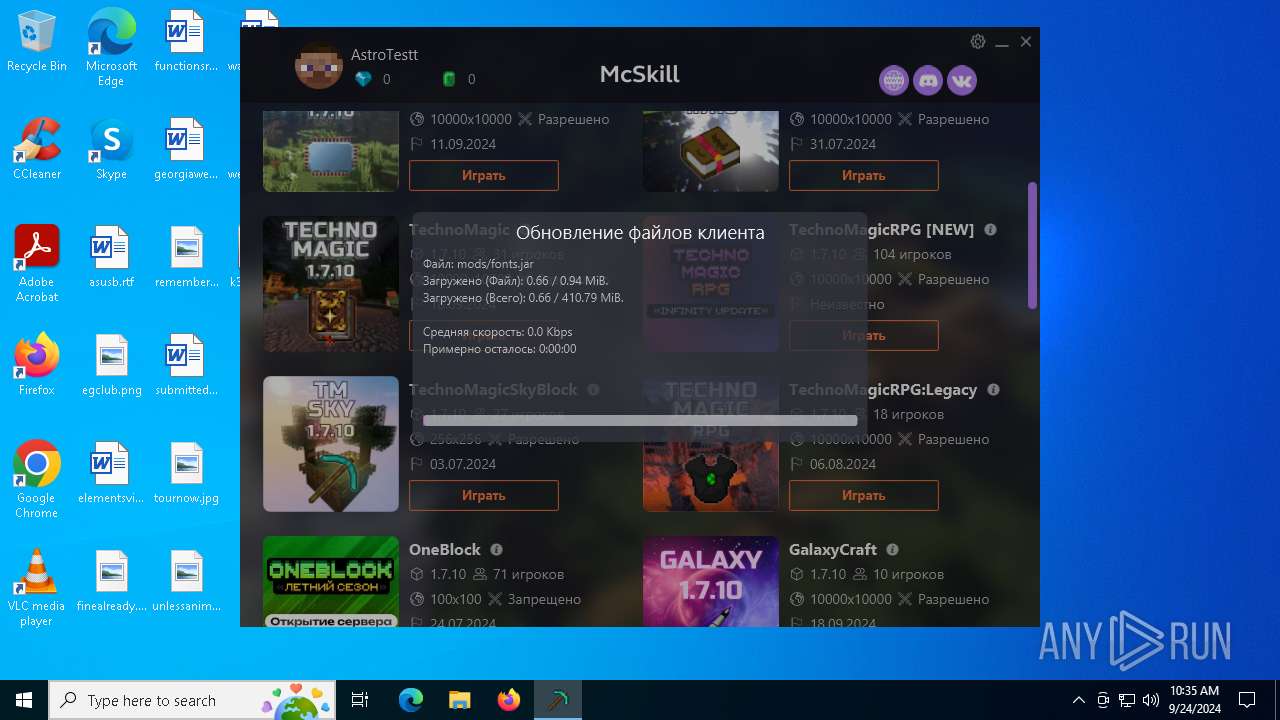
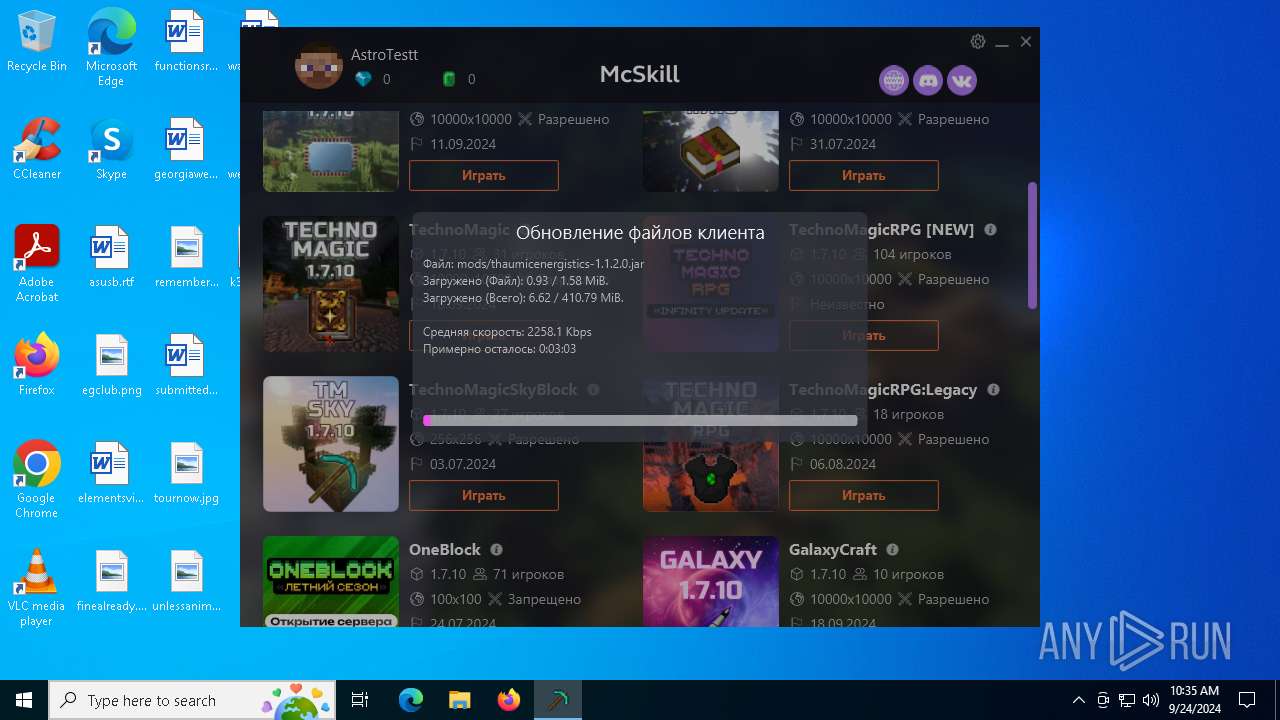
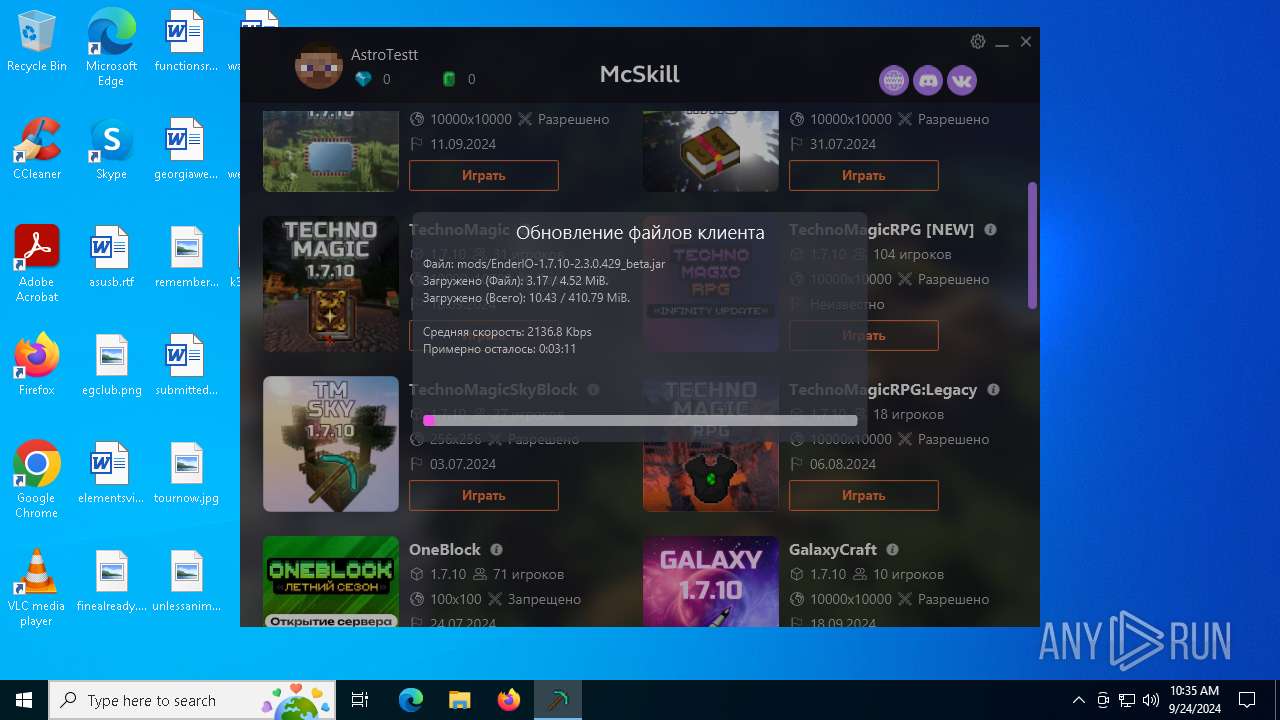
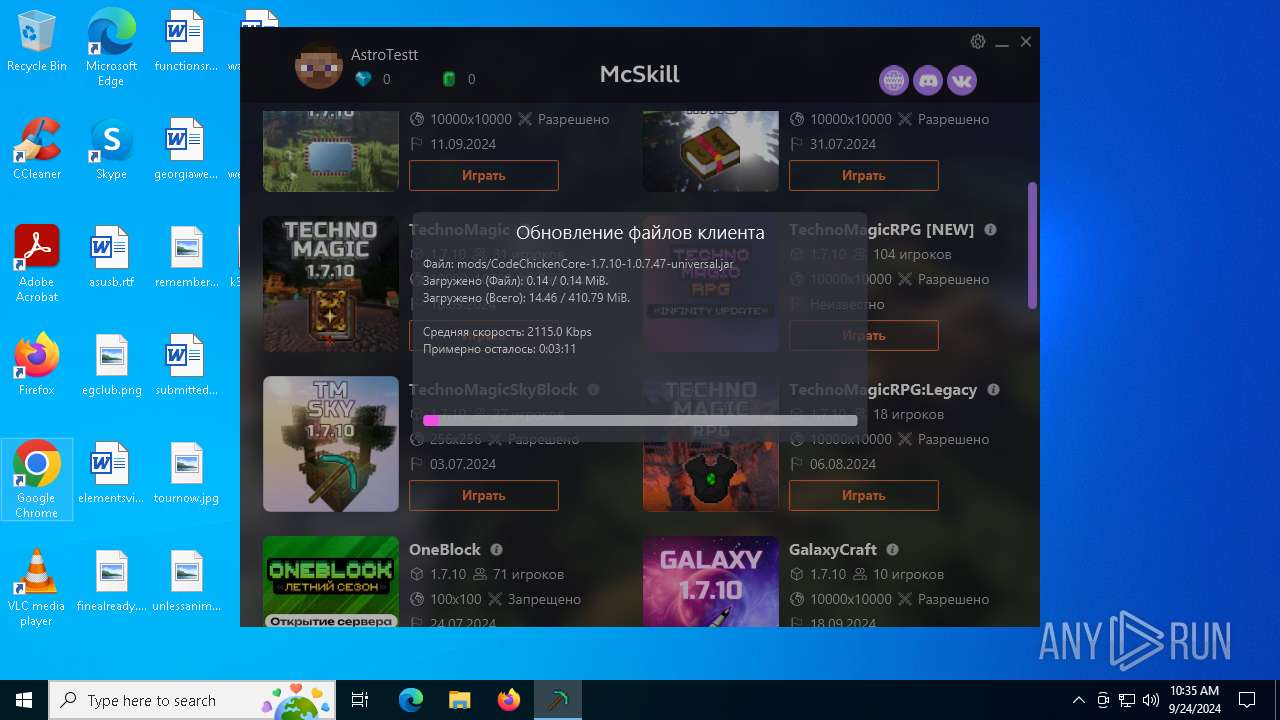
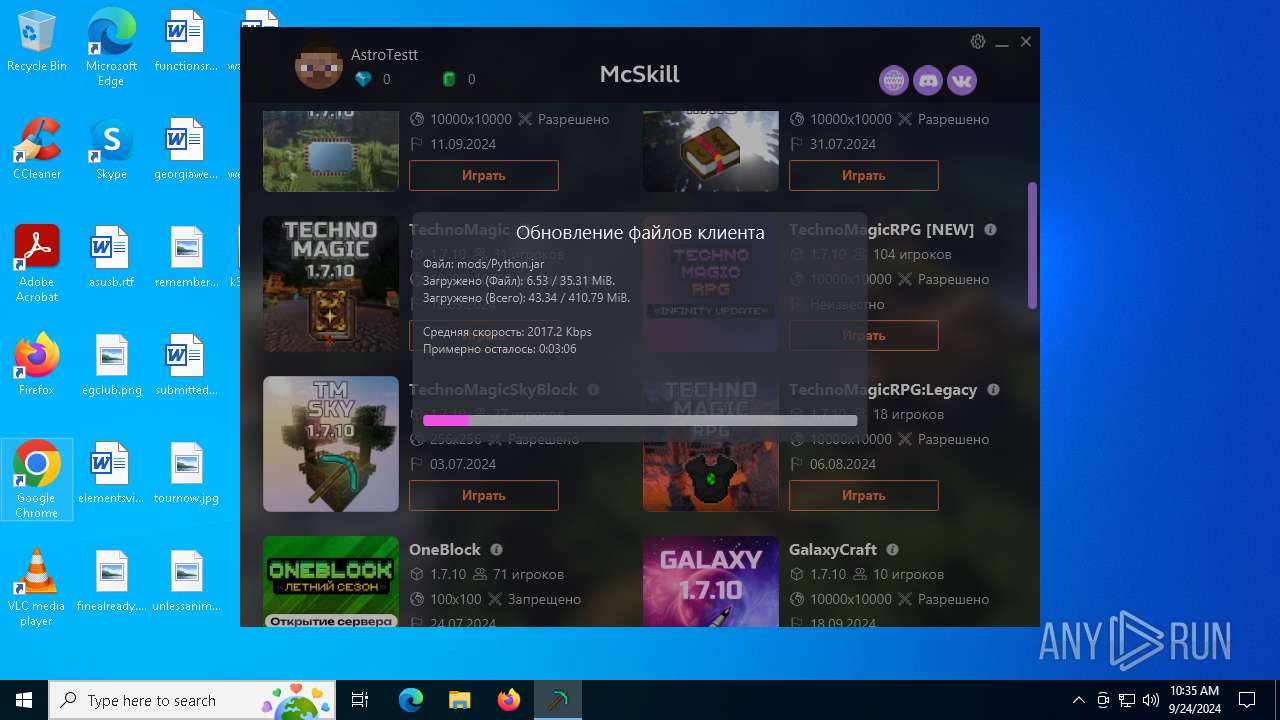
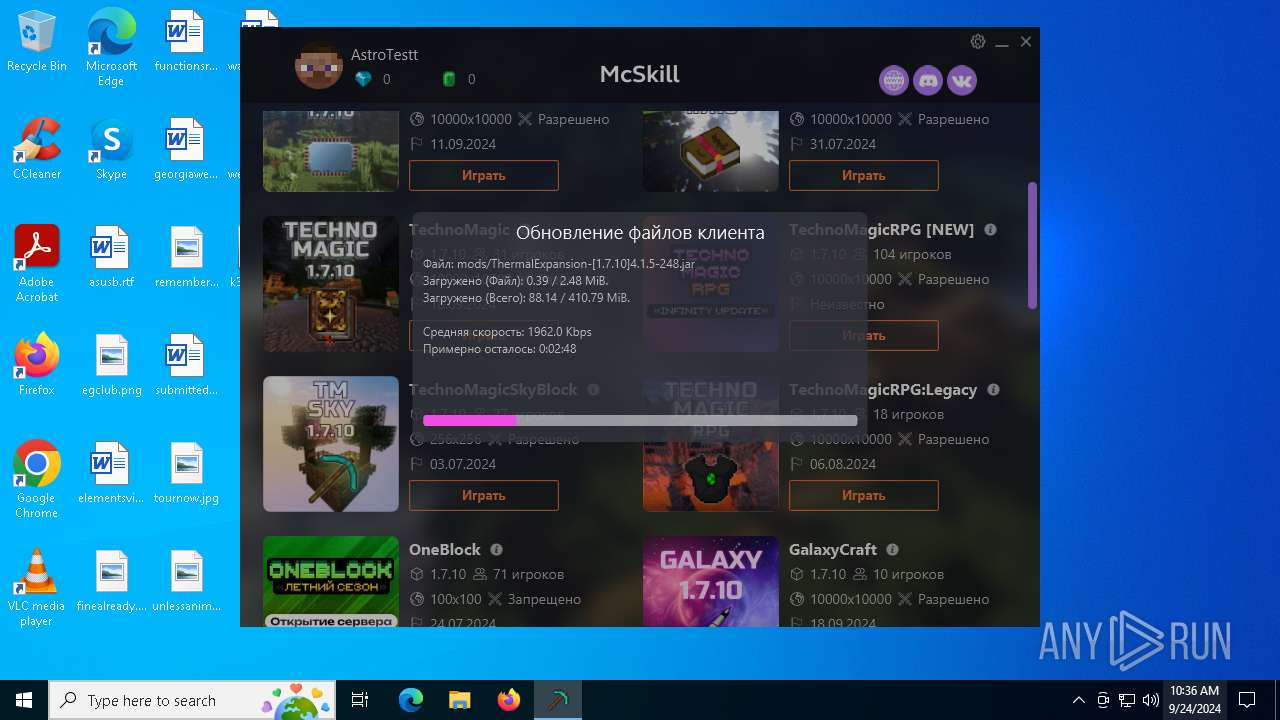
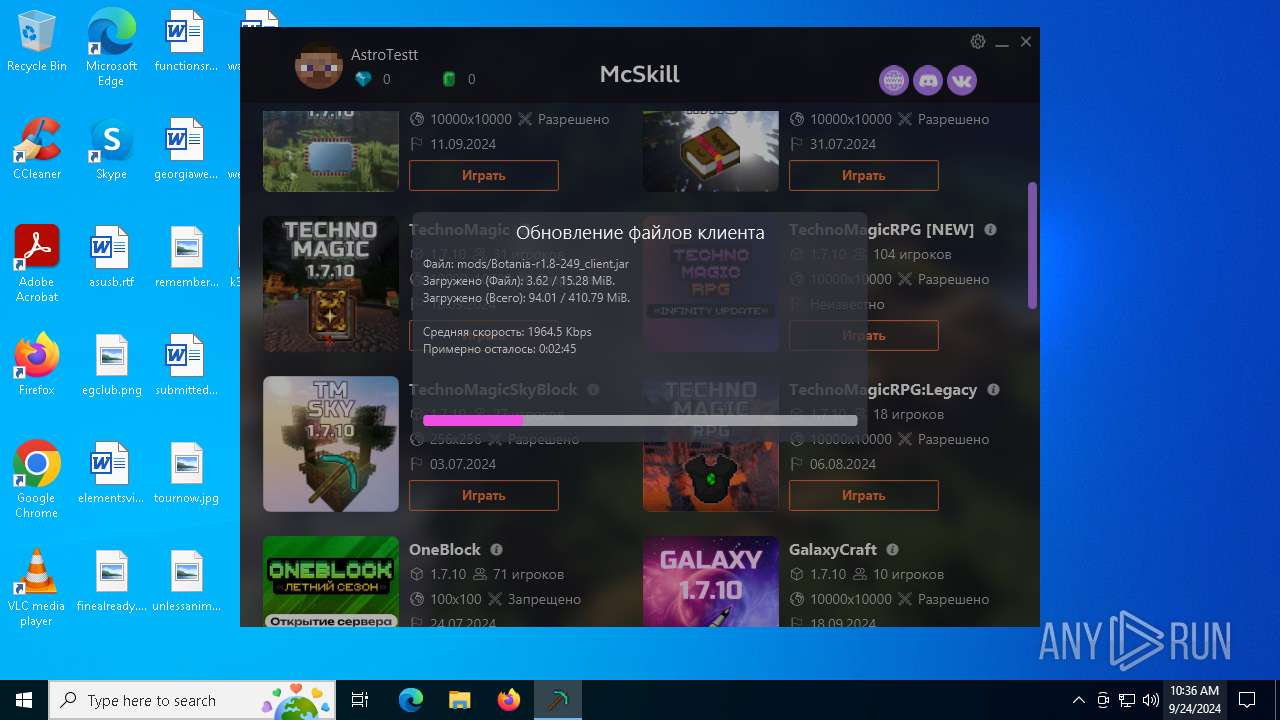
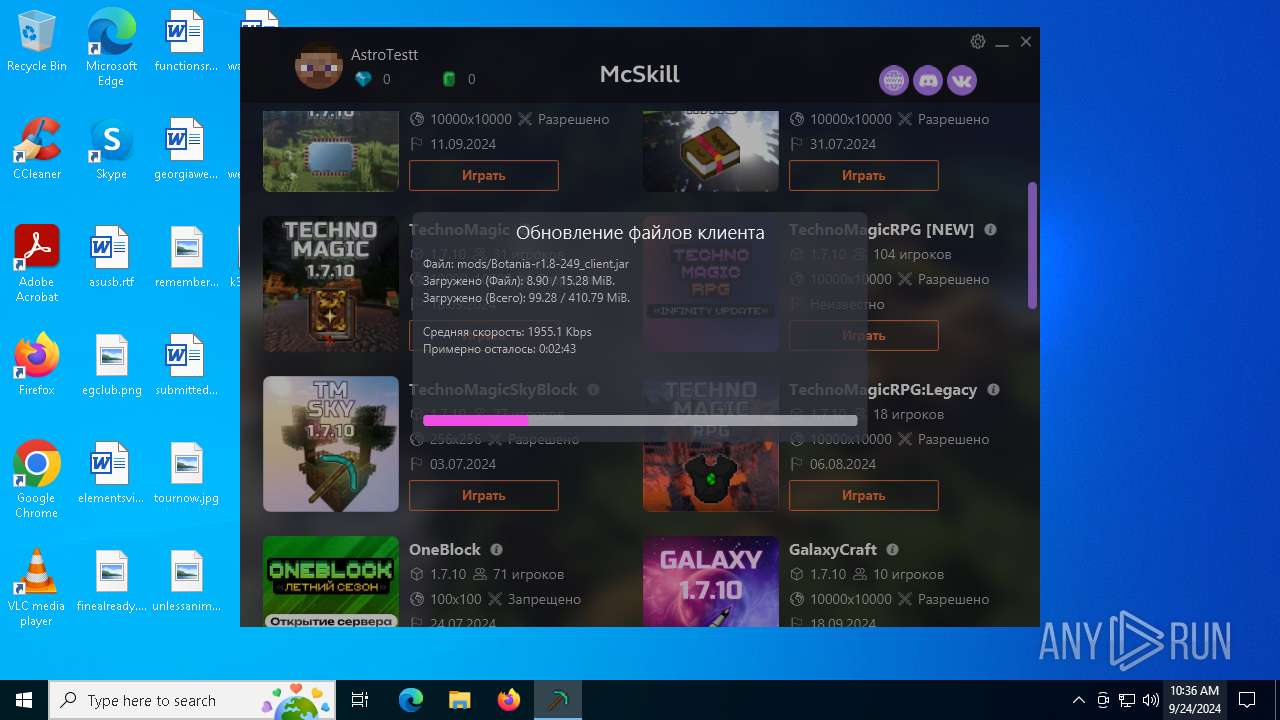
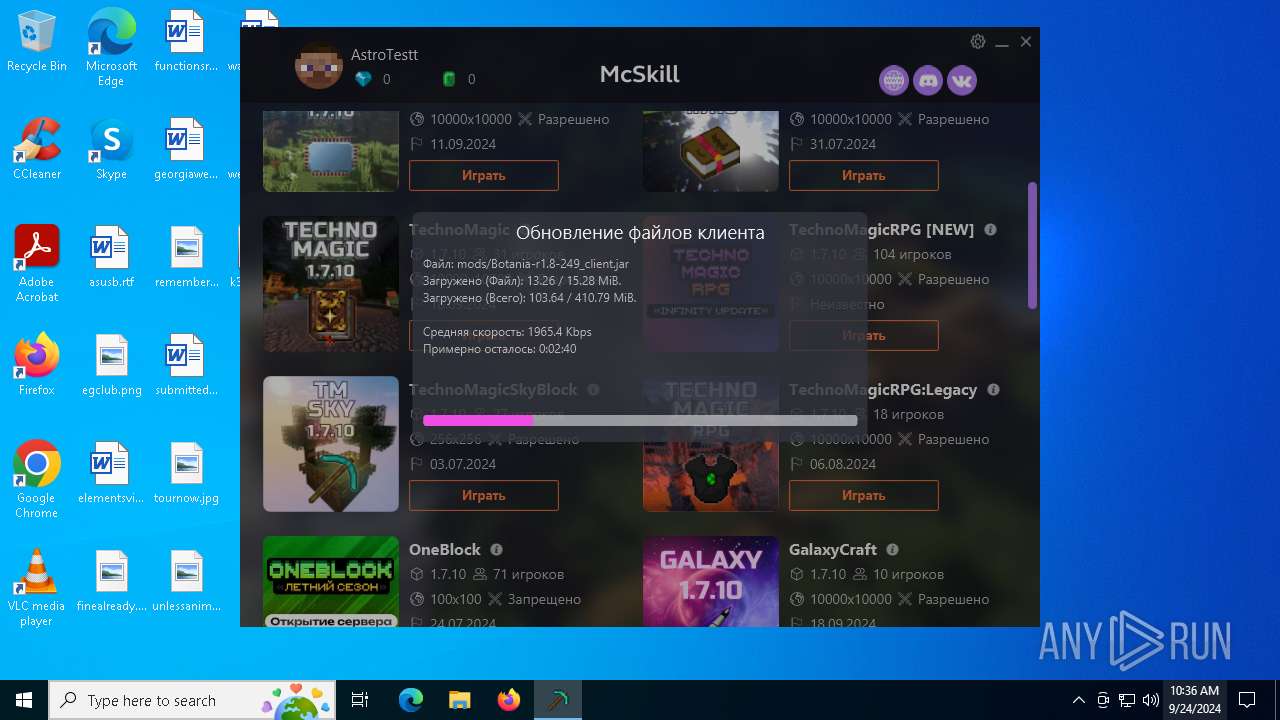
| File name: | McSkill.exe |
| Full analysis: | https://app.any.run/tasks/1a644bf9-24b3-4791-8b44-9c3ffd7731c6 |
| Verdict: | Malicious activity |
| Analysis date: | September 24, 2024, 10:32:02 |
| OS: | Windows 10 Professional (build: 19045, 64 bit) |
| Indicators: | |
| MIME: | application/x-dosexec |
| File info: | PE32 executable (GUI) Intel 80386, for MS Windows |
| MD5: | 72DD72B5BB40F6B3CF3E571E6973CCD4 |
| SHA1: | 9D4FC9F998D1E8AACA493FA465C6732C25940AEF |
| SHA256: | AA8FAF73D4BB12AE7742D09E8FEB04BB3B016A8724CED7846B6D87E562B9C423 |
| SSDEEP: | 196608:vGo/DiQS15aEXB4rlwDe5EXVXi/IYNvCXzAtJsv6tWKFdu9CEpVt:v01farlwDe6XVX5YNaXzcJsv6tWKFduh |
MALICIOUS
No malicious indicators.SUSPICIOUS
The process drops C-runtime libraries
- McSkill.exe (PID: 6320)
- java.exe (PID: 7016)
Connects to unusual port
- java.exe (PID: 7016)
Process drops legitimate windows executable
- java.exe (PID: 7016)
- McSkill.exe (PID: 6320)
Executable content was dropped or overwritten
