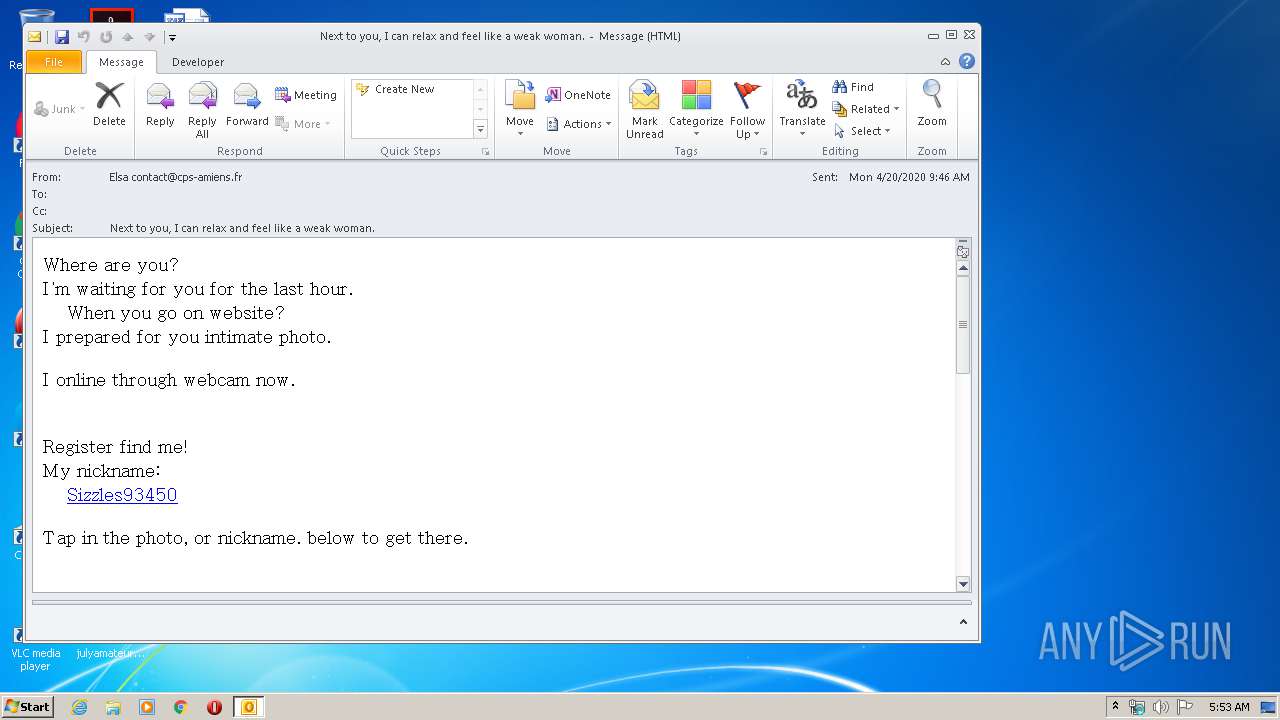
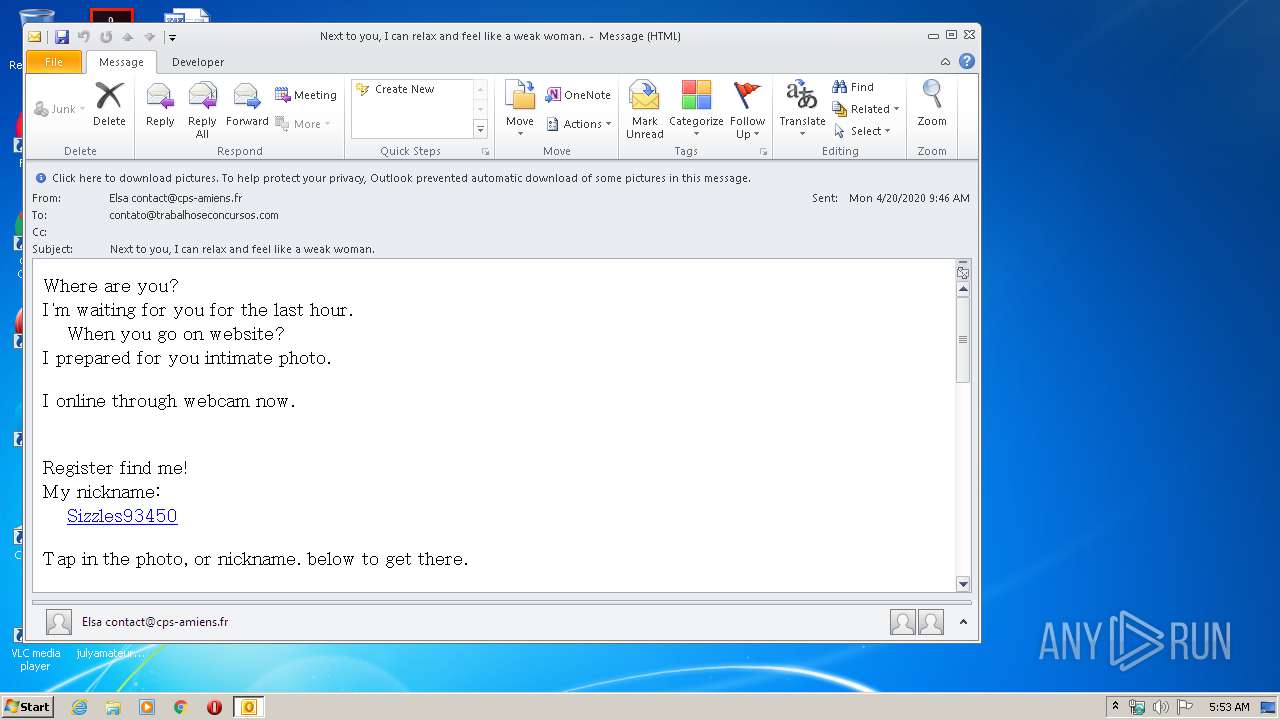
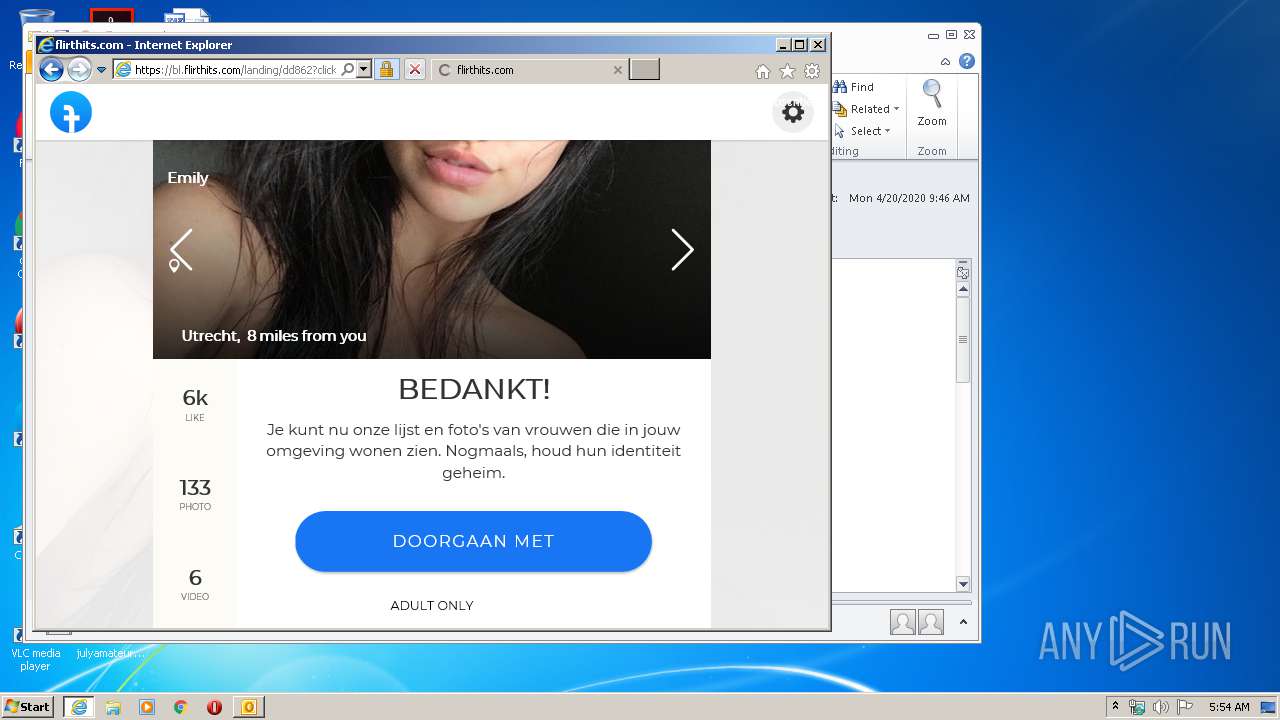
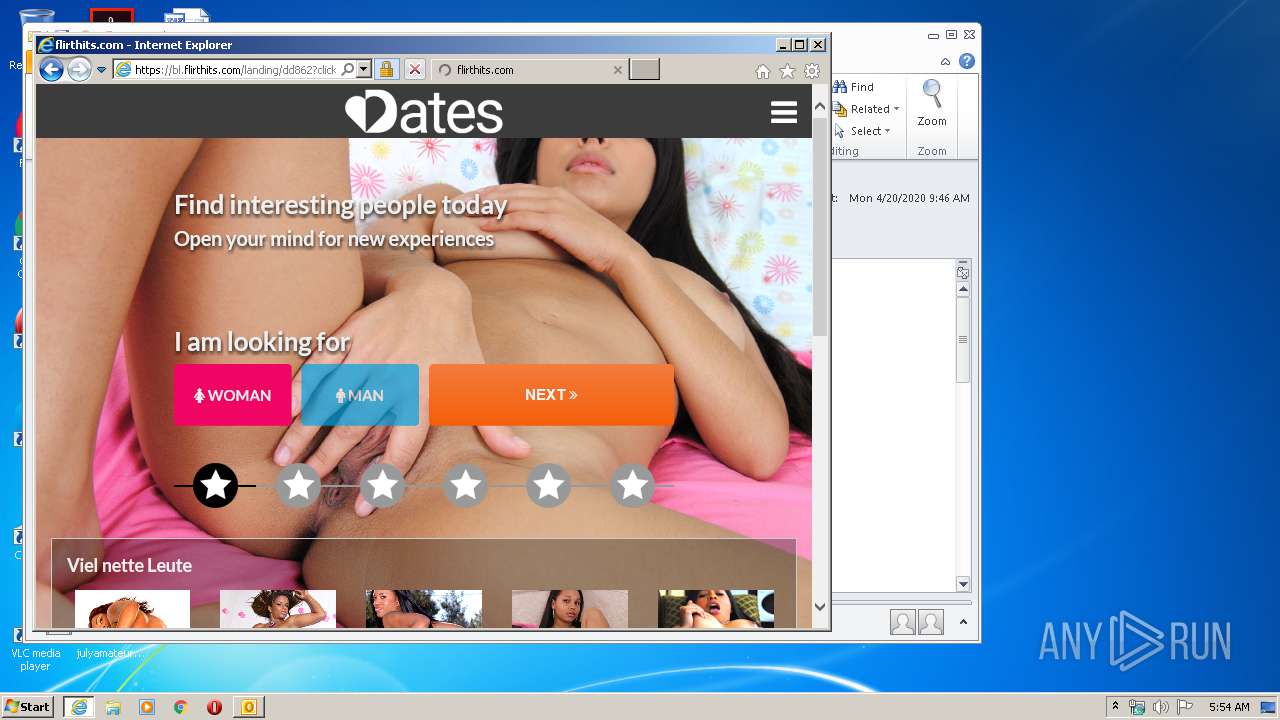
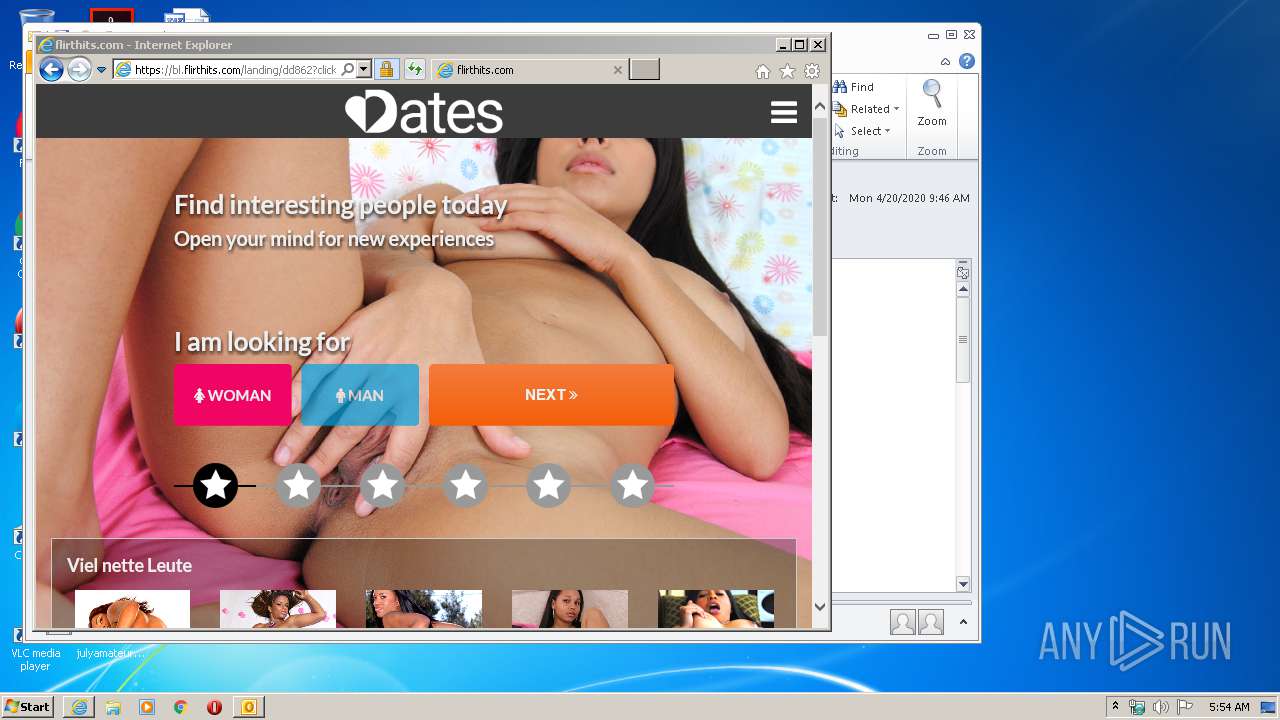
| File name: | I20200421175528 Next to you, I can relax and feel .eml |
| Full analysis: | https://app.any.run/tasks/35a1791c-2e18-49e9-9d8c-9886453b3933 |
| Verdict: | Malicious activity |
| Analysis date: | April 22, 2020, 04:53:28 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | message/rfc822 |
| File info: | RFC 822 mail, ASCII text, with CRLF line terminators |
| MD5: | 716DE102DA9FEBFCB6EC304D8A162DC7 |
| SHA1: | 36BD83D2A855BA181CB33B9045E09C6960816908 |
| SHA256: | AAFEF1140FBF2E9F2867AA41181DB63D409F750B251D01DA54B129945AC2F1F4 |
| SSDEEP: | 384:FIUGhAurDNV0vnmELE+6+JokSJhrfP+H9Q:FIhAu/NWvmEE+W |
MALICIOUS
No malicious indicators.SUSPICIOUS
Reads Internet Cache Settings
- OUTLOOK.EXE (PID: 3680)
Creates files in the user directory
- OUTLOOK.EXE (PID: 3680)
Starts Internet Explorer
- OUTLOOK.EXE (PID: 3680)
INFO
Reads Internet Cache Settings
- iexplore.exe (PID: 2092)
- iexplore.exe (PID: 3556)
Application launched itself
