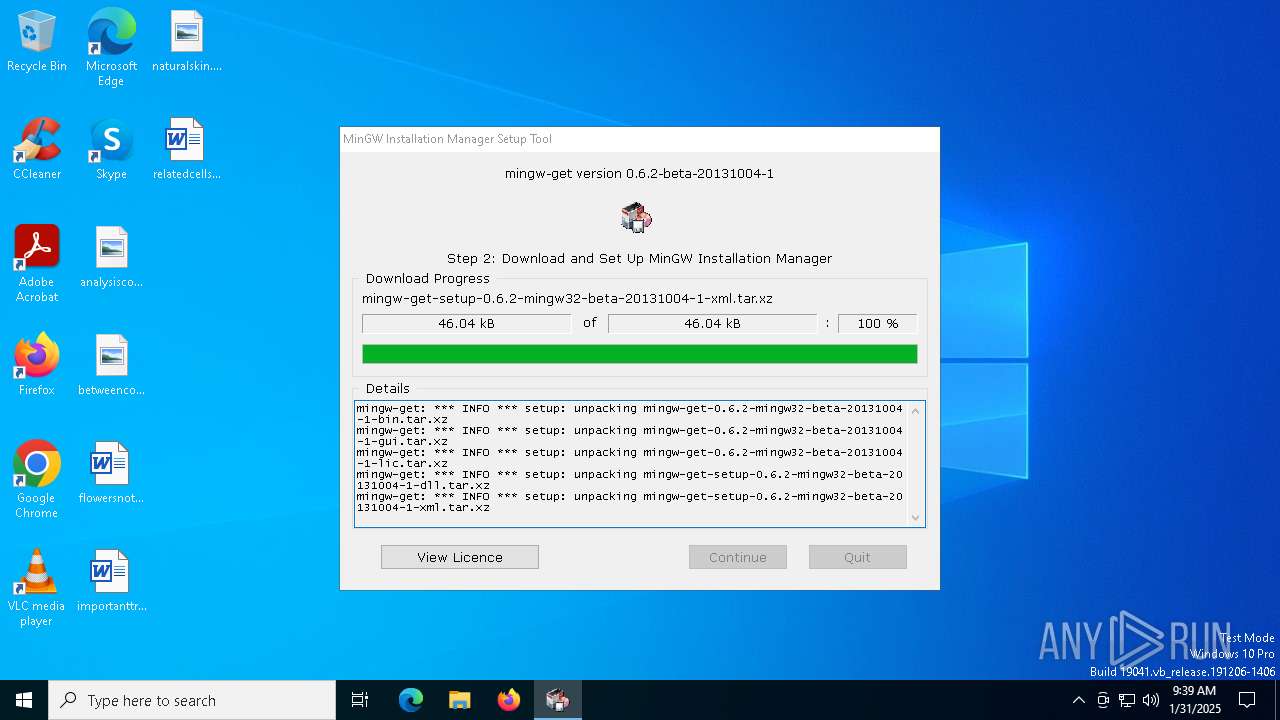
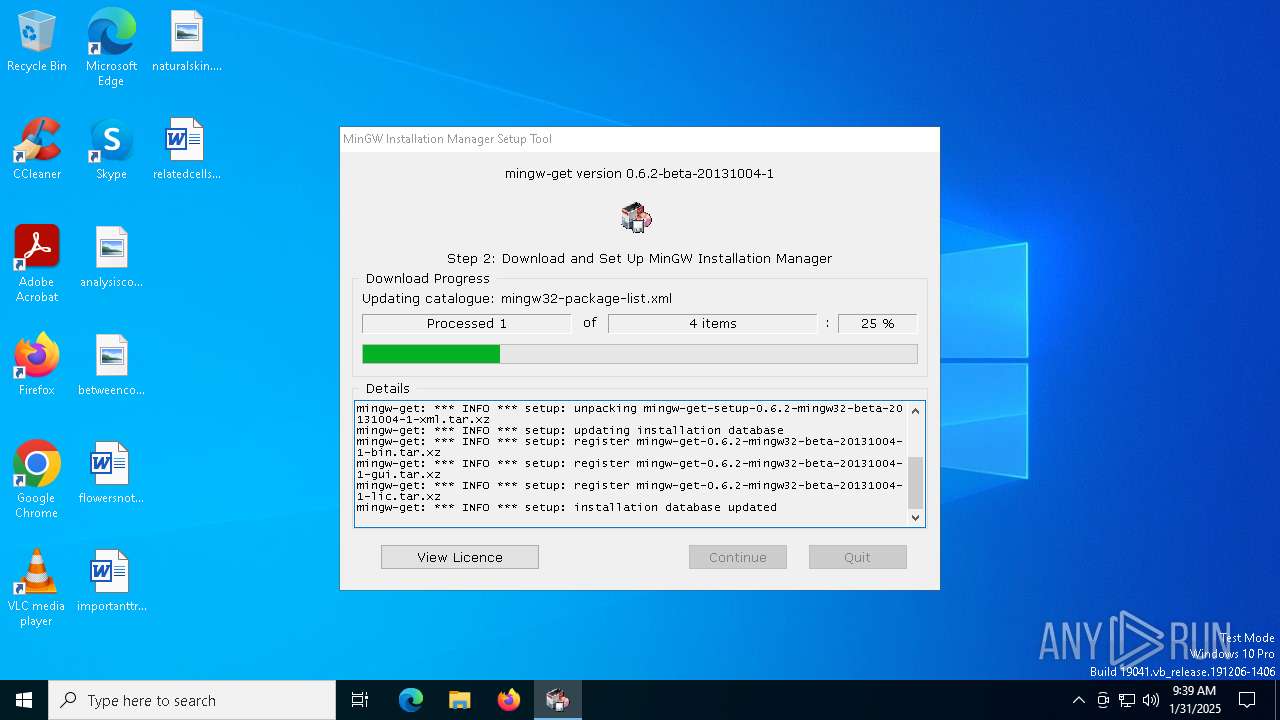
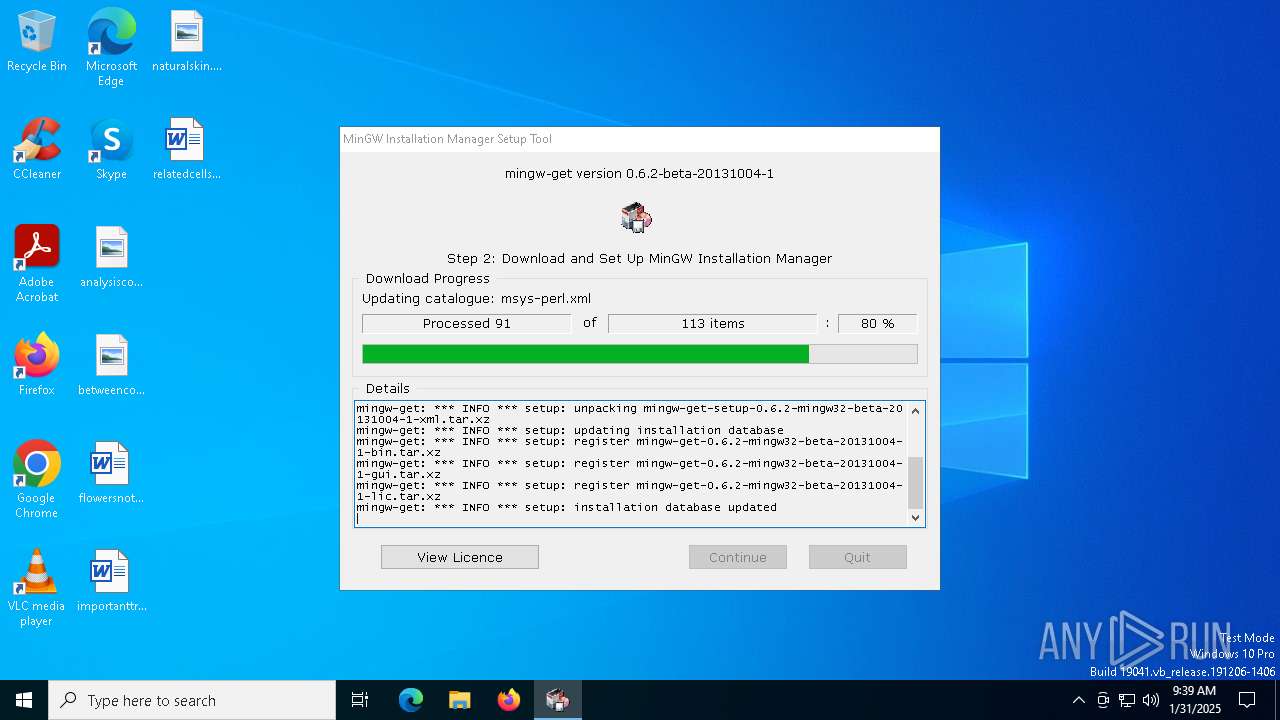
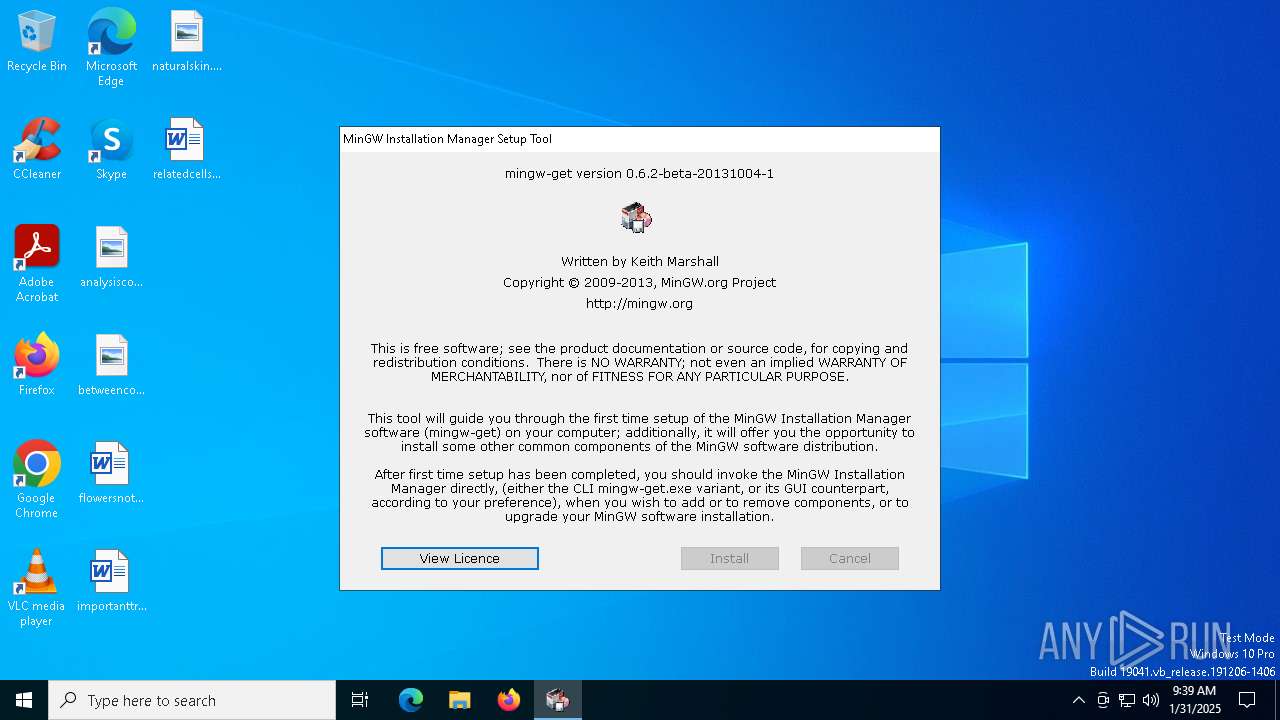
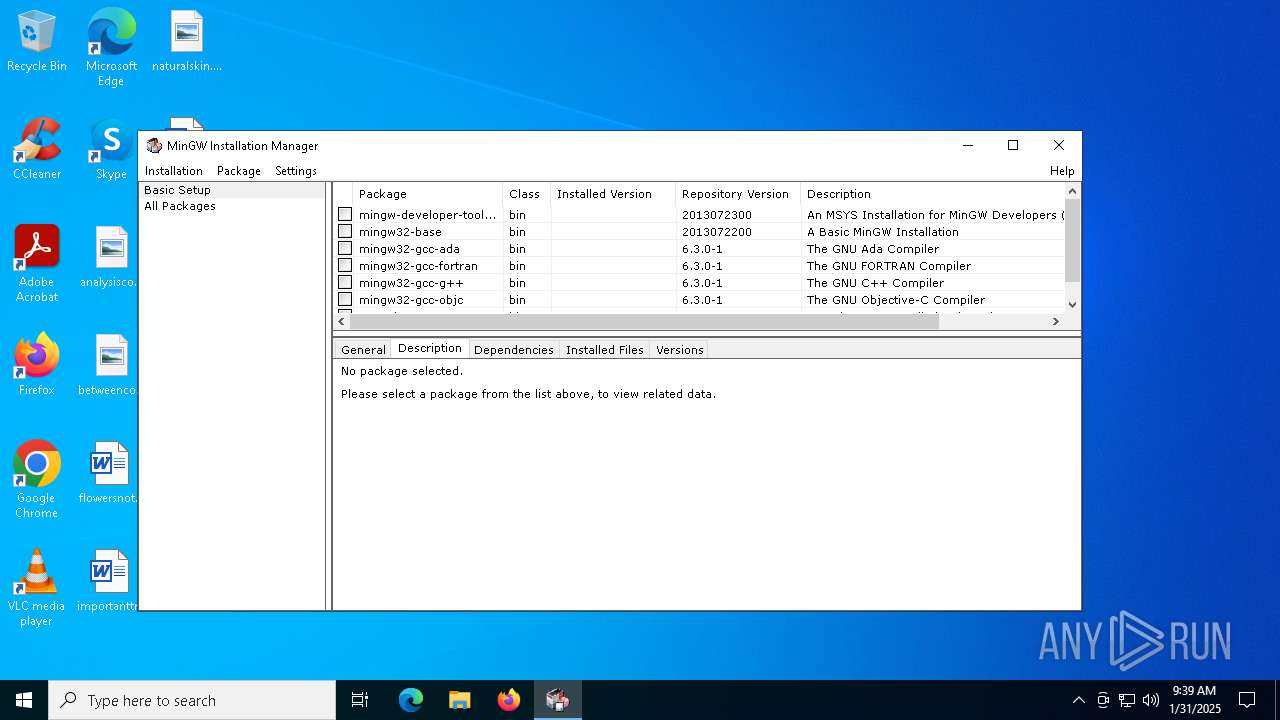
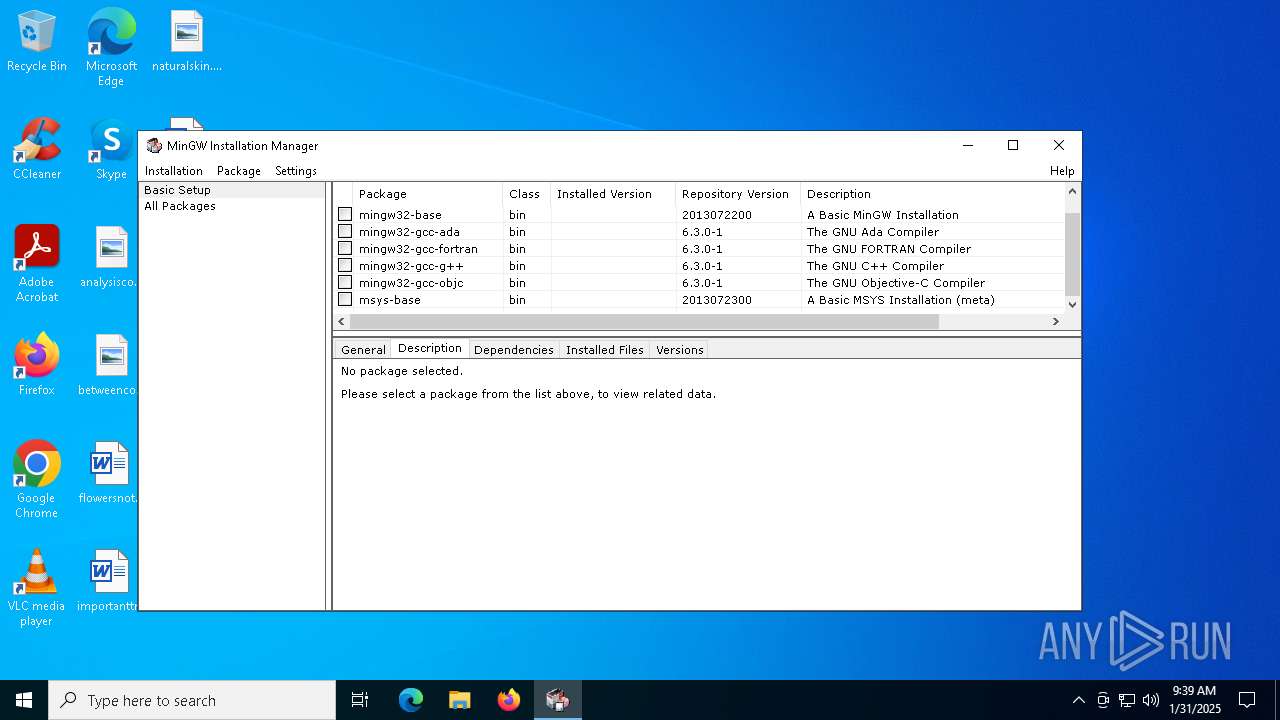
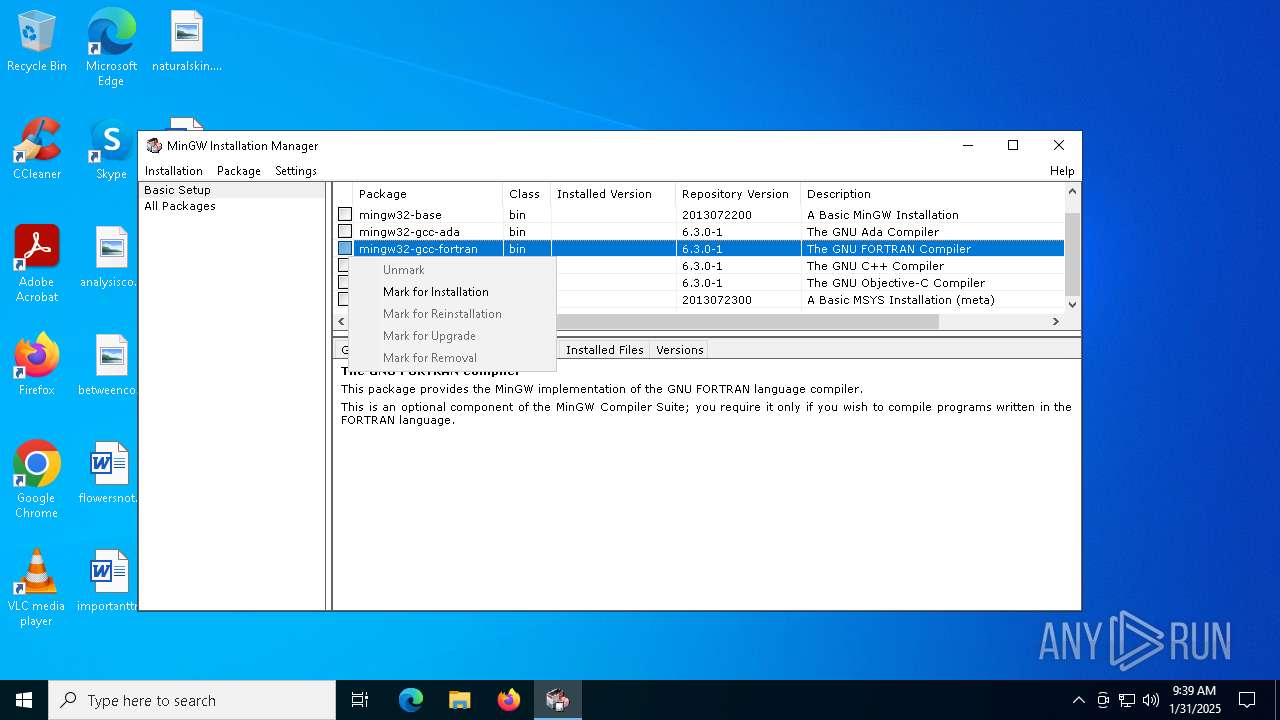
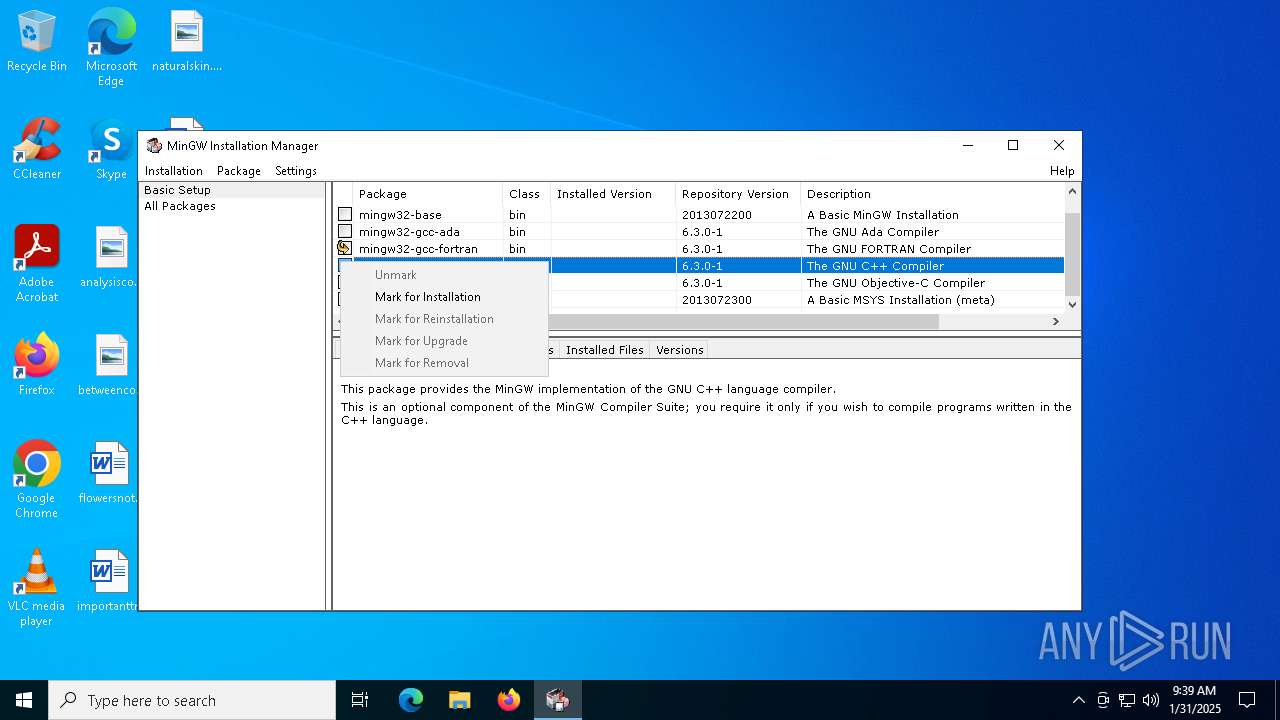
| File name: | mingw-get-setup.exe |
| Full analysis: | https://app.any.run/tasks/8b5c0882-d275-430a-8e3c-fe63e359253d |
| Verdict: | Malicious activity |
| Analysis date: | January 31, 2025, 09:38:42 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Tags: | |
| Indicators: | |
| MIME: | application/vnd.microsoft.portable-executable |
| File info: | PE32 executable (GUI) Intel 80386 (stripped to external PDB), for MS Windows, UPX compressed, 3 sections |
| MD5: | 92D905BDFE13C798A2CDA2BBACDAD932 |
| SHA1: | 66F1355F16AC1E328243E877880EB6E45E8B30E2 |
| SHA256: | AAB27BD5547D35DC159288F3B5B8760F21B0CFEC86E8F0032B49DD0410F232BC |
| SSDEEP: | 1536:+sE5jlwWrw6I3N8SFsngkZ4nJ9jHZN+4Ie6fFF6rS7cnouy8VAtY:tE5Rw6GN8wsngi4nJ7N+P7Foc8outyY |
MALICIOUS
Gets path to any of the special folders (SCRIPT)
- wscript.exe (PID: 4876)
- wscript.exe (PID: 4576)
SUSPICIOUS
Reads security settings of Internet Explorer
- mingw-get-setup.exe (PID: 6348)
Executable content was dropped or overwritten
- mingw-get-setup.exe (PID: 6348)
Gets name of the script (SCRIPT)
- wscript.exe (PID: 4876)
- wscript.exe (PID: 4576)
The process executes JS scripts
