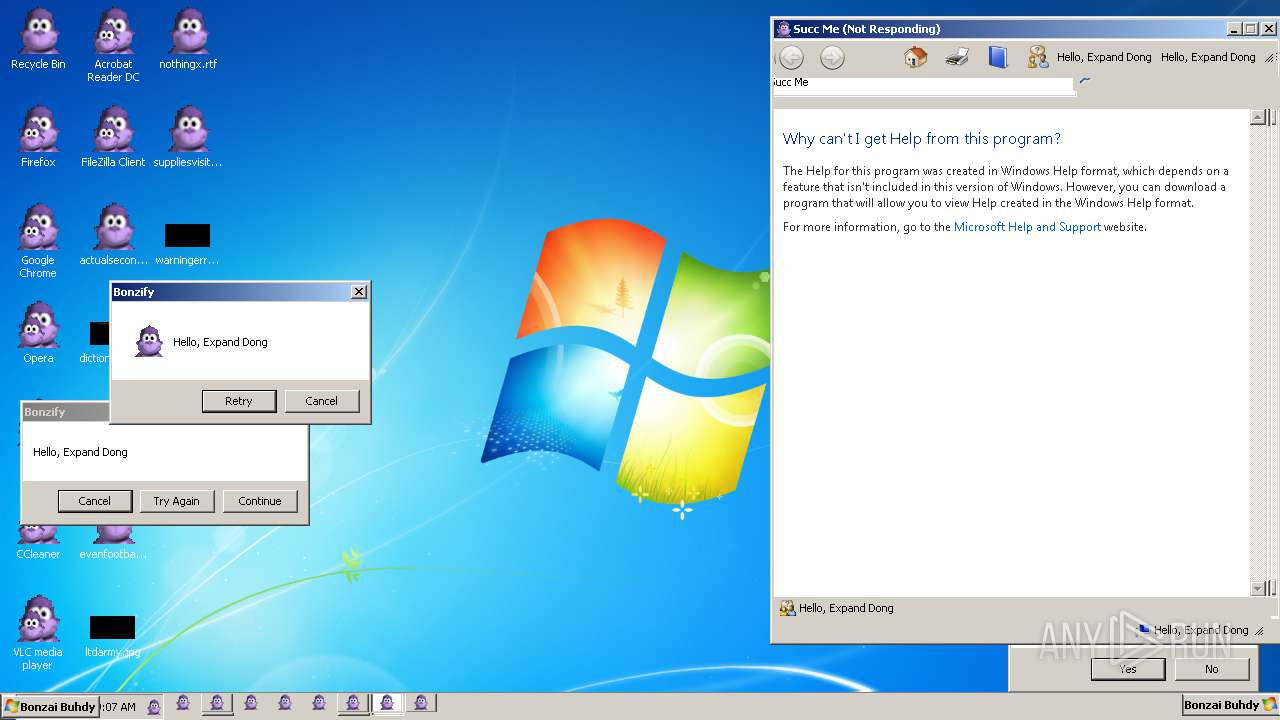
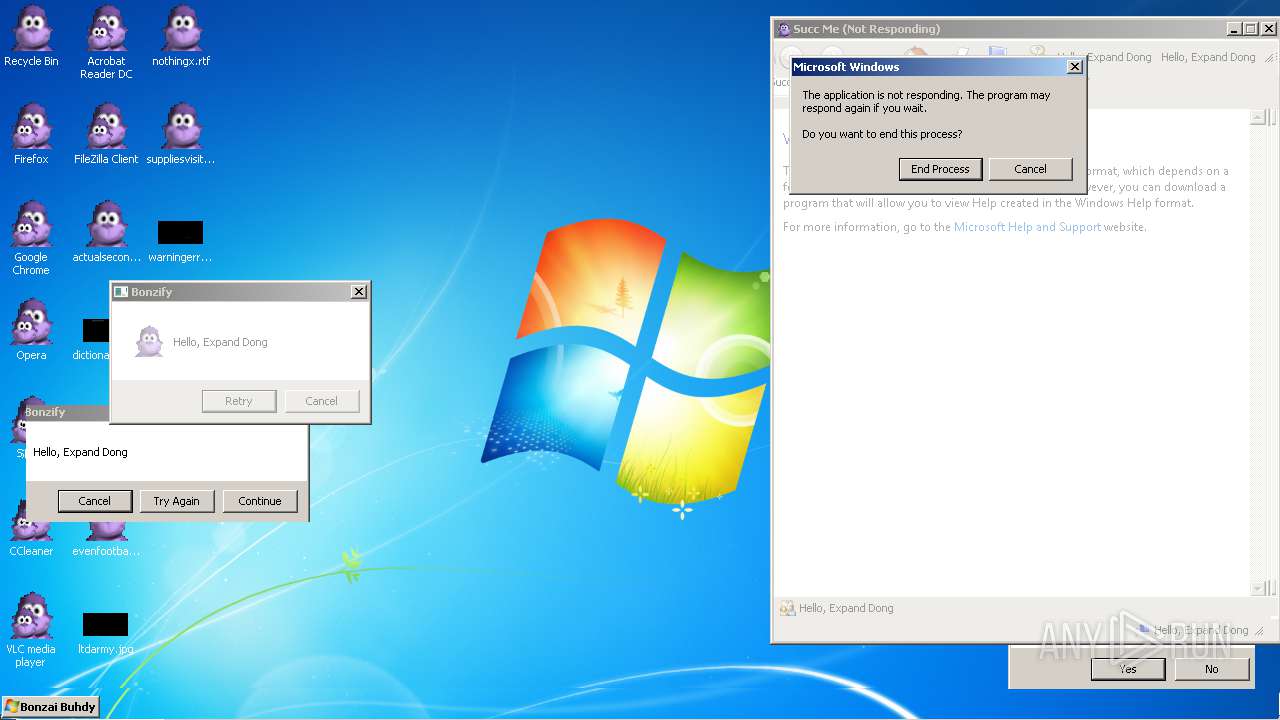
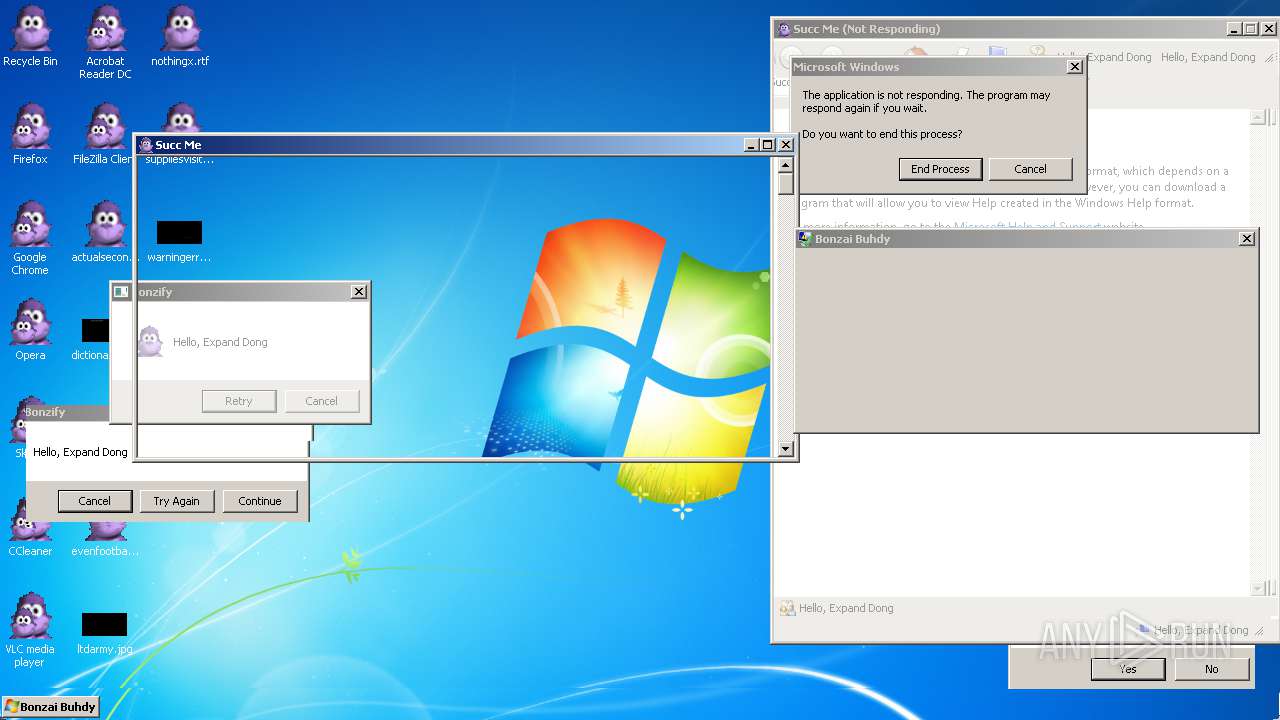
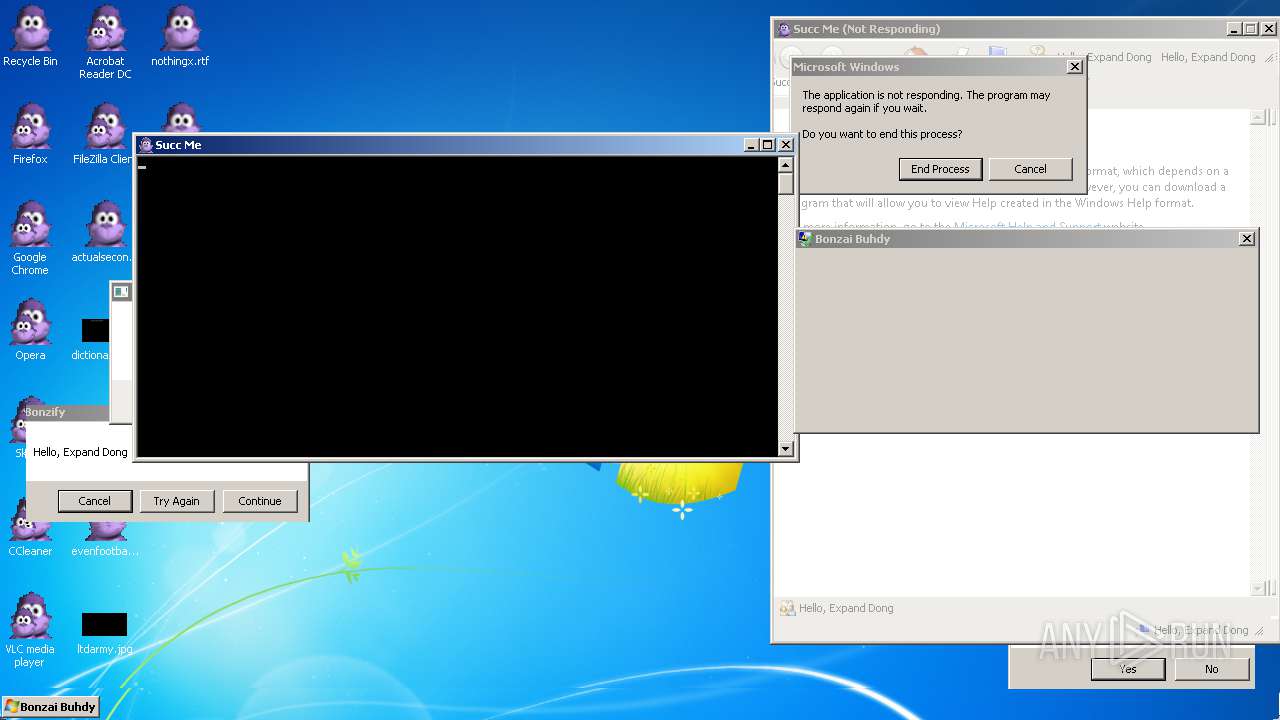
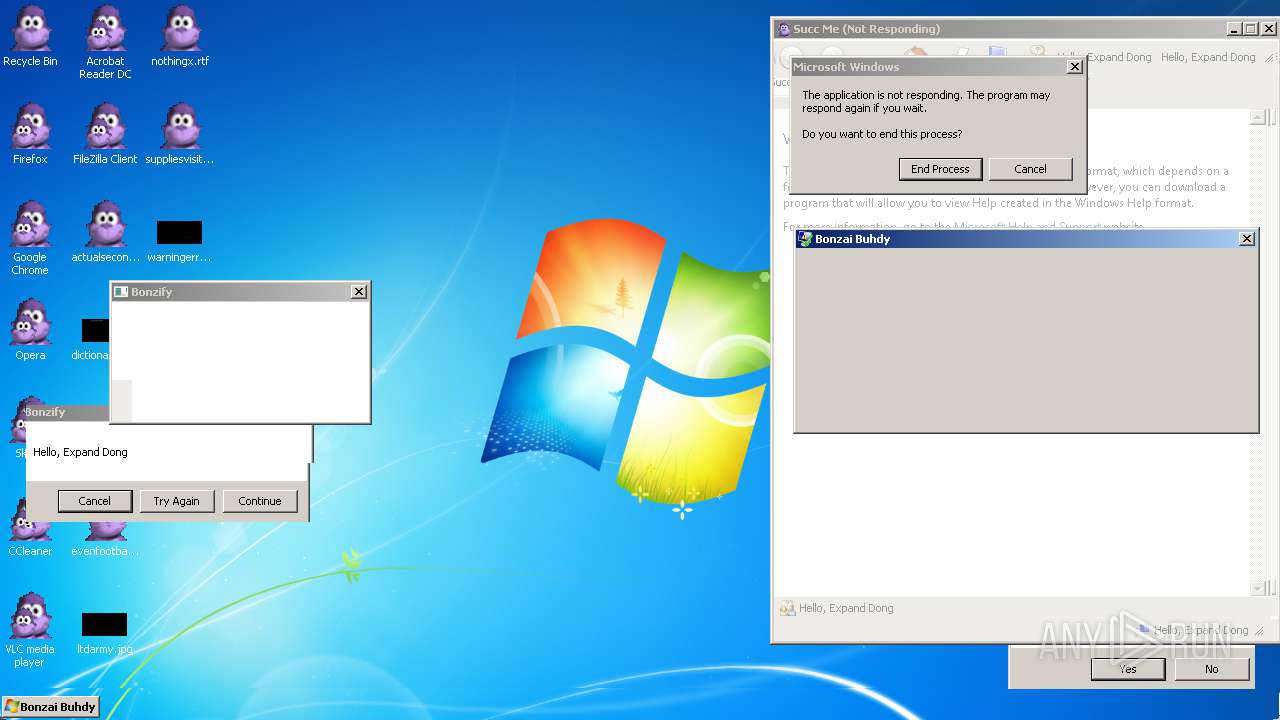
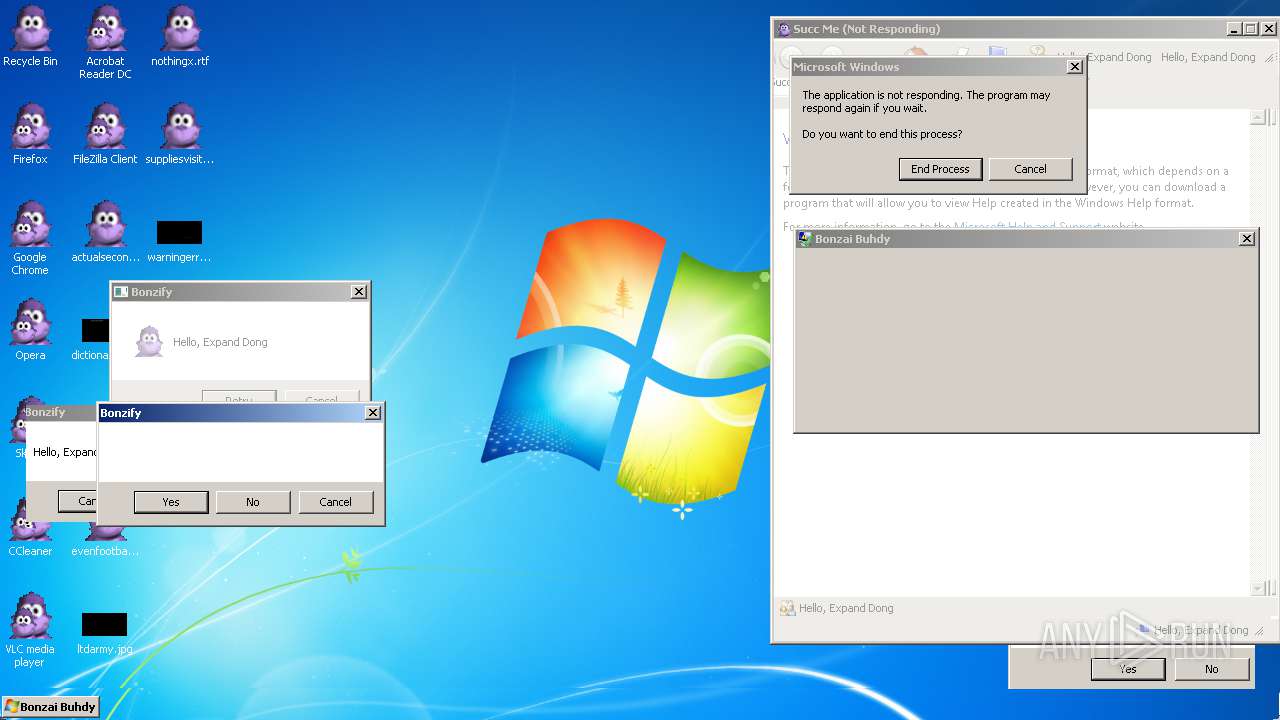
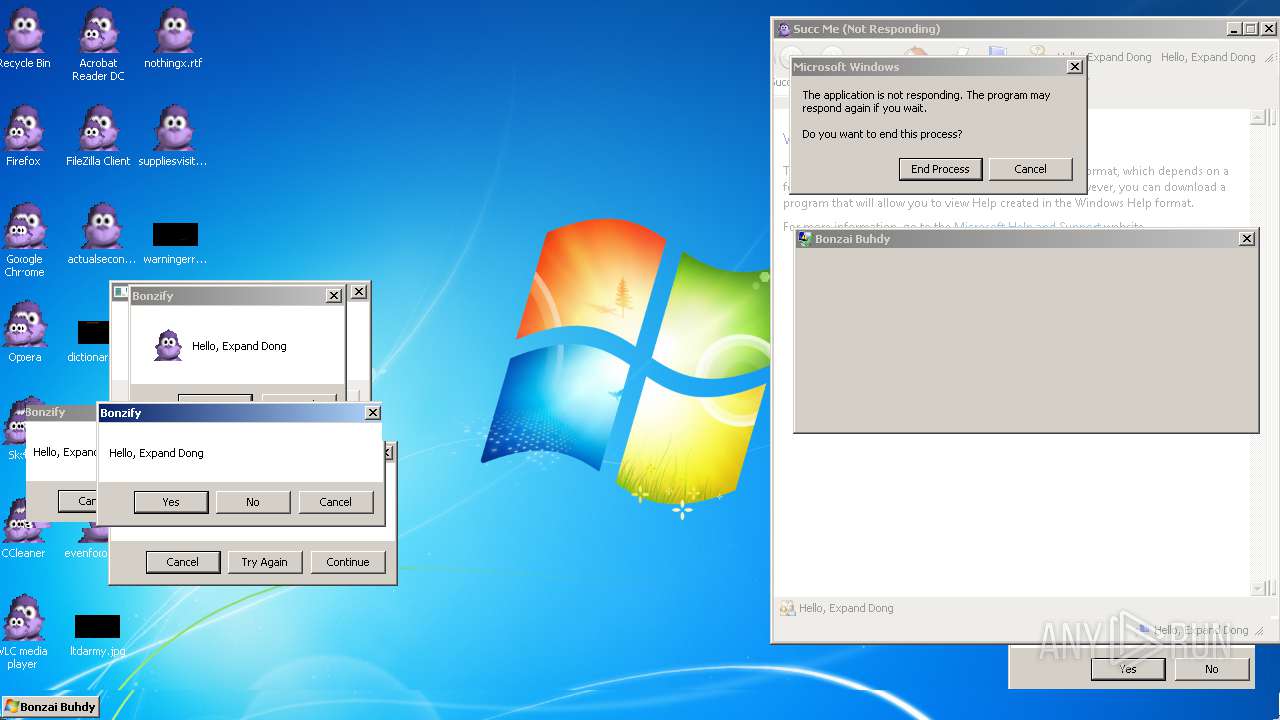
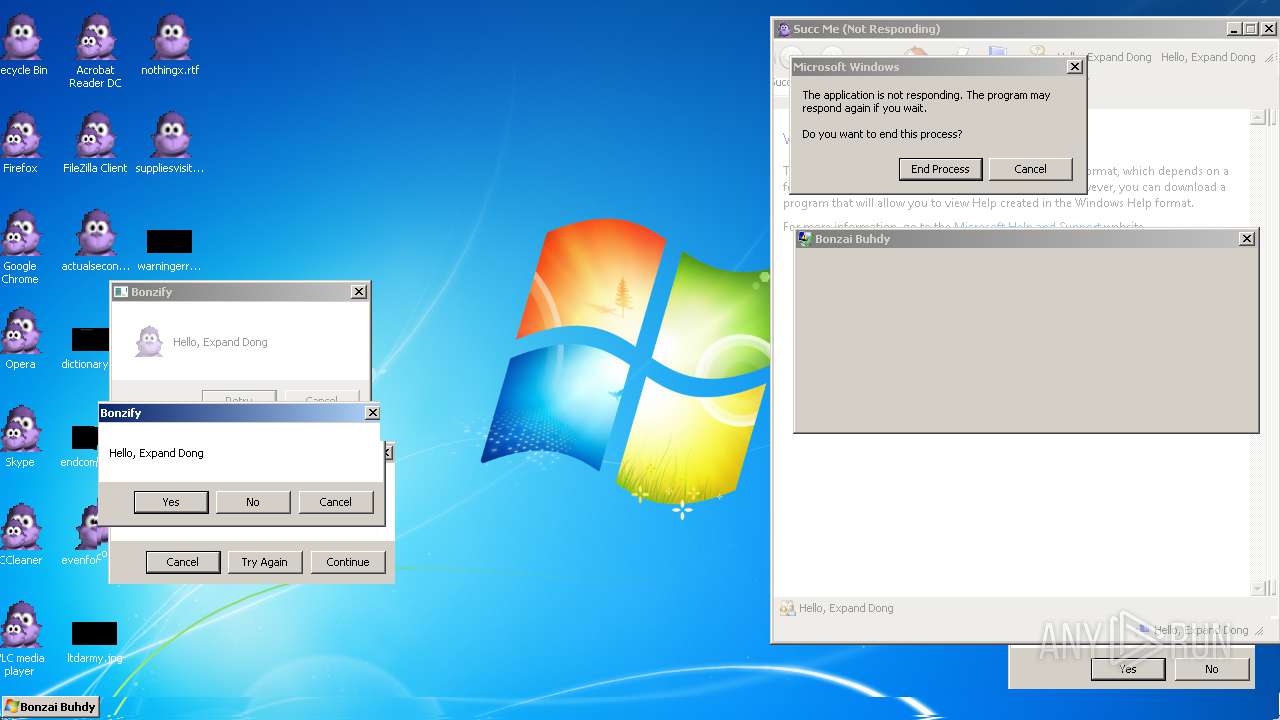
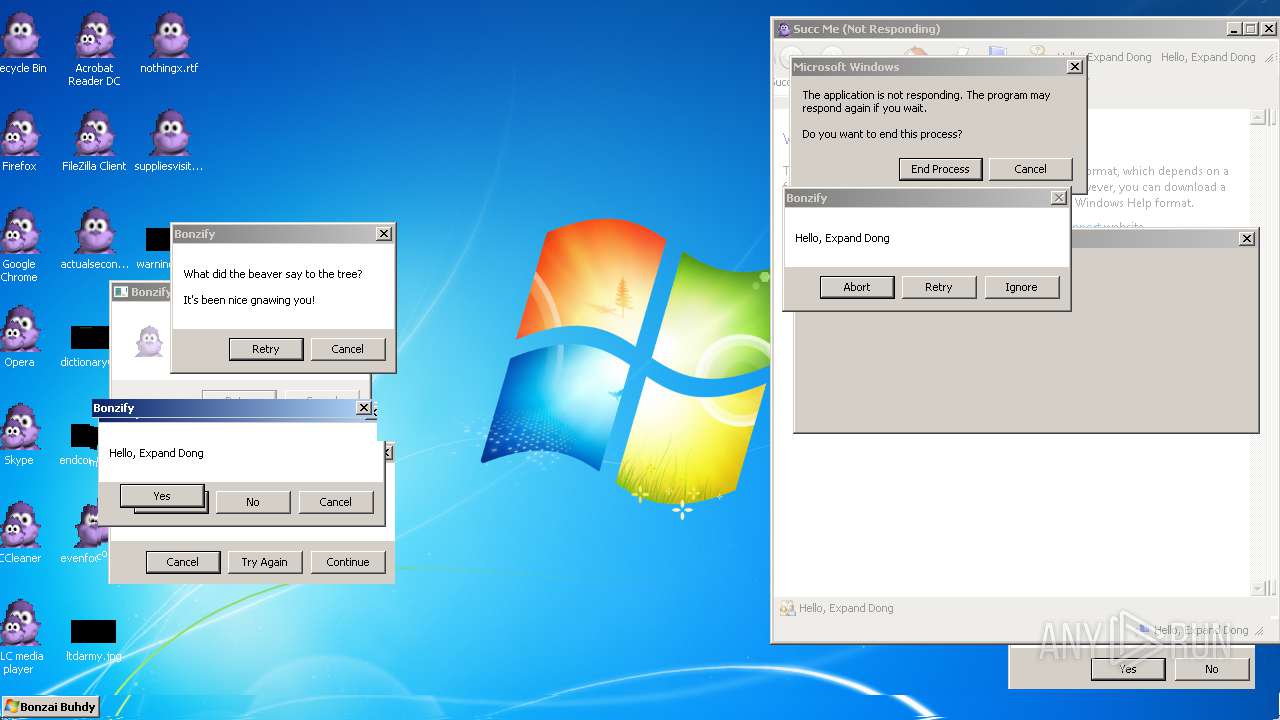
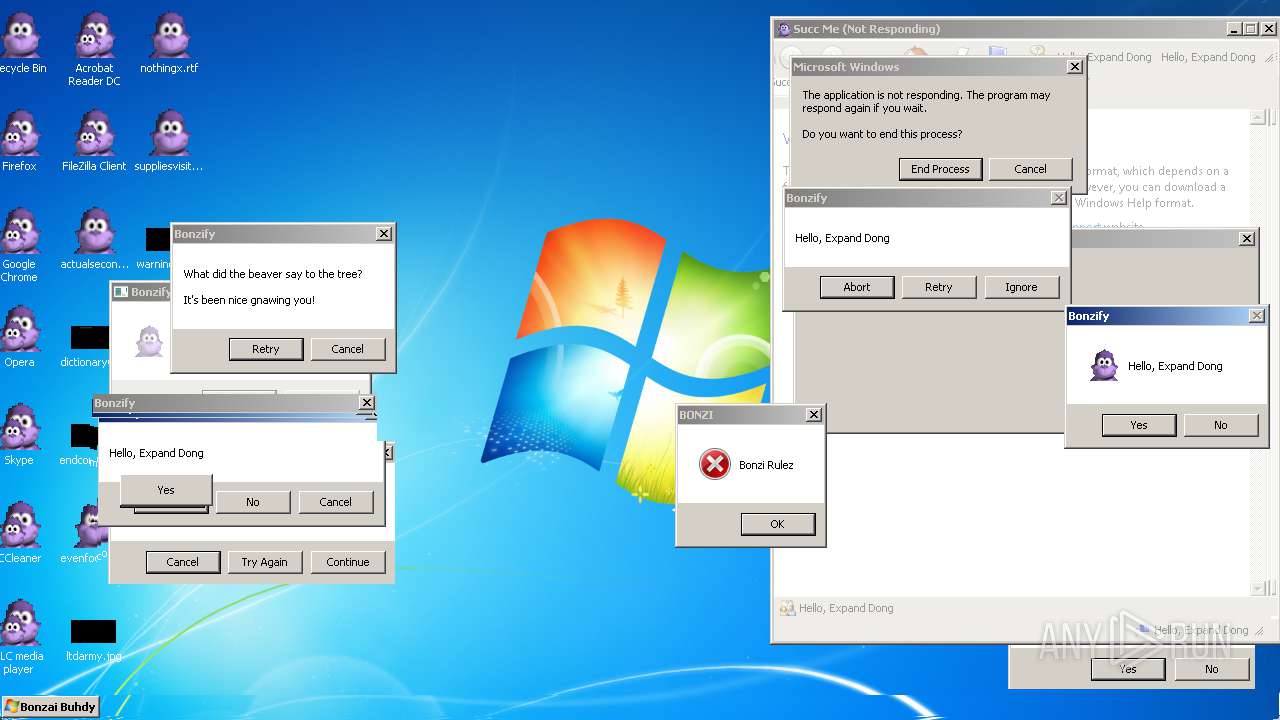
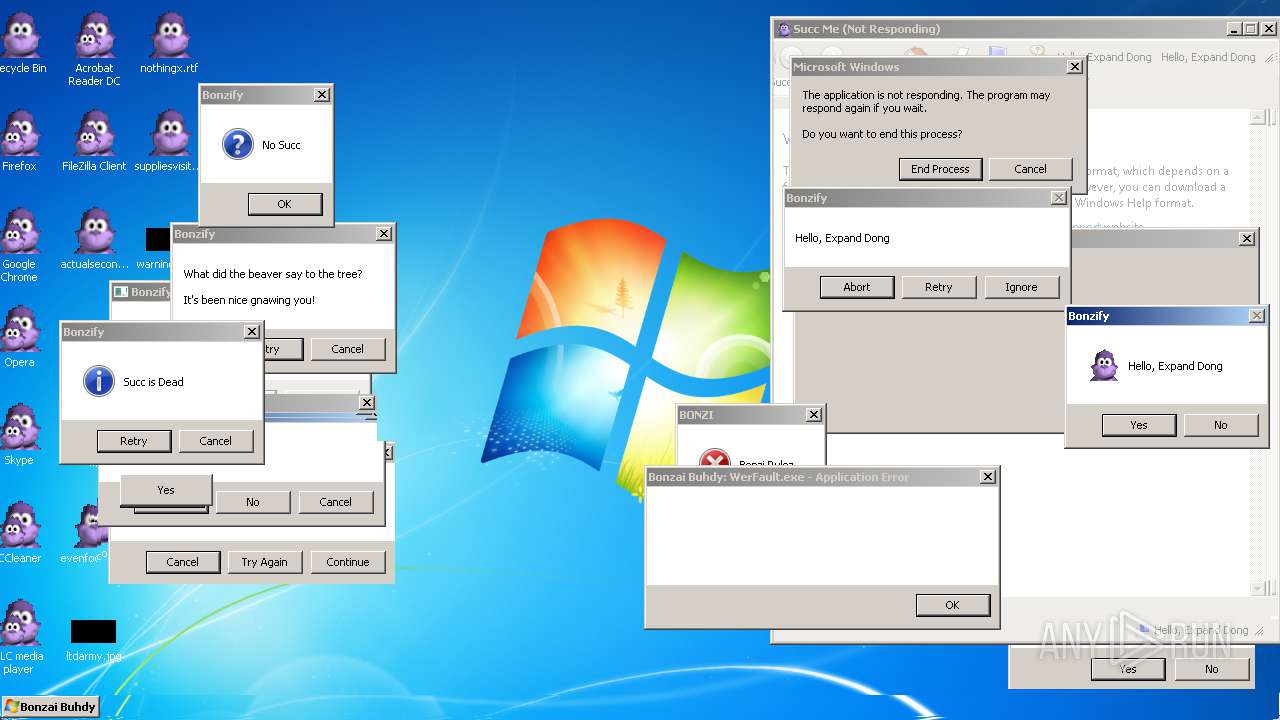
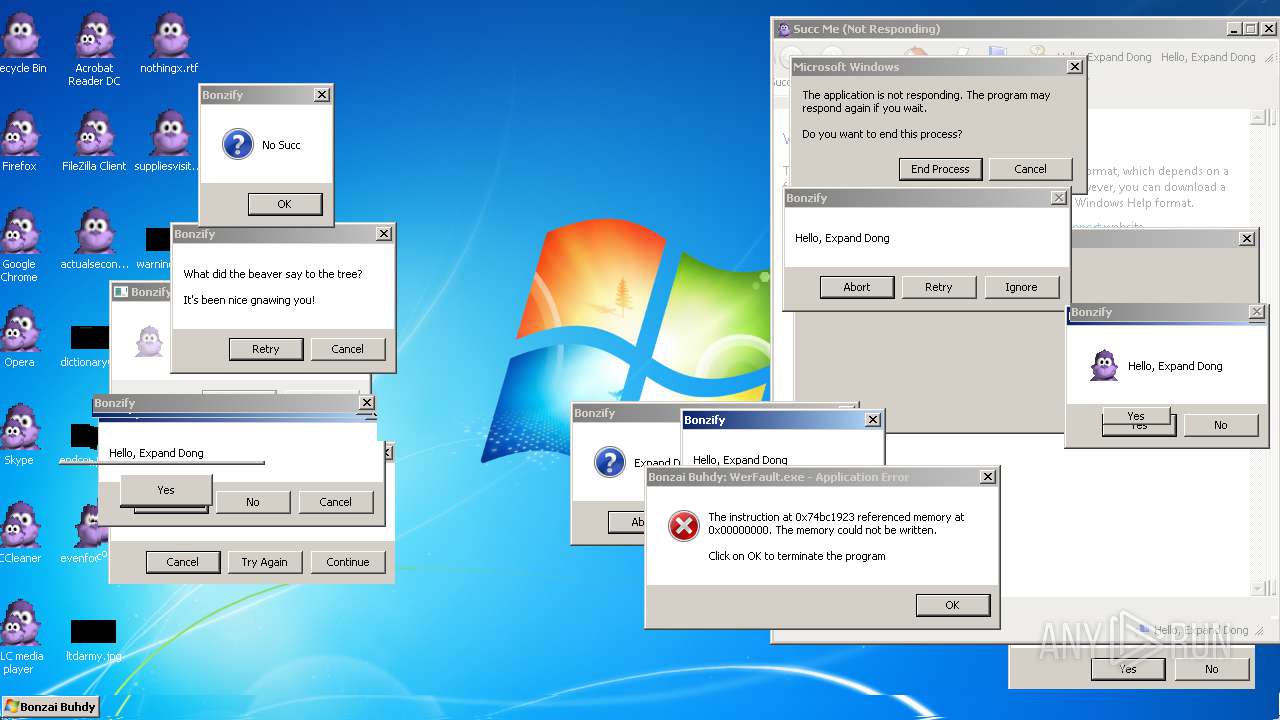
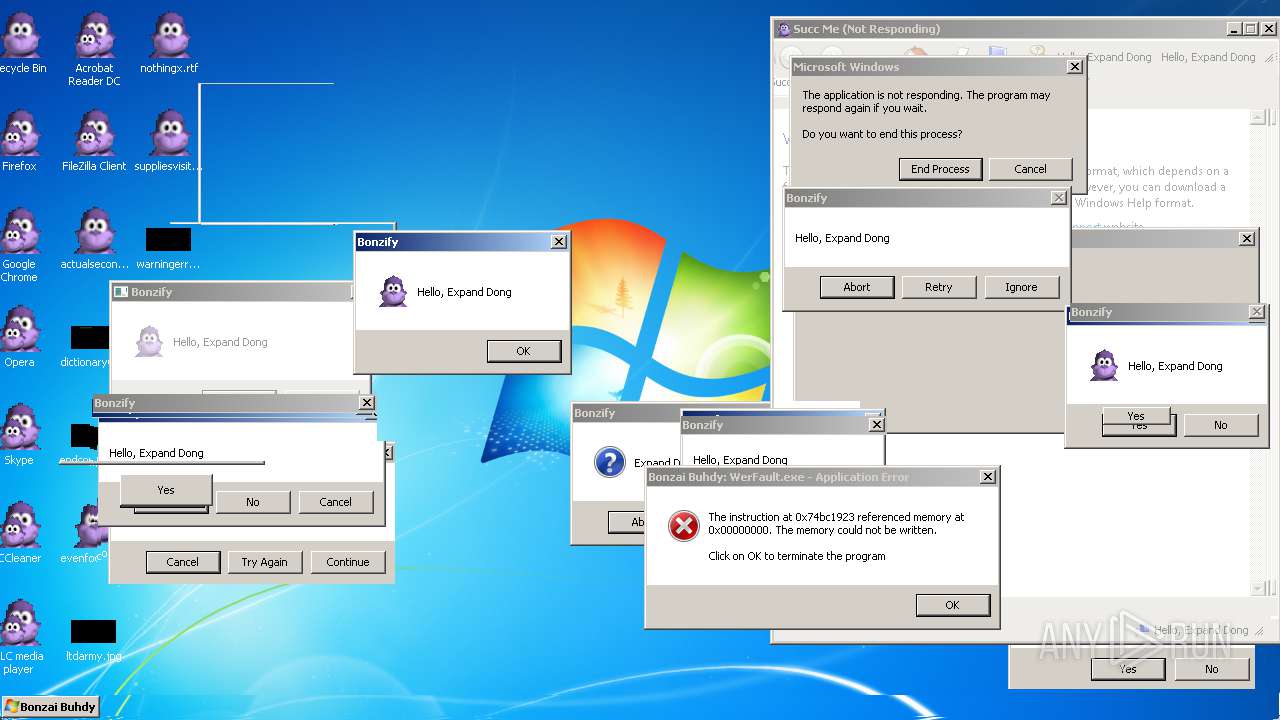
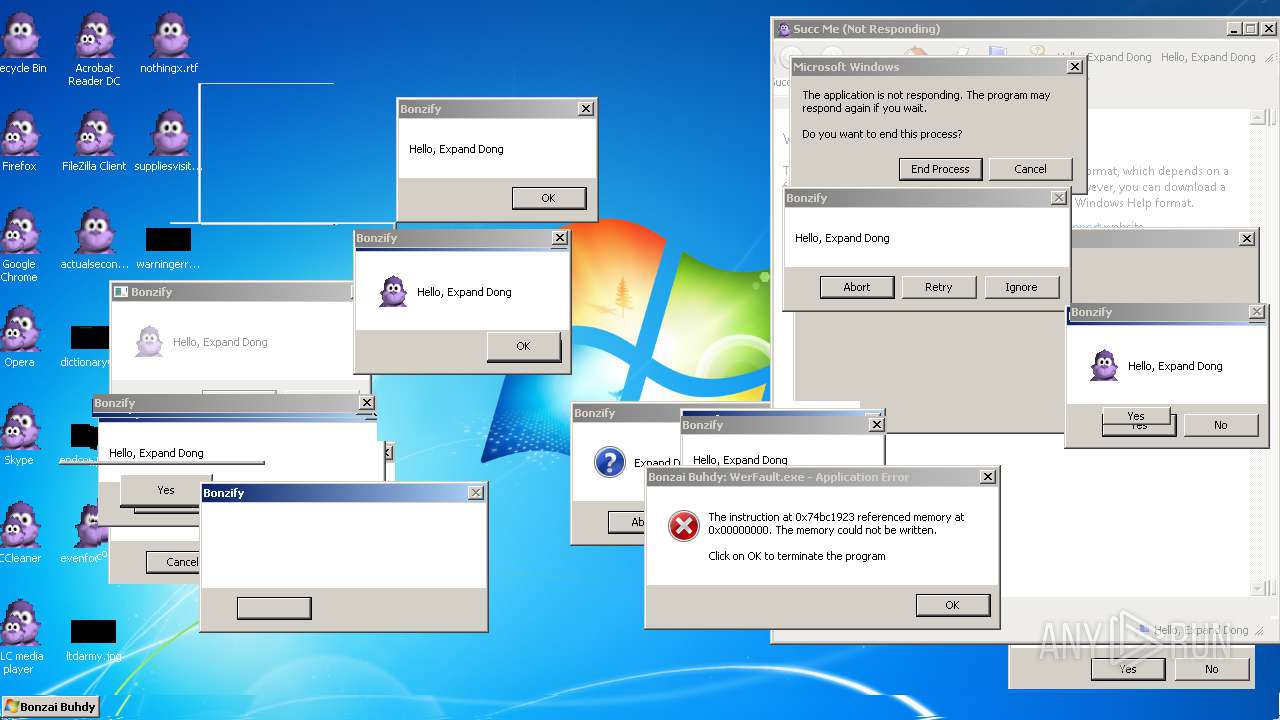
| File name: | Bonzify.exe |
| Full analysis: | https://app.any.run/tasks/6da4c18e-ad1e-484c-b5dd-59abed795aaf |
| Verdict: | Malicious activity |
| Analysis date: | February 11, 2019, 09:05:03 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | CAFD33BB186E79826660C94E4AF5EC89 |
| SHA1: | EA9E283E5BF8B4EBA66ADF3F9E6FD5C2CCFB7445 |
| SHA256: | AB39F9FA9ECB07AC455A1C6BF6BF2A3E7CC66AF911707946402E015512EFA912 |
| SSDEEP: | 196608:JdAMaWetTeAkLIdx751qFTkub//73lc6u7b5VJ2Yx5xIdk3:9aWedh+Idx75QYub//73lc6u7bLMYxD |
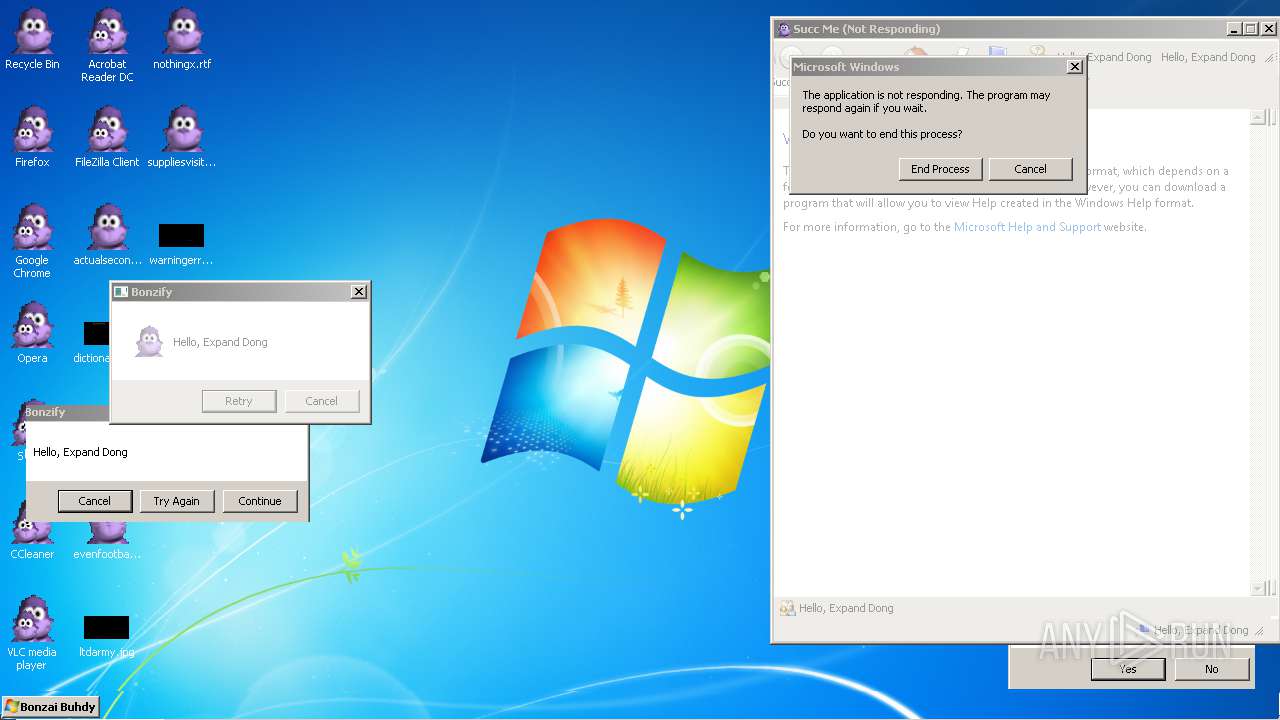
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- INSTALLER.exe (PID: 3376)
- INSTALLER.exe (PID: 3316)
- WerFault.exe (PID: 2740)
Application was dropped or rewritten from another process
- INSTALLER.exe (PID: 3376)
- INSTALLER.exe (PID: 3316)
Changes the autorun value in the registry
- INSTALLER.exe (PID: 3316)
- Bonzify.exe (PID: 3712)
- WerFault.exe (PID: 1436)
- svchost.exe (PID: 300)
- explorer.exe (PID: 3908)
- helppane.exe (PID: 2884)
- svchost.exe (PID: 2216)
- mshta.exe (PID: 4092)
- WerFault.exe (PID: 4020)
- WerFault.exe (PID: 2740)
- UserAccountControlSettings.exe (PID: 3080)
- svchost.exe (PID: 3148)
- WerFault.exe (PID: 2472)
Changes AppInit_DLLs value (autorun option)
