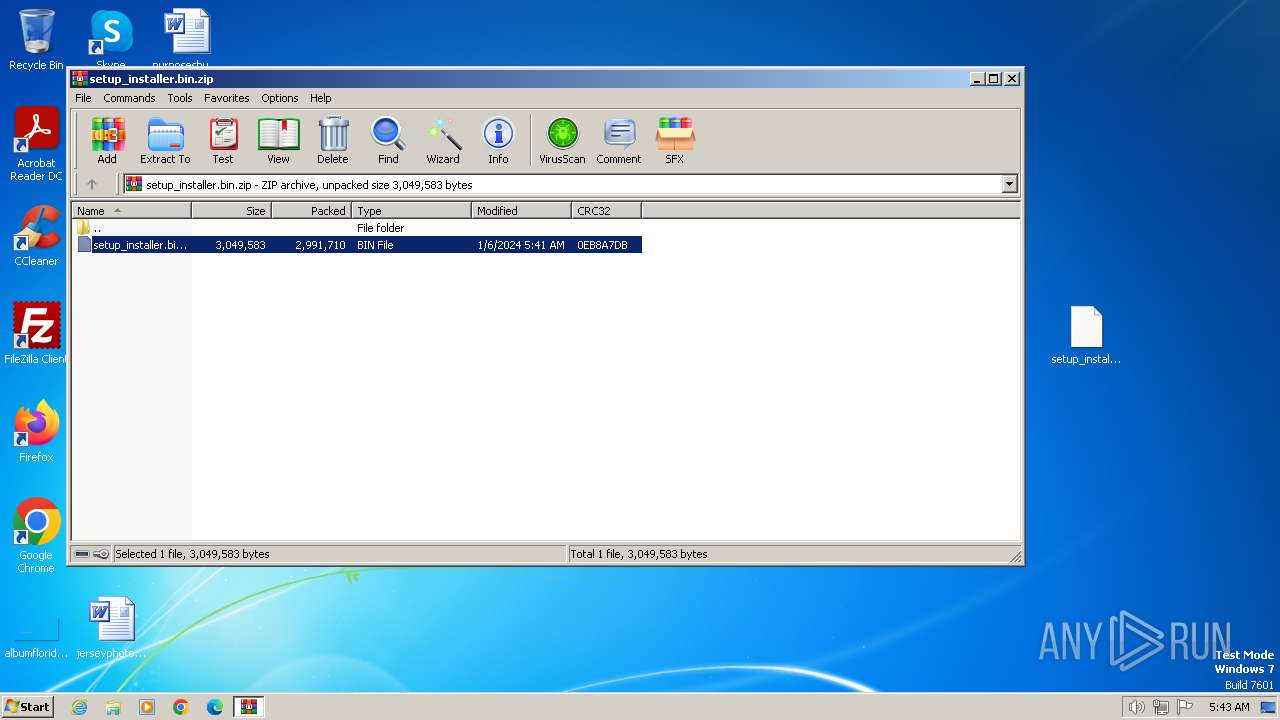
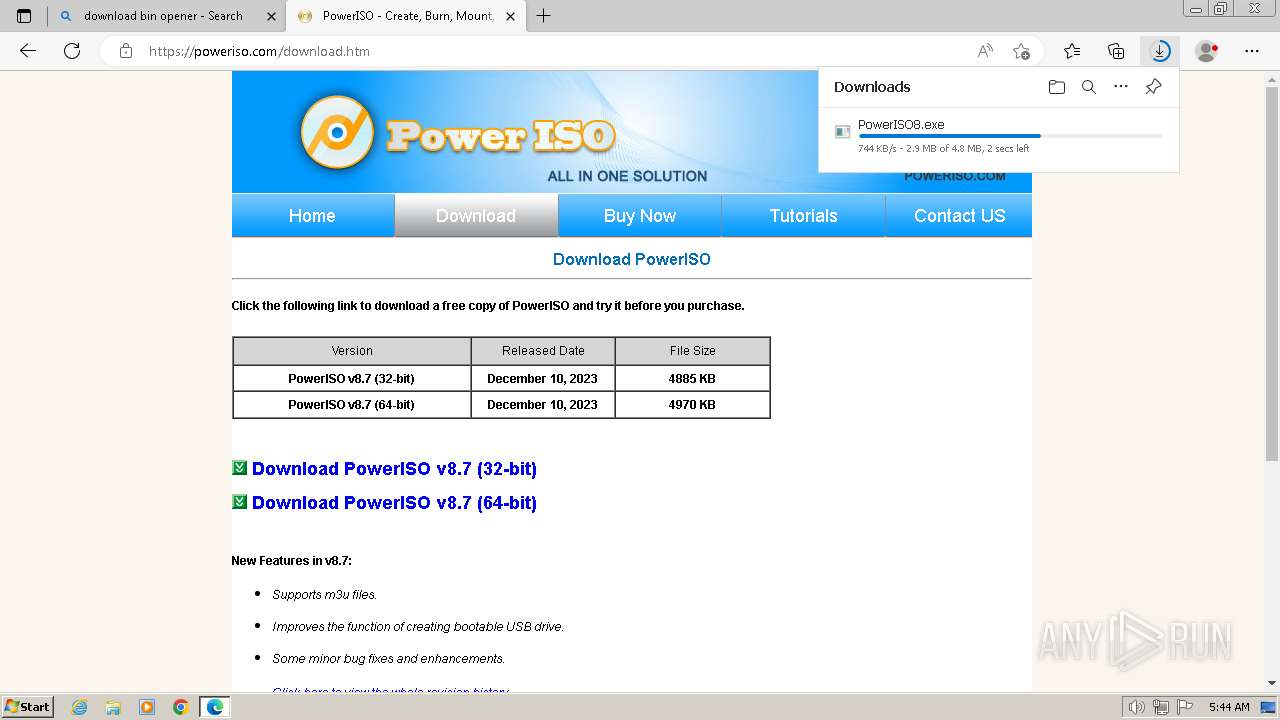
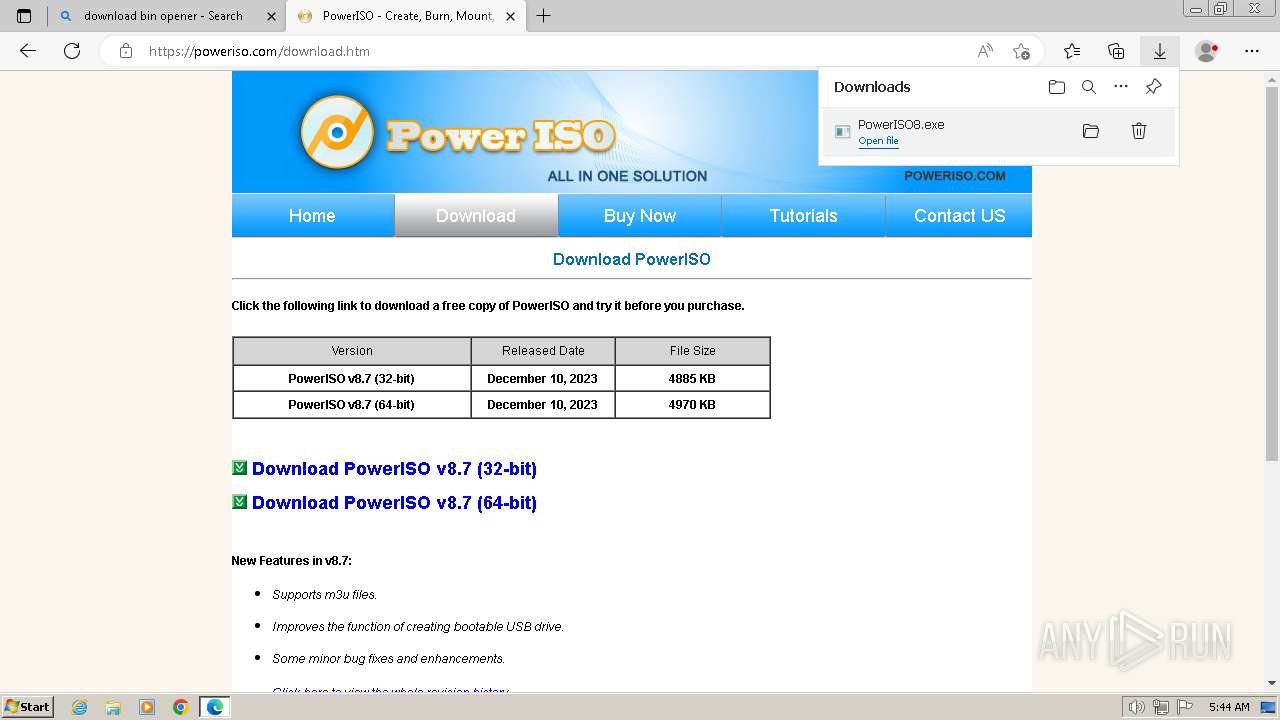
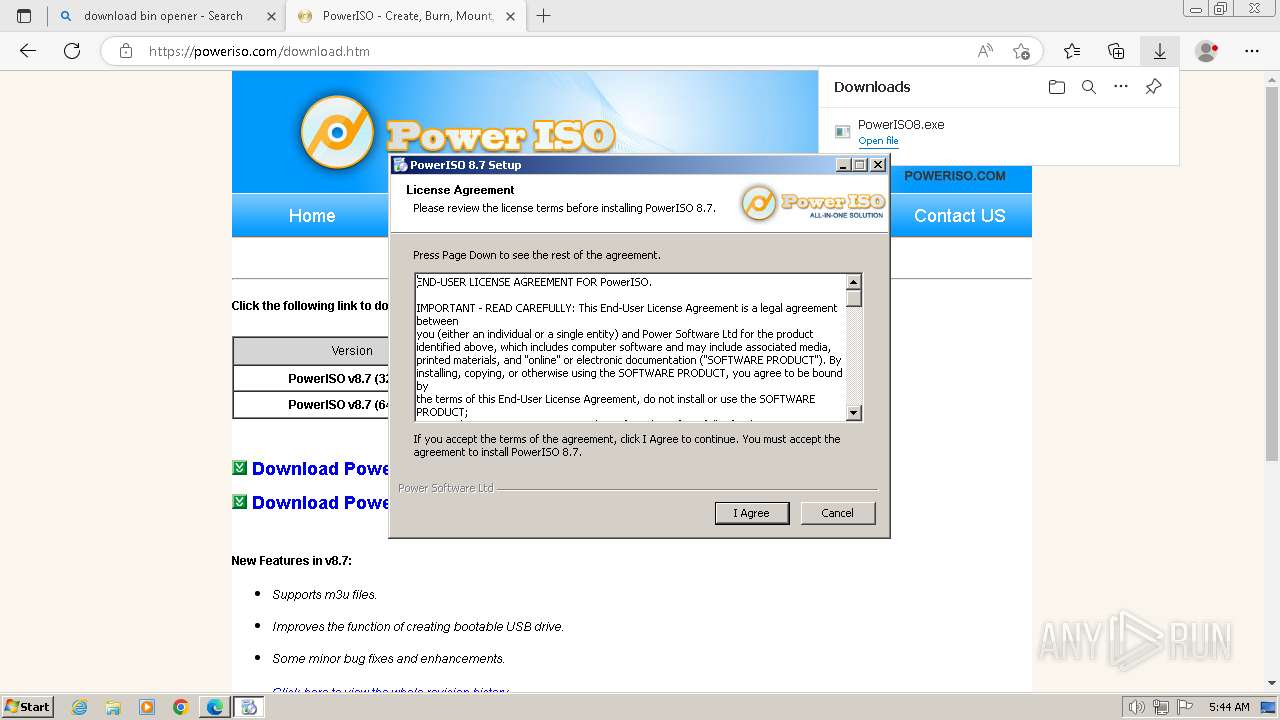
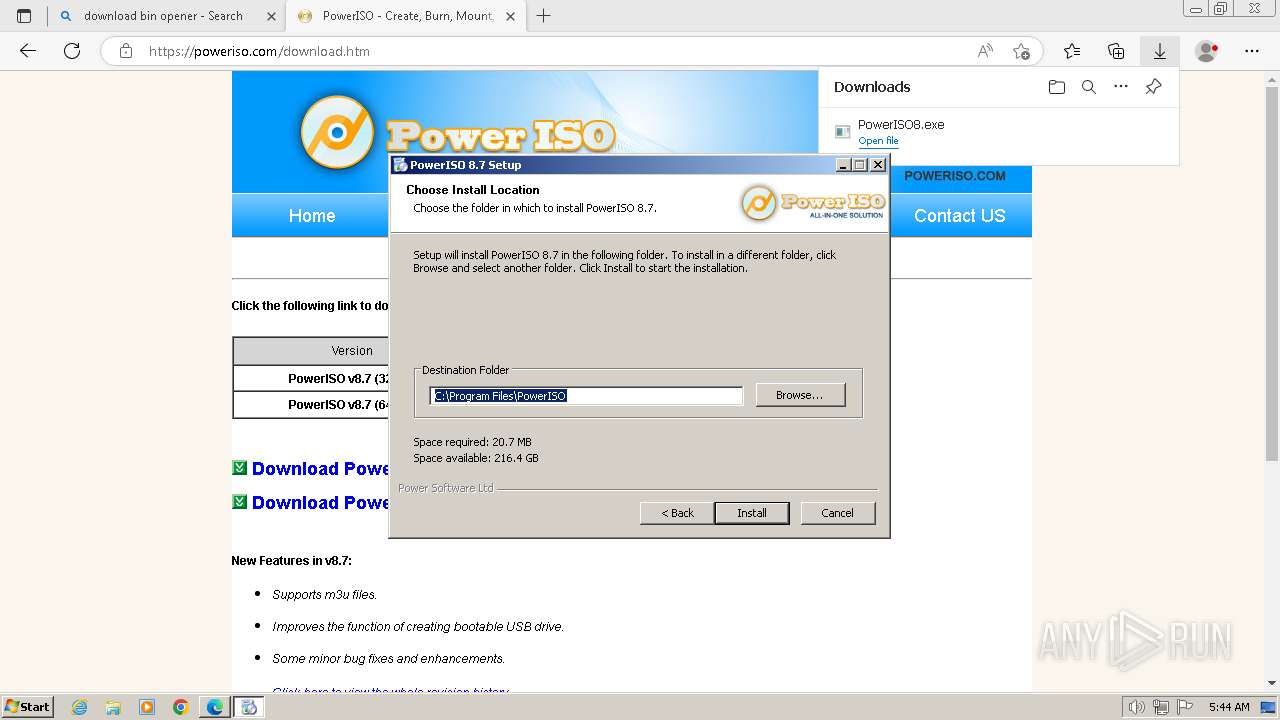
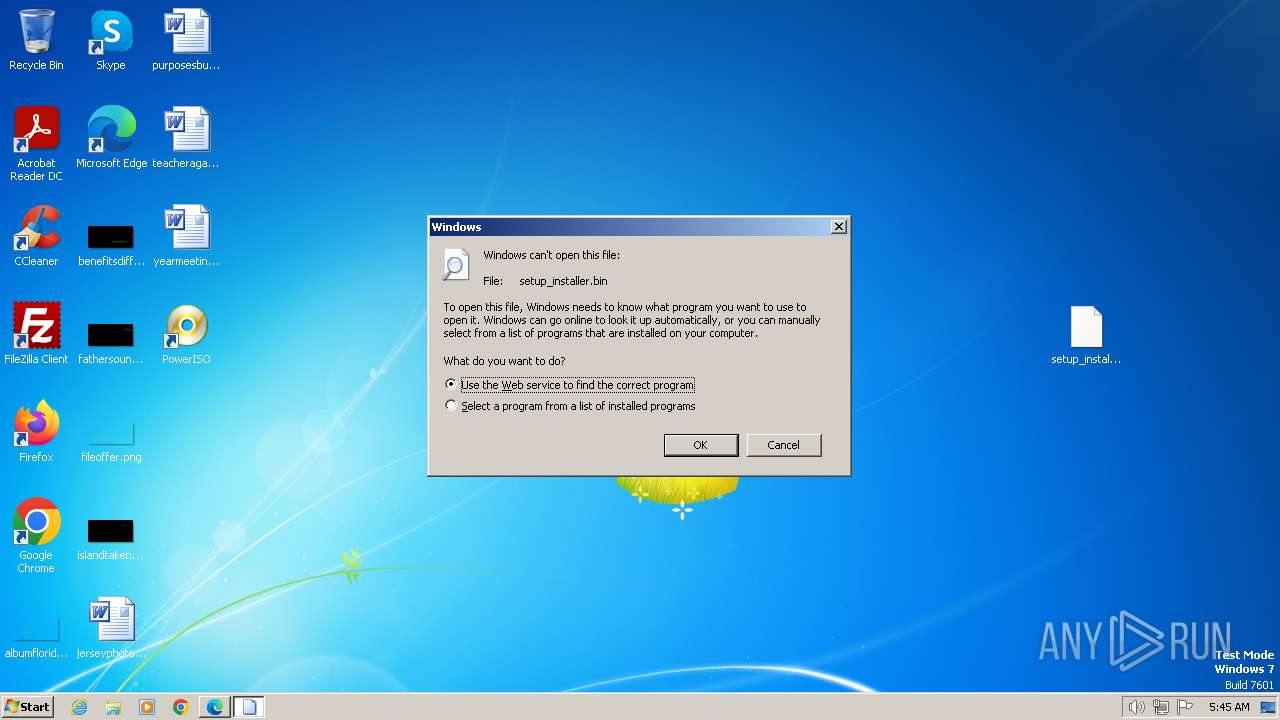
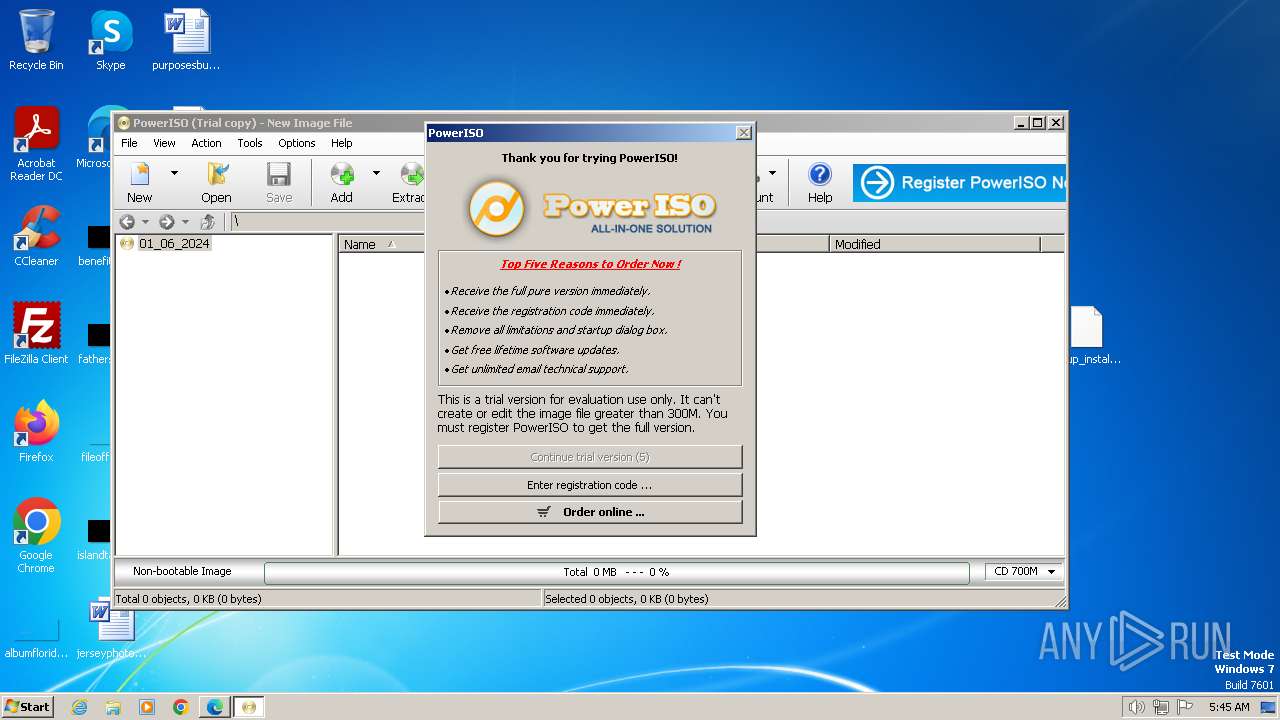
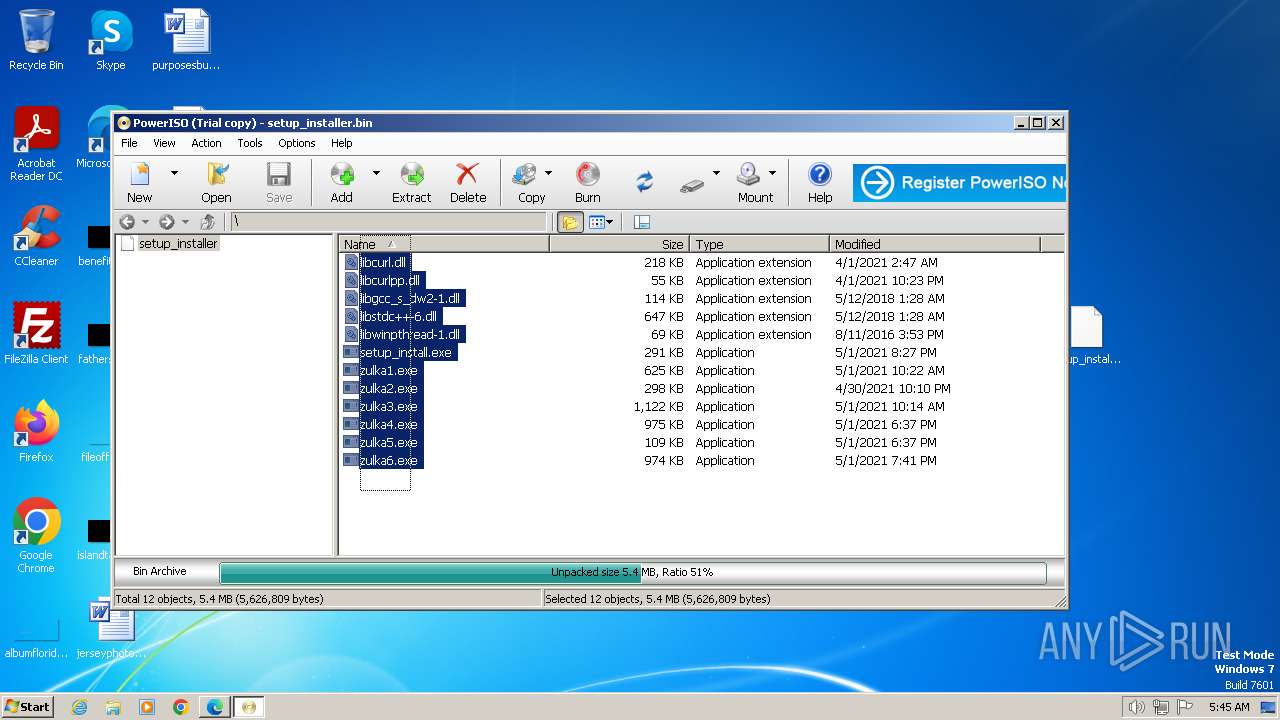
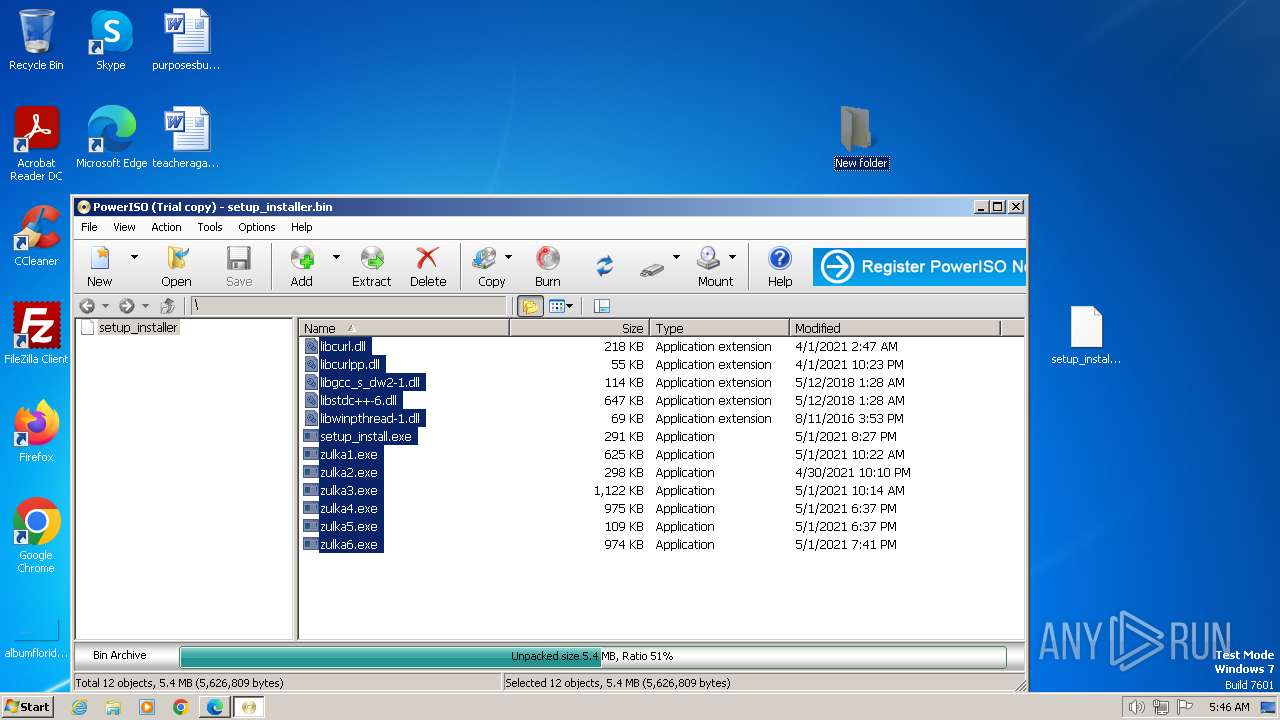
| File name: | setup_installer.bin.zip |
| Full analysis: | https://app.any.run/tasks/32cf7d22-5898-48cd-a84a-d96888563719 |
| Verdict: | Malicious activity |
| Analysis date: | January 06, 2024, 05:42:34 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v5.1 to extract |
| MD5: | BA318B6B520B6A7773A08E116A10AB32 |
| SHA1: | 8FFB8478FF3A0E00FF26F5E9374641BA428A16C1 |
| SHA256: | AB0ABCB3F9390A3783CBDCD89833634B29F527368B40987BC796A3854E21B12A |
| SSDEEP: | 98304:tHr+XwvQzGa1TTHNLzG5CTLREHtCS3qwgw7QSBXRnpjs6hl2e34O5k6mB4bQPkIZ:sFB8dhdU |
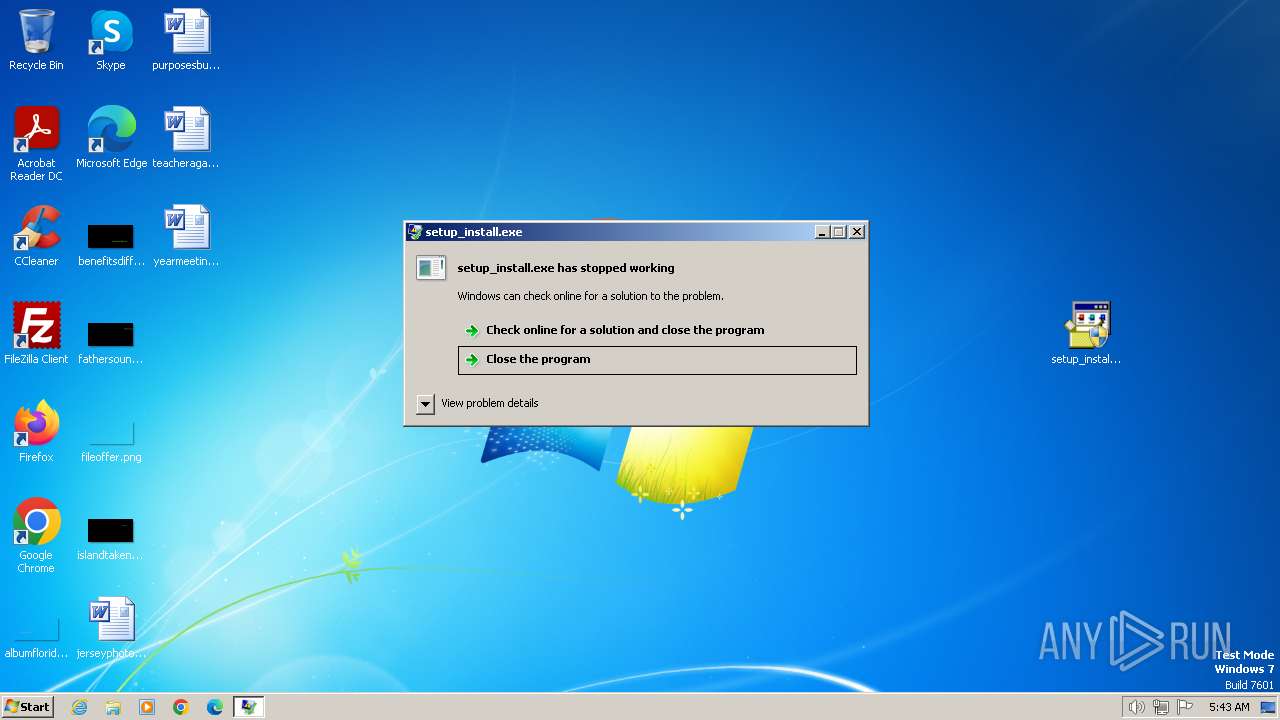
MALICIOUS
Registers / Runs the DLL via REGSVR32.EXE
- PowerISO8.exe (PID: 3992)
- PowerISO.exe (PID: 332)
Creates a writable file in the system directory
- PowerISO8.exe (PID: 3992)
Runs injected code in another process
- rundll32.exe (PID: 3984)
SUSPICIOUS
Reads the Internet Settings
- setup_installer.exe (PID: 1624)
- PowerISO8.exe (PID: 3992)
- PowerISO.exe (PID: 332)
- zulka3.exe (PID: 1344)
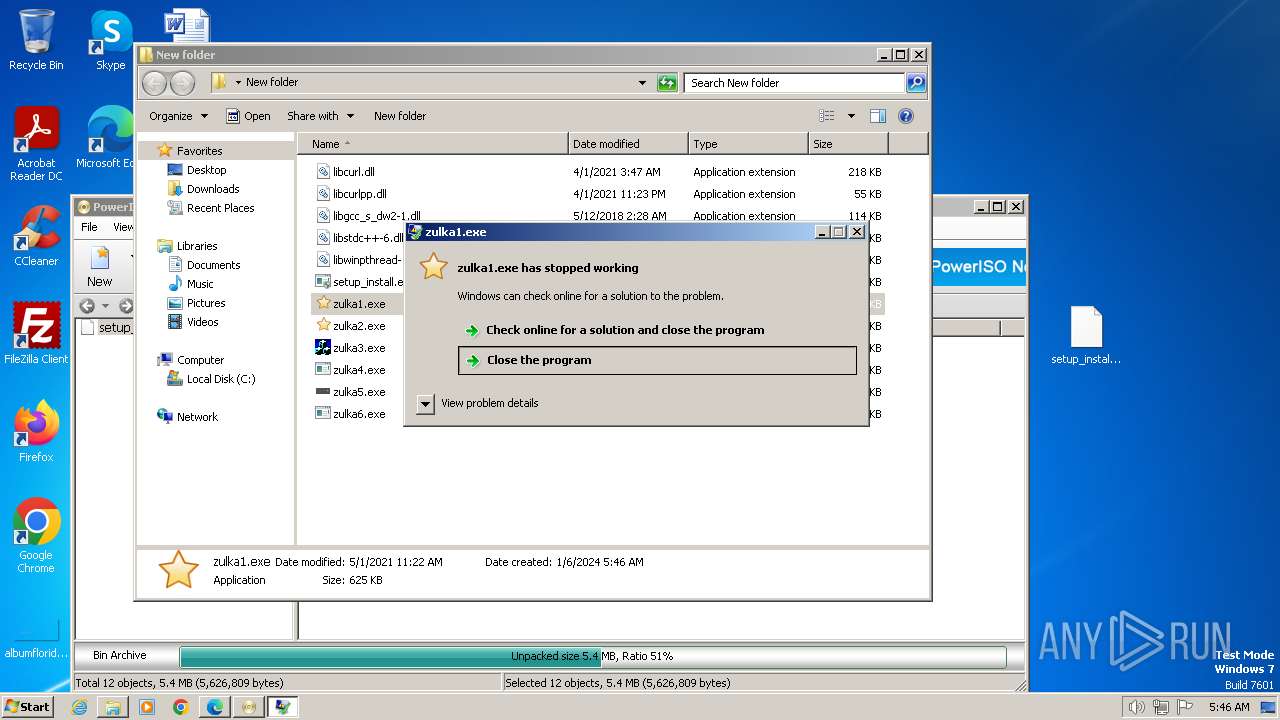
- zulka1.exe (PID: 3616)
- zulka5.exe (PID: 268)
- zulka5.exe (PID: 2472)
The process creates files with name similar to system file names
- PowerISO8.exe (PID: 3992)
Reads settings of System Certificates
- PowerISO8.exe (PID: 3992)
- PowerISO.exe (PID: 332)
- zulka5.exe (PID: 268)
- zulka1.exe (PID: 3616)
Creates files in the driver directory
- PowerISO8.exe (PID: 3992)
