| File name: | Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3 |
| Full analysis: | https://app.any.run/tasks/17c725a5-0d3e-48a1-934f-0ecc9de75735 |
| Verdict: | Malicious activity |
| Analysis date: | May 15, 2025, 16:17:49 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows, 3 sections |
| MD5: | 57AECBCDCB3A5AD31AC07C5A62B56085 |
| SHA1: | A443C574F039828D237030BC18895027CA780337 |
| SHA256: | AB020413DCE53C9D57CF22D75EAF1339D72252D5316617A935149E02FEE42FD3 |
| SSDEEP: | 12288:mjGB20Q5YI8Yu8uXG2wafWVmf1r/lGWlGR:mjGB2H5YI8Yu8uXG2wafWVmf9lGWlGR |
MALICIOUS
Changes the autorun value in the registry
- reg.exe (PID: 7416)
- reg.exe (PID: 7952)
- reg.exe (PID: 7584)
- reg.exe (PID: 8152)
- reg.exe (PID: 496)
- reg.exe (PID: 8068)
- reg.exe (PID: 7428)
- reg.exe (PID: 2040)
- reg.exe (PID: 7572)
- reg.exe (PID: 7716)
- reg.exe (PID: 5204)
- reg.exe (PID: 7812)
- reg.exe (PID: 7996)
- reg.exe (PID: 7744)
- reg.exe (PID: 7788)
- reg.exe (PID: 1180)
- reg.exe (PID: 812)
- reg.exe (PID: 7084)
- reg.exe (PID: 7000)
- reg.exe (PID: 4272)
- reg.exe (PID: 5244)
- reg.exe (PID: 5972)
- reg.exe (PID: 7272)
- reg.exe (PID: 7564)
- reg.exe (PID: 5360)
- reg.exe (PID: 2984)
- reg.exe (PID: 7924)
- reg.exe (PID: 2772)
- reg.exe (PID: 3032)
- reg.exe (PID: 7948)
- reg.exe (PID: 7372)
- reg.exe (PID: 7152)
- reg.exe (PID: 3620)
- reg.exe (PID: 8164)
- reg.exe (PID: 7284)
- reg.exe (PID: 5588)
- reg.exe (PID: 6620)
- reg.exe (PID: 5528)
- reg.exe (PID: 2960)
Starts NET.EXE to view/change shared resources
- cmd.exe (PID: 4200)
- net.exe (PID: 5936)
- net.exe (PID: 1532)
- net.exe (PID: 6048)
SUSPICIOUS
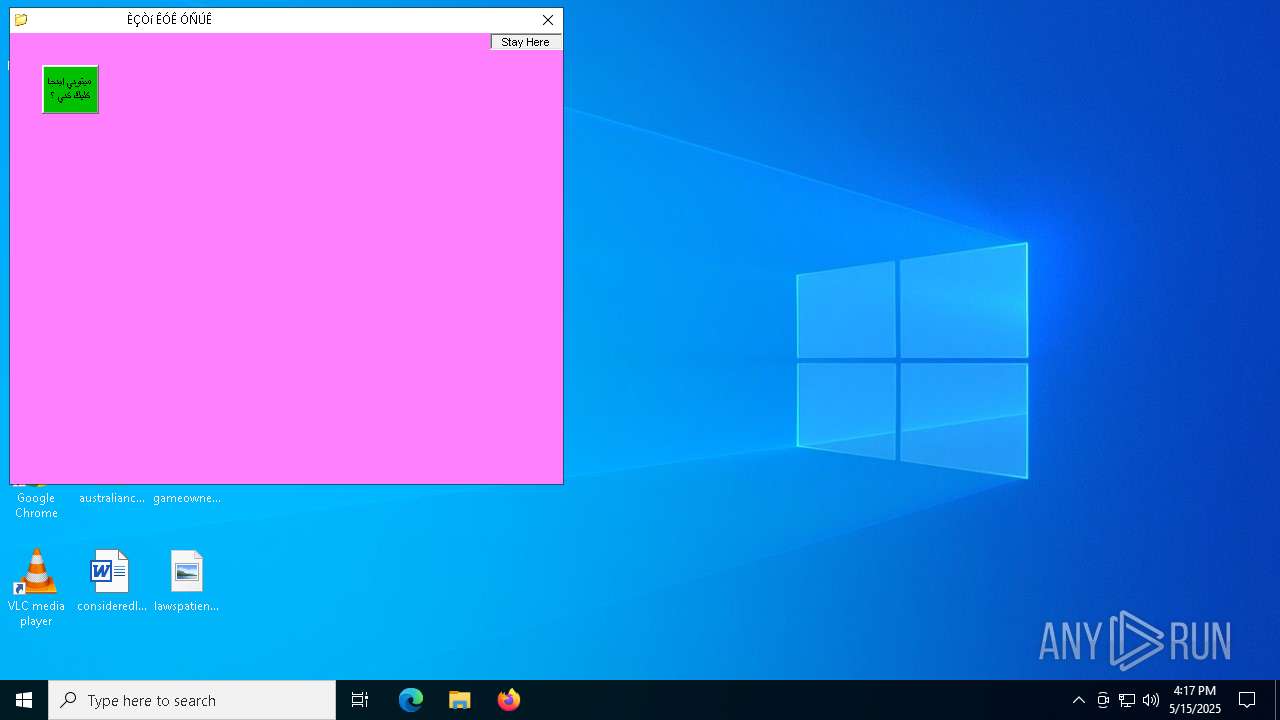
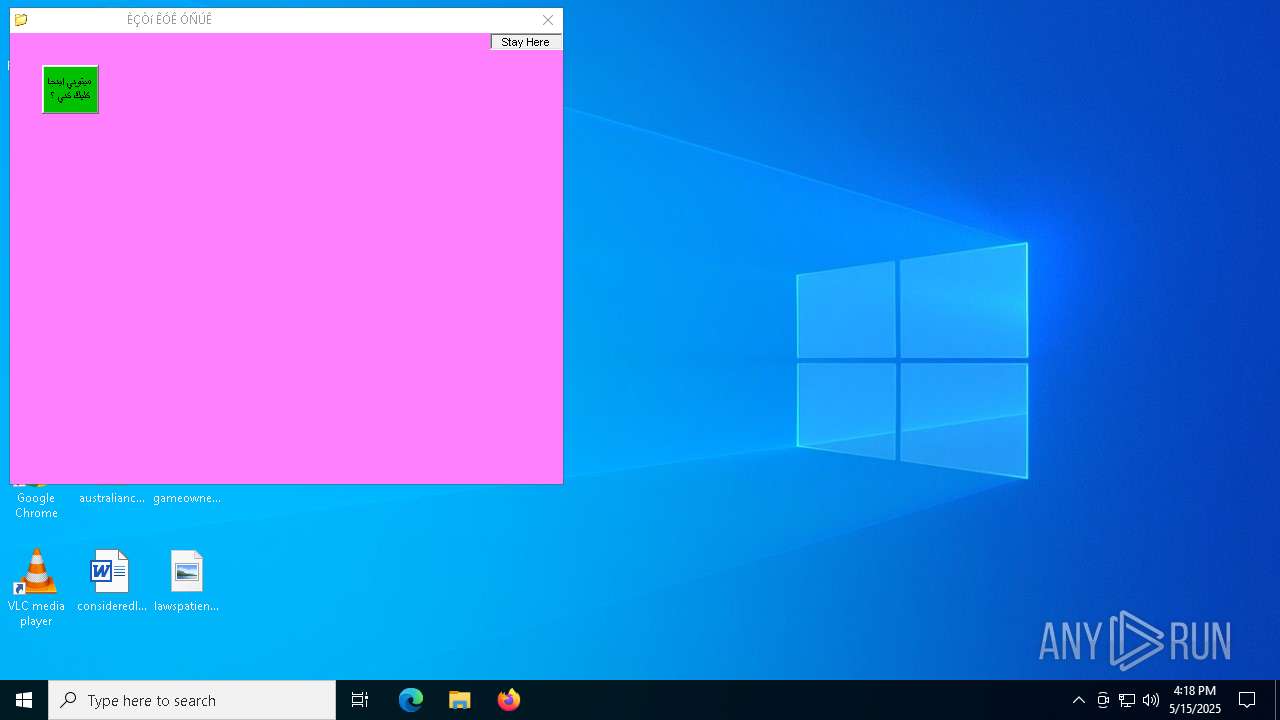
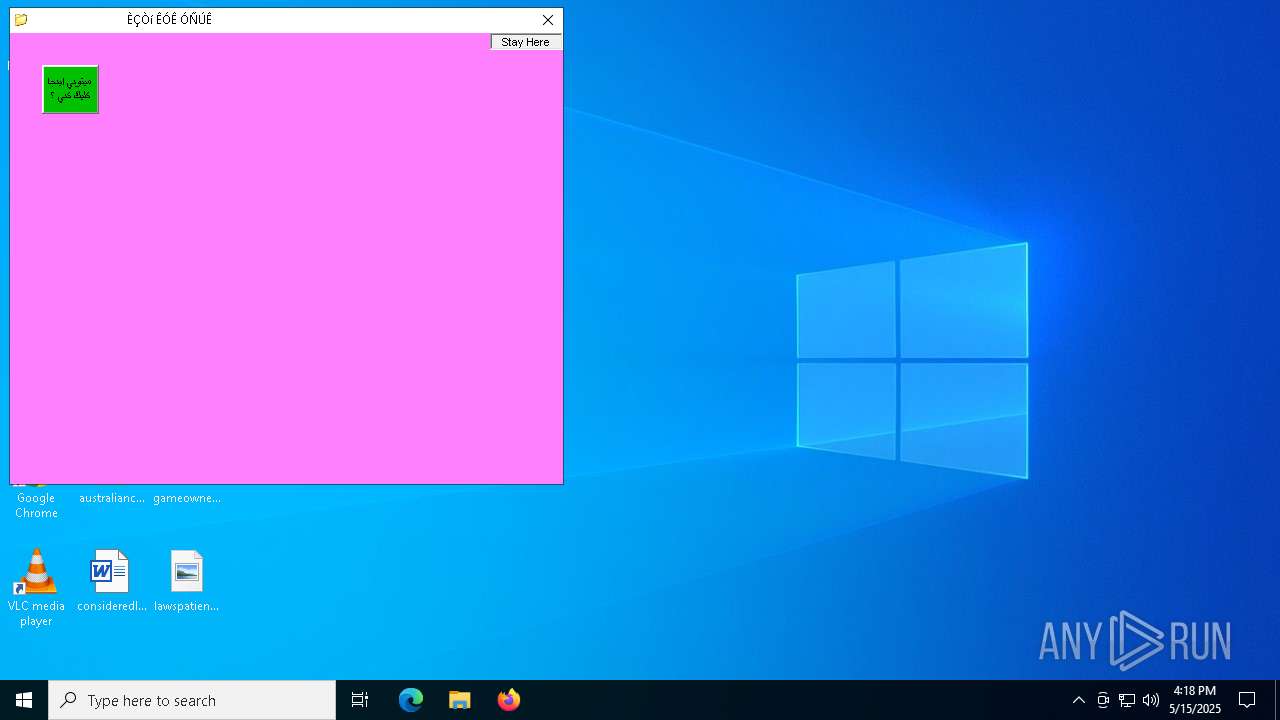
Executable content was dropped or overwritten
- Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe (PID: 7276)
Starts application from unusual location
- Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe (PID: 7276)
- cmd.exe (PID: 7316)
- cmd.exe (PID: 7820)
- ipconfig.exe (PID: 7960)
- smss.exe (PID: 7744)
- smss.exe (PID: 7408)
- PING.EXE (PID: 7340)
- cmd.exe (PID: 6132)
- cmd.exe (PID: 8024)
