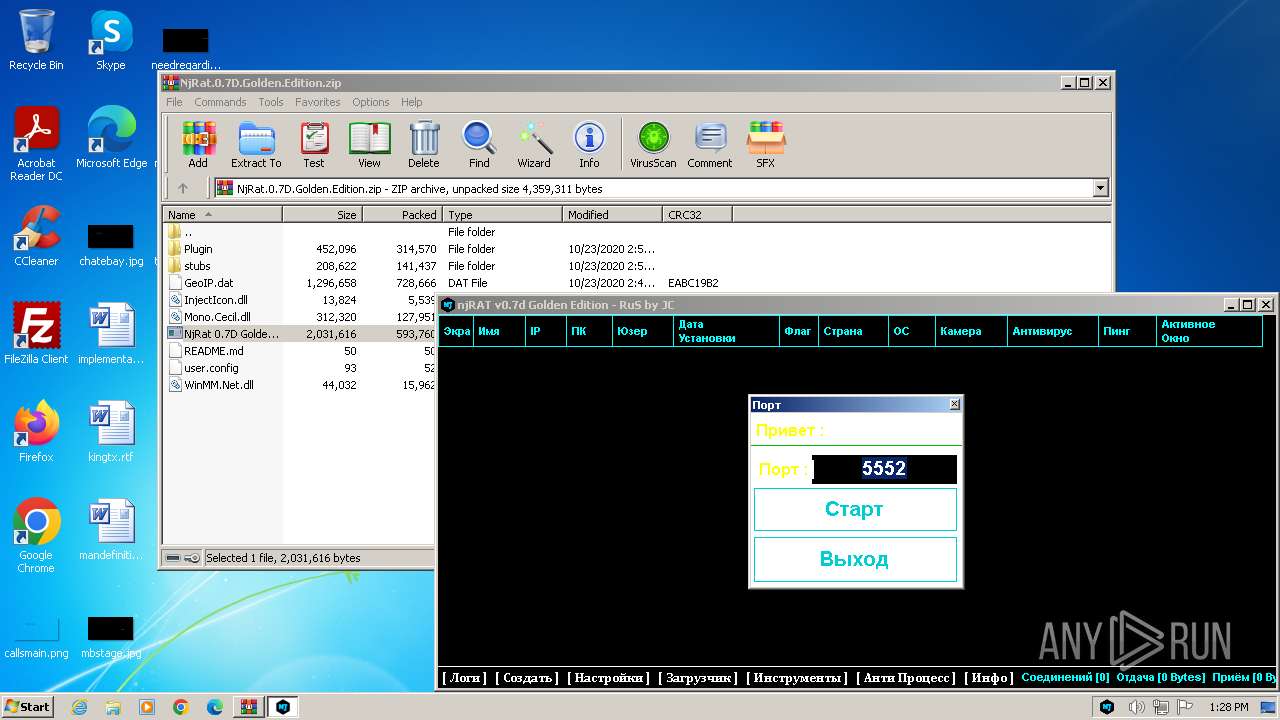
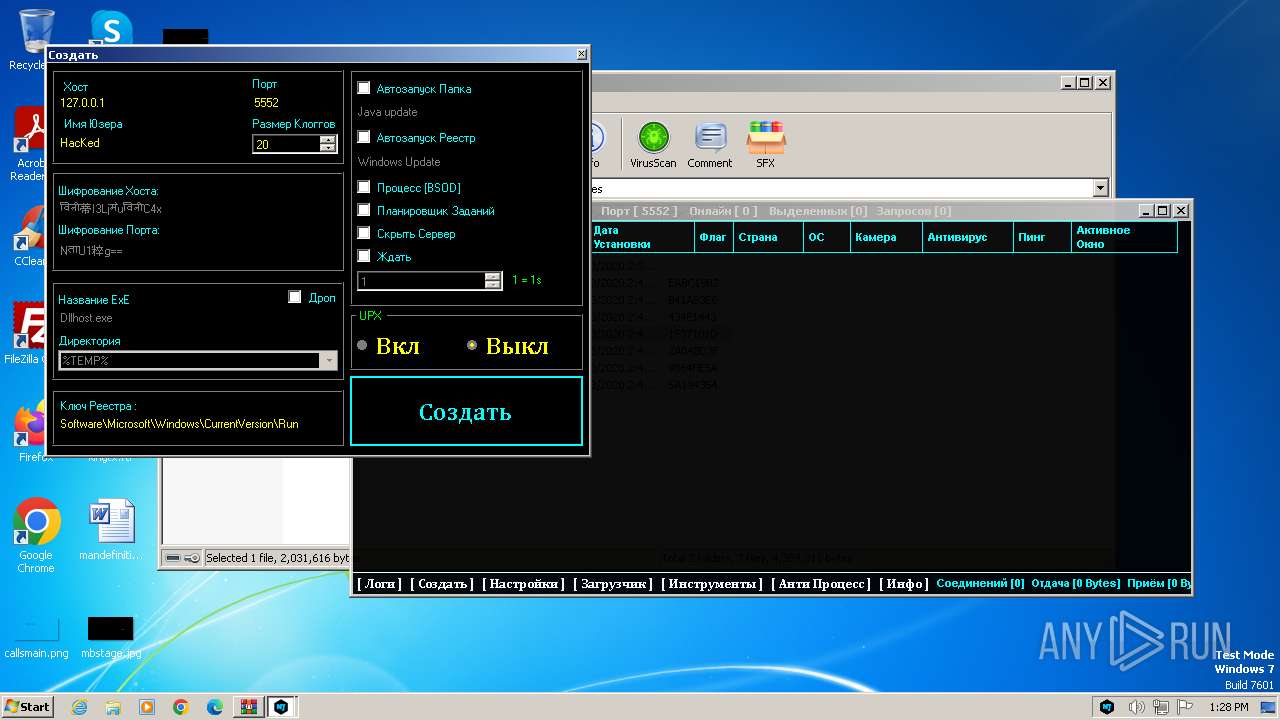
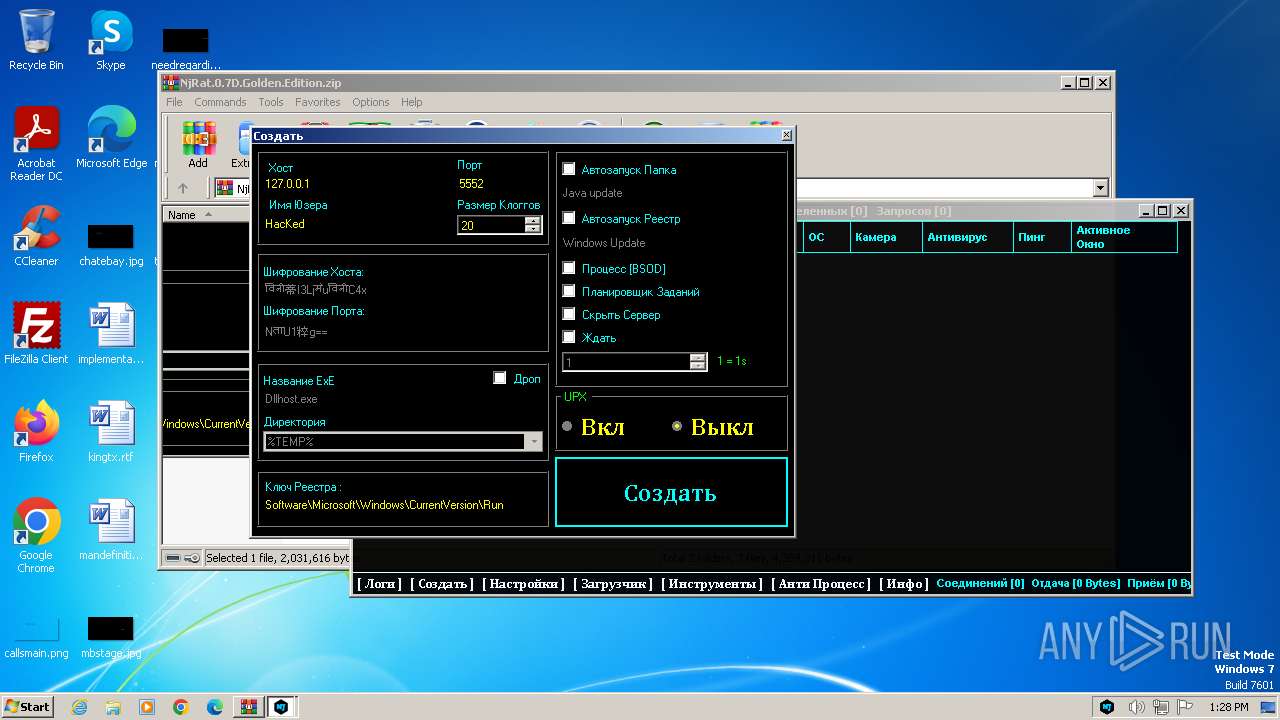
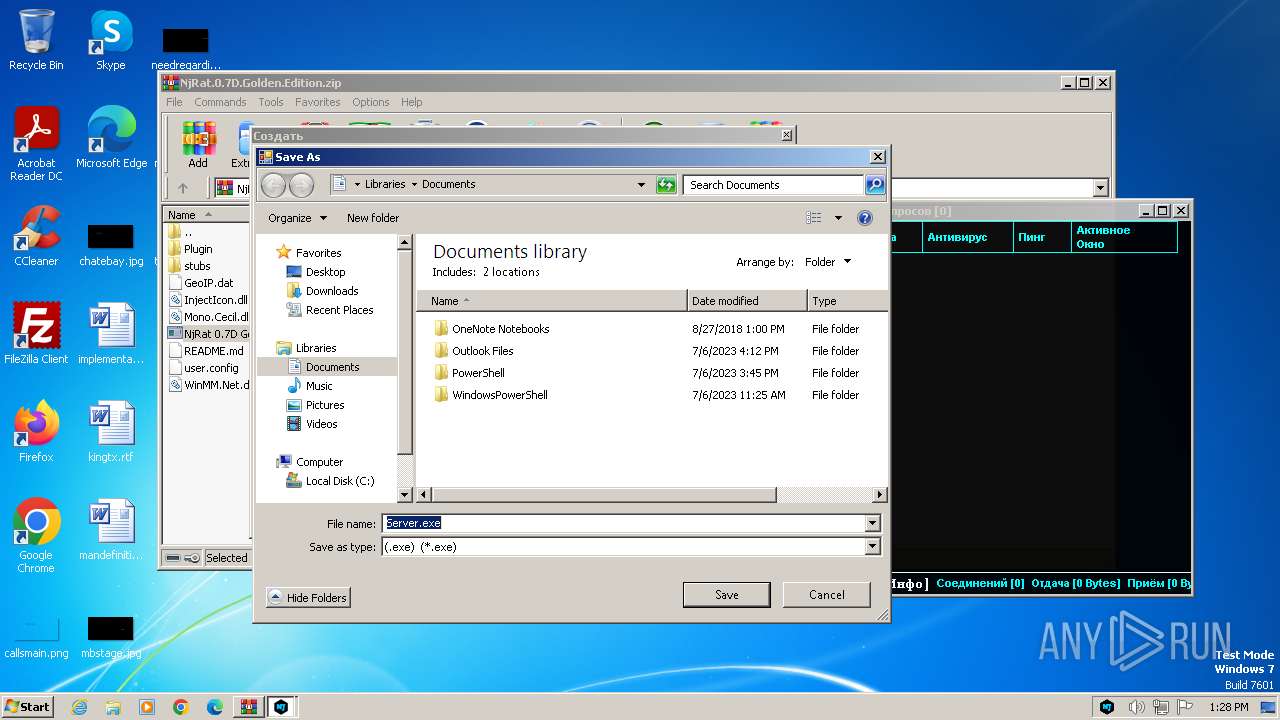
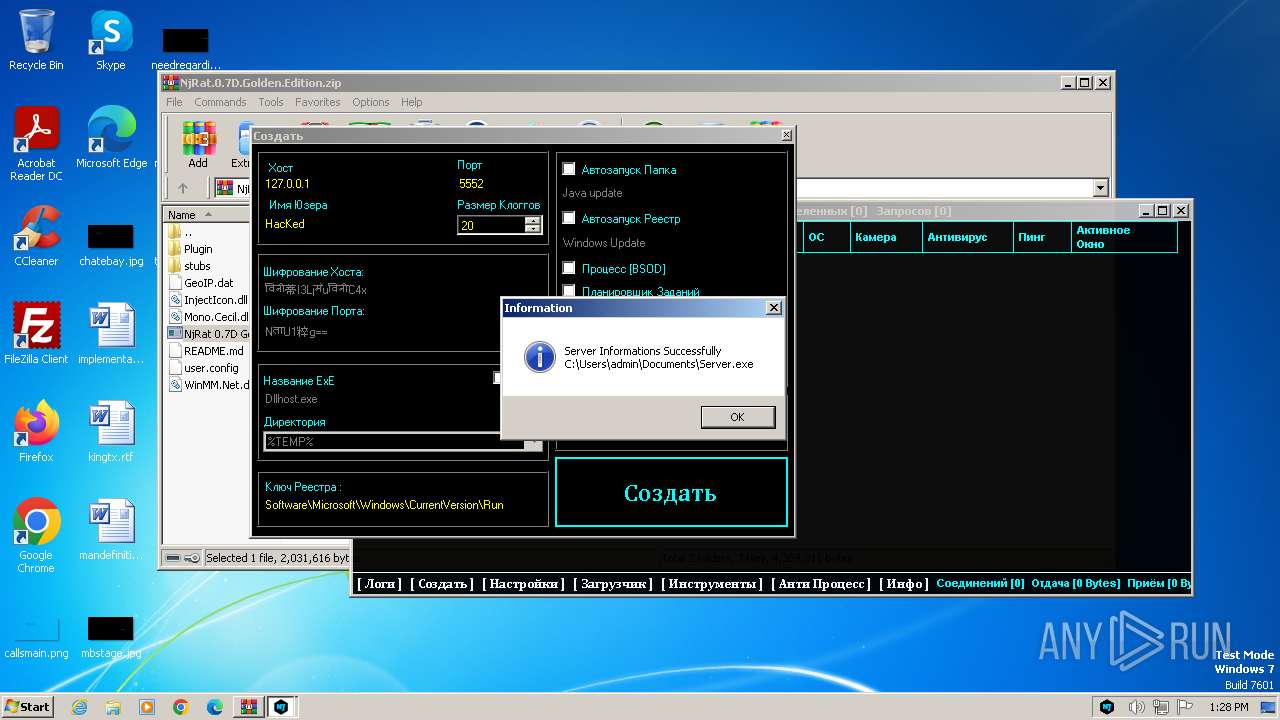
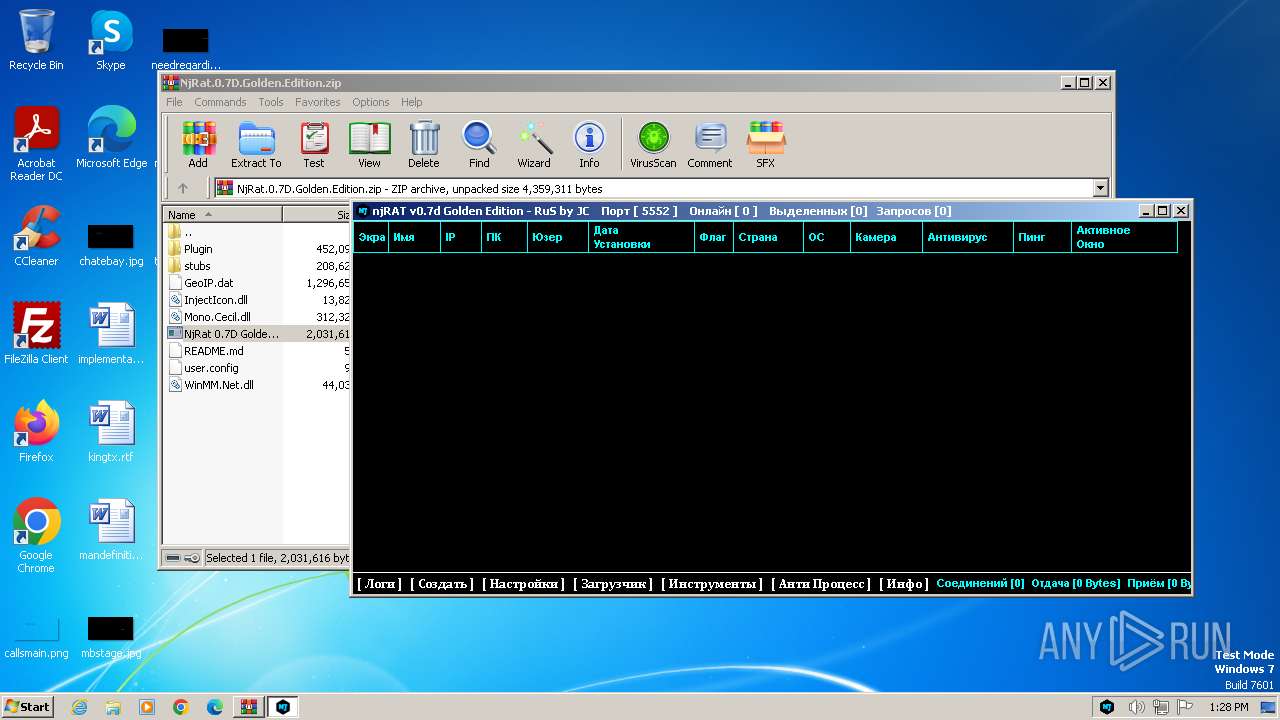
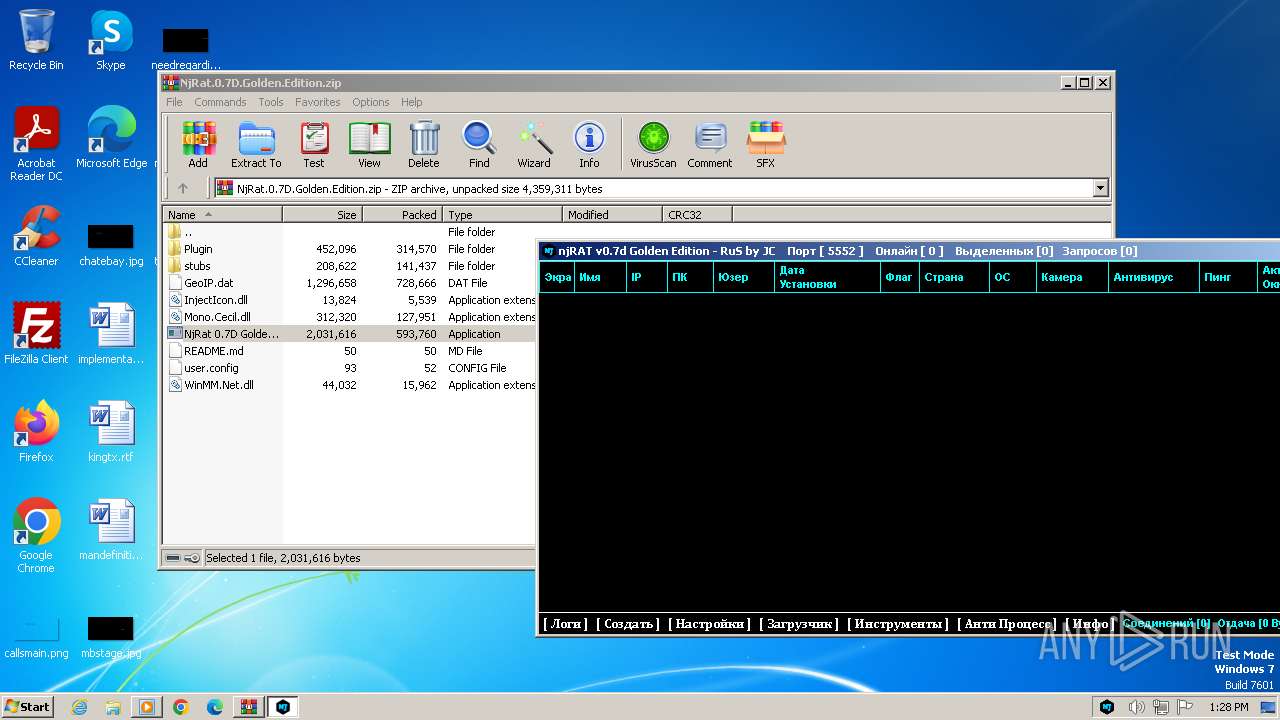
| File name: | NjRat.0.7D.Golden.Edition.zip |
| Full analysis: | https://app.any.run/tasks/013d07a7-a081-4b46-ac4d-aaeba7913e5d |
| Verdict: | Malicious activity |
| Analysis date: | March 03, 2024, 13:27:57 |
| OS: | Windows 7 Professional Service Pack 1 (build: 7601, 32 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/zip |
| File info: | Zip archive data, at least v2.0 to extract, compression method=store |
| MD5: | DE0724E9B662C97A8131D593AE03E1E8 |
| SHA1: | 2367807D0405EF6D7CEF00F0B145C29823DD5128 |
| SHA256: | AAC5B302910BE9B2C904F039129D3C42EB1E4B1539EF6DE621669793A95C7E69 |
| SSDEEP: | 49152:hoQ91Di9X+pMocKQtkWhCTNMH9xf1aawHlFhoTfNAghr5:h991DuOYKQyW4TGHeFhgNHhr5 |
MALICIOUS
