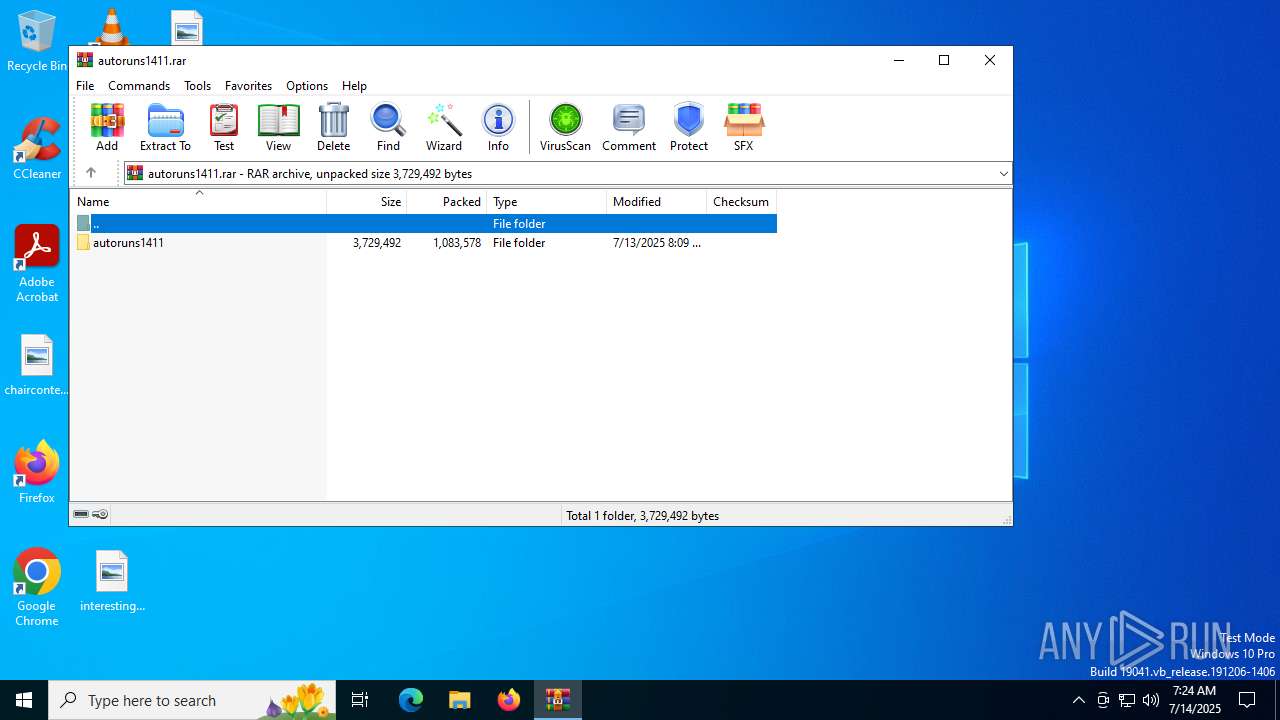
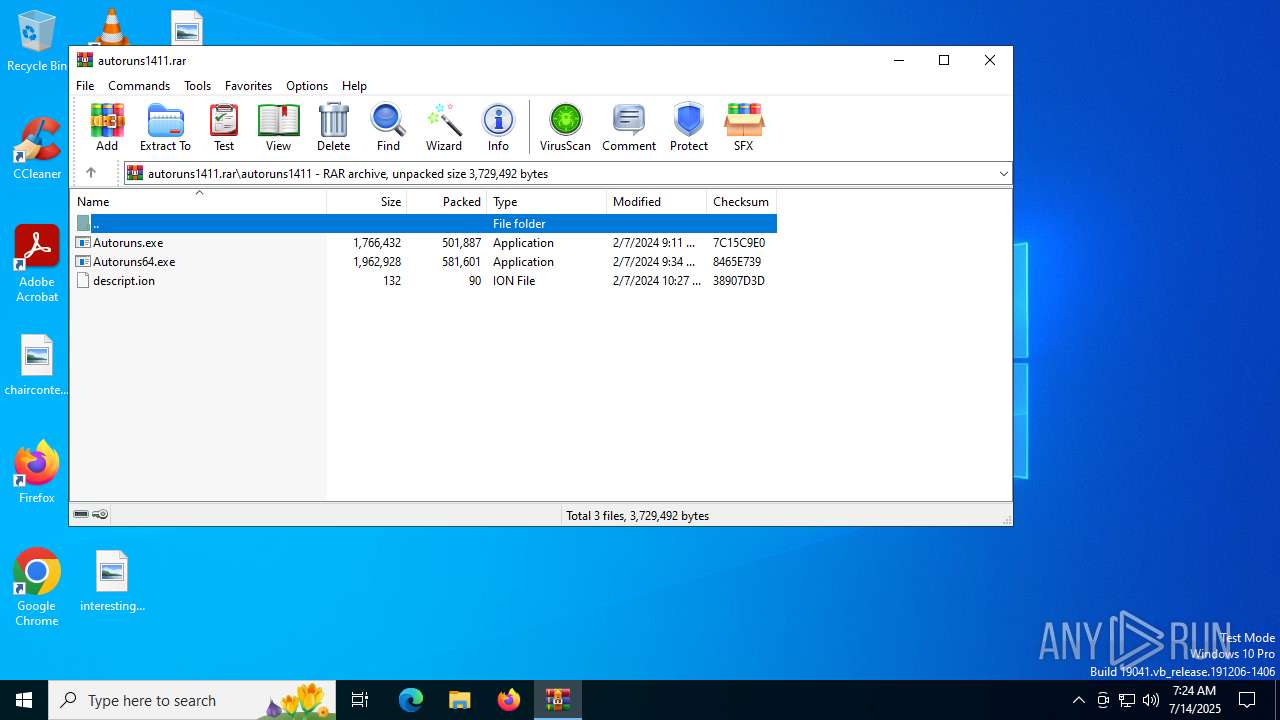
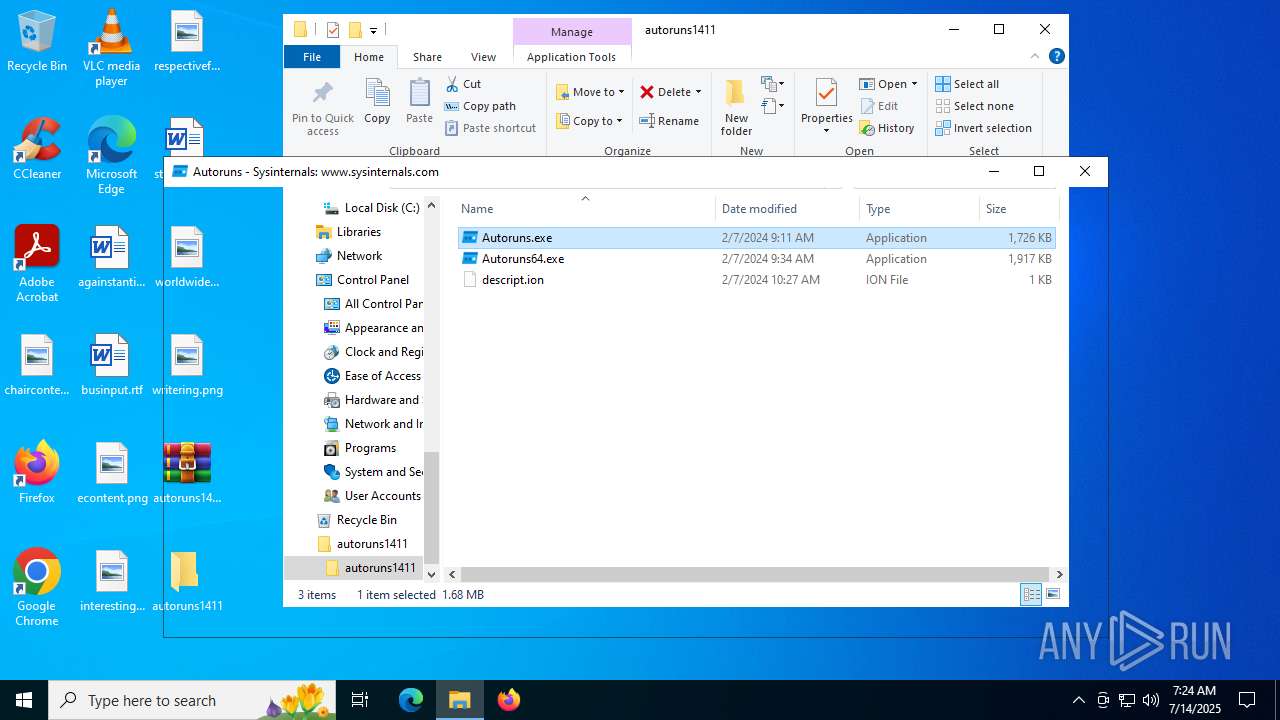
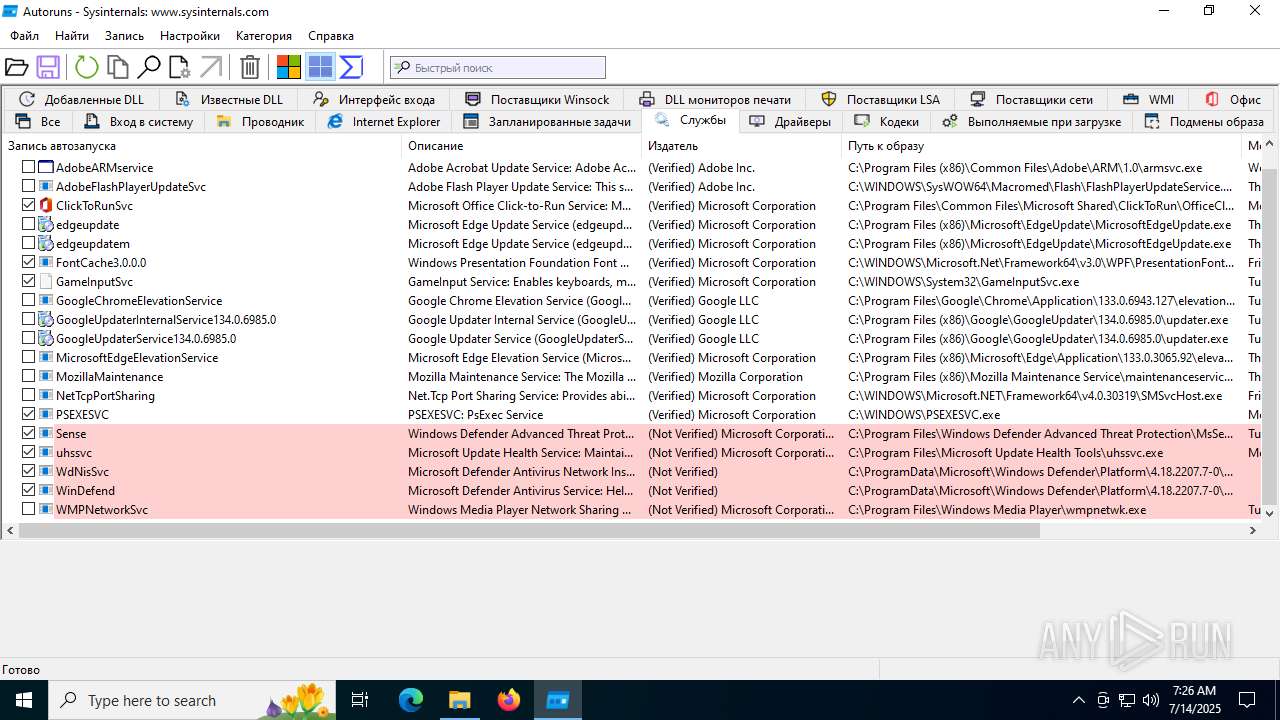
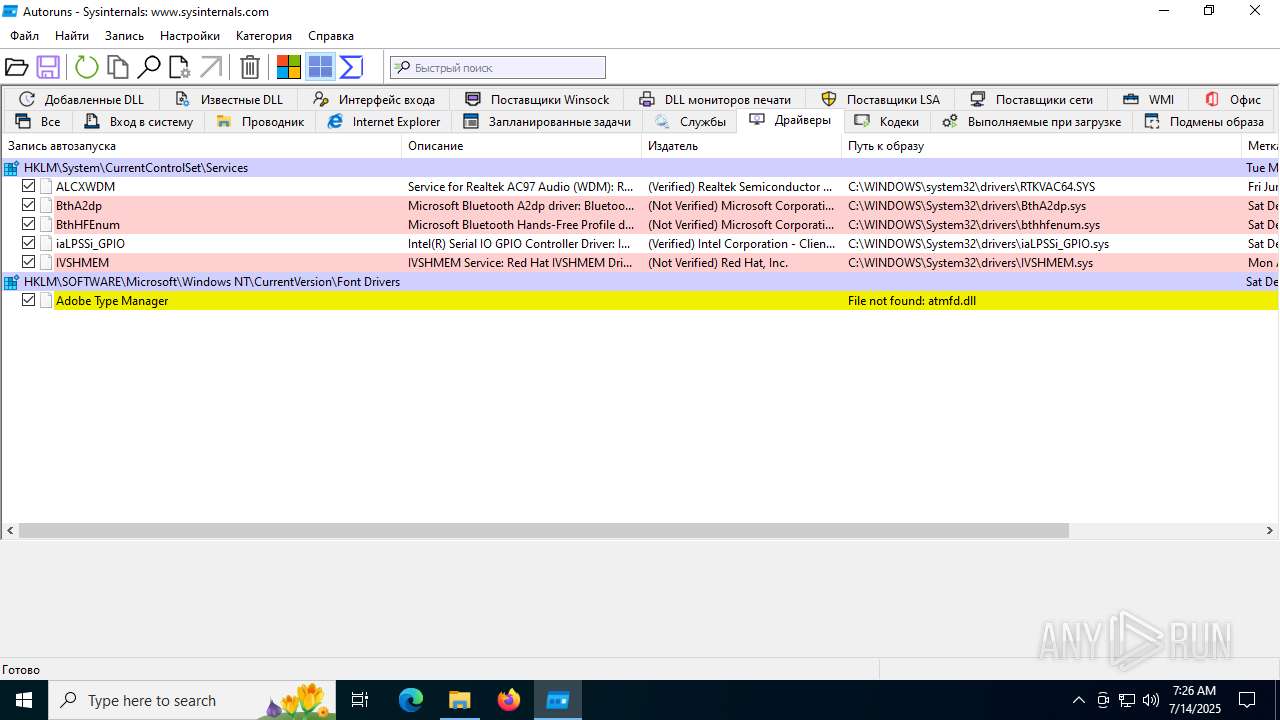
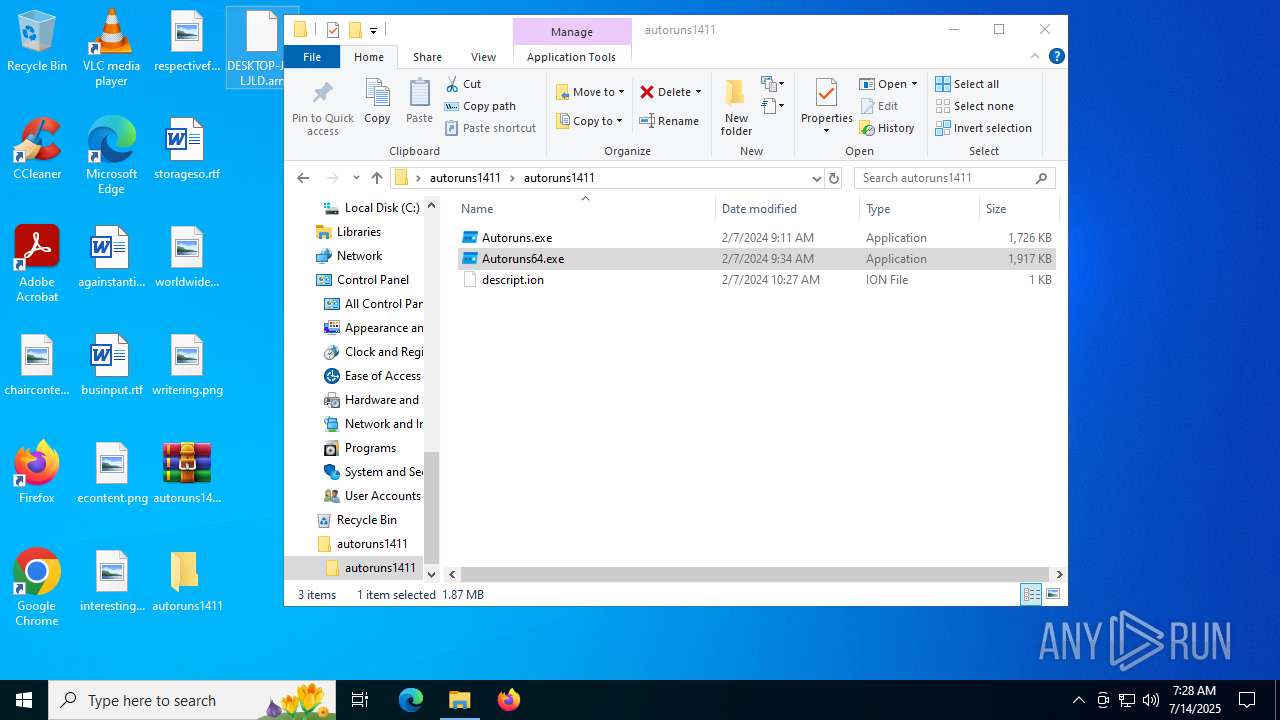
| File name: | autoruns1411.rar |
| Full analysis: | https://app.any.run/tasks/7e2d1575-cb20-48fe-afbd-84727f37f5f1 |
| Verdict: | Malicious activity |
| Analysis date: | July 14, 2025, 07:24:14 |
| OS: | Windows 10 Professional (build: 19044, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/x-rar |
| File info: | RAR archive data, v5 |
| MD5: | C4ED6744F54FE6AF743FE5EE04001754 |
| SHA1: | 38BE65C040963F9F56E8C42B584D85B11BA6ECC9 |
| SHA256: | AADCF85B22ED58351700CF340B92B52C1F05975249516F94D9193003874A2084 |
| SSDEEP: | 49152:uys/gzAc/XeLBXrLsNAFcdPQuWZ4XiknUVqsQdbFgvw6EulXqyo0PJnraCcZGPyo:u3/wAoOF7mACPQubfUVJQdN8JoeRrTcQ |
MALICIOUS
Generic archive extractor
- WinRAR.exe (PID: 2120)
SUSPICIOUS
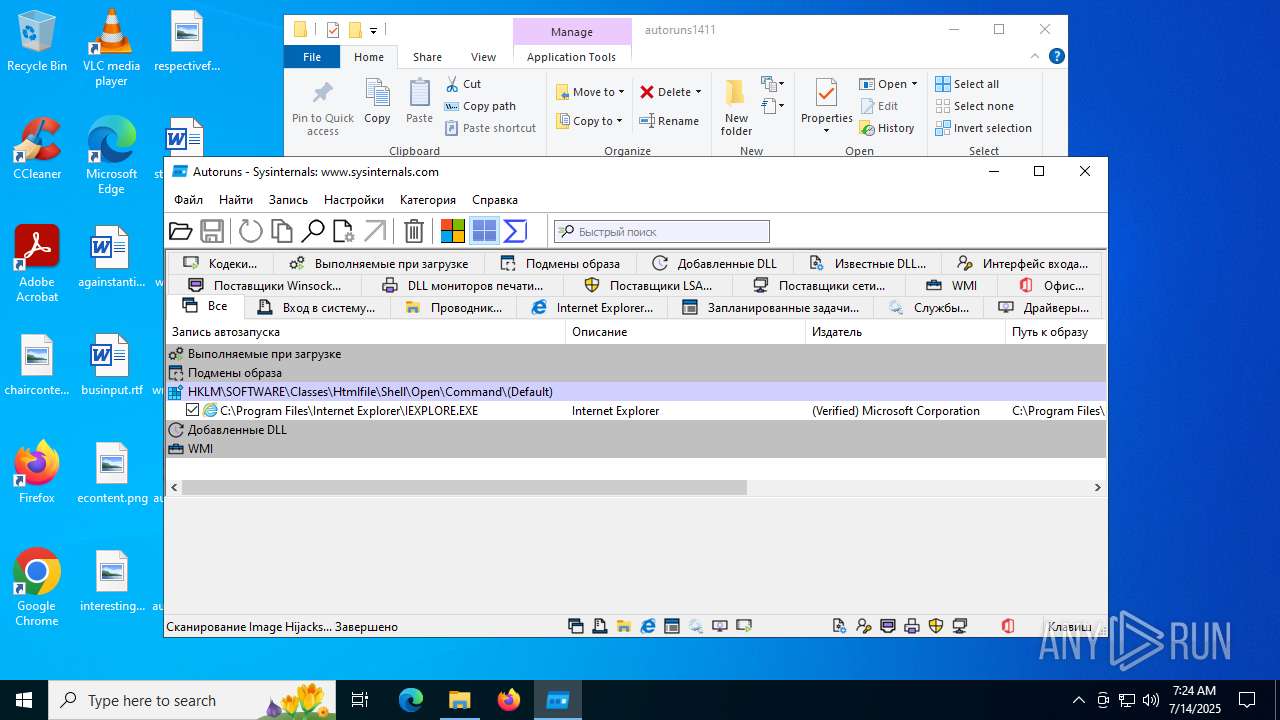
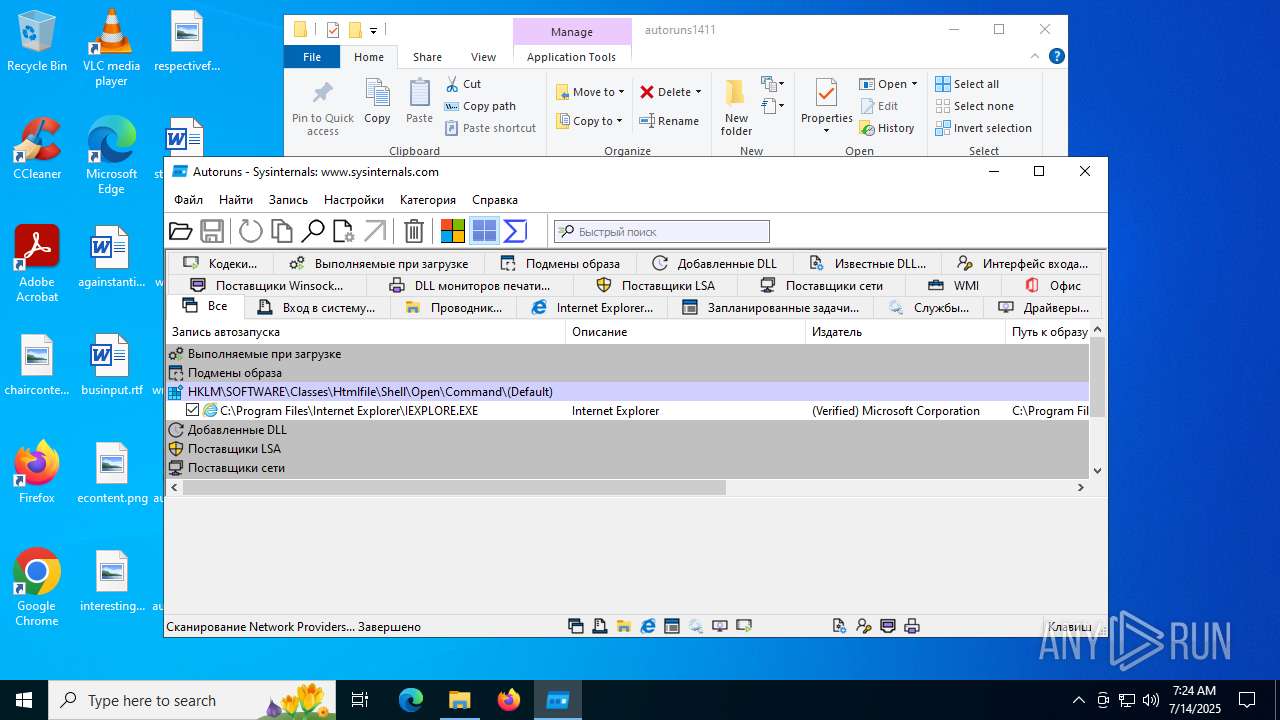
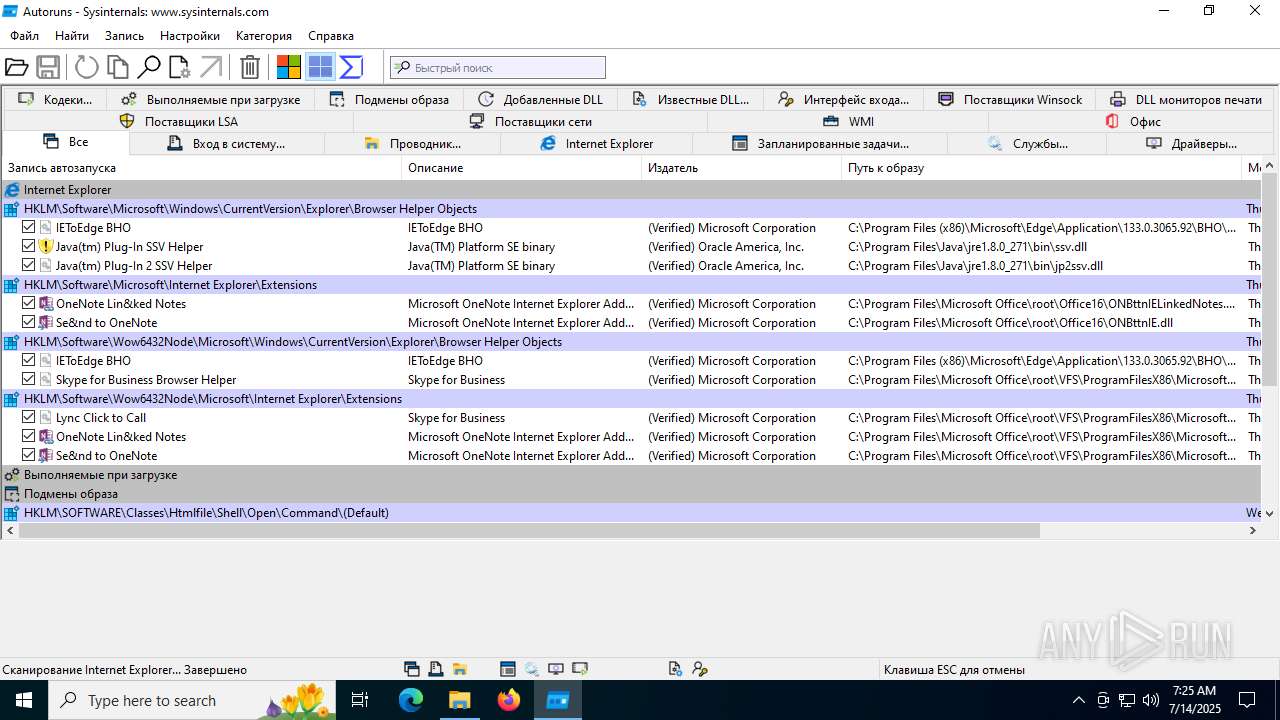
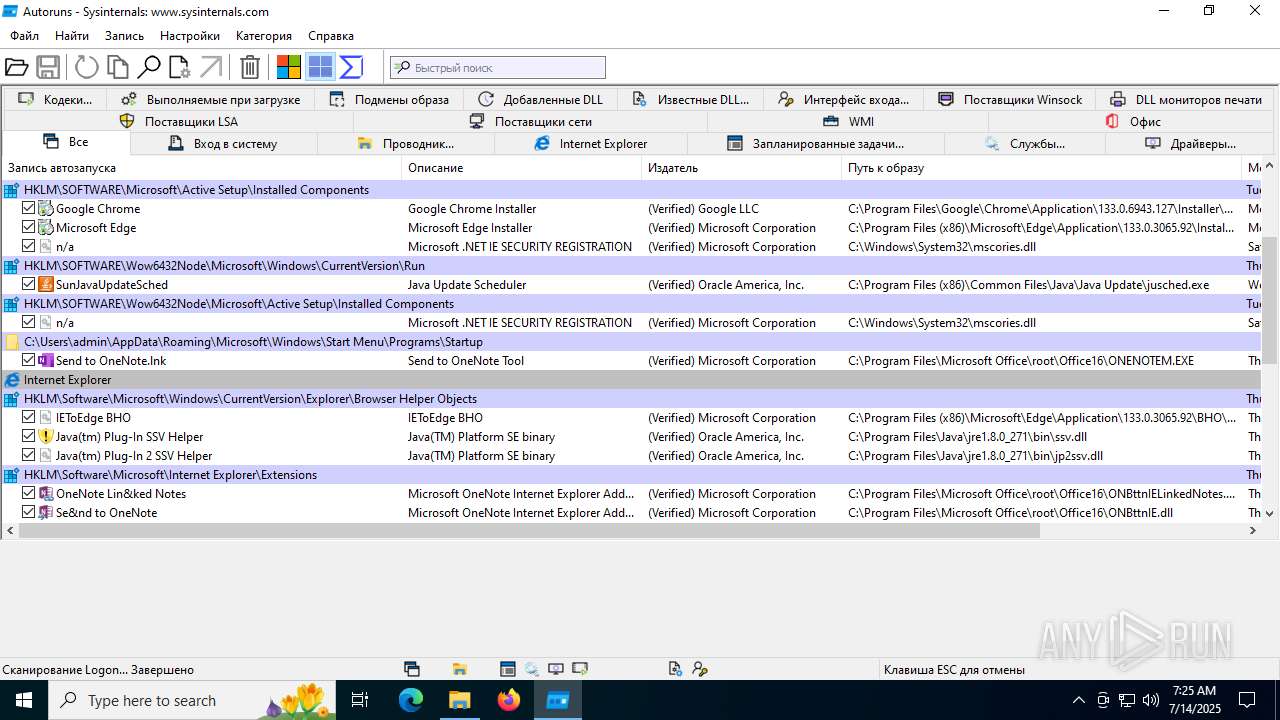
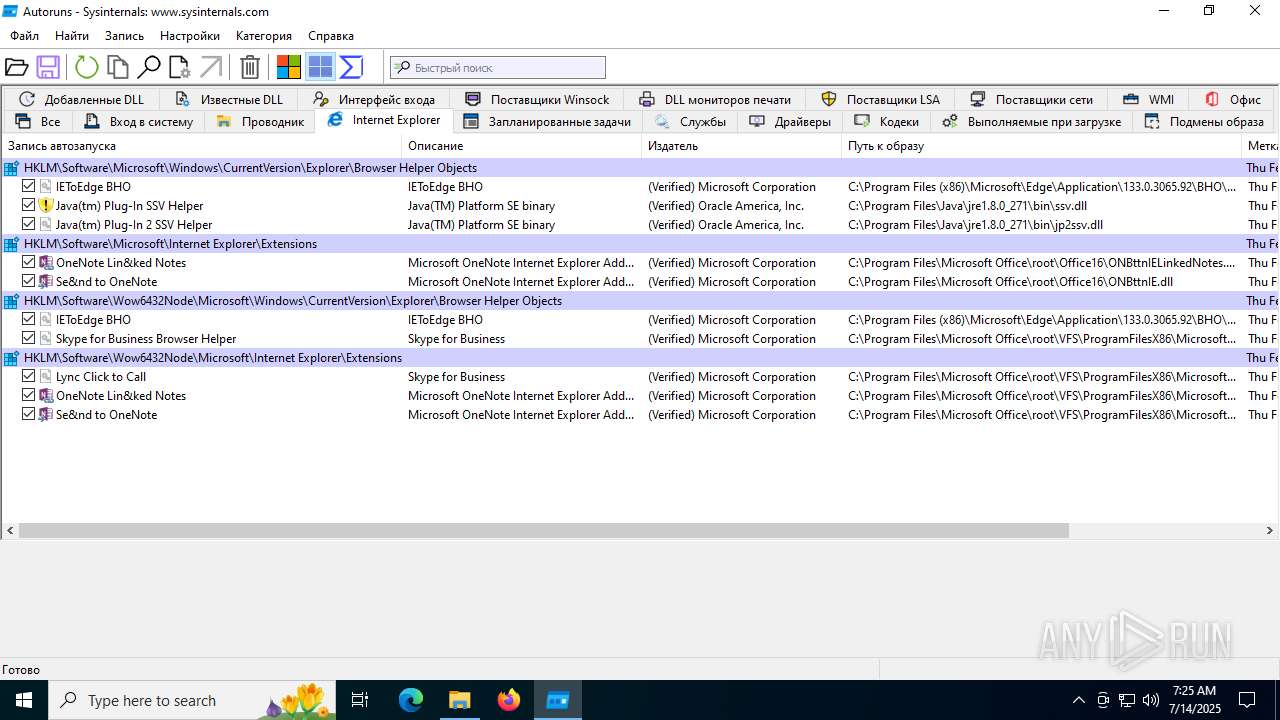
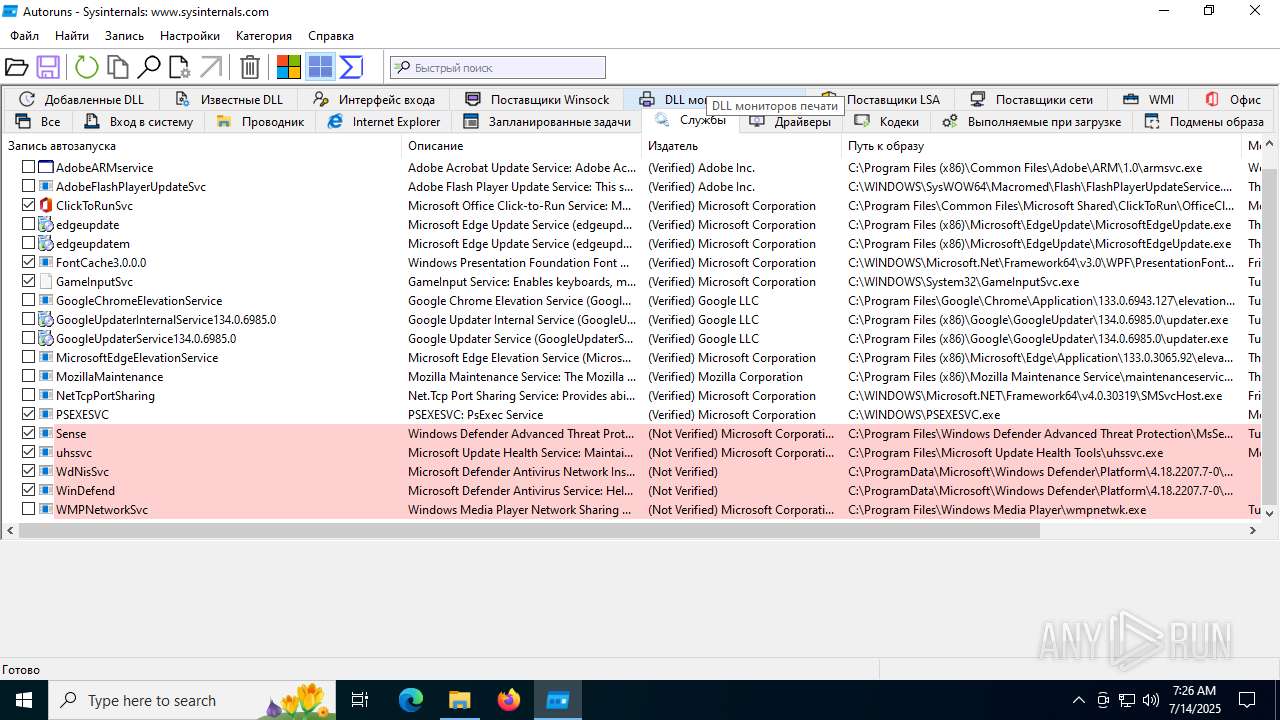
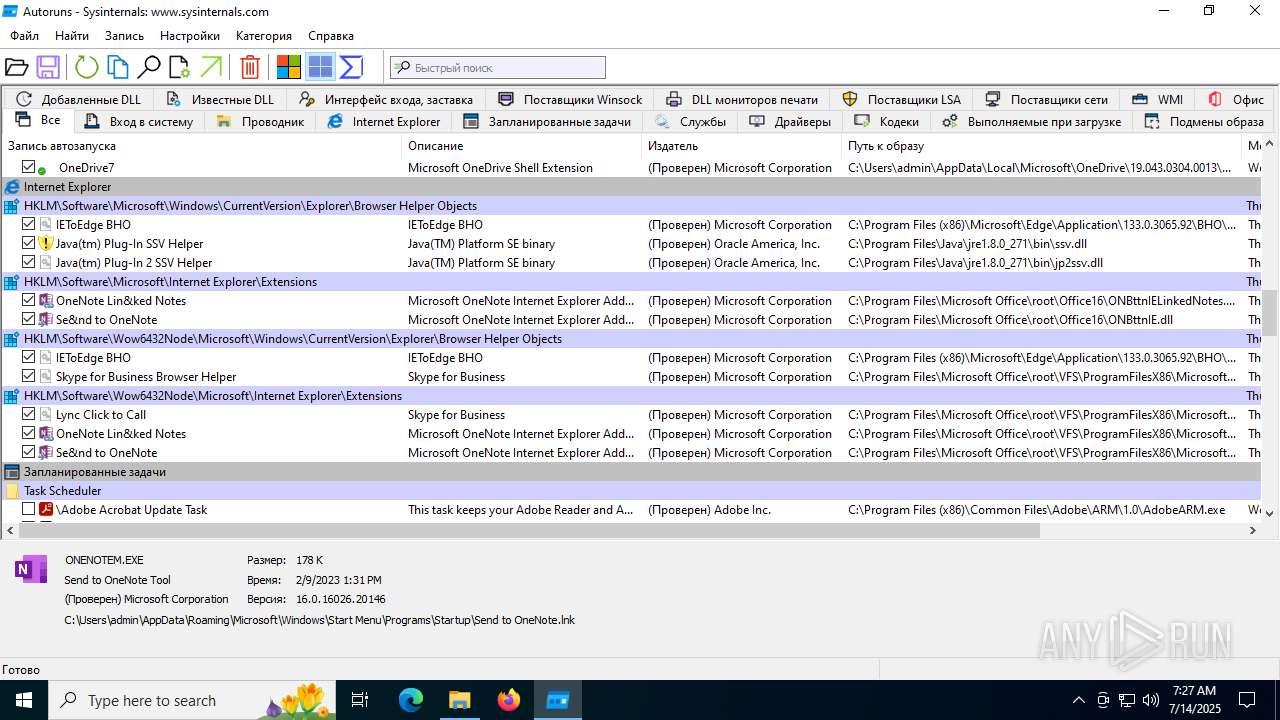
Reads security settings of Internet Explorer
- Autoruns.exe (PID: 1740)
- Autoruns64.exe (PID: 3976)
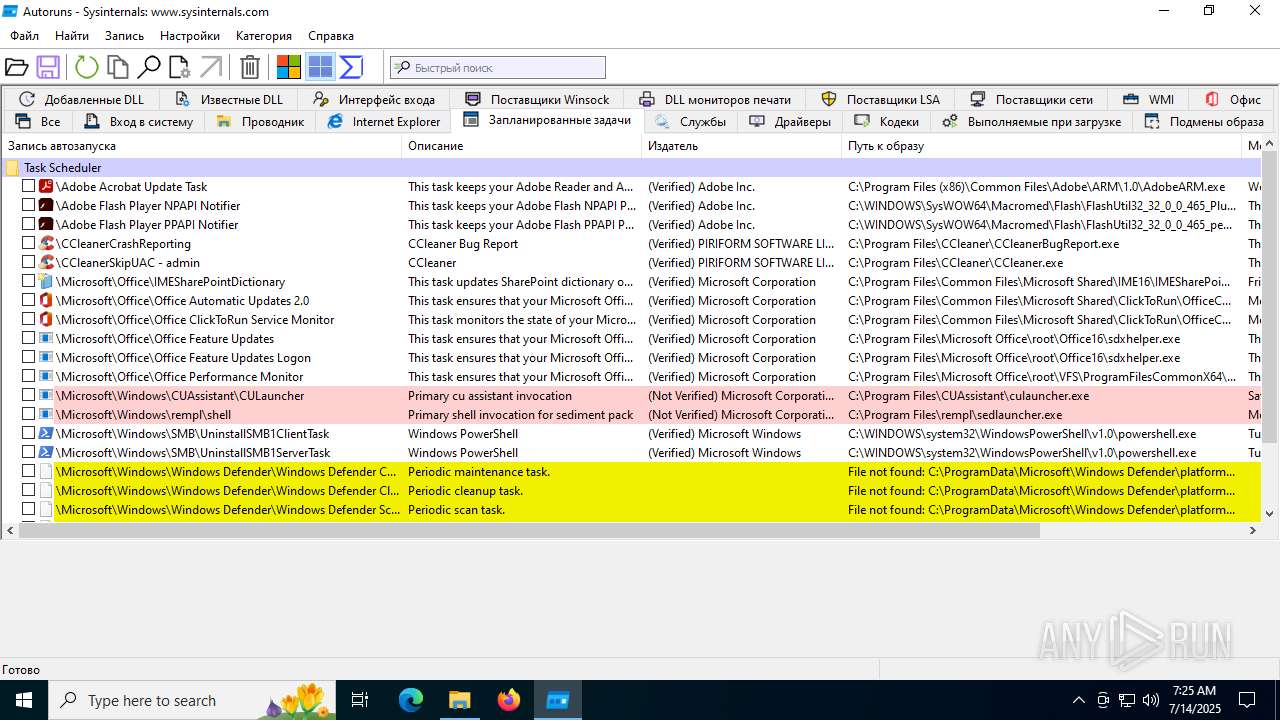
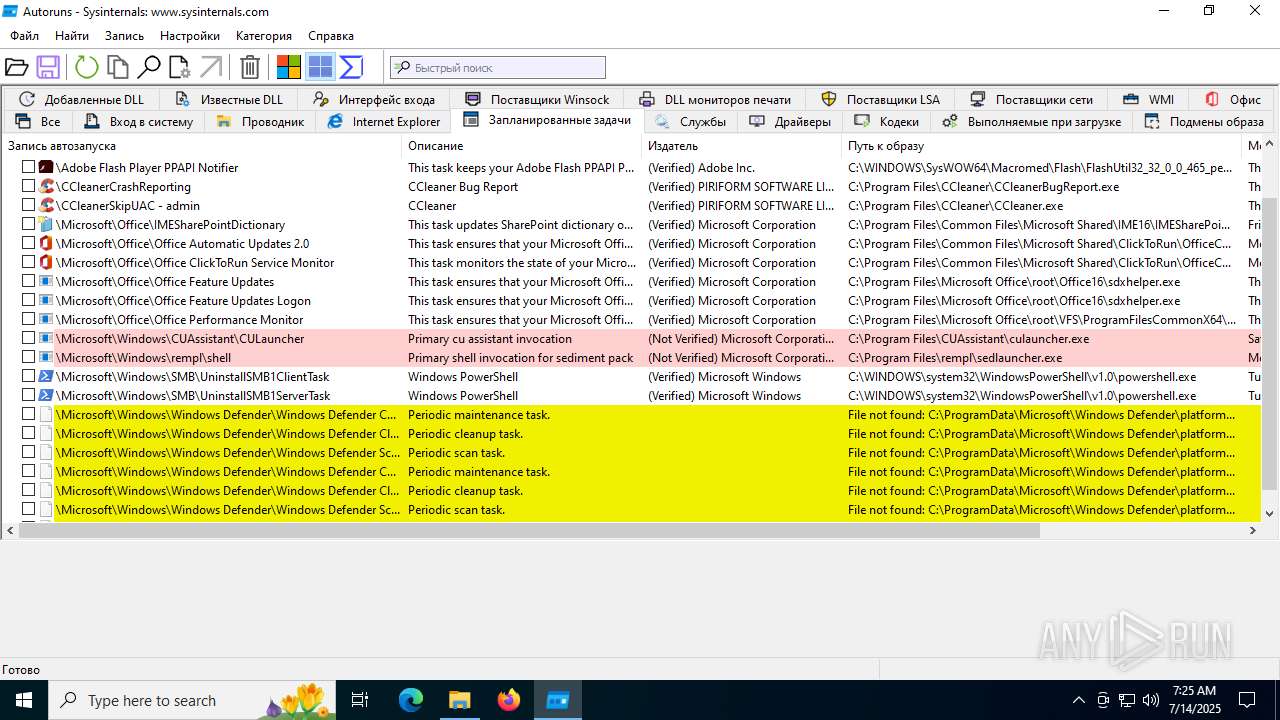
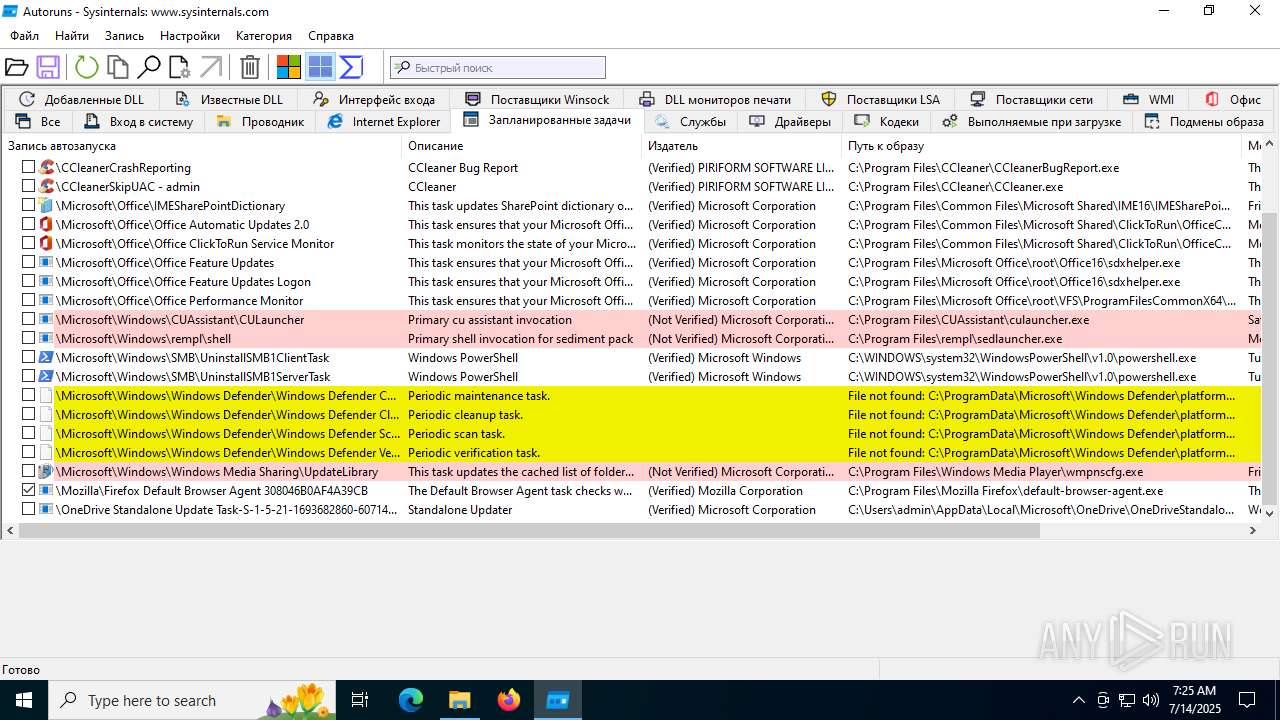
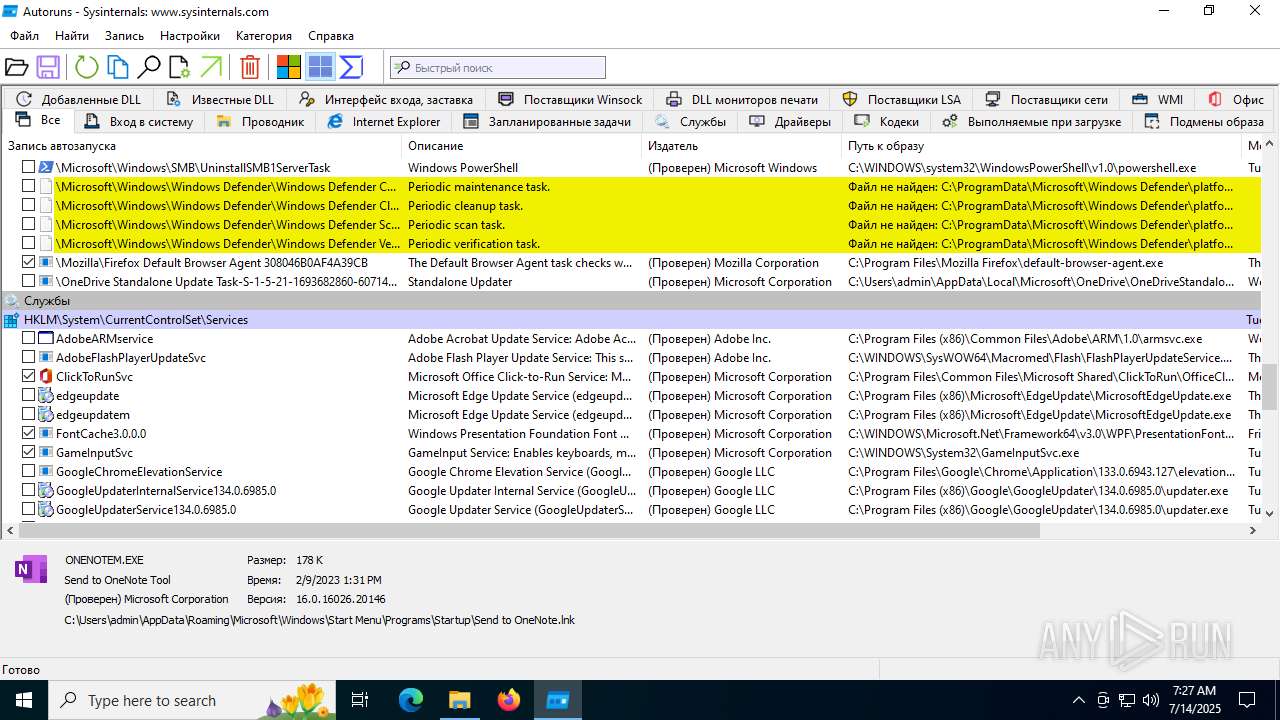
The process executes via Task Scheduler
- updater.exe (PID: 4828)
