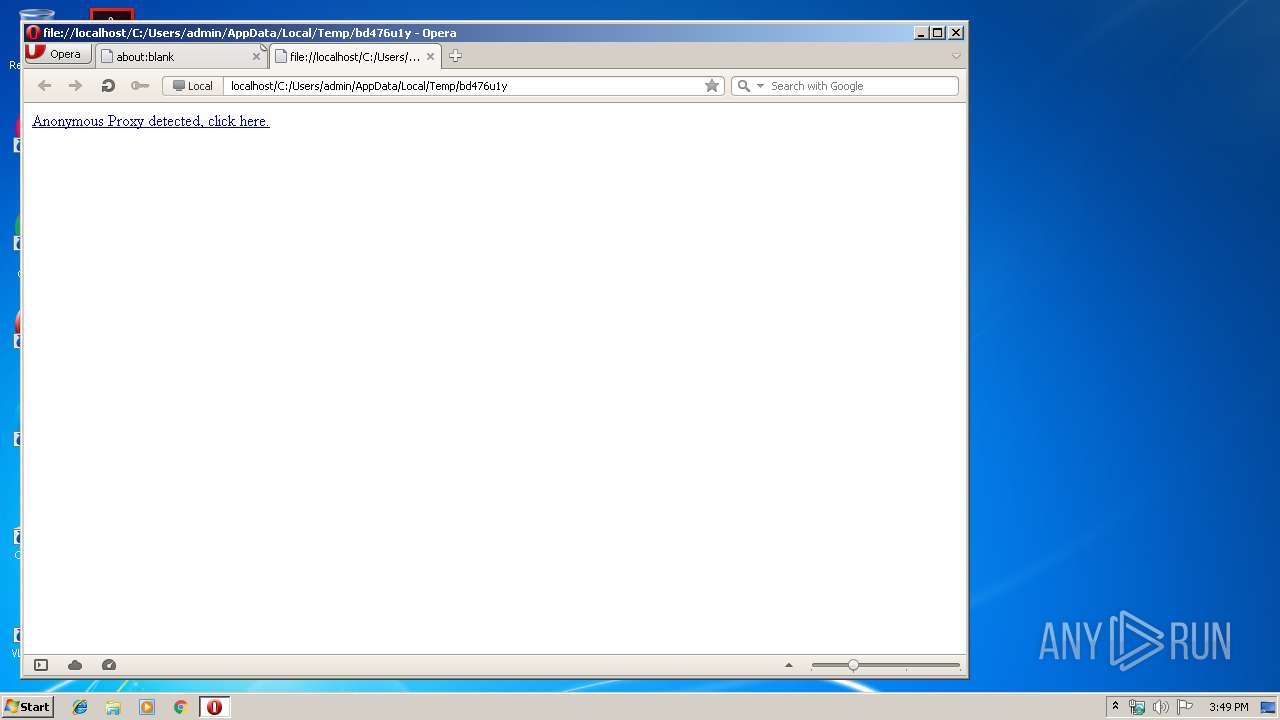
| download: | bd476u1y |
| Full analysis: | https://app.any.run/tasks/06f92a26-ffb7-4c32-b85b-c37e79e4d367 |
| Verdict: | Malicious activity |
| Analysis date: | October 09, 2019, 14:48:11 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | text/plain |
| File info: | ASCII text, with no line terminators |
| MD5: | 99EE039BEEBB7495DA93A31B387BB261 |
| SHA1: | D55D79311BFF72D87EA6E1A40D0246AC1DB820EB |
| SHA256: | AB030A8588EF9530D38A74D9E14B36CCDD792323AF6352D4D5DA9D19B9B95341 |
| SSDEEP: | 3:uNXADiFCDRAKAHEaRE+Vs2+ZJiNRDs7SGKy:uFAyTKEER+T+ZJas7Sdy |
MALICIOUS
No malicious indicators.SUSPICIOUS
No suspicious indicators.INFO
Creates files in the user directory
- Opera.exe (PID: 2596)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
Total processes
33
Monitored processes
2
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
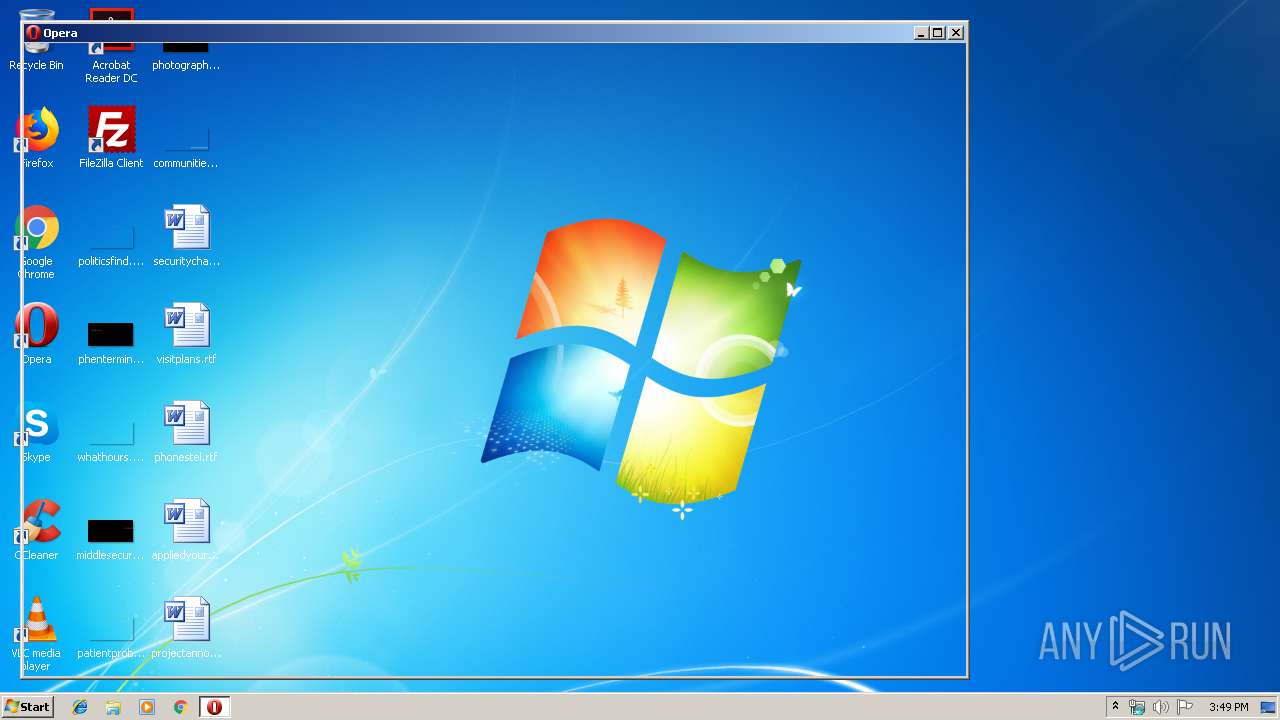
| 2596 | "C:\Program Files\Opera\Opera.exe" "C:\Users\admin\AppData\Local\Temp\bd476u1y" | C:\Program Files\Opera\Opera.exe | rundll32.exe | ||||||||||||
User: admin Company: Opera Software Integrity Level: MEDIUM Description: Opera Internet Browser Exit code: 0 Version: 1748 Modules
| |||||||||||||||
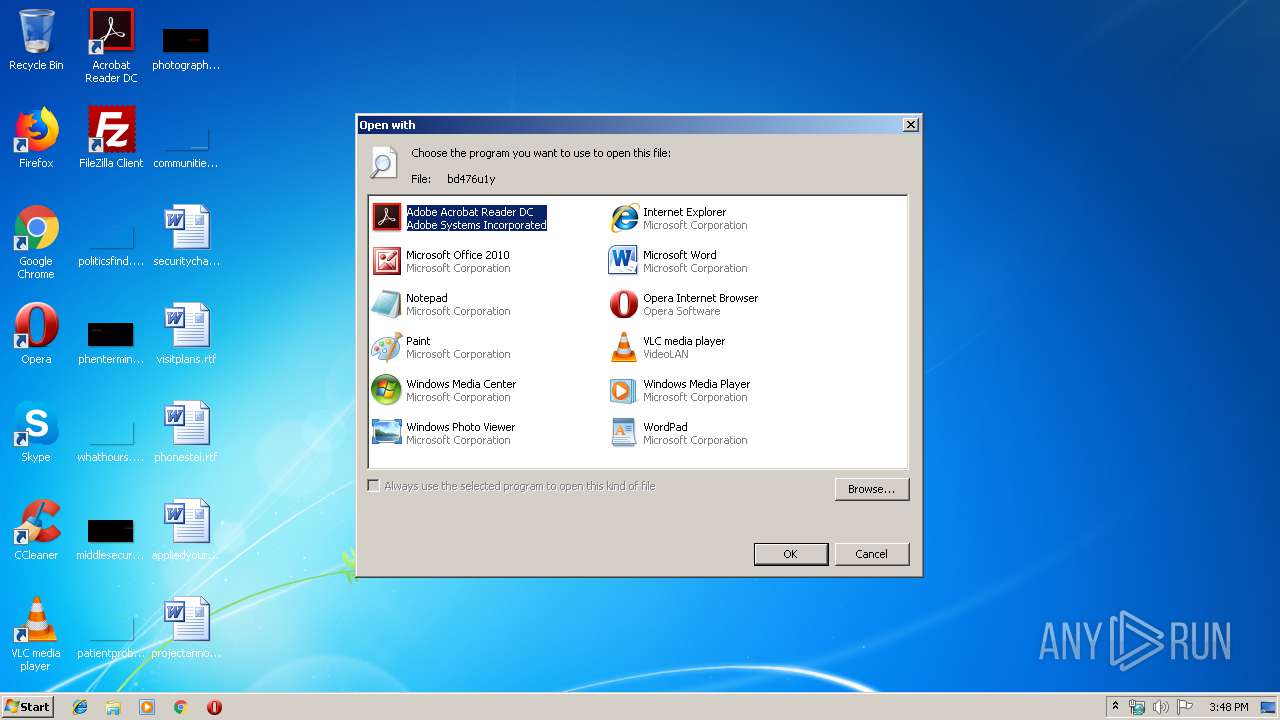