- mingw-get-setup.exe (PID: 6348)
Accesses command line arguments (SCRIPT)
- wscript.exe (PID: 4876)
- wscript.exe (PID: 4576)
INFO
The sample compiled with english language support
- mingw-get-setup.exe (PID: 6348)
Checks supported languages
- mingw-get-setup.exe (PID: 6348)
Creates files or folders in the user directory
- mingw-get-setup.exe (PID: 6348)
Reads the computer name
- mingw-get-setup.exe (PID: 6348)
UPX packer has been detected
- mingw-get-setup.exe (PID: 6348)
Checks proxy server information
- mingw-get-setup.exe (PID: 6348)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | UPX compressed Win32 Executable (39.3) |
|---|---|---|
| .exe | | | Win32 EXE Yoda's Crypter (38.6) |
| .dll | | | Win32 Dynamic Link Library (generic) (9.5) |
| .exe | | | Win32 Executable (generic) (6.5) |
| .exe | | | Generic Win/DOS Executable (2.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2013:10:04 19:21:04+00:00 |
| ImageFileCharacteristics: | No relocs, Executable, No line numbers, No symbols, 32-bit, No debug |
| PEType: | PE32 |
| LinkerVersion: | 2.22 |
| CodeSize: | 77824 |
| InitializedDataSize: | 12288 |
| UninitializedDataSize: | 135168 |
| EntryPoint: | 0x33770 |
| OSVersion: | 4 |
| ImageVersion: | 1 |
| SubsystemVersion: | 4 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.602.22340.1 |
| ProductVersionNumber: | 0.602.22340.1 |
| FileFlagsMask: | 0x003f |
| FileFlags: | Pre-release |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (British) |