- iexplore.exe (PID: 2092)
Changes internet zones settings
- iexplore.exe (PID: 2092)
Creates files in the user directory
- iexplore.exe (PID: 3556)
- iexplore.exe (PID: 2092)
Reads Microsoft Office registry keys
- OUTLOOK.EXE (PID: 3680)
Reads internet explorer settings
- iexplore.exe (PID: 3556)
Reads settings of System Certificates
- iexplore.exe (PID: 3556)
- iexplore.exe (PID: 2092)
Adds / modifies Windows certificates
- iexplore.exe (PID: 2092)
Changes settings of System certificates
- iexplore.exe (PID: 2092)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .eml | | | E-Mail message (Var. 5) (100) |
|---|
Total processes
38
Monitored processes
3
Malicious processes
0
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
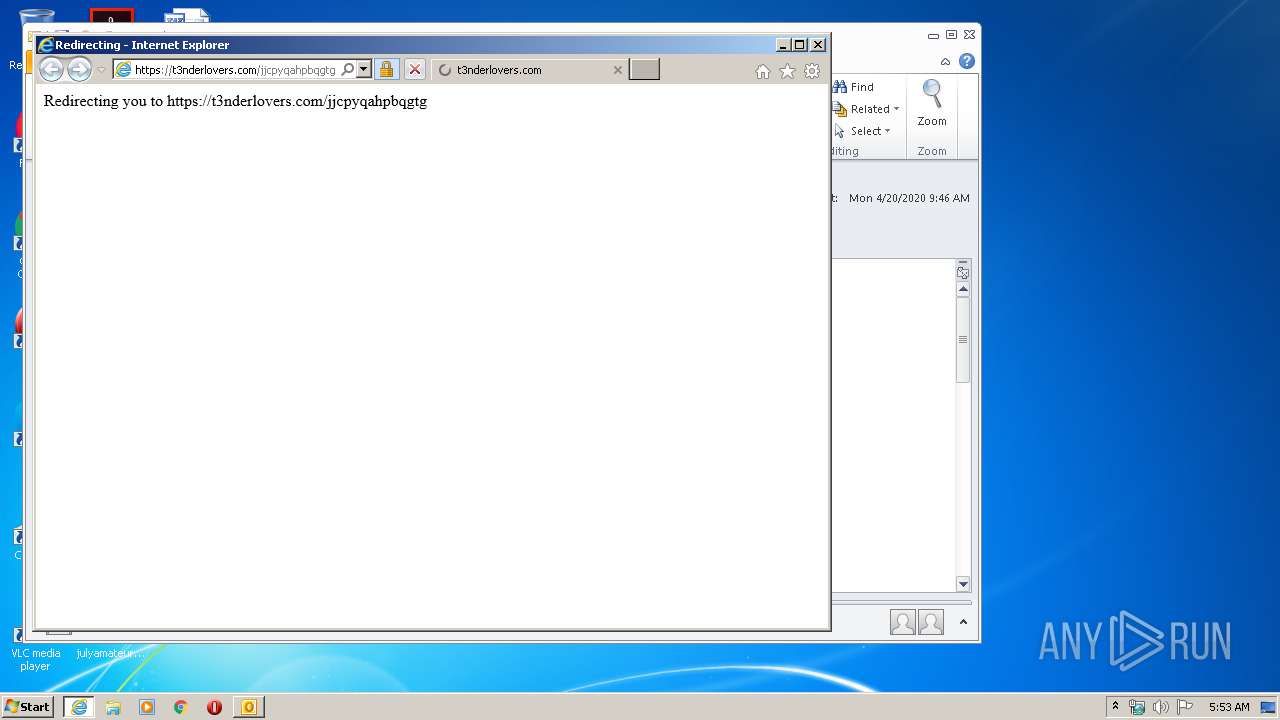
| 2092 | "C:\Program Files\Internet Explorer\iexplore.exe" https://www.google.com/url?q=https%3A%2F%2Ft3nderlovers.com%2Fjjcpyqahpbqgtg&sa=D&sntz=1&usg=AFQjCNHhdY4-RLI5HzEABxo40SbqoIIQmw | C:\Program Files\Internet Explorer\iexplore.exe | OUTLOOK.EXE | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3556 | "C:\Program Files\Internet Explorer\iexplore.exe" SCODEF:2092 CREDAT:267521 /prefetch:2 | C:\Program Files\Internet Explorer\iexplore.exe | iexplore.