SecurityXploded is detected
- WinRAR.exe (PID: 3672)
Drops the executable file immediately after the start
- WinRAR.exe (PID: 3672)
- NjRat 0.7D Golden Edition - Rus.exe (PID: 3972)
SUSPICIOUS
Reads security settings of Internet Explorer
- WinRAR.exe (PID: 3672)
Reads the Internet Settings
- NjRat 0.7D Golden Edition - Rus.exe (PID: 3972)
Executable content was dropped or overwritten
- NjRat 0.7D Golden Edition - Rus.exe (PID: 3972)
INFO
Checks supported languages
- NjRat 0.7D Golden Edition - Rus.exe (PID: 3972)
Reads the computer name
- NjRat 0.7D Golden Edition - Rus.exe (PID: 3972)
Reads the machine GUID from the registry
- NjRat 0.7D Golden Edition - Rus.exe (PID: 3972)
Reads Environment values
- NjRat 0.7D Golden Edition - Rus.exe (PID: 3972)
Create files in a temporary directory
- NjRat 0.7D Golden Edition - Rus.exe (PID: 3972)
Executable content was dropped or overwritten
- WinRAR.exe (PID: 3672)
Manual execution by a user
- explorer.exe (PID: 3996)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .zip | | | ZIP compressed archive (100) |