- PING.EXE (PID: 8092)
- cmd.exe (PID: 728)
- PING.EXE (PID: 6136)
- cmd.exe (PID: 7736)
- PING.EXE (PID: 7800)
- cmd.exe (PID: 7216)
- PING.EXE (PID: 6048)
Creates file in the systems drive root
- Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe (PID: 7276)
- smss.exe (PID: 7744)
- smss.exe (PID: 7408)
Uses REG/REGEDIT.EXE to modify registry
- cmd.exe (PID: 7296)
- cmd.exe (PID: 7772)
- cmd.exe (PID: 7764)
- cmd.exe (PID: 7520)
- cmd.exe (PID: 8012)
- cmd.exe (PID: 8096)
- cmd.exe (PID: 8180)
- cmd.exe (PID: 4164)
- cmd.exe (PID: 4892)
- cmd.exe (PID: 7596)
- cmd.exe (PID: 6480)
- cmd.exe (PID: 6512)
- cmd.exe (PID: 2772)
- cmd.exe (PID: 4068)
- cmd.exe (PID: 7908)
- cmd.exe (PID: 7976)
- cmd.exe (PID: 7824)
- cmd.exe (PID: 8136)
- cmd.exe (PID: 4112)
- cmd.exe (PID: 744)
- cmd.exe (PID: 3300)
- cmd.exe (PID: 5508)
- cmd.exe (PID: 8180)
- cmd.exe (PID: 4180)
- cmd.exe (PID: 6156)
- cmd.exe (PID: 7424)
- cmd.exe (PID: 7304)
- cmd.exe (PID: 3132)
- cmd.exe (PID: 5892)
- cmd.exe (PID: 6584)
- cmd.exe (PID: 6752)
- cmd.exe (PID: 6652)
- cmd.exe (PID: 7792)
- cmd.exe (PID: 3156)
- cmd.exe (PID: 7896)
- cmd.exe (PID: 7680)
- cmd.exe (PID: 7824)
- cmd.exe (PID: 8184)
- cmd.exe (PID: 7488)
- cmd.exe (PID: 6572)
- cmd.exe (PID: 6988)
- cmd.exe (PID: 7772)
- cmd.exe (PID: 5204)
- cmd.exe (PID: 1184)
- cmd.exe (PID: 536)
- cmd.exe (PID: 3300)
Process uses IPCONFIG to get network configuration information
- cmd.exe (PID: 7820)
Starts CMD.EXE for commands execution
- Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe (PID: 7276)
- smss.exe (PID: 7408)
- smss.exe (PID: 7744)
Detected use of alternative data streams (AltDS)
- smss.exe (PID: 7408)
INFO
Failed to create an executable file in Windows directory
- Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe (PID: 7276)
- smss.exe (PID: 7744)
- smss.exe (PID: 7408)
The sample compiled with english language support
- Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe (PID: 7276)
Checks supported languages
- Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe (PID: 7276)
- smss.exe (PID: 7408)
- smss.exe (PID: 7744)
Create files in a temporary directory
- Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe (PID: 7276)
- smss.exe (PID: 7408)
- smss.exe (PID: 7744)
Reads the computer name
- Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe (PID: 7276)
- smss.exe (PID: 7408)
Auto-launch of the file from Registry key
- reg.exe (PID: 7416)
- reg.exe (PID: 7584)
- reg.exe (PID: 7952)
- reg.exe (PID: 8068)
- reg.exe (PID: 8152)
- reg.exe (PID: 496)
- reg.exe (PID: 5204)
- reg.exe (PID: 2040)
- reg.exe (PID: 7572)
- reg.exe (PID: 7428)
- reg.exe (PID: 7788)
- reg.exe (PID: 7812)
- reg.exe (PID: 7744)
- reg.exe (PID: 7000)
- reg.exe (PID: 7716)
- reg.exe (PID: 7996)
- reg.exe (PID: 4272)
- reg.exe (PID: 812)
- reg.exe (PID: 7084)
- reg.exe (PID: 1180)
- reg.exe (PID: 5972)
- reg.exe (PID: 5244)
- reg.exe (PID: 7272)
- reg.exe (PID: 7564)
- reg.exe (PID: 5360)
- reg.exe (PID: 2984)
- reg.exe (PID: 2772)
- reg.exe (PID: 3032)
- reg.exe (PID: 7924)
- reg.exe (PID: 7948)
- reg.exe (PID: 7284)
- reg.exe (PID: 7372)
- reg.exe (PID: 5588)
- reg.exe (PID: 8164)
- reg.exe (PID: 7152)
- reg.exe (PID: 6620)
- reg.exe (PID: 5528)
- reg.exe (PID: 2960)
- reg.exe (PID: 3620)
Manual execution by a user
- smss.exe (PID: 7744)
Reads the software policy settings
- slui.exe (PID: 8124)
Checks proxy server information
- slui.exe (PID: 8124)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 Executable Microsoft Visual Basic 6 (84.4) |
|---|---|---|
| .dll | | | Win32 Dynamic Link Library (generic) (6.7) |
| .exe | | | Win32 Executable (generic) (4.6) |
| .exe | | | Generic Win/DOS Executable (2) |
| .exe | | | DOS Executable Generic (2) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 0000:00:00 00:00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 6 |
| CodeSize: | 229376 |
| InitializedDataSize: | 16384 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x27cc |
| OSVersion: | 4 |
| ImageVersion: | 5.5 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 5.5.0.0 |
| ProductVersionNumber: | 5.5.0.0 |
| FileFlagsMask: | 0x0000 |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | Free Microsoft Games |
| ProductName: | 2009-09-22 |
| FileVersion: | 5.05 |
| ProductVersion: | 5.05 |