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: LOW Description: Internet Explorer Exit code: 0 Version: 11.00.9600.16428 (winblue_gdr.131013-1700) Modules
| |||||||||||||||
| 3680 | "C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE" /eml "C:\Users\admin\AppData\Local\Temp\I20200421175528 Next to you, I can relax and feel .eml" | C:\PROGRA~1\MICROS~1\Office14\OUTLOOK.EXE | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft Outlook Exit code: 0 Version: 14.0.6025.1000 Modules
| |||||||||||||||
Total events
10 937
Read events
1 875
Write events
6 214
Delete events
2 848
Modification events
| (PID) Process: | (3680) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1033 |
Value: Off | |||
| (PID) Process: | (3680) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1041 |
Value: Off | |||
| (PID) Process: | (3680) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1046 |
Value: Off | |||
| (PID) Process: | (3680) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1036 |
Value: Off | |||
| (PID) Process: | (3680) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1031 |
Value: Off | |||
| (PID) Process: | (3680) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1040 |
Value: Off | |||
| (PID) Process: | (3680) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1049 |
Value: Off | |||
| (PID) Process: | (3680) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 3082 |
Value: Off | |||
| (PID) Process: | (3680) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1042 |
Value: Off | |||
| (PID) Process: | (3680) OUTLOOK.EXE | Key: | HKEY_CURRENT_USER\Software\Microsoft\Office\14.0\Common\LanguageResources\EnabledLanguages |
| Operation: | write | Name: | 1055 |
Value: Off | |||
Executable files
0
Suspicious files
49
Text files
84
Unknown types
30
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3680 | OUTLOOK.EXE | C:\Users\admin\AppData\Local\Temp\CVRE0D3.tmp.cvr | — | |
MD5:— | SHA256:— | |||
| 3556 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Cab533.tmp | — | |
MD5:— | SHA256:— | |||
| 3556 | iexplore.exe | C:\Users\admin\AppData\Local\Temp\Low\Tar534.tmp | — | |
MD5:— | SHA256:— | |||