- Bonzify.exe (PID: 3712)
Loads dropped or rewritten executable
- regsvr32.exe (PID: 2492)
- AgentSvr.exe (PID: 2548)
- explorer.exe (PID: 3908)
- regsvr32.exe (PID: 3332)
- WerFault.exe (PID: 1436)
- RDVGHelper.exe (PID: 2660)
- WTVConverter.exe (PID: 2744)
- SetupUtility.exe (PID: 2580)
- conhost.exe (PID: 1780)
- PresentationFontCache.exe (PID: 2708)
- sigverif.exe (PID: 3888)
- DllHost.exe (PID: 3792)
- SearchProtocolHost.exe (PID: 3260)
- svchost.exe (PID: 300)
- explorer.exe (PID: 2704)
- conhost.exe (PID: 3816)
- conhost.exe (PID: 2620)
- SearchProtocolHost.exe (PID: 4016)
- setupugc.exe (PID: 3776)
- nbtstat.exe (PID: 2480)
- winhlp32.exe (PID: 3052)
- helppane.exe (PID: 2884)
- SearchFilterHost.exe (PID: 2980)
- WerFault.exe (PID: 4020)
- WerFault.exe (PID: 2740)
- SearchProtocolHost.exe (PID: 2340)
- svchost.exe (PID: 2216)
- conhost.exe (PID: 3952)
- mshta.exe (PID: 4092)
- chgusr.exe (PID: 2476)
- extrac32.exe (PID: 3616)
- conhost.exe (PID: 896)
- FlickLearningWizard.exe (PID: 640)
- conhost.exe (PID: 2228)
- svchost.exe (PID: 696)
- UserAccountControlSettings.exe (PID: 3080)
- fvenotify.exe (PID: 3996)
- conhost.exe (PID: 2904)
- WerFault.exe (PID: 3296)
- WerFault.exe (PID: 1340)
- conhost.exe (PID: 2700)
- LogonUI.exe (PID: 3076)
- WerFault.exe (PID: 2976)
- conhost.exe (PID: 2824)
- consent.exe (PID: 1016)
- svchost.exe (PID: 3148)
- oobeldr.exe (PID: 2772)
- conhost.exe (PID: 3300)
- taskhost.exe (PID: 1076)
- WerFault.exe (PID: 2148)
- WerFault.exe (PID: 860)
- WerFault.exe (PID: 2472)
- WerFault.exe (PID: 2636)
- conhost.exe (PID: 3532)
- ExtExport.exe (PID: 3424)
- WerFault.exe (PID: 3068)
- conhost.exe (PID: 2156)
- secinit.exe (PID: 1144)
- jsc.exe (PID: 2448)
Changes internet zones settings
- svchost.exe (PID: 300)
- explorer.exe (PID: 3908)