| InternalName: | open2 |
| OriginalFileName: | open2.exe |
Total processes
292
Monitored processes
170
Malicious processes
4
Suspicious processes
45
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 496 | REG ADD HKCU\Software\MICROSOFT\WINDOWS\CURRENTVERSION\RUN /V Csrss /t REG_SZ /d "c:\RECYCLER\smss.exe " /f | C:\Windows\SysWOW64\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | C:\WINDOWS\system32\net1 share Love2="c:\Documents and Settings" /unlimited | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 536 | cmd /c REG ADD HKCU\Software\MICROSOFT\WINDOWS\CURRENTVERSION\RUN /V Csrss /t REG_SZ /d "c:\RECYCLER\smss.exe " /f | C:\Windows\SysWOW64\cmd.exe | — | Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 680 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 728 | cmd /c ping ernet adapter C2 -n 2 -w 3 > "c:\RECYCLER\check_4_online.dlx" | C:\Windows\SysWOW64\cmd.exe | — | smss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 1 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 744 | cmd /c REG ADD HKCU\Software\MICROSOFT\WINDOWS\CURRENTVERSION\RUN /V Csrss /t REG_SZ /d "c:\RECYCLER\smss.exe " /f | C:\Windows\SysWOW64\cmd.exe | — | smss.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Command Processor Exit code: 0 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 780 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | C:\WINDOWS\system32\net1 share Love3=d:\ /unlimited | C:\Windows\SysWOW64\net1.exe | — | net.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Net Command Exit code: 2 Version: 10.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 812 | REG ADD HKCU\Software\MICROSOFT\WINDOWS\CURRENTVERSION\RUN /V Csrss /t REG_SZ /d "c:\RECYCLER\smss.exe " /f | C:\Windows\SysWOW64\reg.exe | cmd.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 1132 | REG ADD HKLM\Software\MICROSOFT\WINDOWS\CURRENTVERSION\RUN /V smss /t REG_SZ /d "smss\smss.exe " /f | C:\Windows\SysWOW64\reg.exe | — | cmd.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Registry Console Tool Exit code: 1 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
6 835
Read events
6 796
Write events
39
