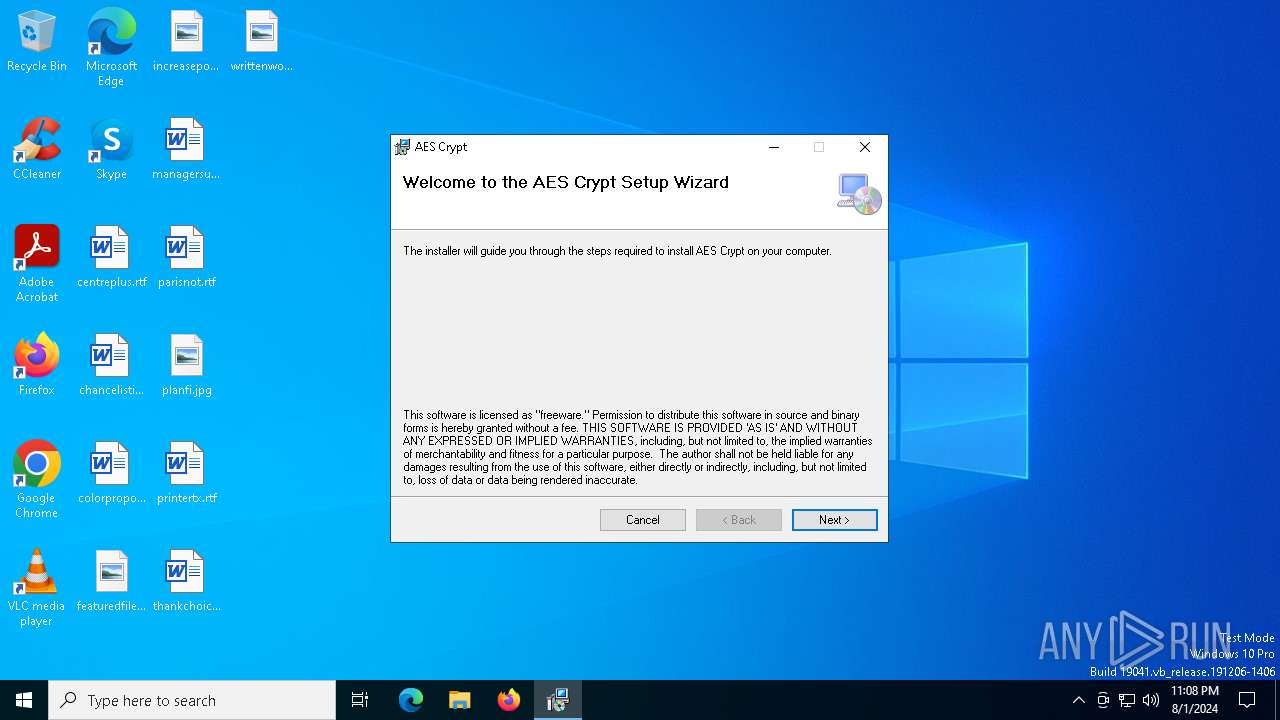
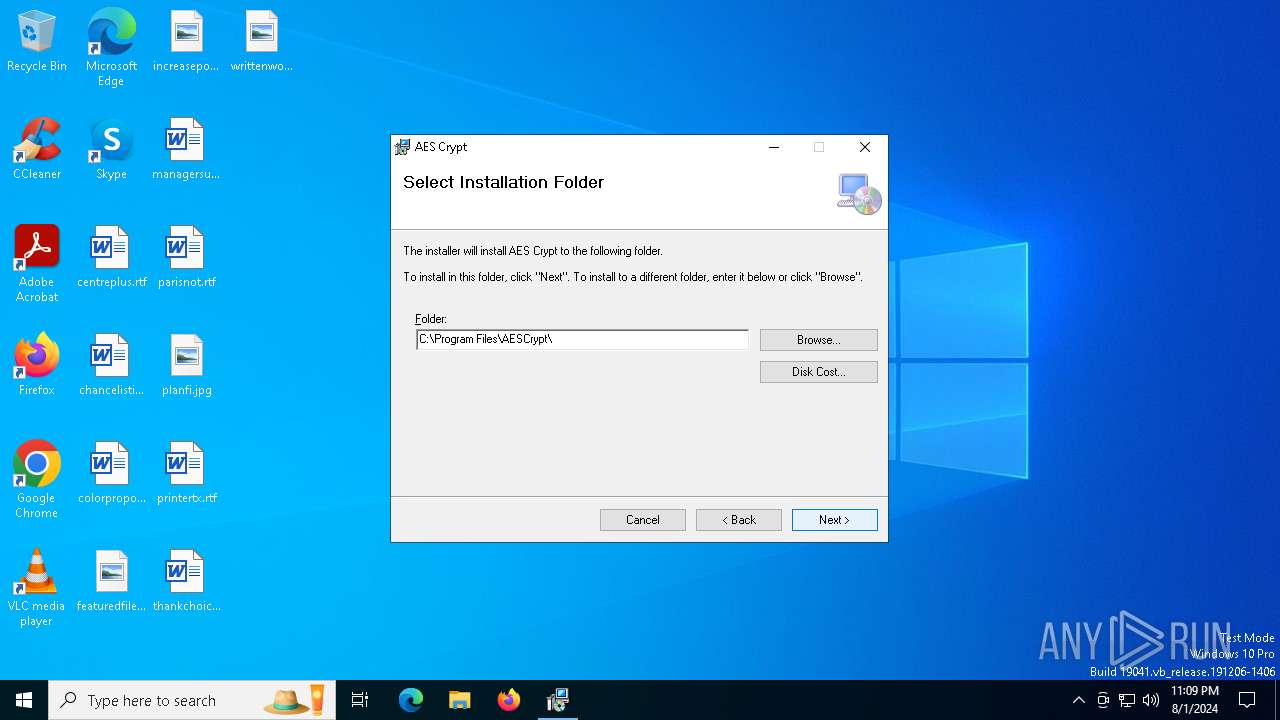
| File name: | AESCrypt.msi |
| Full analysis: | https://app.any.run/tasks/d34f845c-ba6b-425a-8b6c-6b48fdf59ca0 |
| Verdict: | Malicious activity |
| Analysis date: | August 01, 2024, 23:08:49 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-msi |
| File info: | Composite Document File V2 Document, Little Endian, Os: Windows, Version 6.1, MSI Installer, Create Time/Date: Mon Jun 21 07:00:00 1999, Name of Creating Application: Windows Installer, Security: 1, Code page: 1252, Template: x64;1033, Number of Pages: 200, Revision Number: {F56C64FE-F9BD-4368-952E-F5601C31FC95}, Title: AES Crypt, Author: Packetizer, Inc., Comments: AES Crypt - Advanced File Encryption for Windows, Number of Words: 2, Last Saved Time/Date: Fri Apr 17 21:30:39 2015, Last Printed: Fri Apr 17 21:30:39 2015 |
| MD5: | E738DA4DDDE4EC6A45F0E5E64ACC99AA |
| SHA1: | BD7D7AAB63690429EDA5D715D7199FA1EA658FEA |
| SHA256: | AA96E7FACF48235B091B01453AE6290860B1FF28889026E72936172875EFE70C |
| SSDEEP: | 24576:wzmzCXj/uGPBc6ba10EW5SfNP7FVHWw6YJXnqCGoHCX2Fag:wzmzCDuUBo0EWgFjFVH7fFag |
MALICIOUS
Drops the executable file immediately after the start
- msiexec.exe (PID: 6532)
- msiexec.exe (PID: 6808)
SUSPICIOUS
The process drops C-runtime libraries
- msiexec.exe (PID: 6808)
Process drops legitimate windows executable
- msiexec.exe (PID: 6808)
- msiexec.exe (PID: 6532)
Executes as Windows Service
- VSSVC.exe (PID: 7084)
INFO
Checks supported languages
- msiexec.exe (PID: 6916)
- msiexec.exe (PID: 6808)
Reads the computer name
- msiexec.exe (PID: 6808)
- msiexec.exe (PID: 6916)
Executable content was dropped or overwritten
- msiexec.exe (PID: 6532)
- msiexec.exe (PID: 6808)
Application launched itself
- msiexec.exe (PID: 6808)
Create files in a temporary directory
- msiexec.exe (PID: 6916)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .msi | | | Microsoft Windows Installer (98.5) |
|---|---|---|
| .msi | | | Microsoft Installer (100) |
EXIF
FlashPix
| CreateDate: | 1999:06:21 07:00:00 |
|---|---|
| Software: | Windows Installer |
| Security: | Password protected |
| CodePage: | Windows Latin 1 (Western European) |
| Template: | x64;1033 |
| Pages: | 200 |
| RevisionNumber: | {F56C64FE-F9BD-4368-952E-F5601C31FC95} |
| Title: | AES Crypt |
| Subject: | - |
| Author: | Packetizer, Inc. |
| Keywords: | - |
| Comments: | AES Crypt - Advanced File Encryption for Windows |