- explorer.exe (PID: 2704)
- conhost.exe (PID: 1780)
- PresentationFontCache.exe (PID: 2708)
- helppane.exe (PID: 2884)
- svchost.exe (PID: 2216)
- WerFault.exe (PID: 2740)
- mshta.exe (PID: 4092)
- UserAccountControlSettings.exe (PID: 3080)
- consent.exe (PID: 1016)
- svchost.exe (PID: 3148)
- WerFault.exe (PID: 2636)
- conhost.exe (PID: 3532)
- WerFault.exe (PID: 2472)
Loads the Task Scheduler COM API
- explorer.exe (PID: 3908)
- explorer.exe (PID: 2704)
Changes the Startup folder
- conhost.exe (PID: 3532)
SUSPICIOUS
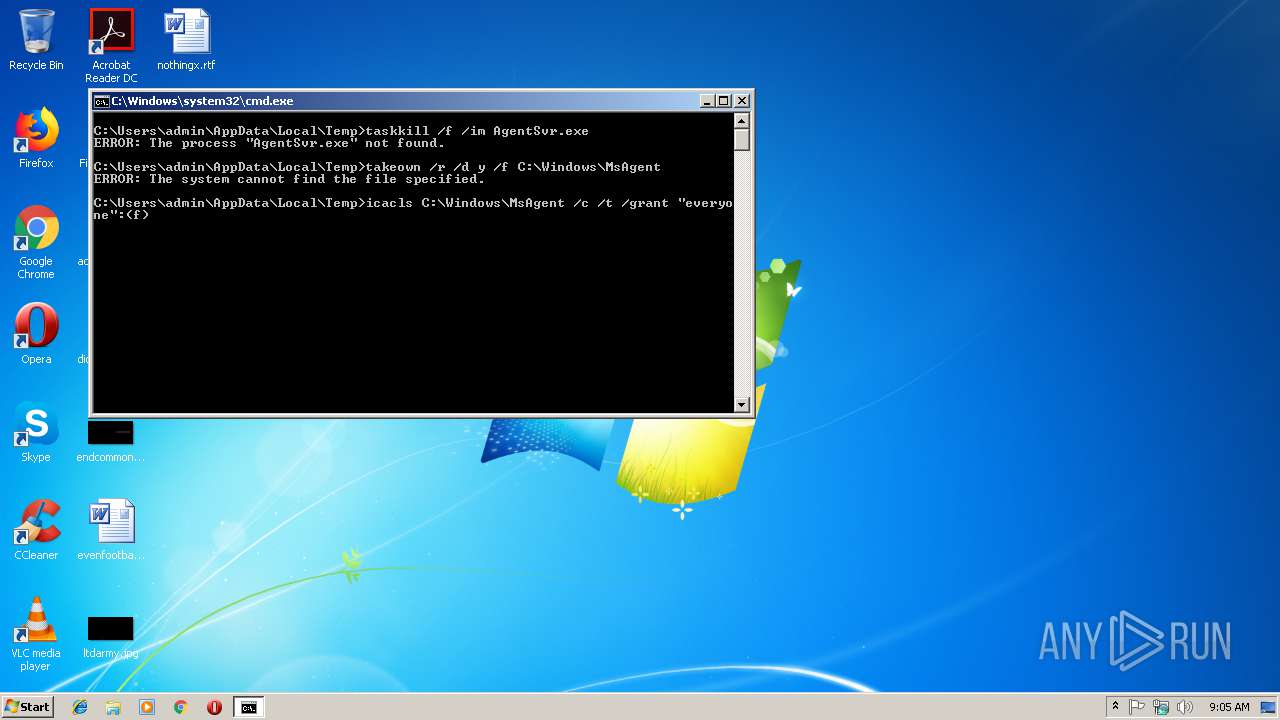
Uses ICACLS.EXE to modify access control list
- cmd.exe (PID: 2232)
Executable content was dropped or overwritten
- Bonzify.exe (PID: 3712)
- INSTALLER.exe (PID: 3316)
Starts CMD.EXE for commands execution
- Bonzify.exe (PID: 3712)
Uses TASKKILL.EXE to kill process
- cmd.exe (PID: 2232)
Creates files in the Windows directory
- Bonzify.exe (PID: 3712)
- INSTALLER.exe (PID: 3376)
- INSTALLER.exe (PID: 3316)
- SetupUtility.exe (PID: 2580)
- setupugc.exe (PID: 3776)
- PresentationFontCache.exe (PID: 2708)
Creates COM task schedule object
- regsvr32.exe (PID: 2228)
- regsvr32.exe (PID: 3264)
- regsvr32.exe (PID: 3284)
- regsvr32.exe (PID: 2132)
- regsvr32.exe (PID: 2544)
- regsvr32.exe (PID: 2296)
- regsvr32.exe (PID: 3332)
- regsvr32.exe (PID: 2492)
- regsvr32.exe (PID: 2236)
- explorer.exe (PID: 3908)
- svchost.exe (PID: 300)
- helppane.exe (PID: 2884)
- WerFault.exe (PID: 4020)
- svchost.exe (PID: 2216)
- WerFault.exe (PID: 2740)
- explorer.exe (PID: 2704)
- mshta.exe (PID: 4092)
- UserAccountControlSettings.exe (PID: 3080)
- svchost.exe (PID: 3148)
- consent.exe (PID: 1016)
- conhost.exe (PID: 3532)
- WerFault.exe (PID: 2636)
- WerFault.exe (PID: 2472)
Removes files from Windows directory
- INSTALLER.exe (PID: 3376)
- INSTALLER.exe (PID: 3316)