Drops a system driver (possible attempt to evade defenses)
- PowerISO8.exe (PID: 3992)
Checks Windows Trust Settings
- PowerISO.exe (PID: 332)
- zulka1.exe (PID: 3616)
Adds/modifies Windows certificates
- PowerISO.exe (PID: 332)
Uses RUNDLL32.EXE to load library
- zulka3.exe (PID: 1344)
Reads security settings of Internet Explorer
- PowerISO.exe (PID: 332)
- zulka1.exe (PID: 3616)
INFO
Drops 7-zip archiver for unpacking
- WinRAR.exe (PID: 116)
- PowerISO8.exe (PID: 3992)
Checks supported languages
- setup_install.exe (PID: 1824)
- PowerISO8.exe (PID: 3992)
- PWRISOVM.EXE (PID: 3096)
- PowerISO.exe (PID: 332)
- zulka3.exe (PID: 1344)
- setup_install.exe (PID: 3440)
- zulka5.exe (PID: 268)
- zulka5.exe (PID: 2472)
- setup_installer.exe (PID: 1624)
- zulka1.exe (PID: 3616)
Manual execution by a user
- msedge.exe (PID: 2244)
- setup_installer.exe (PID: 1504)
- setup_installer.exe (PID: 1624)
- PowerISO.exe (PID: 332)
- rundll32.exe (PID: 4048)
- zulka3.exe (PID: 1344)
- setup_install.exe (PID: 2592)
- setup_install.exe (PID: 3440)
- zulka1.exe (PID: 3616)
- zulka5.exe (PID: 268)
- zulka5.exe (PID: 2472)
- rundll32.exe (PID: 2408)
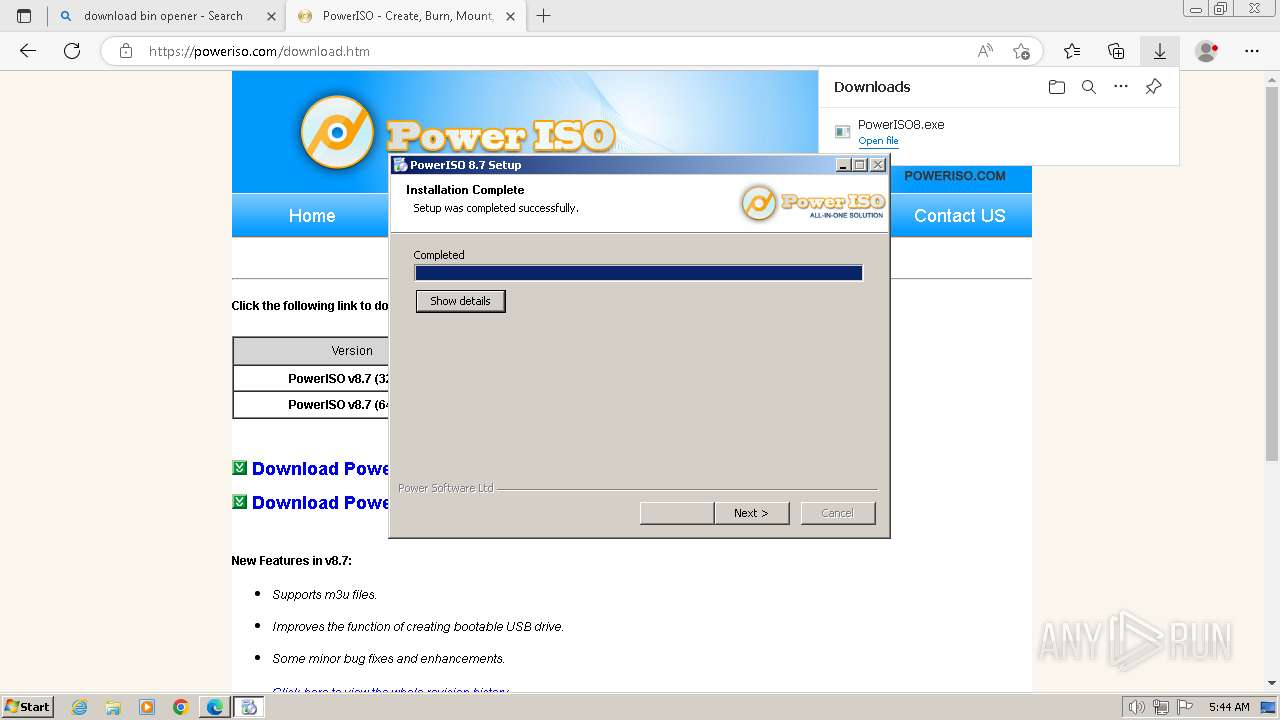
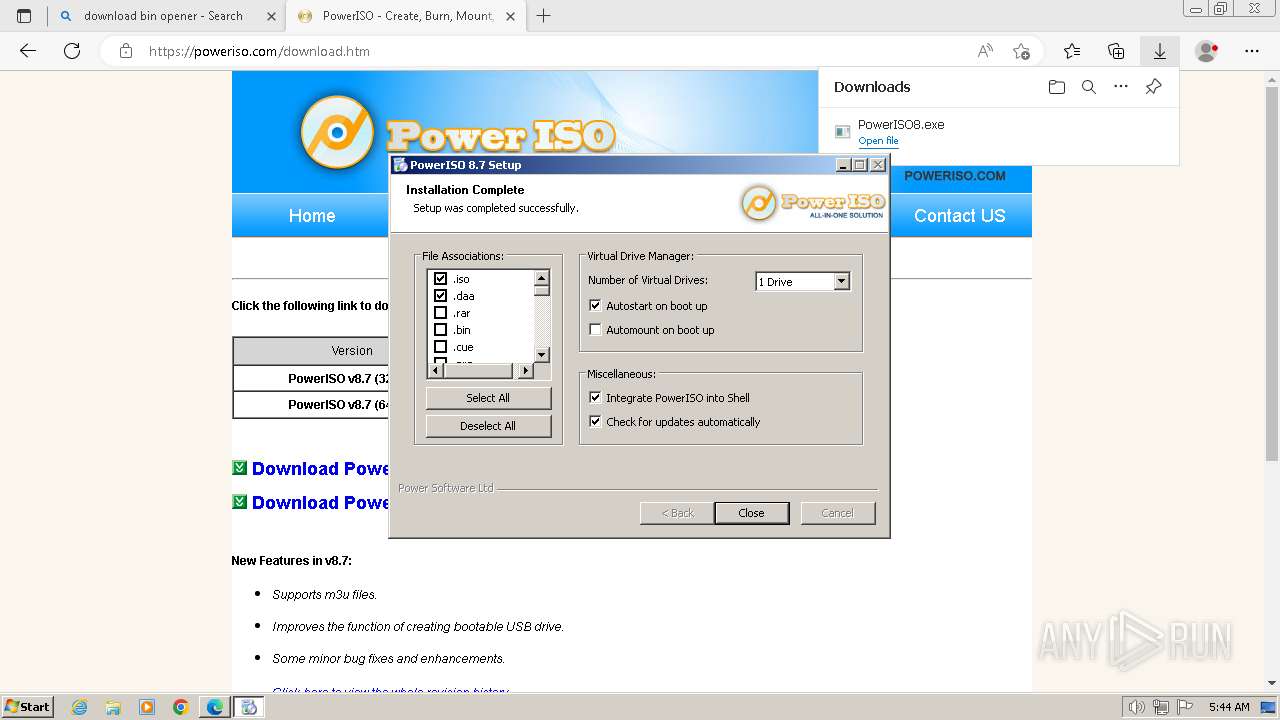
Drops the executable file immediately after the start
- msedge.exe (PID: 2244)
- WinRAR.exe (PID: 116)
- PowerISO8.exe (PID: 3992)
- msedge.exe (PID: 664)
- PowerISO.exe (PID: 332)
- zulka3.exe (PID: 1344)
- setup_installer.exe (PID: 1624)
Reads the computer name
- PowerISO8.exe (PID: 3992)
- setup_install.exe (PID: 1824)
- PowerISO.exe (PID: 332)
- zulka3.exe (PID: 1344)
- setup_install.exe (PID: 3440)
- zulka1.exe (PID: 3616)
- zulka5.exe (PID: 268)
- zulka5.exe (PID: 2472)
- setup_installer.exe (PID: 1624)
Application launched itself