| Words: | 2 |
| ModifyDate: | 2015:04:17 21:30:39 |
| LastPrinted: | 2015:04:17 21:30:39 |
Total processes
139
Monitored processes
8
Malicious processes
1
Suspicious processes
1
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 2128 | "C:\Windows\System32\MsiExec.exe" /Y "C:\Program Files\AESCrypt\AESCrypt.dll" | C:\Windows\System32\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 4060 | C:\WINDOWS\system32\srtasks.exe ExecuteScopeRestorePoint /WaitForRestorePoint:11 | C:\Windows\System32\SrTasks.exe | — | msiexec.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Windows System Protection background tasks. Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5064 | C:\Windows\syswow64\MsiExec.exe -Embedding DD3F1B1B6E5C9BF7F9A1948DAC4E0591 | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 5924 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | SrTasks.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6532 | "C:\Windows\System32\msiexec.exe" /i C:\Users\admin\AppData\Local\Temp\AESCrypt.msi | C:\Windows\System32\msiexec.exe | explorer.exe | ||||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6808 | C:\WINDOWS\system32\msiexec.exe /V | C:\Windows\System32\msiexec.exe | services.exe | ||||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Windows® installer Version: 5.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6916 | C:\Windows\syswow64\MsiExec.exe -Embedding 4AA53E848121011215923A39C5DBEE42 C | C:\Windows\SysWOW64\msiexec.exe | — | msiexec.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Windows® installer Exit code: 0 Version: 5.0.19041.3636 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 7084 | C:\WINDOWS\system32\vssvc.exe | C:\Windows\System32\VSSVC.exe | — | services.exe | |||||||||||
User: SYSTEM Company: Microsoft Corporation Integrity Level: SYSTEM Description: Microsoft® Volume Shadow Copy Service Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
Total events
5 037
Read events
4 734
Write events
284
Delete events
19
Modification events
| (PID) Process: | (6808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SystemRestore |
| Operation: | write | Name: | SrCreateRp (Enter) |
Value: 4800000000000000C1E5F5CF67E4DA01981A00009C080000D50700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Enter) |
Value: 4800000000000000C1E5F5CF67E4DA01981A00009C080000D20700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGetSnapshots (Leave) |
