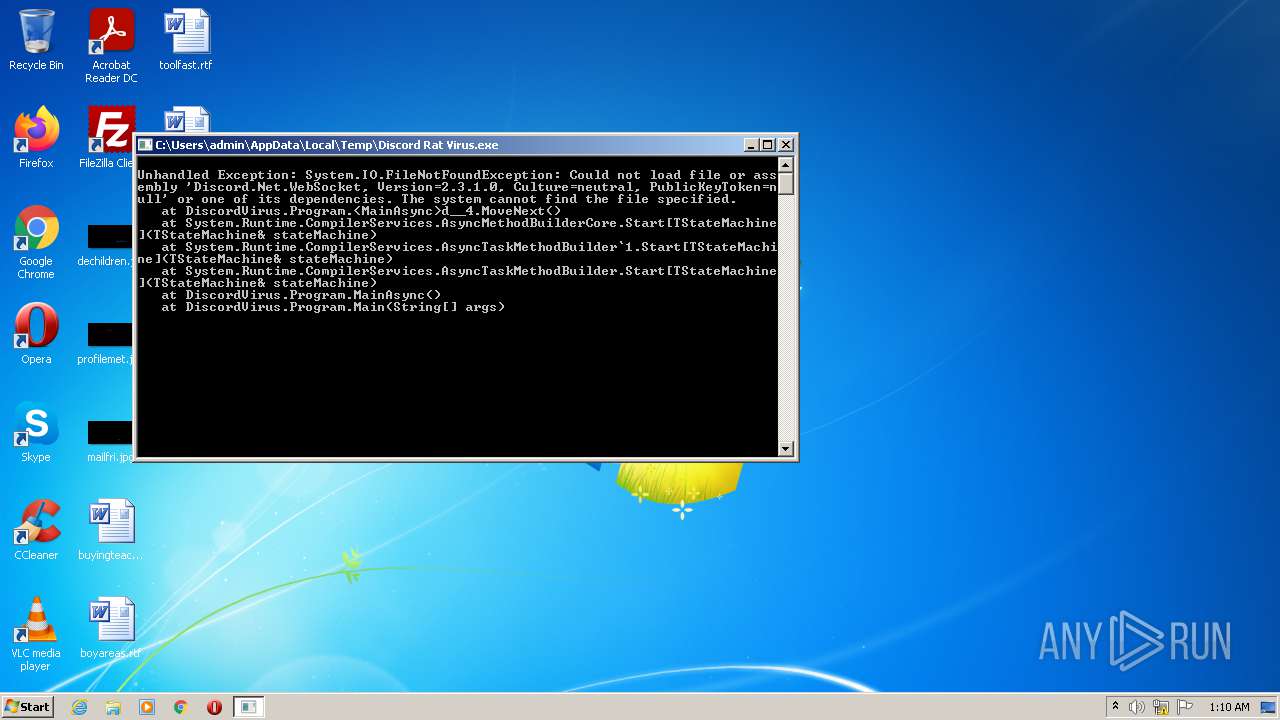
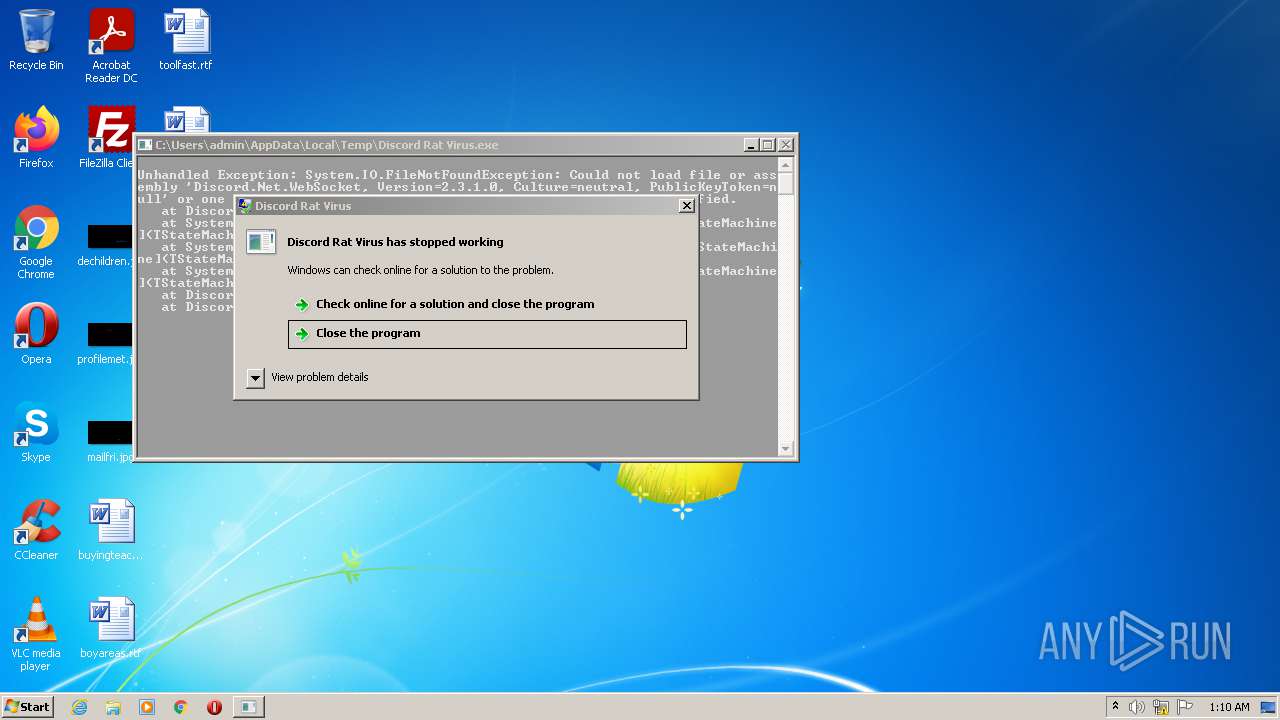
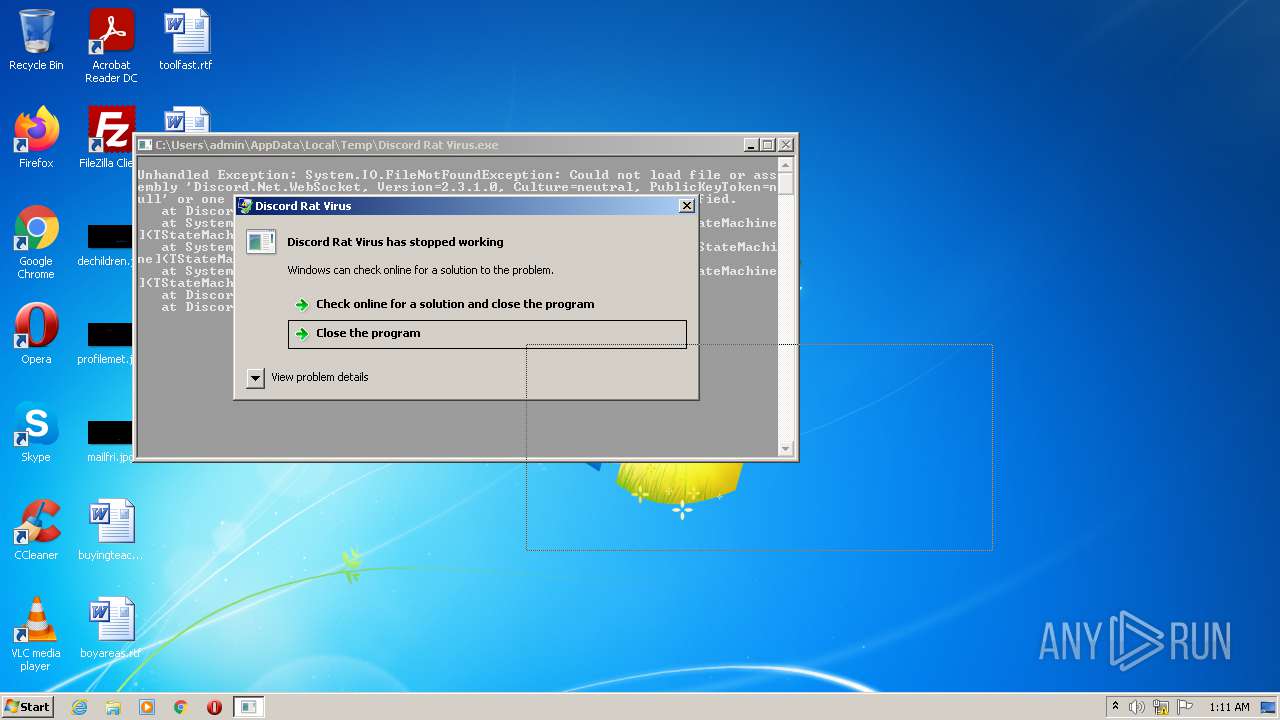
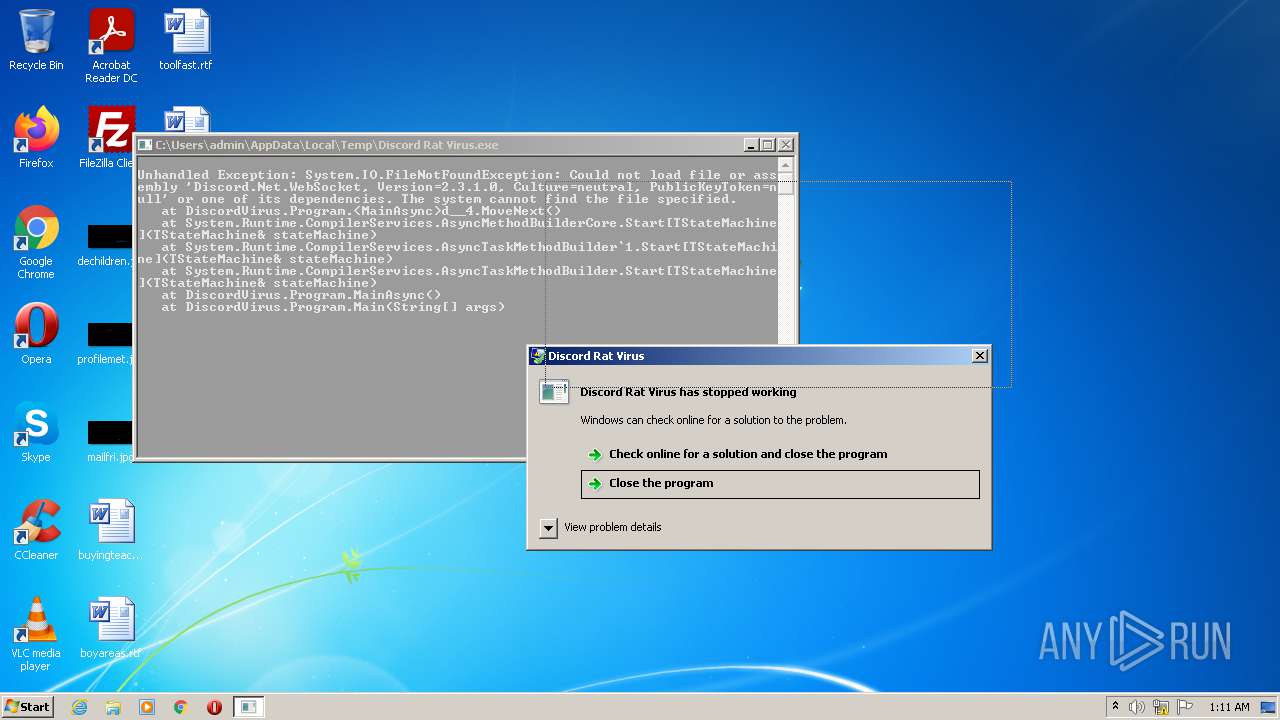
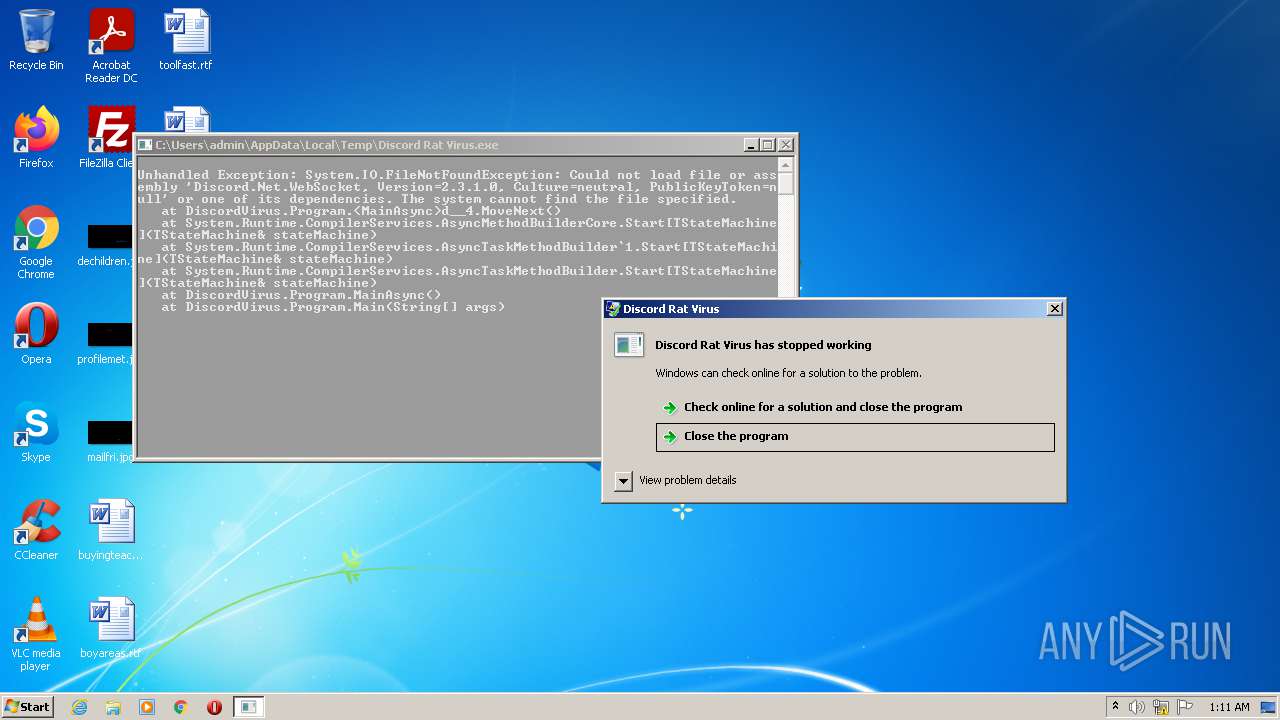
| File name: | Discord Rat Virus.exe |
| Full analysis: | https://app.any.run/tasks/d060c29a-0b0e-4a53-a14b-791d189fa5a1 |
| Verdict: | Malicious activity |
| Analysis date: | August 12, 2021, 00:10:26 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (console) Intel 80386 Mono/.Net assembly, for MS Windows |
| MD5: | 06A767F038DB615F1217F1D5CFB86FBF |
| SHA1: | 5E7BAF7B5E32756C56B6882C73D6076645CD61CF |
| SHA256: | AACF389400BC5E0C9FD83363A4E0AC03A2230CAB33D4A86D81E4DDE62C2C9260 |
| SSDEEP: | 192:eBw1V+Qh6CIcTqDM5ppqAV88L0xSZ3a5d8EXknOKwnPMw4MTmz9+K:333TD5tV88L0xSZ3C8EnKwPMwtmp+ |
MALICIOUS
Actions looks like stealing of personal data
- DllHost.exe (PID: 3140)
Loads dropped or rewritten executable
- MsiExec.exe (PID: 3968)
- MsiExec.exe (PID: 764)
- aspnet_regiis.exe (PID: 4012)
Application was dropped or rewritten from another process
- Setup.exe (PID: 3884)
- mscorsvw.exe (PID: 3116)
- mscorsvw.exe (PID: 4016)
- mscorsvw.exe (PID: 2948)
- mscorsvw.exe (PID: 2092)
- mscorsvw.exe (PID: 2700)
- mscorsvw.exe (PID: 2688)
- mscorsvw.exe (PID: 352)
- mscorsvw.exe (PID: 3420)
- mscorsvw.exe (PID: 3428)
- mscorsvw.exe (PID: 3132)
- mscorsvw.exe (PID: 2380)
- mscorsvw.exe (PID: 2676)
- mscorsvw.exe (PID: 336)
- mscorsvw.exe (PID: 3176)
- mscorsvw.exe (PID: 3720)
- mscorsvw.exe (PID: 2488)
- mscorsvw.exe (PID: 568)
- mscorsvw.exe (PID: 756)
- mscorsvw.exe (PID: 3300)
- mscorsvw.exe (PID: 3672)
- mscorsvw.exe (PID: 420)
- mscorsvw.exe (PID: 1964)
- mscorsvw.exe (PID: 2508)
- mscorsvw.exe (PID: 4008)
- mscorsvw.exe (PID: 2952)
- mscorsvw.exe (PID: 3304)
- mscorsvw.exe (PID: 2312)
- mscorsvw.exe (PID: 2464)
- mscorsvw.exe (PID: 3868)
- mscorsvw.exe (PID: 4008)
- mscorsvw.exe (PID: 1652)
- mscorsvw.exe (PID: 2652)
- mscorsvw.exe (PID: 4028)
- mscorsvw.exe (PID: 2772)
- mscorsvw.exe (PID: 2376)
- mscorsvw.exe (PID: 1428)
- mscorsvw.exe (PID: 4092)
- mscorsvw.exe (PID: 464)
- mscorsvw.exe (PID: 3284)
- ngen.exe (PID: 2556)
- ngen.exe (PID: 2472)
- mscorsvw.exe (PID: 1092)
- mscorsvw.exe (PID: 3956)
- mscorsvw.exe (PID: 1428)
- mscorsvw.exe (PID: 1388)
- mscorsvw.exe (PID: 3412)
- mscorsvw.exe (PID: 2256)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 3492)
- ngen.exe (PID: 2784)
- ngen.exe (PID: 408)
- ngen.exe (PID: 2920)
- ngen.exe (PID: 2620)
- ngen.exe (PID: 2328)
- ngen.exe (PID: 2220)
- ngen.exe (PID: 508)
- ngen.exe (PID: 1268)
- ngen.exe (PID: 3672)
- ngen.exe (PID: 3188)
- ngen.exe (PID: 1312)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 2132)
- ngen.exe (PID: 3044)
- ngen.exe (PID: 2736)
- ngen.exe (PID: 3052)
- ngen.exe (PID: 3760)
- ngen.exe (PID: 3624)
- ngen.exe (PID: 2688)
- ngen.exe (PID: 2360)
- ngen.exe (PID: 1104)
- ngen.exe (PID: 2584)
- ngen.exe (PID: 2380)
- ngen.exe (PID: 3160)
- ngen.exe (PID: 2792)
- ngen.exe (PID: 2196)
- ngen.exe (PID: 4024)
- ngen.exe (PID: 504)
- ngen.exe (PID: 2232)
- ngen.exe (PID: 1252)
- ngen.exe (PID: 3320)
- ngen.exe (PID: 3536)
- ngen.exe (PID: 3788)
- ngen.exe (PID: 3704)
- ngen.exe (PID: 2284)
- ngen.exe (PID: 1300)
- ngen.exe (PID: 2884)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 3032)
- ngen.exe (PID: 2396)
- ngen.exe (PID: 2068)
- ngen.exe (PID: 1140)
- ngen.exe (PID: 3152)
- ngen.exe (PID: 3896)
- ngen.exe (PID: 3640)
- ngen.exe (PID: 2816)
- ngen.exe (PID: 3892)
- ngen.exe (PID: 868)
- ngen.exe (PID: 3444)
- ngen.exe (PID: 1844)
- ngen.exe (PID: 2380)
- ngen.exe (PID: 3180)
- ngen.exe (PID: 3896)
- ngen.exe (PID: 3484)
- ngen.exe (PID: 2128)
- ngen.exe (PID: 3008)
- ngen.exe (PID: 408)
- ngen.exe (PID: 3552)
- ngen.exe (PID: 2072)
- ngen.exe (PID: 2396)
- ngen.exe (PID: 3212)
- ngen.exe (PID: 3024)
- ngen.exe (PID: 784)
- ngen.exe (PID: 3868)
- ngen.exe (PID: 2256)
- ngen.exe (PID: 2000)
- ngen.exe (PID: 1276)
- ngen.exe (PID: 568)
- ngen.exe (PID: 3276)
- ngen.exe (PID: 3416)
- ngen.exe (PID: 2616)
- ngen.exe (PID: 1268)
- ngen.exe (PID: 1844)
- ngen.exe (PID: 3028)
- ngen.exe (PID: 284)
- ngen.exe (PID: 2332)
- ngen.exe (PID: 3468)
- ngen.exe (PID: 3176)
- ngen.exe (PID: 1188)
- ngen.exe (PID: 2720)
- ngen.exe (PID: 2644)
- ngen.exe (PID: 3444)