- msedge.exe (PID: 2244)
- msedge.exe (PID: 2936)
Malware-specific behavior (creating "System.dll" in Temp)
- PowerISO8.exe (PID: 3992)
Create files in a temporary directory
- PowerISO8.exe (PID: 3992)
- PowerISO.exe (PID: 332)
- zulka3.exe (PID: 1344)
- zulka5.exe (PID: 268)
- setup_installer.exe (PID: 1624)
Reads the machine GUID from the registry
- PowerISO8.exe (PID: 3992)
- PowerISO.exe (PID: 332)
- zulka1.exe (PID: 3616)
- zulka5.exe (PID: 268)
- zulka5.exe (PID: 2472)
Reads Environment values
- PowerISO8.exe (PID: 3992)
- zulka5.exe (PID: 268)
- zulka5.exe (PID: 2472)
The process uses the downloaded file
- msedge.exe (PID: 2244)
- msedge.exe (PID: 1536)
Creates files in the program directory
- PowerISO8.exe (PID: 3992)
Creates files or folders in the user directory
- PowerISO.exe (PID: 332)
- zulka1.exe (PID: 3616)
Checks proxy server information
- PowerISO.exe (PID: 332)
- zulka1.exe (PID: 3616)
Application was injected by another process
- svchost.exe (PID: 856)
Checks for external IP
- zulka5.exe (PID: 268)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 51 |
|---|---|
| ZipBitFlag: | 0x0009 |
| ZipCompression: | Unknown (99) |
| ZipModifyDate: | 2024:01:06 05:41:48 |
| ZipCRC: | 0x0eb8a7db |
| ZipCompressedSize: | 2991710 |
| ZipUncompressedSize: | 3049583 |
| ZipFileName: | setup_installer.bin |
Total processes
119
Monitored processes
53
Malicious processes
5
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 116 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\setup_installer.bin.zip" | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 188 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=crashpad-handler "--user-data-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" /prefetch:7 --monitor-self-annotation=ptype=crashpad-handler "--database=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Crashpad" "--metrics-dir=C:\Users\admin\AppData\Local\Microsoft\Edge\User Data" --annotation=IsOfficialBuild=1 --annotation=channel= --annotation=chromium-version=109.0.5414.149 "--annotation=exe=C:\Program Files\Microsoft\Edge\Application\msedge.exe" --annotation=plat=Win32 "--annotation=prod=Microsoft Edge" --annotation=ver=109.0.1518.115 --initial-client-data=0xc8,0xcc,0xd0,0x9c,0xd8,0x6d8ff598,0x6d8ff5a8,0x6d8ff5b4 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 268 | "C:\Users\admin\Desktop\New folder\zulka5.exe" | C:\Users\admin\Desktop\New folder\zulka5.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Description: ORAPOL Exit code: 0 Version: 1.0.0.2 Modules
| |||||||||||||||
| 332 | "C:\Program Files\PowerISO\PowerISO.exe" | C:\Program Files\PowerISO\PowerISO.exe | explorer.exe | ||||||||||||
User: admin Company: Power Software Ltd Integrity Level: MEDIUM Description: PowerISO Exit code: 0 Version: 8, 7, 0, 0 Modules
| |||||||||||||||
| 604 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=15 --mojo-platform-channel-handle=3660 --field-trial-handle=1320,i,9269028847400058733,438729194069623144,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 664 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=network.mojom.NetworkService --lang=en-US --service-sandbox-type=none --mojo-platform-channel-handle=1420 --field-trial-handle=1320,i,9269028847400058733,438729194069623144,131072 /prefetch:3 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | msedge.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 856 | C:\Windows\system32\svchost.exe -k netsvcs | C:\Windows\System32\svchost.