Value: 480000000000000059F93AD067E4DA01981A00009C080000D20700000100000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Enter) |
Value: 480000000000000059F93AD067E4DA01981A00009C080000D10700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppEnumGroups (Leave) |
Value: 4800000000000000AD5C3DD067E4DA01981A00009C080000D10700000100000000000000010000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppCreate (Enter) |
Value: 4800000000000000FE2442D067E4DA01981A00009C080000D00700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows NT\CurrentVersion\SPP |
| Operation: | write | Name: | LastIndex |
Value: 11 | |||
| (PID) Process: | (6808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\SPP |
| Operation: | write | Name: | SppGatherWriterMetadata (Enter) |
Value: 480000000000000035B5BBD067E4DA01981A00009C080000D30700000000000000000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
| (PID) Process: | (6808) msiexec.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\VssapiPublisher |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 48000000000000001D18BED067E4DA01981A0000DC100000E8030000010000000000000000000000257B58C28E99B74291121945F8CBA45400000000000000000000000000000000 | |||
| (PID) Process: | (7084) VSSVC.exe | Key: | HKEY_LOCAL_MACHINE\SYSTEM\ControlSet001\Services\VSS\Diag\Registry Writer |
| Operation: | write | Name: | IDENTIFY (Enter) |
Value: 4800000000000000B66CCCD067E4DA01AC1B0000E0130000E80300000100000001000000000000000000000000000000000000000000000000000000000000000000000000000000 | |||
Executable files
12
Suspicious files
20
Text files
2
Unknown types
0
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6808 | msiexec.exe | C:\System Volume Information\SPP\metadata-2 | — | |
MD5:— | SHA256:— | |||
| 6532 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\MSI54E2.tmp | executable | |
MD5:5494165B1384FAEEFDD3D5133DF92F5A | SHA256:BA0AD3A4D2112B269E379A2231128E7EBE23E95D5D04878D6EE8815E657BB055 | |||
| 5064 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFGC138.tmp | xml | |
MD5:C517737DD6B59D0BD576A0A484C12E8B | SHA256:0774A3FD610BE54DAF2801AC6763F7FDE87073D95435900874C9A61B14F88F50 | |||
| 6916 | msiexec.exe | C:\Users\admin\AppData\Local\Temp\CFG55AD.tmp | xml | |
MD5:C517737DD6B59D0BD576A0A484C12E8B | SHA256:0774A3FD610BE54DAF2801AC6763F7FDE87073D95435900874C9A61B14F88F50 | |||