- java.exe (PID: 7016)
- McSkill.exe (PID: 6320)
INFO
Checks supported languages
- McSkill.exe (PID: 6320)
- java.exe (PID: 7016)
Reads the machine GUID from the registry
- java.exe (PID: 7016)
Sends debugging messages
- McSkill.exe (PID: 6320)
Checks proxy server information
- McSkill.exe (PID: 6320)
Reads the computer name
- McSkill.exe (PID: 6320)
- java.exe (PID: 7016)
Creates files in the program directory
- java.exe (PID: 7016)
Create files in a temporary directory
- java.exe (PID: 7016)
Creates files or folders in the user directory
- McSkill.exe (PID: 6320)
- java.exe (PID: 7016)
Find more information about signature artifacts and mapping to MITRE ATT&CK™ MATRIX at the full report
TRiD
| .exe | | | Win32 EXE PECompact compressed (generic) (83) |
|---|---|---|
| .exe | | | Win32 Executable (generic) (9) |
| .exe | | | Generic Win/DOS Executable (3.9) |
| .exe | | | DOS Executable Generic (3.9) |
EXIF
EXE
| MachineType: | Intel 386 or later, and compatibles |
|---|---|
| TimeStamp: | 2022:02:08 09:19:31+00:00 |
| ImageFileCharacteristics: | Executable, 32-bit |
| PEType: | PE32 |
| LinkerVersion: | 14.16 |
| CodeSize: | 7052800 |
| InitializedDataSize: | 4401664 |
| UninitializedDataSize: | - |
| EntryPoint: | 0x67b858 |
| OSVersion: | 6 |
| ImageVersion: | - |