- PresentationFontCache.exe (PID: 2708)
Creates a software uninstall entry
- INSTALLER.exe (PID: 3316)
Reads internet explorer settings
- helppane.exe (PID: 2884)
- mshta.exe (PID: 4092)
Executes scripts
- UserAccountControlSettings.exe (PID: 3080)
- oobeldr.exe (PID: 2772)
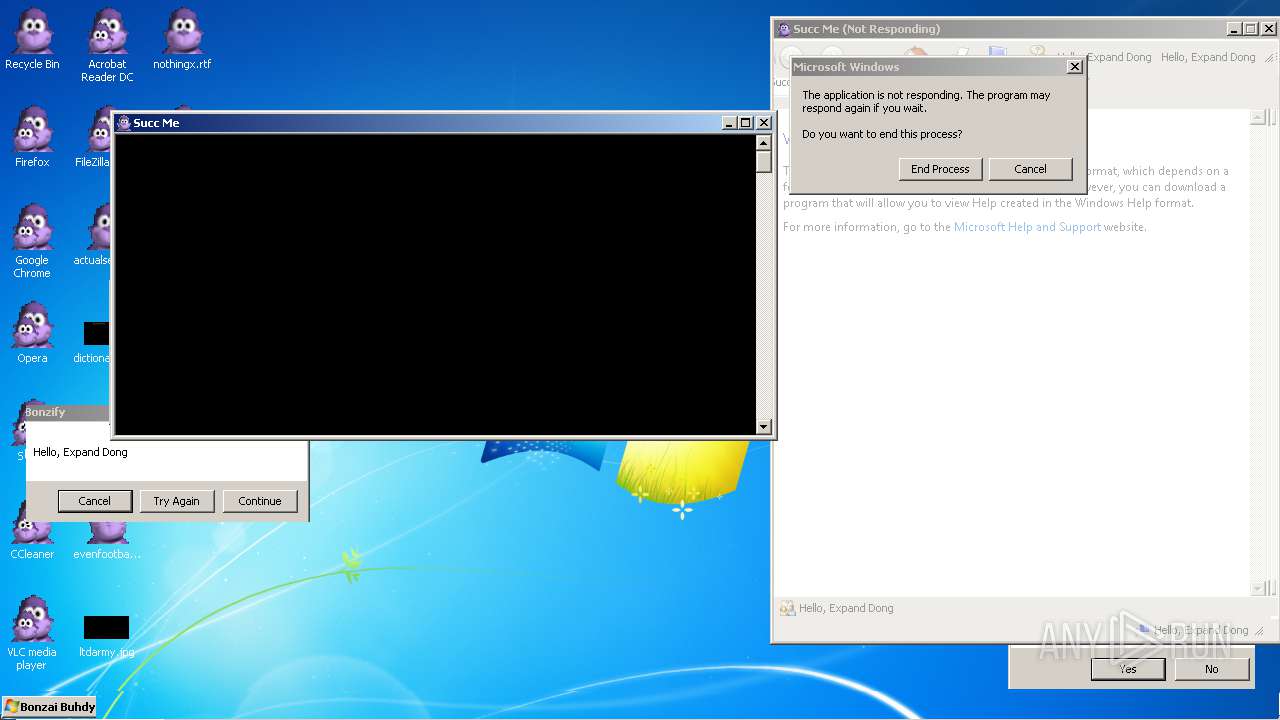
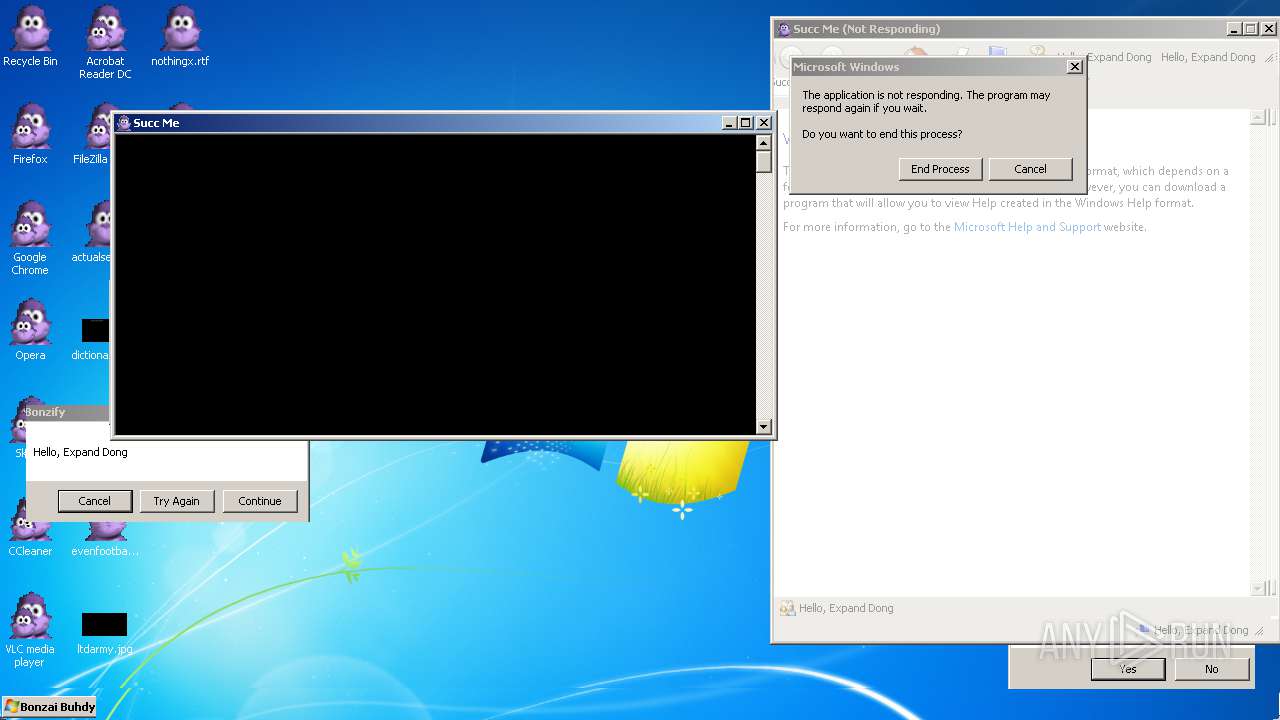
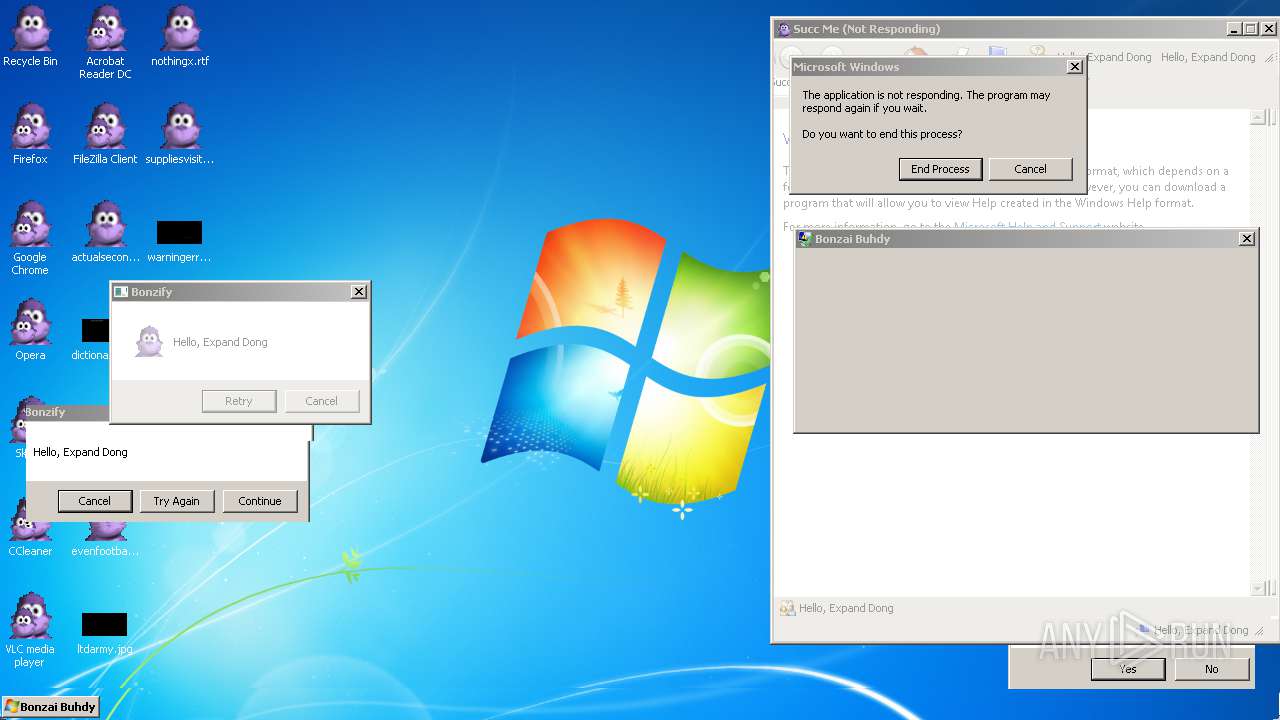
Executes application which crashes
- svchost.exe (PID: 3148)
Modifies the open verb of a shell class
- WerFault.exe (PID: 2636)
- conhost.exe (PID: 3532)
INFO
Dropped object may contain Bitcoin addresses
- Bonzify.exe (PID: 3712)
Application was crashed
- SearchProtocolHost.exe (PID: 3260)
- SearchProtocolHost.exe (PID: 2340)
- helppane.exe (PID: 2884)
- SearchFilterHost.exe (PID: 2980)
- explorer.exe (PID: 2704)
- svchost.exe (PID: 696)
- svchost.exe (PID: 3148)
- WerFault.exe (PID: 2976)
- consent.exe (PID: 1016)
- UserAccountControlSettings.exe (PID: 3080)
- oobeldr.exe (PID: 2772)
- WerFault.exe (PID: 2636)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 MS Cabinet Self-Extractor (WExtract stub) (86.7) |
|---|---|---|
| .exe | | | Win32 Executable MS Visual C++ (generic) (8.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (1.8) |
| .exe | | | Win32 Executable (generic) (1.2) |
| .exe | | | Generic Win/DOS Executable (0.5) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2018:11:04 16:17:05+01:00 |
| PEType: | PE32 |
| LinkerVersion: | 14 |
| CodeSize: | 4096 |
| InitializedDataSize: | 6697984 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x16b0 |
| OSVersion: | 5.1 |
| ImageVersion: | - |
| SubsystemVersion: | 5.1 |
| Subsystem: | Windows GUI |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_GUI |
| Compilation Date: | 04-Nov-2018 15:17:05 |