- ngen.exe (PID: 2464)
- mscorsvw.exe (PID: 308)
- ngen.exe (PID: 2064)
- ngen.exe (PID: 1968)
- ngen.exe (PID: 2396)
- ngen.exe (PID: 1072)
- ngen.exe (PID: 4028)
- ngen.exe (PID: 3840)
- ngen.exe (PID: 2328)
- ngen.exe (PID: 2536)
- ngen.exe (PID: 3488)
- ngen.exe (PID: 2988)
- ngen.exe (PID: 1868)
- ngen.exe (PID: 3208)
- ngen.exe (PID: 3188)
- ngen.exe (PID: 2268)
- ngen.exe (PID: 2620)
- ngen.exe (PID: 2520)
- ngen.exe (PID: 1440)
- ngen.exe (PID: 2748)
- ngen.exe (PID: 2904)
- ngen.exe (PID: 3176)
- ngen.exe (PID: 876)
- ngen.exe (PID: 3892)
- ngen.exe (PID: 3272)
- ngen.exe (PID: 2688)
- ngen.exe (PID: 612)
- ngen.exe (PID: 3704)
- ngen.exe (PID: 504)
- ngen.exe (PID: 560)
- ngen.exe (PID: 2652)
- ngen.exe (PID: 2452)
- ngen.exe (PID: 2704)
- ngen.exe (PID: 2876)
- ngen.exe (PID: 3096)
- ngen.exe (PID: 2572)
- ngen.exe (PID: 352)
- ngen.exe (PID: 2540)
- ngen.exe (PID: 4012)
- ngen.exe (PID: 1004)
- ngen.exe (PID: 1996)
- ngen.exe (PID: 1652)
- ngen.exe (PID: 3540)
- ngen.exe (PID: 2144)
- ngen.exe (PID: 3876)
- ngen.exe (PID: 4036)
- ngen.exe (PID: 2784)
- ngen.exe (PID: 900)
- ngen.exe (PID: 2768)
- ngen.exe (PID: 1104)
- ngen.exe (PID: 1868)
- ngen.exe (PID: 3332)
- ngen.exe (PID: 2948)
- ngen.exe (PID: 3588)
- ngen.exe (PID: 3532)
- ngen.exe (PID: 2688)
- ngen.exe (PID: 4036)
- ngen.exe (PID: 2256)
- ngen.exe (PID: 2772)
- ngen.exe (PID: 3508)
- aspnet_regiis.exe (PID: 4012)
- ngen.exe (PID: 1516)
- ServiceModelReg.exe (PID: 3024)
SUSPICIOUS
Reads the computer name
- Discord Rat Virus.exe (PID: 4044)
- Setup.exe (PID: 3884)
- ngen.exe (PID: 2472)
- ngen.exe (PID: 2556)
- ngen.exe (PID: 3188)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 1312)
- ngen.exe (PID: 2132)
- mscorsvw.exe (PID: 336)
- ngen.exe (PID: 3492)
- mscorsvw.exe (PID: 3116)
- ngen.exe (PID: 2784)
- ngen.exe (PID: 3044)
- ngen.exe (PID: 408)
- ngen.exe (PID: 2620)
- ngen.exe (PID: 2328)
- ngen.exe (PID: 2220)
- ngen.exe (PID: 2920)
- ngen.exe (PID: 1268)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 508)
- ngen.exe (PID: 1252)
- ngen.exe (PID: 3672)
- ngen.exe (PID: 2232)
- ngen.exe (PID: 3536)
- ngen.exe (PID: 2736)
- ngen.exe (PID: 3320)
- ngen.exe (PID: 3052)
- ngen.exe (PID: 3624)
- ngen.exe (PID: 2360)
- ngen.exe (PID: 1104)
- ngen.exe (PID: 2584)
- ngen.exe (PID: 3760)
- mscorsvw.exe (PID: 4016)
- mscorsvw.exe (PID: 2948)
- ngen.exe (PID: 2688)
- mscorsvw.exe (PID: 3176)
- ngen.exe (PID: 2196)
- ngen.exe (PID: 4024)
- ngen.exe (PID: 2380)
- ngen.exe (PID: 3160)
- ngen.exe (PID: 2792)
- ngen.exe (PID: 3444)
- ngen.exe (PID: 2284)
- ngen.exe (PID: 3704)
- mscorsvw.exe (PID: 2092)
- ngen.exe (PID: 504)
- ngen.exe (PID: 2884)
- mscorsvw.exe (PID: 2700)
- ngen.exe (PID: 1300)
- mscorsvw.exe (PID: 2688)
- ngen.exe (PID: 3032)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 3788)
- ngen.exe (PID: 2396)
- mscorsvw.exe (PID: 352)
- ngen.exe (PID: 2068)
- ngen.exe (PID: 1140)
- mscorsvw.exe (PID: 3420)
- mscorsvw.exe (PID: 3428)
- ngen.exe (PID: 3640)
- ngen.exe (PID: 3896)
- ngen.exe (PID: 3152)
- ngen.exe (PID: 2816)
- ngen.exe (PID: 1276)
- ngen.exe (PID: 568)
- ngen.exe (PID: 3276)
- ngen.exe (PID: 868)
- ngen.exe (PID: 3892)
- ngen.exe (PID: 3896)
- ngen.exe (PID: 3484)
- mscorsvw.exe (PID: 3132)
- ngen.exe (PID: 2128)
- mscorsvw.exe (PID: 3720)
- mscorsvw.exe (PID: 2676)
- ngen.exe (PID: 3008)
- ngen.exe (PID: 3180)
- ngen.exe (PID: 408)
- mscorsvw.exe (PID: 2380)
- ngen.exe (PID: 2396)
- mscorsvw.exe (PID: 2488)
- ngen.exe (PID: 2380)
- ngen.exe (PID: 3552)
- ngen.exe (PID: 3868)
- ngen.exe (PID: 3212)
- ngen.exe (PID: 2256)
- ngen.exe (PID: 784)
- ngen.exe (PID: 3024)
- ngen.exe (PID: 2396)
- ngen.exe (PID: 2000)
- mscorsvw.exe (PID: 2312)
- mscorsvw.exe (PID: 308)
- mscorsvw.exe (PID: 2464)
- ngen.exe (PID: 1844)
- ngen.exe (PID: 3028)
- ngen.exe (PID: 284)
- ngen.exe (PID: 1268)
- ngen.exe (PID: 3468)
- mscorsvw.exe (PID: 568)
- ngen.exe (PID: 2616)
- ngen.exe (PID: 2332)
- mscorsvw.exe (PID: 3868)
- ngen.exe (PID: 1188)
- mscorsvw.exe (PID: 4008)
- ngen.exe (PID: 2720)
- ngen.exe (PID: 3416)
- ngen.exe (PID: 2644)
- mscorsvw.exe (PID: 2652)
- ngen.exe (PID: 3176)
- mscorsvw.exe (PID: 1652)
- mscorsvw.exe (PID: 3672)
- ngen.exe (PID: 1968)
- mscorsvw.exe (PID: 420)
- ngen.exe (PID: 3444)
- ngen.exe (PID: 2464)
- mscorsvw.exe (PID: 3300)