| CharacterSet: | Windows, Latin1 |
| ProductName: | mingw-get |
| ProductVersion: | 0.6.2-beta-20131004-1 |
| CompanyName: | MinGW.org Project |
| LegalCopyright: | Copyright © 2009-2013, MinGW.org Project |
| OriginalFileName: | mingw-get-setup.exe |
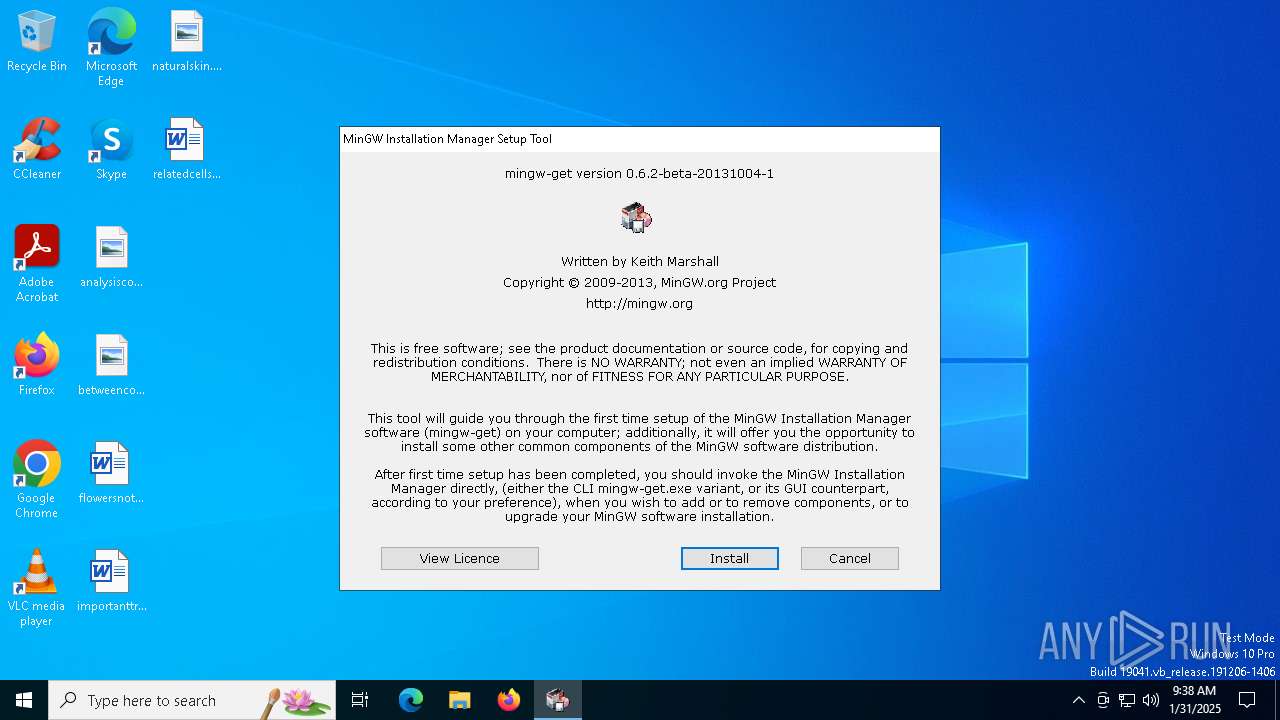
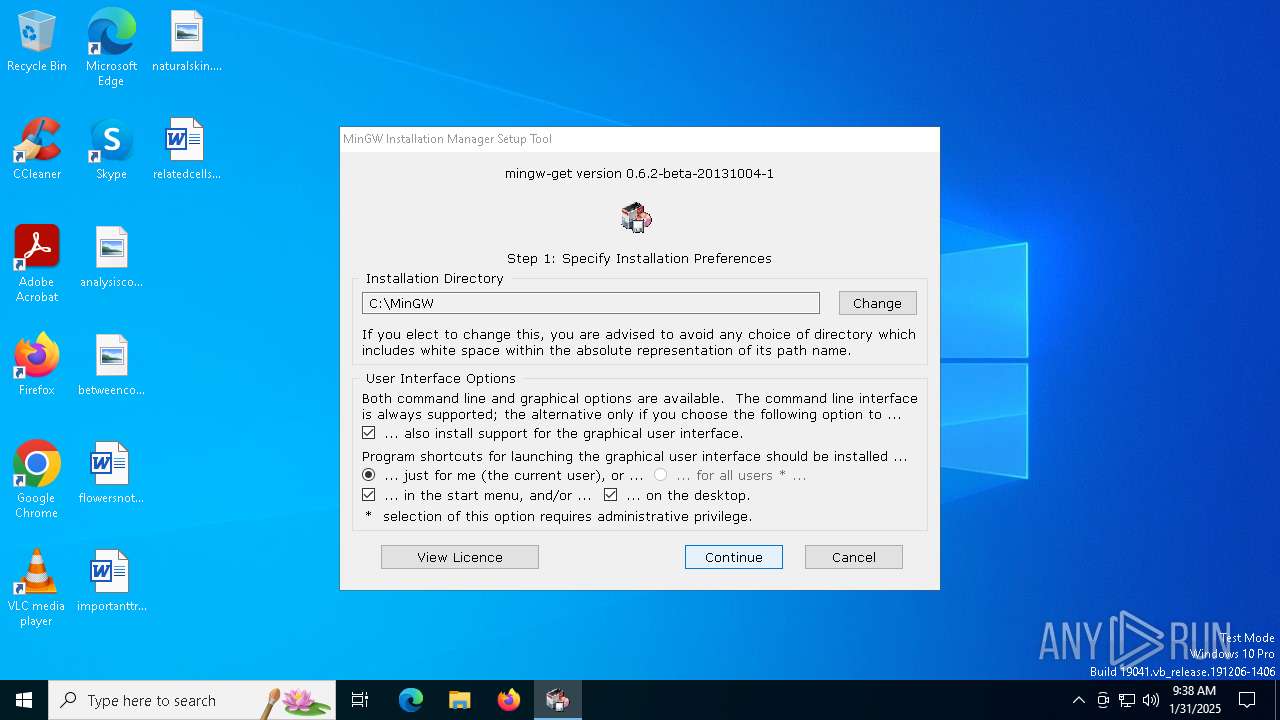
| FileDescription: | MinGW Installation Manager Setup Tool |
| FileVersion: | 0.6.2-beta-20131004-1 |
| InternalName: | mingw-get-setup |
Total processes
131
Monitored processes
3
Malicious processes
1
Suspicious processes
2
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 4576 | wscript -nologo C:\MinGW\libexec\mingw-get\shlink.js --desktop --description "MinGW Installation Manager" C:\MinGW\libexec\mingw-get\guimain.exe "MinGW Installer" | C:\Windows\SysWOW64\wscript.exe | — | mingw-get-setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 4876 | wscript -nologo C:\MinGW\libexec\mingw-get\shlink.js --start-menu --description "MinGW Installation Manager" C:\MinGW\libexec\mingw-get\guimain.exe "MinGW Installation Manager" | C:\Windows\SysWOW64\wscript.exe | — | mingw-get-setup.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Microsoft ® Windows Based Script Host Exit code: 0 Version: 5.812.10240.16384 Modules
| |||||||||||||||
| 6348 | "C:\Users\admin\AppData\Local\Temp\mingw-get-setup.exe" | C:\Users\admin\AppData\Local\Temp\mingw-get-setup.exe | explorer.exe | ||||||||||||