| SubsystemVersion: | 6 |
| Subsystem: | Windows GUI |
| FileVersionNumber: | 0.0.0.0 |
| ProductVersionNumber: | 0.0.0.0 |
| FileFlagsMask: | 0x003f |
| FileFlags: | (none) |
| FileOS: | Win32 |
| ObjectFileType: | Executable application |
| FileSubtype: | - |
| LanguageCode: | English (U.S.) |
| CharacterSet: | Unicode |
| CompanyName: | - |
| FileDescription: | - |
| FileVersion: | 0.0.0.0 |
| LegalCopyright: | - |
| OriginalFileName: | Starter.exe |
| ProductName: | Starter |
| ProductVersion: | 0.0.0.0 |
Total processes
124
Monitored processes
5
Malicious processes
2
Suspicious processes
0
Behavior graph
Click at the process to see the details
Process information
PID | CMD | Path | Indicators | Parent process | |||||||||||
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 1848 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2424 | C:\WINDOWS\system32\icacls.exe C:\ProgramData\Oracle\Java\.oracle_jre_usage /grant "everyone":(OI)(CI)M | C:\Windows\System32\icacls.exe | — | java.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 2572 | \??\C:\WINDOWS\system32\conhost.exe 0xffffffff -ForceV1 | C:\Windows\System32\conhost.exe | — | icacls.exe | |||||||||||
User: admin Company: Microsoft Corporation Integrity Level: MEDIUM Description: Console Window Host Exit code: 0 Version: 10.0.19041.1 (WinBuild.160101.0800) Modules