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Host Process for Windows Services Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 896 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=renderer --disable-gpu-compositing --lang=en-US --js-flags=--ms-user-locale= --device-scale-factor=1 --num-raster-threads=2 --enable-main-frame-before-activation --renderer-client-id=23 --mojo-platform-channel-handle=4636 --field-trial-handle=1320,i,9269028847400058733,438729194069623144,131072 /prefetch:1 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1112 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=chrome.mojom.UtilReadIcon --lang=en-US --service-sandbox-type=icon_reader --mojo-platform-channel-handle=4472 --field-trial-handle=1320,i,9269028847400058733,438729194069623144,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
| 1316 | "C:\Program Files\Microsoft\Edge\Application\msedge.exe" --type=utility --utility-sub-type=edge_collections.mojom.CollectionsDataManager --lang=en-US --service-sandbox-type=collections --mojo-platform-channel-handle=4680 --field-trial-handle=1320,i,9269028847400058733,438729194069623144,131072 /prefetch:8 | C:\Program Files\Microsoft\Edge\Application\msedge.exe | — | msedge.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Microsoft Edge Exit code: 0 Version: 109.0.1518.115 Modules
| |||||||||||||||
Total events
30 058
Read events
29 741
Write events
306
Delete events
11
Modification events
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\virtio_ivshmem_master_build.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (116) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF42000000420000000204000037020000 | |||
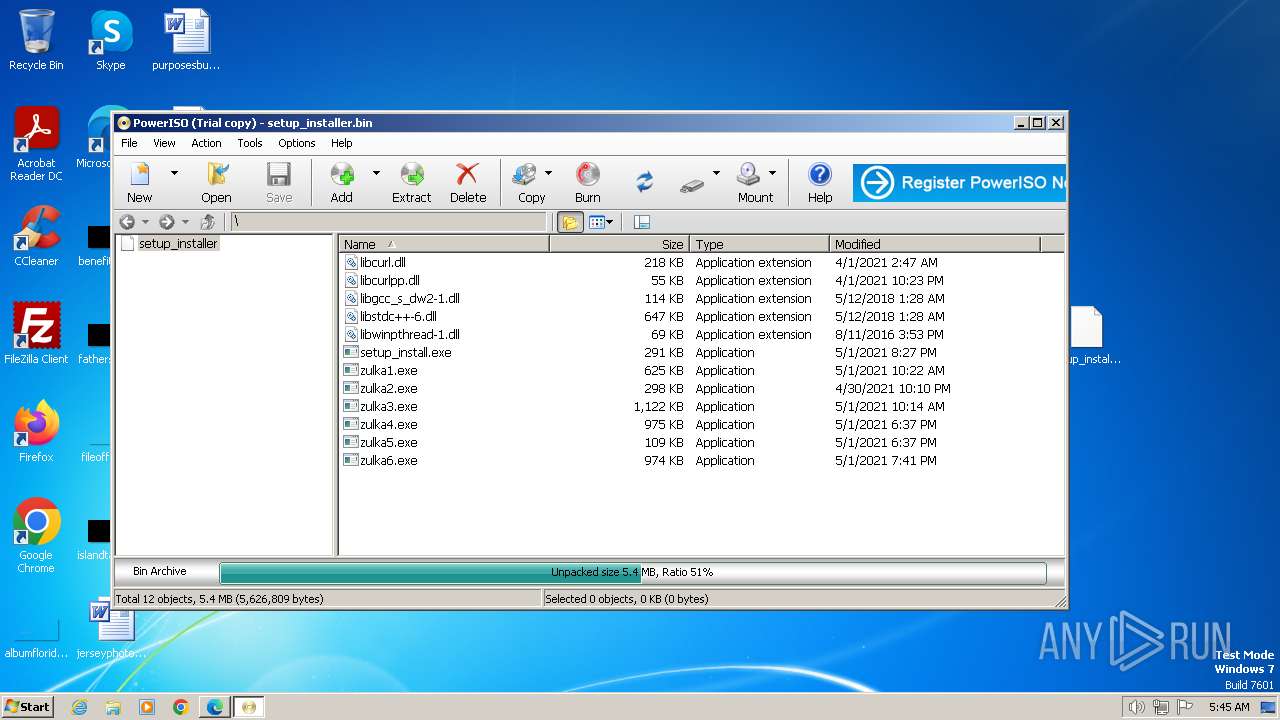
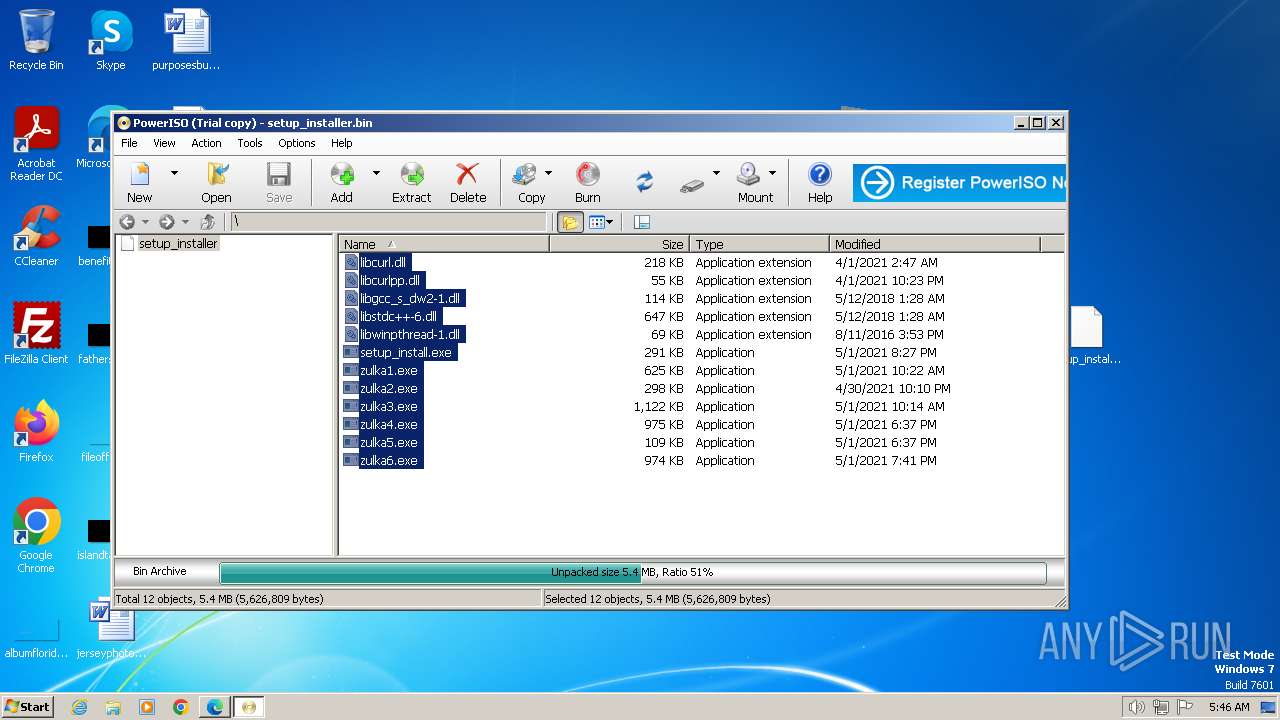
Executable files