User: admin Company: MinGW.org Project Integrity Level: MEDIUM Description: MinGW Installation Manager Setup Tool Version: 0.6.2-beta-20131004-1 Modules
| |||||||||||||||
Total events
1 109
Read events
1 105
Write events
4
Delete events
0
Modification events
| (PID) Process: | (6348) mingw-get-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\History |
| Operation: | write | Name: | CachePrefix |
Value: Visited: | |||
| (PID) Process: | (6348) mingw-get-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Content |
| Operation: | write | Name: | CachePrefix |
Value: | |||
| (PID) Process: | (6348) mingw-get-setup.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Internet Settings\5.0\Cache\Cookies |
| Operation: | write | Name: | CachePrefix |
Value: Cookie: | |||
| (PID) Process: | (4876) wscript.exe | Key: | HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows Script\Settings\Telemetry\wscript.exe |
| Operation: | write | Name: | JScriptSetScriptStateStarted |
Value: 84FC130000000000 | |||
Executable files
6
Suspicious files
46
Text files
241
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6348 | mingw-get-setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\mingw-get-0.6.2-mingw32-beta-20131004-1-gui.tar[1].xz | text | |
MD5:29AD11701E94CA847B735EAD56900846 | SHA256:B54DD765BDED945177A11B07A5923E25700A79C9EFC325AA80A93C6E5A46E401 | |||
| 6348 | mingw-get-setup.exe | C:\MinGW\var\cache\mingw-get\packages\mingw-get-0.6.2-mingw32-beta-20131004-1-bin.tar.xz | binary | |