| 6808 | msiexec.exe | C:\Program Files\AESCrypt\AESCrypt32.exe | executable | |
MD5:6F4C900DE98138DBAA20E27D707C8649 | SHA256:9E54EE322B12982C7164E9FA7120984C4D75546338569CEB3DD5E4B3DD0EC5AB | |||
| 6808 | msiexec.exe | C:\Windows\Installer\inprogressinstallinfo.ipi | binary | |
MD5:D1B5FCBFB9E99B690D3341B31BCA21C3 | SHA256:C16AB4DA45D4C1D3AC08C3B593C2964D035F4F76F67EB0DD53CA33072D426580 | |||
| 6808 | msiexec.exe | C:\Program Files\AESCrypt\AESCrypt.dll | executable | |
MD5:FF91C1C5852C1B87A75D92070793DBF9 | SHA256:71020AA19597AC2D7ADA376B244D71BDA8E747C640735390804D1E163297AB07 | |||
| 6808 | msiexec.exe | C:\Program Files\AESCrypt\aescrypt.exe | executable | |
MD5:E5125D4651C008EBA61D9FD3ABD5AB31 | SHA256:874CB7A8513B781B25E176828FE8FE5AC73FA2FE29EA2AAC5FE0EAAD50E63F39 | |||
| 6808 | msiexec.exe | C:\Windows\Temp\~DFA1876EE0130DBA57.TMP | binary | |
MD5:D1B5FCBFB9E99B690D3341B31BCA21C3 | SHA256:C16AB4DA45D4C1D3AC08C3B593C2964D035F4F76F67EB0DD53CA33072D426580 | |||
| 6808 | msiexec.exe | C:\Windows\Temp\~DFDA739A3086428094.TMP | binary | |
MD5:BF619EAC0CDF3F68D496EA9344137E8B | SHA256:076A27C79E5ACE2A3D47F9DD2E83E4FF6EA8872B3C2218F66C92B89B55F36560 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
4
TCP/UDP connections
33
DNS requests
15
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBTrjrydRyt%2BApF3GSPypfHBxR5XtQQUs9tIpPmhxdiuNkHMEWNpYim8S8YCEAI5PUjXAkJafLQcAAsO18o%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
— | — | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4084 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
5240 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
— | — | 239.255.255.250:1900 | — | — | — | whitelisted |
3260 | svchost.exe | 40.113.110.67:443 | client.wns.windows.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
4436 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | unknown |
5336 | SearchApp.exe | 104.126.37.153:443 | www.bing.com | Akamai International B.V. | DE | unknown |
4436 | svchost.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
5336 | SearchApp.exe | 192.229.221.95:80 | ocsp.digicert.com | EDGECAST | US | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
client.wns.windows.com |
| whitelisted |
login.live.com |
| whitelisted |
www.bing.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
th.bing.com |
| whitelisted |
fd.api.iris.microsoft.com |
| whitelisted |
arc.msn.com |
| whitelisted |
go.microsoft.com |
| whitelisted |