87
Suspicious files
1 197
Text files
81
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1624 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zS856B0D7E\setup_install.exe | executable | |
MD5:5B387F1CF6213197662682C6EE74C30B | SHA256:B77A90B0E6EB28E518F6CD02A4D65B870D99A88E58442A1E3F5ED971CC39A97E | |||
| 2244 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old~RFee76e.TMP | — | |
MD5:— | SHA256:— | |||
| 2244 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\commerce_subscription_db\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1624 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zS856B0D7E\libcurl.dll | executable | |
MD5:D09BE1F47FD6B827C81A4812B4F7296F | SHA256:0DE53E7BE51789ADAEC5294346220B20F793E7F8D153A3C110A92D658760697E | |||
| 1624 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zS856B0D7E\zulka2.exe | executable | |
MD5:82ED3ABE9637BB1C5A42B504778D061D | SHA256:1F3A898548A952EF8B6ABA6E47EE5F8CD8446206BCB901AB77E3439F6E94E439 | |||
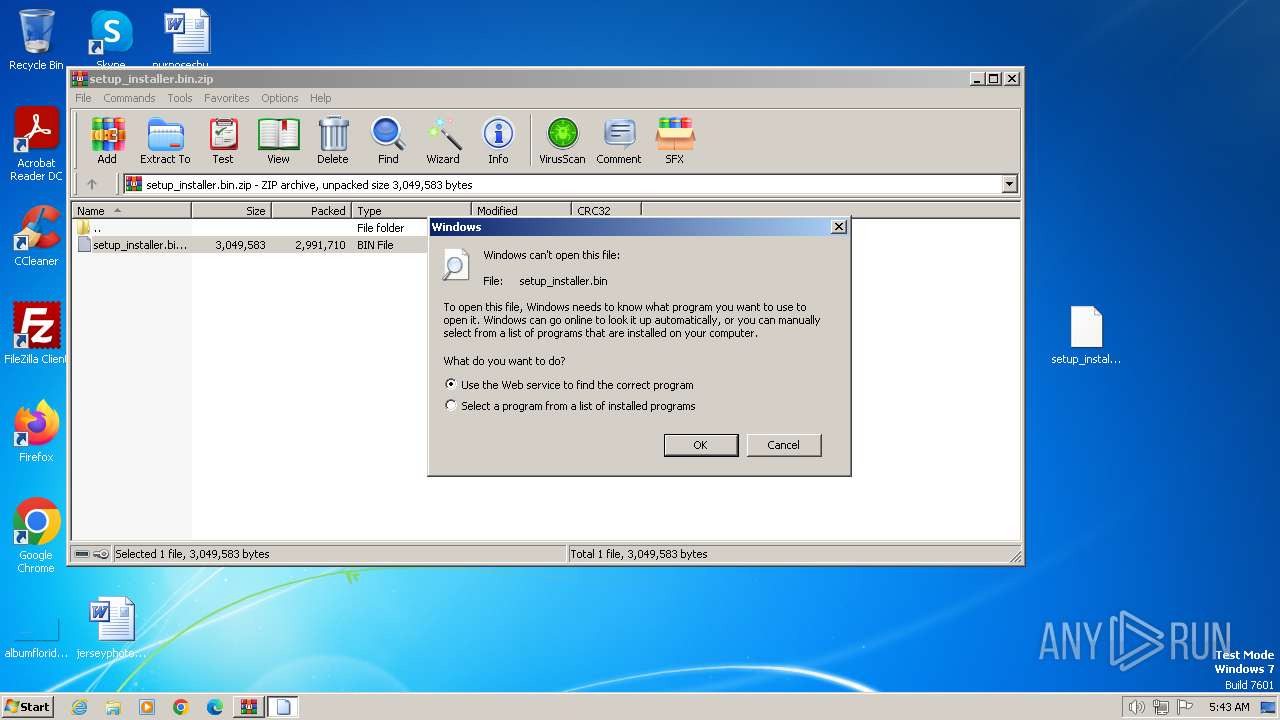
| 116 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$DRb116.25317\setup_installer.bin | executable | |
MD5:C40278CD584D0FF2B3193EAD4D83FF71 | SHA256:E9858377AB766A4A48BCDB45C3B23F6E46AC9CDF5FD8A96FFBFE37197AC6F284 | |||
| 1624 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zS856B0D7E\libcurlpp.dll | executable | |
MD5:E6E578373C2E416289A8DA55F1DC5E8E | SHA256:43E86D650A68F1F91FA2F4375AFF2720E934AA78FA3D33E06363122BF5A9535F | |||
| 2244 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old~RFee79c.TMP | — | |
MD5:— | SHA256:— | |||
| 2244 | msedge.exe | C:\Users\admin\AppData\Local\Microsoft\Edge\User Data\Default\EdgePushStorageWithConnectTokenAndKey\LOG.old | — | |
MD5:— | SHA256:— | |||