MD5:6453E5E9A88511A599630013CA0F2871 | SHA256:D199842BAD7373BC52CEC841D31ABF42C77FEBDDAA9E3D8A3CF3182523B23B01 | |||
| 6348 | mingw-get-setup.exe | C:\MinGW\var\cache\mingw-get\packages\.in-transit\mingw-get-0.6.2-mingw32-beta-20131004-1-bin.tar.xz | binary | |
MD5:6453E5E9A88511A599630013CA0F2871 | SHA256:D199842BAD7373BC52CEC841D31ABF42C77FEBDDAA9E3D8A3CF3182523B23B01 | |||
| 6348 | mingw-get-setup.exe | C:\MinGW\var\cache\mingw-get\packages\mingw-get-0.6.2-mingw32-beta-20131004-1-lic.tar.xz | binary | |
MD5:809D7D44CD3396481057DD6FB615C20A | SHA256:92ADC1151B1463906E2BDB091482BAFD54E363598A618C160AB1DAD19111D510 | |||
| 6348 | mingw-get-setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\KCV3KQBA\mingw-get-0.6.2-mingw32-beta-20131004-1-lic.tar[1].xz | binary | |
MD5:809D7D44CD3396481057DD6FB615C20A | SHA256:92ADC1151B1463906E2BDB091482BAFD54E363598A618C160AB1DAD19111D510 | |||
| 6348 | mingw-get-setup.exe | C:\MinGW\var\cache\mingw-get\packages\mingw-get-0.6.2-mingw32-beta-20131004-1-gui.tar.xz | binary | |
MD5:5EC17E2F07D410F721E38BAFE544F3D6 | SHA256:427887AAF995523083875599295D462F8F805FDE16CA7A770CA93CCF2C198A2C | |||
| 6348 | mingw-get-setup.exe | C:\MinGW\var\cache\mingw-get\packages\.in-transit\mingw-get-0.6.2-mingw32-beta-20131004-1-gui.tar.xz | binary | |
MD5:5EC17E2F07D410F721E38BAFE544F3D6 | SHA256:427887AAF995523083875599295D462F8F805FDE16CA7A770CA93CCF2C198A2C | |||