| |||||||||||||||
| 6320 | "C:\Users\admin\Downloads\McSkill.exe" | C:\Users\admin\Downloads\McSkill.exe | explorer.exe | ||||||||||||
User: admin Integrity Level: MEDIUM Exit code: 0 Version: 0.0.0.0 Modules
| |||||||||||||||
| 7016 | C:\Users\admin\AppData\Roaming\MCSkill\updates\jdk-win64\bin\java.exe -jar C:/Users/admin/AppData/Roaming/MCSkill/updates/Launcher.jar | C:\Users\admin\AppData\Roaming\MCSkill\updates\jdk-win64\bin\java.exe | McSkill.exe | ||||||||||||
User: admin Company: Oracle Corporation Integrity Level: MEDIUM Description: Java(TM) Platform SE binary Version: 8.0.2610.12 Modules
| |||||||||||||||
Total events
3 648
Read events
3 648
Write events
0
Delete events
0
Modification events
Executable files
327
Suspicious files
538
Text files
214
Unknown types
68
Dropped files
PID | Process | Filename | Type | |
|---|---|---|---|---|
| 6320 | McSkill.exe | C:\Users\admin\AppData\Roaming\MCSkill\updates\java64.zip | — | |
MD5:— | SHA256:— | |||
| 6320 | McSkill.exe | C:\Users\admin\AppData\Roaming\MCSkill\updates\jdk-win64\bin\api-ms-win-core-datetime-l1-1-0.dll | executable | |
MD5:F0C9C56F56FFA3ADC548173569DBD793 | SHA256:12D801992BBB09D43BB90330BB96E77BF12E669C325DDA4B5235942221C301C8 | |||
| 6320 | McSkill.exe | C:\Users\admin\AppData\Roaming\MCSkill\updates\jdk-win64\bin\api-ms-win-core-debug-l1-1-0.dll | executable | |