Application launched itself
- updater.exe (PID: 4828)
INFO
Manual execution by a user
- WinRAR.exe (PID: 1200)
- Autoruns.exe (PID: 1740)
- Autoruns64.exe (PID: 3976)
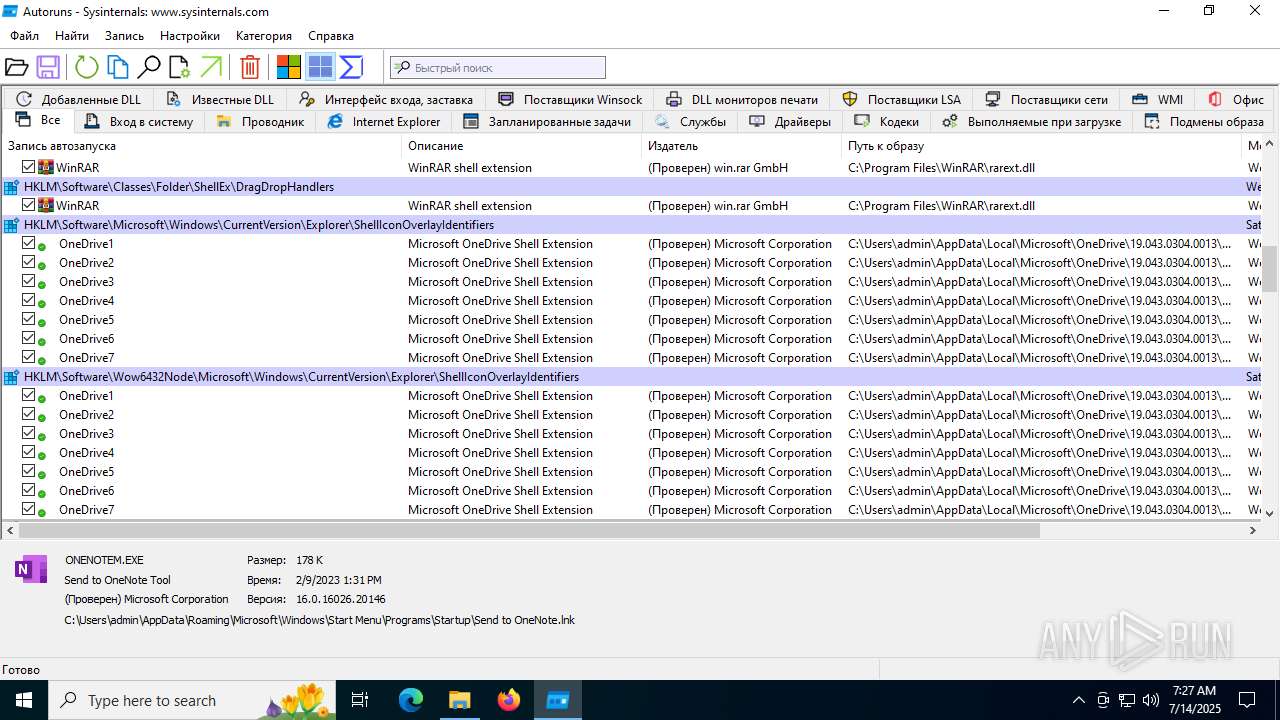
Executable content was dropped or overwritten
- WinRAR.exe (PID: 1200)
Reads the machine GUID from the registry
- Autoruns.exe (PID: 1740)
- Autoruns64.exe (PID: 3976)
Checks supported languages
- Autoruns.exe (PID: 1740)
- updater.exe (PID: 4828)
- updater.exe (PID: 5928)
- Autoruns64.exe (PID: 3976)
Reads the computer name
- Autoruns.exe (PID: 1740)
- updater.exe (PID: 4828)
- Autoruns64.exe (PID: 3976)
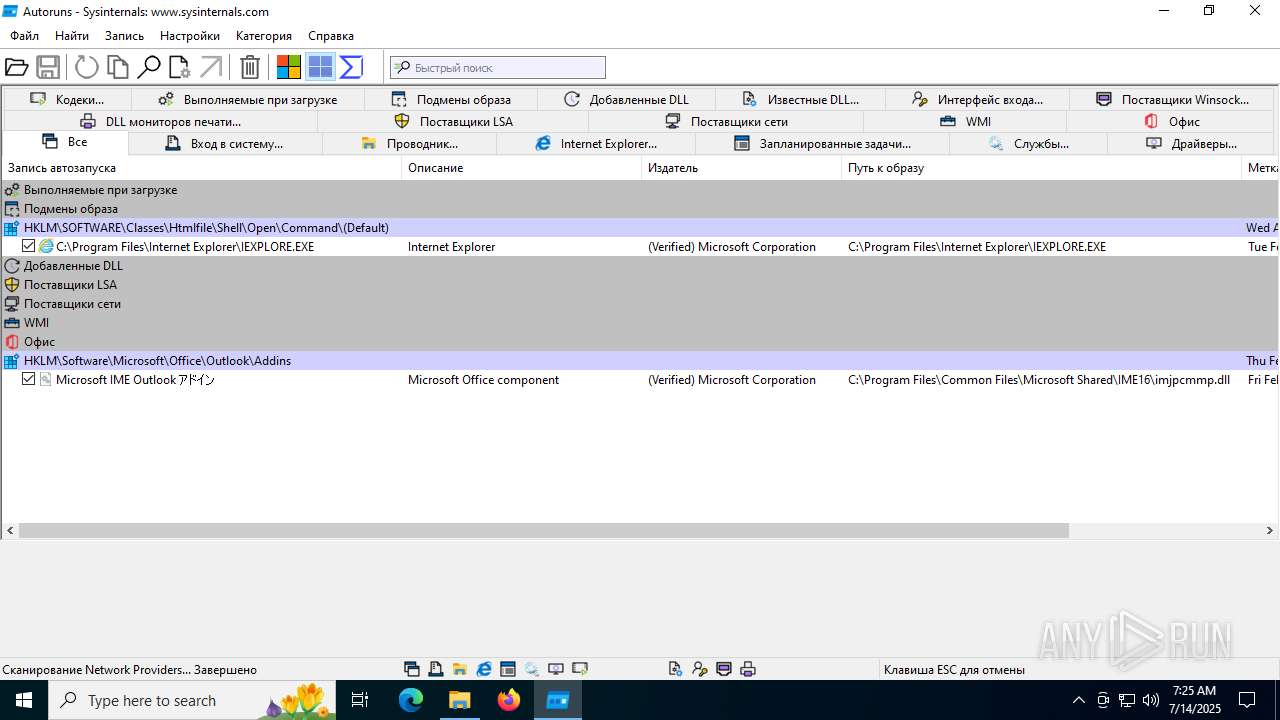
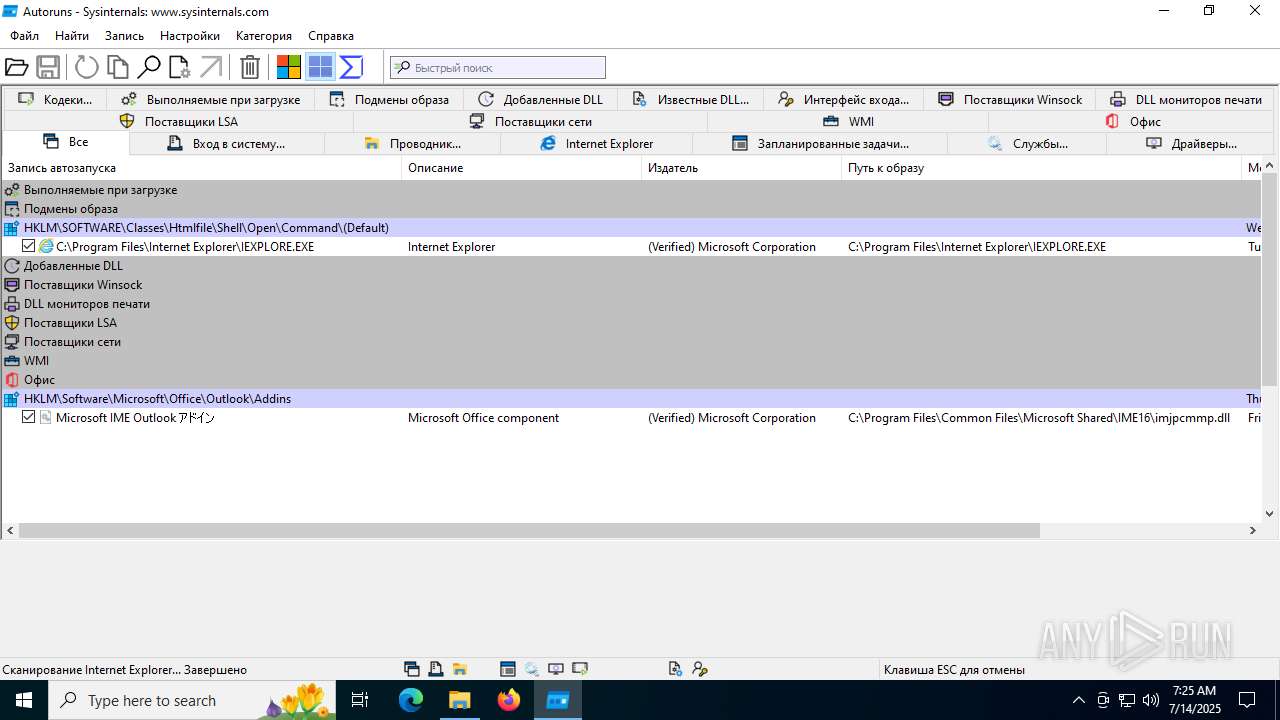
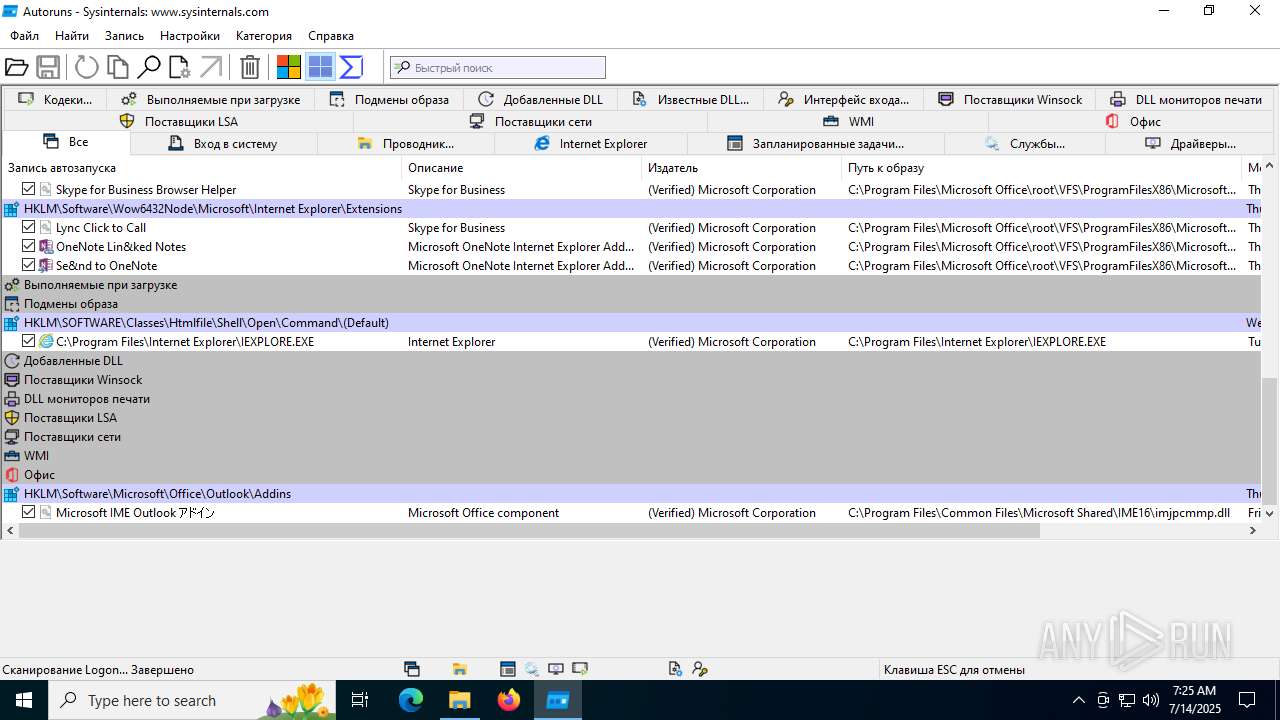
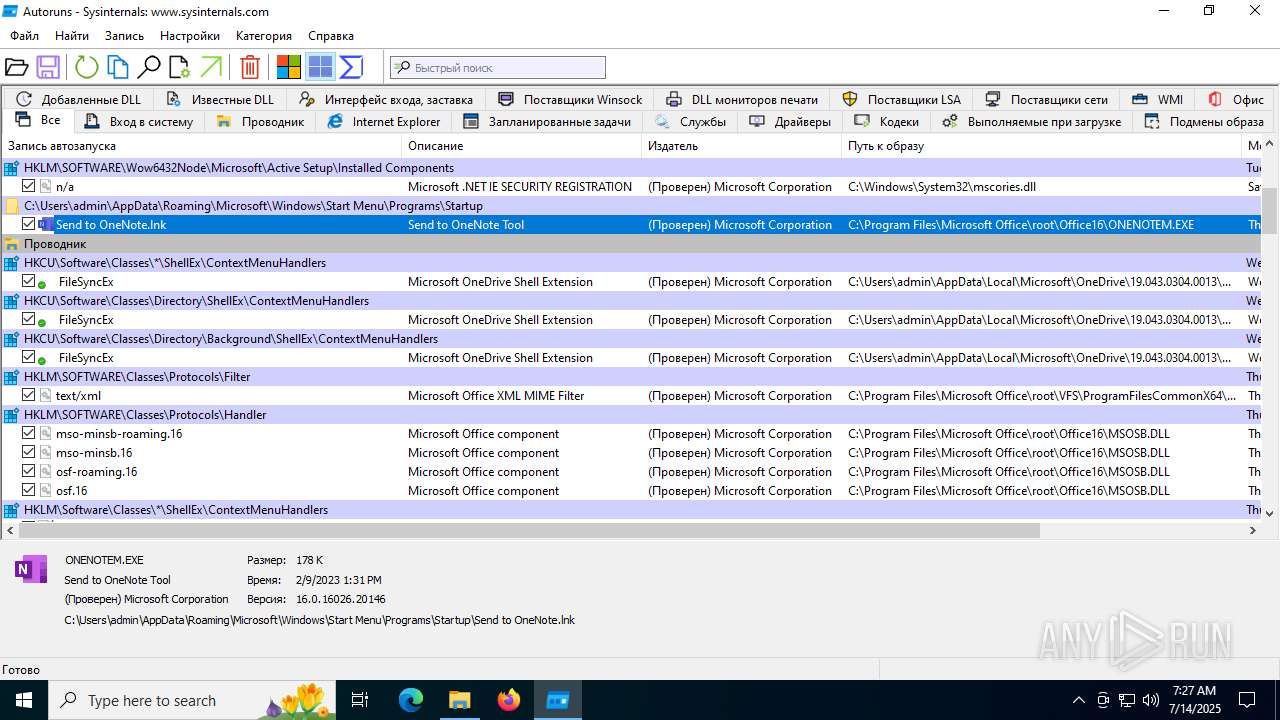
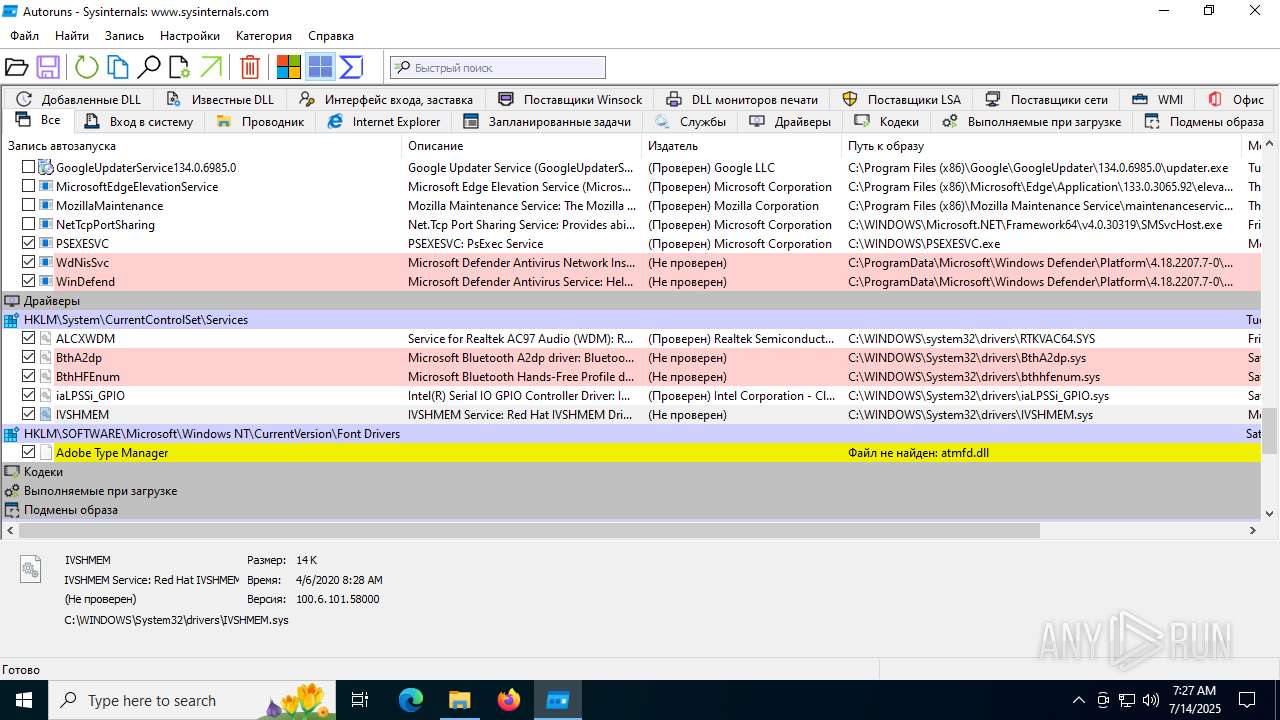
Reads Microsoft Office registry keys
- Autoruns.exe (PID: 1740)
- Autoruns64.exe (PID: 3976)
- OpenWith.exe (PID: 4800)
Checks proxy server information
- Autoruns.exe (PID: 1740)
- slui.exe (PID: 3288)
- Autoruns64.exe (PID: 3976)
Creates files or folders in the user directory
- Autoruns.exe (PID: 1740)
Reads the software policy settings
- Autoruns.exe (PID: 1740)
- slui.exe (PID: 3288)
- Autoruns64.exe (PID: 3976)
Process checks whether UAC notifications are on
- updater.exe (PID: 4828)
Reads security settings of Internet Explorer
- OpenWith.exe (PID: 4800)
- notepad.exe (PID: 2212)
Compiled with Borland Delphi (YARA)
- Autoruns64.exe (PID: 3976)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .rar | | | RAR compressed archive (v5.0) (61.5) |