| Detected languages: |
|
| Debug artifacts: |
|
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x000000D8 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 5 |
| Time date stamp: | 04-Nov-2018 15:17:05 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00001000 | 0x00000F88 | 0x00001000 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.51622 |
.rdata | 0x00002000 | 0x0000109C | 0x00001200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.14506 |
.data | 0x00004000 | 0x00000020 | 0x00000000 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ, IMAGE_SCN_MEM_WRITE | 0 |
.rsrc | 0x00005000 | 0x00661DD0 | 0x00661E00 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 7.84973 |
.reloc | 0x00667000 | 0x000001C4 | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 6.08408 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 4.89623 | 392 | UNKNOWN | English - United States | RT_MANIFEST |
2 | 5.01704 | 2216 | UNKNOWN | UNKNOWN | RT_ICON |
100 | 7.82633 | 5249795 | UNKNOWN | UNKNOWN | DATA |
101 | 7.78087 | 400536 | UNKNOWN | UNKNOWN | DATA |
102 | 7.93147 | 1021232 | UNKNOWN | UNKNOWN | DATA |
103 | 4.86014 | 158 | UNKNOWN | UNKNOWN | DATA |
104 | 4.44475 | 45 | UNKNOWN | UNKNOWN | DATA |
110 | 5.5319 | 15872 | UNKNOWN | UNKNOWN | DATA |
IDI_BONZI | 2.32824 | 34 | UNKNOWN | UNKNOWN | RT_GROUP_ICON |
Imports
ADVAPI32.dll |
KERNEL32.dll |
OLEAUT32.dll |
SHELL32.dll |
SHLWAPI.dll |
USER32.dll |
ole32.dll |
Total processes
175
Monitored processes
85
Malicious processes
19
Suspicious processes
4
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 300 | C:\Windows\System32\svchost.exe -k WerSvcGroup | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 3221226356 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 640 | "C:\Windows\winsxs\x86_microsoft-windows-t..flicklearningwizard_31bf3856ad364e35_6.1.7600.16385_none_0d580453d317a99d\FlickLearningWizard.exe" | C:\Windows\winsxs\x86_microsoft-windows-t..flicklearningwizard_31bf3856ad364e35_6.1.7600.16385_none_0d580453d317a99d\FlickLearningWizard.