MD5:02D669AFDABFE420598041B848B71158 | SHA256:64A9AC181FD91B79270BF01759749394F57BE171436ED46F43D165325BB82067 | |||
| 6320 | McSkill.exe | C:\Users\admin\AppData\Roaming\MCSkill\updates\jdk-win64\bin\api-ms-win-core-errorhandling-l1-1-0.dll | executable | |
MD5:944A33D971704FF815A6C90733D0A72E | SHA256:44822AE123A3D6C3A8BDF9A4D65A4DC89EB31004C72FCFCEFA1DC3A53FF3EAB0 | |||
| 6320 | McSkill.exe | C:\Users\admin\AppData\Roaming\MCSkill\updates\jdk-win64\bin\api-ms-win-core-console-l1-1-0.dll | executable | |
MD5:2C146BC8D73B8944F35506241B9953A9 | SHA256:89384F8F64A9B7F67C8DECCAA721E2D76B8A17026D8083630859ED0CD1A9B58B | |||
| 6320 | McSkill.exe | C:\Users\admin\AppData\Roaming\MCSkill\updates\jdk-win64\bin\api-ms-win-core-console-l1-2-0.dll | executable | |
MD5:7A55E51D07E1F15221EB11479ADBC53F | SHA256:F901B0BC8C00B3AFC80E151E6F54B18F7672F932602C304FBFEEDD5AA3AD63C8 | |||
| 6320 | McSkill.exe | C:\Users\admin\AppData\Roaming\MCSkill\updates\jdk-win64\bin\api-ms-win-core-file-l1-1-0.dll | executable | |
MD5:FEC01082BCCDDADAD0814F30B43AB078 | SHA256:C15DACEC228F40CE4C5B9D69BBA5E6627BC484C6E9D6550A76DB6F332E9F7734 | |||
| 6320 | McSkill.exe | C:\Users\admin\AppData\Roaming\MCSkill\updates\Launcher.jar | java | |