| 6348 | mingw-get-setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\AH8CR9J5\mingw-get-0.6.2-mingw32-beta-20131004-1-lic.tar[1].xz | text | |
MD5:9C2132A11B7F89B0DE18250FE9F971A0 | SHA256:3830171B834649248D333BE21807FA32AF73D45E7E433C184A2A00A509942CC7 | |||
| 6348 | mingw-get-setup.exe | C:\Users\admin\AppData\Local\Microsoft\Windows\INetCache\IE\E4DJRUXW\mingw-get-setup-0.6.2-mingw32-beta-20131004-1-dll.tar[1].xz | text | |
MD5:394F38BF493BCCA1152DFDC9D6523101 | SHA256:F8D0C913E872386F44F39B80DA8137B5FC2DAFB036BC8FB9C083E6E349531FDF | |||
| 6348 | mingw-get-setup.exe | C:\MinGW\var\cache\mingw-get\packages\.in-transit\mingw-get-0.6.2-mingw32-beta-20131004-1-lic.tar.xz | binary | |
MD5:809D7D44CD3396481057DD6FB615C20A | SHA256:92ADC1151B1463906E2BDB091482BAFD54E363598A618C160AB1DAD19111D510 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
109
TCP/UDP connections
68
DNS requests
27
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
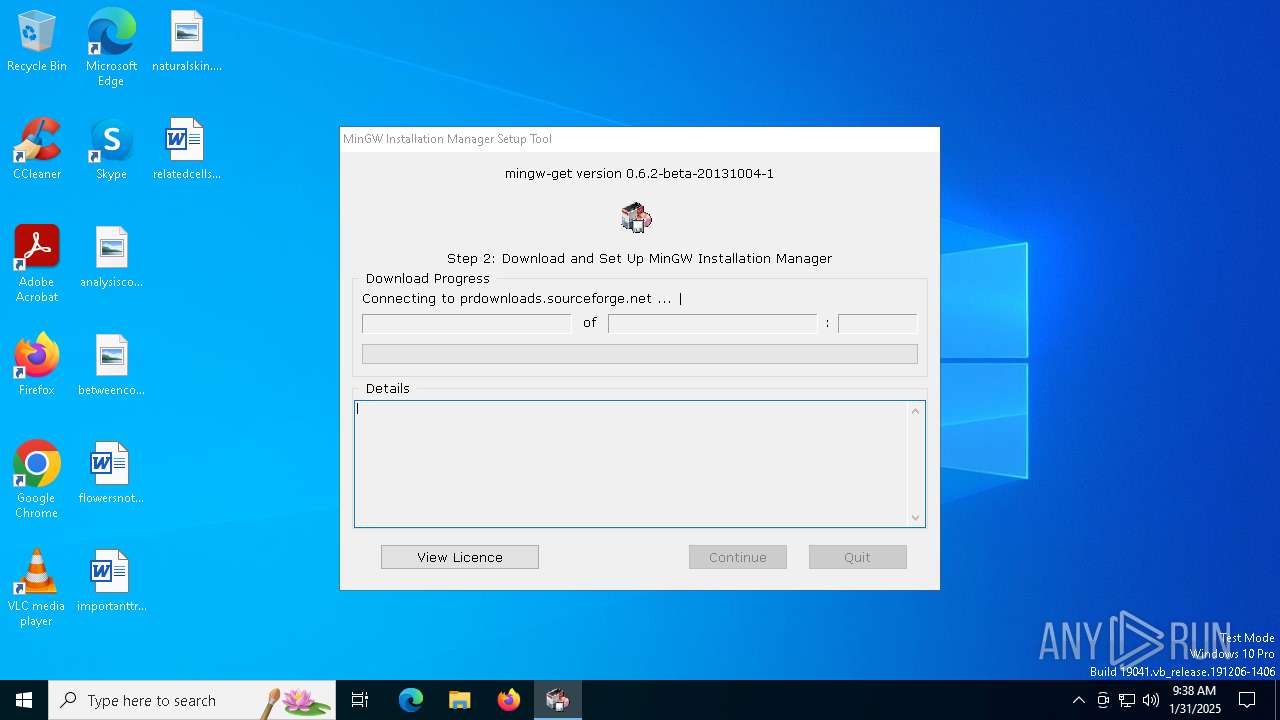
6348 | mingw-get-setup.exe | GET | 301 | 104.18.13.149:80 | http://prdownloads.sourceforge.net/mingw/mingw-get-0.6.2-mingw32-beta-20131004-1-bin.tar.xz?download | unknown | — | — | whitelisted |
— | — | GET | 200 | 184.30.21.171:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
— | — | GET | 200 | 23.48.23.143:80 | http://crl.microsoft.com/pki/crl/products/MicRooCerAut2011_2011_03_22.crl | unknown | — | — | whitelisted |