|---|---|---|
| .rar | | | RAR compressed archive (gen) (38.4) |
EXIF
ZIP
| FileVersion: | RAR v5 |
|---|---|
| CompressedSize: | 501887 |
| UncompressedSize: | 1766432 |
| OperatingSystem: | Win32 |
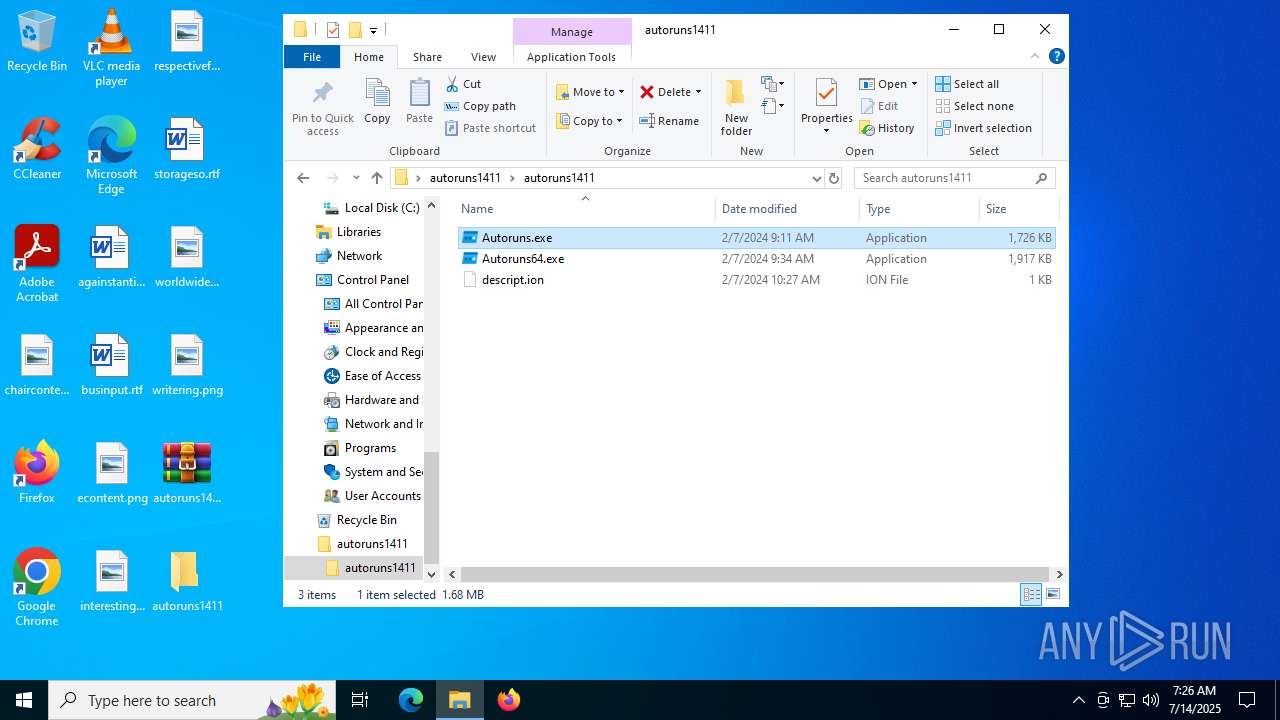
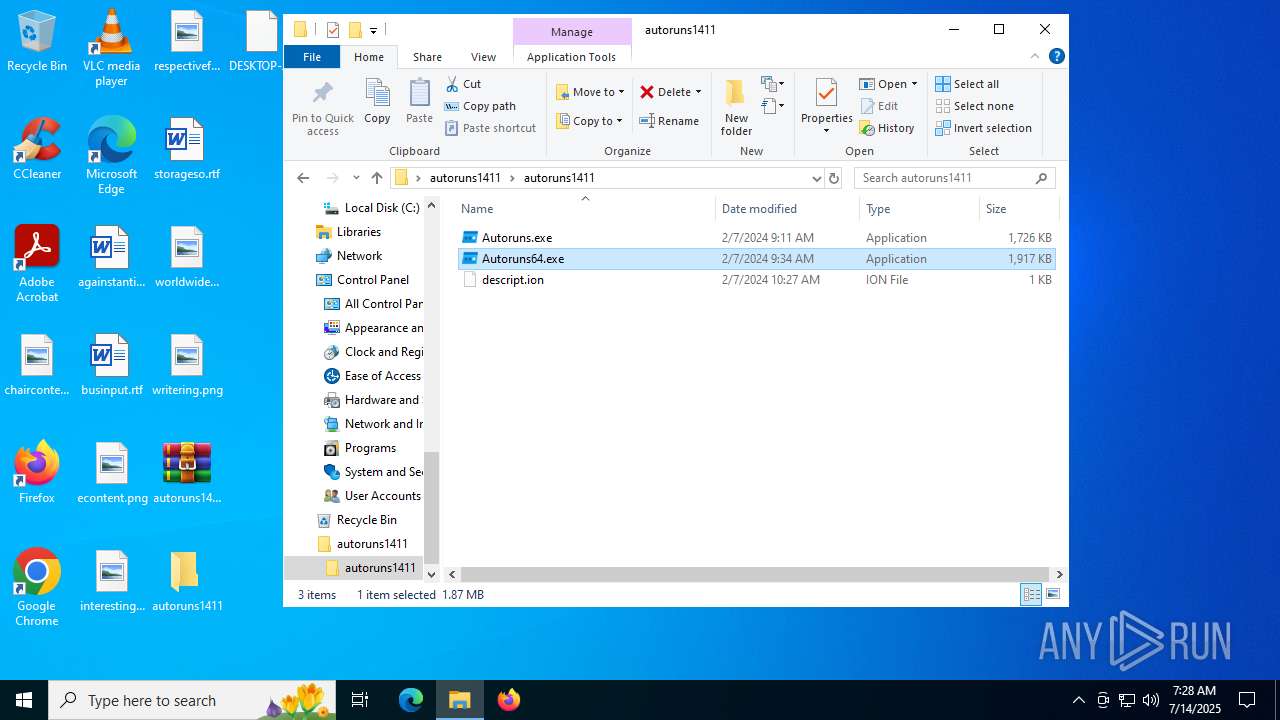
| ArchivedFileName: | autoruns1411/Autoruns.exe |
Total processes
149
Monitored processes
10
Malicious processes
0
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1200 | "C:\Program Files\WinRAR\WinRAR.exe" x -iext -ow -ver -- "C:\Users\admin\Desktop\autoruns1411.rar" C:\Users\admin\Desktop\autoruns1411\ | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
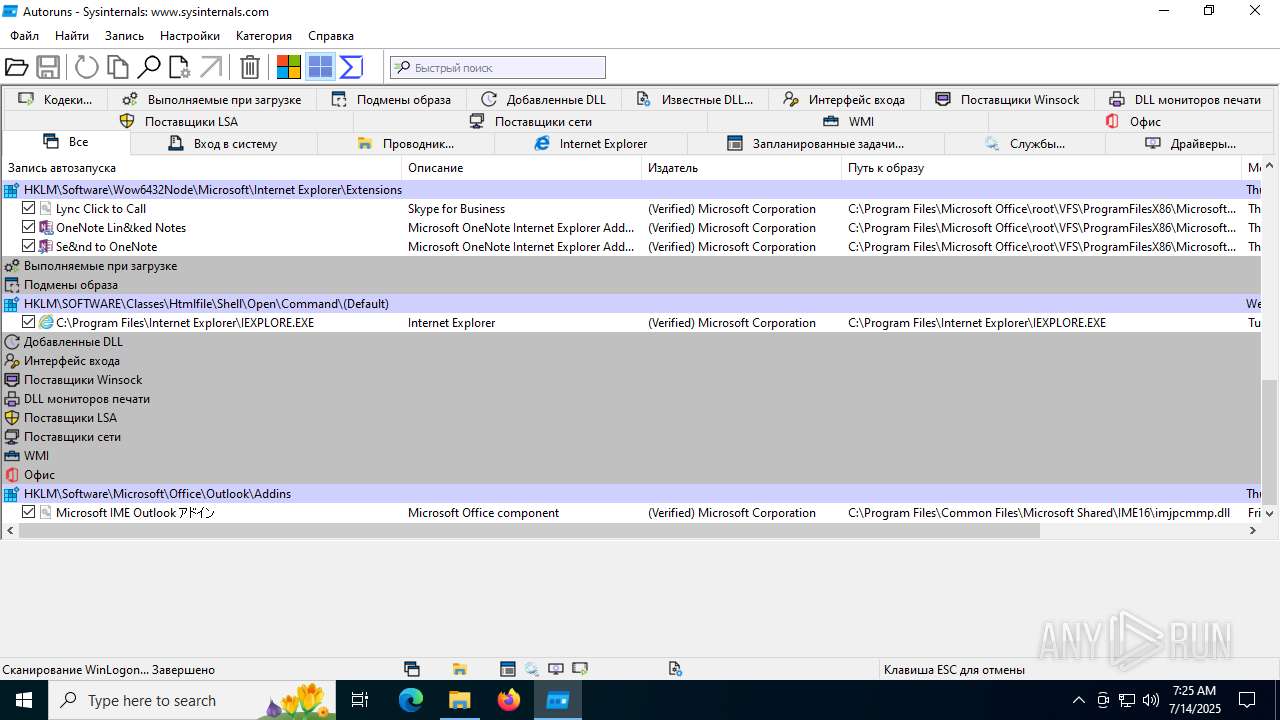
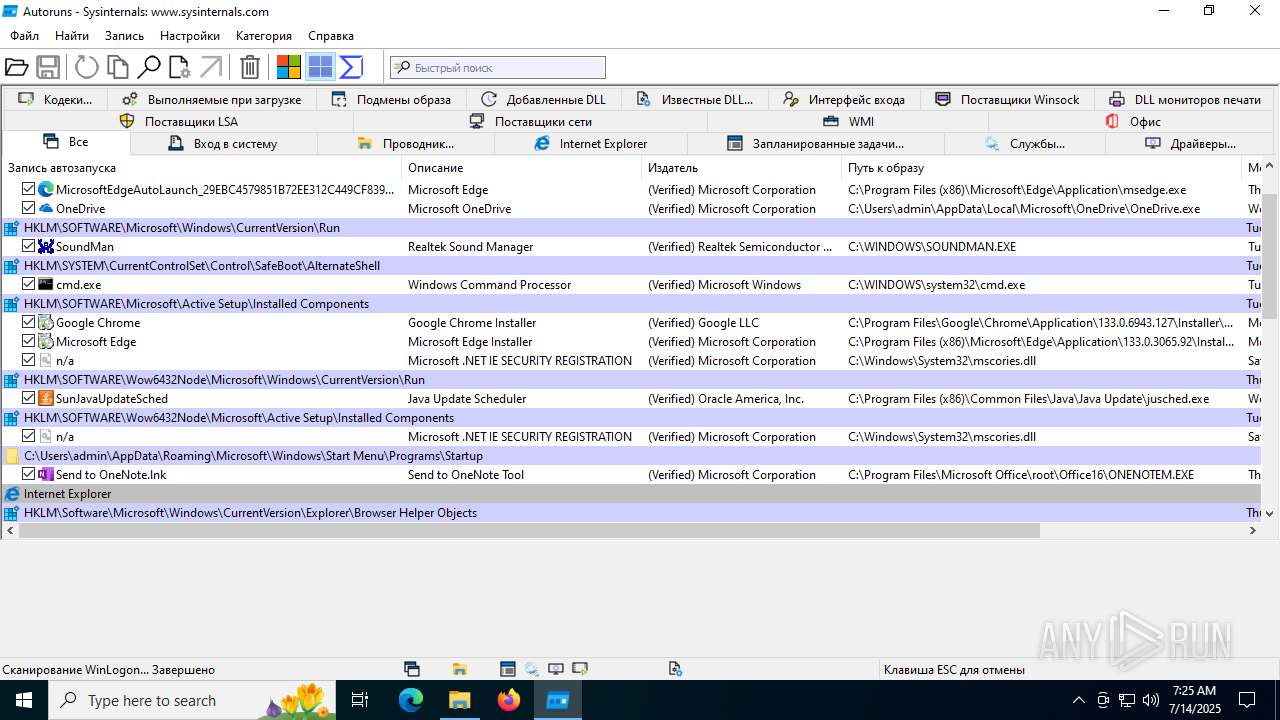
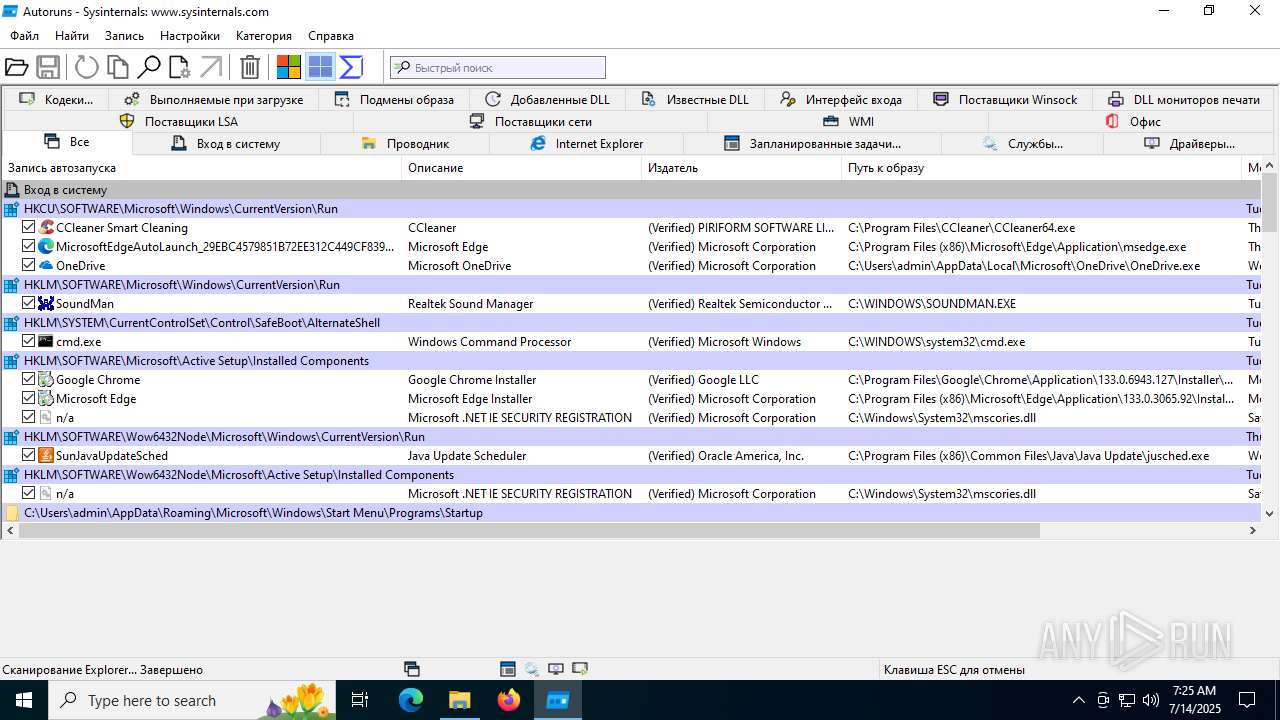
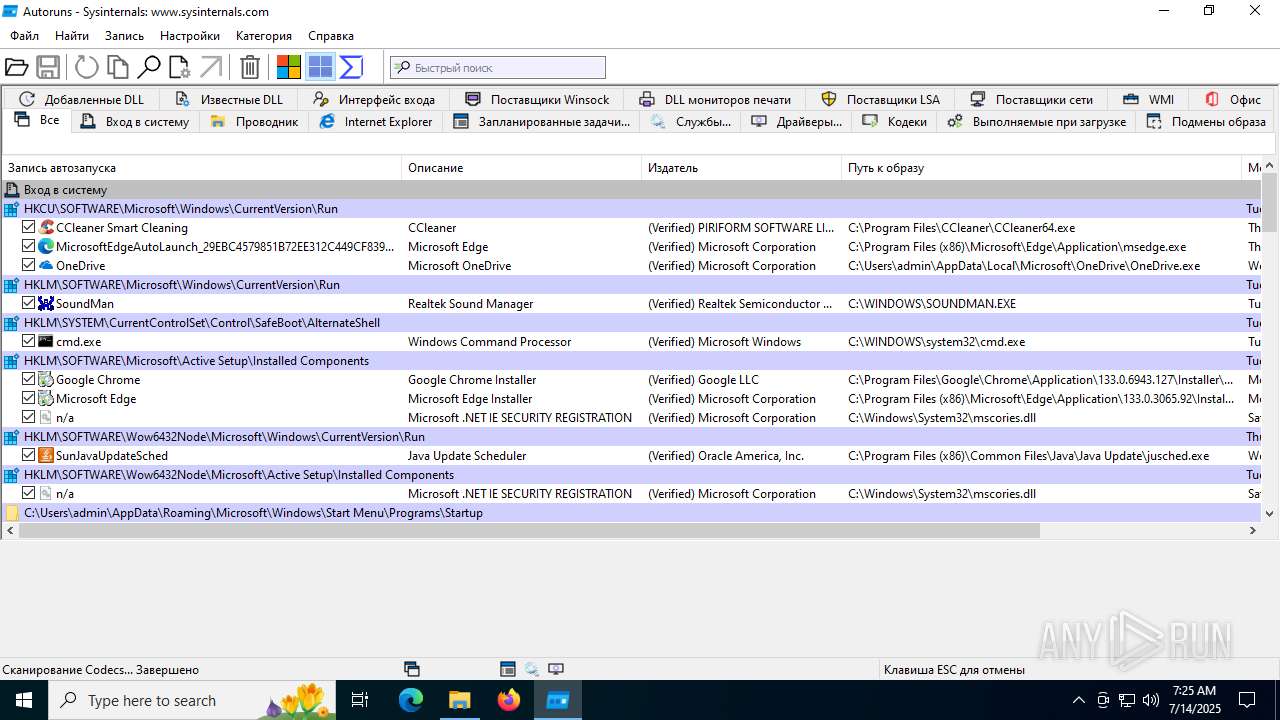
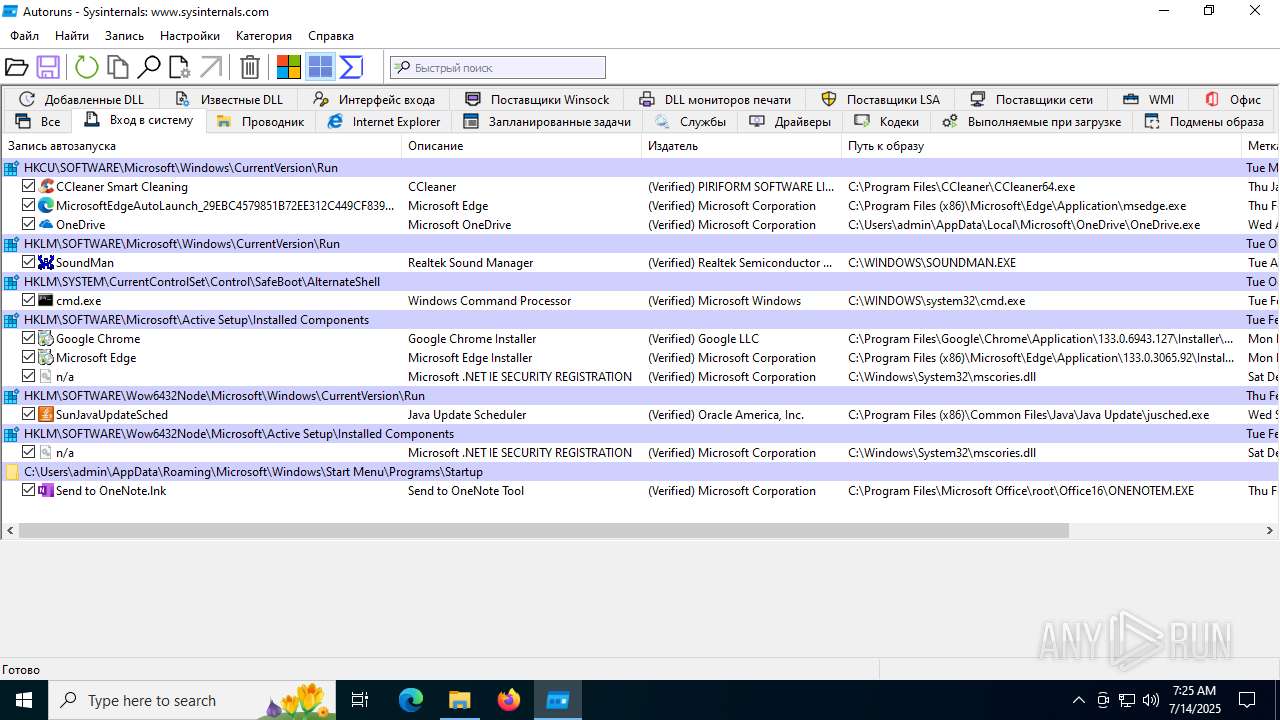
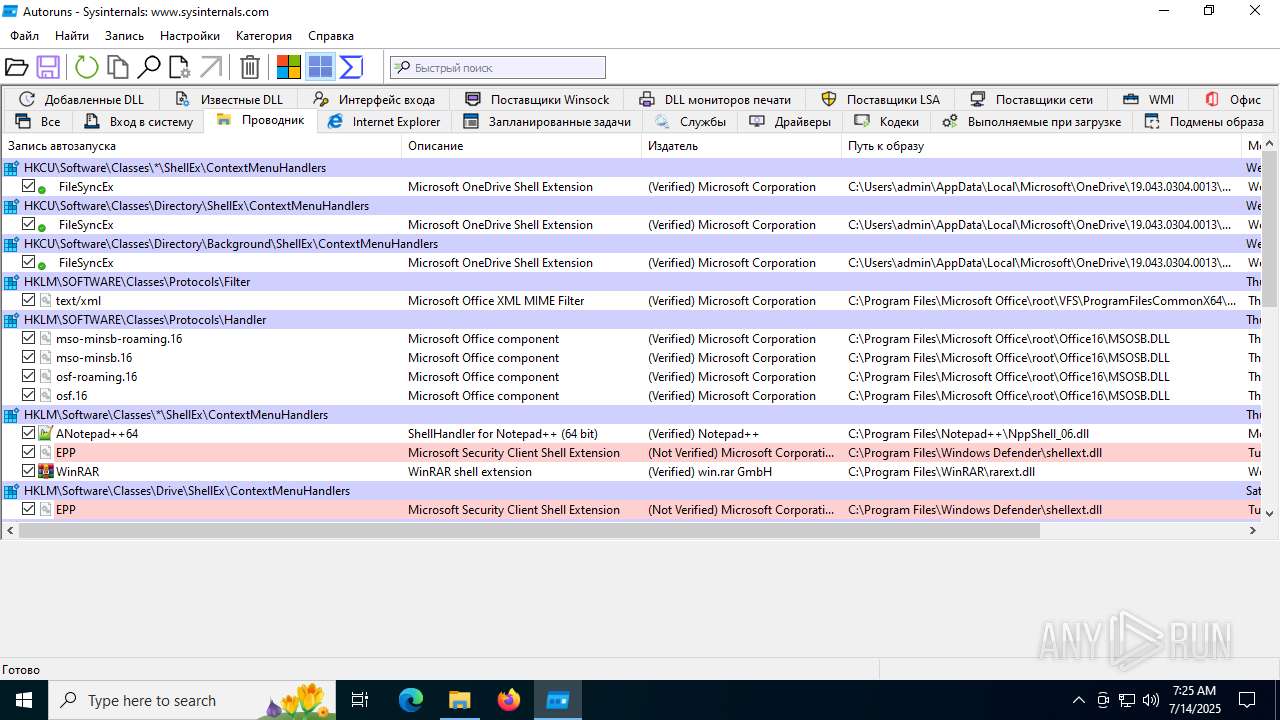
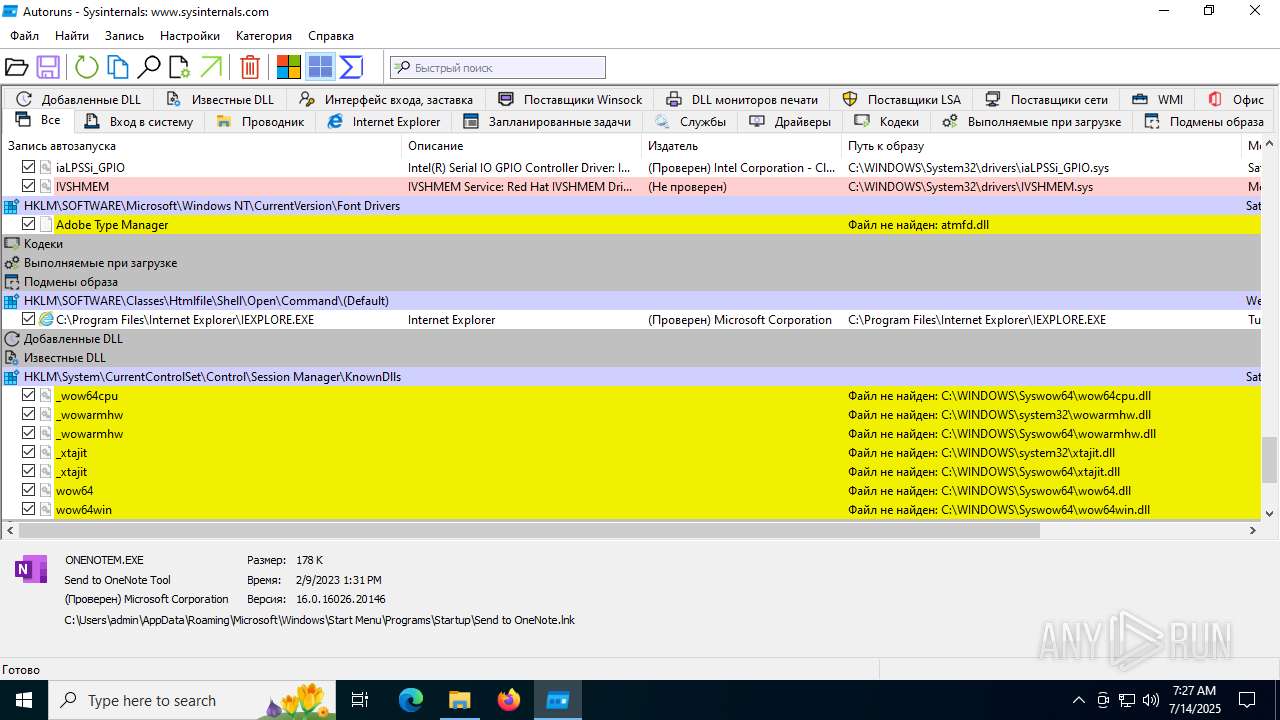
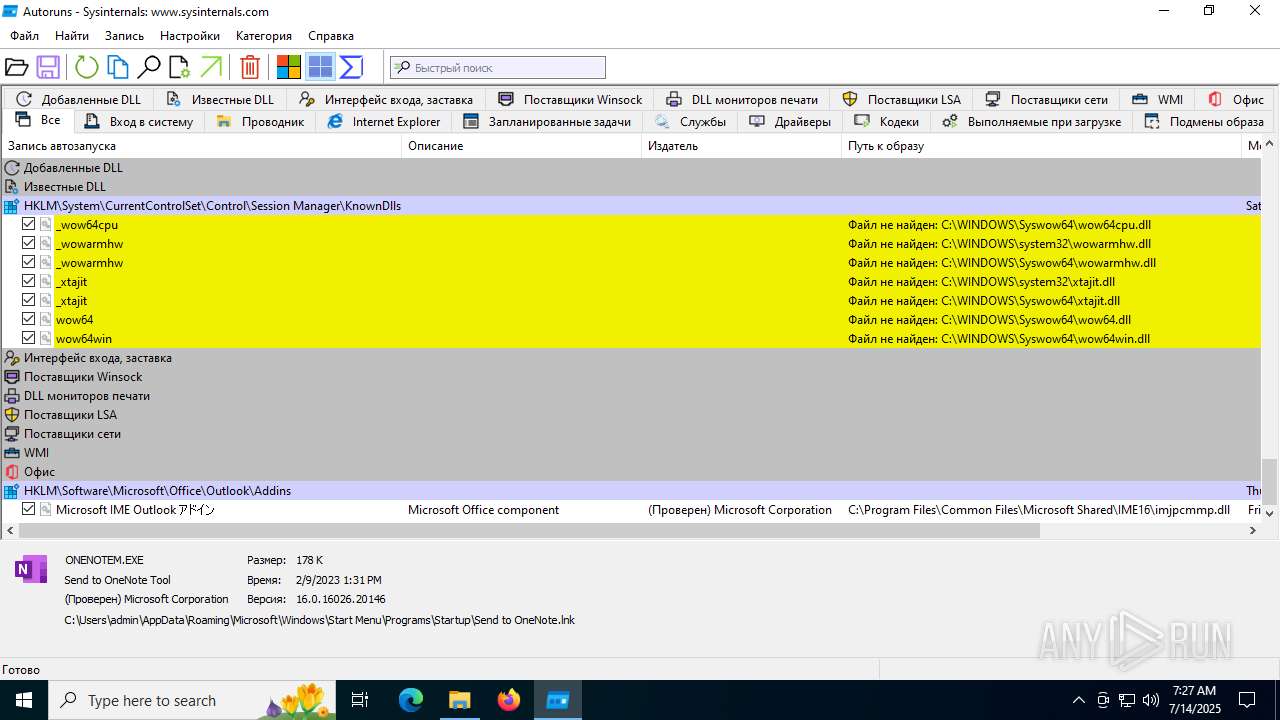
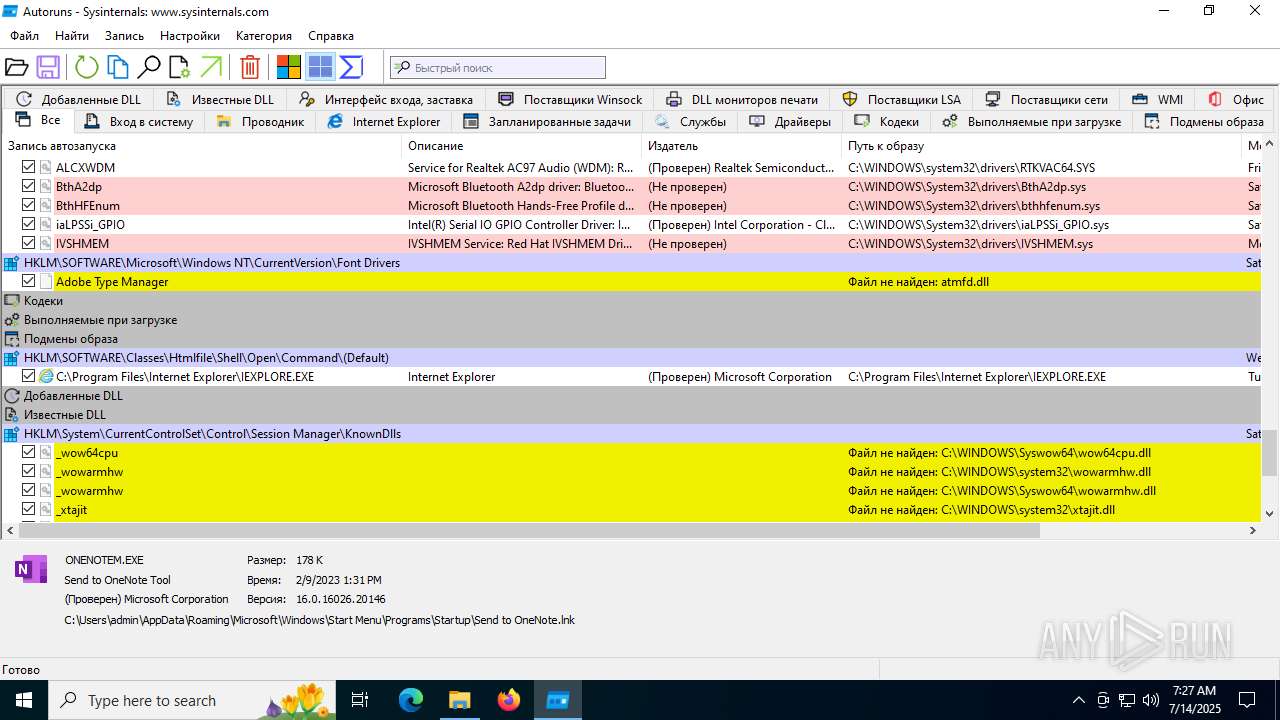
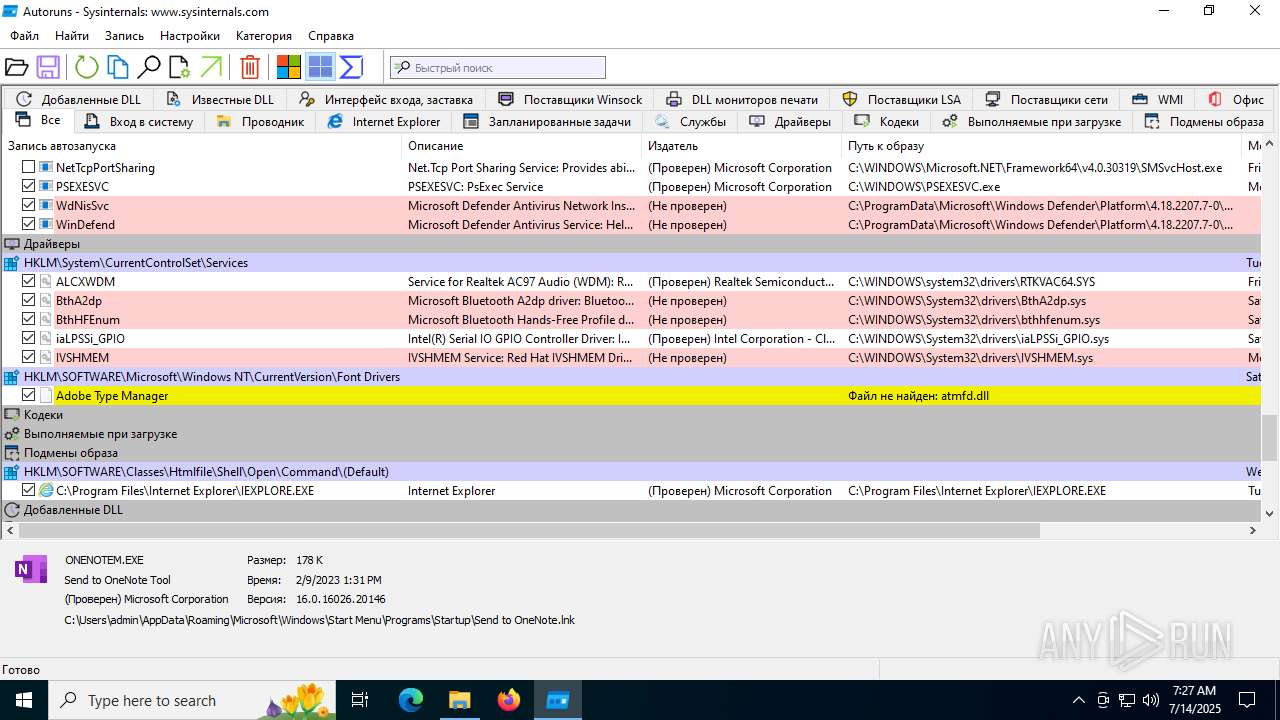
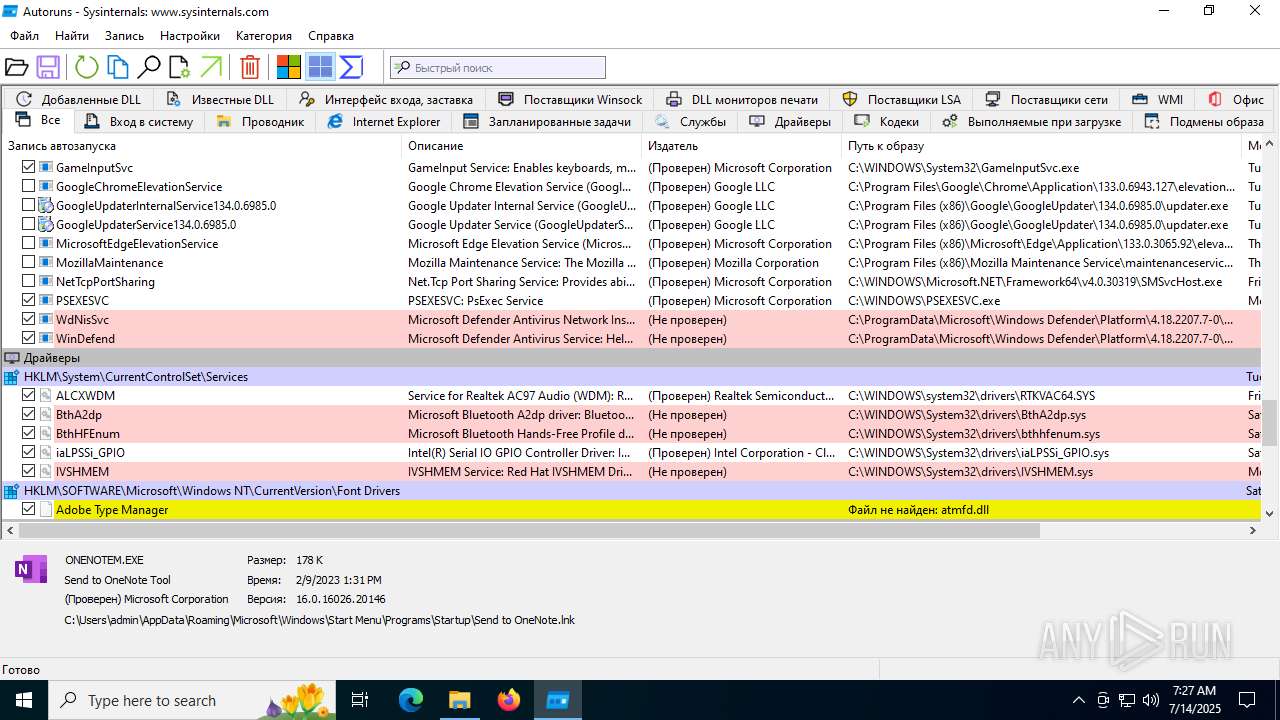
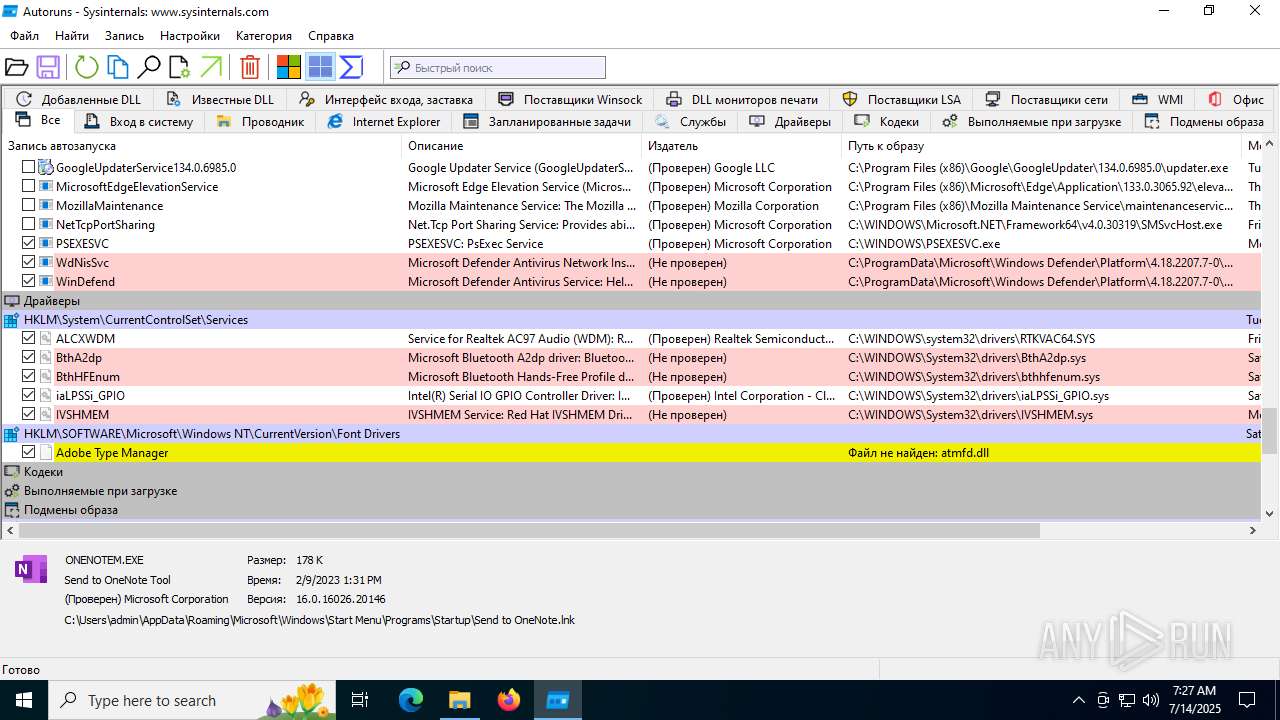
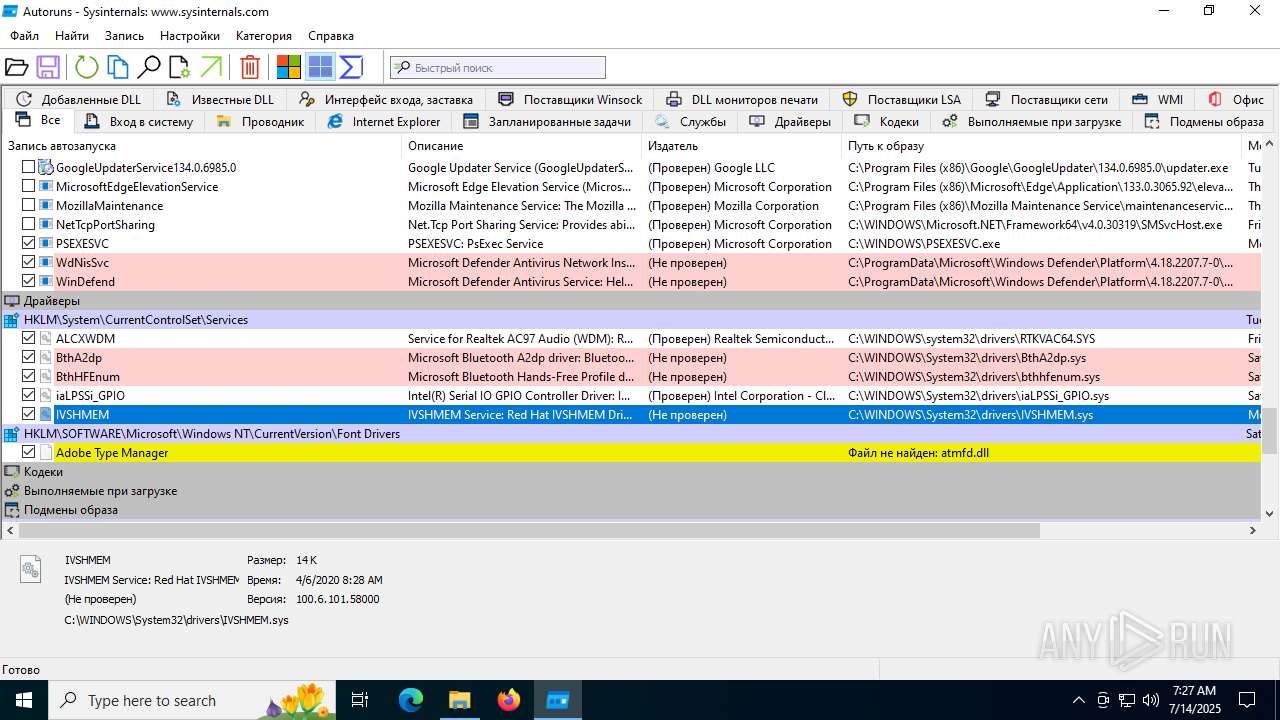
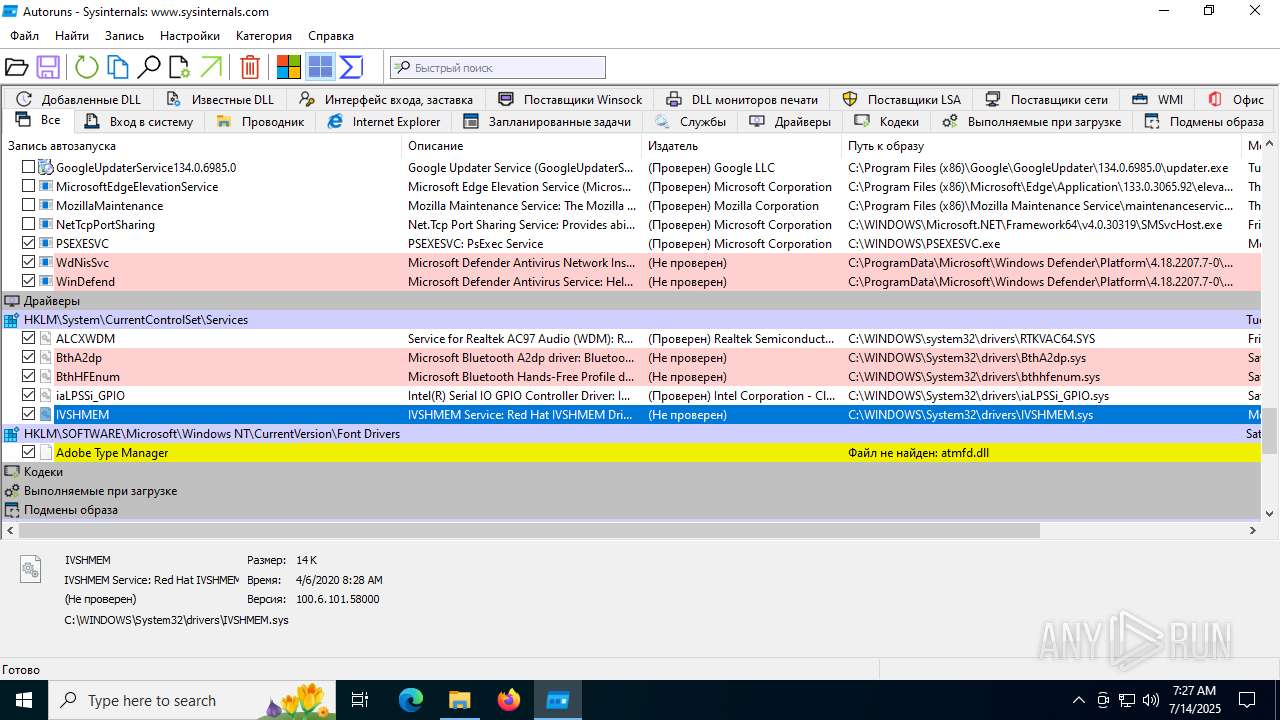
| 1740 | "C:\Users\admin\Desktop\autoruns1411\autoruns1411\Autoruns.exe" | C:\Users\admin\Desktop\autoruns1411\autoruns1411\Autoruns.exe | explorer.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Autostart program viewer Exit code: 1 Version: 14.11 Modules
| |||||||||||||||