MD5:E577BF8A69D6A7A632E33EFEA2E4BBA5 | SHA256:31DE08397A5EE317F032FCB12E9ED04AE635798C63A89B3012DCF596891C1A87 | |||
| 6320 | McSkill.exe | C:\Users\admin\AppData\Roaming\MCSkill\updates\jdk-win64\bin\api-ms-win-core-file-l2-1-0.dll | executable | |
MD5:2E8995E2320E313545C3DDB5C71DC232 | SHA256:C55EB043454AC2D460F86EA26F934ECB16BDB1D05294C168193A05090BF1C56C | |||
| 6320 | McSkill.exe | C:\Users\admin\AppData\Roaming\MCSkill\updates\jdk-win64\bin\api-ms-win-core-profile-l1-1-0.dll | executable | |
MD5:2E19BDBF51D8CAF97B2BCB886FDC5B2D | SHA256:9518B9399AC4D459122E428173B2BAACCD92C02E585A13E58A7812FAD7012381 | |||
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
HTTP(S) requests
5
TCP/UDP connections
57
DNS requests
19
Threats
0
HTTP requests
PID | Process | Method | HTTP Code | IP | URL | CN | Type | Size | Reputation |
|---|---|---|---|---|---|---|---|---|---|
5960 | svchost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBSAUQYBMq2awn1Rh6Doh%2FsBYgFV7gQUA95QNVbRTLtm8KPiGxvDl7I90VUCEAJ0LqoXyo4hxxe7H%2Fz9DKA%3D | unknown | — | — | whitelisted |
2120 | MoUsoCoreWorker.exe | GET | 200 | 95.101.149.131:80 | http://www.microsoft.com/pkiops/crl/MicSecSerCA2011_2011-10-18.crl | unknown | — | — | whitelisted |
3784 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Product%20Root%20Certificate%20Authority%202018.crl | unknown | — | — | whitelisted |