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Flicks Training Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 696 | C:\Windows\System32\svchost.exe -k WerSvcGroup | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 3221225477 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 860 | C:\Windows\system32\WerFault.exe -u -p 2772 -s 260 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 2147942405 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 896 | \??\C:\Windows\system32\conhost.exe | C:\Windows\system32\conhost.exe | — | csrss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1016 | consent.exe 844 342 004295A8 | C:\Windows\system32\consent.exe | svchost.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Consent UI for administrative applications Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1076 | "C:\Windows\winsxs\x86_microsoft-windows-taskhost_31bf3856ad364e35_6.1.7601.17514_none_2a461244b897f204\taskhost.exe" | C:\Windows\winsxs\x86_microsoft-windows-taskhost_31bf3856ad364e35_6.1.7601.17514_none_2a461244b897f204\taskhost.exe | — | WerFault.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Host Process for Windows Tasks Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1144 | "C:\Windows\winsxs\x86_microsoft-windows-secinit_31bf3856ad364e35_6.1.7600.16385_none_878e469b2e51ce80\secinit.exe" | C:\Windows\winsxs\x86_microsoft-windows-secinit_31bf3856ad364e35_6.1.7600.16385_none_878e469b2e51ce80\secinit.exe | — | WerFault.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Security Init Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1340 | C:\Windows\system32\WerFault.exe -u -p 696 -s 280 | C:\Windows\system32\WerFault.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows Problem Reporting Exit code: 2147942405 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 1436 | C:\Windows\system32\WerFault.exe -u -p 3260 -s 1088 | C:\Windows\system32\WerFault.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Problem Reporting Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 559
Read events
3 097
Write events
5 442
Delete events
20
Modification events
| (PID) Process: | (3376) INSTALLER.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\Setup\SetupapiLogStatus |
| Operation: | write | Name: | setupapi.app.log |
Value: 4096 | |||
| (PID) Process: | (2132) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Agent.Control.1 |
| Operation: | write | Name: | |
Value: Microsoft Agent Control 1.5 | |||
| (PID) Process: | (2132) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Agent.Control.1\CLSID |
| Operation: | write | Name: | |
Value: {F5BE8BD2-7DE6-11D0-91FE-00C04FD701A5} | |||
| (PID) Process: | (2132) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Agent.Control.2 |
| Operation: | write | Name: | |
Value: Microsoft Agent Control 2.0 | |||
| (PID) Process: | (2132) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Agent.Control.2\CLSID |
| Operation: | write | Name: | |
Value: {D45FD31B-5C6E-11D1-9EC1-00C04FD7081F} | |||
| (PID) Process: | (2132) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Agent.Control |
| Operation: | write | Name: | |
Value: Microsoft Agent Control 2.0 | |||
| (PID) Process: | (2132) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\Agent.Control\CurVer |
| Operation: | write | Name: | |
Value: Agent.Control.2 | |||