| 2768 | "C:\Windows\system32\rundll32.exe" C:\Windows\system32\shell32.dll,OpenAs_RunDLL C:\Users\admin\AppData\Local\Temp\bd476u1y | C:\Windows\system32\rundll32.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
746
Read events
624
Write events
122
Delete events
0
Modification events
| (PID) Process: | (2768) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Windows\system32\NOTEPAD.EXE |
Value: Notepad | |||
| (PID) Process: | (2768) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\PROGRA~1\MICROS~1\Office14\OIS.EXE |
Value: Microsoft Office 2010 | |||
| (PID) Process: | (2768) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\Software\Microsoft\Windows\Shell\MuiCache |
| Operation: | write | Name: | C:\Program Files\Microsoft Office\Office14\WINWORD.EXE |
Value: Microsoft Word | |||
| (PID) Process: | (2768) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | UNCAsIntranet |
Value: 0 | |||
| (PID) Process: | (2768) rundll32.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Internet Settings\ZoneMap |
| Operation: | write | Name: | AutoDetect |
Value: 1 | |||
| (PID) Process: | (2768) rundll32.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (2596) Opera.exe | Key: | HKEY_CURRENT_USER\Software\Opera Software |
| Operation: | write | Name: | Last CommandLine v2 |
Value: C:\Program Files\Opera\Opera.exe "C:\Users\admin\AppData\Local\Temp\bd476u1y" | |||