- ngen.exe (PID: 2064)
- mscorsvw.exe (PID: 1964)
- ngen.exe (PID: 2904)
- ngen.exe (PID: 3176)
- mscorsvw.exe (PID: 2508)
- ngen.exe (PID: 1072)
- ngen.exe (PID: 876)
- ngen.exe (PID: 2328)
- mscorsvw.exe (PID: 756)
- ngen.exe (PID: 2536)
- ngen.exe (PID: 3892)
- ngen.exe (PID: 3488)
- ngen.exe (PID: 2988)
- mscorsvw.exe (PID: 4008)
- ngen.exe (PID: 3840)
- ngen.exe (PID: 3208)
- ngen.exe (PID: 4028)
- ngen.exe (PID: 1844)
- mscorsvw.exe (PID: 3304)
- ngen.exe (PID: 2268)
- ngen.exe (PID: 1868)
- mscorsvw.exe (PID: 2952)
- mscorsvw.exe (PID: 1092)
- ngen.exe (PID: 2620)
- ngen.exe (PID: 1440)
- ngen.exe (PID: 3188)
- ngen.exe (PID: 2520)
- ngen.exe (PID: 3272)
- ngen.exe (PID: 2688)
- ngen.exe (PID: 1996)
- ngen.exe (PID: 2748)
- ngen.exe (PID: 1004)
- ngen.exe (PID: 2704)
- ngen.exe (PID: 1652)
- ngen.exe (PID: 3704)
- ngen.exe (PID: 560)
- ngen.exe (PID: 504)
- mscorsvw.exe (PID: 3956)
- ngen.exe (PID: 612)
- ngen.exe (PID: 2876)
- ngen.exe (PID: 2652)
- ngen.exe (PID: 2072)
- ngen.exe (PID: 352)
- ngen.exe (PID: 2572)
- ngen.exe (PID: 2540)
- ngen.exe (PID: 4012)
- ngen.exe (PID: 3096)
- ngen.exe (PID: 2688)
- ngen.exe (PID: 3876)
- ngen.exe (PID: 3540)
- ngen.exe (PID: 3532)
- ngen.exe (PID: 4036)
- mscorsvw.exe (PID: 1388)
- mscorsvw.exe (PID: 4028)
- ngen.exe (PID: 2772)
- mscorsvw.exe (PID: 1428)
- ngen.exe (PID: 2256)
- ngen.exe (PID: 2768)
- ngen.exe (PID: 3508)
- ngen.exe (PID: 2784)
- ngen.exe (PID: 900)
- mscorsvw.exe (PID: 3412)
- mscorsvw.exe (PID: 2772)
- ngen.exe (PID: 1104)
- mscorsvw.exe (PID: 2256)
- ngen.exe (PID: 2452)
- ngen.exe (PID: 1868)
- mscorsvw.exe (PID: 2376)
- ngen.exe (PID: 3332)
- ngen.exe (PID: 4036)
- mscorsvw.exe (PID: 4092)
- mscorsvw.exe (PID: 1428)
- ngen.exe (PID: 2144)
- ngen.exe (PID: 3588)
- ngen.exe (PID: 1516)
- mscorsvw.exe (PID: 3284)
- ngen.exe (PID: 2948)
- mscorsvw.exe (PID: 464)
- ServiceModelReg.exe (PID: 3024)
- mofcomp.exe (PID: 2668)
- aspnet_regiis.exe (PID: 4012)
- mofcomp.exe (PID: 4052)
- ngen.exe (PID: 3688)
Checks supported languages
- Discord Rat Virus.exe (PID: 4044)
- Setup.exe (PID: 3884)
- ngen.exe (PID: 2556)
- ngen.exe (PID: 2472)
- ngen.exe (PID: 3188)
- ngen.exe (PID: 1312)
- ngen.exe (PID: 3716)
- mscorsvw.exe (PID: 336)
- ngen.exe (PID: 2132)
- ngen.exe (PID: 3492)
- mscorsvw.exe (PID: 3116)
- ngen.exe (PID: 2784)
- ngen.exe (PID: 3044)
- ngen.exe (PID: 2328)
- ngen.exe (PID: 2220)
- ngen.exe (PID: 2920)
- ngen.exe (PID: 1268)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 3672)
- ngen.exe (PID: 2232)
- ngen.exe (PID: 508)
- ngen.exe (PID: 1252)
- ngen.exe (PID: 2736)
- ngen.exe (PID: 3536)
- ngen.exe (PID: 3320)
- ngen.exe (PID: 3052)
- ngen.exe (PID: 3624)
- ngen.exe (PID: 1104)
- ngen.exe (PID: 2360)
- mscorsvw.exe (PID: 4016)
- ngen.exe (PID: 2584)
- ngen.exe (PID: 3760)
- mscorsvw.exe (PID: 2948)
- ngen.exe (PID: 2688)
- mscorsvw.exe (PID: 3176)
- ngen.exe (PID: 3160)
- ngen.exe (PID: 4024)
- ngen.exe (PID: 2380)
- ngen.exe (PID: 504)
- ngen.exe (PID: 2620)
- ngen.exe (PID: 408)
- ngen.exe (PID: 2792)
- ngen.exe (PID: 2196)
- ngen.exe (PID: 1844)
- ngen.exe (PID: 2284)
- ngen.exe (PID: 3704)
- mscorsvw.exe (PID: 2092)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 3444)
- ngen.exe (PID: 2884)
- ngen.exe (PID: 1300)
- mscorsvw.exe (PID: 2700)
- ngen.exe (PID: 3032)
- mscorsvw.exe (PID: 2688)
- mscorsvw.exe (PID: 352)
- mscorsvw.exe (PID: 3420)
- ngen.exe (PID: 2396)
- ngen.exe (PID: 1140)
- ngen.exe (PID: 3788)
- ngen.exe (PID: 2068)
- mscorsvw.exe (PID: 3428)
- ngen.exe (PID: 3896)
- ngen.exe (PID: 3640)
- ngen.exe (PID: 868)
- ngen.exe (PID: 3152)
- ngen.exe (PID: 2816)
- ngen.exe (PID: 1276)
- ngen.exe (PID: 568)
- ngen.exe (PID: 3276)
- ngen.exe (PID: 3892)
- ngen.exe (PID: 3484)
- mscorsvw.exe (PID: 3132)
- ngen.exe (PID: 2128)
- mscorsvw.exe (PID: 2380)
- mscorsvw.exe (PID: 3720)
- ngen.exe (PID: 3896)
- mscorsvw.exe (PID: 2676)
- ngen.exe (PID: 3180)
- ngen.exe (PID: 408)
- ngen.exe (PID: 3008)
- mscorsvw.exe (PID: 2488)
- ngen.exe (PID: 2380)
- ngen.exe (PID: 3552)
- ngen.exe (PID: 2072)
- ngen.exe (PID: 2396)
- ngen.exe (PID: 3212)
- ngen.exe (PID: 2256)
- ngen.exe (PID: 784)
- ngen.exe (PID: 3868)
- ngen.exe (PID: 3024)
- ngen.exe (PID: 2000)
- ngen.exe (PID: 2396)
- mscorsvw.exe (PID: 2312)
- mscorsvw.exe (PID: 308)