| 3556 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\2T5UM2Q5.txt | — | |
MD5:— | SHA256:— | |||
| 3556 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\BNIF9WBS.txt | — | |
MD5:— | SHA256:— | |||
| 3556 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\B199XKWZ.txt | — | |
MD5:— | SHA256:— | |||
| 3680 | OUTLOOK.EXE | C:\Users\admin\AppData\Roaming\Microsoft\Templates\~$rmalEmail.dotm | pgc | |
MD5:— | SHA256:— | |||
| 3556 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\BE8B021F9E811DFC8C8A28572A17C05A_C6CD4E9CCDD692A49CC7E8E3F7BA531A | binary | |
MD5:— | SHA256:— | |||
| 3556 | iexplore.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\BE8B021F9E811DFC8C8A28572A17C05A_C6CD4E9CCDD692A49CC7E8E3F7BA531A | der | |
MD5:— | SHA256:— | |||
| 3556 | iexplore.exe | C:\Users\admin\AppData\Roaming\Microsoft\Windows\Cookies\Low\3IFPW0UO.txt | text | |
MD5:— | SHA256:— | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
25
TCP/UDP connections
69
DNS requests
33
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3680 | OUTLOOK.EXE | GET | — | 64.4.26.155:80 | http://config.messenger.msn.com/config/msgrconfig.asmx?op=GetOlcConfig | US | — | — | whitelisted |