3784 | SIHClient.exe | GET | 200 | 88.221.169.152:80 | http://www.microsoft.com/pkiops/crl/Microsoft%20ECC%20Update%20Secure%20Server%20CA%202.1.crl | unknown | — | — | whitelisted |
6716 | backgroundTaskHost.exe | GET | 200 | 192.229.221.95:80 | http://ocsp.digicert.com/MFEwTzBNMEswSTAJBgUrDgMCGgUABBQ50otx%2Fh0Ztl%2Bz8SiPI7wEWVxDlQQUTiJUIBiV5uNu5g%2F6%2BrkS7QYXjzkCEAn5bsKVVV8kdJ6vHl3O1J0%3D | unknown | — | — | whitelisted |
Download PCAP, analyze network streams, HTTP content and a lot more at the full report
Connections
PID | Process | IP | Domain | ASN | CN | Reputation |
|---|---|---|---|---|---|---|
4 | System | 192.168.100.255:138 | — | — | — | whitelisted |
6920 | svchost.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
4732 | RUXIMICS.exe | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
— | — | 20.50.80.213:443 | — | MICROSOFT-CORP-MSN-AS-BLOCK | IE | unknown |
— | — | 104.126.37.130:443 | — | Akamai International B.V. | DE | unknown |
— | — | 4.231.128.59:443 | settings-win.data.microsoft.com | MICROSOFT-CORP-MSN-AS-BLOCK | IE | whitelisted |
2120 | MoUsoCoreWorker.exe | 95.101.149.131:80 | www.microsoft.com | Akamai International B.V. | NL | whitelisted |
3888 | svchost.exe | 239.255.255.250:1900 | — | — | — | whitelisted |
6320 | McSkill.exe | 51.83.239.114:443 | upd.mcskill.net | OVH SAS | PL | unknown |