- mscorsvw.exe (PID: 2464)
- ngen.exe (PID: 3028)
- ngen.exe (PID: 284)
- ngen.exe (PID: 1268)
- ngen.exe (PID: 1844)
- ngen.exe (PID: 3468)
- ngen.exe (PID: 2616)
- mscorsvw.exe (PID: 568)
- ngen.exe (PID: 3416)
- ngen.exe (PID: 2332)
- mscorsvw.exe (PID: 3868)
- ngen.exe (PID: 1188)
- mscorsvw.exe (PID: 4008)
- ngen.exe (PID: 2720)
- mscorsvw.exe (PID: 1652)
- ngen.exe (PID: 2644)
- mscorsvw.exe (PID: 2652)
- ngen.exe (PID: 3176)
- ngen.exe (PID: 3444)
- ngen.exe (PID: 2464)
- mscorsvw.exe (PID: 3672)
- ngen.exe (PID: 1968)
- mscorsvw.exe (PID: 420)
- ngen.exe (PID: 2904)
- mscorsvw.exe (PID: 3300)
- ngen.exe (PID: 2064)
- mscorsvw.exe (PID: 1964)
- ngen.exe (PID: 3176)
- ngen.exe (PID: 1072)
- ngen.exe (PID: 876)
- ngen.exe (PID: 2328)
- mscorsvw.exe (PID: 2508)
- ngen.exe (PID: 2988)
- ngen.exe (PID: 2536)
- ngen.exe (PID: 3488)
- mscorsvw.exe (PID: 756)
- ngen.exe (PID: 3892)
- ngen.exe (PID: 3840)
- mscorsvw.exe (PID: 4008)
- ngen.exe (PID: 3208)
- ngen.exe (PID: 4028)
- mscorsvw.exe (PID: 2952)
- mscorsvw.exe (PID: 3304)
- ngen.exe (PID: 1868)
- ngen.exe (PID: 3188)
- ngen.exe (PID: 2268)
- mscorsvw.exe (PID: 1092)
- ngen.exe (PID: 2620)
- ngen.exe (PID: 1440)
- ngen.exe (PID: 2748)
- ngen.exe (PID: 2520)
- ngen.exe (PID: 3272)
- ngen.exe (PID: 2688)
- ngen.exe (PID: 1996)
- ngen.exe (PID: 3704)
- ngen.exe (PID: 1004)
- ngen.exe (PID: 1652)
- ngen.exe (PID: 2704)
- ngen.exe (PID: 2652)
- ngen.exe (PID: 560)
- ngen.exe (PID: 2452)
- ngen.exe (PID: 504)
- ngen.exe (PID: 612)
- ngen.exe (PID: 2876)
- mscorsvw.exe (PID: 3956)
- ngen.exe (PID: 2540)
- ngen.exe (PID: 352)
- ngen.exe (PID: 4012)
- ngen.exe (PID: 3096)
- ngen.exe (PID: 2572)
- ngen.exe (PID: 3876)
- ngen.exe (PID: 3540)
- mscorsvw.exe (PID: 1428)
- ngen.exe (PID: 3532)
- ngen.exe (PID: 2688)
- ngen.exe (PID: 4036)
- mscorsvw.exe (PID: 4028)
- ngen.exe (PID: 2772)
- mscorsvw.exe (PID: 1388)
- ngen.exe (PID: 2256)
- ngen.exe (PID: 3508)
- ngen.exe (PID: 2784)
- ngen.exe (PID: 900)
- mscorsvw.exe (PID: 3412)
- ngen.exe (PID: 2768)
- ngen.exe (PID: 1868)
- mscorsvw.exe (PID: 2772)
- mscorsvw.exe (PID: 2376)
- ngen.exe (PID: 1104)
- mscorsvw.exe (PID: 2256)
- ngen.exe (PID: 2144)
- mscorsvw.exe (PID: 4092)
- mscorsvw.exe (PID: 1428)
- ngen.exe (PID: 3332)
- ngen.exe (PID: 4036)
- mscorsvw.exe (PID: 3284)
- mscorsvw.exe (PID: 464)
- ngen.exe (PID: 3588)
- ngen.exe (PID: 2948)
- ngen.exe (PID: 1516)
- ServiceModelReg.exe (PID: 3024)
- mofcomp.exe (PID: 4052)
- aspnet_regiis.exe (PID: 4012)
- mofcomp.exe (PID: 2668)
- ngen.exe (PID: 3688)
Reads CPU info
- Setup.exe (PID: 3884)
Creates files in the Windows directory
- Setup.exe (PID: 3884)
- ngen.exe (PID: 2556)
- ngen.exe (PID: 2472)
- ngen.exe (PID: 3188)
- ngen.exe (PID: 1312)
- ngen.exe (PID: 3716)
- mscorsvw.exe (PID: 336)
- ngen.exe (PID: 2132)
- ngen.exe (PID: 3492)
- ngen.exe (PID: 2784)
- mscorsvw.exe (PID: 3116)
- ngen.exe (PID: 3044)
- ngen.exe (PID: 408)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 2220)
- ngen.exe (PID: 2328)
- ngen.exe (PID: 2920)
- ngen.exe (PID: 1268)
- ngen.exe (PID: 508)
- ngen.exe (PID: 3672)
- ngen.exe (PID: 1252)
- ngen.exe (PID: 2232)
- ngen.exe (PID: 3052)
- ngen.exe (PID: 3536)
- ngen.exe (PID: 2736)
- ngen.exe (PID: 3320)
- ngen.exe (PID: 3624)
- ngen.exe (PID: 3760)
- ngen.exe (PID: 2360)
- mscorsvw.exe (PID: 4016)
- ngen.exe (PID: 2584)
- ngen.exe (PID: 1104)
- ngen.exe (PID: 2688)
- mscorsvw.exe (PID: 3176)
- ngen.exe (PID: 3160)
- mscorsvw.exe (PID: 2948)
- ngen.exe (PID: 4024)
- ngen.exe (PID: 2380)
- ngen.exe (PID: 504)
- ngen.exe (PID: 2620)
- ngen.exe (PID: 2792)
- ngen.exe (PID: 2196)
- ngen.exe (PID: 3444)
- ngen.exe (PID: 1844)
- ngen.exe (PID: 3704)
- ngen.exe (PID: 2284)
- mscorsvw.exe (PID: 2092)
- ngen.exe (PID: 3716)
- ngen.exe (PID: 2884)
- ngen.exe (PID: 1300)
- mscorsvw.exe (PID: 2700)
- ngen.exe (PID: 3032)
- mscorsvw.exe (PID: 2688)
- mscorsvw.exe (PID: 352)
- ngen.exe (PID: 2396)
- ngen.exe (PID: 2068)
- ngen.exe (PID: 1140)
- mscorsvw.exe (PID: 3420)
- ngen.exe (PID: 3788)
- ngen.exe (PID: 3152)
- ngen.exe (PID: 3640)
- mscorsvw.exe (PID: 3428)
- ngen.exe (PID: 3896)
- ngen.exe (PID: 868)
- ngen.exe (PID: 2816)
- ngen.exe (PID: 1276)
- ngen.exe (PID: 568)
- ngen.exe (PID: 3276)
- ngen.exe (PID: 3892)
- ngen.exe (PID: 3484)
- mscorsvw.exe (PID: 3132)