| 1624 | setup_installer.exe | C:\Users\admin\AppData\Local\Temp\7zS856B0D7E\libgcc_s_dw2-1.dll | executable | |
MD5:9AEC524B616618B0D3D00B27B6F51DA1 | SHA256:59A466F77584438FC3ABC0F43EDC0FC99D41851726827A008841F05CFE12DA7E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
13
TCP/UDP connections
77
DNS requests
113
Threats
3
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
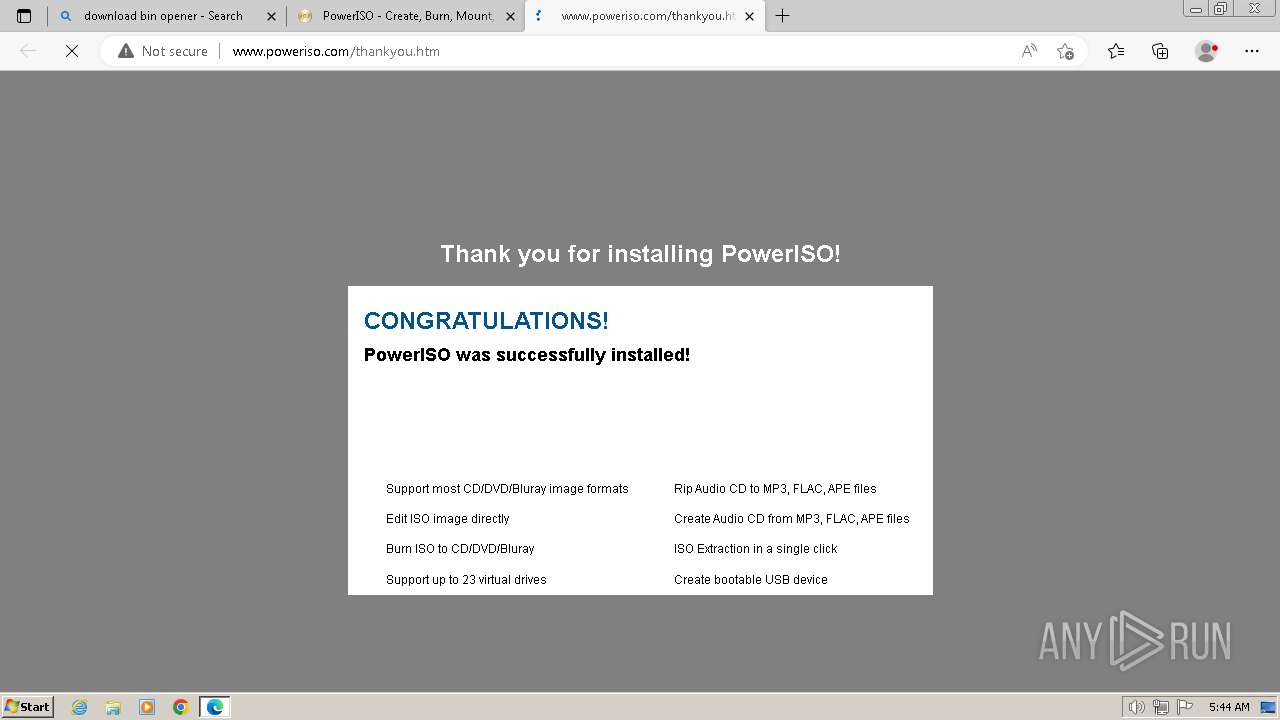
664 | msedge.exe | GET | 200 | 216.92.201.29:80 | http://www.poweriso.com/thankyou.htm | unknown | html | 4.17 Kb | unknown |
664 | msedge.exe | GET | 200 | 216.92.201.29:80 | http://www.poweriso.com/images/thank-you-logo.gif | unknown | image | 20.2 Kb | unknown |
664 | msedge.exe | GET | 200 | 216.92.201.29:80 | http://www.poweriso.com/images/blank.gif | unknown | image | 46 b | unknown |
664 | msedge.exe | GET | 200 | 216.92.201.29:80 | http://www.poweriso.com/images/check.gif | unknown | image | 1.02 Kb | unknown |
332 | PowerISO.exe | GET | 200 | 87.248.202.1:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?45b31ad1f2ad2412 | unknown | compressed | 4.66 Kb | unknown |
332 | PowerISO.exe | GET | 200 | 104.18.38.233:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRTtU9uFqgVGHhJwXZyWCNXmVR5ngQUoBEKIz6W8Qfs4q8p74Klf9AwpLQCEGfe9D7xe9riT%2FWUBgbSwIQ%3D | unknown | binary | 1.42 Kb | unknown |
664 | msedge.exe | GET | 200 | 216.92.201.29:80 | http://www.poweriso.com/favicon.ico | unknown | image | 8.85 Kb | unknown |
664 | msedge.exe | GET | 200 | 216.92.201.29:80 | http://www.poweriso.com/images/thank-you-bg1.gif | unknown | image | 1.03 Kb | unknown |
664 | msedge.exe | GET | 200 | 216.92.201.29:80 | http://www.poweriso.com/images/thank-you-bg.gif | unknown | image | 11.5 Kb | unknown |