| (PID) Process: | (2132) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F} |
| Operation: | write | Name: | |
Value: Microsoft Agent Control 2.0 | |||
| (PID) Process: | (2132) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\ProgID |
| Operation: | write | Name: | |
Value: Agent.Control.2 | |||
| (PID) Process: | (2132) regsvr32.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Classes\CLSID\{D45FD31B-5C6E-11D1-9EC1-00C04FD7081F}\VersionIndependentProgID |
| Operation: | write | Name: | |
Value: Agent.Control | |||
Executable files
8
Suspicious files
5
Text files
47
Unknown types
11
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3316 | INSTALLER.exe | C:\Windows\lhsp\tv\SET2EC0.tmp | — | |
MD5:— | SHA256:— | |||
| 3316 | INSTALLER.exe | C:\Windows\lhsp\tv\SET2ED0.tmp | — | |
MD5:— | SHA256:— | |||
| 3316 | INSTALLER.exe | C:\Windows\lhsp\help\SET2EE1.tmp | — | |
MD5:— | SHA256:— | |||
| 3316 | INSTALLER.exe | C:\Windows\fonts\SET2EF2.tmp | — | |
MD5:— | SHA256:— | |||
| 3316 | INSTALLER.exe | C:\Windows\INF\SET2F12.tmp | — | |
MD5:— | SHA256:— | |||
| 3316 | INSTALLER.exe | C:\Windows\system32\SET2F32.tmp | — | |
MD5:— | SHA256:— | |||
| 3316 | INSTALLER.exe | C:\Windows\Temp\OLD2F4C.tmp | — | |
MD5:— | SHA256:— | |||
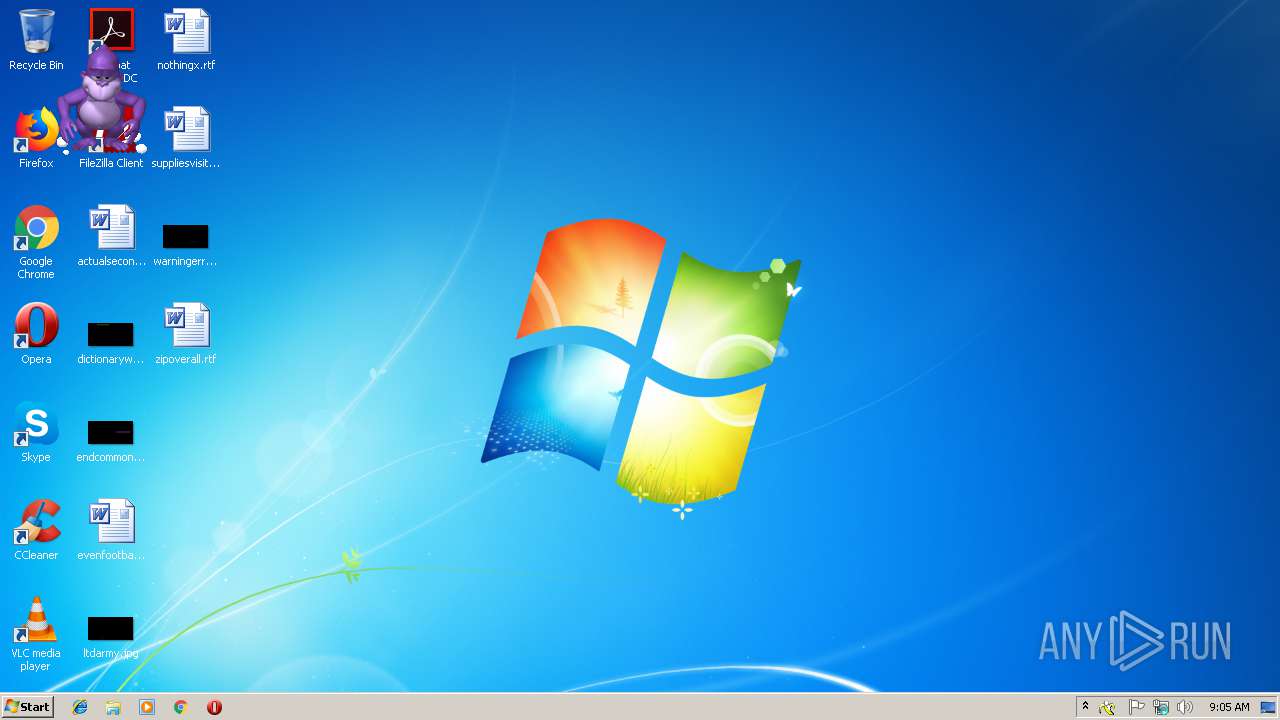
| 3712 | Bonzify.exe | C:\Windows\msagent\chars\Bonzi.acs | — | |
MD5:— | SHA256:— | |||
| 1436 | WerFault.exe | C:\Users\admin\AppData\Local\Temp\WER5735.tmp.mdmp | — | |
MD5:— | SHA256:— | |||
| 3316 | INSTALLER.exe | C:\Users\admin\AppData\Local\Temp\IXP000.TMP\ADVPACK.DLL | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
0
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
DNS requests
Threats
Process | Message |
|---|---|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|
AgentSvr.exe | ClaimOutput
|
AgentSvr.exe | UnclaimOutput
|