|---|
EXIF
ZIP
| ZipRequiredVersion: | 20 |
|---|---|
| ZipBitFlag: | - |
| ZipCompression: | None |
| ZipModifyDate: | 2020:10:23 14:50:18 |
| ZipCRC: | 0x00000000 |
| ZipCompressedSize: | - |
| ZipUncompressedSize: | - |
| ZipFileName: | Plugin/ |
Total processes
39
Monitored processes
3
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 3672 | "C:\Program Files\WinRAR\WinRAR.exe" "C:\Users\admin\AppData\Local\Temp\NjRat.0.7D.Golden.Edition.zip" | C:\Program Files\WinRAR\WinRAR.exe | explorer.exe | ||||||||||||
User: admin Company: Alexander Roshal Integrity Level: MEDIUM Description: WinRAR archiver Exit code: 0 Version: 5.91.0 Modules
| |||||||||||||||
| 3972 | "C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\NjRat 0.7D Golden Edition - Rus.exe" | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\NjRat 0.7D Golden Edition - Rus.exe | WinRAR.exe | ||||||||||||
User: admin Company: Njrat 0.7d Golden Edition Integrity Level: MEDIUM Description: Njrat 0.7d Golden Edition Exit code: 0 Version: 7.1.0.0 Modules
| |||||||||||||||
| 3996 | "C:\Windows\explorer.exe" | C:\Windows\explorer.exe | — | explorer.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows Explorer Exit code: 1 Version: 6.1.7600.16385 (win7_rtm.090713-1255) Modules
| |||||||||||||||
Total events
8 588
Read events
8 529
Write events
55
Delete events
4
Modification events
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtBMP |
Value: | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\Interface\Themes |
| Operation: | write | Name: | ShellExtIcon |
Value: | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CLASSES_ROOT\Local Settings\MuiCache\182\52C64B7E |
| Operation: | write | Name: | LanguageList |
Value: en-US | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 3 |
Value: C:\Users\admin\Desktop\phacker.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 2 |