3556 | iexplore.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQC5g0g8l6k%2FKQIAAAAAYQBa | US | der | 472 b | whitelisted |
3556 | iexplore.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3556 | iexplore.exe | GET | 200 | 93.184.220.29:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTBL0V27RVZ7LBduom%2FnYB45SPUEwQU5Z1ZMIJHWMys%2BghUNoZ7OrUETfACEA%2Fz5hY5qj0aEmX0H4s05bY%3D | US | der | 1.47 Kb | whitelisted |
3556 | iexplore.exe | GET | 200 | 2.21.242.187:80 | http://isrg.trustid.ocsp.identrust.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRv9GhNQxLSSGKBnMArPUcsHYovpgQUxKexpHsscfrb4UuQdf%2FEFWCFiRACEAoBQUIAAAFThXNqC4Xspwg%3D | NL | der | 1.37 Kb | whitelisted |
3556 | iexplore.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/gsr2/ME4wTDBKMEgwRjAJBgUrDgMCGgUABBTgXIsxbvr2lBkPpoIEVRE6gHlCnAQUm%2BIHV2ccHsBqBt5ZtJot39wZhi4CDQHjtJqhjYqpgSVpULg%3D | US | der | 468 b | whitelisted |
3556 | iexplore.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/gts1o1/MFIwUDBOMEwwSjAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEQDzc5EE8o4wJQgAAAAAN5Er | US | der | 472 b | whitelisted |