6348 | mingw-get-setup.exe | GET | 302 | 104.18.13.149:80 | http://downloads.sourceforge.net/project/mingw/Installer/mingw-get/mingw-get-0.6.2-beta-20131004-1/mingw-get-0.6.2-mingw32-beta-20131004-1-bin.tar.xz?download= | unknown | — | — | whitelisted |
6348 | mingw-get-setup.exe | GET | 301 | 104.18.13.149:80 | http://prdownloads.sourceforge.net/mingw/mingw-get-0.6.2-mingw32-beta-20131004-1-gui.tar.xz?download | unknown | — | — | whitelisted |
6348 | mingw-get-setup.exe | GET | 200 | 104.225.3.66:80 | http://netactuate.dl.sourceforge.net/project/mingw/Installer/mingw-get/mingw-get-0.6.2-beta-20131004-1/mingw-get-0.6.2-mingw32-beta-20131004-1-bin.tar.xz?viasf=1 | unknown | — | — | whitelisted |
6348 | mingw-get-setup.exe | GET | 200 | 162.251.232.173:80 | http://versaweb.dl.sourceforge.net/project/mingw/Installer/mingw-get/mingw-get-0.6.2-beta-20131004-1/mingw-get-0.6.2-mingw32-beta-20131004-1-gui.tar.xz?viasf=1 | unknown | — | — | whitelisted |
6348 | mingw-get-setup.exe | GET | 301 | 104.18.13.149:80 | http://prdownloads.sourceforge.net/mingw/mingw-get-0.6.2-mingw32-beta-20131004-1-lic.tar.xz?download | unknown | — | — | whitelisted |
6348 | mingw-get-setup.exe | GET | 302 | 104.18.13.149:80 | http://downloads.sourceforge.net/project/mingw/Installer/mingw-get/mingw-get-0.6.2-beta-20131004-1/mingw-get-0.6.2-mingw32-beta-20131004-1-gui.tar.xz?download= | unknown | — | — | whitelisted |