- ngen.exe (PID: 2128)
- mscorsvw.exe (PID: 3720)
- ngen.exe (PID: 3896)
- ngen.exe (PID: 3008)
- ngen.exe (PID: 408)
- ngen.exe (PID: 3180)
- mscorsvw.exe (PID: 2676)
- mscorsvw.exe (PID: 2380)
- ngen.exe (PID: 2380)
- mscorsvw.exe (PID: 2488)
- ngen.exe (PID: 3552)
- ngen.exe (PID: 2396)
- ngen.exe (PID: 3212)
- ngen.exe (PID: 3868)
- ngen.exe (PID: 3024)
- ngen.exe (PID: 784)
- mscorsvw.exe (PID: 308)
- ngen.exe (PID: 2000)
- ngen.exe (PID: 2396)
- mscorsvw.exe (PID: 2312)
- ngen.exe (PID: 2256)
- ngen.exe (PID: 1844)
- ngen.exe (PID: 3028)
- ngen.exe (PID: 1268)
- mscorsvw.exe (PID: 2464)
- ngen.exe (PID: 3468)
- ngen.exe (PID: 2332)
- ngen.exe (PID: 2616)
- mscorsvw.exe (PID: 568)
- ngen.exe (PID: 284)
- ngen.exe (PID: 1188)
- mscorsvw.exe (PID: 4008)
- ngen.exe (PID: 2720)
- ngen.exe (PID: 3416)
- mscorsvw.exe (PID: 3868)
- mscorsvw.exe (PID: 1652)
- mscorsvw.exe (PID: 2652)
- ngen.exe (PID: 3176)
- ngen.exe (PID: 2644)
- mscorsvw.exe (PID: 3672)
- ngen.exe (PID: 2464)
- ngen.exe (PID: 1968)
- mscorsvw.exe (PID: 420)
- ngen.exe (PID: 3444)
- ngen.exe (PID: 2904)
- mscorsvw.exe (PID: 1964)
- ngen.exe (PID: 2064)
- mscorsvw.exe (PID: 3300)
- mscorsvw.exe (PID: 2508)
- ngen.exe (PID: 1072)
- ngen.exe (PID: 876)
- ngen.exe (PID: 3176)
- ngen.exe (PID: 3892)
- ngen.exe (PID: 3488)
- ngen.exe (PID: 2988)
- ngen.exe (PID: 2328)
- ngen.exe (PID: 2536)
- mscorsvw.exe (PID: 756)
- ngen.exe (PID: 3208)
- mscorsvw.exe (PID: 4008)
- ngen.exe (PID: 4028)
- ngen.exe (PID: 3840)
- ngen.exe (PID: 1868)
- ngen.exe (PID: 3188)
- mscorsvw.exe (PID: 3304)
- mscorsvw.exe (PID: 2952)
- ngen.exe (PID: 2268)
- ngen.exe (PID: 2520)
- ngen.exe (PID: 2620)
- ngen.exe (PID: 1440)
- mscorsvw.exe (PID: 1092)
- ngen.exe (PID: 2688)
- ngen.exe (PID: 1004)
- ngen.exe (PID: 3272)
- ngen.exe (PID: 1996)
- ngen.exe (PID: 2748)
- ngen.exe (PID: 2704)
- ngen.exe (PID: 560)
- ngen.exe (PID: 2452)
- ngen.exe (PID: 1652)
- ngen.exe (PID: 3704)
- ngen.exe (PID: 504)
- ngen.exe (PID: 612)
- mscorsvw.exe (PID: 3956)
- ngen.exe (PID: 2876)
- ngen.exe (PID: 2652)
- ngen.exe (PID: 2072)
- ngen.exe (PID: 3096)
- ngen.exe (PID: 2572)
- ngen.exe (PID: 352)
- ngen.exe (PID: 4012)
- ngen.exe (PID: 2540)
- ngen.exe (PID: 2688)
- ngen.exe (PID: 3876)
- ngen.exe (PID: 3540)
- ngen.exe (PID: 3532)
- ngen.exe (PID: 2256)
- mscorsvw.exe (PID: 4028)
- ngen.exe (PID: 2772)
- mscorsvw.exe (PID: 1388)
- mscorsvw.exe (PID: 1428)
- ngen.exe (PID: 3508)
- ngen.exe (PID: 2784)
- ngen.exe (PID: 900)
- mscorsvw.exe (PID: 3412)
- ngen.exe (PID: 2768)
- mscorsvw.exe (PID: 2376)
- mscorsvw.exe (PID: 2256)
- ngen.exe (PID: 1868)
- mscorsvw.exe (PID: 2772)
- ngen.exe (PID: 1104)
- ngen.exe (PID: 3332)
- ngen.exe (PID: 4036)
- mscorsvw.exe (PID: 4092)
- ngen.exe (PID: 2144)
- mscorsvw.exe (PID: 1428)
- ngen.exe (PID: 2948)
- mscorsvw.exe (PID: 464)
- ngen.exe (PID: 3588)
- mscorsvw.exe (PID: 3284)
- ngen.exe (PID: 1516)
- ngen.exe (PID: 4036)
- aspnet_regiis.exe (PID: 4012)
- msiexec.exe (PID: 1628)
- ngen.exe (PID: 3688)
Reads Environment values
- Setup.exe (PID: 3884)
Executed via COM
- DllHost.exe (PID: 2552)
- DllHost.exe (PID: 3140)
Searches for installed software
- DllHost.exe (PID: 3140)
- msiexec.exe (PID: 1628)
Executed as Windows Service
- msiexec.exe (PID: 1628)
Reads the Windows organization settings
- msiexec.exe (PID: 1628)
Application launched itself
- msiexec.exe (PID: 1628)
Reads Windows owner or organization settings
- msiexec.exe (PID: 1628)
Removes files from Windows directory
- Setup.exe (PID: 3884)
- mscorsvw.exe (PID: 336)
- mscorsvw.exe (PID: 3116)
- mscorsvw.exe (PID: 4016)
- mscorsvw.exe (PID: 3176)
- mscorsvw.exe (PID: 2948)
- mscorsvw.exe (PID: 2092)
- mscorsvw.exe (PID: 2700)
- mscorsvw.exe (PID: 2688)
- mscorsvw.exe (PID: 352)
- mscorsvw.exe (PID: 3428)
- mscorsvw.exe (PID: 3420)
- mscorsvw.exe (PID: 3132)
- mscorsvw.exe (PID: 3720)
- mscorsvw.exe (PID: 2676)
- mscorsvw.exe (PID: 2380)
- mscorsvw.exe (PID: 2488)
- mscorsvw.exe (PID: 308)
- mscorsvw.exe (PID: 2464)
- mscorsvw.exe (PID: 2312)
- mscorsvw.exe (PID: 3868)
- mscorsvw.exe (PID: 4008)
- mscorsvw.exe (PID: 2652)
- mscorsvw.exe (PID: 1652)
- mscorsvw.exe (PID: 3672)
- mscorsvw.exe (PID: 1964)
- mscorsvw.exe (PID: 420)
- mscorsvw.exe (PID: 2508)
- mscorsvw.exe (PID: 3300)
- mscorsvw.exe (PID: 756)