3556 | iexplore.exe | GET | 200 | 2.21.242.245:80 | http://ocsp.int-x3.letsencrypt.org/MFMwUTBPME0wSzAJBgUrDgMCGgUABBR%2B5mrncpqz%2FPiiIGRsFqEtYHEIXQQUqEpqYwR93brm0Tm3pkVl7%2FOo7KECEgM%2BGQfmky2Nq6Onx0xew9KOYA%3D%3D | NL | der | 527 b | whitelisted |
3556 | iexplore.exe | GET | 200 | 151.139.128.14:80 | http://ocsp.comodoca.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBReAhtobFzTvhaRmVeJ38QUchY9AwQUu69%2BAj36pvE8hI6t7jiY7NkyMtQCECsuburZdTZsFIpu26N8jAc%3D | US | der | 727 b | whitelisted |
3556 | iexplore.exe | GET | 200 | 172.217.21.227:80 | http://ocsp.pki.goog/gts1o1/MFEwTzBNMEswSTAJBgUrDgMCGgUABBRCRjDCJxnb3nDwj%2Fxz5aZfZjgXvAQUmNH4bhDrz5vsYJ8YkBug630J%2FSsCEEw0ZZD0YkphCAAAAAA3kSg%3D | US | der | 471 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3556 | iexplore.exe | 172.217.22.100:443 | www.google.com | Google Inc. | US | whitelisted |
3680 | OUTLOOK.EXE | 64.4.26.155:80 | config.messenger.msn.com | Microsoft Corporation | US | whitelisted |
3556 | iexplore.exe | 172.217.21.227:80 | ocsp.pki.goog | Google Inc. | US | whitelisted |
2092 | iexplore.exe | 172.217.22.100:443 | www.google.com | Google Inc. | US | whitelisted |