| 2120 | "C:\Program Files\WinRAR\WinRAR.exe" C:\Users\admin\Desktop\autoruns1411.rar | C:\Program Files\WinRAR\WinRAR.exe | — | explorer.exe | |||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
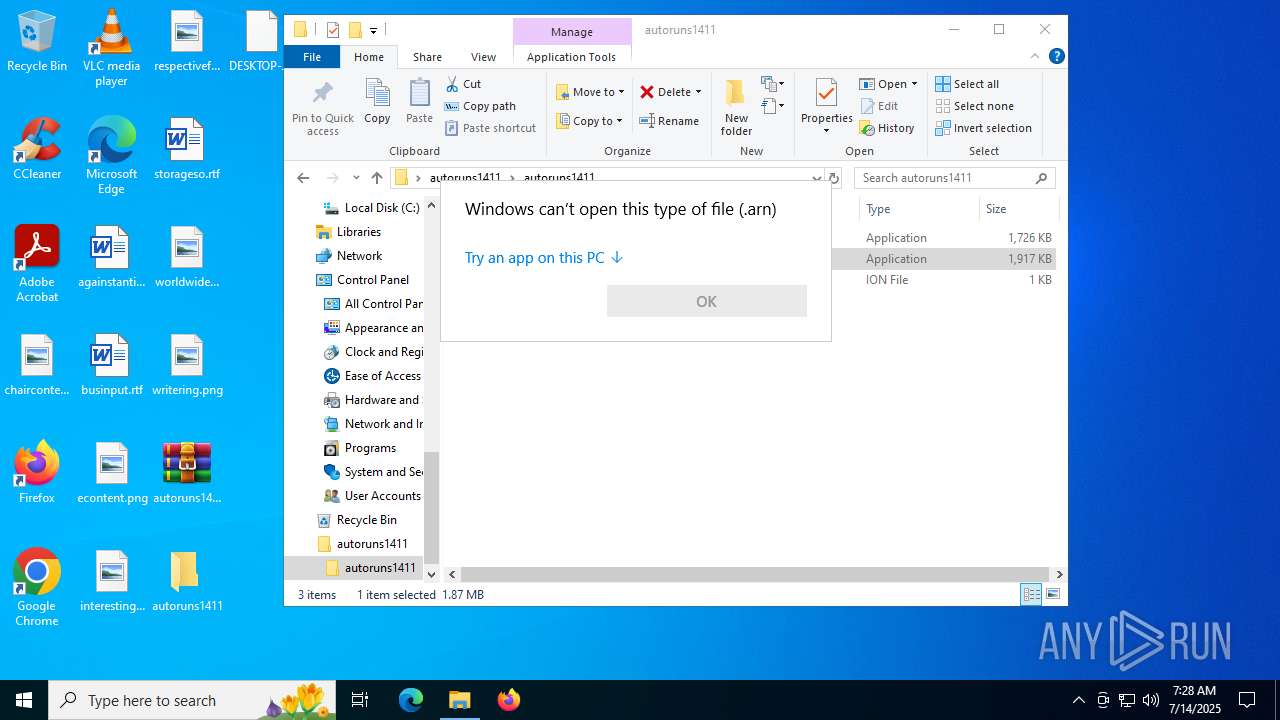
| 2212 | "C:\WINDOWS\system32\NOTEPAD.EXE" C:\Users\admin\Desktop\DESKTOP-JGLLJLD.arn | C:\Windows\System32\notepad.exe | — | OpenWith.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Notepad Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3288 | C:\WINDOWS\System32\slui.exe -Embedding | C:\Windows\System32\slui.exe | svchost.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Activation Client Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 3976 | "C:\Users\admin\Desktop\autoruns1411\autoruns1411\Autoruns64.exe" | C:\Users\admin\Desktop\autoruns1411\autoruns1411\Autoruns64.exe | explorer.exe | ||||||||||||
User: admin Company: Sysinternals - www.sysinternals.com Integrity Level: MEDIUM Description: Autostart program viewer Exit code: 1 Version: 14.11 Modules
| |||||||||||||||
| 4800 | C:\WINDOWS\system32\OpenWith.exe -Embedding | C:\Windows\System32\OpenWith.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Pick an app Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4828 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --wake --system | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | svchost.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