- mscorsvw.exe (PID: 4008)
- mscorsvw.exe (PID: 2952)
- mscorsvw.exe (PID: 3304)
- mscorsvw.exe (PID: 1092)
- mscorsvw.exe (PID: 3956)
- mscorsvw.exe (PID: 4028)
- mscorsvw.exe (PID: 1428)
- mscorsvw.exe (PID: 3412)
- mscorsvw.exe (PID: 1388)
- mscorsvw.exe (PID: 2376)
- mscorsvw.exe (PID: 2256)
- mscorsvw.exe (PID: 568)
- mscorsvw.exe (PID: 4092)
- mscorsvw.exe (PID: 1428)
- mscorsvw.exe (PID: 2772)
- mscorsvw.exe (PID: 464)
- mscorsvw.exe (PID: 3284)
- aspnet_regiis.exe (PID: 4012)
- unlodctr.exe (PID: 1428)
- unlodctr.exe (PID: 3916)
- unlodctr.exe (PID: 1004)
- unlodctr.exe (PID: 2580)
- msiexec.exe (PID: 1628)
- unlodctr.exe (PID: 1436)
Drops a file that was compiled in debug mode
- msiexec.exe (PID: 1628)
Executable content was dropped or overwritten
- msiexec.exe (PID: 1628)
Starts SC.EXE for service management
- ServiceModelReg.exe (PID: 3024)
Checks for the .NET to be installed
- msiexec.exe (PID: 1628)
Drops a file with too old compile date
- msiexec.exe (PID: 1628)
INFO
Checks supported languages
- explorer.exe (PID: 2708)
- DllHost.exe (PID: 2552)
- DllHost.exe (PID: 3140)
- msiexec.exe (PID: 1628)
- MsiExec.exe (PID: 3968)
- sc.exe (PID: 3808)
- sc.exe (PID: 3888)
- sc.exe (PID: 1440)
- sc.exe (PID: 2528)
- sc.exe (PID: 304)
- MsiExec.exe (PID: 764)
- sc.exe (PID: 896)
- wevtutil.exe (PID: 1148)
- unlodctr.exe (PID: 3592)
- sc.exe (PID: 2764)
- sc.exe (PID: 352)
- unlodctr.exe (PID: 3768)
- unlodctr.exe (PID: 1428)
- unlodctr.exe (PID: 1004)
- unlodctr.exe (PID: 3916)
- unlodctr.exe (PID: 2580)
- unlodctr.exe (PID: 1436)
- unlodctr.exe (PID: 2680)
Manual execution by user
- explorer.exe (PID: 2708)
Reads the computer name
- explorer.exe (PID: 2708)
- DllHost.exe (PID: 2552)
- DllHost.exe (PID: 3140)
- MsiExec.exe (PID: 3968)
- msiexec.exe (PID: 1628)
- sc.exe (PID: 3888)
- sc.exe (PID: 1440)
- sc.exe (PID: 3808)
- sc.exe (PID: 304)
- sc.exe (PID: 2528)
- MsiExec.exe (PID: 764)
- sc.exe (PID: 352)
- sc.exe (PID: 896)
- unlodctr.exe (PID: 3592)
- sc.exe (PID: 2764)
- wevtutil.exe (PID: 1148)
- unlodctr.exe (PID: 1428)
- unlodctr.exe (PID: 3916)
- unlodctr.exe (PID: 3768)
- unlodctr.exe (PID: 1004)
- unlodctr.exe (PID: 2580)
- unlodctr.exe (PID: 1436)
Checks Windows Trust Settings
- Setup.exe (PID: 3884)
Reads settings of System Certificates
- Setup.exe (PID: 3884)
Dropped object may contain Bitcoin addresses
- msiexec.exe (PID: 1628)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Generic CIL Executable (.NET, Mono, etc.) (72.2) |
|---|---|---|
| .scr | | | Windows screen saver (12.9) |
| .dll | | | Win32 Dynamic Link Library (generic) (6.4) |
| .exe | | | Win32 Executable (generic) (4.4) |
| .exe | | | Generic Win/DOS Executable (1.9) |
EXIF
EXE
| AssemblyVersion: | 1.0.0.0 |
|---|---|
| ProductVersion: | 1.0.0.0 |
| ProductName: | Discord Rat Virus |
| OriginalFileName: | Discord Rat Virus.exe |
| LegalTrademarks: | - |
| LegalCopyright: | Copyright © 2021 |
| InternalName: | Discord Rat Virus.exe |
| FileVersion: | 1.0.0.0 |
| FileDescription: | Discord Rat Virus |
| CompanyName: | - |
| Comments: | - |
| CharacterSet: | Unicode |
| LanguageCode: | Neutral |
| FileSubtype: | - |
| ObjectFileType: | Executable application |
| FileOS: | Win32 |
| FileFlags: | (none) |
| FileFlagsMask: | 0x003f |
| ProductVersionNumber: | 1.0.0.0 |
| FileVersionNumber: | 1.0.0.0 |
| Subsystem: | Windows command line |
| SubsystemVersion: | 6 |
| ImageVersion: | - |
| OSVersion: | 4 |
| EntryPoint: | 0x43fa |
| UninitializedDataSize: | - |
| InitializedDataSize: | 2048 |
| CodeSize: | 9216 |
| LinkerVersion: | 48 |
| PEType: | PE32 |
| TimeStamp: | 2067:04:14 11:40:25+02:00 |
| MachineType: | Intel 386 or later, and compatibles |
Summary
| Architecture: | IMAGE_FILE_MACHINE_I386 |
|---|---|
| Subsystem: | IMAGE_SUBSYSTEM_WINDOWS_CUI |
| Compilation Date: | 09-Mar-1931 03:12:09 |
| Debug artifacts: |
|
| Comments: | - |
| CompanyName: | - |
| FileDescription: | Discord Rat Virus |
| FileVersion: | 1.0.0.0 |
| InternalName: | Discord Rat Virus.exe |
| LegalCopyright: | Copyright © 2021 |
| LegalTrademarks: | - |
| OriginalFilename: | Discord Rat Virus.exe |
| ProductName: | Discord Rat Virus |
| ProductVersion: | 1.0.0.0 |
| Assembly Version: | 1.0.0.0 |
DOS Header
| Magic number: | MZ |
|---|---|
| Bytes on last page of file: | 0x0090 |