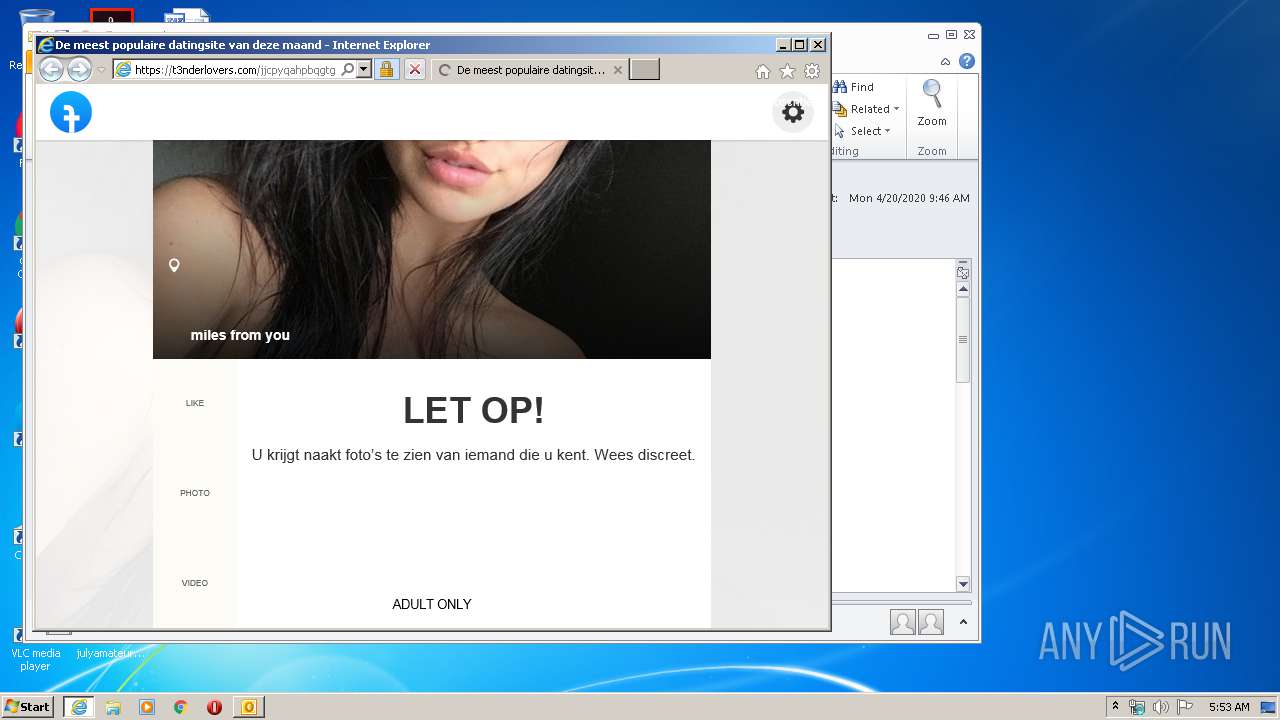
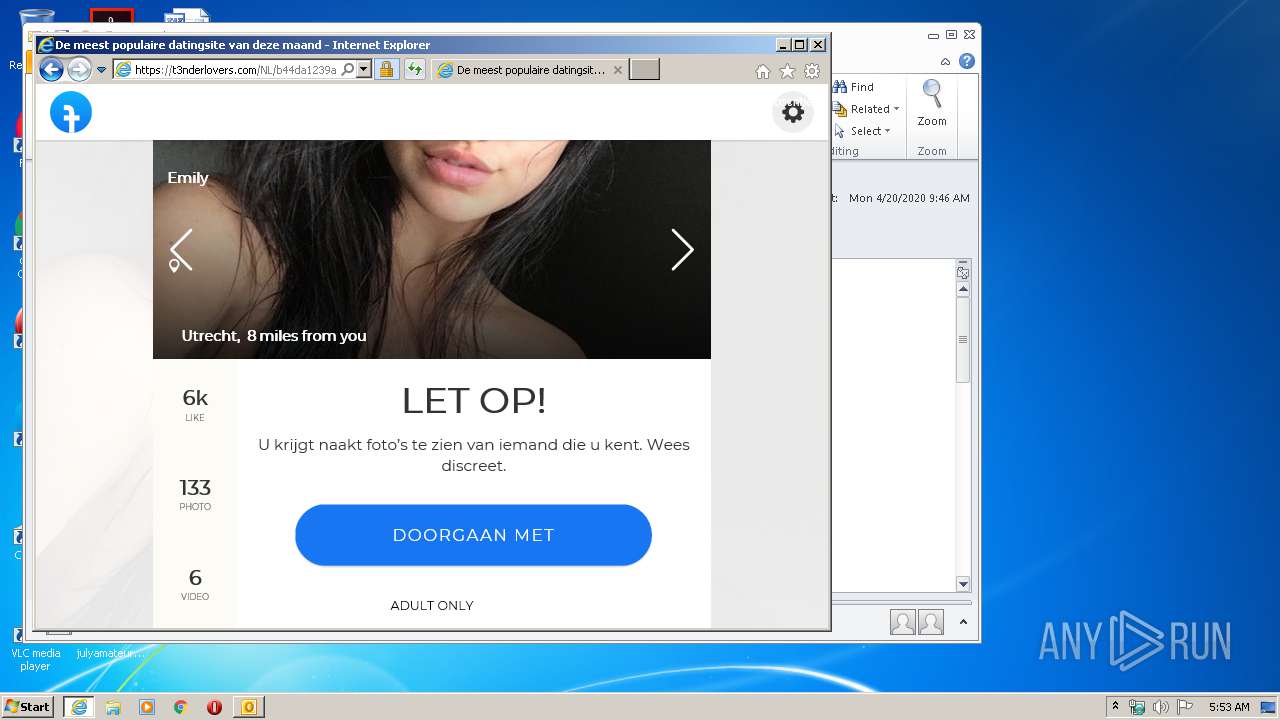
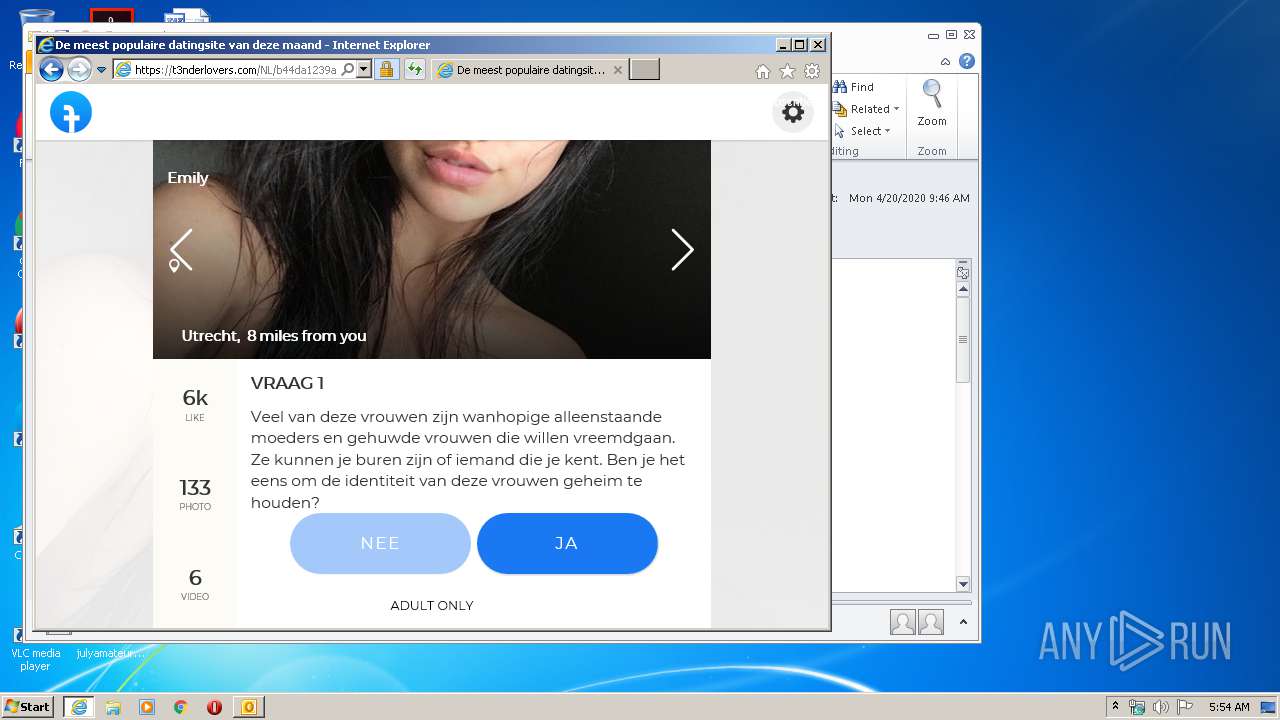
3556 | iexplore.exe | 104.18.55.71:443 | t3nderlovers.com | Cloudflare Inc | US | shared |
3556 | iexplore.exe | 209.197.3.24:443 | code.jquery.com | Highwinds Network Group, Inc. | US | malicious |
3556 | iexplore.exe | 93.184.220.29:80 | ocsp.digicert.com | MCI Communications Services, Inc. d/b/a Verizon Business | US | whitelisted |
3556 | iexplore.exe | 104.16.133.229:443 | cdnjs.cloudflare.com | Cloudflare Inc | US | suspicious |
3556 | iexplore.exe | 216.58.206.3:443 | fonts.gstatic.com | Google Inc. | US | whitelisted |
3556 | iexplore.exe | 156.67.36.11:443 | o-2587.prodtraff.com | CQ International B.V. | DE | unknown |
DNS requests
Domain | IP | Reputation |
|---|---|---|
config.messenger.msn.com |
| whitelisted |
www.google.com |
| malicious |
ocsp.pki.goog |
| whitelisted |
t3nderlovers.com |
| suspicious |
ocsp.digicert.com |
| whitelisted |
fonts.googleapis.com |
| whitelisted |
code.jquery.com |
| whitelisted |
cdnjs.cloudflare.com |
| whitelisted |
api.bing.com |
| whitelisted |
www.bing.com |
| whitelisted |