Delete events
0
Modification events
| (PID) Process: | (7416) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | smss |
Value: c:\RECYCLER\smss.exe | |||
| (PID) Process: | (7584) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | smss |
Value: c:\RECYCLER\smss.exe | |||
| (PID) Process: | (7952) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Csrss |
Value: c:\RECYCLER\smss.exe | |||
| (PID) Process: | (8068) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | smss |
Value: c:\RECYCLER\smss.exe | |||
| (PID) Process: | (8152) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Csrss |
Value: c:\RECYCLER\smss.exe | |||
| (PID) Process: | (496) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Csrss |
Value: c:\RECYCLER\smss.exe | |||
| (PID) Process: | (5204) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Csrss |
Value: c:\RECYCLER\smss.exe | |||
| (PID) Process: | (7428) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Csrss |
Value: c:\RECYCLER\smss.exe | |||
| (PID) Process: | (7572) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Csrss |
Value: c:\RECYCLER\smss.exe | |||
| (PID) Process: | (2040) reg.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run |
| Operation: | write | Name: | Csrss |
Value: c:\RECYCLER\smss.exe | |||
Executable files
3
Suspicious files
2
Text files
7
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 7276 | Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe | C:\RECYCLER\smss.exe | executable | |
MD5:57AECBCDCB3A5AD31AC07C5A62B56085 | SHA256:AB020413DCE53C9D57CF22D75EAF1339D72252D5316617A935149E02FEE42FD3 | |||
| 7276 | Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe | C:\RECYCLER\Downloads.exe | executable | |
MD5:57AECBCDCB3A5AD31AC07C5A62B56085 | SHA256:AB020413DCE53C9D57CF22D75EAF1339D72252D5316617A935149E02FEE42FD3 | |||
| 7276 | Sigmanly_ab020413dce53c9d57cf22d75eaf1339d72252d5316617a935149e02fee42fd3.exe | C:\Users\admin\AppData\Local\Temp\smss.exe | executable | |
MD5:57AECBCDCB3A5AD31AC07C5A62B56085 | SHA256:AB020413DCE53C9D57CF22D75EAF1339D72252D5316617A935149E02FEE42FD3 | |||
| 728 | cmd.exe | C:\RECYCLER\check_4_online.dlx | text | |