| 4844 | C:\WINDOWS\System32\rundll32.exe C:\WINDOWS\System32\shell32.dll,SHCreateLocalServerRunDll {9aa46009-3ce0-458a-a354-715610a075e6} -Embedding | C:\Windows\System32\rundll32.exe | — | svchost.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows host process (Rundll32) Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5928 | "C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe" --crash-handler --system "--database=C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\Crashpad" --url=https://clients2.google.com/cr/report --annotation=prod=Update4 --annotation=ver=134.0.6985.0 "--attachment=C:\Program Files (x86)\Google\GoogleUpdater\updater.log" --initial-client-data=0x298,0x29c,0x2a0,0x274,0x2a4,0x111c460,0x111c46c,0x111c478 | C:\Program Files (x86)\Google\GoogleUpdater\134.0.6985.0\updater.exe | — | updater.exe | |||||||||||
User: SYSTEM Company: Google LLC Integrity Level: SYSTEM Description: Google Updater Exit code: 0 Version: 134.0.6985.0 Modules
| |||||||||||||||
Total events
90 424
Read events
90 298
Write events
123
Delete events
3
Modification events
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\preferences.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\chromium_ext.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\omni_23_10_2024_.zip | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\Desktop\autoruns1411.rar | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | mtime |
Value: 100 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\Interface\MainWin |
| Operation: | write | Name: | Placement |
Value: 2C0000000000000001000000FFFFFFFFFFFFFFFFFFFFFFFFFFFFFFFF3D0000002D000000FD03000016020000 | |||
| (PID) Process: | (2120) WinRAR.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\WinRAR\FileList\ArcColumnWidths |