Value: C:\Users\admin\Desktop\Win7-KB3191566-x86.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 1 |
Value: C:\Users\admin\Desktop\curl-8.5.0_1-win32-mingw.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\ArcHistory |
| Operation: | write | Name: | 0 |
Value: C:\Users\admin\AppData\Local\Temp\NjRat.0.7D.Golden.Edition.zip | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | name |
Value: 120 | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | size |
Value: 80 | |||
| (PID) Process: | (3672) WinRAR.exe | Key: | HKEY_CURRENT_USER\Software\WinRAR\FileList\FileColumnWidths |
| Operation: | write | Name: | type |
Value: 120 | |||
Executable files
17
Suspicious files
1
Text files
16
Unknown types
1
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\Plugin\sc2.dll | executable | |
MD5:9C8B5C9EC7D24EF02C7DF4E589DBA366 | SHA256:F97AADB4D1C59F4B3155A9EC57F91A05700AED38B0090096F8F1E0E7975B6561 | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\Plugin\ch.dll | executable | |
MD5:2490EDA5B4450138BA79F39FCC90048A | SHA256:3BC2898DA9CD9E202B7795B330FA3DAFF81A4B02AB4ECFE47FDD712C53252F12 | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\Plugin\cam.dll | executable | |
MD5:7EBA4D9562BF7FC14F2C1BB142A1AA6F | SHA256:5F00CDA5808E3FD126D452708308DDEE6556CB83ADACCD02EFE83654A40FC641 | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\Plugin\mic.dll | executable | |
MD5:1607999C56366FC2096A27A8BD237B98 | SHA256:7D327985D7E4F83ADFFBDF831C1E999C68CB90238790B63260AF19D24BFA66B8 | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\Plugin\pw.dll | executable | |
MD5:872401528FC94C90F3DE6658E776CC36 | SHA256:3A1CC072EFFD8C38406A6FDDF4D8F49C5366BB0E32071311D90DB669940987CE | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\stubs\dlnormal.bin | executable | |
MD5:2B53E572879A63AAA6AB032221A24D99 | SHA256:0E36C6FBBC68953D2702C3D5F84EEB35912CE9A53AADF467F8DF60FAF51A7F5E | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\Plugin\AntiProcess.dll | executable | |