MD5:1AEE8EDDEF535A3C072B7F520EAF5560 | SHA256:18E39B4A5A91F2CF56367C2D7B53830881D5D885BCCCC234219C39FD0AF44353 | |||
| 7736 | cmd.exe | C:\RECYCLER\check_4_online.dlx | text | |
MD5:1AEE8EDDEF535A3C072B7F520EAF5560 | SHA256:18E39B4A5A91F2CF56367C2D7B53830881D5D885BCCCC234219C39FD0AF44353 | |||
| 7408 | smss.exe | C:\RECYCLER\autorun.INF | binary | |
MD5:CBA289891EC7B2F21BDA3435F229537B | SHA256:34E37C589C9CDFEA750288F65D019AFEE10644722CC520F1E95FEBC5758FD4F0 | |||
| 7744 | smss.exe | C:\Users\admin\AppData\Local\Temp\~DF0F9965A0F0281101.TMP | binary | |
MD5:E282EC2773982235D407598EA8D3253A | SHA256:601F6ABAD2FF2BBBB6EB24C0BB2278FB0824E5CC6E43CEA0AAF863CEC66AB197 | |||
| 7820 | cmd.exe | C:\RECYCLER\IP.dlx | text | |
MD5:0108E9FF349A806F8F3C353A9518AAF7 | SHA256:E2CE1D3DEA7E89DE201CFF72092824C668DF8C3DEC86613AFD9209BDE6EFB816 | |||
| 7408 | smss.exe | C:\RECYCLER\Checked_IPs.dlx | text | |
MD5:CC19931A85B9CC4771F1C9A522A6DCDA | SHA256:C343143C0B0E252BB4406FCD4F9333C393A486E82926BF1A6CFF385191BC7F20 | |||
| 8024 | cmd.exe | C:\RECYCLER\check_4_online.dlx | text | |
MD5:1AEE8EDDEF535A3C072B7F520EAF5560 | SHA256:18E39B4A5A91F2CF56367C2D7B53830881D5D885BCCCC234219C39FD0AF44353 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
2
TCP/UDP connections
35
DNS requests
7
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
2104 | svchost.exe | GET | 200 | 23.219.150.101:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
2104 | svchost.exe | GET | 200 | 2.16.168.124:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
— | — | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
2104 | svchost.exe | 51.124.78.146:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2104 | svchost.exe | 2.16.168.124:80 | crl.microsoft.com | Akamai International B.V. | RU | whitelisted |
2104 | svchost.exe | 23.219.150.101:80 | www.microsoft.com | AKAMAI-AS | CL | whitelisted |
2104 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
2196 | svchost.exe | 224.0.0.251:5353 | — | — | — | unknown |
2196 | svchost.exe | 224.0.0.252:5355 | — | — | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
activation-v2.sls.microsoft.com |
| whitelisted |