| Operation: | write | Name: | name |
Value: 256 | |||
Executable files
2
Suspicious files
31
Text files
2
Unknown types
25
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1200 | WinRAR.exe | C:\Users\admin\Desktop\autoruns1411\autoruns1411\Autoruns.exe | executable | |
MD5:56C1E507A5EBE89C3963AE6414D534EA | SHA256:9440F9E674A19CCC65EB15F29E50E2D66982548325B2F69EFB9CA28FDD1636FB | |||
| 1740 | Autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\36AC0BE60E1243344AE145F746D881FE | der | |
MD5:C6F7D090D87C6DC222163220F0BCAD74 | SHA256:751DB37215004FADF8C7EC5D5DCF0272F20742BDDEB4C8C13DB9C05A067969BC | |||
| 1200 | WinRAR.exe | C:\Users\admin\Desktop\autoruns1411\autoruns1411\descript.ion | text | |
MD5:DE44E9DE0D7677A0EE44CB1DAFB6ED60 | SHA256:2FDD5E128A10B86A32DA550CAF954BE84FAA835E5E45EDD4FBA58E324ED40DF3 | |||
| 1740 | Autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\A583E2A51BFBDC1E492A57B7C8325850 | der | |
MD5:144D698C7F3CCD662F9460D8F443A2BB | SHA256:C5714AC85358D727F4EA913F814CCADCD7F6E063D95B54B886CCF6BFC31612C1 | |||
| 1740 | Autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\A583E2A51BFBDC1E492A57B7C8325850 | binary | |
MD5:34FD9A8717C3F434AEDFCA8DE42040EA | SHA256:05C59F625ED10C775CF5BA6A5FB0C028C868B9986DA8405EF418DF9393812875 | |||
| 1740 | Autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\0B8A20E1F3F4D73D52A19929F922C892 | der | |
MD5:A511DAB56DC44A64A1114B7814E4F8C6 | SHA256:08FA57906B20E454242889F05F1609C276B91A06561121E9012A88A50FF23F9F | |||