| (PID) Process: | (2596) Opera.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\72\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
Executable files
0
Suspicious files
23
Text files
11
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 2596 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr6BA1.tmp | — | |
MD5:— | SHA256:— | |||
| 2596 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr6BF0.tmp | — | |
MD5:— | SHA256:— | |||
| 2596 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opr6C6E.tmp | — | |
MD5:— | SHA256:— | |||
| 2596 | Opera.exe | C:\Users\admin\AppData\Local\Opera\Opera\cache\sesn\opr00001.tmp | — | |
MD5:— | SHA256:— | |||
| 2596 | Opera.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Recent\CustomDestinations\SXTM9G2ARLWN1XZQXILY.temp | — | |
MD5:— | SHA256:— | |||
| 2596 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr7866.tmp | — | |
MD5:— | SHA256:— | |||
| 2596 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\opr9BAE.tmp | — | |
MD5:— | SHA256:— | |||
| 2596 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\sessions\oprA767.tmp | — | |
MD5:— | SHA256:— | |||
| 2596 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\operaprefs.ini | text | |
MD5:— | SHA256:— | |||
| 2596 | Opera.exe | C:\Users\admin\AppData\Roaming\Opera\Opera\opssl6.dat | binary | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
5
DNS requests
4
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
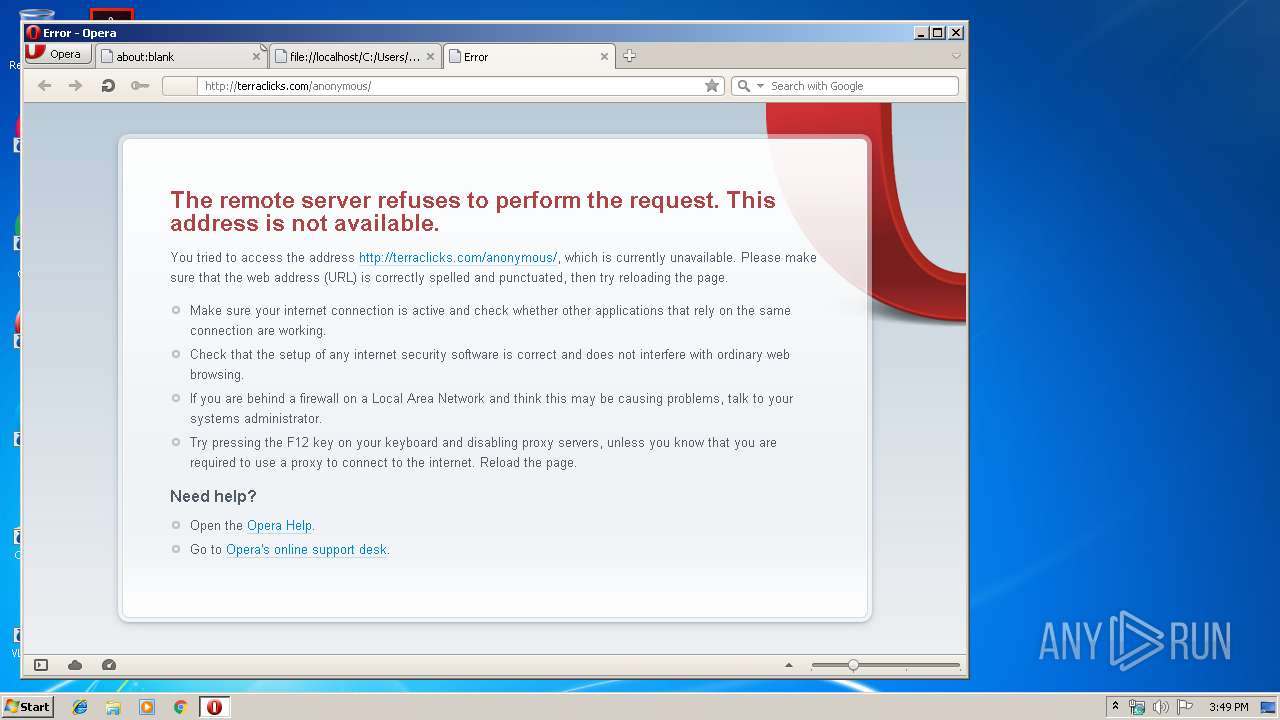
2596 | Opera.exe | GET | 403 | 198.134.112.242:80 | http://terraclicks.com/anonymous/ | US | — | — | whitelisted |
2596 | Opera.exe | GET | 200 | 93.184.220.29:80 | http://crl4.digicert.com/DigiCertHighAssuranceEVRootCA.crl | US | der | 528 b | whitelisted |
2596 | Opera.exe | GET | 400 | 107.167.110.216:80 | http://sitecheck2.opera.com/?host=terraclicks.com&hdn=cDOyel7aPvJbA0Pombwvog== | US | html | 150 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
2596 | Opera.exe | 185.26.182.94:443 | certs.opera.com | Opera Software AS | — | whitelisted |
2596 | Opera.exe | 93.184.220.29:80 | crl4.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
2596 | Opera.exe | 198.134.112.242:80 | terraclicks.com | Webair Internet Development Company Inc. | US | suspicious |
2596 | Opera.exe | 107.167.110.216:80 | sitecheck2.opera.com | Opera Software Americas LLC | US | malicious |
DNS requests
Domain | IP | Reputation |
|---|---|---|
certs.opera.com |
| whitelisted |
crl4.digicert.com |
| whitelisted |
terraclicks.com |
| whitelisted |
sitecheck2.opera.com |
| whitelisted |