5960 | svchost.exe | 40.126.32.136:443 | login.live.com | MICROSOFT-CORP-MSN-AS-BLOCK | NL | whitelisted |
DNS requests
Domain | IP | Reputation |
|---|---|---|
settings-win.data.microsoft.com |
| whitelisted |
www.microsoft.com |
| whitelisted |
google.com |
| whitelisted |
upd.mcskill.net |
| unknown |
login.live.com |
| whitelisted |
ocsp.digicert.com |
| whitelisted |
slscr.update.microsoft.com |
| whitelisted |
fe3cr.delivery.mp.microsoft.com |
| whitelisted |
nexusrules.officeapps.live.com |
| whitelisted |
launcher.mcskill.net |
| unknown |
Threats
Process | Message |
|---|---|
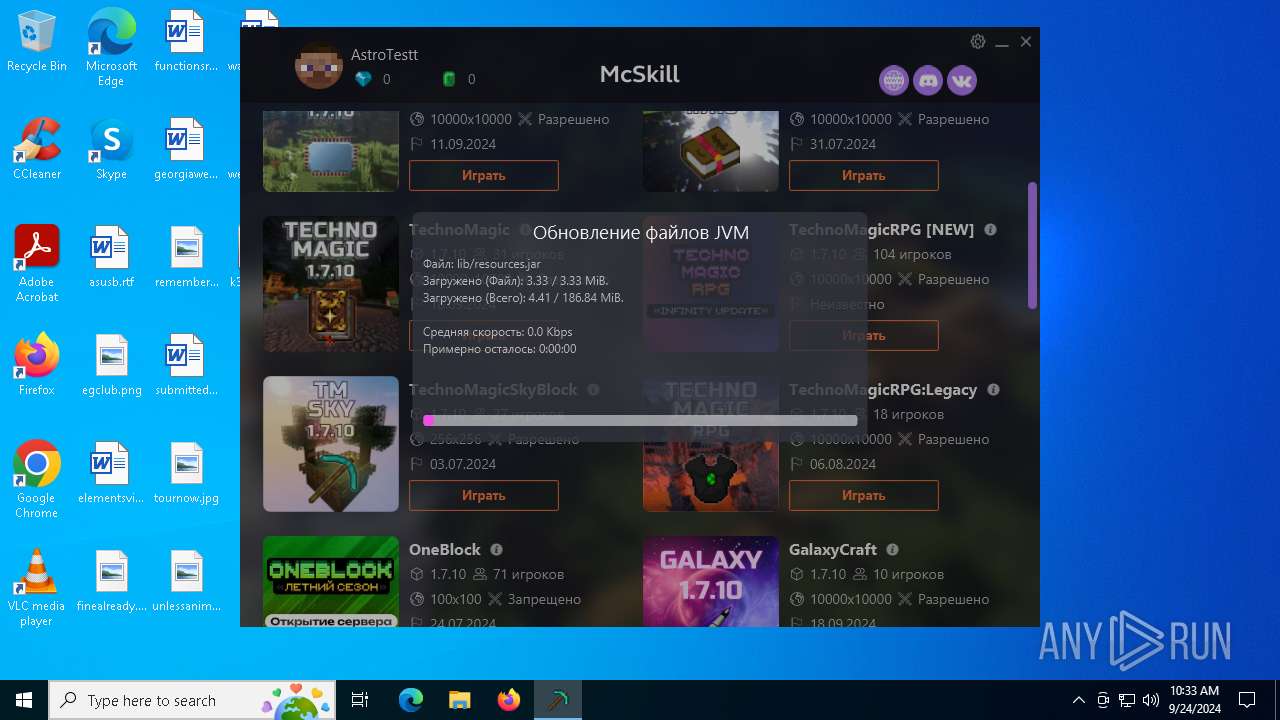
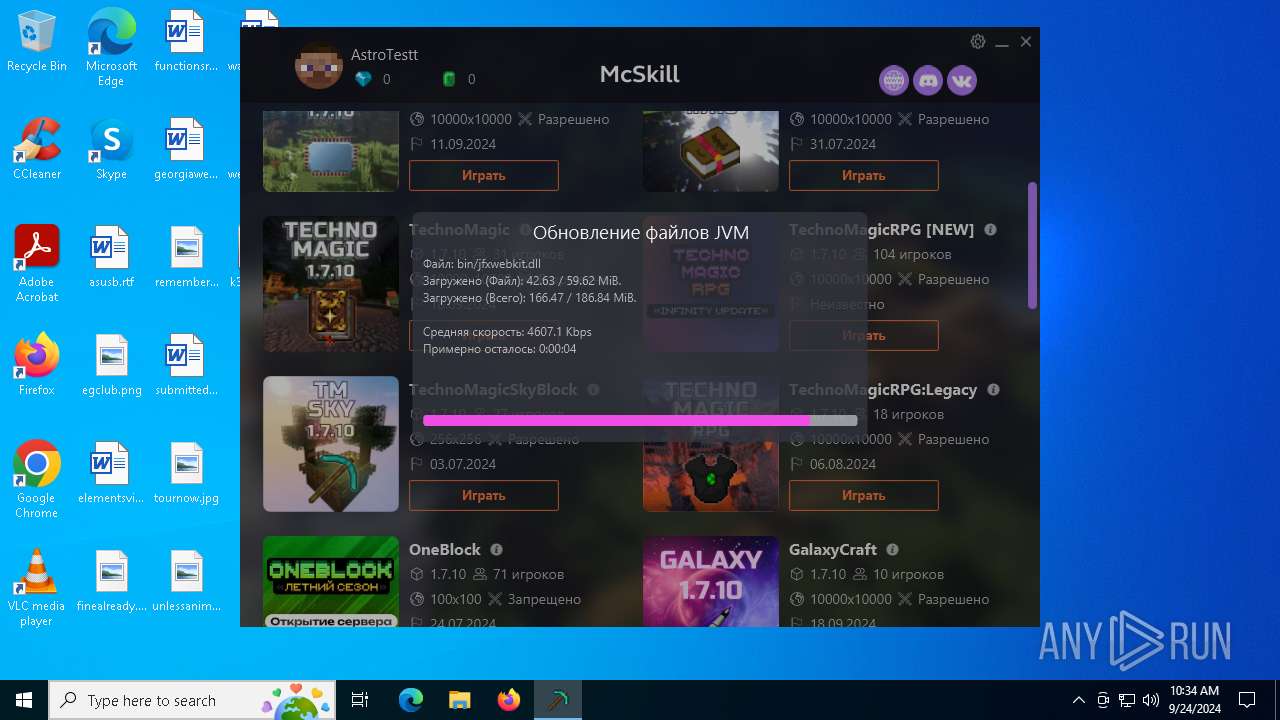
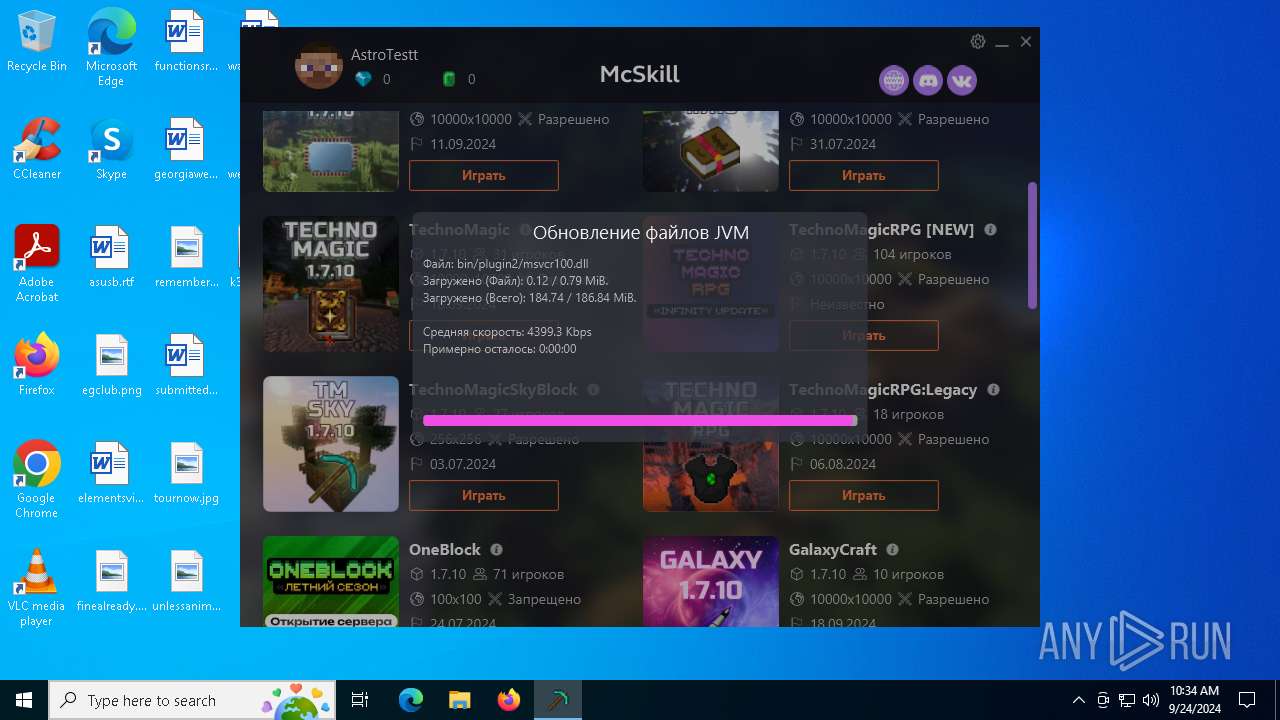
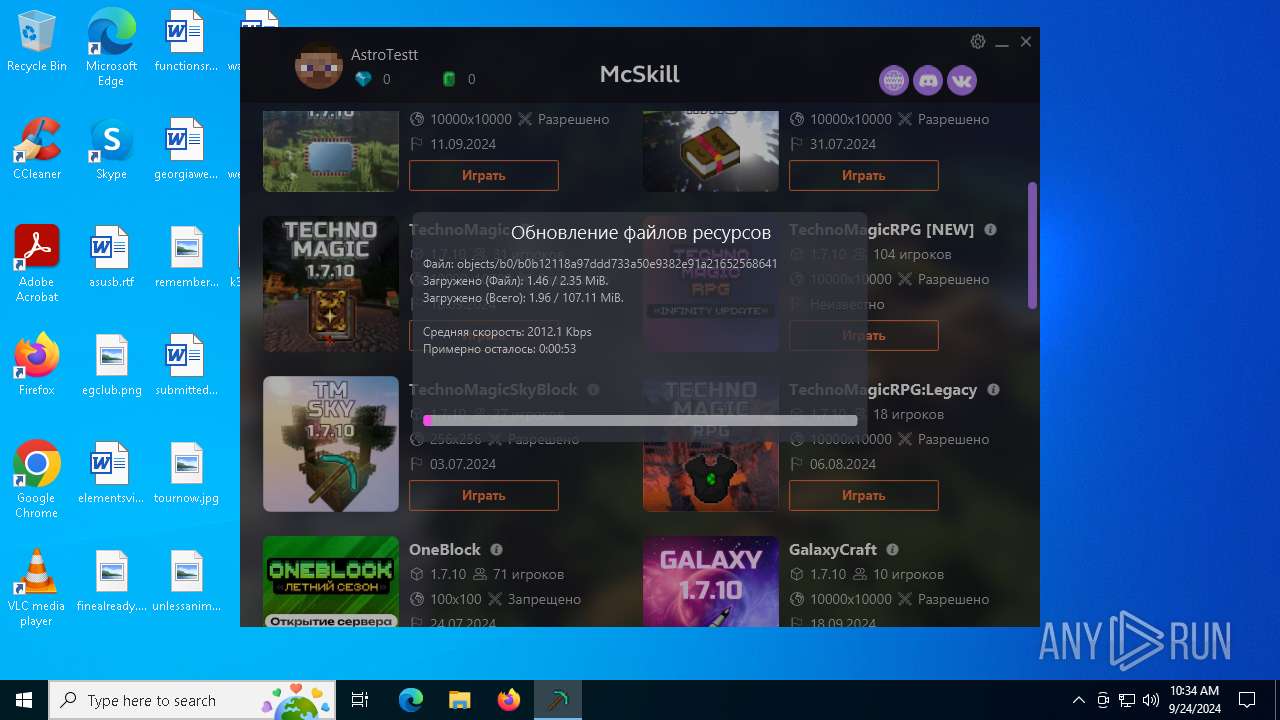
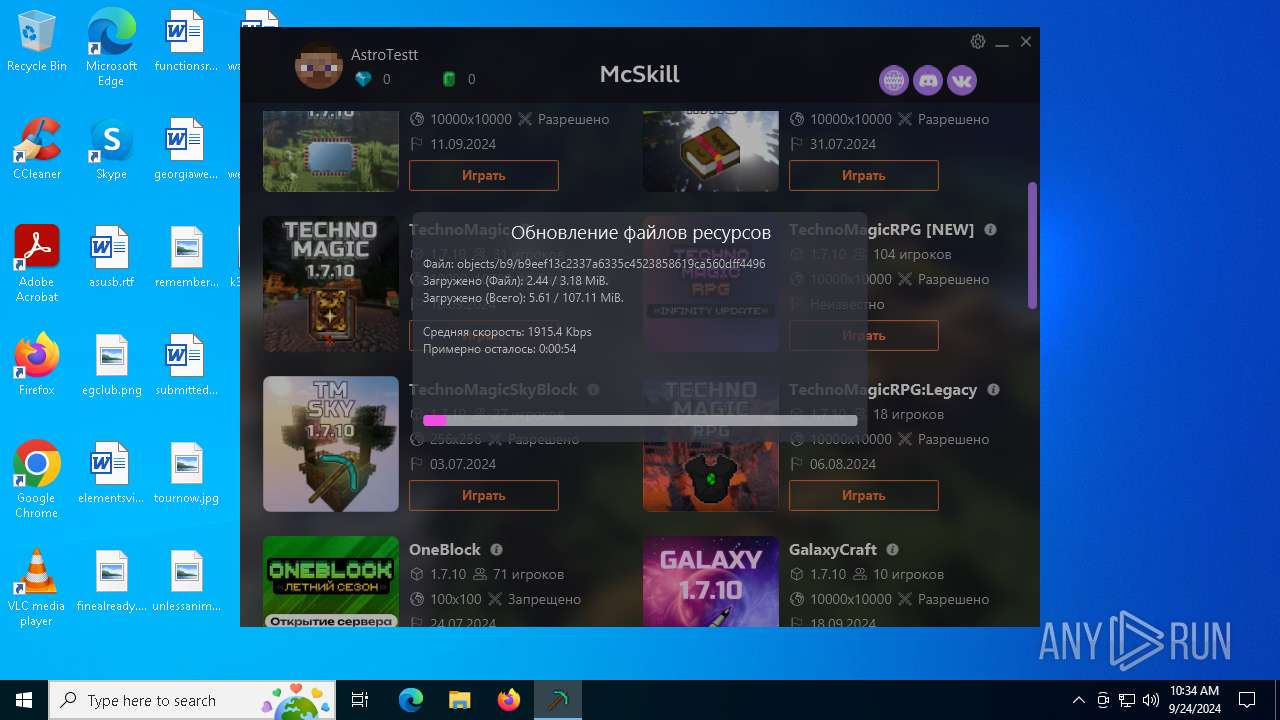
McSkill.exe | "Set JVM path: updates/jdk-win64/bin/java.exe"
|
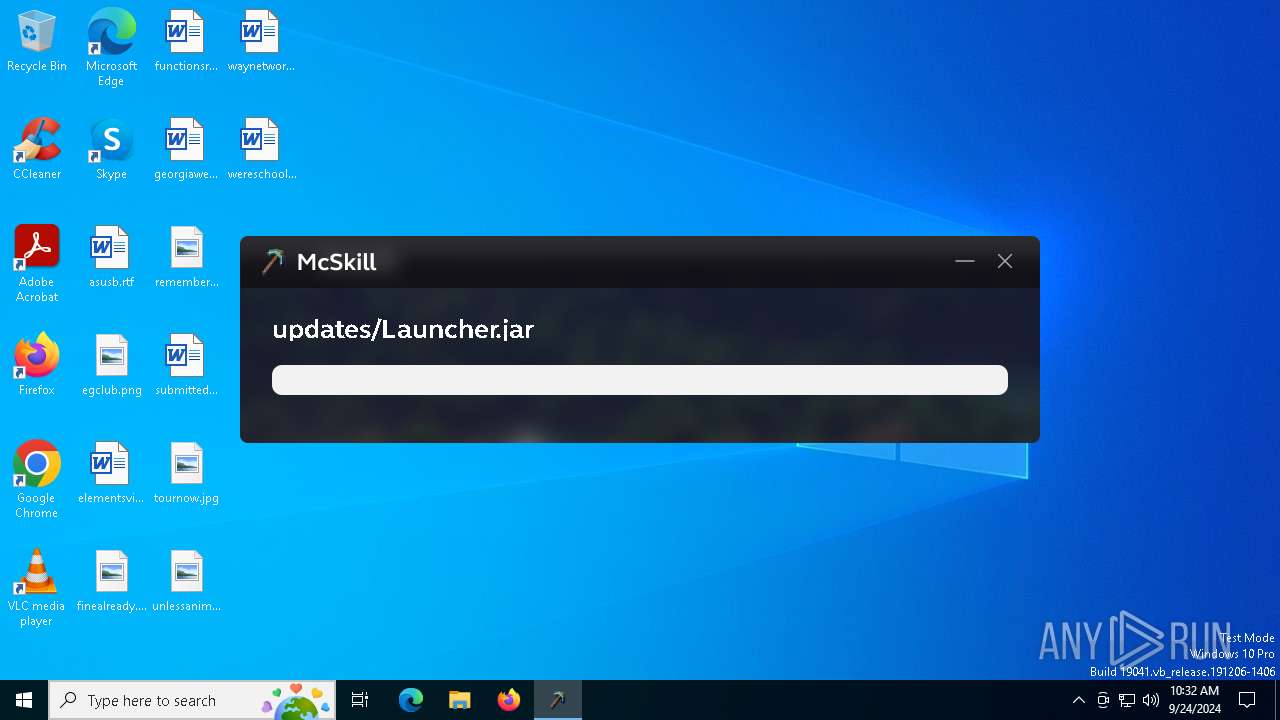
McSkill.exe | "Downloading: https://upd.mcskill.net/updates/Launcher.jar"
|
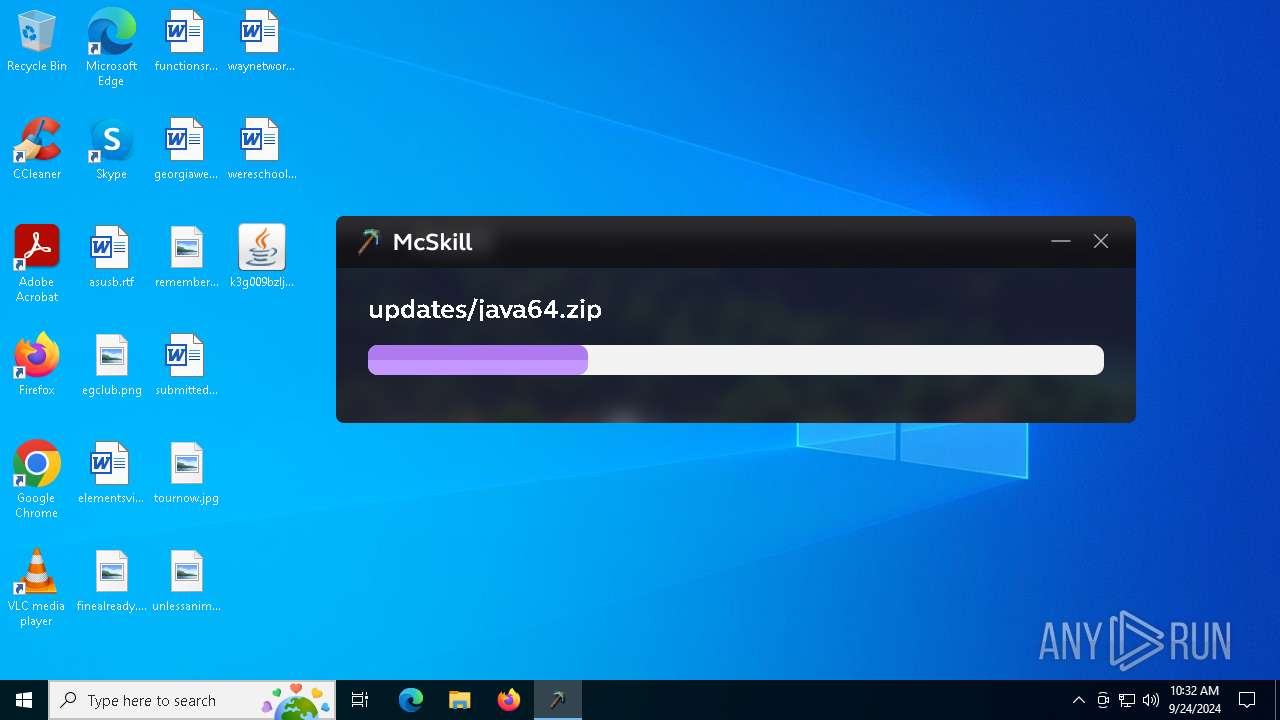
McSkill.exe | "Downloading: https://upd.mcskill.net/updates/java64.zip"
|
McSkill.exe | "Java path: C:/Users/admin/AppData/Roaming/MCSkill/updates/jdk-win64/bin/java.exe"
|
McSkill.exe | "Launcher path: C:/Users/admin/AppData/Roaming/MCSkill/updates/Launcher.jar"
|