6348 | mingw-get-setup.exe | GET | 302 | 104.18.13.149:80 | http://downloads.sourceforge.net/project/mingw/Installer/mingw-get/mingw-get-0.6.2-beta-20131004-1/mingw-get-0.6.2-mingw32-beta-20131004-1-lic.tar.xz?download= | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4712 | MoUsoCoreWorker.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
1684 | svchost.exe | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 51.104.136.2:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 23.48.23.143:80 | crl.microsoft.com | Akamai International B.V. | DE | whitelisted |
— | — | 184.30.21.171:80 | www.microsoft.com | AKAMAI-AS | DE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6348 | mingw-get-setup.exe | 104.18.13.149:80 | prdownloads.sourceforge.net | CLOUDFLARENET | — | whitelisted |
6348 | mingw-get-setup.exe | 104.225.3.66:80 | netactuate.dl.sourceforge.net | NETACTUATE | US | whitelisted |
1684 | svchost.exe | 40.127.240.158:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
6348 | mingw-get-setup.exe | 162.251.232.173:80 | versaweb.dl.sourceforge.net | FIBERHUB | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
crl.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
prdownloads.sourceforge.net |
| whitelisted |
downloads.sourceforge.net |
| whitelisted |
netactuate.dl.sourceforge.net |
| whitelisted |
settings-win.data.microsoft.com |
| whitelisted |
versaweb.dl.sourceforge.net |
| whitelisted |
cfhcable.dl.sourceforge.net |
| whitelisted |
pilotfiber.dl.sourceforge.net |
| whitelisted |
cytranet-dal.dl.sourceforge.net |
| whitelisted |