| 1740 | Autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\36AC0BE60E1243344AE145F746D881FE | binary | |
MD5:045960292690BD1763ECE2D43B65B951 | SHA256:6DF148C33AEAAF87FF7CA308B885752D5877F04282835DF8FA2651F010CCE207 | |||
| 1740 | Autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\Content\45AE547469FB7137480E06153457A2DD | der | |
MD5:1C377FFC470964E618886611D50CD89D | SHA256:68F63C2B85F7A54CF432D286F6F262F2A99B0D6F53EEDA3D56801D4DDA29C588 | |||
| 1200 | WinRAR.exe | C:\Users\admin\Desktop\autoruns1411\autoruns1411\Autoruns64.exe | executable | |
MD5:A29E9ABC719BC144867EBB6ED3232F2D | SHA256:694236339883F54CCA1DF17DC7AE60F41679F1AF3279E71FA7B2F8A55BE53301 | |||
| 1740 | Autoruns.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\4C7F163ED126D5C3CB9457F68EC64E9E | binary | |
MD5:FEEFC5047B8907775DE7758B716EACF0 | SHA256:6FAC45E39ACF9B52426713F815A548ACF606E55FD0117C55367541A709F8139E | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
60
TCP/UDP connections
47
DNS requests
41
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
1268 | svchost.exe | GET | 200 | 23.216.77.28:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1268 | svchost.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
1740 | Autoruns.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20Time-Stamp%20PCA%202010(1).crl | unknown | — | — | whitelisted |
1740 | Autoruns.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTfqhLjKLEJQZPin0KCzkdAQpVYowQUsT7DaQP4v0cB1JgmGggC72NkK8MCEAPxtOFfOoLxFJZ4s9fYR1w%3D | unknown | — | — | whitelisted |
1740 | Autoruns.exe | GET | 200 | 23.216.77.6:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