| Pages in file: | 0x0003 |
| Relocations: | 0x0000 |
| Size of header: | 0x0004 |
| Min extra paragraphs: | 0x0000 |
| Max extra paragraphs: | 0xFFFF |
| Initial SS value: | 0x0000 |
| Initial SP value: | 0x00B8 |
| Checksum: | 0x0000 |
| Initial IP value: | 0x0000 |
| Initial CS value: | 0x0000 |
| Overlay number: | 0x0000 |
| OEM identifier: | 0x0000 |
| OEM information: | 0x0000 |
| Address of NE header: | 0x00000080 |
PE Headers
| Signature: | PE |
|---|---|
| Machine: | IMAGE_FILE_MACHINE_I386 |
| Number of sections: | 3 |
| Time date stamp: | 09-Mar-1931 03:12:09 |
| Pointer to Symbol Table: | 0x00000000 |
| Number of symbols: | 0 |
| Size of Optional Header: | 0x00E0 |
| Characteristics: |
|
Sections
Name | Virtual Address | Virtual Size | Raw Size | Charateristics | Entropy |
|---|---|---|---|---|---|
.text | 0x00002000 | 0x00002400 | 0x00002400 | IMAGE_SCN_CNT_CODE, IMAGE_SCN_MEM_EXECUTE, IMAGE_SCN_MEM_READ | 5.45706 |
.rsrc | 0x00006000 | 0x000005EC | 0x00000600 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_READ | 4.16564 |
.reloc | 0x00008000 | 0x0000000C | 0x00000200 | IMAGE_SCN_CNT_INITIALIZED_DATA, IMAGE_SCN_MEM_DISCARDABLE, IMAGE_SCN_MEM_READ | 0.0815394 |
Resources
Title | Entropy | Size | Codepage | Language | Type |
|---|---|---|---|---|---|
1 | 5.00112 | 490 | UNKNOWN | UNKNOWN | RT_MANIFEST |
Imports
mscoree.dll |
Total processes
436
Monitored processes
222
Malicious processes
55
Suspicious processes
147
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 284 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe uninstall "System.Printing, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" /NoDependencies | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Common Language Runtime native compiler Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 304 | sidtype NetPipeActivator restricted | C:\Windows\system32\sc.exe | — | ServiceModelReg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 308 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 118 -InterruptEvent 0 -NGENProcess 108 -Pipe 114 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 336 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 118 -InterruptEvent 0 -NGENProcess 10c -Pipe 114 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 352 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 118 -InterruptEvent 0 -NGENProcess 108 -Pipe 114 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 352 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe uninstall "System.Web.Entity, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b77a5c561934e089" /NoDependencies | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Common Language Runtime native compiler Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 352 | sidtype NetMsmqActivator restricted | C:\Windows\system32\sc.exe | — | ServiceModelReg.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: A tool to aid in developing services for WindowsNT Exit code: 0 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
| 408 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe uninstall "System.Configuration, Version=4.0.0.0, Culture=neutral, PublicKeyToken=b03f5f7f11d50a3a" /NoDependencies | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Common Language Runtime native compiler Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 408 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe uninstall "System.Activities.DurableInstancing, Version=4.0.0.0, Culture=neutral, PublicKeyToken=31bf3856ad364e35" /NoDependencies | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.exe | — | MsiExec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: Microsoft Common Language Runtime native compiler Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
| 420 | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe -StartupEvent 118 -InterruptEvent 0 -NGENProcess 10c -Pipe 114 -Comment "NGen Worker Process" | C:\Windows\Microsoft.NET\Framework\v4.0.30319\mscorsvw.exe | — | ngen.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: HIGH Description: .NET Runtime Optimization Service Exit code: 0 Version: 4.0.30319.34209 built by: FX452RTMGDR Modules
| |||||||||||||||
Total events
393 769
Read events
387 080
Write events
2 492
Delete events
4 197
Modification events
| (PID) Process: | (2552) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Direct3D\MostRecentApplication |
| Operation: | write | Name: | Name |
Value: DllHost.exe | |||
| (PID) Process: | (2552) DllHost.exe | Key: | HKEY_CURRENT_USER\Software\Microsoft\Windows Photo Viewer\Viewer |
| Operation: | write | Name: | MainWndPos |
Value: 6000000034000000A00400008002000000000000 | |||
| (PID) Process: | (3884) Setup.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\16C\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (1628) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Owner |
Value: 5C060000EDDE30BF0E8FD701 | |||
| (PID) Process: | (1628) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | SessionHash |
Value: 3D0F347B09D32049E3210D125C9BD4A3F27F263695DCC7331F1C418721D2CFD5 | |||
| (PID) Process: | (1628) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | Sequence |
Value: 1 | |||
| (PID) Process: | (1628) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFiles0000 |
Value: C:\Windows\Microsoft.NET\Framework\v4.0.30319\SetupCache\v4.5.51209\Setup.exe | |||
| (PID) Process: | (1628) msiexec.exe | Key: | HKEY_USERS\S-1-5-21-1302019708-1500728564-335382590-1000\Software\Microsoft\RestartManager\Session0000 |
| Operation: | write | Name: | RegFilesHash |
Value: 5F33E85395C8E04FB99FDF179E0BECD77E7E248C9B6FCCC88A9CEA91EBBFE964 | |||
| (PID) Process: | (1628) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\InProgress |
| Operation: | write | Name: | (default) |
Value: C:\Windows\Installer\14d958.ipi | |||
| (PID) Process: | (1628) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Installer\Folders |
| Operation: | write | Name: | C:\Config.Msi\ |
Value: | |||
Executable files
837
Suspicious files
23
Text files
373
Unknown types
107
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 1628 | msiexec.exe | C:\Windows\Installer\MSIE146.tmp | — | |
MD5:— | SHA256:— | |||
| 3884 | Setup.exe | C:\Users\admin\AppData\Local\Temp\Microsoft .NET Framework 4.5.2 Setup_20210812_011226802.html | html | |
MD5:— | SHA256:— | |||
| 3884 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\57C8EDB95DF3F0AD4EE2DC2B8CFD4157 | binary | |
MD5:— | SHA256:— | |||
| 3884 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\696F3DE637E6DE85B458996D49D759AD | binary | |
MD5:— | SHA256:— | |||
| 2556 | ngen.exe | C:\Windows\Microsoft.NET\Framework\v4.0.30319\ngen.log | txt | |
MD5:— | SHA256:— | |||
| 336 | mscorsvw.exe | C:\Windows\assembly\temp\VJVOGMFO5E | — | |
MD5:— | SHA256:— | |||
| 3884 | Setup.exe | C:\Users\admin\AppData\Local\Temp\HFIB536.tmp.html | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
| 3116 | mscorsvw.exe | C:\Windows\assembly\temp\XIANH1F3BN | — | |
MD5:— | SHA256:— | |||
| 3884 | Setup.exe | C:\Users\admin\AppData\LocalLow\Microsoft\CryptnetUrlCache\MetaData\F90F18257CBB4D84216AC1E1F3BB2C76 | binary | |
MD5:— | SHA256:— | |||
| 3884 | Setup.exe | C:\Users\admin\AppData\Local\Temp\HFIC008.tmp.html | text | |
MD5:F3B25701FE362EC84616A93A45CE9998 | SHA256:B3D510EF04275CA8E698E5B3CBB0ECE3949EF9252F0CDC839E9EE347409A2209 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
3
TCP/UDP connections
2
DNS requests
2
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
3884 | Setup.exe | GET | 200 | 205.185.216.42:80 | http://ctldl.windowsupdate.com/msdownload/update/v3/static/trustedr/en/disallowedcertstl.cab?6e742027920331b7 | US | compressed | 4.70 Kb | whitelisted |
3884 | Setup.exe | GET | 200 | 92.123.194.162:80 | http://crl.microsoft.com/pki/crl/products/microsoftrootcert.crl | unknown | der | 767 b | whitelisted |
3884 | Setup.exe | GET | 200 | 92.123.194.162:80 | http://crl.microsoft.com/pki/crl/products/MicrosoftTimeStampPCA.crl | unknown | der | 519 b | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
3884 | Setup.exe | 205.185.216.42:80 | ctldl.windowsupdate.com | Highwinds Network Group, Inc. | US | whitelisted |
3884 | Setup.exe | 92.123.194.162:80 | crl.microsoft.com | Akamai International B.V. | — | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
ctldl.windowsupdate.com |
| whitelisted |
crl.microsoft.com |
| whitelisted |
Threats
Process | Message |
|---|---|
Setup.exe | The requested operation is successful. Changes will not be effective until the system is rebooted.
|