1080 | svchost.exe | GET | 304 | 87.248.202.1:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?89bca2e7018c82c0 | unknown | — | — | unknown |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |
664 | msedge.exe | 204.79.197.203:443 | ntp.msn.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
2244 | msedge.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
664 | msedge.exe | 204.79.197.239:443 | edge.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | unknown |
664 | msedge.exe | 13.107.42.16:443 | config.edge.skype.com | MICROSOFT-CORP-MSN-AS-BLOCK | US | whitelisted |
664 | msedge.exe | 23.36.163.97:443 | assets.msn.com | Akamai International B.V. | DE | unknown |
664 | msedge.exe | 2.21.20.136:443 | img-s-msn-com.akamaized.net | Akamai International B.V. | DE | unknown |
664 | msedge.exe | 18.245.60.76:443 | sb.scorecardresearch.com | — | US | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
estrix.xyz |
| unknown |
ntp.msn.com |
| whitelisted |
edge.microsoft.com |
| whitelisted |
config.edge.skype.com |
| whitelisted |
assets.msn.com |
| whitelisted |
img-s-msn-com.akamaized.net |
| whitelisted |
sb.scorecardresearch.com |
| shared |
th.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |
c.msn.com |
| whitelisted |
Threats
PID | Process | Class | Message |
|---|---|---|---|
1080 | svchost.exe | Potential Corporate Privacy Violation | AV POLICY Suspicious Connection to Faceit Domain (DNS Query) |
1080 | svchost.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in DNS Lookup) |
268 | zulka5.exe | Potential Corporate Privacy Violation | ET POLICY IP Check Domain (iplogger .org in TLS SNI) |
Process | Message |
|---|---|
msedge.exe | [0106/054459.880:ERROR:exception_handler_server.cc(527)] ConnectNamedPipe: The pipe is being closed. (0xE8)
|