MD5:B21947A28760750689F46E071D575D07 | SHA256:F643AB116E7BD8515032A502B8700AFB5BDBFC08FC1CAA08817B3061E98B763E | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\stubs\dlentrypoint.bin | executable | |
MD5:4A7B5A4DA67C17C762CB538E6FEC9ED1 | SHA256:C8294263BB4E447F53EEB9E639DBA6EC24D735D80A7D05894E8B88BD115F2970 | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\stubs\Anti.bin | executable | |
MD5:2170473F4F2B81E9B909996B0F459D16 | SHA256:01D0BEDCC943E13E341578423A2FC6848D9F63F1C5800B9A16BD64F65A1FCDDE | |||
| 3672 | WinRAR.exe | C:\Users\admin\AppData\Local\Temp\Rar$EXa3672.47769\stubs\startupch.egg | text | |
MD5:F8320B26D30AB433C5A54546D21F414C | SHA256:60A33E6CF5151F2D52EDDAE9685CFA270426AA89D8DBC7DFB854606F1D1A40FE | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
0
TCP/UDP connections
4
DNS requests
0
Threats
0
HTTP requests
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
4 | System | 192.168.100.255:137 | — | — | — | whitelisted |
1080 | svchost.exe | 224.0.0.252:5355 | — | — | — | unknown |