1740 | Autoruns.exe | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicCodSigPCA2011_2011-07-08.crl | unknown | — | — | whitelisted |
1740 | Autoruns.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSRXerF0eFeSWRripTgTkcJWMm7iQQUaDfg67Y7%2BF8Rhvv%2BYXsIiGX0TkICEAV14ffsm9imej9hicY%2Bl7s%3D | unknown | — | — | whitelisted |
1740 | Autoruns.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSPwl%2BrBFlJbvzLXU1bGW08VysJ2wQUj%2Bh%2B8G0yagAFI8dwl2o6kP9r6tQCEA0srM0%2BnuwGc4QQujG%2FZZU%3D | unknown | — | — | whitelisted |
1740 | Autoruns.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBT3xL4LQLXDRDM9P665TW442vrsUQQUReuir%2FSSy4IxLVGLp6chnfNtyA8CEAQJGBtf1btmdVNDtW%2BVUAg%3D | unknown | — | — | whitelisted |
1740 | Autoruns.exe | GET | 200 | 2.17.190.73:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSnR4FoxLLkI7vkvsUIFlZt%2BlGH3gQUWsS5eyoKo6XqcQPAYPkt9mV1DlgCEAkQWITrlZ07yLmU%2BRintu4%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
5944 | MoUsoCoreWorker.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2140 | RUXIMICS.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
1268 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1268 | svchost.exe | 23.216.77.28:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
1268 | svchost.exe | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
2292 | svchost.exe | 20.190.159.68:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2292 | svchost.exe | 2.17.190.73:80 | ocsp.digicert.com | AKAMAI-AS | DE | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |